Advancing Video Data Privacy Preservation in IoT Networks through Video Blockchain †
Abstract
1. Introduction
2. Materials and Methods
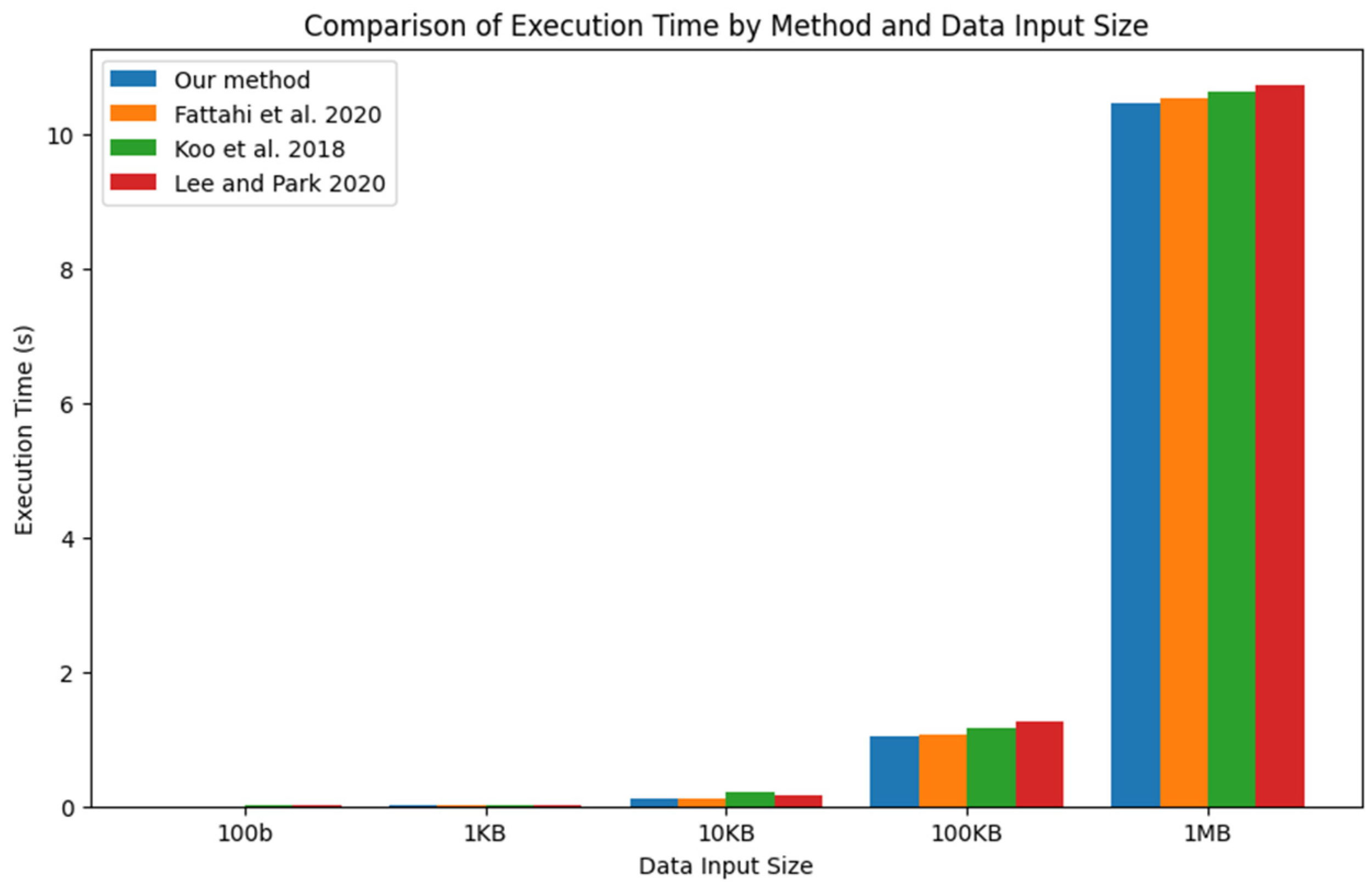
2.1. Evaluating the Performance of Existing Hashing Functions
- N: the total number of interactions
- : Start and end times for the ith iteration, respectively.
