Unveiling Dark Web Identity Patterns: A Network-Based Analysis of Identification Types and Communication Channels in Illicit Activities
Abstract
1. Introduction
- What are the predominant types of IDs used on the Dark Web, and how do they facilitate communication and coordination?This question seeks to identify the most common ID types (e.g., email, Telegram, cryptocurrency wallets) and their roles in enabling interactions within the Dark Web.
- How are different topics of activity (e.g., hacking, finance, drugs–narcotics) distributed across the Dark Web network IDs, and what are their linguistic and structural characteristics?This question explores the thematic and linguistic patterns of Dark Web activities, focusing on how different topics are organized and interconnected between different forms of identification.
- How do ID subnetworks differ in terms of connectivity, cohesion, and fragmentation?This question investigates and compares the overall structural organization of subnetworks of activity by ID type, including the largest connected components, subnetworks, and their metrics (e.g., density, average path, centrality).
- How do specific ID types (e.g., Telegram, email, XMR wallets) contribute to the overall network, and what are their unique roles in facilitating different types of activities?This question examines the distinct roles of various ID types, focusing on their centrality, connectivity, and specialization within the network.
- What insights can be gained from analyzing the central areas of activity (largest connected components and k-cores) of the Dark Web network, and how do they reveal the key areas of activity?This question focuses on identifying the core areas of activity within the network, using k-cores and connected components.
2. State of the Art
3. Materials and Methods
3.1. Data Gathering and Preprocessing
3.2. Analytical Tools
3.3. Validation and Error Estimation
