2. Materials and Methods
2.2. Data Collection
This study focuses on collecting literature in both the Chinese and English languages. The identification of specialized words is accomplished through expert consultation and a literature expansion method. The literature expansion method involves utilizing highly cited keywords and their associated literature keywords to expand and refine the search terms used in this paper.
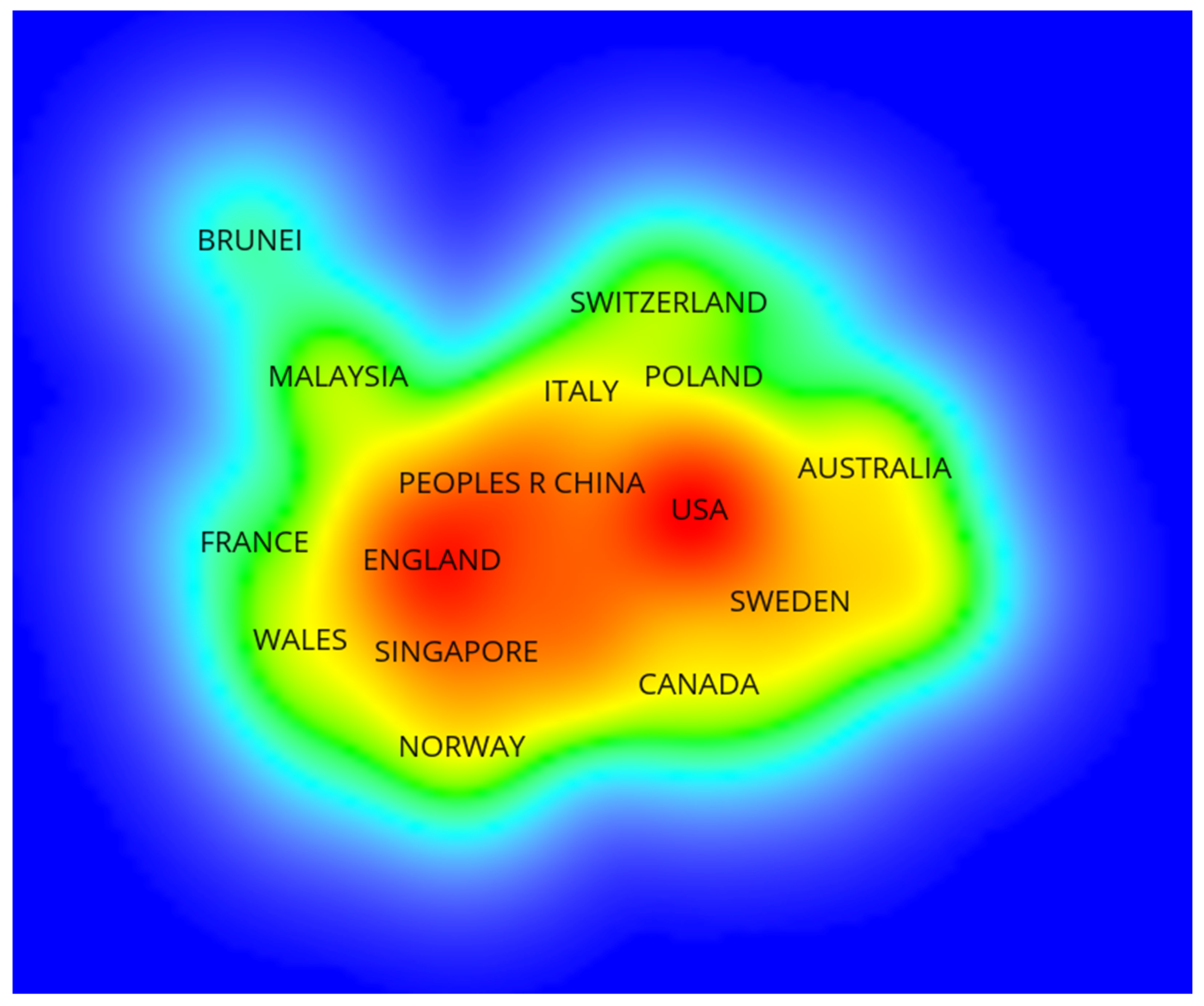
In Chinese, the keywords “Internet”, “cyberspace”, “international”, “global”, “rules”, and “governance” were used to search the Chinese Social Sciences Citation Index (CSSCI) for records from 1998 to 15 September 2020. The CSSCI, established in 1998 by Nanjing University as the authoritative citation index for Chinese humanities and social sciences, provides quality evaluation functions that enhance the precision of sample selection. To improve recall, a supplementary manual search using related terms was conducted on the CNKI database for works prior to 1998, but no additional results were found. After filtering and de-duplication, 204 valid papers, including all record fields and references, were obtained. Accordingly, 1999 was selected as the starting year of this study.