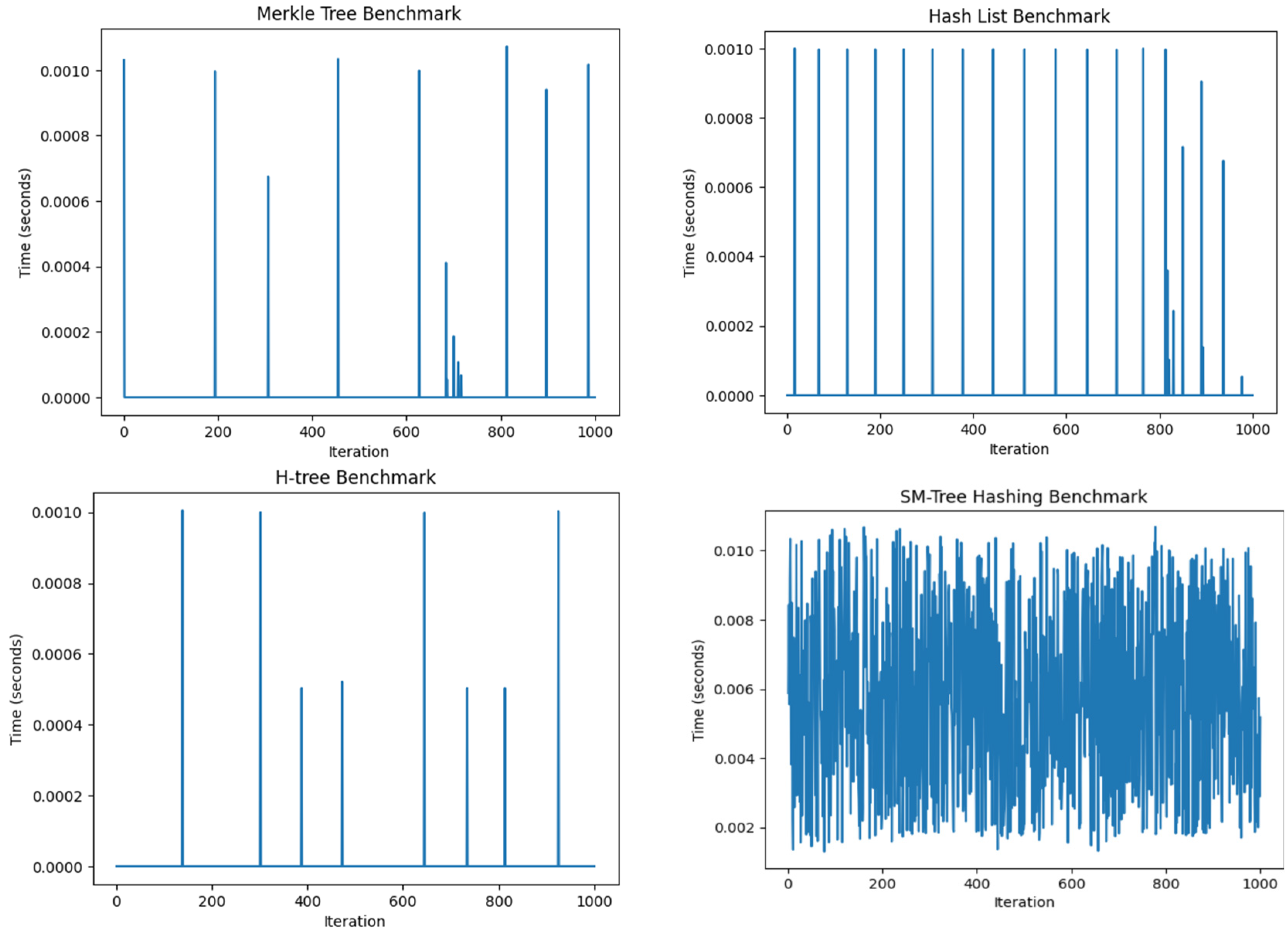
2.2. Evaluate the Best Data Structure for Video Blockchain
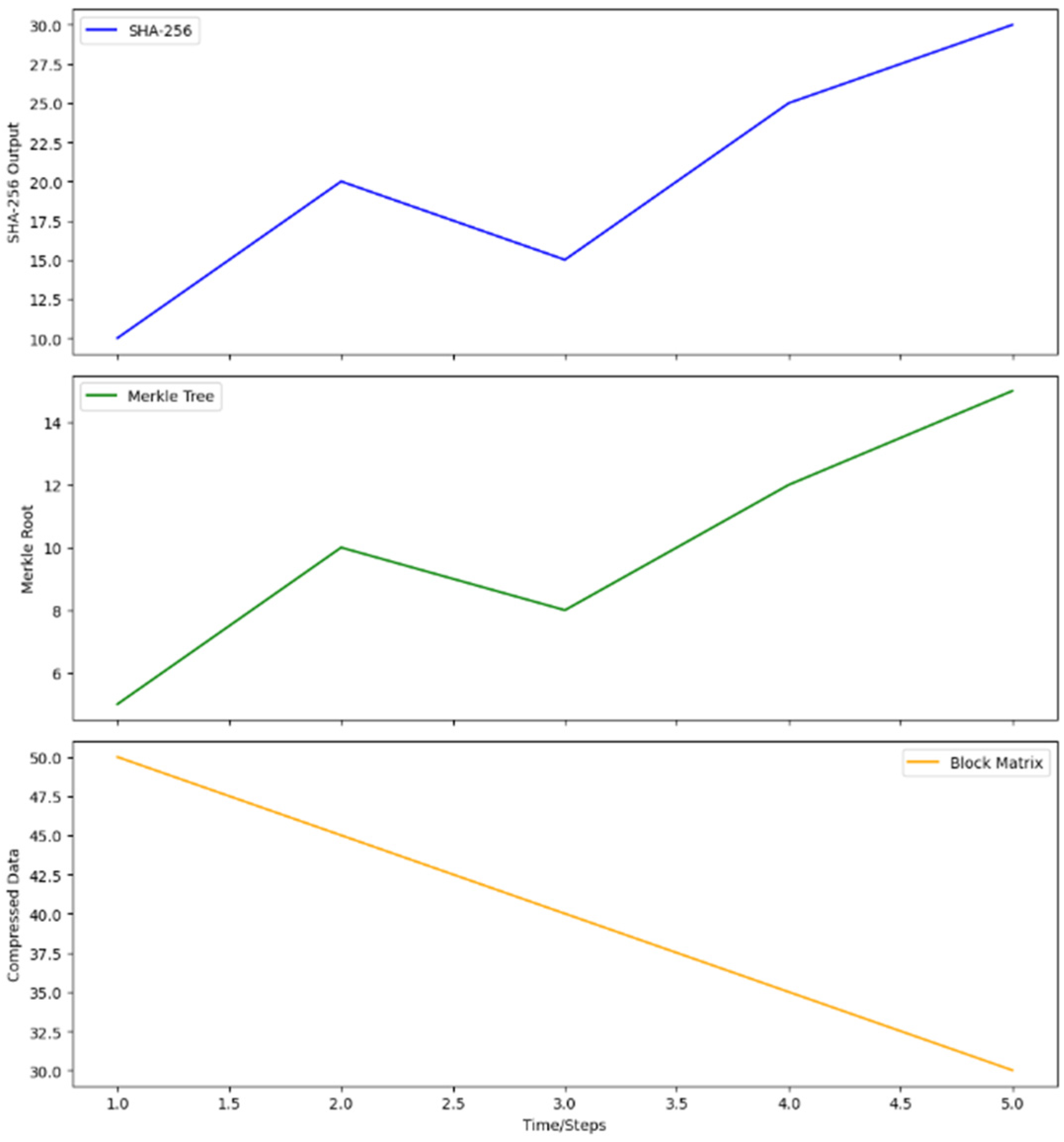
2.3. The Integration of Video Blockchain Technology into IoT Networks
| Algorithm 1: Block Matrix |
| Input: A video file consisting of frames. (1) Divide each frame into uniform blocks of 16 × 16 pixels. (2) Arrange the blocks from each frame into a matrix format, with rows indicating blocks and columns denoting frames. (3) Apply compression techniques (e.g., JPEG) to each block for data size reduction. (4) Store the resulting compressed block matrix in a binary format. (5) To retrieve a specific frame, load the compressed matrix and select the appropriate column of blocks. (6) To access a particular block within a frame, locate and decompress the corresponding row from the matrix. |
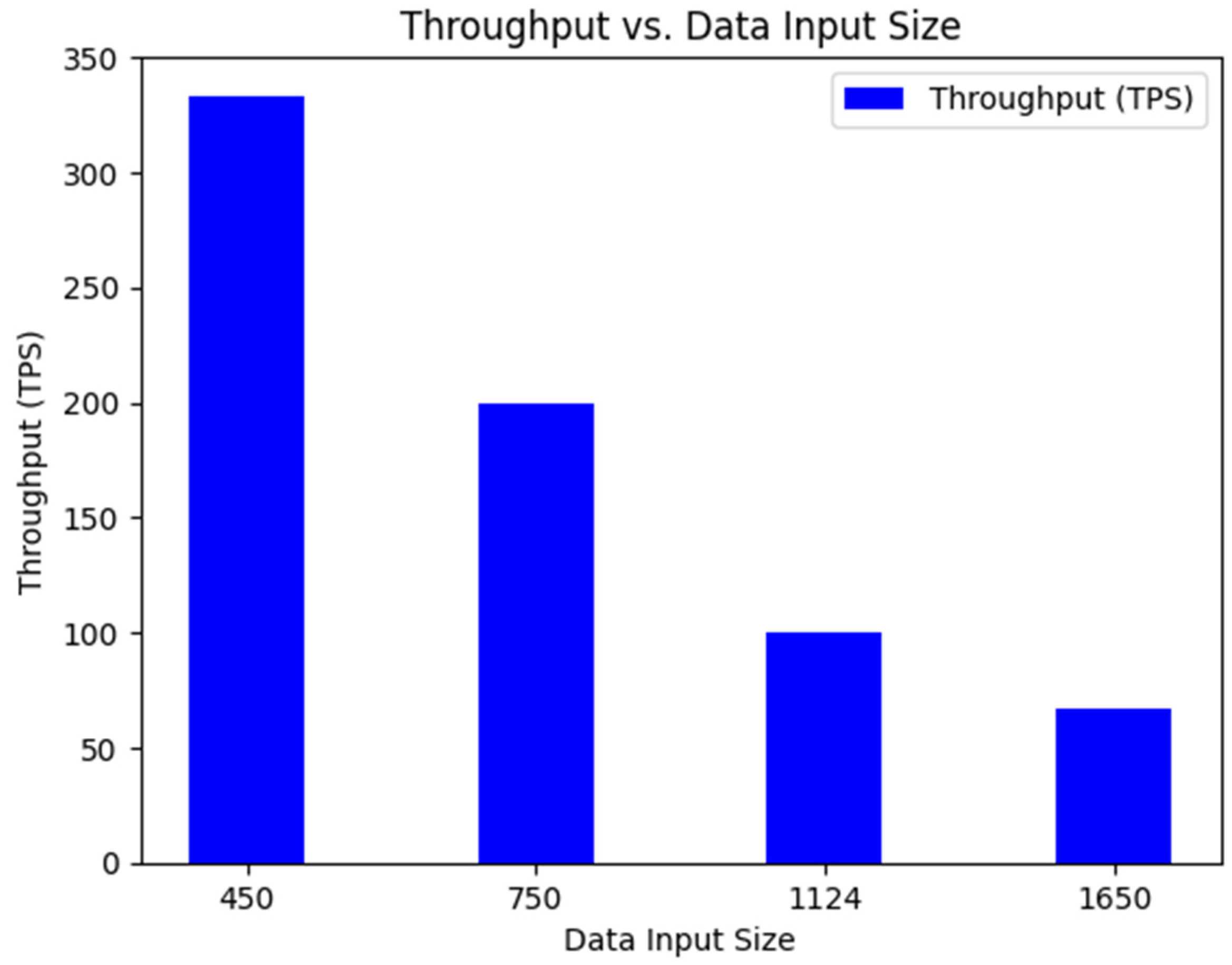
3. Results Analysis and Discussion
4. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Aldairi, A.; Tawalbeh, L. Cyber security attacks on smart cities and associated mobile technologies. Procedia Comput. Sci. 2017, 109, 1086–1091. [Google Scholar] [CrossRef]
- Alketbi, A.; Nasir, Q.; Abu Talib, M. Novel blockchain reference model for government services: Dubai government case study. Int. J. Syst. Assur. Eng. Manag. 2020, 11, 1170–1191. [Google Scholar] [CrossRef]
- Gedara, K.M.; Nguyen, M.; Yan, W.Q. Enhancing privacy protection in intelligent surveillance: Video blockchain solutions. In Blockchain and Applications, 5th International Congress; Machado, J.M., Prieto, J., Vieira, P., Peixoto, H., Abelha, A., Arroyo, D., Vigneri, L., Eds.; BLOCKCHAIN 2023. Lecture Notes in Networks and Systems; Springer: Cham, Switzerland, 2023; Volume 778. [Google Scholar] [CrossRef]
