Abstract
With the rapid development of blockchain technology, consensus algorithms have become a significant research focus. Practical Byzantine Fault Tolerance (PBFT), as a widely used consensus mechanism in consortium blockchains, has undergone numerous enhancements in recent years. However, existing review studies primarily emphasize broad comparisons of different consensus algorithms and lack an in-depth exploration of PBFT optimization strategies. The lack of such a review makes it challenging for researchers and practitioners to identify the most effective optimizations for specific application scenarios. In this paper, we review the improvement schemes of PBFT from three key directions: communication complexity optimization, dynamic node management, and incentive mechanism integration. Specifically, we explore hierarchical networking, adaptive node selection, multi-leader view switching, and a hybrid consensus model incorporating staking and penalty mechanisms. Finally, this paper presents a comparative analysis of these optimization strategies, evaluates their applicability across various scenarios, and offers insights into future research directions for consensus algorithm design.
1. Introduction
In recent years, distributed technologies have been widely adopted, with blockchain emerging as a prominent example of distributed database technology [1]. Blockchain is renowned for its characteristics of decentralization, immutability, transparency, and anonymity, providing a reliable framework for establishing trust within distributed systems. Initially, blockchain was primarily used to support cryptocurrency transactions and ledger functionalities. Over time, with technological advancements, blockchain has been applied across various domains, including finance [2], supply chain management [3] mechanical engineering [4], and the Internet of Things (IoT) [5].
The reliability of the blockchain system is highly dependent on the design of the consensus mechanism, a technology that enables efficient transaction verification by coordinating the protocols among network nodes and is crucial for maintaining data consistency and operational integrity. In the coalition chain scenario, algorithms such as PBFT, FBFT, DPoS, PoA, and Kafka constitute the mainstream solutions, and their degree of decentralization presents significant differences. Specifically, as follows: (1) Permission-based algorithms: the PoA mechanism [6] adopts a pre-selected authorization node model, and although its centralized architecture improves processing efficiency, there is a risk of single-point failure, and the failure of an authorization node may lead to system paralysis. Similarly, Kafka consensus [7] needs to rely on external message queues, introducing an additional operation and maintenance complexity and potential failure chains; (2) the delegated verification mechanism: DPoS [8] achieves transaction confirmation by electing representative nodes, although it is widely used in coalition chains. The failure of delegated nodes to perform their duties or malicious behavior may trigger a systematic trust crisis; (3) the fault-tolerant balancing scheme: PBFT, in contrast, builds a fault-tolerant framework through a three-phase communication protocol, which maintains network consistency even in the case of a 1/3 node failure. This balancing advantage enables it to gain a widespread application in scenarios such as supply chain traceability and cross-organizational data collaboration, supporting full-process automated validation from production traceability to delivery auditing, significantly enhancing the auditability and execution efficiency of the business chain. The blockchain transaction on-chain process is shown in Figure 1.
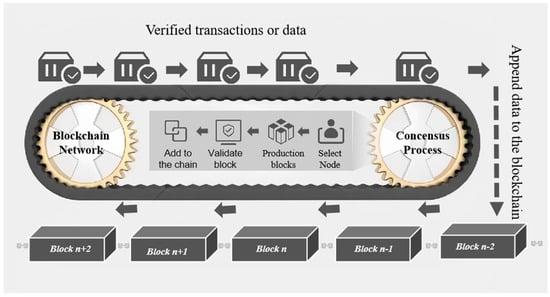
Figure 1.
A blockchain transaction on-chain schematic diagram.
Current reviews of blockchain consensus algorithms often exhibit a generalized breadth-oriented approach, primarily focusing on horizontal comparisons and analyzes of advantages and disadvantages across different algorithms. However, there has been a limited in-depth exploration of the evolutionary trajectory, optimization strategies, and applicability of individual consensus algorithms. Taking the PBFT consensus algorithm as an example, PBFT serves as a core consensus algorithm in consortium blockchain scenarios and has undergone multi-layered improvements in recent years. However, existing studies have extensively discussed improvements to the PBFT consensus, but they have yet to systematically classify the optimization methods of a PBFT consensus across multiple dimensions, nor have they provided a comprehensive evaluation of its network models, security, and applicability.
This paper focuses on the evolutionary trajectory of PBFT improvement algorithms, analyzing three key technical directions: communication complexity optimization, dynamic node management, and incentive mechanism integration. Specifically, it explores the following:
- (1)
- Strategies for reducing communication overhead, and leveraging hierarchical networking and message compression;
- (2)
- Flexible architecture designs that support dynamic node admission and reputation evaluation;
- (3)
- Optimized view-change mechanisms based on a multi-leader node selection approach;
- (4)
- Hybrid consensus models incorporating token staking and penalty mechanisms. Finally, the study constructs a comparative matrix of optimization pathways and a scenario-based applicability framework, providing a structured reference for future research.
This paper systematically explores the evolution path and optimization strategies of the PBFT consensus algorithm in consortium blockchain scenarios. The paper is structured into six core sections. The first section introduces the background and significance of blockchain consensus research. The second section presents the theoretical foundations of blockchain technology and consensus algorithms. The third section reviews mainstream consensus algorithms and their optimization strategies. The fourth section focuses on various improvements to the PBFT consensus algorithm. The fifth section discusses the existing challenges in consensus mechanisms and future development directions. Finally, the sixth section provides a summary of the research conducted in this paper.
2. Introduction to Blockchain
2.1. Blockchain Technology
As a decentralized distributed information management architecture [9], blockchain technology is fundamentally characterized by its ability to establish a trustworthy value transfer network through cryptographic principles and consensus mechanisms. A blockchain system adopts a chain-structured data model, integrates transaction records to form data blocks chronologically, and achieves irreversible linking between blocks with the help of hash pointers, ultimately constructing a distributed ledger system with a full historical traceability [10]. Its decentralized characteristics are rooted in the P2P network architecture, which ensures that each node participates in the collaboration process in a peer-to-peer capacity. At the security level, asymmetric encryption algorithms provide underlying protection for information transmission, and digital signature technology verifies the real identity of the transaction subject. Different from the traditional trust model relying on centralized institutions, blockchain reconstructs the trust paradigm through cryptographic principles and consensus mechanisms: network nodes collaborate to verify the legitimacy of transactions based on the predefined protocols, which not only eliminates the risk of double spending, but also significantly reduces the possibility of data tampering.
At this stage, the evolution of blockchain technology presents multidimensional breakthroughs: the optimization of the consensus layer: a new type of fault-tolerant algorithm significantly improves the verification efficiency; the upgrading of the contract function: Turing-complete smart contracts support the deployment of complex business logic; and the enhancement of cross-chain synergy: the atomic exchange protocol promotes the flow of value between heterogeneous chains [11]. These technological iterations are driving the accelerated penetration of blockchain applications from cryptocurrency to supply chain traceability, digital identity management, intelligent IOT, and other scenarios. However, network throughput bottlenecks, arithmetic resource consumption, and privacy leakage risks are still key factors restricting large-scale landing, giving rise to the continuous exploration of innovative solutions such as slice verification and homomorphic encryption.
A blockchain block is composed of two primary elements: the block header and the block body. Its cryptographic design, combined with a layered architecture, establishes the fundamental technical basis for data immutability. This structure ensures secure data storage through the following three layers:
- (1)
- The information encapsulation layer of the block header
As the core verification unit of blockchain, the block header employs a streamlined data structure to store six key parameters: (1)Version Number (Version): indicates the state of protocol iterations; (2) Timestamp (Timestamp): records the time of block generation; (3) Previous Block Hash (Previous Block Hash): establishes the chain linkage by referencing the preceding block; (4) Merkle Root (Merkle Root): generated through binary tree-based hash computations; (5) Nonce (Nonce): used in the proof-of-work (PoW) computation; (6) Target Hash (Target Hash): defines the current network difficulty threshold. Among these, the Merkle Root acts as a cryptographic identifier, ensuring transaction integrity. It is derived by applying a double-hash (Double Hash) computation to transaction data within the block, iteratively merging hash values layer by layer in a bottom-up manner according to the Merkle tree structure, ultimately forming a unique root hash digest.
- (2)
- The data storage layer of the block structure
The block body organizes verified transaction records using a Merkle tree topology [12], where each leaf node corresponds to the SHA-256 hash value of a single transaction. Intermediate nodes are generated by concatenating the hash values of two lower-level nodes and then hashing the result again. This structure offers the advantage of O(log n) verification complexity, enabling lightweight nodes to validate the existence of specific transactions by simply retrieving the corresponding Merkle path. All transaction data must undergo validation by consensus nodes, including checks for digital signatures, input-output consistency, and other integrity constraints, before being permanently included in the block body.
- (3)
- The collaborative layer of the security mechanism
The block header and block body are irreversibly linked through cryptographic hash functions. Any tampering with a transaction within the block body will alter the Merkle Root hash, which in turn causes a cascading failure through the hash chain in subsequent blocks. The chain’s nested structure uses timestamps and predecessor hashes to establish a temporal and spatial anchor, in conjunction with the security threshold defined by the consensus mechanism. This layered architecture ensures data integrity while optimizing storage efficiency and validation speed. The block header requires only 80 bytes for core verification, while the block body can be elastically expanded to support the storage of massive transaction volumes. The structure of a block is illustrated in Figure 2.
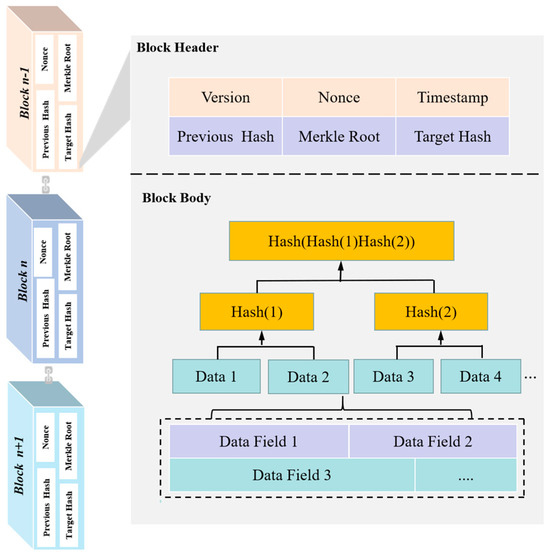
Figure 2.
Block structure diagram.
2.2. The Classification of Blockchain
Blockchain functions as a distributed shared ledger or database, and possesses key characteristics such as decentralization, transparency, and immutability, which ensure its trustworthiness and reliability. Currently, based on its permission scope and access control, blockchain can be classified into public chains [13], private chains [14], and consortium chains [15]. Each type of blockchain has its unique features. Public chains, with their high degree of decentralization and transparency, are widely applied in scenarios such as cryptocurrencies. Private chains, with their lower degree of decentralization and enhanced privacy, provide efficient management and data protection across various sectors. Consortium chains, combining the characteristics of both public and private chains, strike a balance between multi-party collaboration and partial decentralization. They offer significant advantages in traceability and auditability, making it easy to track the source and historical records of transactions [16]. A comparison of the features of different types of blockchains is shown in Table 1 below.

Table 1.
A comparison of features across different types of blockchains.
As shown in Table 1, public blockchains typically rely on proof-based consensus mechanisms and are fully decentralized in terms of governance without the need for third-party institutions to intervene. For example, Ethereum and Bitcoin are typical public blockchain platforms that are primarily utilized in the financial sector. In contrast, private blockchains focus more on privacy and security and often use more robust consensus algorithms. Among them, the Raft mechanism is a common choice, which ensures data consistency and security by selecting a leader node to coordinate the transaction operations of other nodes. Private blockchains are primarily used in internal networks within enterprises or departmental networks and operate under a fully centralized governance structure [17]. Representative application platforms include Viewstamped Replication (VR). Consortium blockchains, on the other hand, feature a partially decentralized structure. They integrate the transparency and decentralization characteristics of public blockchains with the security and data consistency present in private blockchains. Common consensus algorithms for consortium blockchains include PBFT, BFT, and Kafka. Popular open-source platforms used in consortium blockchains include Hyperledger Fabric and FISCO-BCOS.
2.3. Blockchain-Related Surveys
Blockchain research is currently experiencing explosive growth, with the global academic output increasing exponentially. After 2020, the scale of research expanded rapidly, reaching a peak of over 20,000 papers in 2024, highlighting a wave of innovation during the technology’s maturation phase. The research landscape shows significant interdisciplinary characteristics: computer science, which accounts for 60%, and dominates breakthroughs in the technological foundation; engineering and mathematics provide methodological support; and traditional fields such as medicine and energy have seen over 3000 papers, with application scenarios like medical blockchain and green energy chains accelerating their implementation. Research hotspots are extending into emerging directions such as the metaverse and federated learning, with an annual growth rate of 40%. Meanwhile, core technologies such as smart contracts and the Internet of Things (IoT) continue to evolve. These multidimensional breakthroughs are driven both by the intrinsic motivations of technology and by the pressing need for trusted infrastructure in the digital economy era.
According to bibliometric data from Scopus, the system presents a dynamic global panorama of blockchain research from 2008 to 2025. The research trends exhibit a clear temporal gradient: in the early years (2008–2010), the literature was sparsely distributed, but after 2020, there was an explosive increase. From 2021 to 2024, the literature accounted for over 75% of the total, peaking at 20,662 papers in 2024, underscoring the academic focus during the technology’s maturation phase. In terms of subject distribution, there is a significant technological driving force, with computer science (57,535 papers), which accounts for over 60%, leading the research landscape, followed by engineering [18] (32,415 papers) and mathematics (14,415 papers) as core support fields. At the same time, the literature from non-traditional domains such as medicine and environmental science has surpassed 3000 papers, confirming the cross-disciplinary integration trend of technological applications. Regarding regional contributions, China leads the global output with 19,857 papers (64%), followed by the United States, India, and Australia in the second tier. English-language papers account for 98.2%, while Chinese (1626 papers) has become the second most common publication language, reflecting the deepening of the domestic research ecosystem. The institutional network displays a “dual-core drive” feature, with Beijing University of Posts and Telecommunications (922 papers) and the Chinese Academy of Sciences (859 papers) leading academic production. Research themes are organized into a three-tier structure: blockchain foundational technologies (26,661 occurrences), the Internet of Things (11,858 occurrences), and smart contracts (8948 occurrences) form a technological triangle, with medical, supply chain, and energy fields occupying the top application spots. Emerging directions such as the metaverse (of an annual growth of 40%) and federated learning show strong potential. It should be noted that 31.17% of funding sources and 38.71% of literature types are missing, and data for 2025 may include preprints. Nevertheless, the overall data still provides a comprehensive global knowledge map of blockchain research, offering a quantitative benchmark for analyzing technological evolution and identifying key innovators. The visualization of bibliometric data is shown in Figure 3 below.