In the English language, the Web of Science (WoS) database core collection, specifically the Social Science Citation Index (SSCI) database, served as the data source. The search was conducted using the following keywords: “Cyberspace”, “Cyber”, “International”, “Global”, “Rule”, “Law”, “Norms”, and “Global Governance”. These keywords were combined and arranged, and a comprehensive search was performed across the entire database for articles of the “Article” type in the subject (Topic) field. Initially, 146 articles were obtained, and after removing duplicates, 144 articles remained, encompassing all record fields and references. The data collection process concluded on 3 January 2021.
We use CSSCI to represent Chinese-language social science scholarship and SSCI to represent internationally indexed English-language scholarship. These indices are not fully equivalent in coverage; therefore, we treat them as proxies for two language-based corpora rather than directly comparable country datasets. To enhance comparability, we applied harmonized search strings, inclusion/exclusion criteria, and time boundaries across both corpora. The data collection process ensures a comprehensive selection of literature in both languages, enabling a robust analysis of the research topic in the field of international rules of cyberspace governance.
3. Results and Discussion
3.4. Analysis of Research Developments and Basic Knowledge
In the mapping of knowledge domains, the analysis of research developments and basic knowledge is conducted through co-citation analysis of the fundamental knowledge, which is a collection of co-cited literature. Co-citation analysis involves examining the relationship between two papers when they appear together in the reference list of a third cited paper. This analysis allows for the exploration of the research developments through the cited literature. The node type used in the analysis is “reference”.
3.4.1. WoS Literature
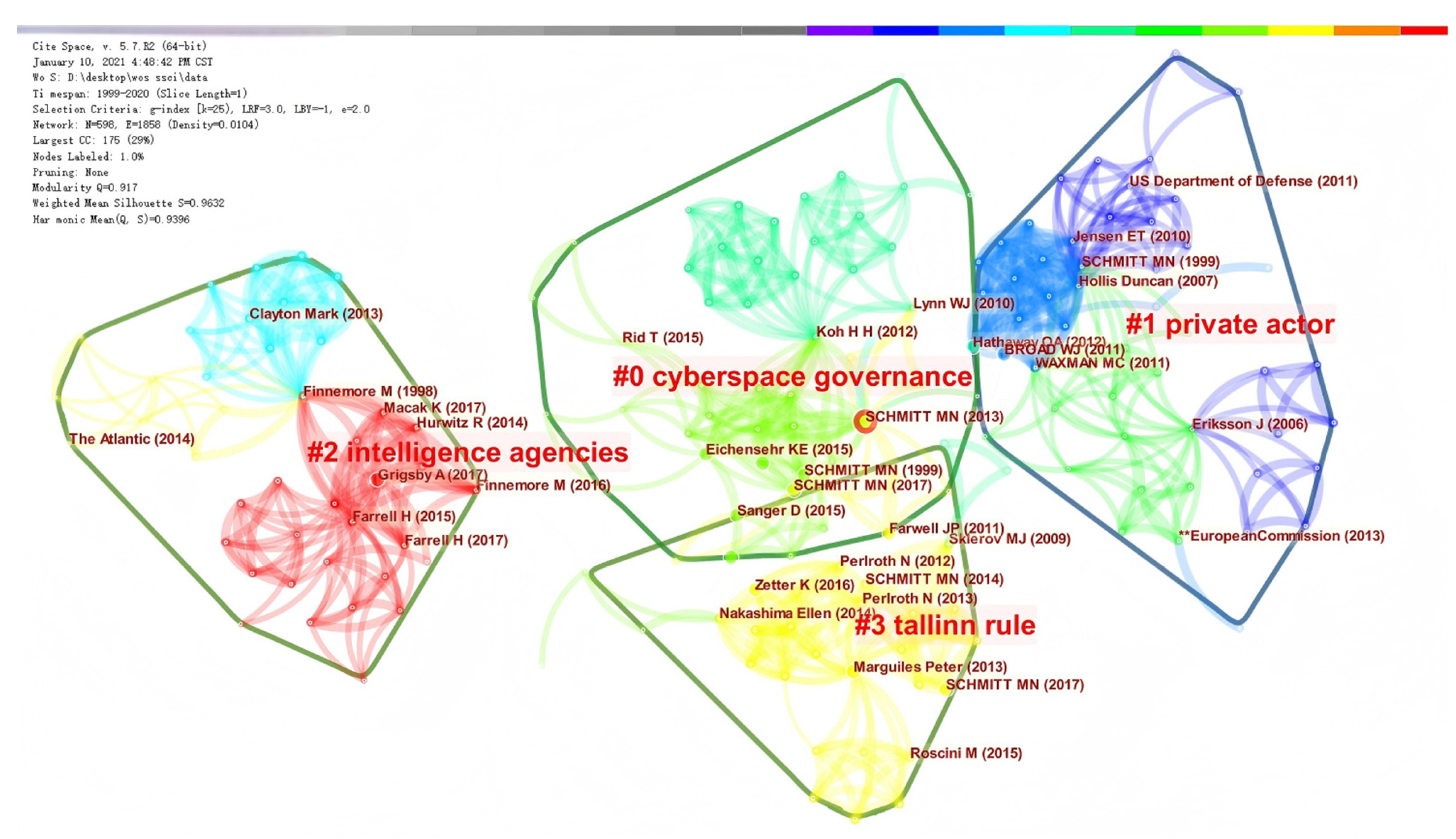
Based on the SSCI-indexed English-language literature in Web of Science, the co-citation network shows a Modularity Q of 0.917, indicating a well-partitioned structure with clear community boundaries, and a mean silhouette of 0.9632, suggesting high cluster validity. Using the log-likelihood ratio (LLR) to derive cluster labels, four major thematic groupings emerge: cyberspace governance, private actors, intelligence agencies, and the
Tallinn Manual. As visualized in
Figure 4, citations are both concentrated within clusters and cross-cutting across them, reflecting a tightly knit yet interdisciplinary knowledge base. Within this network, the
