blockHealthSecure: Integrating Blockchain and Cybersecurity in Post-Pandemic Healthcare Systems
Abstract
1. Introduction
2. Background Study
2.1. Blockchain Technology in Healthcare
2.2. Cybersecurity Challenges in Healthcare
3. Methodology
3.1. Structure of the Proposed Blockchain System
3.2. Consensus Mechanism
- High security: Only verified and trusted healthcare providers participate in the validation process.
- Low latency: Faster transaction validation compared to Proof of Work (PoW).
- Energy efficiency: Requires significantly less computational power, making it scalable for healthcare operations.
3.3. Detail Explanation of the Proposed Method
3.3.1. How Blockchain Enhances Healthcare Security
Data Immutability and Integrity
Cryptographic Verification
3.3.2. How Smart Contracts Automate Access Control, Auditing, and Compliance Enforcement
Automated Access Control
Smart Contracts for Auditing
Compliance Enforcement
3.3.3. How AI-Driven IDS Systems Detect and Mitigate Cyber Threats in Real-Time
Threat Detection with Machine Learning
Automated Threat Mitigation
- Revoking blockchain access tokens for compromised accounts.
- Blocking malicious IP addresses attempting unauthorized blockchain transactions.
- Alerting cybersecurity teams for manual intervention.
3.3.4. Integration of Zero Trust Architecture (ZTA) for Access Control
- Least-privilege access: Users and devices only receive access to the minimum necessary data to perform their tasks. Even healthcare providers cannot access full medical records unless explicitly authorized.
- Continuous authentication and verification: Every request to access patient data is re-evaluated in real time, ensuring dynamic access control. AI-powered risk scoring assesses whether to allow, deny, or restrict access based on user behavior and device security.
- Micro-segmentation: Network segmentation isolates critical patient records and blocks lateral movement in case of a breach. If one segment is compromised, the attack cannot spread to other parts of the system.
- Multi-factor authentication (MFA): Advanced MFA mechanisms, including biometric authentication and cryptographic tokens, ensure that only authorized personnel gain access. Blockchain-based authentication further eliminates the risk of credential theft.
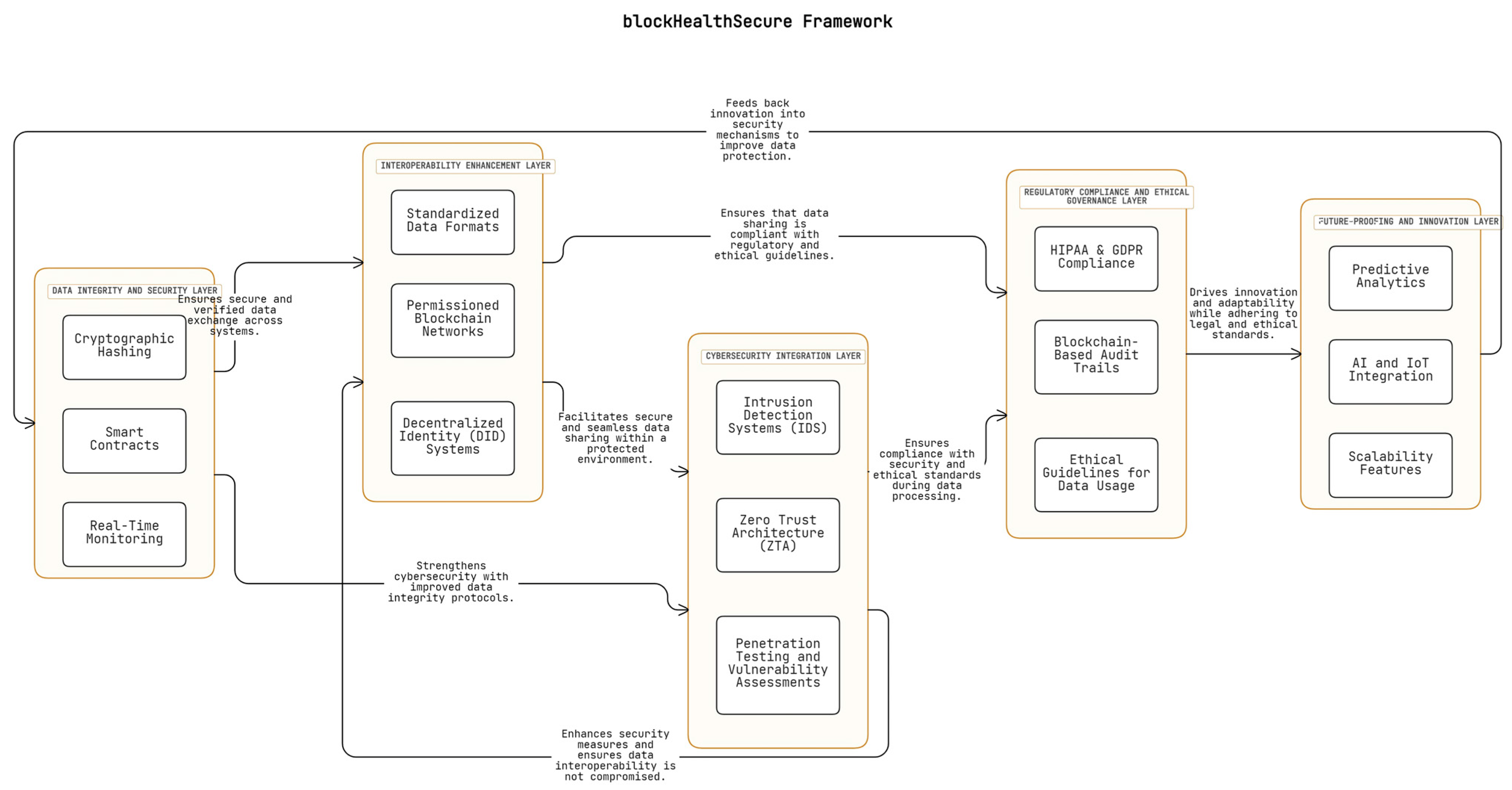
4. blockHealthSecure Framework
4.1. Introduction to the blockHealthSecure Framework
4.2. Components of the blockHealthSecure Framework
4.2.1. Data Integrity and Security Layer
- Cryptographic hashing: Hashing algorithms are used to verify data integrity by converting sensitive information into a fixed size of characters, ensuring that any alteration in the data can be detected.
- Smart contracts: Smart contracts are self-executing agreements where the terms are embedded directly in the code. They automate data access and exchange, ensuring transactions are secure and resistant to tampering.
