AI-Based Solutions for Security and Resource Optimization in IoT Environments: A Systematic Review
Abstract
1. Introduction
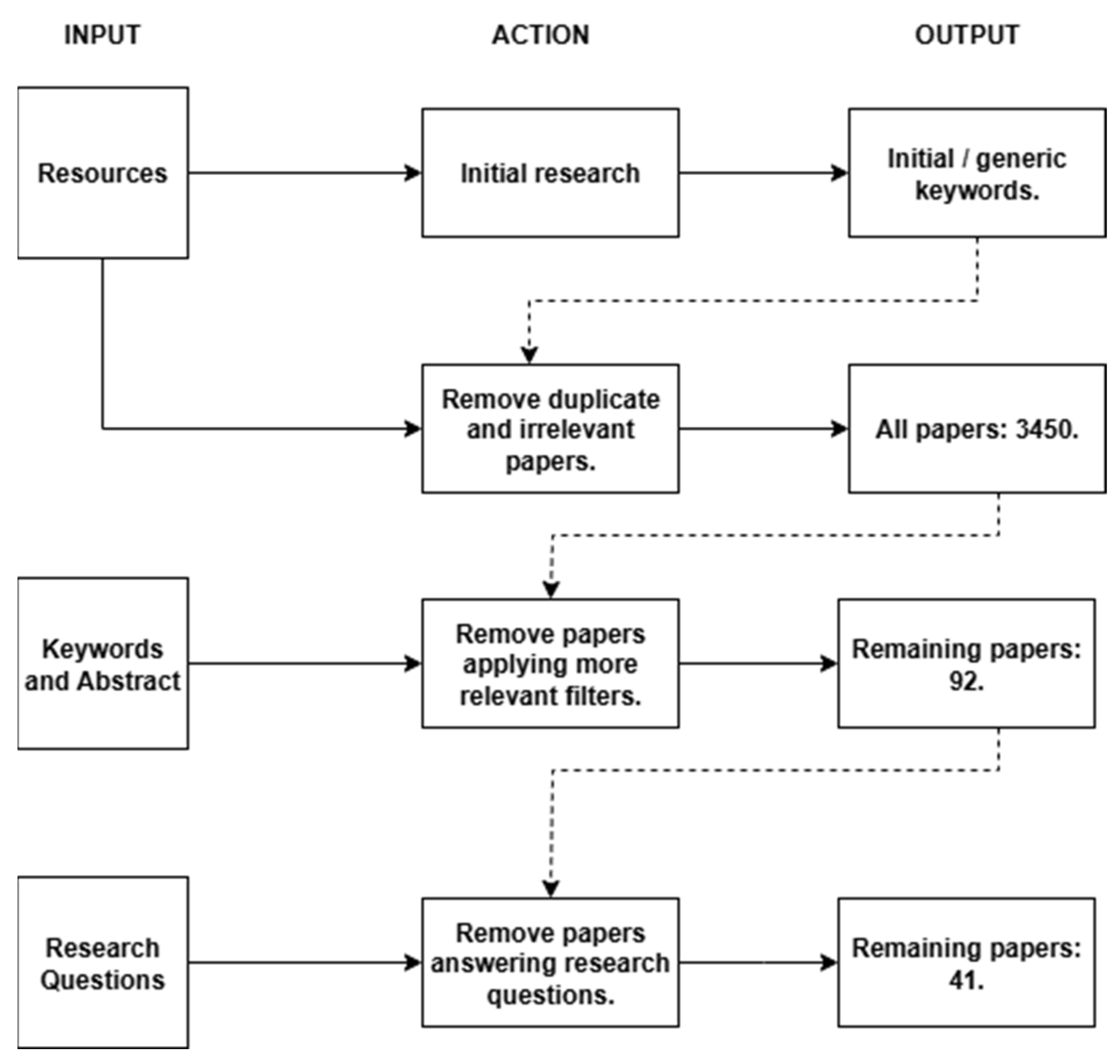
2. Research Methodology
- RQ1: Does the article/paper propose or evaluate techniques and algorithms applied (or that could be applied) to IoT systems?
- RQ2: Does the article/paper address scalability or real-time processing in AI/IoT environments?