2013 and 2017 versions of the Tallinn Manual collectively functions as a central reference point rather than an exclusive corpus: it crystallizes earlier doctrinal debates in international law and provides a widely shared touchstone for subsequent scholarship.
Notably, works in law, national security, and political science occupy the highest ranks by citation and betweenness (intermediary) centrality, underscoring their bridging role across thematic communities. Key authors include Schmitt, Waxman, Hathaway et al., and the Tallinn Manual Project. Collectively, these references demonstrate that the field’s foundational knowledge is anchored in legal scholarship; in this sense, English-language research on international rules in cyberspace originates from—and continues to be structured by—the international law tradition.
Table 3 reports the top ten references by betweenness centrality and citation counts.
The analysis reveals that the largest cluster of research in this field is related to international law. Research developments, as indicated by the cited articles, are concentrated in the years 2015 to 2018 and revolve around the discussion of the status and role of international law in the governance of cyberspace. One of the key themes explored is whether it is possible to establish a model of cyber governance that emphasizes state control and whether states can exercise sovereignty over cyberspace.
It is argued that, apart from China and Russia, most countries are hesitant to participate in the formulation of relevant international law in cyberspace. As a result, non-state-driven norms, such as the
Tallinn Manual, have become the mainstay of governance. However, these norms lack legal effect, creating a power vacuum that requires urgent regulation [
5].
While the
Tallinn Manual aims to establish practical international law in the realm of cyberspace, subsequent practices have led to various conceptual interpretations of the agreement over time. This exposes the divergence between states’ national security interests and the treaty itself [
6].
Huang Zhixiong et al. [
7] provide a general summary of five controversial areas of legal governance in cyberspace and argue for the need to find the preferred method of developing international law. They suggest that the overall convergence of interests between competing models of cyberspace governance, such as shared responsibility and cooperation, will be mutually beneficial [
7].
The second cluster focuses on the nature of cyber-attacks and the legal liability of private actors involved in cyber-attacks. The cited literature in this cluster, primarily concentrated between 2012 and 2013, highlights the need for the regulation of cyber-attacks under international law.