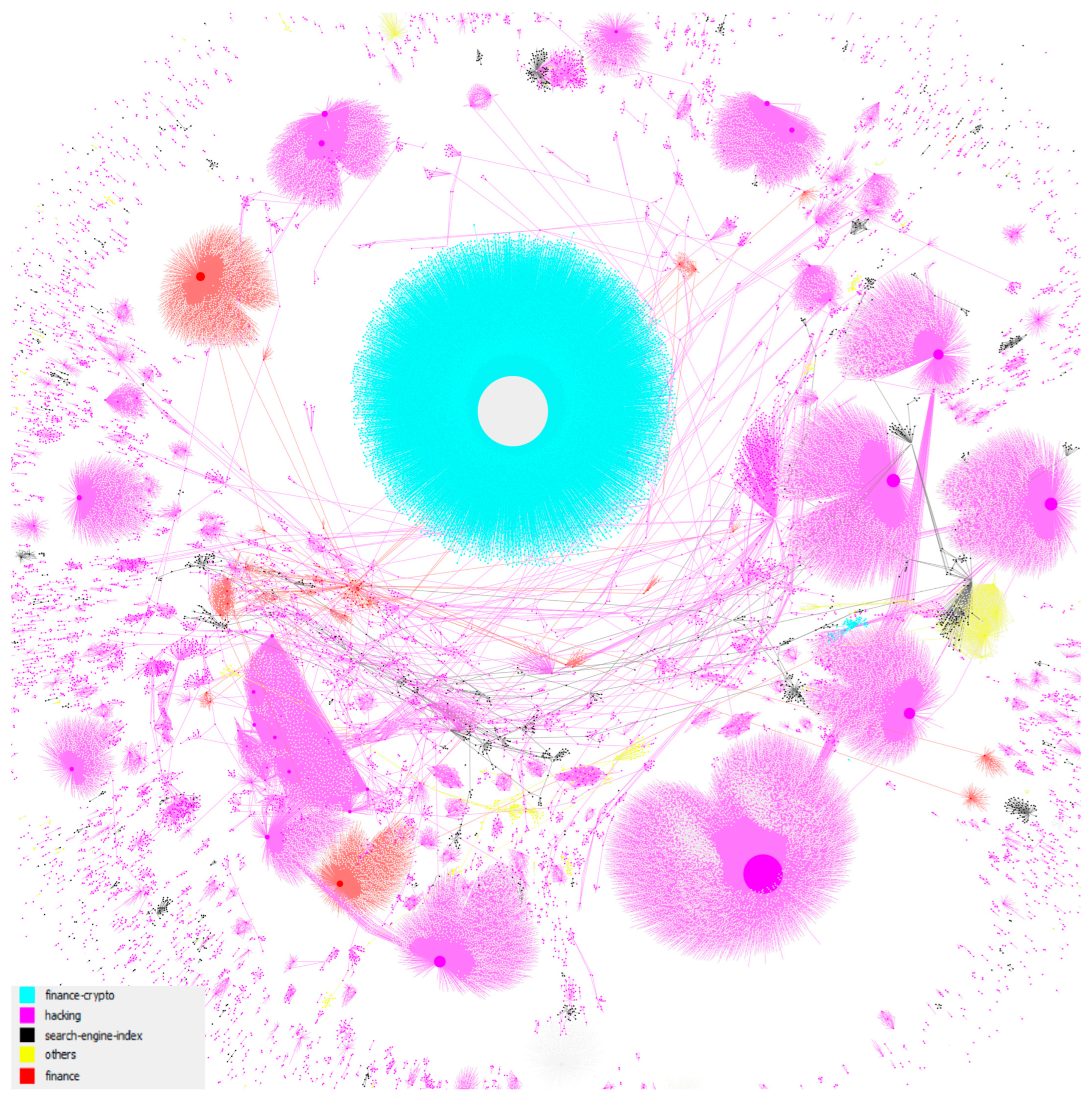
4. Results
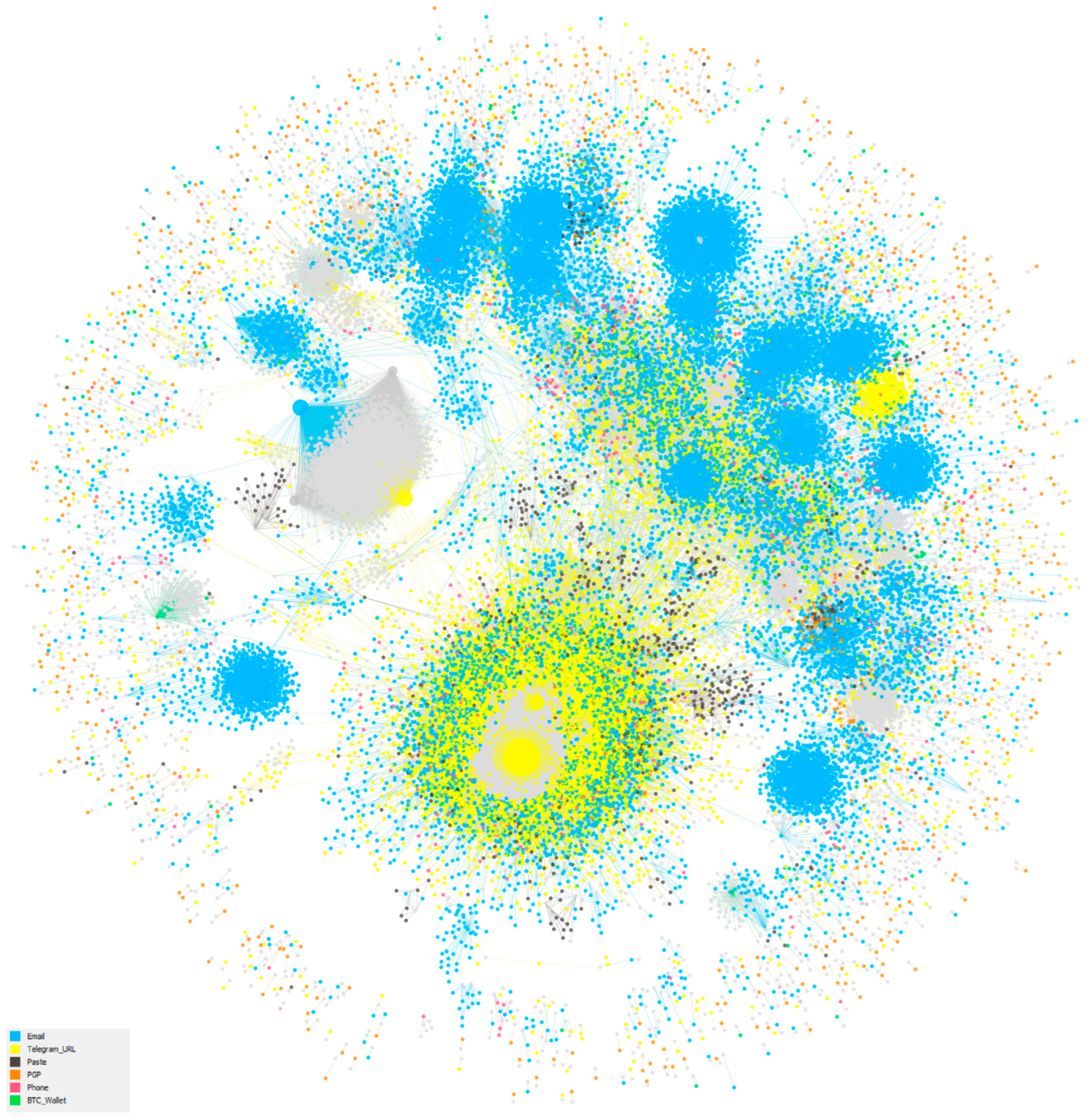
4.1. ID Types and Their Connections
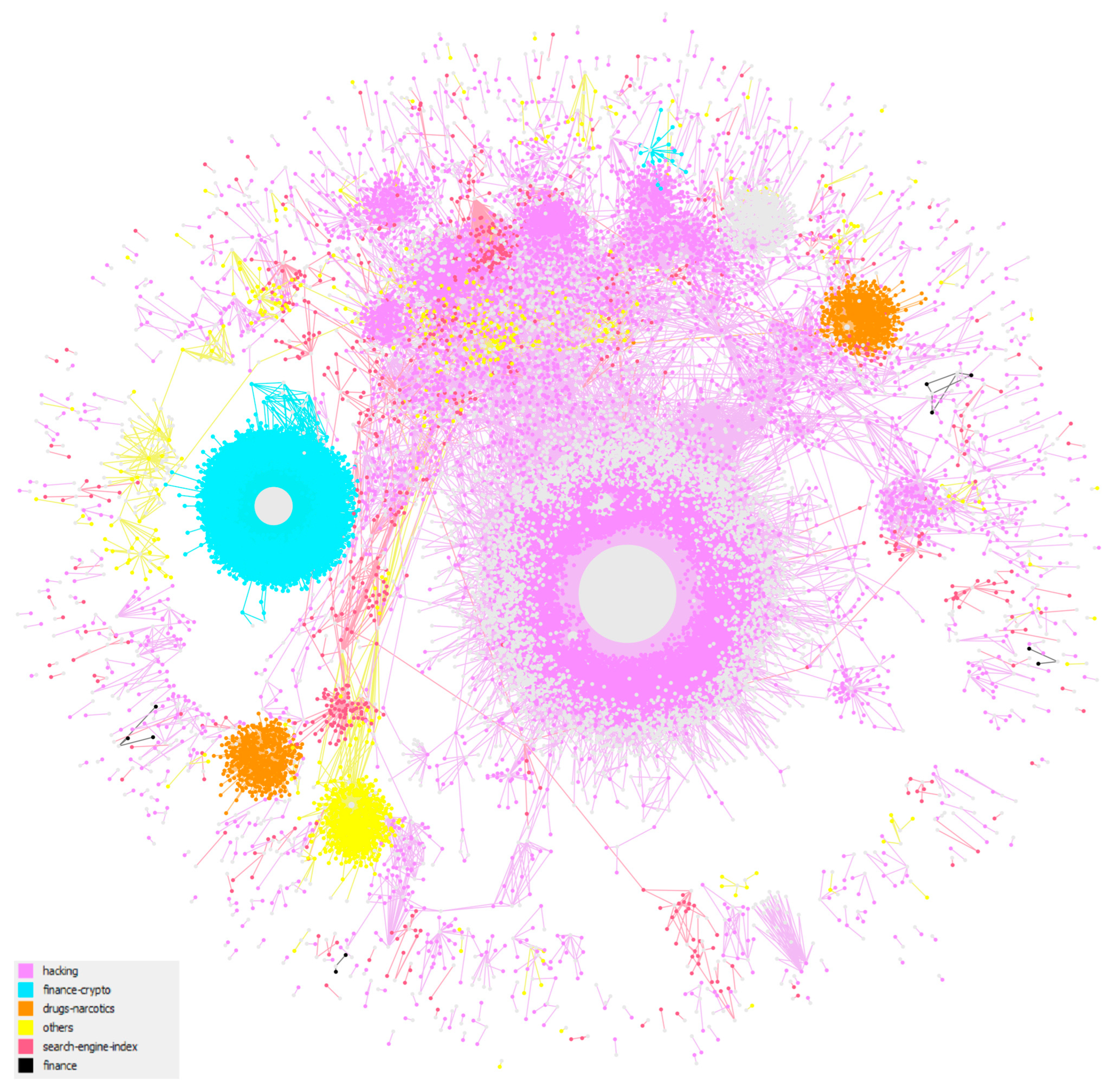
4.2. Top Topics and Languages for the Largest ID Networks
4.3. Main Network
4.3.1. Overall Network Structure
4.3.2. Largest Connected Component
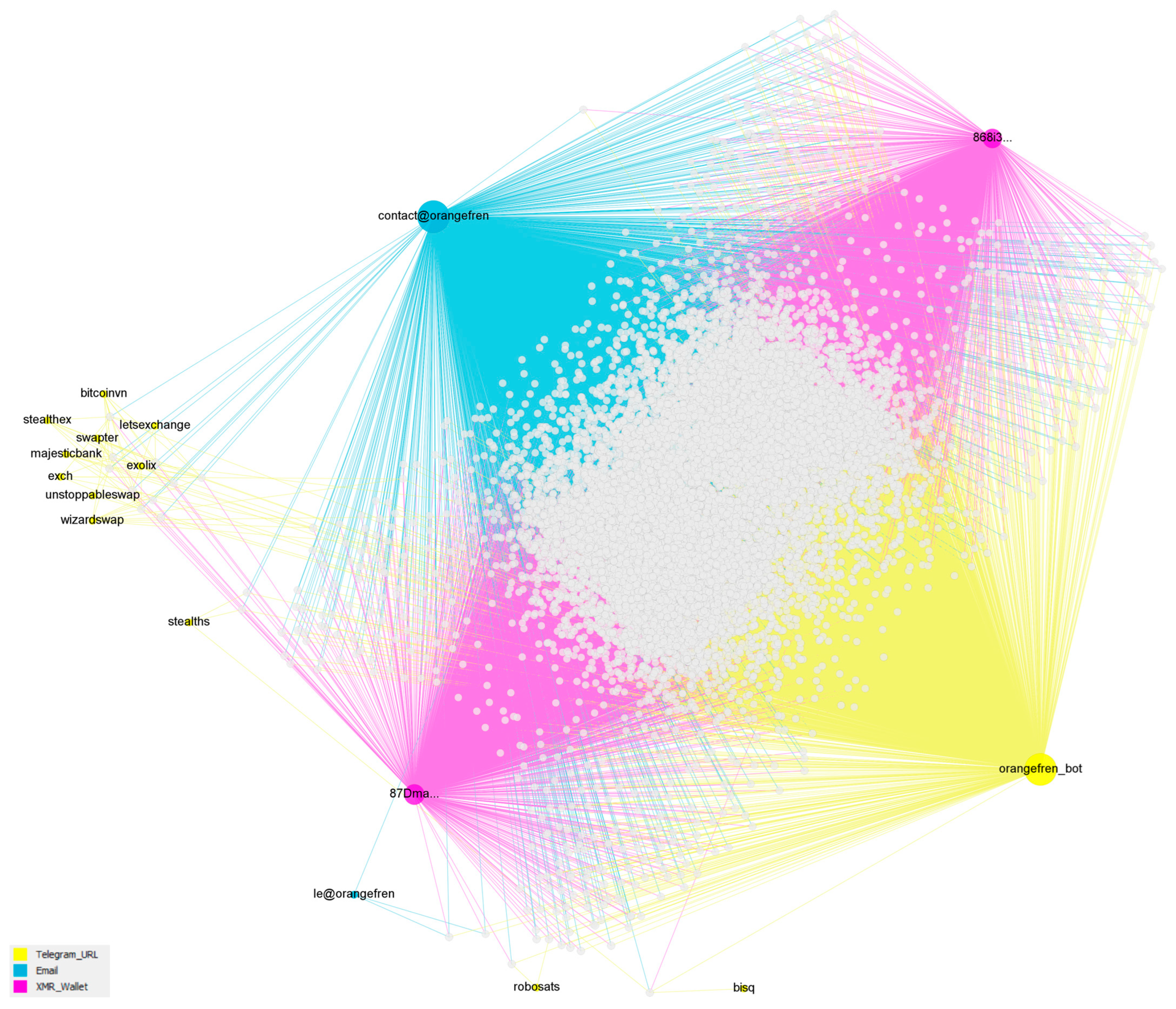
4.3.3. Second Largest Connected Component
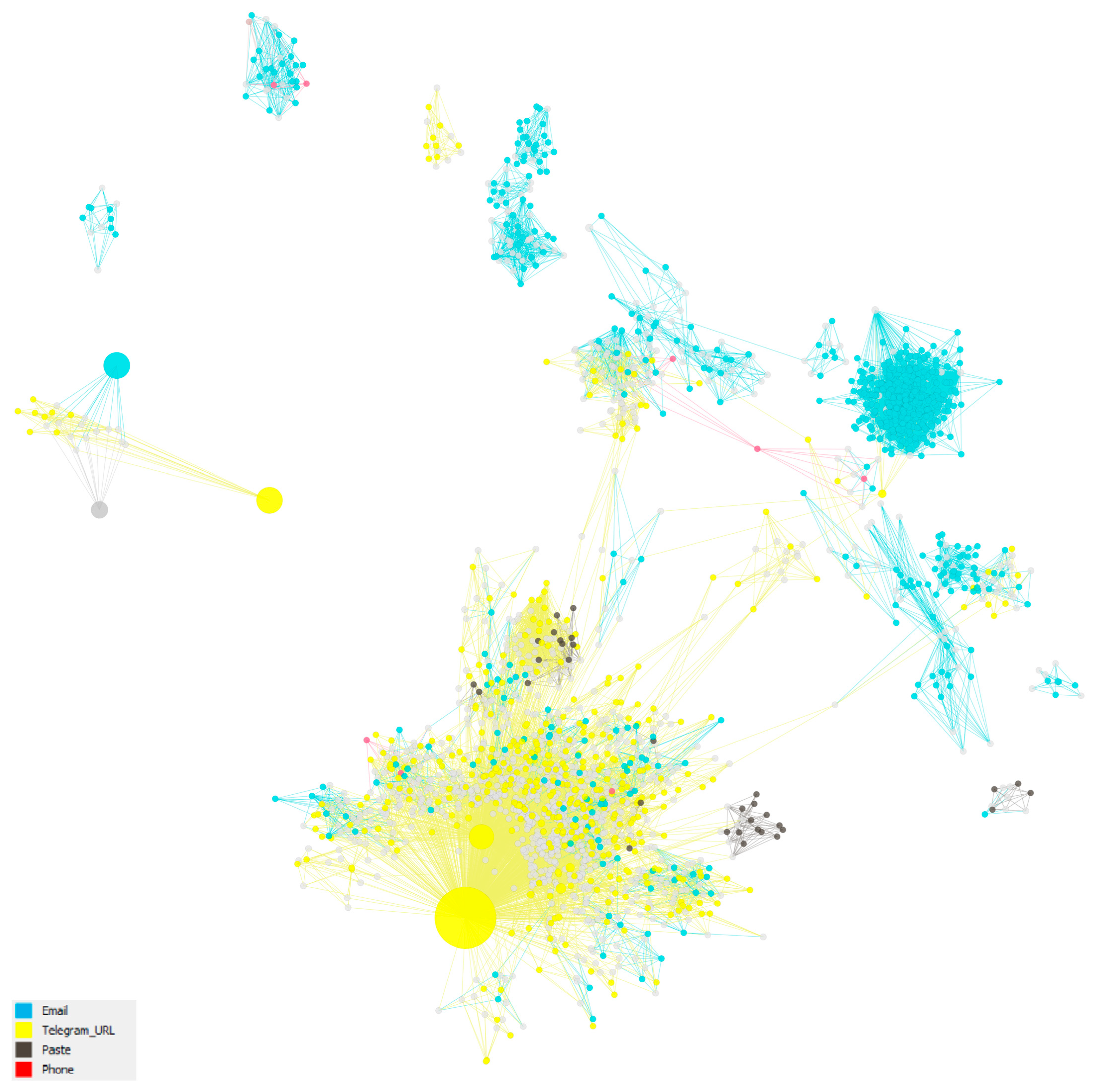
4.3.4. k-Core Analysis: The 5-Core
4.4. Subnetworks by ID Type
4.4.1. Metrics of Subnetworks by ID Type
4.4.2. Telegram Subnetwork by Topic
4.4.3. Email Subnetwork by Topic
4.5. Qualitative Content Analysis
- Telegram—primarily used for coordination, broadcast announcements, and contact exchange.
- XMR wallets—predominantly used for payment instructions, escrow, and transaction verification.
- Email—used for customer follow-ups, negotiation of trades, or technical inquiries.
5. Discussion
Limitations and Future Work
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Chertoff, M.; Simon, T. The Impact of the Dark Web on Internet Governance and Cyber Security; Global Commission on Internet Governance: Waterloo, ON, Canada, 2025. [Google Scholar]
- Soska, K.; Christin, N. Measuring the longitudinal evolution of the online anonymous marketplace ecosystem. In Proceedings of the USENIX Security Symposium, Washington, DC, USA, 12–14 August 2015; pp. 33–48. [Google Scholar]
- Weimann, G. Terrorist migration to the Dark Web. Perspect. Terror. 2016, 10, 40–44. [Google Scholar]
- De-Marcos, L.; Domínguez-Díaz, A. LLM-Based Topic Modeling for Dark Web Q&A forums: A Comparative Analysis with Traditional Methods. IEEE Access 2025, 13, 67159–67169. [Google Scholar] [CrossRef]
- De-Marcos, L.; Domínguez-Díaz, A.; Stapić, Z. What’s Going on in Dark Web Question and Answer Forums: Topic Diversity and Linguistic Characteristics. IEEE Access 2025, 13, 149880–149890. [Google Scholar] [CrossRef]