- Real-time monitoring: This component enables continuous monitoring of healthcare systems to identify unauthorized access or potential security breaches, delivering real-time alerts and ensuring a swift response.
4.2.2. Interoperability Enhancement Layer
- Standardized data formats: Standardized data formats like HL7 and FHIR (Fast Healthcare Interoperability Resources) enable the seamless transfer of medical information between different systems.
- Permissioned blockchain networks: These are blockchain networks in which participants are verified, ensuring that only authorized entities can access and share data, thereby promoting trust within healthcare networks.
- Decentralized Identity (DID) systems: DID systems empower patients and healthcare providers to manage their identities securely, ensuring privacy while allowing for effective data sharing.
4.2.3. Cybersecurity Integration Layer
- Intrusion Detection Systems (IDS): IDS track network traffic for any suspicious activity and potential threats, offering early alerts for unauthorized access attempts.
- Zero Trust Architecture (ZTA): ZTA ensures that no device or user is automatically trusted, necessitating ongoing authentication and validation to reduce vulnerabilities.
- Penetration testing and vulnerability assessments: These proactive measures identify and assess system vulnerabilities, allowing for timely patching and hardening of the healthcare infrastructure.
4.2.4. Regulatory Compliance and Ethical Governance Layer
- HIPAA/GDPR compliance: Healthcare systems must adhere to stringent data protection laws, such as HIPAA in the U.S. and the GDPR in Europe, to ensure patient data privacy and security.
- Blockchain-based audit trails: Blockchain offers an unchangeable and transparent record of data transactions, ensuring accountability and providing a clear trace of all interactions with healthcare data.
- Ethical guidelines for data usage: Ethical guidelines govern the appropriate use of patient data, ensuring that patient rights and privacy are respected throughout the data lifecycle.
4.2.5. Future-Proofing and Innovation Layer
- Predictive analysis: Predictive models can forecast health trends and patient needs, enabling healthcare providers to respond proactively to potential public health emergencies.
- AI and IoT integration: Combining AI with the IoT enhances patient monitoring, enables personalized healthcare services, and supports better decision-making.
- Scalability features: The framework is built to scale as healthcare data volume grows, ensuring it can manage large datasets while preserving performance and security.
4.3. Connectivity and Feedback Loops
4.4. Roles of Different Participants in the blockHealthSecure Framework
- Patients retain full control over their personal health records (PHR) via blockchain-based access control.