Currently, the primary normative systems governing cyber-attacks are the laws of war, international treaties, and domestic criminal laws. However, the laws of war offer guidance only for a small subset of cyber-attacks that qualify as armed attacks or occur in the context of ongoing armed conflict [
8]. The laws of war also provide limited clarity on the legality of cyber-attacks themselves and when they rise to the level of acts of war justifying a resort to force. Therefore, there is a need to address cyber-attacks within the framework of the laws of war [
9]. It is argued that cyber-attacks that do not qualify as armed attacks, such as those targeting the intellectual property rights of other countries, should be considered “transnational damage” and dealt with using traditional international legal principles [
10]. To address these issues, establishing international cooperation, agreeing on definitions of cyber-attacks, cybercrime, and cyber warfare, strengthening the basis for information sharing, evidence collection, and criminal prosecution of those involved in cyber-attacks, and establishing new international laws pertaining to cyber-attacks are crucial steps [
8].
Overall, this cluster highlights the need to regulate cyber-attacks under international law, beyond the scope of armed conflicts, and emphasizes the importance of international cooperation in addressing the challenges posed by cyber-attacks.
The third cluster focuses on international rule-making subjects and roles in the governance of cyberspace. The main concerns in this cluster revolve around the competition among various actors in the international cyberspace governance rule-making process, the roles they play in establishing international rules, and the issue of accountability. The research developments in this area, as indicated by the citing literature, mainly emerged in 2020.
Given that existing UN-led negotiation processes are unlikely to achieve diplomatic breakthroughs, more and more states are considering non-state actors as duty bearers, and state-sponsored actors are being held responsible for cybersecurity threats [
11]. National security and intelligence agencies also play a significant role in cybersecurity and contribute to the development of regulatory policies, emphasizing the importance of normative practices at the micro level [
12].
The fourth cluster focuses on research related to the Tallinn rules and state responsibility in legal science. The research developments in this field are concentrated in 2018. While the research content overlaps with the first cluster, the emphasis is on cyber-attacks and attribution analysis. Some scholars argue that states should be held responsible for the damage occurring in cyberspace and liable for illegal acts [
13]. However, the technical and legal challenges of attribution in cyberspace pose obstacles to the effective functioning of the state responsibility framework in international law. The principle of due diligence is suggested as a better and more appropriate standard for attribution in cyberspace [
14].
3.4.2. CSSCI Literature
The analysis of CSSCI literature resulted in the identification of five significant co-citation clusters: Internet governance #0, Internet governance #1, international relations norms #2, strategic stability and misperceptions #3. Chinese literature research is concentrated in the field of Internet governance, with a greater focus on the perspectives of political science and international relations.
Both the first and second clusters emphasize Internet governance, but they have different emphases and theoretical bases. Cluster #0 explores macro-concepts related to Internet governance, while Cluster #1 focuses on governance paths and solutions for specific problems. Cluster #0 emerged earlier and investigates topics such as network sovereignty, global internet governance, public goods, and China’s path. Cluster #1, on the other hand, examines specific governance solutions and paths, including ecological governance, self-organizing paths, the Digital Silk Road, the “Third Way,” the Cyber Community of Destiny, and Sino-European cooperation. The research in Cluster #1 revolves around how China should participate in existing Internet governance issues, such as Internet regulation, space activities, low-intensity military operations, digital Silk Road, and Sino-European cooperation on cyberspace governance.
Cluster #2 focuses on topics such as the value identity of governance processes, current dilemmas, conceptual governance, conceptual distribution, and the Chinese solution. Cluster #4 delves into competition over the path of cyberspace governance in terms of strategic stability, sustainable development, the relationship between major powers, and international security architecture, with a greater emphasis on macro strategies.
Scholars like Chuanying Lu, Zhou, Thomas Reid, Karsten Geier, Robert Jervis, and Thomas Renard have made significant contributions to this field, particularly in exploring the barriers to strategic cooperation and the problem of misperceptions in Sino-European network governance. Their research has laid the foundation for further studies in this area.