- RQ3: Is the solution integrated into a specific AI/IoT architecture?
- RQ4: Does the solution evaluate privacy, security, or ethical aspects?
- RQ5: Does the article/paper provide experimental validation?
3. AI/ML Techniques in IoT Systems
3.1. Supervised and Unsupervised Learning–How to Prevent an Attack?
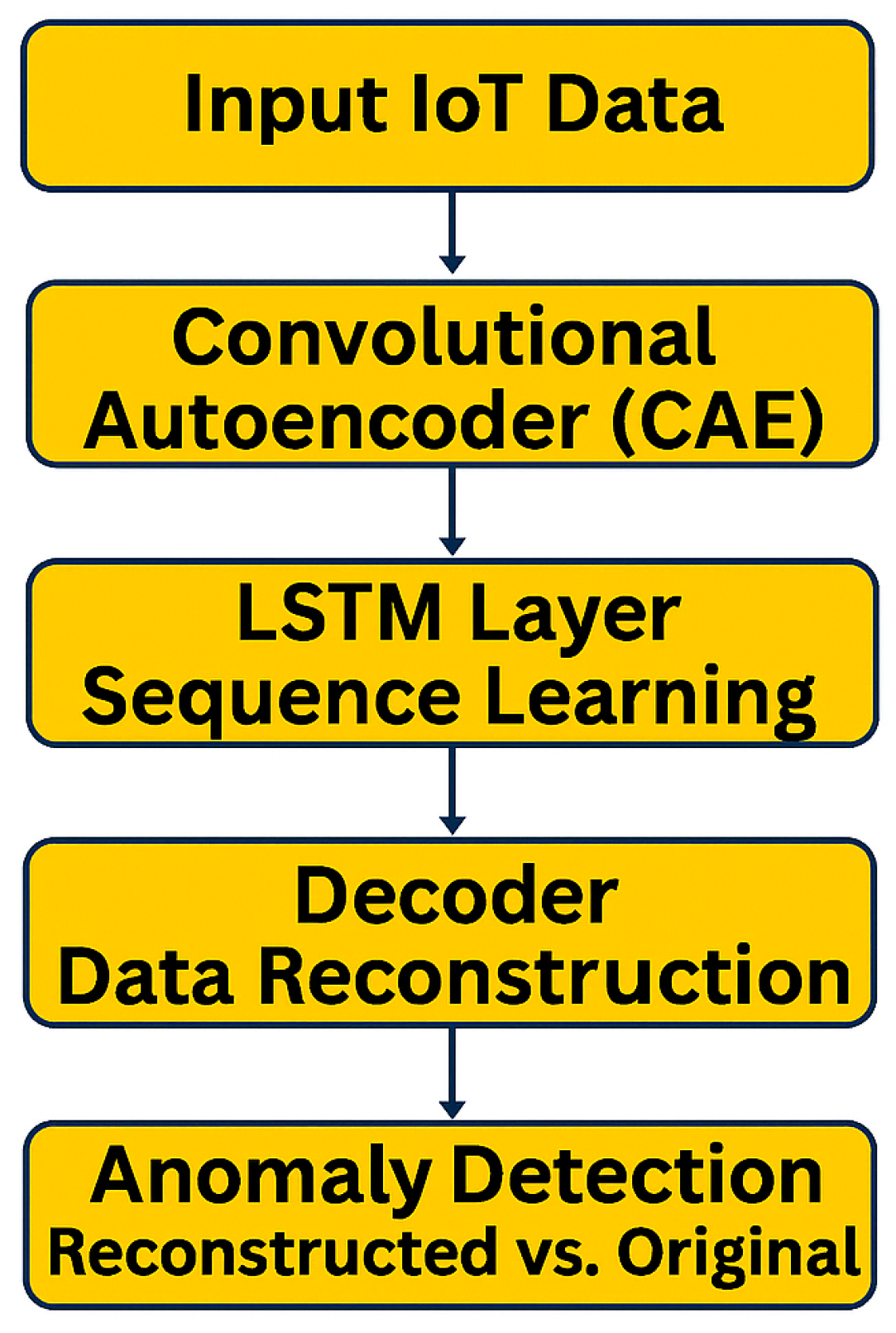
3.2. Anomaly Detection
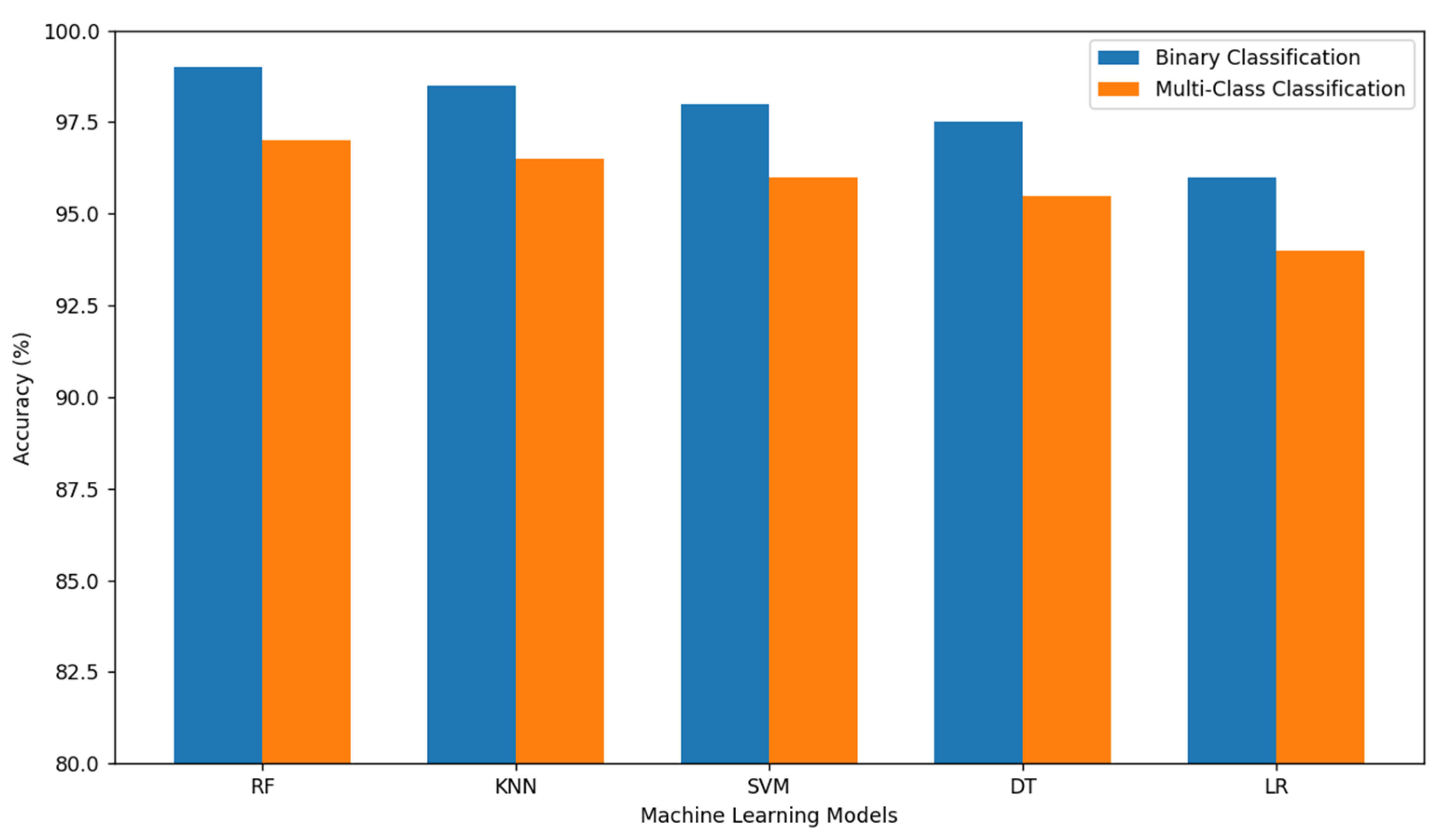
3.3. A More Comprehensive and Reliable Comparison of AI/ML Techniques
4. Internet of Things and Its Use Cases
4.1. Privacy and Security
4.2. Waste Reduction
4.3. A More Comprehensive and Reliable Comparison of IoT Use Cases
5. Final Discussion and Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Krishnan, S.K.; Nagaprakash, T.; Karthikeyan, R. Systematic Literature Review of Product Feature Prioritization Frameworks in Startups Building Digital Products Using PRISMA. In Proceedings of the IEEE 11th Region 10 Humanitarian Technology Conference (R10-HTC), Rajkot, India, 16–18 October 2023. [Google Scholar]
- Gautam, A.; Singh, S.; Arora, K.; Kaur, A. A Comparative Analysis of Supervised, Semi Supervised and Unsupervised Object Detection Techniques in Video Surveillance. In Proceedings of the 7th International Conference on Signal Processing, Computing and Control (ISPCC), Solan, India, 6–8 March 2025. [Google Scholar]