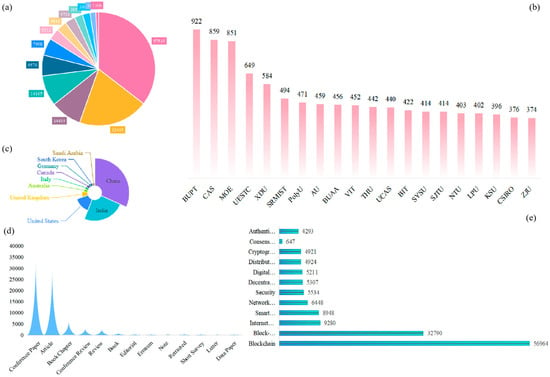
Figure 3.
A visualization of measurement data. (a) The distribution of blockchain research subject areas. (b) A map of blockchain research university contributions. (c) A map of blockchain research country contributions. (d) The distribution of blockchain literature types. (e) A blockchain research high-frequency keyword word cloud.
2.4. The Blockchain Economic Incentive Mechanism
The fundamental nature of blockchain is to provide decentralized services, and some even argue that it functions as a public good in an economic sense. However, the sustainability of any service relies on both cost maintenance and economic incentives. Given the absence of a centralized authority in blockchain architecture, the system must rely on incentive mechanisms to ensure long-term node participation and network stability.
Incentive mechanisms serve not only as the foundation of blockchain operations but also as the lifeblood of its decentralized public infrastructure. Their core objective is to align individual economic rationality with the system’s overarching goals by integrating cryptographic constraints with game-theoretic design to establish a sustainable value exchange framework. On one hand, incentive mechanisms compensate for computational, storage, and operational costs through block rewards and transaction fees, ensuring the reliability and availability of the infrastructure. On the other hand, they deter malicious behavior through dynamic adjustment measures such as staking mechanisms, yield decay, and penalty enforcement, thereby enhancing the network’s resistance to attacks and maintaining its integrity. More importantly, incentive mechanisms foster a self-reinforcing economic loop: initial liquidity is injected through block rewards, market pricing is shaped by transaction fees, and the value capture is achieved via token burning or staking, ultimately leveraging network effects to drive a positive feedback cycle. This intricately designed incentive topology enables trustless collaboration among unacquainted participants in an open environment, effectively resolving the classic “tragedy of the commons” problem in distributed systems. As a result, blockchain can achieve secure, trustworthy, and sustainable public governance even in adversarial settings.
Table 2 presents a comparison of validator rewards across different consensus mechanisms. Consensus mechanisms aim to balance security, efficiency, decentralization, and economic incentives. PoW ensures high security but consumes substantial energy, while PoS and DPoS enhance efficiency at the cost of decentralization, posing a risk of wealth concentration. PBFT and its variants offer a high throughput but lack strong economic incentives. In contrast, Paxos and Raft, designed for distributed computing, prioritize consistency over economic rewards. Paxos provides a robust fault tolerance but is complex to implement, whereas Raft is simpler in design but less suitable for large-scale blockchain networks. Ultimately, the choice of a consensus mechanism depends on the trade-offs among decentralization, performance, and incentives.

Table 2.
A comparison of validator rewards in consensus mechanisms.
3. An Introduction to Mainstream Consensus Algorithms
As the core mechanism of distributed systems, consensus algorithms aim to address the issues of data consistency and trustworthy collaboration in multi-node environments. Their value has expanded beyond the early blockchain domain (such as Bitcoin’s PoW mechanism) into a wide range of interdisciplinary scenarios. As illustrated in Figure 3, the research and application of consensus algorithms follow a multidimensional, integrated approach. Firstly, the foundational technological layer encompasses key areas of computer science, such as distributed systems, cryptography, and cybersecurity, which provide the theoretical basis for the design of consensus mechanisms. In the finance and payment sectors (e.g., Bitcoin, financial payments, energy trading), consensus algorithms highlight their critical role in decentralized trust building. In the physical economy and supply chains (e.g., agricultural traceability and supply chain management), they enhance transparency and efficiency through immutable distributed ledgers. Emerging front-end scenarios (e.g., healthcare, the Internet of Things, and digital intellectual property) further explore the potential of algorithms in privacy protection, resource coordination, and ownership verification. Cross-disciplinary fields, such as virtual gaming economies and specific economic models (e.g., Blackmixtm), demonstrate the adaptability of consensus mechanisms in complex collaborative relationships. Additionally, Figure 4 provides a systematical overview of outlines of the implementation theories of commonly used consensus algorithms and the practical application scenarios of each algorithm.
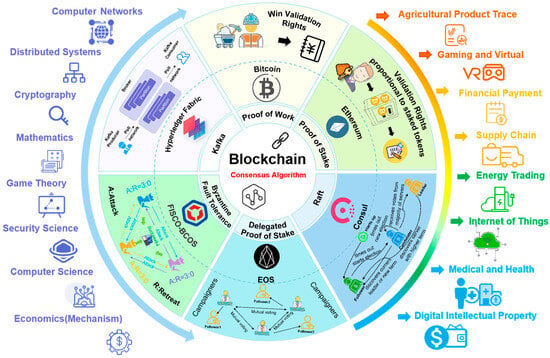
Figure 4.
An overview of blockchain consensus algorithms.
3.1. The Mainstream Consensus Algorithms of Public Blockchains
The commonly used consensus algorithms in public blockchains include PoW and PoS. PoW relies on computational power competition, ensuring high security but consuming a substantial amount of energy. PoS selects validators based on stake weight, enhancing efficiency while posing a risk of centralization. Different consensus algorithms balance security, efficiency, and decentralization, making them suitable for various blockchain applications.
3.1.1. POW
Proof of Work (PoW), as the fundamental consensus mechanism of distributed ledger technology [19], relies on solving cryptographic puzzles and computational resource competition to achieve transaction validation and ledger consistency in a decentralized environment. In terms of technical implementation, the PoW mechanism requires participating nodes to perform high-intensity hash calculations on the block header parameters, which include a random number (Nonce). Nodes search for a valid hash solution by iterating through different Nonce values to meet a preset difficulty threshold (such as a constraint on the number of leading zeros) [20]. The first node to complete the computation gains the right to add the block to the ledger and distributes the new block across the network through a broadcast mechanism. Other nodes can quickly verify the validity of the computation based on the one-way nature of the hash function and synchronize the global state by following the “longest chain rule”, thus constructing a distributed consensus system with resistance to Sybil attacks.
From a security perspective, PoW establishes a dual-defense mechanism by introducing a competitive computational model. The PoW consensus process schematic is shown in Figure 5. This security architecture based on mathematical certainty allows public blockchains such as Bitcoin to ensure censorship resistance and data finality even in the absence of centralized regulation. However, the PoW mechanism’s high reliance on computing power brings about huge energy consumption, which has become a major bottleneck restricting the widespread application of blockchain technology. Therefore, the industry is gradually exploring more energy-efficient consensus schemes, such as Proof of Stake (PoS). By optimizing the verification process and redesigning the incentive mechanism, researchers are pushing the distributed system towards sustainability.
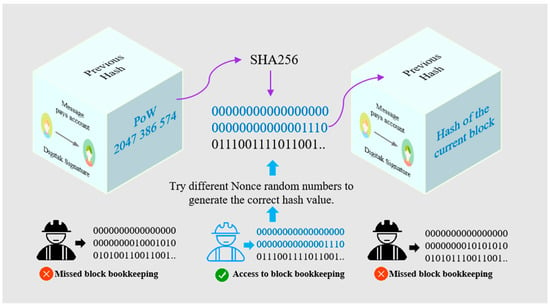
Figure 5.
A PoW consensus process schematic.
Although PoW is still the core consensus mechanism of blockchain, its high energy consumption has prompted academics to actively seek more efficient alternatives. To reduce the environmental impact of PoW, Noureddine Lasla et al. [21] proposed the Green-PoW algorithm, which grants the runner-up in a mining competition the exclusive right to compute the subsequent blocks, in order to reduce unnecessary energy consumption while maintaining network security. In addition to energy-saving optimization, research also focuses on the dual utilization of computational resources. For example, the Proof of Learning (PoLe) consensus mechanism proposed by Yixiao Lan et al. [22] attempts to combine the PoW computation process with neural network optimization so that blockchain computing can serve machine learning tasks at the same time.
Further innovations address emerging security challenges within the blockchain ecosystem. Jiahui Chen et al. [23] developed a post-quantum PoW variant tailored for smart city applications, integrating quantum-resistant cryptographic primitives to defend against future quantum computing threats. Similarly, Mostefa Kara et al. [24] improved PoW’s energy efficiency with the Computation-and-Waiting PoW (CW-PoW) protocol, introducing multi-round proof verification to minimize redundant computation. The adaptability of PoW to different network architectures has also been explored. In decentralized opportunity networks (OppNets), Sanjay Kumar Dhurandher et al. [25] demonstrated the feasibility of PoW through a blockchain-based secure routing protocol (BDRP), ensuring tamper-proof and decentralized routing decisions. For hierarchical data ecosystems, Ronghua Xu et al. [26] designed a federated ledger framework (Fed-DDM) using scalable PoW to synchronize multiple private sub-ledgers, enabling secure cross-network data markets.
PoW’s applications have expanded to specific blockchain implementations across various fields. In healthcare IoT systems, G. S. Gunanidhi et al. [27] proposed an enhanced PoW (E-PoW) consensus mechanism to enhance the data security and improve the operational efficiency of patient monitoring. Similarly, V. Saini et al. [28] validated PoW’s practicality in peer-to-peer energy trading within residential communities, emphasizing its role in ensuring transaction integrity and secure payment mechanisms. Finally, Yu Tang et al. [29] combined PoW principles with edge computing through the Hedera consensus algorithm, incorporating permissionless access, scalability, and energy efficiency, suitable for multi-access edge computing (MEC) networks supporting the IoT. Overall, these studies highlight the evolution of PoW from a single-function consensus protocol to a flexible framework that adapts to energy constraints, security demands, and heterogeneous network environments.
As shown in Table 3, the existing research on improvements to the PoW algorithm can be categorized into three systematic directions: resource allocation optimization, security enhancement, and functional utility expansion. In the area of resource allocation, improvements focus on dynamically adjusting computational power allocation strategies (such as multi-round verification mechanisms and edge computing collaboration) to reduce redundant computations, thereby significantly lowering energy consumption. The security enhancement direction is centered on addressing emerging threats, including the integration of quantum-resistant cryptography to defend against quantum attacks, as well as the development of parameter optimization mechanisms based on specific scenarios to improve data protection in particular fields (such as the healthcare IoT). Research on functional expansion seeks to move beyond the traditional goal of mining, exploring computational power reuse technologies (such as the integration of machine learning tasks) and layered ledger architectures. These research directions aim to enhance the practical value of PoW computing resources and achieve cross-domain collaboration and data synchronization. This trend shows that the PoW mechanism is evolving from an energy-intensive consensus to a configurable multi-objective framework by optimizing the verification logic, upgrading the cryptography technology, and improving the utilization of computing resources. This technological evolution not only alleviates the energy bottleneck of PoW but also enhances the flexibility of blockchain in heterogeneous networks and vertical application scenarios, and provides new ideas for optimizing the consensus mechanism in terms of security, sustainability, and value reuse. Although optimizations such as Green-PoW and Compute-and-Wait reduce redundant computations and energy consumption to some extent, they fail to fundamentally address the high energy costs and mining centralization inherent in PoW mechanisms. These improvements often require cross-domain technological integration and quantum-resistant designs, adding to implementation complexity while potentially undermining decentralization and posing long-term security risks.

Table 3.
A comparison of PoW improvement algorithms.
3.1.2. PoS
Proof of Stake (PoS) is a distributed consensus mechanism based on the economic interests of token holders [30]. It replaces the traditional proof of work (PoW) model of computational power competition with a probabilistic mechanism for allocating block creation rights, aiming to address the energy efficiency bottleneck in blockchain systems. In the PoS framework, validating nodes participate in the consensus process by staking a certain amount of native tokens. The system dynamically allocates block creation probabilities based on parameters such as the staking ratio and token holding duration, while using Byzantine fault tolerance (BFT) algorithms to validate transaction validity. Compared to the hash power consumption of PoW, PoS ensures network security through economic incentives, as attackers would need to control the majority of tokens in the network to launch an effective attack. However, PoS can lead to some degree of centralization, as individuals or entities with more tokens have a higher chance of becoming validators. To address this, Current PoS variants, such as Delegated Proof of Stake (DPoS), further enhance consensus efficiency and decentralization by introducing mechanisms like validator elections and random seed generation.
The development of blockchain consensus mechanisms has witnessed a paradigm shift toward the Proof of Stake (PoS) protocol, driven by the need to overcome the inherent limitations of traditional Proof of Work (PoW) systems. PoW, exemplified by Bitcoin’s mining mechanism, has gained widespread attention due to its high energy consumption and environmental impact caused by its computation-intensive operations [31]. In response, PoS has emerged as a sustainable alternative, significantly reducing energy demands by replacing competitive computational challenges with validators’ stakes [32]. Ethereum’s transition to PoS during its “Merge” event is a prime example of this shift, marking a pivotal moment that made Ethereum the largest cryptocurrency by market capitalization to adopt this consensus model [33,34]. Academic research on PoS has systematically addressed its various challenges and opportunities. Theoretical frameworks have explored reward distribution mechanisms to incentivize honest participation [32], while security analyzes have identified vulnerabilities such as remote attacks and validator collusion [35]. Game theory models have further analyzed the strategic interactions between validators, providing insights into equilibrium states under adversarial conditions [36]. To facilitate systematic progress, Lina Ge et al. [37] categorized PoS improvement proposals based on objectives like scalability and attack resistance, offering guidance for algorithm selection in different applications. Recent innovations have focused on optimizing validator economics and enhancing network decentralization. For instance, emerging solutions like EigenLayer and Lido have introduced novel staking architectures to lower entry barriers for validators, increase capital liquidity, and reduce centralization risks [38].