- Kühn, P.; Wittorf, K.; Reuter, C. Navigating the shadows: Manual and semi-automated evaluation of the dark web for cyber threat intelligence. IEEE Access 2024, 12, 118903–118922. [Google Scholar] [CrossRef]
- Sangher, K.S.; Singh, A.; Pandey, H.M.; Kumar, V. Towards Safe Cyber Practices: Developing a Proactive Cyber-Threat Intelligence System for Dark Web Forum Content by Identifying Cybercrimes. Information 2023, 14, 349. [Google Scholar] [CrossRef]
- Bugajewska, M. A survey of challenges in dark web crawling: Technical, security, and ethical perspective. In Artificial Intelligence and Machine Learning. IBIMA-AI 2024. Communications in Computer and Information Science; Soliman, K.S., Ed.; Springer: Cham, Switzerland, 2025; Volume 2300. [Google Scholar] [CrossRef]
- Arabnezhad, E.; La Morgia, M.; Mei, A.; Nemmi, E.N.; Stefa, J. A light in the dark web: Linking dark web aliases to real internet identities. In Proceedings of the 2020 IEEE 40th International Conference on Distributed Computing Systems (ICDCS), Singapore, 29 November–1 December 2020; pp. 311–321. [Google Scholar] [CrossRef]
- Manolache, A.; Brad, F.; Barbalau, A.; Ionescu, R.T.; Popescu, M. VeriDark: A large-scale benchmark for authorship verification on the dark web. In Proceedings of the 36th International Conference on Neural Information Processing Systems (NIPS ’22); Koyejo, S., Mohamed, S., Agarwal, A., Belgrave, D., Cho, K., Oh, A., Eds.; Curran Associates Inc.: Red Hook, NY, USA, 2022; Article 1133; Volume 35, pp. 15574–15588. [Google Scholar]
- Nali, M.C.; Purushothaman, V.; Li, Z.; Larsen, M.Z.; Cuomo, R.E.; Yang, J.; Mackey, T.K. Identification and characterization of illegal sales of cannabis and nicotine delivery products on Telegram messaging platform. Nicotine Tob. Res. 2024, 26, 771–779. [Google Scholar] [CrossRef]
- La Morgia, M.; Mei, A.; Mongardini, A.M.; Wu, J. Uncovering the dark side of Telegram: Fakes, clones, scams, and conspiracy movements. arXiv 2021, arXiv:2111.13530. [Google Scholar] [CrossRef]