- Gedara, K.M.; Nguyen, M.; Yan, W.Q. Visual Blockchain for Intelligent Surveillance in a Smart City; IGI Global: Hershey, PA, USA, 2022; pp. 210–222. [Google Scholar] [CrossRef]
- Moolikagedara, K.; Nguyen, M.; Yan, W.Q.; Li, X.J. Video Blockchain: A decentralized approach for secure and sustainable networks with distributed video footage from vehicle-mounted cameras in smart cities. Electronics 2023, 12, 3621. [Google Scholar] [CrossRef]
- Hu, R.; Yan, W.Q. Design and implementation of visual blockchain with Merkle tree. In Handbook of Research on Multimedia Cyber Security; IGI Global: Hershey, PA, USA, 2020; pp. 282–295. [Google Scholar]
- Shu, Y.; Yu, J.; Yan, W.Q. Blockchain for Security of a Cloud-Based Online Auction System; IGI Global: Hershey, PA, USA, 2019; pp. 189–210. [Google Scholar]
- Fu, J.; Qiao, S.; Huang, Y.; Si, X.; Li, B.; Yuan, C. A Study on the Optimization of Blockchain Hashing Algorithm Based on PRCA. Secur. Commun. Netw. 2020, 2020, 8876317. [Google Scholar] [CrossRef]
- Priyadharshini, K.; Canessane, R.A. Blockchain-Based Security Algorithm on IoT Framework for Shielded Communication in Smart Cities. In Proceedings of the 3rd International Conference on Intelligent Communication Technologies and Virtual Mobile Networks, ICICV 2021, Tirunelveli, India, 4–6 February 2021; pp. 320–327. [Google Scholar] [CrossRef]
- Lin, I.C.; Liao, T.C. A survey of blockchain security issues and challenges. Int. J. Netw. Secur. 2017, 19, 653–659. [Google Scholar] [CrossRef]
- Swaminathan, A.; Mao, Y.; Wu, M. Robust and secure image hashing. IEEE Trans. Inf. Forensics Secur. 2006, 1, 215–230. [Google Scholar] [CrossRef]