These developments aim to balance the security guarantees inherent in PoS ecosystems with the need for inclusive participation. Despite progress, gaps remain in understanding validator behavior dynamics, particularly in incentive coordination and governance frameworks [38]. Nevertheless, collective advancements highlight the potential of PoS to address scalability, energy efficiency, and security challenges that are limitations of traditional PoW systems. Ethereum’s successful transition exemplifies the feasibility of large-scale PoS adoption, marking a key milestone in the evolution of blockchain toward sustainable and resilient consensus models [36]. Future research directions emphasize the integration of hybrid consensus mechanisms, formal verification tools, and cross-chain interoperability to further refine the applicability of PoS in heterogeneous blockchain environments.
As shown in Table 4, the existing improvements to the PoS algorithm can be systematically categorized into three main directions: the optimization of the incentive mechanism, the enhancement of security mechanisms, and structural efficiency improvements. In the realm of incentive mechanisms, dynamic reward distribution models (such as evolutionary game theory) incentivize honest behavior by adjusting staking reward ratios, while re-staking and liquidity token schemes (such as Eigen Layer) reduce participation barriers and promote network decentralization. The security enhancement direction focuses on attack defense and behavioral modeling, including defense strategies against long-range attacks and validator collusion, as well as a game-theoretic equilibrium analysis of ransom attacks, systematically improving the protocol’s resistance to malicious activity. Structural optimization focuses primarily on improving efficiency, including lightweight designs that reduce communication overhead (e.g., threshold signatures vs. dynamic committees) and standardized guidance for classification frameworks that help optimize algorithm selection. In addition, formal verification tools leverage mathematical abstractions to ensure the reliability of key aspects (e.g., verifier exit). These optimizations reflect the fact that the core of the PoS development path lies in balancing security, efficiency, and participation. However, PoS significantly enhances energy efficiency through stake-based validation and dynamic incentive mechanisms, but its optimization strategies may exacerbate power imbalances. Large stakeholders inherently hold greater influence in the consensus process, increasing the risk of centralization. Additionally, the design of incentive and penalty mechanisms is highly complex, and any imbalance could lead to unfair competition among validators, ultimately compromising network security and stability. By dynamically adjusting economic incentives, strengthening security, and optimizing the network architecture, the blockchain consensus mechanism is evolving towards a higher robustness and lower energy consumption. Future research may further explore hybrid consensus schemes and cross-chain collaboration to meet the complex needs in heterogeneous environments.

Table 4.
A comparison of PoS improvement algorithms.
3.2. The Mainstream Consensus Algorithms of Private Blockchains
Common consensus algorithms used in private blockchains include Raft and Paxos. Raft achieves consistency through leader election and log replication, with a simple structure, making it suitable for private blockchains with fewer nodes and high consistency requirements. Paxos ensures consistency through a voting mechanism, which, although more complex, can tolerate partial node failures and is suited for distributed systems with high consistency needs. These algorithms effectively guarantee data consistency and fault tolerance in private blockchains.
3.2.1. Paxos
The Paxos consensus mechanism, proposed by Leslie Lamport in 1990, is a classic solution to the distributed consistency problem [40], whose core goal is to synchronize the state of nodes in asynchronous network environments, so that the system can reach a majority decision even if some of the nodes fail. The protocol adopts a two-stage interaction process to achieve a fault-tolerant consensus, i.e., the “propose–accept” model. In the first phase (preparation phase), the proposer submits an incrementally numbered proposal to the acceptor to obtain the commitment of the majority of the nodes and to lock the priority. In the second phase (acceptance phase), the proposer submits a final proposal based on the numbering, and a decision is reached if a majority of the acceptors agree. The Paxos mechanism maintains a balance between security and activity, and can theoretically tolerate up to half of the node failures. However, its implementation complexity makes it difficult to apply directly in practice, prompting the development of optimized versions such as Multi-Paxos and Raft, which improve utility by simplifying the process of role partitioning and log replication.
Consensus algorithms are a key infrastructure for achieving reliability in distributed computing environments. Recent academic research has focused on refining and expanding the theoretical foundation of the Paxos protocol, which serves as the cornerstone of distributed consensus. Heidi Howard et al. [41] established a comparison framework between Paxos and Raft, emphasizing their shared commitment to fault tolerance while contrasting their methods for leader election dynamics. To improve the accessibility of teaching, Seif Haridi et al. [42] structured a lecture system around the principles of leader-based sequential Paxos, bridging the gap between abstract theory and practical implementation for learners. Isaac Sheff et al. [43] introduced Heterogeneous Paxos, showcasing an innovative architecture that achieves optimal consensus in three message exchanges, addressing heterogeneity in node roles, network assumptions, and fault models. At the same time, significant progress has been made in formalizing the security guarantees of Paxos. Aman Goel et al. [44] are pioneers in using structural invariants derived from Lamport’s original specification to apply automated proof techniques, simplifying the verification of this historically complex algorithm. Xing et al. [45] proposed an automatic alert method based on Paxos algorithm for anomalous data in power grid reports. The grid report data is automatically collected using RPA technique, and then the isolated forest algorithm with incremental learning of subforest gradual update is used to detect anomalies in the collected data. Heidi Howard et al. [46], in “Relaxed Paxos”, revisited the quorum requirements, proposing a two-phase consensus model that reduces synchronization overhead while maintaining correctness. Pasindu Tennage et al. [47] introduced Baxos, a leaderless variant of Multi-Paxos, which employs a random backoff mechanism to mitigate adversarial attacks. Pasindu Tennage et al. [48] combined Multi-Paxos with modular state machine replication in Mandator and Sporades, achieving high-throughput consensus in geographically distributed systems. Siswandi Agung Hidayat et al. [49] conducted empirical evaluations using NS3 simulations to quantify the performance trade-offs between Paxos, Raft, and PBFT, emphasizing the relevance of consensus mechanisms for delay-sensitive applications such as blockchain systems. Theoretical advancements continue to shape the trajectory of the field. Murdoch J. Gabbay et al. [50] contributed a declarative framework using three-valued modal logic to formally specify distributed algorithms like Paxos, enabling a rigorous analysis of system behavior through mathematical abstraction. This work reflects the growing intersection between formal methods and practical consensus engineering.
As shown in Table 5, on the theoretical level, some studies focus on the development of formal verification tools. By using automated theorem proving or modal logic frameworks, these studies shift the validation of Paxos correctness from empirical derivation to mathematical provability, significantly enhancing the rigor of protocol design. In terms of performance optimization, efforts have been made to reduce message complexity (such as in three-message consensus), introduce random backoff mechanisms, or relax quorum constraints. These strategies help lower synchronization overhead and improve the system’s tolerance to network dynamics and adversarial environments. For scenario adaptation, improvements have been achieved through modular design (such as hierarchical state machine replication), hybrid node role support, or cross-protocol performance comparison, which extend the applicability of Paxos in wide-area networks, educational settings, and heterogeneous networks. Overall, these advancements highlight a common evolutionary trajectory for Paxos: while maintaining basic fault tolerance, the protocol balances the demands of theoretical correctness, real-time efficiency, and scenario specificity. This is accomplished through dynamic adjustments in leader mechanisms, message propagation strategies, or validation rules, thus driving the consensus algorithm toward a greater generalization and robustness. However, the practical optimization of Paxos is often challenging for large-scale distributed systems due to its complex implementation and high message transmission overhead.

Table 5.
A comparison of Paxos improvements.
3.2.2. Raft
Raft, a significant advancement in the field of distributed consensus algorithms [51], was introduced by Diego Ongaro and John Ousterhout in 2014. Its primary objective is to enhance the clarity and maintainability of consensus protocols by optimizing the state machine replication process, thereby better meeting the needs of practical engineering practices. The algorithm is based on the Strong Leader model and divides the system’s operation into three key modules: leader election, log replication, and safety.
During the leader election phase, nodes initiate the election process through a random timeout mechanism. The election process ensures the emergence of a unique leader based on the principles of term (Term) increment and majority voting, effectively coordinating the system’s operation. Once the system enters the log replication phase, the leader node takes on the responsibility of receiving client requests and synchronizing log entries to the follower nodes. After the majority of follower nodes confirm the log entries, the leader node can commit the log and update the state machine, driving the continuous evolution of the system’s state. In terms of ensuring safety, the Raft mechanism introduces Log Matching and Leader Restriction mechanisms to maintain consistency in the system’s state. Even in extreme scenarios where no more than half of the nodes fail, these mechanisms ensure that the system remains stable and operational. The Raft consensus process is shown in Figure 6.
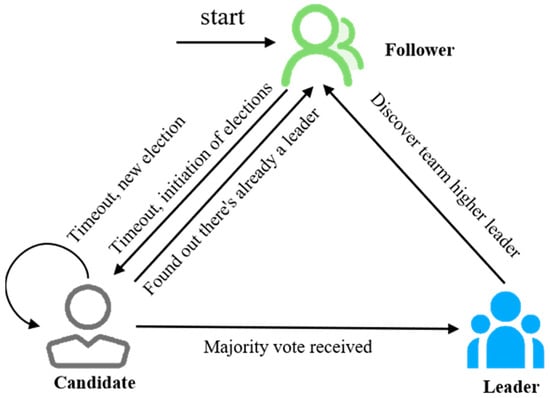
Figure 6.
A Raft consensus schematic diagram.
Compared to the theoretical completeness of the Paxos algorithm, the Raft consensus mechanism significantly reduces the complexity of algorithm implementation by clearly defining the roles and state machines (including follower, candidate, and leader roles) and designing an intuitive log replication process. At the same time, Raft demonstrates a comparable performance to Paxos, showcasing a good balance.
Raft is a leader-based consensus algorithm that has become a focal point for innovation. Researchers have adjusted its core principles to address challenges in real-time systems, adversarial environments, and cross-industry use cases. Yuchen Wang et al. [52] redesigned Raft to optimize its performance in high real-time and adversarial settings, demonstrating an enhanced fault tolerance through dynamic leader reconfiguration. This work laid the foundation for platform-specific adaptations, such as Wei Fu et al. [53] integrating Raft into Hyperledger Fabric. By improving the log replication protocol and leader election mechanism, measurable improvements in blockchain transaction throughput were achieved, highlighting Raft’s versatility in permissioned blockchain architectures.
Industry applications have driven the protocol’s new implementations. In supply chain management, Isti Surjandari et al. [54] leveraged Raft’s transparency guarantees to design a halal industry blockchain network, ensuring traceability across multi-channel transactions. Meanwhile, Anastasios Alexandridi et al. [55] validated the applicability of Raft in healthcare through a Hyperledger-based patient data management system, emphasizing compliance with regulatory privacy standards. For enterprise financial systems, Na Du et al. [56] extended Raft’s scalability through a Multi-Raft variant optimized for supply chain finance, introducing a weighted node election mechanism to balance load distribution in large consortium blockchains. The Internet of Things (IoT) paradigm has given rise to specialized Raft derivatives. Lu Hou et al. [57] combined Raft with multi-access edge computing (MEC) to develop a smart transaction migration framework that reduces latency in private blockchain networks while maintaining Byzantine fault tolerance. Building upon this, Xiaojun Xu et al. [55] introduced a weighted leader selection algorithm that prioritizes gateway functionality, addressing resource heterogeneity in IoT deployments and mitigating Sybil attack risks. As decentralized systems expand into 6G infrastructure, the behavior of Raft in wireless environments has been rigorously analyzed. Haoxiang Luo et al. [58] conducted a comparative study of Raft and PBFT under non-ideal THz/mmWave channel conditions, quantifying the performance degradation caused by Rayleigh fading and path loss. Additionally, Yuetai Li et al. [59] established probabilistic reliability metrics for Raft in wireless mesh networks, enabling data-driven deployment strategies that consider node mobility and intermittent connectivity. J. H. F. Battisti et al. [60] systematically evaluated the protocol’s versatility in the blockchain ecosystem, benchmarking Raft’s efficiency in Hyperledger Fabric and Ethereum cloud deployments. Their findings revealed a context-dependent trade-off between consensus latency and resource utilization, providing architectural guidance for platform selection in enterprise environments.
Overall, these studies demonstrate that Raft has evolved from a general consensus protocol into a modular framework adaptable to specific industry requirements. While successful in vertical applications, horizontal challenges remain, particularly in balancing the simplicity of the algorithm with the complexity of cross-domain interoperability. Emerging research directions include integrating machine learning into adaptive leader election and developing hybrid consensus models that combine the advantages of Raft with complementary protocols such as PBFT. These innovations are expected to further solidify Raft’s role in next-generation decentralized systems, from IoT edge networks to smart infrastructures supporting 6G.
As shown in Table 6, existing research on improvements to the Raft algorithm can be systematically categorized into three main directions: performance optimization, scenario-specific adaptation, and network environment adaptability enhancement. Performance optimization approaches focus on improving the real-time processing efficiency and fault tolerance by reducing consensus delay and balancing load pressure through dynamic leader reconfiguration, streamlined log replication protocols, and weighted election mechanisms. Scenario-specific adaptation designs are tailored to meet the specific requirements of various vertical domains. Examples include multi-channel transaction tracking in supply chain scenarios, privacy and compliance optimization in medical healthcare data management, and lightweight Byzantine fault tolerance frameworks for IoT edge networks, highlighting the customizability of Raft in cross-industry applications. Network adaptability improvements focus on wireless communication environments (such as 6G non-ideal channels and node mobility). By employing probabilistic reliability modeling and quantifying channel loss, these enhancements strengthen the protocol’s robustness in dynamic topologies and high-interference scenarios. These improvements indicate that Raft’s evolutionary path is centered on modular expansion, adjusting election logic, log management strategies, and network interaction rules to balance algorithm simplicity with the need for an adaptation to complex scenarios. Future research may need to further explore hybrid consensus models (such as incorporating the fault tolerance mechanism of PBFT) and intelligent decision-making technologies (such as machine learning-driven dynamic parameter tuning) to address the challenges of decentralized systems in ultra-large-scale, highly heterogeneous environments.

Table 6.
A comparison of Raft consensus improvements.
3.3. The Mainstream Consensus Algorithms Used in Consortium Blockchains
The mainstream consensus algorithms in consortium blockchains include DPoS, Kafka, and PBFT, with PBFT being the most widely adopted. This is due to its participation of multiple nodes in jointly validating transaction consistency and its ability to tolerate up to one-third of Byzantine nodes, which has contributed to its widespread recognition.
3.3.1. DPoS
Delegated Proof of Stake (DPoS) [62] is a derivative of Proof of Stake (PoS), which was first applied to the PeerCoin system in 2013 to address the resource consumption issue of the PoW mechanism. Under PoW, nodes need to compete for block rights through a large number of computations, while PoS reduces the computation consumption by pledging tokens to determine the block production rights. Although PoS still relies on hash computation, it eliminates the need for continuous brute-force Nonce solving, and the hash value only needs to be computed once in each round of consensus. The higher the number of tokens held by the node, the higher the probability of obtaining the right to produce blocks.