3.5. Structural Hole Analysis
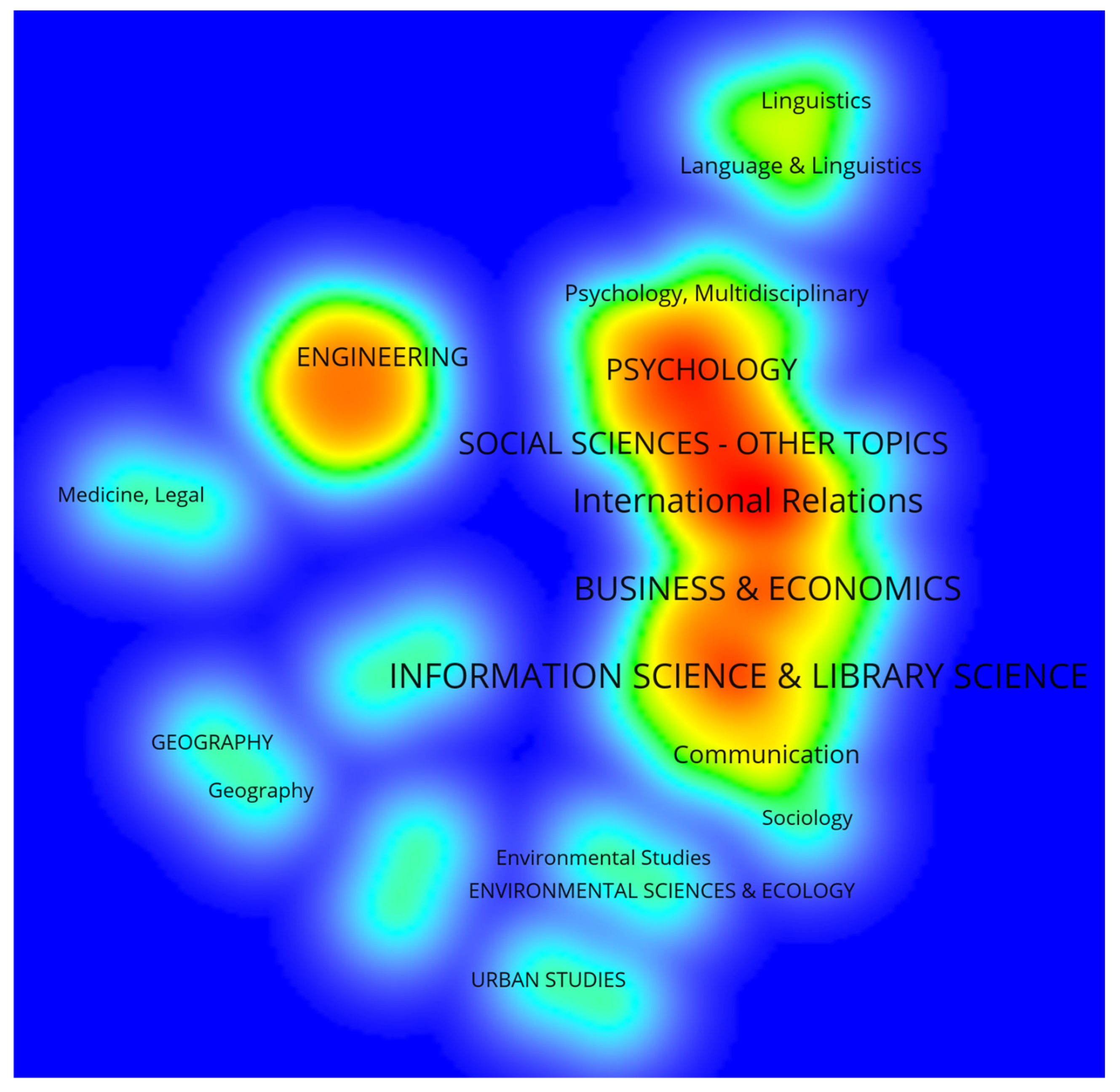
The communication discipline in CSSCI journals has a higher focus on international Internet governance. This is different from the WoS journals in the communication disciplines.
However, there is a clear structural hole in the minimal degree of connection between the research of communication scholars and international law, international relations, and political governance. The two clusters on the right side of the figure above are a series of articles by Hong Yu of Zhejiang University, focusing on the perspective of state and communication (the red connecting line, which also represents the more recent tangent of the emergence of this research). There are also a series of review articles about the research of the journalism and communication discipline on new media (Weibo and WeChat), which mainly focus on the years 2012–2014.
We manually screened and analyzed 37 Chinese papers in an independent CiteSpace project. The variable for this analysis was set at g-index (k = 25), and the keywords of the papers and the co-cited literature were analyzed. The results showed the following categories:
Yan Li and Runxi Zeng studied the conflict between the U.S. and China since the outbreak of the COVID-19 epidemic. They argue that technology and ideology are the two main factors affecting the change in the international Internet governance system [
15]. The epidemic has led the U.S. to strengthen its control over the international Internet, and the Internet governance system will not change in the direction China expects in the short term. Hong Yu also examines the issue of Internet governance from both technical and national perspectives. They argue that the national restoration of “people-centered” and “a community with a shared future for mankind” as the value standard and action standard is to serve the construction and improvement of socialism with Chinese characteristics in the global context [
16].