- Lee, S.; Yoon, C.; Kang, H.; Kim, Y.; Kim, Y.; Han, D.; Son, S.; Shin, S. Cybercriminal minds: An investigative study of cryptocurrency abuses in the dark web. In Proceedings of the Network and Distributed Systems Security (NDSS) Symposium 2019, San Diego, CA, USA, 24–27 February 2019; pp. 24–27. [Google Scholar] [CrossRef]
- Paquet-Clouston, M.; Haslhofer, B.; Dupont, B. Ransomware payments in the Bitcoin ecosystem. J. Cybersecur. 2019, 5, 1–11. [Google Scholar] [CrossRef]
- Dearden, T.E.; Tucker, S.E. Follow the money: Analyzing darknet activity using cryptocurrency and the Bitcoin blockchain. J. Contemp. Crim. Justice 2023, 39, 257–275. [Google Scholar] [CrossRef]
- Décary-Hétu, D.; Dupont, B. The social network of hackers. Glob. Crime 2012, 13, 160–175. [Google Scholar] [CrossRef]
- Takaaki, S.; Atsuo, I. Dark web content analysis and visualization. In Proceedings of the ACM International Workshop on Security and Privacy Analytics (IWSPA ’19), Richardson, TX, USA, 27 March 2019; pp. 53–59. [Google Scholar] [CrossRef]
- Cilleruelo, C.; de-Marcos, L.; Junquera-Sanchez, J.; Martinez-Herraiz, J. Interconnection between darknets. IEEE Internet Comput. 2021, 25, 61–70. [Google Scholar] [CrossRef]
- Alharbi, A.; Alhassan, M.; Alshahrani, M.; Alzahrani, A. Exploring the topological properties of the Tor dark web. IEEE Access 2021, 9, 21746–21758. [Google Scholar] [CrossRef]
- Borgatti, S.P.; Everett, M.G.; Johnson, J.C. Analyzing Social Networks; SAGE Publications: Thousand Oaks, CA, USA, 2018. [Google Scholar]
- Javed, M.S.; Sajjad, S.M.; Mehmood, D.; Mansoor, K.; Iqbal, Z.; Kazim, M.; Muhammad, Z. Analyzing Tor Browser Artifacts for Enhanced Web Forensics, Anonymity, Cybersecurity, and Privacy in Windows-Based Systems. Information 2024, 15, 495. [Google Scholar] [CrossRef]