DPoS introduces a proxy mechanism on this basis, where token holders can pledge tokens in exchange for voting rights and elect representative nodes responsible for block production. This model is similar to the operation of a company’s board of directors, in which the token holders delegate the block production duties to more specialized nodes, while still sharing the block production rewards. The node with the highest number of votes becomes the block producer, from which a node is elected in each consensus round to generate a new block and broadcast it to other producers for verification. If a node fails to produce a block in time or generates an invalid block, it will be disqualified and a replacement node will be re-elected to ensure a stable operation of the system.
DPoS has evolved into a versatile framework that balances efficiency, security, and scalability in decentralized systems. Recent academic research has focused on improving its core mechanisms while expanding its applicability across various technological and social domains. The fundamental improvements of DPoS address both theoretical and practical challenges. Qian Hua et al. [63] pioneered an optimized DPoS variant that enhances blockchain network security through dynamic validator selection, reducing vulnerabilities to Sybil attacks. Building on this, Yaxing Wei et al. [64] integrated anomaly detection and reward–punishment mechanisms into DPoS, creating a self-regulating system that mitigates malicious behavior within the Internet of Things (IoT) ecosystem. Additionally, Yong Liu et al. [65] introduced adjacency voting and fuzzy value analysis to improve decentralization metrics, ensuring fair participation in the consensus process without compromising computational efficiency. DPoS has demonstrated its adaptability to specific industry needs. In the transportation sector, Di Wang et al. [66] utilized consortium blockchain and DPoS to protect carpool data flows, enabling privacy-preserving transaction validation for urban transportation systems. In public governance, Yuetong Chen et al. [65] redesigned DPoS to facilitate collaborative network opinion management, embedding fairness constraints to maintain the credibility of decentralized decision-making. The algorithm’s flexibility extends to autonomous systems: Jun Liu et al. [67] implemented a DPoS-based multi-robot coordination protocol, proving its practicality in delay-sensitive industrial automation scenarios. Industrial IoT (IIoT) applications have driven significant innovations in DPoS. Yue Wang et al. [68] developed a privacy-preserving data-sharing framework for smart factories, combining DPoS with zero-knowledge proofs to protect IIoT sensor networks. Furthermore, Ehtisham Ul Haque et al. [69] proposed a lightweight DPoS derivative for scalable IoT data management, optimizing consensus overhead in resource-constrained edge environments. These advancements collectively address the dual requirements of security and efficiency in industrial digitization. Siyi Liao et al. [70] combined DPoS with digital twin architectures to achieve real-time consensus in blockchain-enhanced smart city traffic networks. Meanwhile, Pengfei Wang et al. [71] re-imagined the federated learning market through a social IoT framework governed by DPoS, incentivizing data contributions while maintaining model integrity—an important advancement in distributed machine learning ecosystems.
The surveyed literature highlights the evolution of DPoS from a blockchain consensus mechanism to a cross-domain coordination tool. Reference [67] demonstrates its adaptability to industry demands, while [68] emphasizes its potential as a driver of large-scale, interoperable decentralized systems. Ongoing challenges include balancing decentralization with regulatory compliance in public sector applications [66] and optimizing energy efficiency in resource-intensive deployments [69]. Emerging research avenues include quantum-resistant DPoS variants and hybrid consensus models that integrate machine learning for adaptive validator selection. These developments may solidify DPoS’s role in next-generation infrastructures, from smart cities to Industry 4.0 ecosystems.
As shown in Table 7, existing improvements to the DPoS algorithm can be systematically categorized into three main directions: security enhancement, vertical scenario adaptation, and efficiency and resource optimization. Security-enhancing methods strengthen resistance to Sybil attacks and data leakage protection by incorporating dynamic validator election, anomaly detection mechanisms, and privacy-preserving computation technologies (such as zero-knowledge proofs), ensuring the trustworthiness of consensus participants and the confidentiality of data. Research on vertical scenario adaptation customizes consensus rules and interaction protocols to meet the differentiated needs of fields such as transportation, industrial IoT, and federated learning. Examples include privacy-preserving carpool transaction verification, multi-robot collaborative scheduling, and real-time synchronization in digital twins, highlighting DPoS’s flexible scalability in cross-domain applications. The efficiency optimization direction focuses on lightweight designs (such as edge device resource management) and real-time performance improvements (such as consensus acceleration in latency-sensitive scenarios). However, this optimization strategy inevitably increases centralization risks, undermining decentralization.

Table 7.
A comparison of DPoS consensus optimization.
3.3.2. Kafka
Kafka, originally developed by LinkedIn, is a distributed, partitioned, and multi-replicated messaging system coordinated by ZooKeeper. Its most prominent feature is the ability to process large amounts of data in real-time to meet various use case scenarios. Fundamentally, Kafka provides transaction sequencing services alongside fault tolerance capabilities. For each chain, Kafka assigns a partition and a single partition topic. Ordering nodes can read from the partition to obtain a consistent transaction ordering list across all ordering nodes. When the transaction threshold is reached, batching occurs, generating new blocks. In the event of node failure, alternative ordering nodes can take over to distribute the blocks. All ordering nodes maintain local block logs, ensuring the integrity and security of transaction data.
The Hyperledger Fabric open-source platform [73] adopts the Kafka consensus algorithm, benefiting greatly from Kafka’s high performance. Multiple ordering nodes synchronize through Kafka, though Kafka itself is not an ordering node; it merely connects the ordering nodes through streams. Although Kafka provides fault tolerance, it lacks safeguards against malicious network attacks. To address these threats, a Byzantine Fault Tolerance (BFT) scheme is necessary. Nonetheless, this solution has not yet been integrated into the Hyperledger Fabric framework. The role of consensus mechanisms in distributed systems has been widely explored, with Apache Kafka emerging as a key technology for scalable data flows and fault-tolerant architectures. Performance evaluations by Paul Le Noac’h et al. [74] conducted a rigorous benchmarking of Apache Kafka’s latency and throughput in big data streaming environments, identifying optimizations for real-time processing.
Beyond traditional use cases, Nuttapong Klaokliang et al. [75] pioneered Kafka within the blockchain ecosystem, proposing a Hyperledger Fabric IoT authorization architecture enhanced by genetic algorithms. This highlights Kafka’s adaptability to heterogeneous frameworks that require robust consensus mechanisms. Furthermore, a comparative analysis further elucidates Kafka’s technical trade-offs. Bhole Rahul Hiraman et al. [76] evaluated Kafka’s performance in stream processing pipelines, confirming its dominance in high-capacity data environments. Additionally, MANUELA PETRESCU et al. [77] compared Kafka’s log replication mechanism with the Raft consensus protocol, emphasizing the differing approaches to fault tolerance and leader election. Finally, Gyeongsik Yang et al. [78] conducted a detailed resource analysis of Kafka, Raft, and PBFT within Hyperledger Fabric, concluding that the choice of consensus algorithm significantly impacts blockchain performance metrics, such as latency and computational overhead.
As shown in Table 8, existing research on improvements to Kafka can be systematically categorized into two main directions: cross-domain technology integration and performance quantification evaluation. The performance quantification evaluation direction provides empirical evidence for algorithm selection in industrial scenarios through the benchmark testing of latency/throughput, fault tolerance mechanism comparison (e.g., differences in log replication between Kafka and Raft), and resource overhead modeling. These improvements demonstrate that Kafka is evolving from a traditional messaging queue system to a cross-platform data coordination hub, supporting high-concurrency, low-latency distributed data stream demands through architecture simplification, protocol extension, and multi-technology collaboration. Future research may need to explore intelligent scheduling (e.g., AI-driven dynamic load balancing) and novel security mechanisms (e.g., quantum-safe log encryption) to address the complexity of large-scale data ecosystems and emerging attack threats.

Table 8.
A comparison of Kafka consensus improvements.
3.3.3. PBFT
The PBFT (Practical Byzantine Fault Tolerance) consensus algorithm is based on Byzantine fault tolerance [79] and is designed to address the problem of Byzantine failures in distributed systems. It reaches consensus through communication and collaboration between nodes to ensure that the system remains secure and consistent even in the presence of faulty nodes. The core idea of the algorithm is to eliminate the influence of faulty or malicious nodes by implementing mutual verification and consensus among multiple nodes, thus ensuring the normal operation of the entire system. Nodes verify messages received from the master node and other nodes, using mechanisms such as signatures and message digests to assess the consistency and legitimacy of the messages. A node moves to the next stage and broadcasts its message to other nodes only when it receives a sufficient number of valid messages (2f + 1 valid messages, where f denotes the number of Byzantine nodes). Through the process of collaboration and validation between nodes, PBFT can reach consensus, thus ensuring that the system remains secure and consistent even in the face of Byzantine failures [80].
Current traceability systems mainly rely on centralized databases managed by enterprises or third-party organizations [81]; however, this model has many challenges, such as a high risk of data tampering, lack of transparency, and expensive trust costs. In addition, due to limited data sharing between various links in the supply chain, a complete traceability chain is difficult to establish, which in turn affects the confidence of consumers and regulators. Blockchain technology, with its decentralized architecture, data immutability and traceability features, provides an ideal solution to such problems. The introduction of smart contracts allows transactions to be executed automatically, ensuring the authenticity and tamperability of data on the chain, while reducing reliance on intermediaries and increasing transparency. In addition, multi-node consensus mechanisms, such as PBFT, strengthen data consistency and enhance the security and reliability of the system. Figure 7 illustrates a traceability system based on PBFT. The system comprises four key nodes—producer, transporter, seller, and consumer—that interact via blockchain to store and verify transaction data, enhancing transparency and traceability [82].
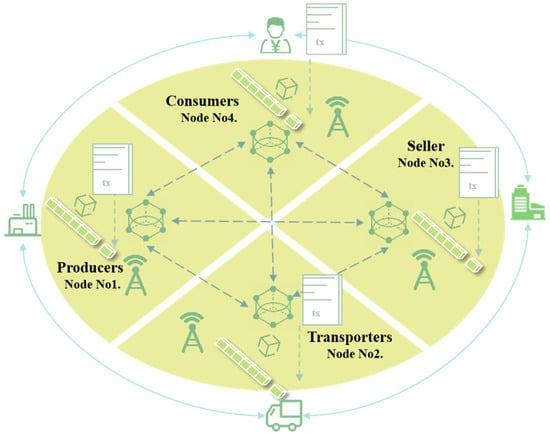
Figure 7.
The architecture of a blockchain-based traceability system with a PBFT consensus algorithm.
- (1)
- PBFT consensus protocol
The PBFT consensus protocol is the core of the consensus algorithm [83], which is responsible for coordinating all nodes in the network to agree on the order of transaction requests. The consensus process is divided into five phases: request, pre-prepare, prepare, commit and reply, each of which plays a key role in guaranteeing the integrity and reliability of the consensus. Figure 8 visually illustrates the execution of the PBFT consensus protocol.
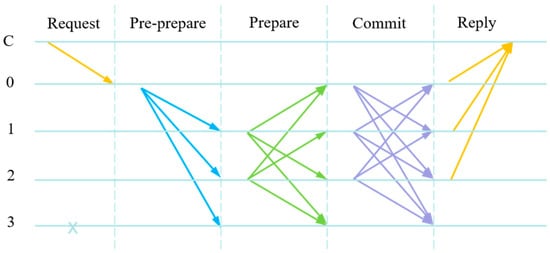
Figure 8.
The PBFT consensus protocol.
The overall protocol execution process is as follows:
- (1)
- Request phase: the client sends a request to the master node to start the consensus process. The master node is responsible for coordinating the subsequent steps.
- (2)
- Pre-prepare phase: The master node broadcasts a pre-prepare message containing the request digest and a unique sequence number. Upon receiving the message, replica nodes verify its authenticity and log it locally, ensuring data consistency across the network.
- (3)
- Prepare phase: The replica node sends prepare messages to acknowledge the receipt of the pre-prepare message, including the request summary, sequence number, and formal acknowledgment. The next step is triggered when the node has accumulated a sufficient number of prepare messages.
- (4)
- Commit phase: The replica node sends a commit message to inform other nodes that the request has been validated and approved. This message includes the request summary, sequence number, and acknowledgment to reinforce consensus. Once the node receives a sufficient number of commit messages, it can execute the request.
- (5)
- Reply phase: the replica node sends a reply message to the client with the execution result. The client confirms a successful execution upon receiving enough reply messages.
This phased process enables PBFT to securely and efficiently process transactions while resisting Byzantine faults, enhancing system stability and reliability [84].
- (2)
- View change protocol
In the context of blockchain consensus mechanisms [85], such as Practical Byzantine Fault Tolerance (PBFT), the view change protocol serves as an essential fault-tolerance strategy [86]. This mechanism is particularly useful in circumstances where the current leader node becomes unresponsive or fails to act within expected parameters. When the participating nodes detect that the leader does not achieve consensus within a set timeframe, a view change is initiated to facilitate the election of a new leader. This proactive measure not only ensures the smooth continuity of system operations but also significantly enhances the overall fault tolerance of the network. As illustrated in Figure 9, the view change process in PBFT consists of two main phases: the normal consensus phase and the view change phase [87].
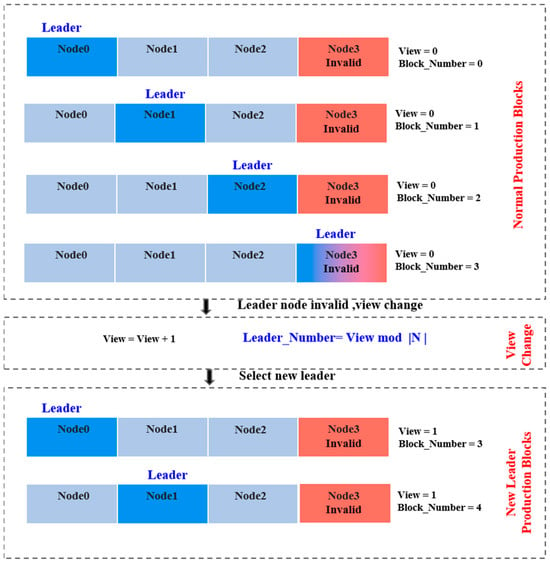
Figure 9.
A flowchart of the view switching process.
- (1)
- Normal Consensus Phase
Initially, Node0 acts as the leader, coordinating the consensus process, while other nodes (Node1, Node2, and Node3) participate in validation and voting. If the leader (Node0) fails to reach consensus effectively, the nodes mark it as invalid, triggering the transition to the view change phase.