- Huang, J.-J. Consistent Fuzzy Analytic Hierarchy Process by Considering Fuzzy Input and Output Data. In Proceedings of the 2016 Joint 8th International Conference on Soft Computing and Intelligent Systems (SCIS) and 17th International Symposium on Advanced Intelligent Systems (ISIS), Sapporo, Japan, 25–28 August 2016. [Google Scholar] [CrossRef]
- Sayogo, D.S.; Najafabadi, M.M.; Tayi, G.K.; Pardo, T.A. Privacy, confidentiality, and security challenges for interoperable data platforms in supply chains. Public Adm. Inf. Technol. 2016, 26, 109–128. [Google Scholar] [CrossRef]
- Khan, P.W.; Byun, Y.C.; Park, N. A data verification system for cctv surveillance cameras using blockchain technology in smart cities. Electronics 2020, 9, 484. [Google Scholar] [CrossRef]
- George, R.V.; Harsh, H.O.; Ray, P.; Babu, A.K. Food quality traceability prototype for restaurants using blockchain and food quality data index. J. Clean Prod. 2019, 240, 118021. [Google Scholar] [CrossRef]
- Chen, J.; Ruan, Y.; Guo, L.; Lu, H. BCVehis: A Blockchain-based service prototype of vehicle history tracking for used-car trades in China. IEEE Access 2020, 8, 214842–214851. [Google Scholar] [CrossRef]
- Deepak, K.; Badiger, A.N.; Akshay, J.; Awomi, K.A.; Deepak, G.; Harish Kumar, N. Blockchain-Based Management of Video Surveillance Systems: A Survey. In Proceedings of the 2020 6th International Conference on Advanced Computing and Communication Systems, ICACCS 2020, Coimbatore, India, 6–7 March 2020; pp. 1256–1258. [Google Scholar] [CrossRef]
- Zajac, P. Ephemeral keys authenticated with merkle trees and their use in iot applications. Sensors 2021, 21, 2036. [Google Scholar] [CrossRef] [PubMed]