- Healthcare providers must request data access, which is authorized via smart contracts and validated through blockchain authentication mechanisms.
- Regulatory bodies can audit blockchain logs but cannot modify patient records, ensuring transparency and compliance.
4.5. Operation and Control Mechanisms of Smart Contracts
- Deployment: Smart contracts are initiated by healthcare providers and reviewed by regulatory bodies before activation.
- Modification control: Any updates require multi-signature approval from at least two regulatory bodies, preventing unauthorized tampering.
- Auditing mechanisms: Regular blockchain audits and automated alerts detect anomalies and security breaches.
- The patient authorizes access through the Decentralized Identity (DID) system.
- A smart contract logs the request and encrypts the patient’s approval on the blockchain.
- The healthcare provider submits a request to retrieve the medical record.
- The smart contract verifies authorization and grants time-limited access.
- The provider accesses the record securely, and the blockchain logs the transaction, ensuring immutability and auditability.
- If the provider attempts unauthorized access, the Intrusion Detection System (IDS) triggers an alert, revoking access.
5. Blockchain and Cybersecurity Integration in Post-Pandemic Healthcare Systems
5.1. The Role of Blockchain in Healthcare
5.2. Cybersecurity Measures in Post-Pandemic Healthcare Systems
5.2.1. Strengthening Perimeter Security
5.2.2. Implementing Zero Trust Architecture (ZTA)
5.2.3. Adopting Endpoint Security Solutions
5.2.4. Enhancing Data Encryption
5.2.5. Leveraging AI for Threat Detection
5.2.6. Compliance with Regulatory Standards
5.2.7. Improving Incident Response Mechanisms
5.2.8. Fostering Cybersecurity Awareness
5.2.9. Resilience Through Redundancy
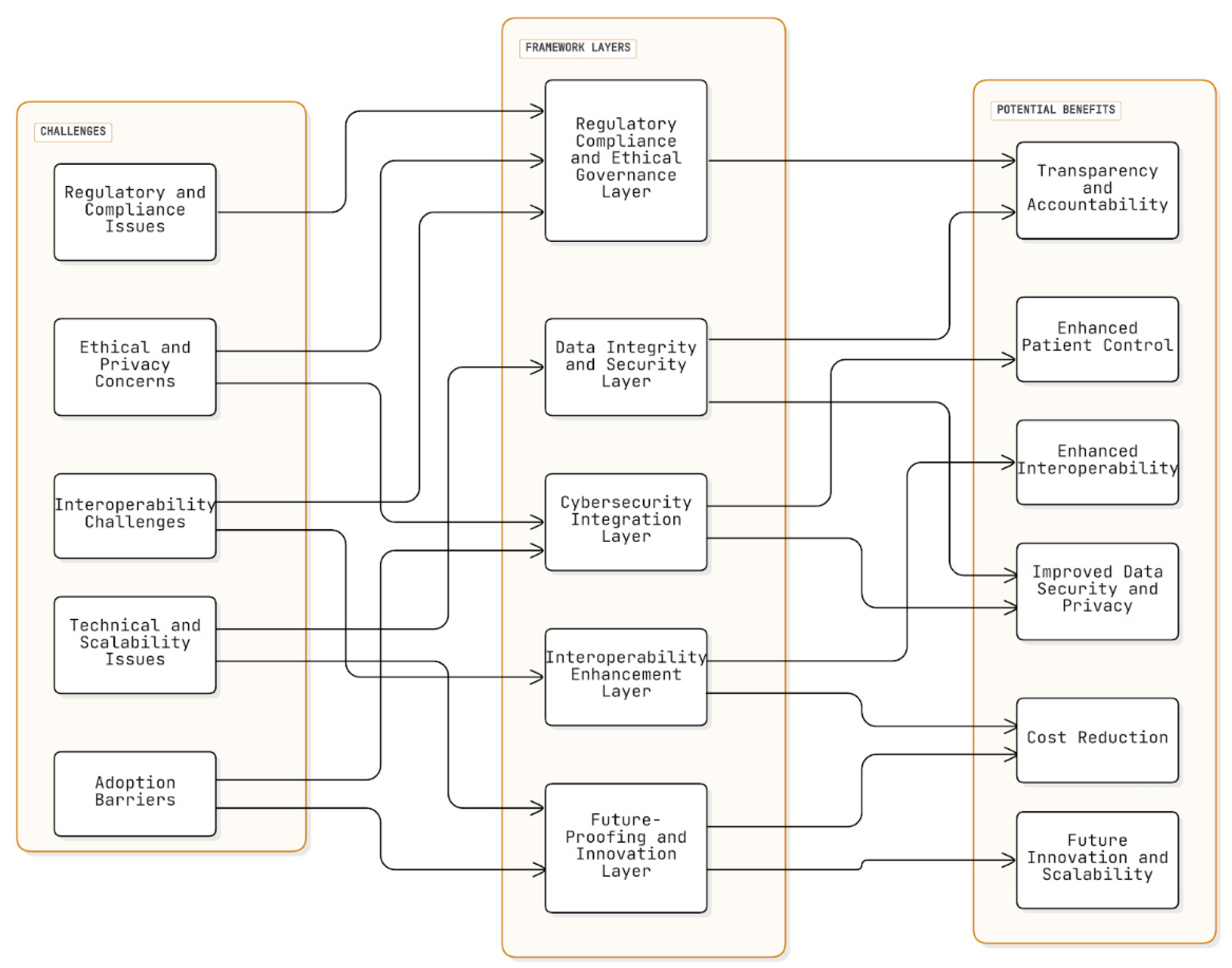
6. Challenges and Potential Benefits
6.1. Challenges
6.1.1. Technical and Scalability Issues
6.1.2. Regulatory and Compliance Issues
6.1.3. Adoption Barriers
6.1.4. Interoperability Challenges
6.1.5. Ethical and Privacy Concerns
6.2. Potential Benefits