- Dalal, K.R. Analyzing the Role of Supervised and Unsupervised Machine Learning in IoT. In Proceedings of the International Conference on Electronics and Sustainable Communication Systems (ICESC), Coimbatore, India, 2–4 July 2020. [Google Scholar]
- Donoso-Daille, P.; Peesapati, V.; Smith, C.; Tavernier, K.; Tavernier, G. Classification of Partially Labelled Partial Discharge Datasets Using Semi-Supervised Learning. In Proceedings of the 10th International Conference on Condition Monitoring and Diagnosis (CMD), Gangneung, Republic of Korea, 20–24 October 2024. [Google Scholar]
- Lounis, K.; Zulkernine, M. Attacks and Defenses in Short-Range Wireless Technologies for IoT; IEEE: New York, NY, USA, 2020; pp. 8892–88932. [Google Scholar]
- Traynor, O. IoT Cybersecurity: Connecting the Dots. 2025. Available online: https://cybelangel.com/iot_cybersecurity/ (accessed on 8 May 2025).
- Abdel-Basset, M.; Moustafa, N.; Hawash, H. Deep Learning Approaches for Security Threats in IoT Environments; Wiley and Sons: Hoboken, NJ, USA, 2023; pp. 1–26. [Google Scholar]
- Vyas, M.; Vijayaganth, R.; Chandhok, J.; Srivastava, A.; Sethu, A.; Tiwari, M. Revolutionizing IoT Network Security with Deep Learning-Anomaly Detection Model. In Proceedings of the 4th International Conference on Electronics and Sustainable Communication Systems (ICESC-2023), Coimbatore, India, 6–8 July 2023. [Google Scholar]
- Ullah, I.; Mahmoud, Q.H. Design and Development of a Deep Learning-Based Model for Anomaly Detection in IoT Networks; IEEE: New York, NY, USA, 2021; pp. 103906–103926. [Google Scholar]
- Elsayed, M.A.; Russell, P.; Nandy, B.; Seddigh, N.; Zincir-Heywood, A.N. Anomaly Detection for IoT Networks: Empirical Study. In Proceedings of the IEEE Canadian Conference on Electrical and Computer Engineering (CCECE), Regina, SK, Canada, 24–27 September 2023. [Google Scholar]
- Kamaldeep, K.; Malik, M.; Dutta, M.; Granjal, J. IoT-Sentry: A Cross-Layer-Based Intrusion Detection System in Standardized Internet of Things. IEEE Sens. J. 2021, 21, 28066–28076. [Google Scholar] [CrossRef]
- Kandhro, I.A.; Al Enezi, S.M.; Ali, F.; Kehar, A.; Fatima, K.; Uddin, M.; Karuppayah, S. Detection of Real-Time Malicious Intrusions and Attacks in IoT Empowered Cybersecurity Infrastructures. IEEE Access 2023, 11, 9136–9148. Available online: https://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=10023499 (accessed on 30 June 2025).
