Improving the Cybersecurity Awareness of Young Adults through a Game-Based Informal Learning Strategy
Abstract
1. Introduction
2. Background
- Properties: online or in person, group or individual;
- The theories on which the courses were based: Protection Motivation Theory, Theory of Planned Behavior, Theory of Reasoned Action, Signal Detection Theory, and General Deterrence Theory;
- The targets at which the courses were aimed: employees, students, young adults, or the general population;
- The effects of the training: fun, usefulness, or effectiveness.
2.1. Informal Learning
2.2. Serious Games
2.3. A Behavioral Account
2.4. Cookies Anyone?
2.5. Target Population
3. Game Design
3.1. Goal
3.2. Narrative Content
3.3. Rules
3.4. Scope
3.5. Genre
3.6. Esthetic
3.7. Character Design
3.8. Game Mode
3.9. Game Level Design
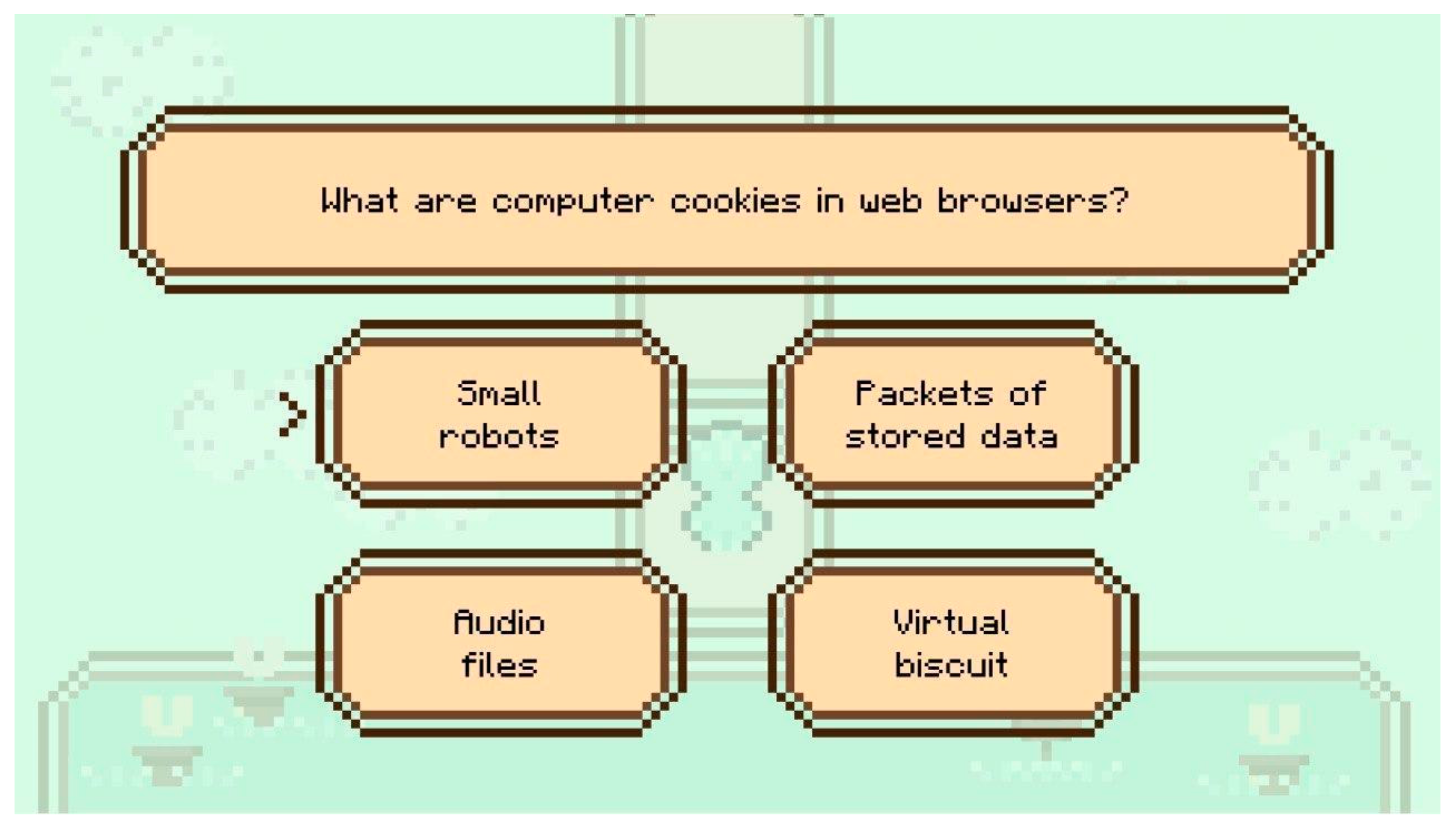
3.10. Quiz
- Knowledge (Introduction to Cookies): The first level introduces players to the basics of cookies, covering key concepts such as what cookies are, where they come from, their primary purpose, and the types of information they store. This level also explains relevant cookie regulations, including the GDPR 2018 regulation. It serves as an essential foundation for players, helping them understand cookies before moving on to more complex topics in later levels.
- Types (Types of Cookies): In the second level, players learn to identify different types of cookies and understand the kinds of information they store. This level distinguishes between technical, profiling, and third-party cookies, as well as between session and persistent cookies. It also explains the differences between hybrid and zombie cookies, highlighting how they differ from traditional cookies and the common issues caused by zombie cookies during browsing.
- Risks (Risks and Threats): The third level focuses on the potential risks associated with cookies, such as user tracking. It emphasizes the importance of being aware of these risks, particularly since cookies can handle sensitive information, including personal and financial data. This level also covers cyberattacks that exploit cookies, such as cookie poisoning and cross-site scripting (XSS), as well as the consequences of session cookie breaches and the best practices for safely managing cookies.
- Solutions (Solutions and Best Practices): The final level provides practical tips and strategies for safely managing cookies. It covers the importance of deleting cookies and offers guidance on how to control and manage them in browsers. This level also explains the functions of common cookie management tools, the effects of browsing in private or incognito mode, and explores safer alternatives to cookies. Additionally, it highlights the benefits of using the “I Don’t Care About Cookies” extension and discusses how to identify GDPR-compliant sites, stressing the importance of reading privacy policies and cookie-related documents.