6.2.1. Improved Data Security and Privacy
6.2.2. Enhanced Interoperability
6.2.3. Cost Reduction
6.2.4. Enhanced Patient Control
6.2.5. Transparency and Accountability
6.2.6. Future Innovation and Scalability
7. Future Prospects and Innovations
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Miriam, H.; Doreen, D.; Dahiya, D.; Rene Robin, C.R. Secured Cyber Security Algorithm for Healthcare System Using Blockchain Technology. Intell. Autom. Soft Comput. 2023, 35, 1889. [Google Scholar] [CrossRef]
- Pokharel, B.P.; Kshetri, N. blockLAW: Blockchain Technology for Legal Automation and Workflow--Cyber Ethics and Cybersecurity Platforms. arXiv 2024, arXiv:2410.06143. [Google Scholar]
- Kshetri, N.; Bhushal, C.S.; Pandey, P.S. BCT-CS: Blockchain technology applications for Cyber defense and Cybersecurity: A survey and solutions. Int. J. Adv. Comput. Sci. Appl. 2022, 13, 364–370. [Google Scholar] [CrossRef]
- IBM Security X-Force Threat Intelligence Index 2024. IBM. Available online: https://www.ibm.com/reports/threat-intelligence (accessed on 20 December 2024).
- 2024 Data Breach Investigations Report. Verizon Business. Available online: https://www.verizon.com/business/resources/reports/dbir/ (accessed on 22 December 2024).
- Begum, K.; Rashid, M.M.; Mozumder, M.A.I.; Kim, H.-C. Leveraging the Power of Blockchain for Secure Healthcare Data Management System. In Proceedings of the 2023 26th International Conference on Computer and Information Technology (ICCIT), Cox’s Bazar, Bangladesh, 13–15 December 2023. [Google Scholar]
- Sharma, S.R.; Kshetri, N. Blockchain Technology for Cybersecurity, Cyber Data, and Cyber Communication in Today’s Cyber World. In Blockchain Technology for Cyber Defense, Cybersecurity, and Countermeasures: Techniques, Solutions, and Applications; CRC Press: Boca Raton, FL, USA, 2025; pp. 94–105. [Google Scholar]
- HIPAA Compliance Guidelines. The HIPAA Journal. Available online: https://www.hipaajournal.com/hipaa-compliance-guidelines/ (accessed on 14 December 2024).
- Everything You Need to Know About GDPR Compliance. GDPR.eu. Available online: https://gdpr.eu/compliance/ (accessed on 14 December 2024).