- (2)
- View Change Phase
The system initiates the view change mechanism, wherein all nodes collaborate to elect a new leader. In the diagram, Node1 is selected as the new leader, taking over the responsibility of coordinating the consensus process [88].
The newly elected leader synchronizes the network, restoring consensus operations and ensuring blockchain stability. The view change mechanism enhances protocol robustness, keeping the network operational despite node failures or adversarial behavior.
Although the Practical Byzantine Fault Tolerance (PBFT) algorithm allows the system to function normally even in the presence of faulty or malicious nodes [89], it has attracted significant attention. However, several issues have been exposed in the practical application of the PBFT algorithm. These deficiencies primarily include the following aspects:
- The leader selection mechanism in the PBFT algorithm is relatively arbitrary, which can result in unstable leader performance or an increased risk of attacks from malicious nodes, thereby leading to frequent view changes that impact the system’s overall performance.
- The PBFT consensus algorithm utilizes a three-phase communication model. While it ensures the security of consensus, the communication overhead significantly increases in large-scale networks, which reduces the overall efficiency of the system.
- The PBFT consensus algorithm lacks an effective reward and punishment mechanism, which hinders the ability to incentivize honest nodes to participate in the consensus process. Additionally, it lacks effective means to penalize malicious nodes, thus limiting the system’s robustness when defending against attacks.
- The PBFT algorithm requires a fixed number of consensus nodes during the consensus process, meaning that nodes cannot be dynamically added or removed within the consensus network.
To address the shortcomings of the PBFT consensus algorithm, researchers both domestically and internationally have explored the limitations of traditional PBFT, primarily focusing on the following four aspects: hierarchical group consensus methods, the introduction of incentive and penalty mechanisms to reduce the number of consensus nodes, improvements to consensus through multiple leader nodes, and the optimization of the consensus algorithm based on optimistic mechanisms. Table 9 provides a summary of PBFT consensus optimization strategies.

Table 9.
A summary of PBFT consensus algorithm optimization strategies.
4. Analysis of the Improved PBFT Consensus Algorithm
With the growing popularity of blockchain research, consensus algorithms, as a key technology for implementing blockchain, have garnered widespread attention from researchers. As the number of nodes increases, the transaction throughput of traditional PBFT significantly decreases, while communication overhead and transaction delays increase substantially. To address these issues, researchers both domestically and internationally have explored the limitations of traditional PBFT, focusing primarily on four aspects: hierarchical group consensus methods, the introduction of reward and punishment mechanisms to reduce the number of consensus nodes, improvements to multi-leader consensus algorithms, and improvements to consistency protocols based on optimistic node assumptions [90].
4.1. The Hierarchical Group Consensus Algorithm
The PBFT consensus protocol distinguishes between two distinct types of nodes: primary nodes and replica nodes. Each node type is designed to fulfill specific functions that enhance the overall efficiency and effectiveness of the consensus network. Primary nodes are responsible for leading the consensus process, while replica nodes play a critical role in validating transactions and maintaining the integrity of the network. The coordinated interaction between these two types of nodes is essential for achieving a reliable consensus in distributed systems. However, as the number of nodes within the network increases, a significant challenge emerges, as communication overhead and consensus latency is associated with the traditional PBFT consensus algorithm. With more nodes participating in the consensus process, the volume of messages that must be exchanged escalates, which can lead to an increased latency in reaching an agreement. This scalability issue poses significant hurdles for the efficient performance of the PBFT protocol, particularly in larger networks where the demands for rapid consensus and low communication costs become paramount. To address this challenge, researchers have proposed dividing the consensus process into groups and modifying the consensus protocol to operate as an intra-group consensus followed by inter-group confirmation. In this approach, a specific grouping algorithm is first employed to partition the nodes into groups, where nodes within each group achieve synchronous consensus. Afterward, the primary nodes of each group mutually confirm whether consensus has been reached. The hierarchical grouping consensus process is illustrated in Figure 10. This method effectively reduces the communication overhead required for consensus confirmation during the prepare and commit phases, thereby increasing transaction throughput and reducing consensus latency.
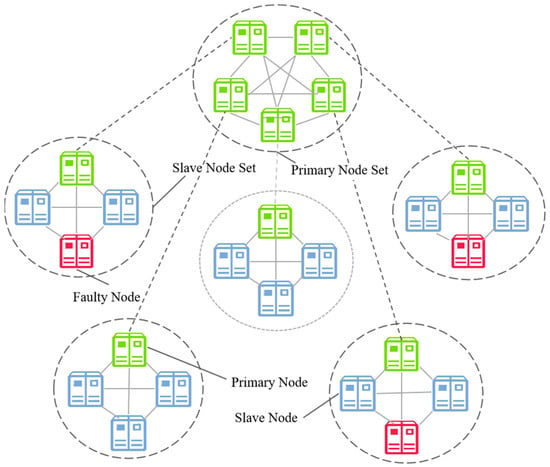
Figure 10.
The hierarchical consensus network topology.
Liu C et al. [91] addressed the issues of high latency, large system overhead, and limited scalability in the application of blockchain technology for drug traceability. They proposed a Practical Byzantine Fault Tolerance algorithm based on grouping and credit voting (P-PBFT). This algorithm first designs a grouping strategy based on the response speed between drug supply chain nodes, dividing the consensus node set and conducting group consensus. Additionally, the algorithm’s credit model and voting mechanism dynamically update the nodes’ credibility based on their behavior during consensus, assessing the nodes’ reliability, and electing a leader node based on credibility. This algorithm not only improves throughput but also significantly reduces consensus latency. Wang Y et al. [92] suggested a consensus algorithm based on feature-based trust groups, referred to as GPBFT. Initially, this algorithm assesses the trust levels of nodes involved in the transaction process employing the EigenTrust model, which serves as the foundation for selecting both leader and replica nodes. Additionally, it categorizes the nodes within the blockchain system into several groups, achieving consensus within individual groups while designating the leader node externally. This approach minimizes communication overhead when dealing with a substantial number of nodes within the system. Liu S et al. [93] proposed a consensus algorithm known as credit-based Byzantine Fault Tolerance (CBFT). This algorithm categorizes network nodes into various consensus groups—management nodes, candidate nodes, and regular nodes—determined by their response times to the management nodes. Consensus is established within and among these groups to minimize communication overhead while improving system security. Furthermore, CBFT incorporates a reputation evaluation framework that sorts nodes into different categories according to the reputation model. During each consensus round, the reputation scores of nodes are updated based on their responsiveness, past reliability, and the precision of transaction consensus. Nodes that exhibit a higher credibility are chosen as leaders to decrease the chances of malicious leaders emerging.
Zhang R et al. [94] introduced an enhanced reputation-based Practical Byzantine Fault Tolerance consensus algorithm (RPBFT) that integrates node grouping and reputation-driven voting. Initially, the RPBFT algorithm optimizes the consistency process by leveraging the response speed of nodes within each group as a criterion for grouping, which is succeeded by achieving consensus within the group. The leader node within each group obtains the consensus result and participates in confirming consensus outside the group, reducing both communication overhead and latency between nodes. Furthermore, the RPBFT algorithm introduces a reputation model and voting mechanism, where the leader node of each group is elected based on reputation-driven voting, thereby enhancing the credibility and reliability of trusted nodes and preventing leader node failure.
Widya Nita Suliyanti et al. [95] have put forward the Dual-Layer Byzantine Fault Tolerance (DLBFT) mechanism, which aims to significantly boost the scalability of blockchain technology while simultaneously enhancing the efficiency of information exchange within Building Information Modeling (BIM). This innovative study presents a dual-layer network architecture that is designed to optimize communication and data flow. In this architecture, each node in the first layer is interconnected with multiple nodes in the second layer, creating a well-defined and structured grouping of nodes. The framework utilizes the Byzantine Fault Tolerance (BFT) algorithm, which plays a crucial role in facilitating consensus among nodes. This algorithm is pivotal in ensuring that information is exchanged securely and efficiently across the network. By implementing DLBFT, the researchers aim to address the challenges related to scalability in blockchain systems while maintaining the integrity and reliability of data exchange in BIM contexts. Zhong et al. [96] proposed ST-PBFT, a partitioning method based on consistent hashing, designed to reduce communication complexity in IP transaction scenarios. Furthermore, Shen et al. [86] introduced GV-PBFT, a PBFT consensus optimization algorithm based on group reputation values, aimed at enhancing system efficiency.
Jian Liu et al. [97] introduced the Grouped Multilayer PBFT (GM-PBFT) consensus algorithm, specifically optimized for digital asset trading scenarios, aiming to mitigate communication complexity and enhance consensus efficiency. Overall, these studies highlight continuous advancements in PBFT consensus mechanisms, leveraging techniques such as node grouping, reputation-based selection, and algorithmic optimizations to improve scalability, communication efficiency, and fault tolerance in blockchain systems.
As shown in Table 10, this section provides an explanation of the grouping methods used for the algorithms introduced. These grouped consensus algorithms, while ensuring consensus efficiency, have also made significant improvements in fault tolerance in some cases. The primary reason for this improvement is that, by grouping nodes within the network, these algorithms allow each group to tolerate up to f Byzantine nodes (where N = 3f + 1), while also tolerating f Byzantine nodes outside the group. Therefore, from an overall perspective, these algorithms can tolerate nearly half of the Byzantine nodes within the network. The optimization algorithms, however, exhibit challenges such as complex inter-group coordination and the risk of load imbalance. They are suitable for scenarios with concentrated node geographic locations and stable network topologies (e.g., supply chain traceability systems), but perform poorly in highly dynamic wireless networks, such as vehicular networks (VANETs).

Table 10.
A comparison of grouping methods for each algorithm.
4.2. Select High-Quality Nodes for Participation in Consensus
With the expansion of blockchain nodes, large-scale network situations experience a rapid increase in node count, which results in a notable decline in the effectiveness of the PBFT consensus. In various research efforts focused on enhancing PBFT consensus algorithms, numerous researchers have proposed implementing reward and penalty systems to identify honest or high-performing nodes for participation in the consensus, while other nodes serve as candidates and do not engage in the process. This strategy effectively reduces the number of participating nodes (e.g., selecting half or a third of the total nodes), and communication overhead between nodes can be reduced, thereby improving the throughput of consensus transactions. The process of selecting high-quality nodes for consensus participation is illustrated in Figure 11.
Figure 11.
A diagram of selecting high-quality nodes for consensus participation.
Liu W et al. [98] proposed a QoS-aware trust service trust evaluation mechanism to achieve service reliability ranking. By integrating both static and dynamic QoS metrics to compute a global evaluation value, they select more reliable and secure nodes to participate in consensus, reducing the number of participating nodes and, in turn, lowering communication costs while enhancing consensus efficiency. Xu G et al. [99] introduced a secure and efficient PBFT consensus algorithm for vehicular networks based on a distributed blockchain structure. This algorithm incorporates a reputation model, selecting the top half of nodes by reputation to participate in consensus. After each round of consensus, node reputations are updated, which helps reduce the number of nodes and lower communication costs, improving system throughput. Gao S et al. [100] proposed an innovative, optimized Practical Byzantine Fault Tolerance consensus algorithm (T-PBFT) based on the EigenTrust model. This multi-stage consensus algorithm evaluates the trustworthiness of nodes through transactions interactions, selecting high-quality nodes to form the consensus group. Only members of the consensus group can participate in the network consensus, significantly enhancing consensus efficiency.
Liu et al. [101] proposed 5G-PBFT, which introduces a reputation model based on node performance and behavior. This model dynamically selects consensus nodes based on their reputation scores to ensure the reliability of node selection. Subsequently, the algorithm leverages the reputation model along with a verifiable random function (VRF) to elect the primary node, considering both its reliability and the randomness of the selection process. Finally, by utilizing the low-latency characteristics of 5G networks, the commit phase is omitted, effectively reducing communication complexity. K. Riahi et al. [102] introduced APBFT, an adaptive version of the PBFT protocol that enhances the efficiency of the consensus process by adjusting the number of nodes involved based on their response times and reliability. This method minimizes communication overhead and decreases response latency, all the while preserving the algorithm’s asynchronous characteristics, thereby increasing its resilience to Denial-of-Service (DoS) attacks. Xiaowei Wang and his team Ref. [103] proposed XG-PBFT, an improved PBFT algorithm based on XGBoost-based grouping. XG-PBFT constructs a dataset by training on key parameters that influence node performance, which serves as a classification index for nodes. The XGBoost algorithm is then used to train the dataset, and new nodes joining the system are grouped accordingly based on the trained model. Nodes with higher parameter scores are assigned to the consensus group to participate in consensus, while the remaining nodes are placed in a general group to assist in consensus verification. To minimize system resource consumption, XG-PBFT optimizes the PBFT consensus protocol by addressing its high communication complexity.
Table 11 provides a comparative overview of the mechanisms for rewards and penalties utilized by various consensus algorithms. This table offers an in-depth summary of these mechanisms and elucidates their impact on the number of nodes engaged in the consensus process. Here, N signifies the overall number of nodes within the network, whereas d indicates the threshold for nodes that participate in consensus for the T-PBFT algorithm. In scenarios involving large-scale networks, the implementation of these algorithms can greatly diminish the number of nodes engaged in the consensus process. Consequently, this results in a notable decrease in both communication overhead and latency, while enhancing transaction throughput. Nevertheless, a significant challenge lies in the fact that these algorithms may introduce centralization risks and increase the overhead of dynamic assessments. They are suitable for scenarios where node behavior is relatively stable and reputation evaluation data is complete (e.g., enterprise-level consortium blockchains). However, they are vulnerable to reputation falsification attacks in open and dynamic environments, such as public IoT networks.

Table 11.
A comparison of reward and penalty mechanisms across different algorithms.
4.3. Improvements to Multi-Leader Consensus Algorithms
In the conventional PBFT consensus algorithm, the primary node is chosen by applying the modulus operation of the view number against the overall count of nodes. Nevertheless, should the primary node experience a failure, it can lead to a frequent switching of views, which may adversely affect the efficiency of consensus. To address this issue, researchers worldwide have proposed various multi-primary-node consensus algorithm improvements.