There are four main types of actors involved in the formulation of international rules in cyberspace: states involved in multilateral diplomatic norms, expert groups, industry organizations, and multi-stakeholders. Jun Zou suggests that “multi-stakeholderism” represents the dominant direction of global Internet governance [
17]. Jie Gu proposes to break the logic of dichotomy and reshape the theoretical framework of Internet governance from the perspective of new institutionalism [
18]. Lina Zhou introduces the trends of Internet content governance in the UK, highlighting the expansion of legislative governance and the end of the era of self-regulation [
19].
Another hot topic focuses on the issue of discourse in international cyberspace governance. Weidong Yang analyzes the “dual power” game from the perspective of the field of discourse and rulemaking in cyberspace [
20]. Xiaoyan Liu et al. explain the discourse power game from the perspective of international cybersecurity. They argue that, as the military dimension in the concept of cybersecurity is the most controversial and the most significant area of conflict of interest among countries, the rules and discourse proposed by the United States and other cyber-first countries should be carefully identified and responded to. They suggest that it is necessary for China to enhance its discursive power by constructing an “international cyber conflict” regulation system and emphasizing the main position of the United Nations in the creation of international rules on cybercrime [
21].
In general, related research in Chinese, especially in the field of communication, involves broader discussions and lacks examination of details. There are more circumstantial examinations of new communication governance challenges brought about by cyberspace, but there is a lack of connection with theories related to cyberspace governance. Additionally, there is a lack of segmented research on new issues brought about by new technologies in the communication dimension, involving personal privacy, user data, blockchain, etc. Middle-range theoretical research is also rare.
4. Summary and Conclusions
Through a comparison and analysis of the literature in the WoS-SSCI database and CSSCI journals, it is found that research on international rules in cyberspace started earlier in English and has a higher degree of literature coupling compared to Chinese research. Chinese scholars have shown significant attention and momentum in later stages, but the mainstream theoretical basis and cited literature in this field are still dominated by British and American studies, indicating a larger academic influence and impact from those countries.
The knowledge base in this field consists mainly of articles, institutional reports, and media reports, with relatively few books. The Tallinn Manual is the most widely cited book in this field. In the CSSCI journals, English research is often used as the theoretical basis or source of viewpoints, with many citations of foreign works on international relations and international political science. Notable works include “Network and State: The Global Politics of Internet Governance”, “Governance without Government”, “Code 2.0: Law in Cyberspace”, and “Global Game of Internet Governance”, some of which were published as early as 1992. The challenge for Chinese scholars is to synchronize domestic research with English research in terms of basic knowledge and even surpass British and American research to establish theoretical innovation.
Over the past five years, both English and Chinese literature have seen a relatively high publication trend, but research developments and hotspots differ. While cyberspace sovereignty and cyberspace governance from a globalization perspective are common topics, the research of Chinese scholars is more focused on policy issues and research phases. English literature has a clear theoretical foundation, maintains continuous and in-depth focus on basic topics, and takes a broader perspective, with distinct research areas in law and international relations. Research on cyberspace law and cyber warfare is particularly well developed. English studies also address issues such as inequality in cyberspace and cybercrime in developing countries, broadening the existing research ideas.
Notably, the focus on international rules in cyberspace within the field of communication is a characteristic of Chinese research, providing new perspectives and opportunities for interdisciplinary crossover. However, attention should be given to the structural gap between this existing research and mainstream research on cyberspace governance, both domestically and internationally. This is reflected in the selection of research literature in related fields. Greater attention should be paid to new progress in related English research to establish a new direction for Chinese communication research, moving beyond macro issues to analyze international cyberspace governance.
Overall, the academic concerns of Chinese scholars regarding international rules in cyberspace receive support at the national level, and Chinese scholars are also visible in English journals. For example, Zhixiong Huang has published numerous papers in both Chinese and English and has been involved in the compilation of the Tallinn Manual 2.0. However, to increase the citation frequency and centrality of Chinese scholars’ articles and better introduce national-level advocates to the international community through academic discussions, it is necessary to carefully examine the differences between the current hotspots and internationally recognized topics. This will involve building an academic community studying international cyberspace governance rules and enhancing theoretical innovations. As a developing country, China’s attempts and efforts to break through the national security paradigm require global attention and involvement from the academic community in the form of discussions on these issues. This study highlights two more specific directions: (1) bridging the structural gap between communication studies and normative international law by fostering joint research programs, and (2) encouraging Chinese scholarship to strengthen cross-lingual dialog by engaging more directly with international theoretical debates.