- Figueras-Martín, E.; Magán-Carrión, R.; Boubeta-Puig, J. Drawing the web structure and content analysis beyond the Tor darknet: Freenet as a case of study. J. Inf. Secur. Appl. 2022, 66, 103229. [Google Scholar] [CrossRef]
- Hiramoto, N.; Tsuchiya, Y. Measuring dark web marketplaces via Bitcoin transactions: From birth to independence. Forensic Sci. Int. Digit. Investig. 2020, 35, 301086. [Google Scholar] [CrossRef]
- Tsuchiya, Y.; Hiramoto, N. Dark web in the dark: Investigating when transactions take place on cryptomarkets. Forensic Sci. Int. Digit. Investig. 2021, 36, 301093. [Google Scholar] [CrossRef]
- Almukaynizi, M.; Grimm, A.; Nunes, E.; Shakarian, J.; Shakarian, P. Predicting cyber threats through hacker social networks in darkweb and deepweb forums. In Proceedings of the CSS ’17, CSSSA’s Annual Conference on Computational Social Science, New York, NY, USA, 19–22 October 2017; pp. 1–10. [Google Scholar] [CrossRef]
- Sarkar, S.; Almukaynizi, M.; Shakarian, J.; Shakarian, P. Predicting enterprise cyber incidents using social network analysis on dark web hacker forums. Cyber Def. Rev. 2019, 4, 87–102. [Google Scholar]
- Dalins, J.; Wilson, C.; Carman, M. Criminal motivation on the dark web: A categorisation model for law enforcement. Digit. Investig. 2018, 24, 62–71. [Google Scholar] [CrossRef]
- Dolejška, D.; Koutenský, M.; Veselý, V.; Pluskal, J. Busting up monopoly: Methods for modern darknet marketplace forensics. Forensic Sci. Int. Digit. Investig. 2023, 46, 301604. [Google Scholar] [CrossRef]
- Jin, P.; Kim, N.; Lee, S.; Jeong, D. Forensic investigation of the dark web on the Tor network: Pathway toward the surface web. Int. J. Inf. Secur. 2024, 23, 331–346. [Google Scholar] [CrossRef]
- Bastian, M.; Heymann, S.; Jacomy, M. Gephi: An open source software for exploring and manipulating networks. In Proceedings of the International AAAI Conference on Web and Social Media, San Jose, CA, USA, 17–20 May 2020; Volume 3, pp. 361–362. [Google Scholar]