- Xue, B.; Zhao, H.; Yao, W. Deep Transfer Learning for IoT Intrusion Detection. In Proceedings of the IEEE 3rd International Conference on Computing, Networks and Internet of Thing, Qingdao, China, 20–22 May 2022. [Google Scholar]
- Ruzafa-Alcázar, P.; Fernandez-Saura, P.; Mármol Campos, E.; González Vidal, A.; Hernández-Ramos, J.L.; Bernal Bernabe, J.; Skarmeta, A.F. Intrusion Detection Based on Privacy-Preserving Federated Learning for the Industrial IoT; IEEE Transactions on Industrial Informatics: New York, NY, USA, 2022. [Google Scholar]
- Anupama, A.; Prasad, R.R. Hybrid Intrusion Detection System. In Proceedings of the International Conference on Quantum Technologies, Communications, Computing, Hardware and Embedded Systems Security, Kottayam, India, 15–16 September 2023. [Google Scholar]
- Hairab, B.I.; Elsayed, M.S.; Jurcut, A.D.; Azer, M.A. Anomaly Detection Based on CNN and Regularization Techniques Against Zero-Day Attacks in IoT Networks; IEEE Access: New York, NY, USA, 2022; Volume 10. [Google Scholar]
- Park, C.; Lee, J.; Kim, Y.; Park, J.-G.; Kim, H.; Hong, D. An Enhanced AI-Based IDS Using GANs; IEEE Internet of Things Journal: New York, NY, USA, 2022; Volume 10. [Google Scholar]
- Said, R.B.; Sabir, Z.; Askerzade, I. CNN-BiLSTM: A Hybrid Deep Learning Approach for Network Intrusion Detection System in Software-Defined Networking with Hybrid Feature Selection; IEEE Access: New York, NY, USA, 2023; Volume 11. [Google Scholar]
- Santos, R.R.D.; Viegas, E.K.; Santin, A.O. A Reminiscent Intrusion Detection Model Based on Deep Autoencoders and Transfer Learning. In Proceedings of the IEEE Global Communications Conference, Madrid, Spain, 7–11 December 2021. [Google Scholar]
- da Cruz, M.A.A.; Abbade, L.R.; Lorenz, P.; Mafra, S.B.; Rodrigues, J.J.P.C. Detecting Compromised IoT Devices Through XGBoost; IEEE Transactions on Intelligent Transportation Systems: New York, NY, USA, 2022. [Google Scholar]
- Hossain, M.D.; Ochiai, H.; Fall, D.; Kadobayashi, Y. LSTM-based Network Attack Detection: Performance Comparison by Hyper-parameter Values Tuning. In Proceedings of the IEEE International Conference on Cyber Security and Cloud Computing (CSCloud), New York, NY, USA, 1–3 August 2020. [Google Scholar]
- Wang, W.; Du, X.; Wang, N. Cloud IDS Using Feature Selection and SVM; IEEE Access: New York, NY, USA, 2023; Volume 7. [Google Scholar]
- Gazdar, T.; Gazdar, T.; Alqarni, H.; Bakhsh, A.; Aljidaani, M.; Alzahrani, M. A 2-Layers Deep learning Based Intrusion Detection System for Smart Home. In Proceedings of the 5th IEEE National Computing Colleges Conference, Makkah, Saudi Arabia, 17–18 December 2022. [Google Scholar]
- Panthakkan, A.; Anzar, S.M.; Mansoor, W. Enhancing IoT Security: A Machine Learning Approach to Intrusion Detection System Evaluation. In Proceedings of the IEEE International Conference and Expo on Real Time Communications at IIT (RTC), Chicago, IL, USA, 2–5 October 2023. [Google Scholar]
- Rani, D.; Gill, N.S.; Gulia, P.; Arena, F.; Pau, G. Design of an Intrusion Detection Model for IoT-Enabled Smart Home; IEEE Access: New York, NY, USA, 2023; Volume 11. [Google Scholar]
- Zhang, K.; Qian, Y.; Motti, V.; Fung, V. A Study on the Privacy Concerns of the Internet of Things. In Proceedings of the 7th IEEE Cybersecurity in Networking Conference, Montreal, QC, Canada, 16–18 October 2023. [Google Scholar]
- Awad, A.I.; Abawajy, J. Security and Privacy in the Internet of Things: Architectures, Techniques and Applications; Wiley and Sons: Hoboken, NJ, USA, 2022; Chapters 1–12. [Google Scholar]
- Won, Y.-S.; Park, J.-Y.; Han, D.-G.; Bhasin, S. Practical Cold boot attack on IoT device––Case study on Raspberry Pi. In Proceedings of the IEEE International Symposium on the Physical and Failure Analysis of Integrated Circuits, Singapore, 20–23 July 2020. [Google Scholar]
