User Authentication Mechanisms Based on Immersive Technologies: A Systematic Review
Abstract
1. Introduction
- We provide a comprehensive consolidation of immersive technologies for user authentication in virtual, augmented and mixed reality (compared to previous work).
- The present work is the first systematic review that tried to identify authentication methods related to VR, AR, and MR, while limiting the scope of the research to papers presenting immersive technologies as a solution.
- In addition to grouping authentication methods into categories, we also focus on the success and error rate, the tools/devices/techniques used, and the main strengths and weaknesses of each method.
2. Related Work
3. Research Methodology
3.1. Research Scope
3.2. Research Aim and Research Question
- RQ1. Which are the state-of-the-art user authentication mechanisms based on immersive technology?
- RQ2. What types of authentication schemes are mostly investigated in the reviewed literature?
- RQ3. What is the success and error rate of the proposed schemes?
- RQ4. Which tools/devices/techniques are elaborated in these methods?
- RQ5. What are the main strengths and weaknesses of each of these methods?
3.3. SLR Method
3.4. Search Strategy and Eligibility Criteria
 |
4. Results
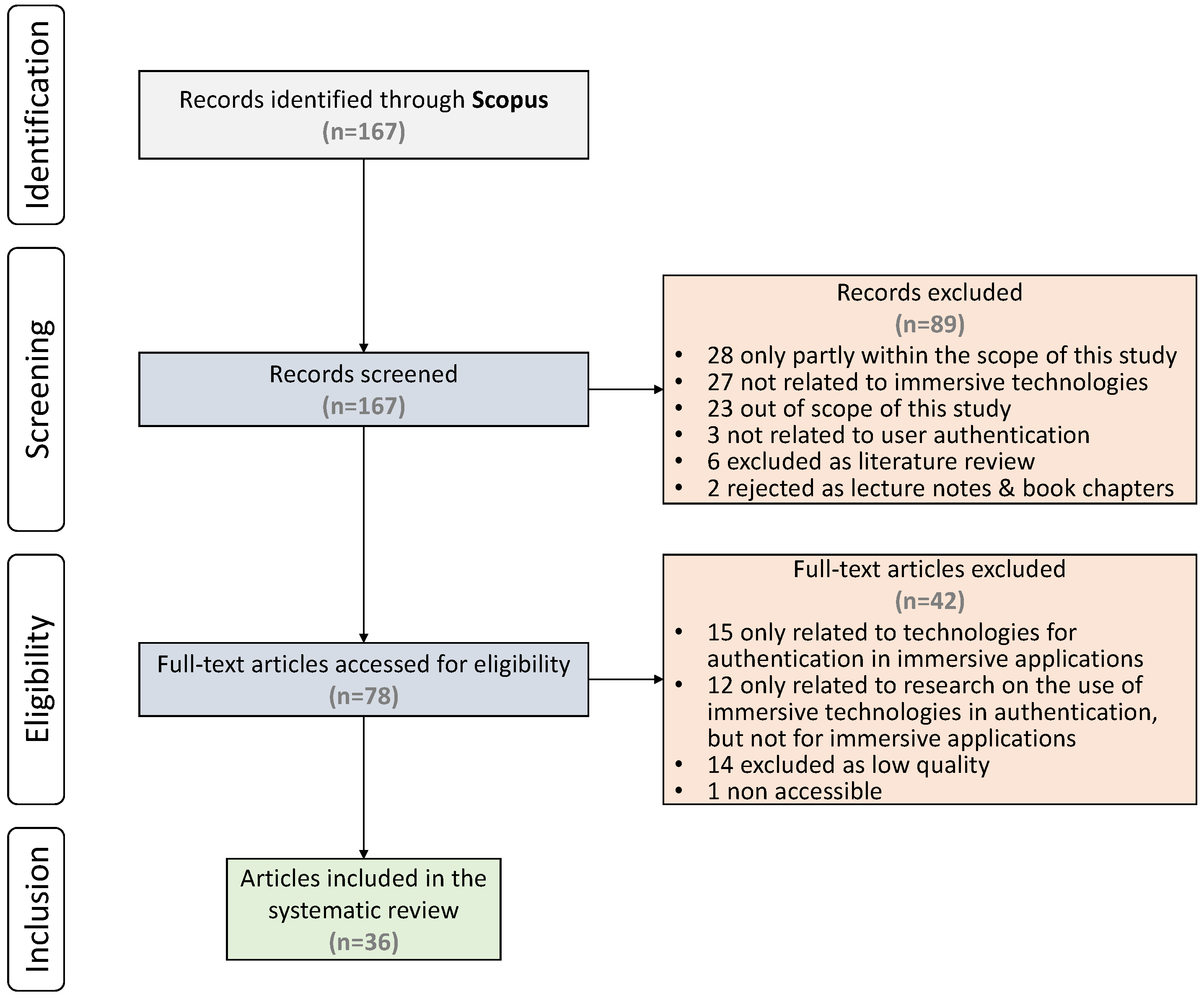
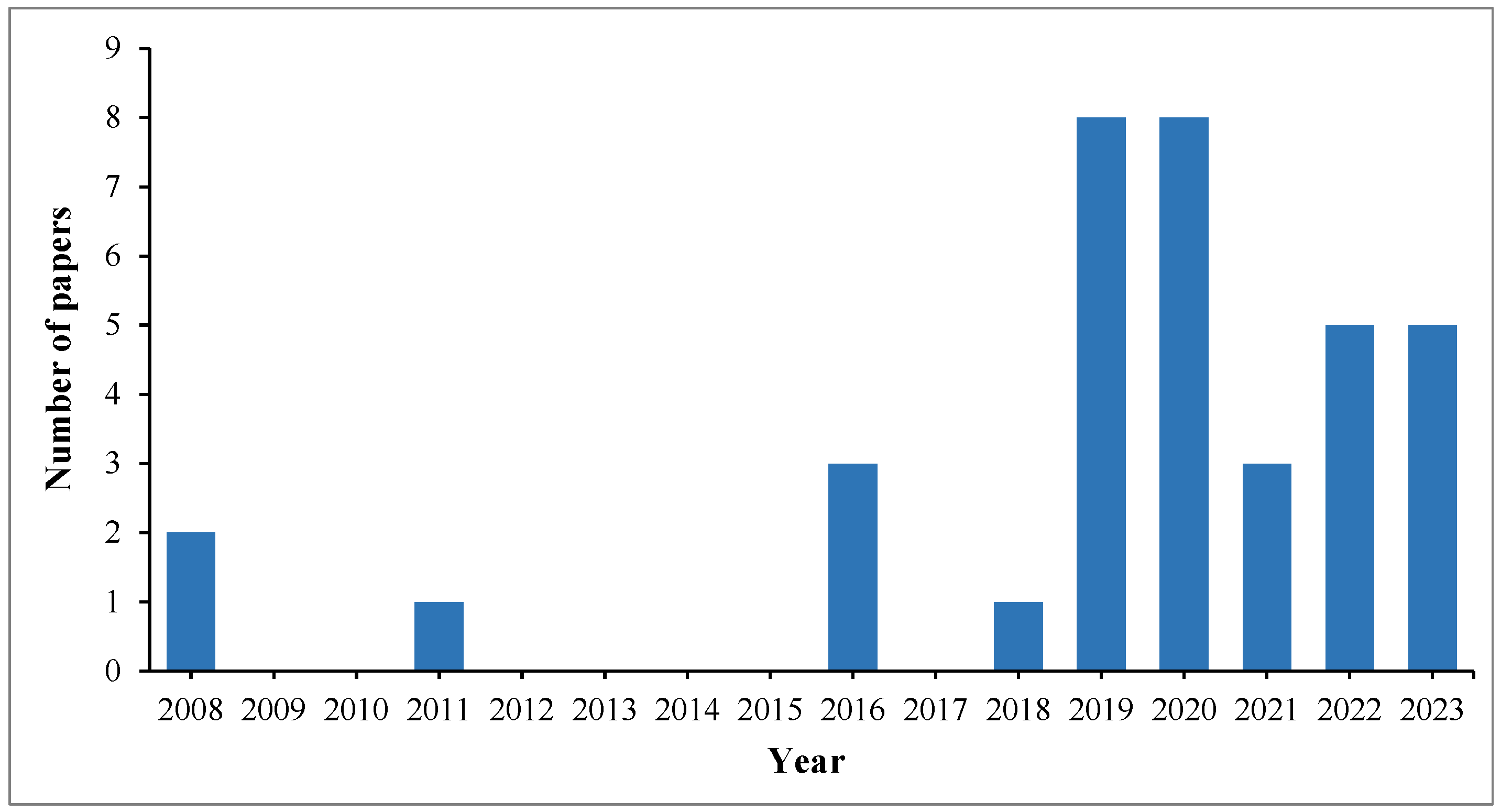
4.1. Selection of Relevant Publications
- 28 papers which were only partly within the scope of the research,
- 27 papers which were not related to immersive technologies (for example, some were mentioning virtual machines),
- 23 papers which were out of the scope of the research,
- 3 papers which were not related to user authentication,
- 6 papers which were excluded as literature reviews, and
- 2 papers which were rejected as lecture notes and book chapters.
- 12 papers related to research on the use of immersive technologies in authentication (only, but for general applications, not for immersive applications).
- 15 papers related to technologies for authentication in immersive applications (but not immersive technologies).
- 14 papers were excluded for low quality, as they did not provide adequate information for the process and results.