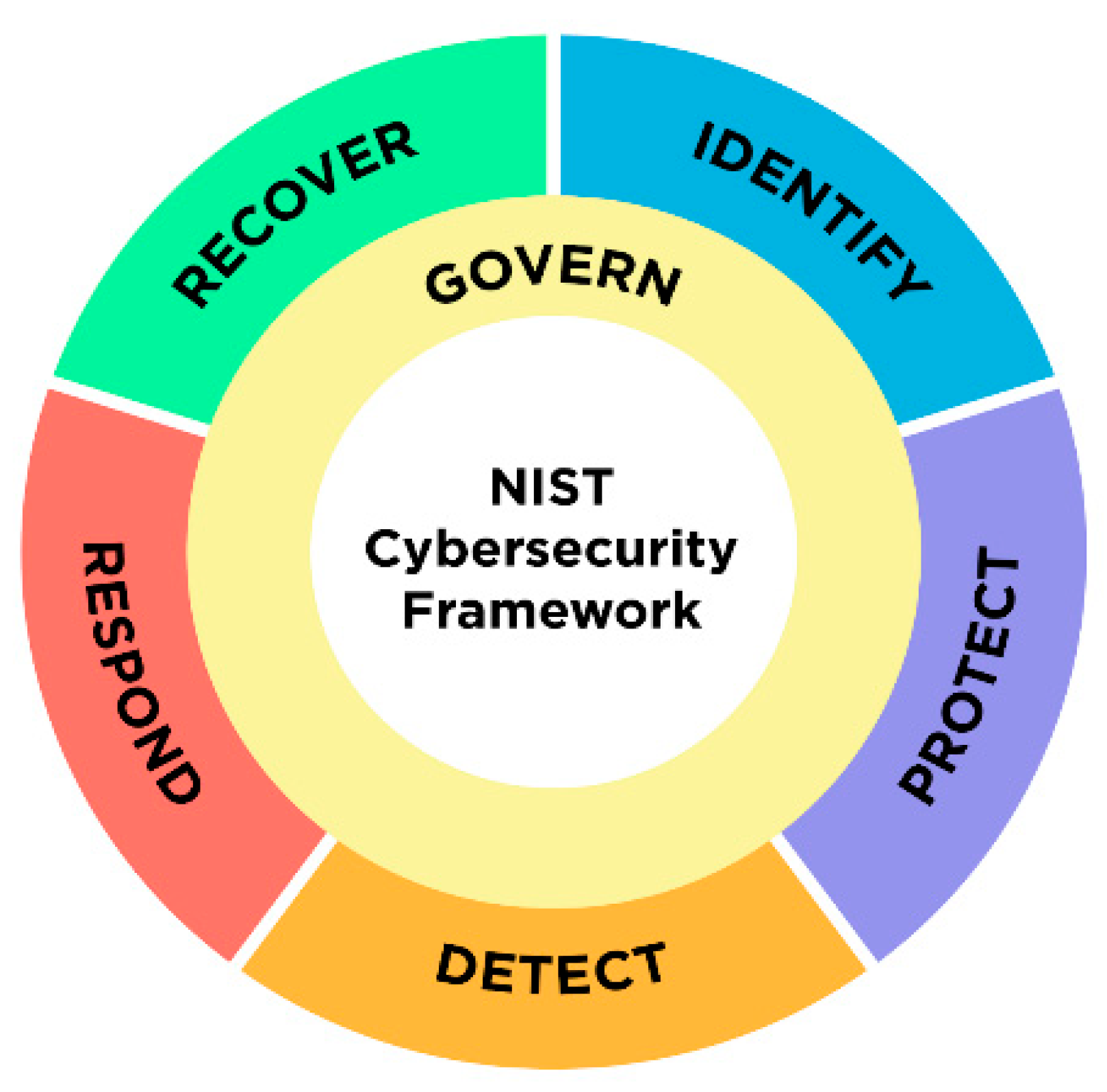
- The NIST Cybersecurity Framework (CSF) 2.0. 2024. Available online: https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.29.pdf (accessed on 13 November 2024).
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Bitcoin White Paper. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 13 November 2024).
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Ettaloui, N.; Arezki, S.; Gadi, T. An overview of blockchain-based Electronic Health Records and compliance with GDPR and HIPAA. Data Metadata 2023, 2, 166. [Google Scholar] [CrossRef]
- Zhang, W.; Qamar, F.; Abdali, T.-A.N.; Hassan, R.; Jafri, S.T.; Nguyen, Q.N. Blockchain technology: Security issues, healthcare applications, challenges, and future trends. Electronics 2023, 12, 546. [Google Scholar] [CrossRef]
- Satybaldy, A.; Hasselgren, A.; Nowostawski, M. Decentralized Identity Management for E-Health Applications: State-of-the-Art and Guidance for Future Work. Blockchain Healthc. Today 2022, 5. [Google Scholar] [CrossRef] [PubMed]
- Haleem, A.; Javaid, M.; Singh, R.P.; Suman, R.; Rab, S. Blockchain technology applications in Healthcare: An overview. Int. J. Intell. Netw. 2021, 2, 130–139. [Google Scholar] [CrossRef]
- Buterin, V. A Next-Generation Smart Contract and Decentralized Application Platform. Ethereum White Paper. 2014. Available online: https://ethereum.org/en/whitepaper/ (accessed on 9 November 2024).