3.11. Reward
3.12. Challenge
3.13. Rank
4. Discussion and Conclusions
Future Directions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Rahman, T.; Rohan, R.; Pal, D.; Kanthamanon, P. Human factors in cybersecurity: A scoping review. In Proceedings of the 12th International Conference on Advances in Information Technology, Bangkok, Thailand, 29 June–1 July 2021; pp. 1–11. [Google Scholar]
- Alsharif, M.; Mishra, S.; AlShehri, M. Impact of Human Vulnerabilities on Cybersecurity. Comput. Syst. Sci. Eng. 2022, 40. [Google Scholar] [CrossRef]
- Zwilling, M.; Klien, G.; Lesjak, D.; Wiechetek, Ł.; Cetin, F.; Basim, H.N. Cyber security awareness, knowledge and behavior: A comparative study. J. Comput. Inf. Syst. 2022, 62, 82–97. [Google Scholar] [CrossRef]
- Lorenz, B.; Kikkas, K.; Klooster, A. The four most-used passwords are love, sex, secret, and god: Password security and training in different user groups. In Proceedings of the International Conference on Human Aspects of Information Security, Privacy, and Trust, Las Vegas, NV, USA, 21–26 July 2013; pp. 276–283. [Google Scholar]
- Tempestini, G.; Rovira, E.; Pyke, A.; Di Nocera, F. The Cybersecurity Awareness INventory (CAIN): Early Phases of Development of a Tool for Assessing Cybersecurity Knowledge Based on the ISO/IEC 27032. J. Cybersecur. Priv. 2023, 3, 61–75. [Google Scholar] [CrossRef]
- Di Nocera, F.; Tempestini, G.; Presaghi, F. Reliability and validity of the Cybersecurity Awareness INventory (CAIN). Behav. Inf. Technol. 2024, 1–12. [Google Scholar] [CrossRef]
- González-Manzano, L.; de Fuentes, J.M. Design recommendations for online cybersecurity courses. Comput. Secur. 2019, 80, 238–256. [Google Scholar] [CrossRef]
- Payne, B.K.; He, W.; Wang, C.; Wittkower, D.E.; Wu, H. Cybersecurity, technology, and society: Developing an interdisciplinary, open, general education cybersecurity course. J. Inf. Syst. Educ. 2021, 32, 1334. [Google Scholar] [CrossRef]
- He, W.; Zhang, Z. Enterprise cybersecurity training and awareness programs: Recommendations for success. J. Organ. Comput. Electron. Commer. 2019, 29, 249–257. [Google Scholar] [CrossRef]
- He, W.; Ash, I.; Anwar, M.; Li, L.; Yuan, X.; Xu, L.; Tian, X. Improving employees’ intellectual capacity for cybersecurity through evidence-based malware training. J. Intellect. Cap. 2020, 21, 203–213. [Google Scholar] [CrossRef]
- Pruemmer, J.; van Steen, T.; van den Berg, B. A systematic review of current cybersecurity training methods. Comput. Secur. 2023, 136, 103585. [Google Scholar] [CrossRef]
- Abawajy, J. User preference of cyber security awareness delivery methods. Behav. Inf. Technol. 2014, 33, 237–248. [Google Scholar] [CrossRef]