Z. Zeng et al. [104] proposed an approach that introduces an optimized Practical Byzantine Fault Tolerance (PBFT) consensus algorithm that leverages the concepts of Vague sets and credit ratings to effectively tackle existing challenges within the consensus mechanism. By incorporating Vague sets, this algorithm significantly improves the efficiency of the voting process that is essential for achieving consensus among nodes. It achieves this enhancement by carefully balancing the influences of both positive and negative votes, thereby offering a more nuanced and rational framework for evaluating the behavior of individual nodes. This advanced evaluation criterion not only facilitates more informed decision-making within the network but also contributes to the overall reliability and robustness of the consensus protocol. This serves as the basis for primary node selection. Additionally, the algorithm quantifies node attributes and optimizes the selection of consensus nodes to improve the overall consensus efficiency. Aublin P. L. et al. [105] proposed a Byzantine fault-tolerant architecture that employs multiple primary replicas in parallel, enhancing system robustness through redundancy. Their protocol follows an N ≥ 3f + 1 node configuration to tolerate up to f Byzantine node failures. The core mechanism establishes a collaborative oversight system between a Primary Instance (responsible for request ordering and execution authorization) and Backup Instances (which validate ordering correctness and monitor the primary node). When an anomaly is detected in the primary node, a dynamic view-switching mechanism is employed to rapidly replace the faulty instance. Alqahtani S. et al. [106] introduced a multi-leader mechanism to overcome the communication bottleneck in single-leader Byzantine Fault Tolerant (BFT) protocols. Their approach optimizes the communication complexity to O(N), ensuring stability even when proposal voting and coordination phases overlap. The BigBFT protocol achieves block ordering in two rounds of communication while leveraging pipelining techniques to transmit blocks from the same or different rounds, ultimately reaching consensus efficiently. Avarikioti Z. et al. [107] proposed a parallel-leading Byzantine Fault Tolerant state machine replication protocol designed for partially synchronous models with theoretical performance guarantees. Their FnF-BFT algorithm enables all replicas to act as leaders and propose requests independently, allowing for parallel request execution. By distributing the workload across the entire network, leader parallelization mitigates the bottleneck of a single leader, significantly enhancing system throughput. Table 12 provides a comparative analysis of multi-leader selection mechanisms across different algorithms.

Table 12.
A comparison of multi-leader selection mechanisms across different algorithms.
Having multiple leaders helps lower the complexity of the consensus process while also improving system throughput. These advantages become particularly evident in large-scale networks. However, employing multiple leaders also presents several challenges, including the complexity of leader synchronization and view switching, as well as increased resource consumption. This approach is only suitable for high-throughput, low-latency closed networks (e.g., cloud computing centers). In resource-constrained or high packet loss wireless networks (e.g., 6G edge computing), its performance may deteriorate significantly.
4.4. An Optimized Consensus Algorithm Based on an Optimistic Mechanism
In the standard PBFT consensus algorithm, the consensus is achieved during the prepare phase. At this point, Byzantine malicious nodes can be detected, and the system can tolerate up to f Byzantine nodes while still reaching consensus. In other words, as long as the primary node is honest and the number of Byzantine nodes does not surpass f + 1, consensus consistency is ensured during the pre-prepare and prepare phases.
However, when the primary node itself is Byzantine, two common types of errors may occur when applying the PBFT algorithm in a traceability system:
- (1)
- Advantageous Byzantine Error: The primary node may alter a correct message received from the client to one that is beneficial to itself before broadcasting it to the network. For example, it may modify message m into m’.
- (2)
- Consistency Byzantine Error: The primary node might send different messages (m and m’) with the same sequence number (n) to different nodes, or assign the same sequence number to different client request messages (m and m’). This inconsistency can cause problems during view changes, where nodes present conflicting information, undermining the security of the consensus. In the traditional two-phase PBFT protocol, security issues in the network arise only when the primary node encounters a consistency error. A specific example of such an issue is as follows:
When the primary node receives client message requests, m and m’, it may attempt to assign them the same sequence number n. As a result, in the pre-prepare messages forwarded to other nodes, some may contain <m, v, n>, while others may contain <m’, v, n>. Additionally, the primary node might simultaneously send both <m, v, n> and <m’, v, n> to other malicious nodes.
Assume there are seven nodes (nodes 0, 1, 2, 3, 4, 5, and 6), with the number of Byzantine nodes being f = 2, and the primary node (node 0) and node 6 being malicious. The following will discuss the scenarios encountered during the two-phase consensus submission. Suppose the primary node (node 0) is malicious. After receiving two request messages, m and m’, from the client (C), it sends a malicious message <m, v, n> with sequence number n to nodes 1, 2, and 3 (f + 1 honest nodes) during the pre-prepare phase, and sends a malicious message <m’, v, n> with the sequence number n to nodes 4 and 5 (f honest nodes). Both messages <m, v, n> and <m’, v, n> are also sent to node 6 (a Byzantine node). In the prepare phase, each node forwards a prepare message to others after receiving the pre-prepare message from the primary node. Node 6 may randomly choose to forward either <m, v, n> or <m’, v, n>. Suppose node 6 only forwards the correct prepare message containing <m, v, n> to node 2 (fewer than f + 1 honest nodes), and sends the incorrect prepare message containing <m’, v, n> to other nodes. In this case, node 2 will receive the prepare messages {m, m, m, m, m’, m’, m}. At this point, node 2 collects 2f + 1 = 5 identical prepare messages and submits message <m, v, n>. However, the other nodes will receive either {m, m, m, m, m’, m’, m’} or {m’, m, m, m, m’, m’, m’}. Since they fail to receive 2f + 1 = 5 identical prepare messages, they will not submit the message, and these nodes will issue a view-change request. The newly selected primary node will collect 2f + 1 view-change requests to determine the submission status of message <m, v, n>. At this point, there will be view-change requests from nodes 1, 3, 4, 5, and 6, and none of them will have submitted <m, v, n>. The new primary node will assume that <m, v, n> has not been submitted by any node. However, node 2 has already submitted <m, v, n>, and the new primary node will initiate a new consensus message <m, v + 1, n> or renumber message m as k <m, v + 1, k>. This results in a conflict between the already-submitted message <m, v, n> from node 2 and the newly initiated consensus message. As a result, the system’s consistency and security are weakened. The specific consensus process where the primary node causes consistency errors and undermines system security in the two-phase consensus is shown in Figure 12 below. (In the figure below, x represents a node encountering a Byzantine problem, and the arrows indicate communication messages being sent between nodes).
Figure 12.
A case diagram of a PBFT algorithm primary node consistency error.
In the traditional three-phase confirmation of PBFT, the commit phase is used to ensure that incomplete requests, such as request m, can still be executed even after a primary node switch. Specifically, if replica i in view v executed request m with number n, replica j in view v + 1 can also execute request m with the same number n, thereby avoiding inconsistent primary nodes from sending two different transaction messages under the same sequence number.
To address the aforementioned primary node consistency errors, scholars both domestically and internationally have proposed modifications based on specific application scenarios or the introduction of incentive mechanisms to maintain the primary node’s reliability. These modifications include reducing the PBFT consensus protocol from three phases to two phases, or simplifying the PBFT commit phase, to minimize consensus communication overhead and enhance efficiency.
Haytham Qushtom et al. [108] introduced a consensus mechanism that combines Proof of Stake (PoS) with Practical Byzantine Fault Tolerance (PBFT). This approach effectively reduces the influence of harmful nodes, encompassing both solitary validators and leaders, while ensuring optimal performance. The model encourages integrity by integrating trust scores and reward systems as essential elements in the processes of block validation and ordering. Laphou Lao et al. [109] introduced G-PBFT (Geographic-PBFT), which leverages the geographic information of fixed IoT devices to achieve consensus, thereby mitigating Sybil attacks. In G-PBFT, fixed, trustworthy, and capable nodes are selected as endorsers, reducing the computational overhead associated with transaction validation and record-keeping. Bo Gan et al. [110], considering the characteristics of Cognitive IoT (CIoT), proposed EIoT-PBFT, a multi-stage consensus algorithm based on PBFT. EIoT-PBFT consists of three phases: grouping, scoring, and consensus achievement.
As shown in Table 13, These studies are based on edge devices or reliable reward-and-punishment mechanisms, assuming that the primary node will never encounter consistency errors. Simplifying consensus consistency can reduce the communication overhead and latency. However, these optimization studies carry the risk of primary node failure and exhibit strong scenario dependence. These studies are only applicable to specific scenarios, and their theoretical framework remains optimistic, assuming that the primary node will not fail. Nevertheless, in open, dynamic, or multi-tenant environments, the risks are significantly higher. In practical applications, challenges still exist.

Table 13.
The applicability of various algorithms.
5. Discussion and Future Directions
PBFT as a foundational Byzantine Fault Tolerance (BFT) algorithm, demonstrates high performance in small-scale node environments [111]. However, its linear message complexity leads to significant performance degradation when the system scales to a larger number of nodes. Specifically, the algorithm faces three key technical bottlenecks: (1) the storage volume of messages increases quadratically with the scale of nodes; (2) network latency sensitivity causes a sharp rise in delay under asynchronous conditions; and (3) inherent flaws such as the absence of a node evaluation mechanism and insufficient system openness. Current research indicates that introducing novel validation mechanisms or optimizing communication protocols to improve PBFT’s architecture can effectively enhance its overall performance. This provides researchers with a continuous path for optimization. The findings of this survey are summarized below, along with potential future directions for research.
5.1. The Hierarchical Clustering Mechanism
The topological divide-and-conquer strategy is employed to partition consensus nodes into logical subgroups, thereby reducing local communication complexity and improving overall efficiency [112]. This approach has been supported by multiple empirical studies; however, its technical implementation must address two core issues: (1) The design of node selection algorithms in dynamic environments must balance load balancing and security thresholds, where an optimal number of groups can enhance consensus efficiency. (2) Improper clustering could lead to additional resource consumption.
To address the aforementioned challenges, future approaches could introduce adaptive dynamic grouping algorithms and reputation-based grouping mechanisms for consensus node topology. This would effectively optimize load balance and improve consensus efficiency, while also preventing resource waste caused by improper grouping. Additionally, adopting a hierarchical hybrid consensus model, which executes lightweight consensus algorithms within subgroups and employs more fault-tolerant mechanisms at the inter-group level, can reduce the overall communication complexity and enhance the scalability of consortium blockchains.
5.2. Multi-Leadership Structure
The multi-leader model enhances system throughput through parallel processing, but it introduces the challenge of leader synchronization. Additionally, the presence of multiple leaders increases the risk of multiple nodes being attacked and becoming ineffective.
To address the synchronization and security challenges of multi-leader consensus models, a decentralized scheduling-based leader synchronization mechanism can be introduced in the future. By leveraging Byzantine fault-tolerant clock synchronization or distributed lock techniques, multiple leaders can efficiently coordinate their actions. Additionally, integrating a dynamic primary node election mechanism that adjusts the number of leaders based on network load and reputation assessment can help reduce synchronization overhead and mitigate security risks. Furthermore, the introduction of a multi-layered primary node architecture can optimize task distribution, enhance system throughput, and alleviate single-point overloads, thereby further strengthening the robustness of consortium blockchains.
5.3. The Optimistic Consensus Algorithm
The optimistic consensus algorithm enhances the consistency of consensus protocols; nevertheless, its practicality is constrained. It can effectively reach consensus solely when implemented on particular edge device nodes. Moreover, incorporating a reputation system to validate the main node seems rather hopeful. Even with reputation-driven reward and punishment systems in place, the main node continues to encounter threats from malicious actions or potential failures.
In the optimization of optimistic consensus algorithms, enhancing the reputation evaluation mechanism is crucial. In the future, adopting a time-weighted reputation model can more accurately assess the long-term behavior of nodes and prevent reputation fraud. Additionally, integrating secret sharing mechanisms or multi-signature techniques can ensure system continuity and security, even in the event of primary node failures.
Looking ahead, blockchain is expected to play an increasingly vital role in smart manufacturing. With the advancement of AI, 5G communication, and digital twin technology, blockchain can serve as a trusted data infrastructure, facilitating cross-enterprise and cross-regional collaboration in intelligent production. Moreover, its decentralized data management capabilities can support the development of distributed smart manufacturing platforms, enabling seamless data sharing and optimized resource allocation among different manufacturing enterprises. In the future, blockchain is poised to drive mechanical manufacturing toward a higher degree of automation, intelligence, and traceability, providing strong support for the digital transformation of the global manufacturing industry.
6. Conclusions
This paper comprehensively reviews the evolution and optimization strategies of the PBFT consensus algorithm in coalition chains, and provides an in-depth analysis of the core challenges such as communication complexity, master node selection mechanism, and incentive structure. To address these issues, the researchers propose a series of improvements, including hierarchical group consensus, reputation-based node selection, multi-master node architecture, and a hybrid consensus model incorporating economic incentives. Among these strategies, hierarchical consensus mechanisms and high-quality node selection are the most commonly adopted approaches, as they effectively reduce the number of participating nodes and optimize message transmission paths, thereby lowering communication complexity. Additionally, the multi-leader consensus model alleviates the computational burden on a single master node, enhancing system throughput, while the introduction of incentive mechanisms improves node honesty and strengthens system resilience against malicious attacks. These optimizations provide a more efficient and secure consensus framework for consortium blockchain applications, though they also introduce challenges such as increased centralization tendencies and the complexity of incentive models. Future research could further explore the application of machine learning in dynamic node selection, enhance cross-chain interoperability, and optimize the communication overhead to facilitate the widespread application of the PBFT consensus algorithm in large-scale blockchain systems.
Funding
This paper was supported by Innovative Research Group of Chongqing Municipal Education Commission (CXQT19026), and Cooperative Project between Chinese Academy of Sciences and University in Chongqing (HZ2021011). Moreover, this work was supported by the Research Startup Fund of Chongqing University of Technology (0119240197).
Data Availability Statement
No new data were created or analyzed in this study. Data sharing is not applicable to this article.
Conflicts of Interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
References
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar]
- Iansiti, M.; Lakhani, K.R. The truth about blockchain. Harv. Bus. Rev. 2017, 95, 118–127. [Google Scholar]
- Ye, S.; Sun, Y.; Zhang, J.; Chen, J.; Xu, B.; Zhao, S.; Liu, H. A new coupled dynamic model to study the vibration and lubrication characteristics of slipper/swash-plate interface in an axial piston pump. Proc. Inst. Mech. Eng. Part J J. Eng. Tribol. 2025, 13506501241308942. [Google Scholar]
- Ye, S.; Lin, Q.; Zheng, C.; Zhao, S.; Liu, H. Dynamic modeling and vibration response analysis of an internal gear pump. Proc. Inst. Mech. Eng. Part C J. Mech. Eng. Sci. 2024, 09544062241303386. [Google Scholar]
- Fernández-Caramés, T.M.; Fraga-Lamas, P. A Review on the Use of Blockchain for the Internet of Things. IEEE Access 2018, 6, 32979–33001. [Google Scholar]
- Neetu, S.; Rajesh, R. Scalable and Cost-Efficient PoA Consensus-Based Blockchain Solution for Vaccination Record Management. Wirel. Pers. Commun. Int. J. 2024, 135, 1177–1207. [Google Scholar]
- Young-Eisendrath, P.; Dawson, T. The Cambridge Companion to Kafka. J. Hist. Behav. Sci. 2008.