- Lee, H.; Jiang, M.; Zhao, Q. FedAssist: Federated Learning in AI-Powered Prosthetics for Sustainable and Collaborative Learning. In Proceedings of the IEEE 46th Annual International Conference of the IEEE Engineering in Medicine and Biology Society, Orlando, FL, USA, 15–19 July 2024. [Google Scholar]
- Mukhtar, B.I.; Elsayed, M.S.; Jurcut, A.D.; Azer, M.A. IoT Vulnerabilities and Attacks: SILEX Malware Case Study. Symmetry 2023, 15, 1978. [Google Scholar] [CrossRef]
- Rahman, A.; Tan, S.W.; Asyhari, T.; Kurniawan, I.F.; Alenazi, M.J.F.; Uddi, M. IoT Enabled Intelligent Garbage Management System for Smart City: A Fairness Perspective; IEEE Access: New York, NY, USA, 2024; Volume 12. [Google Scholar]
- Sosunova, I.; Porras, J. IoT-Enabled Smart Waste Management Systems for Smart Cities: A Systematic Review; IEEE Access: New York, NY, USA, 2022; Volume 10. [Google Scholar]
- Zielonka, A.; Wozniak, M.; Garg, S.; Kaddoum, G.; Piran, M.J.; Muhammad, G. Smart Homes: How Much Will They Support Us? A Research on Recent Trends and Advances; IEEE Access: New York, NY, USA, 2021; Volume 9. [Google Scholar]
- Kayastha, S.; Upadhyaya, P. Design and Implementation of a Cost-Efficient Smart Home System with Enhanced Security and Energy Management. In Proceedings of the IEEE Artificial Intelligence for Transforming Business and Society, Kathmandu, Nepal, 5 November 2020. [Google Scholar]
- Bhatt, S.; Pham, T.K.; Gupta, M.; Benson, J.; Park, J.; Sandhu, R. Attribute-Based Access Control for AWS Internet of Things and Secure Industries of the Future. IEEE Access 2021, 9, 107200–107223. [Google Scholar] [CrossRef]
- Alzubi, A.A.; Galyna, K. Artificial Intelligence and Internet of Things for Sustainable Farming and Smart Agriculture. IEEE Access 2023, 11, 78686–78692. [Google Scholar] [CrossRef]
- Naji, H.K.; Goga, N.; Karkar, A.; Ali, H.; Falahi, M.; Marin, I.; Popa, R.-C. Software Implementation of a Smart Bracelet Prototype to Monitor Vital Signs, Locate, and Track COVID-19 Patients in Quarantine Zone. In Proceedings of the IEEE International Conference on Blockchain, Smart Healthcare and Emerging Technologies, Bucharest, Romania, 24–25 October 2022. [Google Scholar]
- Khalid, A.; Sakthivel, U.; Senthilkumaran, T.; Drieberg, M.; Sebastian, P.; Abd Aziz, A.; Hai, L. Extended Lifetime of IoT Applications using Energy Saving Schemes. In Proceedings of the IEEE International Conference on Future Trends in Smart Communities, Kuching, Sarawak, Malaysia, 1–2 December 2022. [Google Scholar]
- Pradeep, A. Influence of IoT Technologies in Education. In Proceedings of the 5th International Conference on Inventive Research in Computing Applications (ICIRCA), Coimbatore, India, 3–5 August 2023. [Google Scholar]
- Wang, M.; Kang, J.; Liu, W.; Zhang, F.; Su, J.; Yang, Z.; Fang, Z.; Li, X.; Yu, W. Design and Implementation of an Automatic Emulsion Dispensing and Remote Monitoring System Based on IoT Platform. IEEE Access 2023, 11, 102768–102780. [Google Scholar] [CrossRef]
- Hasan, H.H.; Bouloukakis, G.; Kattepur, A.; Conan, D.; Belaïd, D. Implementation of an Adaptive Flow Management Framework for IoT Spaces. In Proceedings of the IEEE/ACM 18th Symposium on Software Engineering for Adaptive and Self-Managing Systems (SEAMS), Melbourne, Australia, 15–16 May 2023. [Google Scholar]
- Miryahyaei, M.; Fartash, M.; Torkestani, J.A. Focal Causal Temporal Convolutional Neural Networks: Advancing IIoT Security with Efficient Detection of Rare Cyber-Attacks. Sensors 2024, 24, 6335. [Google Scholar] [CrossRef] [PubMed]
- Aldahaid, A.; Almars, A.M.; Alharbi, F.; Atlam, E.; Mahgoub, I. Machine Learning-Based Security Solutions for IoT Networks: A Comprehensive Survey. Sensors 2025, 25, 3341. [Google Scholar] [CrossRef] [PubMed]