- Michelin, R.A.; Ahmed, N.; Kanhere, S.S.; Seneviratne, A.; Jha, S. Leveraging Lightweight Blockchain to Establish Data Integrity for Surveillance Cameras. In Proceedings of the IEEE International Conference on Blockchain and Cryptocurrency, ICBC 2020, Toronto, ON, Canada, 2–6 May 2020; pp. 3–5. [Google Scholar]
- Gergely, A.M.; Crainicu, B. Randadminsuite: A new privacy-enhancing solution for private blockchains. Procedia Manuf. 2020, 46, 562–569. [Google Scholar] [CrossRef]
- Fitwi, A.; Chen, Y. Secure and Privacy-Preserving Stored Surveillance Video Sharing Atop Permissioned Blockchain. In Proceedings of the 2021 International Conference on Computer Communications and Networks (ICCCN), Athens, Greece, 19–22 July 2021; pp. 1–8. [Google Scholar]
- Hasan, O.; Brunie, L.; Bertino, E. Privacy-Preserving reputation systems based on blockchain and other cryptographic building blocks: A survey. ACM Comput. Surv. (CSUR) 2023, 55, 1–37. [Google Scholar] [CrossRef]
- Du, J.; Jiang, C.; Gelenbe, E.; Xu, L.; Li, J.; Ren, Y. Distributed data privacy preservation in iot applications. IEEE Wirel. Commun. 2018, 25, 68–76. [Google Scholar] [CrossRef]
- Ali, M.S.; Dolui, K.; Antonelli, F. IoT data privacy via blockchains and IPFS. In ACM International Conference Proceeding Series; Association for Computing Machinery: New York, NY, USA, 2017. [Google Scholar]
- Loukil, F.; Ghedira-Guegan, C.; Boukadi, K.; Benharkat, A.N.; Benkhelifa, E. Data privacy based on iot device behavior control using blockchain. ACM Trans. Internet Technol. 2021, 21, 1–20. [Google Scholar] [CrossRef]