- Xu, G.; Liu, Y.; Khan, P.W. Improvement of the DPoS consensus mechanism in blockchain based on vague sets. IEEE Trans. Ind. Inform. 2019, 16, 4252–4259. [Google Scholar] [CrossRef]
- Underwood, S. Blockchain beyond Bitcoin. Commun. ACM 2016, 59, 15–17. [Google Scholar] [CrossRef]
- Zhang, C.; Chen, J.; Li, J.; Peng, Y.; Mao, Z. Large language models for human–robot interaction: A review. Biomim. Intell. Robot. 2023, 3, 100131. [Google Scholar] [CrossRef]
- Peng, Y.; Sakai, Y.; Funabora, Y.; Yokoe, K.; Aoyama, T.; Doki, S. Funabot-Sleeve: A Wearable Device Employing McKibben Artificial Muscles for Haptic Sensation in the Forearm. IEEE Robot. Autom. Lett. 2025, 10, 1944–1951. [Google Scholar] [CrossRef]
- Li, H.; Lu, R.; Zhou, L.; Yang, B.; Shen, X. An Efficient Merkle-Tree-Based Authentication Scheme for Smart Grid. IEEE Syst. J. 2014, 8, 655–663. [Google Scholar]
- Ferdous, M.S.; Chowdhury MJ, M.; Hoque, M.A. A survey of consensus algorithms in public blockchain systems for crypto-currencies. J. Netw. Comput. Appl. 2021, 182, 103035. [Google Scholar]
- Yang, R.; Wakefield, R.; Lyu, S.; Jayasuriya, S.; Han, F.; Yi, X.; Yang, X.; Amarasinghe, G.; Chen, S. Public and private blockchain in construction business process and information integration. Autom. Constr. 2020, 118, 103276. [Google Scholar]
- Dib, O.; Brousmiche, K.L.; Durand, A.; Thea, E.; Hamida, E.B. Consortium blockchains: Overview, applications and challenges. Int. J. Adv. Telecommun. 2018, 11, 51–64. [Google Scholar]
- Mao, Z.; Kobayashi, R.; Nabae, H.; Suzumori, K. Multimodal strain sensing system for shape recognition of tensegrity structures by combining traditional regression and deep learning approaches. IEEE Robot. Autom. Lett. 2024, 9, 10050–10056. [Google Scholar]
- Bai, X.; Peng, Y.; Li, D.; Liu, Z.; Mao, Z. Novel soft robotic finger model driven by electrohydrodynamic (EHD) pump. J. Zhejiang Univ.-Sci. A 2024, 25, 596–604. [Google Scholar] [CrossRef]
- Mao, Z.; Bai, X.; Peng, Y.; Shen, Y. Design, modeling, and characteristics of ring-shaped robot actuated by functional fluid. J. Intell. Mater. Syst. Struct. 2024, 35, 1459–1470. [Google Scholar]
- Zhonghua, C.; Goyal, S.B.; Rajawat, A.S. Smart contracts attribute-based access control model for security & privacy of IoT system using blockchain and edge computing. J. Supercomput. 2024, 80, 1396–1425. [Google Scholar]
- Peng, Y.; Yang, X.; Li, D.; Ma, Z.; Liu, Z.; Bai, X.; Mao, Z. Predicting flow status of a flexible rectifier using cognitive computing. Expert Syst. Appl. 2025, 264, 125878. [Google Scholar]
- Lasla, N.; Alsahan, L.; Abdallah, M.; Younis, M. Green-PoW: An Energy-Efficient Blockchain Proof-of-Work Consensus Algorithm. Comput. Netw. 2020, 214, 109118. [Google Scholar]
- Lan, Y.; Liu, Y.; Li, B. Proof of Learning (PoLe): Empowering Machine Learning with Consensus Building on Blockchains. Proc. AAAI Conf. Artif. Intell. 2020, 35, 16063–16066. [Google Scholar]
- Chen, J.; Gan, W.; Hu, M.; Chen, C.-M. On the Construction of a Post-Quantum Blockchain for Smart City. J. Inf. Secur. Appl. 2020, 58, 102780. [Google Scholar]
- Kara, M.; Laouid, A.; AlShaikh, M.; Hammoudeh, M.; Bounceur, A.; Euler, R.; Amamra, A.; Laouid, B. A Compute and Wait in PoW (CW-PoW) Consensus Algorithm for Preserving Energy Consumption. Appl. Sci. 2021, 15, 6750. [Google Scholar]
- Dhurandher, S.K.; Singh, J.; Nicopolitidis, P.; Kumar, R.; Gupta, G. A Blockchain-based Secure Routing Protocol for Opportunistic Networks. J. Ambient. Intell. Humaniz. Comput. 2021, 13, 2191–2203. [Google Scholar]
- Xu, R.; Chen, Y. Fed-DDM: A Federated Ledgers Based Framework for Hierarchical Decentralized Data Marketplaces. In Proceedings of the 2021 International Conference on Computer Communications and Networks (ICCCN), Athens, Greece, 19–22 July 2021. [Google Scholar]
- Gunanidhi, G.S.; Krishnaveni, R. Improved Security Blockchain for IoT Based Healthcare Monitoring System. In Proceedings of the Second International Conference on Artificial Intelligence and Smart Energy (ICAIS), Coimbatore, India, 23–25 February 2022. [Google Scholar]
- Saini, V.; Purohit, C.S.; Kumar, R.; Al-Sumaiti, A. Proof of Work Consensus Based Peer to Peer Energy Trading in the Indian Residential Community. Energies 2023, 16, 1253. [Google Scholar] [CrossRef]
- Tang, Y.; Yan, J.; Chakraborty, C.; Sun, Y. Hedera: A Permissionless and Scalable Hybrid Blockchain Consensus Algorithm in Multiaccess Edge Computing for IoT. IEEE Internet Things J. 2023, 10, 21187–21202. [Google Scholar]
- Islam, M.R.; Rashid, M.; Rahman, M.A.; Mohamad, M.; Embong, A.H. A Comprehensive Analysis of Blockchain-based Cryptocurrency Mining Impact on Energy Consumption. Int. J. Adv. Comput. Sci. Appl. 2022, 13, 590–598. [Google Scholar]
- Motepalli, S.; Jacobsen, H.-A. Reward Mechanism for Blockchains Using Evolutionary Game Theory. In Proceedings of the 2021 3rd Conference on Blockchain Research & Applications for Innovative Networks and Services (BRAINS), Paris, France, 27–30 September 2021. [Google Scholar]
- Xu, C.; Qu, Y.; Luan, T.; Eklund, P.W.; Xiang, Y.; Gao, L. A Lightweight and Attack-Proof Bidirectional Blockchain Paradigm for Internet of Things. IEEE Internet Things J. 2022, 9, 4371–4384. [Google Scholar]
- Bhudia, A.; Cartwright, A.; Cartwright, E.; Hurley-Smith, D.; Hernandez-Castro, J. Game Theoretic Modelling of A Ransom and Extortion Attack on Ethereum Validators. In Proceedings of the 18th International Conference on Availability, Reliability and Security, Benevento, Italy, 29 August–1 September 2023. [Google Scholar]
- Rashid, M.; Rasool, I.; Zafar, N.; Afzaal, H. Formal Modeling and Verification of Validator Voluntarily Exit in Ethereum 2.0 Beacon Chain. In Proceedings of the 2023 2nd International Conference On Emerging Trends in Electrical, Control, and Telecommunication Engineering (ETECTE), Lahore, Pakistan, 27–29 November 2023. [Google Scholar]
- Grandjean, D.; Heimbach, L. Roger Wattenhofer; Ethereum Proof-of-Stake Consensus Layer: Participation and Decentralization. In Proceedings of the International Conference on Financial Cryptography and Data Securit, Willemstad, Curaçao, 4–8 March 2023. [Google Scholar]
- Asif, R.; Hassan, S.R. Shaping the Future of Ethereum: Exploring Energy Consumption in Proof-of-Work and Proof-of-Stake Consensus. Front. Blockchain 2023, 6, 1151724. [Google Scholar]
- Ge, L.; Wang, J.; Zhang, G. Survey of Consensus Algorithms for Proof of Stake in Blockchain. Secur. Commun. Netw. 2022, 2022, 2812526. [Google Scholar] [CrossRef]
- Li, L. Mitigating Challenges in Ethereum’s Proof-of-Stake Consensus: Evaluating The Impact of EigenLayer and Lido. arXiv 2024, arXiv:2410.23422. [Google Scholar]
- Neu, J.; Tas, E.N.; Tse, D.C. Two More Attacks on Proof-of-Stake GHOST/Ethereum. In Proceedings of the 2022 ACM Workshop On Developments in Consensus, Los Angeles, CA, USA, 7 November 2022. [Google Scholar]
- Lin, Z.; Zhang, Q.; Tian, Z.; Yu, P.; Ye, Z.; Zhuang, H.; Lan, J. Slam2: Simultaneous localization and multimode mapping for indoor dynamic environments. Pattern Recognit. 2025, 158, 111054. [Google Scholar] [CrossRef]
- Howard, H.; Mortier, R. Paxos vs Raft: Have We Reached Consensus On Distributed Consensus? In Proceedings of the 7th Workshop on Principles and Practice of Consistency for Distributed Data, Heraklion, Greece, 27 April 2020. [Google Scholar]
- Haridi, S.; Kroll, L.; Carbone, P. Lecture Notes On Leader-based Sequence Paxos—An Understandable Sequence Consensus Algorithm. arXiv 2020, arXiv:2008.13456. [Google Scholar]
- Sheff, I.; Wang, X.; van Renesse, R.; Myers, A.C. Heterogeneous Paxos: Technical Report. arXiv 2020, arXiv:2011.08253. [Google Scholar]
- Goel, A.; Sakallah, K. Towards An Automatic Proof of Lamport’s Paxos. In Proceedings of the 2021 Formal Methods in Computer Aided Design (FMCAD), Vienna, Austria, 2–6 October 2021. [Google Scholar]
- Xing, W.; Wu, T.; Wang, X. Automated alarm method for abnormal data in power grid reports based on Paxos algorithm. In Proceedings of the Third International Conference on Computer Technology, Information Engineering, and Electron Materials (CTIEEM 2023), Zhengzhou, China, 17–19 November 2023. [Google Scholar]
- Howard, H.; Mortier, R. Relaxed Paxos: Quorum Intersection Revisited (Again). In Proceedings of the 9th Workshop on Principles and Practice of Consistency for Distributed Data, New York, NY, USA, 5–8 April 2022. [Google Scholar]
- Tennage, P.; Basescu, C.; Kogias, E.K.; Syta, E.; Jovanovic, P.; Ford, B. Baxos: Backing Off for Robust and Efficient Consensus. arXiv 2022, arXiv:2204.10934. [Google Scholar]
- Desjardins, A.; Kogias, E.K. Mandator and Sporades: Robust Wide-Area Consensus with Efficient Request Dissemination. arXiv 2022, arXiv:2209.06152. [Google Scholar]
- Hidayat, S.A.; Juniardi, W.; Khatami, A.; Sari, R.F. Performance Comparison and Analysis of Paxos, Raft and PBFT Using NS3. In Proceedings of the 2022 IEEE International Conference on Internet of Things and Intelligence Systems (IoTaIS), Bali, Indonesia, 24–26 November 2022. [Google Scholar]
- Gabbay, M.J.; Zanolini, L. A Declarative Approach to Specifying Distributed Algorithms Using Three-valued Modal Logic. arXiv 2025, arXiv:2502.00892. [Google Scholar]
- Sakic, E.; Kellerer, W. Response Time and Availability Study of RAFT Consensus in Distributed SDN Control Plane. IEEE Trans. Netw. Serv. Manag. 2017, 15, 304–318. [Google Scholar] [CrossRef]
- Wang, Y.; Li, S.; Xu, L.; Xu, L. Improved Raft Consensus Algorithm in High Real-Time and Highly Adversarial Environment. In Web Information Systems and Applications, Proceedings of the 18th International Conference, WISA 2021, Kaifeng, China, 24–26 September 2021, Proceedings 18; Springer International Publishing: Cham, Switzerland, 2021. [Google Scholar]
- Fu, W.; Wei, X.; Tong, S. An Improved Blockchain Consensus Algorithm Based on Raft. Arab. J. Sci. Eng. 2021, 46, 8137–8149. [Google Scholar] [CrossRef]
- Surjandari, I.; Yusuf, H.; Laoh, E.; Maulida, R. Designing A Permissioned Blockchain Network for The Halal Industry Using Hyperledger Fabric with Multiple Channels and The Raft Consensus Mechanism. J. Big Data 2021, 8, 1–16. [Google Scholar] [CrossRef]
- Xu, X.; Hou, L.; Li, Y.; Geng, Y. Weighted RAFT: An Improved Blockchain Consensus Mechanism for Internet of Things Application. In Proceedings of the 2021 7th International Conference on Computer and Communications (ICCC), Chengdu, China, 10–13 December 2021. [Google Scholar]
- Du, N.; Yan, D.; Liang, Z.; Huang, Y.; Liu, T.; Zhong, C. Research on Optimization of Efficient and Scalable Mutli-Raft Consensus Algorithm for Supply Chain Finance. In Proceedings of the 2022 IEEE International Conference on Sensing, Diagnostics, Prognostics, and Control (SDPC), Chongqing, China, 5–7 August 2022. [Google Scholar]
- Hou, L.; Xu, X.; Zheng, K.; Wang, X. An Intelligent Transaction Migration Scheme for RAFT-based Private Blockchain in Internet of Things Applications. IEEE Commun. Lett. 2021, 25, 2753–2757. [Google Scholar]
- Luo, H.; Yang, X.; Yu, H.; Sun, G.; Lei, B.; Guizani, M. Performance Analysis and Comparison of Nonideal Wireless PBFT and RAFT Consensus Networks in 6G Communications. IEEE Internet Things J. 2023, 11, 9752–9765. [Google Scholar]
- Li, Y.; Fan, Y.; Zhang, L.; Crowcroft, J. RAFT Consensus Reliability in Wireless Networks: Probabilistic Analysis. IEEE Internet Things J. 2023, 10, 12839–12853. [Google Scholar]