- Jacomy, M.; Venturini, T.; Heymann, S.; Bastian, M. ForceAtlas2, a continuous graph layout algorithm for handy network visualization designed for the Gephi software. PLoS ONE 2014, 9, e98679. [Google Scholar] [CrossRef]
- Watts, D.J. Networks, dynamics, and the small-world phenomenon. Am. J. Sociol. 1999, 105, 493–527. [Google Scholar] [CrossRef]
- Phillips, E.; Nurse, J.R.C.; Goldsmith, M.; Creese, S. Extracting social structure from darkweb forums. In Proceedings of the International Conference on Cyber Security for Sustainable Society, Coventry, UK, 26–27 February 2015; pp. 11–27. [Google Scholar]
- L’Huillier, B.; Ríos, S.A.; Alvarez, H.; Aguilera, F. Topic-based social network analysis for virtual communities of interests in the dark web. In Proceedings of the ACM SIGKDD Workshop on Intelligence and Security Informatics ACM, Washington, DC, USA, 25–28 July 2010; pp. 9:1–9:9. [Google Scholar] [CrossRef]
- Pete, I.; Hughes, J.; Chua, Y.T.; Bada, M. A social network analysis and comparison of six dark web forums. In Proceedings of the 2020 IEEE European Symposium on Security and Privacy Workshops (EuroSPW), Genoa, Italy, 7–11 September 2020; pp. 484–493. [Google Scholar] [CrossRef]
- Zhang, Y.; Zeng, S.; Fan, L.; Dang, Y.; Larson, C.A.; Chen, H. Dark web forums portal: Searching and analyzing jihadist forums. In Proceedings of the 2009 IEEE International Conference on Intelligence and Security Informatics, Dallas, TX, USA, 8–11 June 2009; pp. 71–76. [Google Scholar]

| Topic | #Domains | #Documents |
|---|---|---|
| hacking | 8 | 155,489 |
| search-engine-index | 14 | 33,541 |
| finance–crypto | 4 | 23,088 |
| drugs–narcotics | 6 | 8551 |
| others | 4 | 5145 |
| finance | 2 | 3189 |
| electronics | 1 | 232 |
| Total | 53 | 229,235 |
| ID Type | #IDs | #Documents | Main Topic | # | Main Language | # |
|---|---|---|---|---|---|---|
| 43,298 | 29,735 | finance–crypto | 17,640 | English | 22,385 | |