- Cerasoli, C.P.; Alliger, G.M.; Donsbach, J.S.; Mathieu, J.E.; Tannenbaum, S.I.; Orvis, K.A. Antecedents and outcomes of informal learning behaviors: A meta-analysis. J. Bus. Psychol. 2018, 33, 203–230. [Google Scholar] [CrossRef]
- Marsick, V.J.; Watkins, K. Informal and Incidental Learning in the Workplace; Routledge: New York, NY, USA, 2015. [Google Scholar]
- Blume, B.D.; Ford, J.K.; Baldwin, T.T.; Huang, J.L. Transfer of training: A meta-analytic review. J. Manag. 2010, 36, 1065–1105. [Google Scholar] [CrossRef]
- Lecat, A.; Raemdonck, I.; Beausaert, S.; März, V. The what and why of primary and secondary school teachers’ informal learning activities. Int. J. Educ. Res. 2019, 96, 100–110. [Google Scholar] [CrossRef]
- Mahoney, J.L.; Larson, R.W.; Eccles, J.S. (Eds.) Organ. Act. as Context. Dev. Extracurricular Act. after-School Community Programs; Lawrence Erlbaum Associates Publishers: Mahwah, NJ, USA, 2005; pp. 3–22. [Google Scholar]
- Rader, E.; Wash, R. Identifying patterns in informal sources of security information. J. Cybersecur. 2015, 1, 121–144. [Google Scholar] [CrossRef]
- Rader, E.; Wash, R.; Brooks, B. Stories as informal lessons about security. In Proceedings of the Eighth Symposium on Usable Privacy and Security, Washington, DC, USA, 11–13 July 2012; pp. 1–17. [Google Scholar]
- Pfeffer, K.; Mai, A.; Weippl, E.; Rader, E.; Krombholz, K. Replication: Stories as informal lessons about security. In Proceedings of the Eighteenth Symposium on Usable Privacy and Security (SOUPS 2022), Boston, MA, USA, 7–9 August 2022; pp. 1–18. [Google Scholar]
- Švábenský, V.; Čeleda, P.; Vykopal, J.; Brišáková, S. Cybersecurity knowledge and skills taught in capture the flag challenges. Comput. Secur. 2021, 102, 102154. [Google Scholar] [CrossRef]
- Balon, T.; Baggili, I. Cyber Competitions: A survey of competitions, tools, and systems to support cybersecurity education. Educ. Inf. Technol. 2023, 28, 11759–11791. [Google Scholar] [CrossRef]
- Breuer, J.; Bente, G. Why so serious? On the relation of serious games and learning. J. Comput. Game Cult. 2010, 4, 7–24. [Google Scholar] [CrossRef]
- Hendrix, M.; Al-Sherbaz, A.; Victoria, B. Game based cyber security training: Are serious games suitable for cyber security training? Int. J. Serious Games 2016, 3, 53–61. [Google Scholar] [CrossRef]
- Alotaibi, F.; Furnell, S.; Stengel, I.; Papadaki, M. A review of using gaming technology for cyber-security awareness. Int. J. Inf. Secur. Res. (IJISR) 2016, 6, 660–666. [Google Scholar] [CrossRef]
- Hill, W.A., Jr.; Fanuel, M.; Yuan, X.; Zhang, J.; Sajad, S. A survey of serious games for cybersecurity education and training. KSU Proc. Cybersecur. Educ. Res. Pract. 2020, 7, 1–17. [Google Scholar]