- Kalbo, N.; Mirsky, Y.; Shabtai, A.; Elovici, Y. The security of ip-based video surveillance systems. Sensors 2020, 20, 4806. [Google Scholar] [CrossRef] [PubMed]
- Zhu, G.; Ding, Y.; Cao, Y. The Effect of block-matrix interface of srm with high volumetric block proportion on its uniaxial compressive strength. Appl. Sci. 2023, 13, 3463. [Google Scholar] [CrossRef]
- Majdoubi, D.E.L.; El Bakkali, H.; Sadki, S. Towards Smart Blockchain-Based System for Privacy and Security in a Smart City Environment. In Proceedings of the 2020 5th International Conference on Cloud Computing and Artificial Intelligence: Technologies and Applications, CloudTech, Marrakesh, Morocco, 24–26 November 2020. [Google Scholar] [CrossRef]
- Drijvers, M.; Edalatnejad, K.; Ford, B.; Kiltz, E.; Loss, J.; Neven, G.; Stepanovs, I. On the Security of Two-Round Multi-Signatures. In Proceedings of the 2019 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 19–23 May 2019; pp. 1084–1101. [Google Scholar] [CrossRef]
- Anajemba, J.H.; Tang, Y.; Iwendi, C.; Ohwoekevwo, A.; Srivastava, G.; Jo, O. Realizing efficient security and privacy in IoT networks. Sensors 2020, 20, 2609. [Google Scholar] [CrossRef] [PubMed]
- Fattahi, S.M.; Makanju, A.; Milani Fard, A. SIMBA: An efficient simulator for blockchain applications. In Proceedings of the 50th Annual IEEE/IFIP International Conference on Dependable Systems and Networks: Supplemental Volume, DSN-S 2020, Valencia, Spain, 29 June–2 July 2020; pp. 51–52. [Google Scholar] [CrossRef]
- Koo, D.; Shin, Y.; Yun, J.; Hur, J. Improving security and reliability in Merkle tree-based online data authentication with leakage resilience. Appl. Sci. 2018, 8, 2532. [Google Scholar] [CrossRef]