- Battisti, J.H.F.; Batista, V.E.; Koslovski, G.P.; Pillon, M.A.; Miers, C.; Marques, M.A.; Simplício, M.A.; Kreutz, D. Performance Analysis of The Raft Consensus Algorithm on Hyperledger Fabric and Ethereum on Cloud. In Proceedings of the 2023 IEEE International Conference on Cloud Computing Technology and Science (CloudCom), Naples, Italy, 4–6 December 2023. [Google Scholar]
- Alexandridis, A.; Al-Sumaidaee, G.; Alkhudary, R.; Zilic, Z. Making Case for Using RAFT in Healthcare Through Hyperledger Fabric. In Proceedings of the 2021 IEEE International Conference On Big Data (Big Data), Orlando, FL, USA, 15–18 December 2021. [Google Scholar]
- Mišić, J.; Mišić, V.B.; Chang, X. Toward Decentralization in DPoS Systems: Election, Voting, and Leader Selection Using Virtual Stake. IEEE Trans. Netw. Serv. Manag. 2024, 21, 1777–1790. [Google Scholar]
- Hu, Q.; Yan, B.; Han, Y.; Yu, J. An Improved Delegated Proof of Stake Consensus Algorithm. Procedia Comput. Sci. 2021, 187, 341–346. [Google Scholar]
- Wei, Y.; Liang, L.; Zhou, B.; Feng, X. A Modified Blockchain DPoS Consensus Algorithm Based on Anomaly Detection and Reward-Punishment. In Proceedings of the 2021 13th International Conference on Communication Software and Networks (ICCSN), Chongqing, China, 4–7 June 2021. [Google Scholar]
- Chen, Y.; Liu, F. Improvement of DPoS Consensus Mechanism in Collaborative Governance of Network Public Opinion. In Proceedings of the 2021 4th International Conference on Advanced Electronic Materials, Computers and Software Engineering (AEMCSE), Changsha, China, 26–28 March 2021. [Google Scholar]
- Wang, D.; Zhang, X. Secure Ride-Sharing Services Based on A Consortium Blockchain. IEEE Internet Things J. 2021, 8, 2976–2991. [Google Scholar]
- Liu, J.; Xie, M.; Chen, S.; Ma, C.; Gong, Q. An Improved DPoS Consensus Mechanism in Blockchain Based on PLTS for The Smart Autonomous Multi-robot System. Inf. Sci. 2021, 575, 528–541. [Google Scholar]
- Wang, Y.; Che, T.; Zhao, X.; Zhou, T.; Zhang, K.; Hu, X. A Blockchain-Based Privacy Information Security Sharing Scheme in Industrial Internet of Things. Sensors 2022, 22, 3426. [Google Scholar] [CrossRef]
- Haque, E.U.; Shah, A.; Iqbal, J.; Ullah, S.S.; Alroobaea, R.; Hussain, S. A Scalable Blockchain Based Framework for Efficient IoT Data Management Using Lightweight Consensus. Sci. Rep. 2024, 14, 7841. [Google Scholar]
- Liao, S.; Wu, J.; Bashir, A.; Yang, W.; Li, J.; Tariq, U. Digital Twin Consensus for Blockchain-Enabled Intelligent Transportation Systems in Smart Cities. IEEE Trans. Intell. Transp. Syst. 2022, 23, 22619–22629. [Google Scholar] [CrossRef]
- Wang, P.; Zhao, Y.; Obaidat, M.; Wei, Z.; Qi, H.; Lin, C.; Xiao, Y.; Zhang, Q. Blockchain-Enhanced Federated Learning Market with Social Internet of Things. IEEE J. Sel. Areas Commun. 2022, 40, 3405–3421. [Google Scholar] [CrossRef]
- Liu, Y.; Xu, G. Fixed Degree of Decentralization DPoS Consensus Mechanism in Blockchain Based on Adjacency Vote and the Average Fuzziness of Vague Value. Comput. Netw. 2021, 199, 108432. [Google Scholar] [CrossRef]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. arXiv 2018, arXiv:1801.10228. [Google Scholar]
- Le Noac’h, P.; Costan, A.; Bougé, L. A Performance Evaluation of Apache Kafka in Support of Big Data Streaming Applications. In Proceedings of the 2017 IEEE International Conference on Big Data (Big Data), Boston, MA, USA, 11–14 December 2017. [Google Scholar]
- Klaokliang, N.; Teawtim, P.; Aimtongkham, P.; So-In, C.; Niruntasukrat, A. A Novel IoT Authorization Architecture on Hyperledger Fabric With Optimal Consensus Using Genetic Algorithm. In Proceedings of the 2018 Seventh ICT International Student Project Conference (ICT-ISPC), Nakhon Pathom, Thailand, 11–13 July 2018. [Google Scholar]
- Hiraman, B.R.; Viresh, M.C.; Abhijeet, C.K. A Study of Apache Kafka in Big Data Stream Processing. In Proceedings of the 2018 International Conference on Information, Communication, Engineering and Technology (ICICET), Pune, India, 29–31 August 2018. [Google Scholar]
- Petrescu, M.; Petrescu, R. Log Replication in Raft Vs Kafka. Stud. Univ. Babeș-Bolyai Inform. 2020, 65, 10–24193. [Google Scholar] [CrossRef]
- Yang, G.; Lee, K.; Lee, K.; Yoo, Y.; Lee, H.; Yoo, C. Resource Analysis of Blockchain Consensus Algorithms in Hyperledger Fabric. IEEE Access 2022, 10, 74902–74920. [Google Scholar] [CrossRef]
- Castro, M.; Liskov, B. Practical byzantine fault tolerance. OsDI 1999, 99, 173–186. [Google Scholar]
- Wu, X.; Wang, Z.; Li, X.; Chen, L. DBPBFT: A hierarchical PBFT consensus algorithm with dual blockchain for IoT. Future Gener. Comput. Syst. 2025, 162, 107429. [Google Scholar] [CrossRef]
- Wang, Y.; Xing, X.; Li, P.; Chen, L. LT-DBFT: A Hierarchical Blockchain Consensus Using Location and Trust in IoT. IEEE Internet Things J. 2025. [Google Scholar] [CrossRef]
- Abbessi, W.; Ouni, S.; Othmen, R.B.; Wang, G. Random cluster parallel PBFT global consensus for consistent blockchain distributed ledger. Clust. Comput. 2025, 28, 187. [Google Scholar] [CrossRef]
- Jia, G.; Shen, Z.; Sun, H.; Xin, J.; Wang, D. RWA-BFT: Reputation-Weighted Asynchronous BFT for Large-Scale IoT. Sensors 2025, 25, 413. [Google Scholar] [CrossRef] [PubMed]
- Zhang, H.; Zhao, Y. SatBFT: An Efficient and Scalable Consensus Protocol for Blockchain-Enabled Space-Air-Ground Integrated Network. IEEE Trans. Cogn. Commun. Netw. 2025. [Google Scholar] [CrossRef]
- Zheng, J.; Zhang, Y. TRBFT: An Efficient Blockchain Consensus for Edge Computing-Enabled IoT Systems. IEEE Internet Things J. 2025. [Google Scholar]
- Chen, W.; Li, X.; Wang, G.; Li, L.; Shen, J.; Li, E. HML-BFT: Hybrid multi-layer BFT consensus with reputation model for large-scale blockchain. Peer-to-Peer Netw. Appl. 2025, 18, 1–14. [Google Scholar]
- Ding, K.; Gerhard, D.; Fan, L. AML-Based Multi-Dimensional Co-Evolution Approach Supported by Blockchain: Architecture Design and Case Study on Intelligent Production Lines for Industry 4.0. Information 2025, 16, 243. [Google Scholar] [CrossRef]
- Elomda, B.M.; Abdelbary, T.A.A.; Hassan, H.A.; Hamza, K.S.; Kharma, Q. An Enhanced Multi-Layer Blockchain Security Model for Improved Latency and Scalability. Information 2025, 16, 241. [Google Scholar] [CrossRef]
- Alabdulatif, A. Blockchain-Based Privacy-Preserving Authentication and Access Control Model for E-Health Users. Information 2025, 16, 219. [Google Scholar] [CrossRef]
- Liu, S.; Wang, X.; Hui, L.; Wu, W. Blockchain-Based Decentralized Federated Learning Method in Edge Computing Environment. Appl. Sci. 2023, 13, 1677. [Google Scholar] [CrossRef]
- Liu, S.; Zhang, R.; Liu, C.; Shi, D. P-PBFT: An improved blockchain algorithm to support large-scale pharmaceutical traceability. Comput. Biol. Med. 2023, 154, 106590. [Google Scholar]
- Wang, Y.; Zhong, M.; Cheng, T. Research on PBFT consensus algorithm for grouping based on feature trust. Sci. Rep. 2022, 12, 12515. [Google Scholar] [CrossRef]
- Liu, S.; Zhang, R.; Liu, C.; Xu, C.; Wang, J. An improved PBFT consensus algorithm based on grouping and credit grading. Sci. Rep. 2023, 13, 13030. [Google Scholar]
- Liu, S.; Zhang, R.; Liu, C.; Xu, C.; Zhou, J.; Wang, J. Improvement of the PBFT algorithm based on grouping and reputation value voting. Int. J. Digit. Crime Forensics (IJDCF) 2022, 14, 1–15. [Google Scholar]
- Suliyanti, W.N.; Sari, R.F. Blockchain-Based Double-Layer Byzantine Fault Tolerance for Scalability Enhancement for Building Information Modeling Information Exchange. Big Data Cogn. Comput. 2023, 7, 90. [Google Scholar] [CrossRef]
- Zhong, W.; Feng, W.; Huang, M.; Feng, S. ST-PBFT: An Optimized PBFT Consensus Algorithm for Intellectual Property Transaction Scenarios. Electronics 2023, 12, 325. [Google Scholar] [CrossRef]
- Liu, J.; Feng, W.; Huang, M.; Feng, S.; Zhang, Y. Grouped Multilayer Practical Byzantine Fault Tolerance Algorithm: A Practical Byzantine Fault Tolerance Consensus Algorithm Optimized for Digital Asset Trading Scenarios. Sensors 2023, 23, 8903. [Google Scholar] [CrossRef]
- Liu, W.; Zhang, X.; Feng, W.; Huang, M.; Xu, Y. Optimization of PBFT algorithm based on QoS-aware trust service evaluation. Sensors 2022, 22, 4590. [Google Scholar] [CrossRef]
- Xu, G.; Bai, H.; Xing, J.; Luo, T.; Xiong, N.N.; Cheng, X.; Liu, S.; Zheng, X. SG-PBFT: A secure and highly efficient distributed blockchain PBFT consensus algorithm for intelligent Internet of vehicles. J. Parallel Distrib. Comput. 2022, 164, 1–11. [Google Scholar]
- Gao, S.; Yu, T.; Zhu, J.; Cai, W. T-PBFT: An EigenTrust-based practical Byzantine fault tolerance consensus algorithm. China Commun. 2019, 16, 111–123. [Google Scholar]
- Liu, X.; Fan, X.; Niu, B.; Zheng, X. 5G-Practical Byzantine Fault Tolerance: An Improved PBFT Consensus Algorithm for the 5G Network. Information 2025, 16, 202. [Google Scholar] [CrossRef]
- Riahi, K.; Abouaissa, A.; Idoumghar, L. APBFT: An Adaptive PBFT Consensus for Private Blockchains. In Proceedings of the GLOBECOM 2022—2022 IEEE Global Communications Conference, Rio de Janeiro, Brazil, 4–8 December 2022; pp. 1788–1793. [Google Scholar]
- Wang, X.; Zhang, H.; Zhang, J.; Ge, Y.; Cui, K.; Peng, Z.; Li, Z.; Wang, L. An Improved Practical Byzantine Fault-Tolerant Algorithm Based on XGBoost Grouping for Consortium Chains. Comput. Mater. Contin. 2025, 82, 1295–1311. [Google Scholar]
- Zeng, Z.; Wen, B.; Du, W.; Zhang, F.; Zhou, W. PBFT Consensus Algorithm Optimization Scheme Based on Vague Sets and Credit Rating. In Proceedings of the 2023 6th International Conference on Software Engineering and Computer Science (CSECS), Chengdu, China, 22–24 December 2023; pp. 1–5. [Google Scholar]
- Aublin, P.L.; Mokhtar, S.B.; Quema, V. RBFT: Redundant Byzantine Fault Tolerance. In Proceedings of the 2013 IEEE 33rd International Conference on Distributed Computing Systems, Philadelphia, PA, USA, 8–11 July 2013. [Google Scholar]
- Alqahtani, S.; Demirbas, M. BigBFT: A Multileader Byzantine Fault Tolerance Protocol for High Throughput. In Proceedings of the 2021 IEEE International Performance, Computing, and Communications Conference (IPCCC), Austin, TX, USA, 29–31 October 2021. [Google Scholar]
- Avarikioti, Z.; Heimbach, L.; Schmid, R.; Vanbever, L.; Wattenhofer, R.; Wintermeyer, P. FnF-BFT: Exploring Performance Limits of BFT Protocols. arXiv 2020, arXiv:2009.02235. [Google Scholar]
- Qushtom, H.; Mišić, J.; Mišić, V.B.; Chang, X. A Two-Stage PBFT Architecture With Trust and Reward Incentive Mechanism. IEEE Internet Things J. 2023, 10, 11440–11452. [Google Scholar]
- Lao, L.; Dai, X.; Xiao, B.; Guo, S. G-PBFT: A Location-based and Scalable Consensus Protocol for IoT-Blockchain Applications. In Proceedings of the 2020 IEEE International Parallel and Distributed Processing Symposium (IPDPS), New Orleans, LA, USA, 18–22 May 2020; pp. 664–673. [Google Scholar]
- Gan, B.; Wang, Y.; Wu, Q.; Zhou, Y.; Jiang, L. EIoT-PBFT: A multi-stage consensus algorithm for IoT edge computing based on PBFT. Microprocess. Microsyst. 2022, 95, 104713. [Google Scholar]
- Tian, Z.; Zhao, D.; Lin, Z.; Zhao, W.; Flynn, D.; Jiang, Y.; Tian, D.; Zhang, Y.; Sun, Y. Efficient and balanced exploration-driven decision making for autonomous racing using local information. IEEE Trans. Intell. Veh. 2024, 1–17. [Google Scholar] [CrossRef]
- Mao, Z.; Hosoya, N.; Maeda, S. Flexible electrohydrodynamic fluid-driven valveless water pump via immiscible interface. Cyborg Bionic Syst. 2024, 5, 0091. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).