- Dubovitskaya, A.; Baig, F.; Xu, Z.; Shukla, R.; Zambani, P.S.; Swaminathan, A.; Jahangir, M.M.; Chowdhry, K.; Lachhani, R.; Idnani, N.; et al. Action-EHR: Patient-centric blockchain-based electronic health record data management for cancer care. J. Med. Internet Res. 2020, 22, e13598. [Google Scholar] [CrossRef] [PubMed]
- Shaukat, K.; Luo, S.; Varadharajan, V.; Hameed, I.A.; Xu, M. A survey on machine learning techniques for cyber security in the last decade. IEEE Access 2020, 8, 222310–222354. [Google Scholar] [CrossRef]
- Chaturvedi, I.; Pawar, P.M.; Muthalagu, R.; Tamizharasan, P.S. Zero Trust Security Architecture for Digital Privacy in Healthcare. In Springer Tracts in Electrical and Electronics Engineering; Springer: Berlin/Heidelberg, Germany, 2024; pp. 1–23. [Google Scholar] [CrossRef]
- Ullah, F.; He, J.; Zhu, N.; Wajahat, A.; Nazir, A.; Qureshi, S.; Pathan, M.S.; Dev, S. Blockchain-enabled EHR Access Auditing: Enhancing Healthcare Data Security. Heliyon 2024, 10, e34407. [Google Scholar] [CrossRef] [PubMed]
- Bajwa, J.; Munir, U.; Nori, A.; Williams, B. Artificial Intelligence in healthcare: Transforming the practice of medicine. Future Healthc. J. 2021, 8, e188–e194. [Google Scholar] [CrossRef] [PubMed]
- Satamraju, K.P. Proof of concept of scalable integration of internet of things and blockchain in Healthcare. Sensors 2020, 20, 1389. [Google Scholar] [CrossRef]
- Sarosh, P.; Parah, S.A.; Malik, B.A.; Hijji, M.; Muhammad, K. Real-time medical data security solution for Smart Healthcare. IEEE Trans. Ind. Inform. 2023, 19, 8137–8147. [Google Scholar] [CrossRef]
- Yigzaw, K.Y.; Olabarriaga, S.D.; Michalas, A.; Marco-Ruiz, L.; Hillen, C.; Verginadis, Y.; de Oliveira, M.T.; Krefting, D.; Penzel, T.; Bowden, J.; et al. Health Data Security and Privacy: Challenges and solutions for the future. In Roadmap to Successful Digital Health Ecosystems; Academic Press: Cambridge, MA, USA, 2022; pp. 335–362. [Google Scholar] [CrossRef]
- Pradhan, B.; Bhattacharyya, S.; Pal, K. IOT-based applications in healthcare devices. J. Healthc. Eng. 2021, 2021, 1–18. [Google Scholar] [CrossRef] [PubMed]
- Adere, E. M Blockchain in healthcare and IOT: A systematic literature review. Array 2022, 14, 100139. [Google Scholar] [CrossRef]
- Liu, H.; Crespo, R.G.; Martínez, O.S. Enhancing privacy and data security across healthcare applications using blockchain and distributed ledger concepts. Healthcare 2020, 8, 243. [Google Scholar] [CrossRef]
- Nifakos, S.; Chandramouli, K.; Nikolaou, C.K.; Papachristou, P.; Koch, S.; Panaousis, E.; Bonacina, S. Influence of human factors on cyber security within healthcare organisations: A systematic review. Sensors 2021, 21, 5119. [Google Scholar] [CrossRef]
- Bodkhe, U.; Tanwar, S.; Parekh, K.; Khanpara, P.; Tyagi, S.; Kumar, N.; Alazab, M. Blockchain for Industry 4.0: A comprehensive review. IEEE Access 2020, 8, 79764–79800. [Google Scholar] [CrossRef]
- Corte-Real, A.; Nunes, T.; da Cunha, P.R. Reflections about Blockchain in health data sharing: Navigating a disruptive technology. Int. J. Environ. Res. Public Health 2024, 21, 230. [Google Scholar] [CrossRef]
- Onik Md, M.; Aich, S.; Yang, J.; Kim, C.-S.; Kim, H.-C. Blockchain in Healthcare: Challenges and solutions. In Big Data Analytics for Intelligent Healthcare Management; Academic Press: Cambridge, MA, USA, 2019; pp. 197–226. [Google Scholar] [CrossRef]
- Angraal, S.; Krumholz, H.M.; Schulz, W.L. Blockchain technology: Applications in Health Care. Circ. Cardiovasc. Qual. Outcomes 2017, 10. [Google Scholar] [CrossRef] [PubMed]
- Villarreal, E.R.; Garcia-Alonso, J.; Moguel, E.; Alegria, J.A. Blockchain for Healthcare Management Systems: A survey on interoperability and Security. IEEE Access 2023, 11, 5629–5652. [Google Scholar] [CrossRef]
- Nzuva, S. Smart contracts implementation, applications, benefits, and limitations. J. Inf. Eng. Appl. 2019, 9, 63–75. [Google Scholar] [CrossRef]