- Kulshrestha, S.; Agrawal, S.; Gaurav, D.; Chaturvedi, M.; Sharma, S.; Bose, R. Development and validation of serious games for teaching cybersecurity. In Proceedings of the Serious Games: Joint International Conference, JCSG 2021, Virtual Event, 12–13 January 2022; Proceedings 7. Springer International Publishing: Berlin/Heidelberg, Germany, 2022; pp. 247–262. [Google Scholar]
- Coenraad, M.; Pellicone, A.; Ketelhut, D.J.; Cukier, M.; Plane, J.; Weintrop, D. Experiencing cybersecurity one game at a time: A systematic review of cybersecurity digital games. Simul. Gaming 2020, 51, 586–611. [Google Scholar] [CrossRef]
- Hart, S.; Margheri, A.; Paci, F.; Sassone, V. Riskio: A serious game for cyber security awareness and education. Comput. Secur. 2020, 95, 101827. [Google Scholar] [CrossRef]
- Jaffray, A.; Finn, C.; Nurse, J.R. Sherlocked: A detective-themed serious game for cyber security education. In Proceedings of the Human Aspects of Information Security and Assurance: 15th IFIP WG 11.12 International Symposium, HAISA 2021, Virtual Event, 7–9 July 2021; Proceedings 15. Springer International Publishing: Berlin/Heidelberg, Germany, 2021; pp. 35–45. [Google Scholar]
- Gaurav, D.; Kaushik, Y.; Supraja, S.; Yadav, M.; Gupta, M.P.; Chaturvedi, M. Empirical study of adaptive serious games in enhancing learning outcome. Int. J. Serious Games 2022, 9, 27–42. [Google Scholar] [CrossRef]
- Skinner, B.F. An operant analysis of problem solving. In Problem Solving: Research, Method, and Theory; Kleinmuntz, B., Ed.; Wiley: New York, NY, USA, 1966; pp. 225–257. [Google Scholar]
- Skinner, B.F. An operant analysis of problem solving, Note 6.1–6.4. In Contingencies of Reinforcement: A Theoretical Analysis; Skinner, B.F., Ed.; Appleton-Century-Crofts: New York, NY, USA, 1969; pp. 157–171. [Google Scholar]
- Pierce, W.D.; Cheney, C.D. Behavior Analysis and Learning: A Biobehavioral Approach; Routledge: London, UK, 2017. [Google Scholar]
- Deterding, S.; Sicart, M.; Nacke, L.; O‘Hara, K.; Dixon, D. Gamification. Using game-design elements in non-gaming contexts. In Proceedings of the CHI’11 Extended Abstracts on Human Factors in Computing Systems, Vancouver, BC, Canada, 7–12 May 2011; pp. 2425–2428. [Google Scholar]
- Skinner, B.F. The shame of American education. Am. Psychol. 1984, 39, 947. [Google Scholar] [CrossRef]
- Di Nocera, F.; Tempestini, G. Getting rid of the usability/security trade-off: A behavioral approach. J. Cybersecur. Priv. 2022, 2, 245–256. [Google Scholar] [CrossRef]
- Utz, C.; Degeling, M.; Fahl, S.; Schaub, F.; Holz, T. (Un) informed consent: Studying GDPR consent notices in the field. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; pp. 973–990. [Google Scholar]
- Giese, J.; Stabauer, M. Factors that Influence Cookie Acceptance. In HCI in Business; Fui-Hoon Nah, F., Siau, K., Eds.; Government and Organizations; HCII 2022; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2022; Volume 13327. [Google Scholar]