- Nguyen, D.C.; Ding, M.; Pathirana, P.N.; Seneviratne, A.; Li, J.; Poor, H.V. Federated Learning: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2021, 23, 3. [Google Scholar] [CrossRef]
| Incident | Year | Description |
|---|---|---|
| Casino Thermostat Breach | 2017 | Data exfiltration via smart thermostat. |
| Ring Camera Hacks | 2019 | Unauthorized surveillance. |
| BrickerBot | 2017 | Permanent device damage. |
| Mirai Botnet | 2016 | DDoS via default credentials. |
| Paper | Techniques | Accuracy | Strengths | Weaknesses |
|---|---|---|---|---|
| IoT-Sentry: A Cross-Layer-Based Intrusion Detection System in Standardized Internet of Things (2021) [11] | Ensemble Learning Model. | 99%. | High accuracy, real-world dataset. | Limited to specific testbed. |
| Detection of Real-Time Malicious Intrusions and Attacks in IoT Empowered Cybersecurity Infrastructures (2023) [12] | MLP, RNN, DNN. | 95–97%. | High TNR and High DR. | High resource usage. |
| Deep Transfer Learning for IoT Intrusion Detection (2022) [13] | Autoencoder + CNN. | Could be > 99%. | High generalization, robust. | Requires pretraining. |
| Intrusion Detection Based on Privacy-Preserving Federated Learning for the Industrial IoT (2022) [14] | Federated Learning. | Typically, above 90%. | Data privacy, distributed training. | Communication overhead. |
| Hybrid Intrusion Detection System (2023) [15] | RF, RNN. | Typically, above 99%. | High TNR and effective detection. | Model complexity. |
| Anomaly Detection Based on CNN and Regularization Techniques Against Zero-Day Attacks in IoT Networks (2022) [16] | CNN + L1/L2 Regularization. | Up to 99.2%. | High detection rate. | Computationally expensive |
| An Enhanced AI-Based IDS Using GANs (2022) [17] | GAN, Autoencoder. | Up to 90% for Binary Classification. | Handles imbalanced data. | Training instability. |
| CNN-BiLSTM Hybrid IDS (2023) [18] | CNN, BiLSTM. | Up to 97% | Classifying temporal and spatial data. | Requires large training data. |
| A Reminiscent Intrusion Detection Model Based on Deep Autoencoders and Transfer Learnings (2021) [19] | Deep Autoencoder, Transfer Learning. | Up to 90%. | Low labeling and compute cost. | High false positives. |
| Detecting Compromised IoT Devices through XGBoost (2022) [20] | XGBoost. | Up to 93%. | High accuracy, fast inference. | Overfitting risk. |
| LSTM-based Network Attack Detection: Performance Comparison by Hyper-parameter Values Tuning(2020) [21] | LSTM. | DDoS attacks: 99.08%. | High accuracy for sequential attacks. | Training time and complexity. |
| Cloud IDS Using Feature Selection and SVM (2023) [22] | ECOFS + SVM. | Up to 95%. | Low computational cost. | Limited to classical ML. |
| A 2-Layers Deep learning Based Intrusion Detection System for Smart Home (2023) [23] | CNN, LSTM. | CNN-LSTM: Up to 90%. | Hybrid architecture. | Scalability. |
| Enhancing IoT Security: A Machine Learning Approach to Intrusion Detection System Evaluation (2023) [24] | DT, SVM, KNN, RF. | RF: 95.12%. | Comprehensive evaluation. | Scalability not addressed. |
| Design of an Intrusion Detection Model for IoT-Enabled Smart Home (2023) [25] | RF, SVM, KNN, NB. | RF: 98.99%. | High accuracy, comparative evaluation. | Scalability not addressed. |
| Paper | Use Case | Strength | Disadvantages |
|---|---|---|---|
| IoT-Enabled Smart Waste Management Systems for Smart Cities: A Systematic Review [32] | Smart waste management in urban environments. | Structured methodology, stakeholder centric. | Rapidly evolving field and focused on solid waste only. |
| Smart Homes: How Much Will They Support Us? A Research on Recent Trends and Advances [33] | Smart homes supporting daily life through IoT. | Covers multiple domains (healthcare, energy, security). | No specific implementation. |