- Lee, D.; Park, N. Blockchain based privacy preserving multimedia intelligent video surveillance using secure Merkle tree. Multimed. Tools Appl. 2020, 80, 34517–34534. [Google Scholar] [CrossRef]




| SHA256 | SHA3 | |
|---|---|---|
| SHA256 | 1 | 3 |
| SHA3 | 1/3 | 1 |
| Data Structure | Performance (s) | Norm. Performance | Weighted Norm. Perf. | Sep. from Best | Sep. from Worst | Relative Closeness | Rank |
|---|---|---|---|---|---|---|---|
| Merkle tree | 0.001500 | 0.402329 | 0.402329 | 0.159135 | 0.025899 | 0.139969 | 1 |
| Hash List | 0.001800 | 0.482795 | 0.482795 | 0.229808 | 0.006475 | 0.027403 | 2 |
| H-tree | 0.002000 | 0.536439 | 0.536439 | 0.284117 | 0.000719 | 0.002526 | 3 |
| SM-Tree | 0.002100 | 0.563261 | 0.563261 | 0.313430 | 0.000000 | 0.000000 | 4 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Moolikagedara, K.; Nguyen, M.; Yan, W.; Li, X. Advancing Video Data Privacy Preservation in IoT Networks through Video Blockchain. Information 2024, 15, 171. https://doi.org/10.3390/info15030171
Moolikagedara K, Nguyen M, Yan W, Li X. Advancing Video Data Privacy Preservation in IoT Networks through Video Blockchain. Information. 2024; 15(3):171. https://doi.org/10.3390/info15030171
Chicago/Turabian StyleMoolikagedara, Kasun, Minh Nguyen, Weiqi Yan, and Xuejun Li. 2024. "Advancing Video Data Privacy Preservation in IoT Networks through Video Blockchain" Information 15, no. 3: 171. https://doi.org/10.3390/info15030171
APA StyleMoolikagedara, K., Nguyen, M., Yan, W., & Li, X. (2024). Advancing Video Data Privacy Preservation in IoT Networks through Video Blockchain. Information, 15(3), 171. https://doi.org/10.3390/info15030171