- Ndayizigamiye, P.; Dube, S. Potential adoption of blockchain technology to enhance transparency and accountability in the public healthcare system in South Africa. In Proceedings of the 2019 International Multidisciplinary Information Technology and Engineering Conference (IMITEC), Vanderbijlpark, South Africa, 21–22 November 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Fatoum, H.; Hanna, S.; Halamka, J.D.; Sicker, D.C.; Spangenberg, P.; Hashmi, S.K. Blockchain integration with digital technology and the future of HealthCare Ecosystems: Systematic Review. J. Med. Internet Res. 2021, 23, e19846. [Google Scholar] [CrossRef] [PubMed]
- Andrew, J.; Isravel, D.P.; Sagayam, K.M.; Bhushan, B.; Sei, Y.; Eunice, J. Blockchain for Healthcare Systems: Architecture, Security Challenges, Trends and Future Directions. J. Netw. Comput. Appl. 2023, 215, 103633. [Google Scholar] [CrossRef]
| Cybersecurity Challenges | Description | Blockchain-Based Solution |
|---|---|---|
| Data Breaches | Frequent cyberattacks exposing sensitive health records and patient data. | Blockchain’s cryptographic security and decentralized storage ensure tamper-proof and secure data management |
| Unauthorized Access to Health Records | Insider threats and lack of access control lead to misuse of patient data. | Permissioned blockchain networks enforce strict access controls and transparent access logs. |
| Interoperability Risks | Fragmented healthcare systems hinder secure data exchange between institutions | Standardized data formats on blockchain enable seamless and secure data sharing across healthcare entities |
| Ransomware Attacks | Cybercriminals encrypt data, demanding payment to release it. | Decentralized and immutable data storage on blockchain prevents unauthorized encryption or manipulation of data. |
| Lack of Auditability and Transparency | Limited visibility into who accesses or modifies healthcare data. | Blockchain’s immutable ledger ensures transparent, tamper-proof audit trails for data usage and modifications. |
| Fraudulent Activities in Clinical Trials | Manipulated data reduces trust and increases operational risks. | Blockchain provides verifiable and transparent records, preventing data manipulation in clinical trials. |
| Supply Chain Security | Counterfeit drugs and inefficiencies in pharmaceutical tracking. | Blockchain enhances traceability and authenticity, ensuring secure pharmaceutical supply chains. |
| Category | Details |
|---|---|
| Frequency | 1378 incidents, 1220 with confirmed data disclosure |
| Top Patterns | Miscellaneous Errors, Privilege Misuse, and System Intrusion (83% of breaches) |
| Threat Actors | Internal (70%), External (30%) (breaches) |
| Actor Motives | Financial (98%), Espionage (1%) (breaches) |
| Data Compromised | Personal (75%), Internal (51%), Other (25%), Credentials (13%) (breaches) |
| Consistent Trends | System Intrusion breaches remain in the top three attack patterns |
| Layer | Functionality |
|---|---|
| Data Integrity and Security Layer | Uses cryptographic hashing and decentralized storage to prevent data tampering and unauthorized modifications. |
| Interoperability Enhancement Layer | Implements FHIR/HL7 standards and permissioned blockchain networks to facilitate secure medical data exchange between healthcare providers. |
| Cybersecurity Integration Layer | Incorporates Intrusion Detection Systems (IDS), Zero Trust Architecture (ZTA), and AI-driven threat analysis to monitor and mitigate cyber threats. |
| Regulatory Compliance and Governance Layer | Ensure compliance with HIPAA, GDPR, and NIST standards through blockchain-based audit trials and automated access controls. |
| Future-Proofing and Innovation Layer | Focuses on AI-driven analytics, IoT integration, and scalability features to ensure adaptability to emerging healthcare challenges. |
| Participant | Role in the Blockchain System |
|---|---|
| Patients | Own and control access to their health records using Decentralized Identity (DID) mechanisms. |
| Healthcare Providers | Upload medical data securely using cryptographic hashing and interact with smart contracts for automated data verification. |
| Regulatory Authorities | Monitor compliance, conduct audits, and verify transactions on the blockchain to ensure regulatory adherence. |