| Design and Implementation of a Cost-Efficient Smart Home System with Enhanced Security and Energy Management [34] | Smart home system integrating IoT for security and energy management. | Practical implementation with hardware, software integration and cost efficiency. | Limited scalabulity for large homes or buildings. |
| Attribute-Based Access Control for AWS Internet of Things and Secure Industries of the Future [35] | Industrial IoT security using AWS IoT for smart manufacturing environments. | Real-world implementation using AWS IoT. | Focused on AWS ecosystem, limiting generalizability. |
| Artificial Intelligence and Internet of Things for Sustainable Farming and Smart Agriculture [36] | Smart agriculture using IoT and AI to improve resource efficiency and sustainability. | Real-world relevance with qualifiable benefits. | Lacks specific hardware/software deployment case studies. |
| Software Implementation of a Smart Bracelet Prototype to Monitor Vital Signs, Locate, and Track COVID-19 Patients in Quarantine Zone [37] | Wearable bracelet for real-time health monitoring and quarantine enforcement. | Fully implemented prototype with hardware and software. | Focused on COVID-19, limiting broader applicability. |
| Extended Lifetime of IoT Applications using Energy Saving Schemes [38] | Enhancing energy efficiency and device lifetime in IoT networks through adaptive strategies. | Focused on practical energy-saving techniques. | Limited to specific hardware and simulation environments and does not address security. |
| Influence of IoT Technologies in Education [39] | Explores the integration of IoT technologies into educational environments. | Timely and relevant topic. | Generalized discussion without specific educational levels or contexts. |
| Design and Implementation of an Automatic Emulsion Dispensing and Remote Monitoring System Based on IoT Platform [40] | Intelligent coal mine production: automatic emulsion dispensing and remote monitoring. | Real-world industrial deployment; High accuracy and reliability. | Focused on a specific industrial niche (coal mining). |
| Implementation of an Adaptive Flow Management Framework for IoT-Enhanced Spaces (PlanIoT) [41] | Adaptive flow management in IoT-enhanced smart environments. | Addresses real-time performance in IoT systems; Adaptable to various smart environments. | Focused on edge computing scenarios; Evaluation limited to specific testbeds. |
| Focal Causal Temporal Convolutional Neural Networks: Advancing IIoT Security with Efficient Detection of Rare Cyber-Attacks [42] | Intrusion detection in network traffic where rare cyber-attacks are difficult to detect due to imbalanced datasets. | Binary Hierarchical Architecture: Converts multi-class classification into sequential binary tasks, improving detection of minority classes. | While performance is strong in offline datasets, real-time deployment and adaptability are not tested. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alioanei, C.; Popescu, N. AI-Based Solutions for Security and Resource Optimization in IoT Environments: A Systematic Review. Information 2025, 16, 841. https://doi.org/10.3390/info16100841
Alioanei C, Popescu N. AI-Based Solutions for Security and Resource Optimization in IoT Environments: A Systematic Review. Information. 2025; 16(10):841. https://doi.org/10.3390/info16100841
Chicago/Turabian StyleAlioanei, Cosmin, and Nirvana Popescu. 2025. "AI-Based Solutions for Security and Resource Optimization in IoT Environments: A Systematic Review" Information 16, no. 10: 841. https://doi.org/10.3390/info16100841
APA StyleAlioanei, C., & Popescu, N. (2025). AI-Based Solutions for Security and Resource Optimization in IoT Environments: A Systematic Review. Information, 16(10), 841. https://doi.org/10.3390/info16100841