- Kulyk, O.; Hilt, A.; Gerber, N.; Volkamer, M. “This Website Uses Cookies”: Users’ Perceptions and Reactions to the Cookie Disclaimer. In Proceedings of the European Workshop on Usable Security (EuroUSEC), London, UK, 23 April 2018. [Google Scholar]
- Bravo-Lillo, C.; Cranor, L.; Komanduri, S.; Schechter, S.; Sleeper, M. Harder to ignore? Revisiting {Pop-Up} fatigue and approaches to prevent it. In Proceedings of the 10th Symposium on Usable Privacy and Security (SOUPS 2014), Menlo Park, CA, USA, 9–11 July 2014; pp. 105–111. [Google Scholar]
- Bravo-Lillo, C.; Komanduri, S.; Cranor, L.F.; Reeder, R.W.; Sleeper, M.; Downs, J.; Schechter, S. Your attention please: Designing security-decision UIs to make genuine risks harder to ignore. In Proceedings of the Ninth Symposium on Usable Privacy and Security, Newcastle, UK, 24–26 July 2013; pp. 1–12. [Google Scholar]
- NordVPN Misfortune Cookie? Billions of Stolen Cookies Expose Your Data. Available online: https://nordvpn.com/research-lab/stolen-cookies-study/ (accessed on 1 July 2024).
- Higley, E. Defining Young Adulthood. DNP Qualif. Manuscr. 2019, 17, 1–28. Available online: https://repository.usfca.edu/dnp_qualifying/17 (accessed on 1 July 2024).
- Zhao, J.; Wang, G.; Dally, C.; Slovak, P.; Edbrooke-Childs, J.; Van Kleek, M.; Shadbolt, N. I make up a silly name’ Understanding Children’s Perception of Privacy Risks Online. In Proceedings of the 2019 CHI Conference on Human Factors in Computing Systems, Glasgow, Scotland, UK, 4–9 May 2019; pp. 1–13. [Google Scholar]
- Alanazi, M.; Freeman, M.; Tootell, H. Exploring the factors that influence the cybersecurity behaviors of young adults. Comput. Hum. Behav. 2022, 136, 107376. [Google Scholar] [CrossRef]
- Razali, N.E.M.; Ramli, R.Z.; Mohamed, H.; Zin NA, M.; Rosdi, F.; Diah, N.M. Identifying and validating game design elements in serious game guidelines for climate change. Heliyon 2022, 8, e08773. [Google Scholar] [CrossRef]
- Starks, K. Cognitive behavioral game design: A unified model for designing serious games. Front. Psychol. 2014, 5, 28. [Google Scholar] [CrossRef]
- Antin, J.; Churchill, E.F. Badges in Social Media: A Social Psychological Perspective. In Proceedings of the CHI 2011 Gamification Workshop Proceedings, Vancouver, BC, Canada, 7–12 May 2011; ACM Press: New York, NY, USA, 2011. [Google Scholar]
- Isbister, K.; Schaffer, N. Game Usability: Advancing the Player Experience, 1st ed.; CRC Press: Boca Raton, FL, USA, 2008. [Google Scholar]
- Lankoski, P.; Björk, S. Gameplay design patterns for believable non-player characters. In Proceedings of the DiGRA 2007 Conference: Situated Play, Tokyo, Japan, 24–28 September 2007. [Google Scholar]
- Butler, A.C.; Roediger, H.L., III. Testing improves long-term retention in a simulated classroom setting. Eur. J. Cogn. Psychol. 2007, 19, 514–527. [Google Scholar] [CrossRef]