| Insurance Companies | Access patient-approved medical records for claims processing, reducing fraud and ensuring faster approvals. |
| Cybersecurity Teams | Oversee intrusion detection, malware analysis, and system monitoring, ensuring security across all layers. |
| Function | Description |
|---|---|
| Patient Consent Management | Automates patient approval and revocation of medical data access requests. |
| Medical Record Validation | Ensures that only verified healthcare providers can update patient records. |
| Insurance Claims Processing | Automates claim verification, reducing fraudulent transactions and improving efficiency. |
| Role | Description | Benefits | Example | Ref. |
|---|---|---|---|---|
| Data Integrity | Blockchain’s immutable ledger ensures that any alterations to data are permanently recorded, providing a transparent and secure audit trail. | Reduces fraud and unauthorized modifications. | Tracking changes in Electronic Medical Records (EMRs). | [21] |
| Decentralized Data Management | Eliminate the need for a central authority by distributing data across various nodes in the blockchain network. | Remove single points of failure, improving system resilience | Decentralized access for hospital networks. | [15] |
| Secure Data Sharing | Facilitates encrypted and efficient data exchange among healthcare providers while maintaining authenticity. | Enhances interoperability and reduces data silos. | Sharing lab results between hospitals. | [16] |
| Patient Empowerment | Decentralized Identity (DID) systems empower patients to control their personal health data, allowing them to decide who can access it. | Builds trust, improves data transparency, and supports privacy. | Patients managing their digital health records. | [15] |
| Data Provenance | It monitors the source and changes to data, ensuring accountability and verifying the authenticity of data usage. | Ensures reliability and reduces data tampering. | Maintaining an accurate supply chain for medical devices | [22] |
| Compliance and Reporting | Automates compliance tracking for regulations like HIPAA and GDPR through smart contracts and immutable records. | Reduces administrative burden, ensures regulatory adherence. | Automating GDPR-compliant data access logs. | [13] |
| Fraud Detection | Blockchains’ transparency enables real-time fraud detection and accountability in medical billing and insurance claims. | Minimizes financial losses from fraudulent activities. | Verifying insurance claims against treatment records. | [16] |
| Scalable Research Collaboration | Provides a secure, shared database for researchers to store and share anonymized data without compromising patient privacy. | Facilitates global research collaboration. | Sharing anonymized genomic data for medical research. | [23] |
| Supply Chain Integrity | Tracks the journey of pharmaceuticals and medical supplies from production to delivery, ensuring authenticity. | Reduces counterfeit medicines and improves supply chain efficiency. | Monitoring vaccine distribution. | [22,24] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pokharel, B.P.; Kshetri, N.; Sharma, S.R.; Paudel, S. blockHealthSecure: Integrating Blockchain and Cybersecurity in Post-Pandemic Healthcare Systems. Information 2025, 16, 133. https://doi.org/10.3390/info16020133
Pokharel BP, Kshetri N, Sharma SR, Paudel S. blockHealthSecure: Integrating Blockchain and Cybersecurity in Post-Pandemic Healthcare Systems. Information. 2025; 16(2):133. https://doi.org/10.3390/info16020133
Chicago/Turabian StylePokharel, Bishwo Prakash, Naresh Kshetri, Suresh Raj Sharma, and Sobaraj Paudel. 2025. "blockHealthSecure: Integrating Blockchain and Cybersecurity in Post-Pandemic Healthcare Systems" Information 16, no. 2: 133. https://doi.org/10.3390/info16020133
APA StylePokharel, B. P., Kshetri, N., Sharma, S. R., & Paudel, S. (2025). blockHealthSecure: Integrating Blockchain and Cybersecurity in Post-Pandemic Healthcare Systems. Information, 16(2), 133. https://doi.org/10.3390/info16020133