| Telegram | 11,218 | 76,967 | hacking | 55,482 | Russian | 50,416 |
| Paste | 860 | 623 | hacking | 589 | Russian | 495 |
| PGP | 745 | 895 | search-engine-index | 856 | English | 860 |
| Phone | 531 | 807 | hacking | 656 | Russian | 560 |
| BTC wallet | 292 | 1944 | other | 689 | English | 1106 |
| Discord URL | 97 | 260 | hacking | 217 | English | 199 |
| XMR wallet | 20 | 17,644 | finance–crypto | 17,597 | English | 17,663 |
| Skype URL | 6 | 13 | hacking | 13 | Russian | 13 |
| DASH wallet | 2 | 4 | hacking | 2 | English/Russian | 2 |
| BNB wallet | 1 | 2 | hacking | 2 | English/Bulgarian | 1 |
| ZEC wallet | 1 | 1 | hacking | 1 | Russian | 1 |
| Overall network | 57,071 | 82,285 | hacking | 57,223 | Russian | 50,852 |
| ID Type | Topic | #Documents | Language | #Documents |
|---|---|---|---|---|
| Telegram | hacking | 55,482 | Russian | 50,411 |
| finance–crypto | 17,614 | English | 17,614 | |
| drugs–narcotics | 1671 | English | 1614 | |
| finance–crypto | 17,640 | English | 17,640 | |
| hacking | 9347 | Russian | 7129 | |
| search-engine-index | 1378 | English | 1357 | |
| XMR wallet | finance–crypto | 17,597 | English | 17,597 |
| search-engine-index | 30 | English | 30 | |
| hacking | 14 | Russian | 11 | |
| BTC wallet | other | 689 | Portuguese | 641 |
| drugs–narcotics | 355 | English | 355 | |
| hacking | 308 | Russian | 182 |
| Subcategory | #Nodes | #Edges | #Documents | #IDs | Connected Components | Size Largest Component | Density | Avg. Path Length | Diameter | Avg. Degree | Avg. Closeness | Avg. Betweenness |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| BTC Wallet | 2236 | 2024 | 1944 | 292 | 224 | 644 (28.8%) | 0.004 | 1.11 | 7 | 0.004 | 0.598 | <0.001 |
| Discord URL | 357 | 314 | 260 | 97 | 66 | 71 (19.9%) | 0.013 | 1.68 | 5 | 0.012 | 0.657 | <0.001 |
| 73,033 | 83,464 | 29,735 | 43298 | 3044 | 17,649 (24.2%) | <0.001 | 3.35 | 32 | <0.001 | 0.446 | <0.001 | |