- Blunt, R. Do serious games work? Results from three studies. ELearn 2009, 2009, 1. [Google Scholar] [CrossRef]
- Adachi, P.J.; Willoughby, T. More than just fun and games: The longitudinal relationships between strategic video games, self-reported problem solving skills, and academic grades. J. Youth Adolesc. 2013, 42, 1041–1052. [Google Scholar] [CrossRef] [PubMed]
- Rogers, S. Level Up! The Guide to Great Video Game Design; John Wiley & Sons: Hoboken, NJ, USA, 2014. [Google Scholar]
- Kuntjara, H.; Almanfaluthi, B. Character design in games analysis of character design theory. J. Games Game Art Gamification 2017, 2, 42–47. [Google Scholar] [CrossRef]
- Burgerman, J. 20 Top Character Design Tips. Available online: http://www.creativebloq.com/character-design/tips-51326432015 (accessed on 7 August 2024).
- Ivy, J.W.; Meindl, J.N.; Overley, E.; Robson, K.M. Token economy: A systematic review of procedural descriptions. Behav. Modif. 2017, 41, 708–737. [Google Scholar] [CrossRef] [PubMed]
- Vorderer, P.; Klimmt, C.; Ritterfeld, U. Enjoyment: At the heart of media entertainment. Commun. Theory 2004, 14, 388–408. [Google Scholar] [CrossRef]
- Busse, J.; Lange, A.; Hobert, S.; Schumann, M. How to Design Learning Applications That Support Learners in Their Moment of Need–Didactic Requirements of Micro Learning. In Proceedings of the Americas Conference on Information Systems (AMCIS 2020), Salt Lake City, UT, USA, 12–16 August 2020; pp. 1–10. [Google Scholar]
- Leong, K.; Sung, A.; Au, R.; Lee, C. A study of preferred learning time of online learners in multimedia microlearning in higher education contexts. Online J. TVET Pract. 2022, 7, 11–23. [Google Scholar] [CrossRef]






Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tempestini, G.; Merà, S.; Palange, M.P.; Bucciarelli, A.; Di Nocera, F. Improving the Cybersecurity Awareness of Young Adults through a Game-Based Informal Learning Strategy. Information 2024, 15, 607. https://doi.org/10.3390/info15100607
Tempestini G, Merà S, Palange MP, Bucciarelli A, Di Nocera F. Improving the Cybersecurity Awareness of Young Adults through a Game-Based Informal Learning Strategy. Information. 2024; 15(10):607. https://doi.org/10.3390/info15100607
Chicago/Turabian StyleTempestini, Giorgia, Sara Merà, Marco Pietro Palange, Alexandra Bucciarelli, and Francesco Di Nocera. 2024. "Improving the Cybersecurity Awareness of Young Adults through a Game-Based Informal Learning Strategy" Information 15, no. 10: 607. https://doi.org/10.3390/info15100607
APA StyleTempestini, G., Merà, S., Palange, M. P., Bucciarelli, A., & Di Nocera, F. (2024). Improving the Cybersecurity Awareness of Young Adults through a Game-Based Informal Learning Strategy. Information, 15(10), 607. https://doi.org/10.3390/info15100607