| Paste | 1483 | 1681 | 623 | 860 | 289 | 60 (4.0%) | 0.003 | 2.31 | 9 | 0.003 | 0.699 | <0.001 |
| PGP | 1640 | 1009 | 895 | 745 | 670 | 59 (3.6%) | 0.002 | 1.23 | 5 | 0.002 | 0.906 | <0.001 |
| Phone | 1338 | 1159 | 807 | 531 | 330 | 55 (4.1%) | 0.003 | 1.68 | 5 | 0.003 | 0.745 | <0.001 |
| Telegram | 88,185 | 141,476 | 76,967 | 11218 | 621 | 66,201 (75.1%) | <0.001 | 5.23 | 28 | <0.001 | 0.408 | <0.001 |
| XMR Wallet | 17,664 | 17,644 | 17,644 | 20 | 20 | 9204 (52.1%) | 0.050 | 1 | 1 | 0.050 | 0.501 | <0.001 |
| Overall network | 139,356 | 248,791 | 82,285 | 57071 | 1848 | 106,924 (76.72%) | <0.001 | 8.58 | 26 | <0.001 | 0.401 | <0.001 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
de-Marcos, L.; Domínguez-Díaz, A.; Junquera-Sánchez, J.; Cilleruelo, C.; Martínez-Herráiz, J.-J. Unveiling Dark Web Identity Patterns: A Network-Based Analysis of Identification Types and Communication Channels in Illicit Activities. Information 2025, 16, 924. https://doi.org/10.3390/info16110924
de-Marcos L, Domínguez-Díaz A, Junquera-Sánchez J, Cilleruelo C, Martínez-Herráiz J-J. Unveiling Dark Web Identity Patterns: A Network-Based Analysis of Identification Types and Communication Channels in Illicit Activities. Information. 2025; 16(11):924. https://doi.org/10.3390/info16110924
Chicago/Turabian Stylede-Marcos, Luis, Adrián Domínguez-Díaz, Javier Junquera-Sánchez, Carlos Cilleruelo, and José-Javier Martínez-Herráiz. 2025. "Unveiling Dark Web Identity Patterns: A Network-Based Analysis of Identification Types and Communication Channels in Illicit Activities" Information 16, no. 11: 924. https://doi.org/10.3390/info16110924
APA Stylede-Marcos, L., Domínguez-Díaz, A., Junquera-Sánchez, J., Cilleruelo, C., & Martínez-Herráiz, J.-J. (2025). Unveiling Dark Web Identity Patterns: A Network-Based Analysis of Identification Types and Communication Channels in Illicit Activities. Information, 16(11), 924. https://doi.org/10.3390/info16110924