- 1 paper was not accessible online.
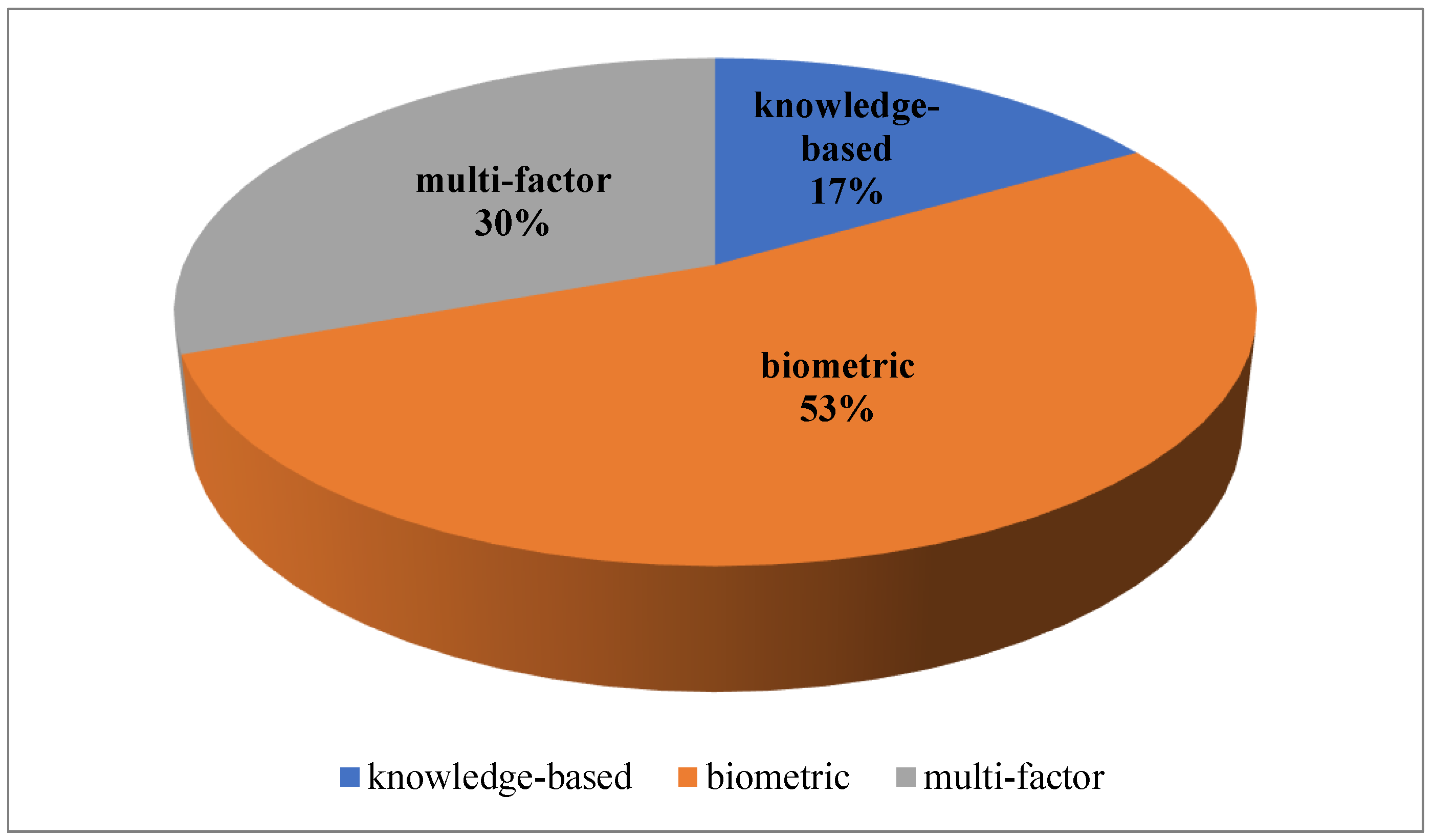
4.2. Immersive Technology-Based Authentication Methods
4.2.1. Knowledge-Based Methods
- Rubik cube: Mathis et al., in [13,15,52], use a version of a Rubik cube for authentication in VR applications. We note, however, that RubikBiom [52] is classified as a multi-factor method in this review, as the authors describe it as “human behavioral biometrics collected during knowledge-based authentication”. These schemes present to the user a cube (3 × 3 × 3 dimensions) with colored surfaces. In this respect, the method makes use of 2D grids on 3D objects. The user needs to select a digit–color combination to authenticate themself. Mathis et al. [13,52] developed a scheme (RubikAuth) based on the above colored-cube concept. In fact, their work in 2021 [13] is an extension of the previous 2020 [15] development. A matrix of nine digits is depicted on each of the five out of six surfaces of the cube (the sixth is not used) and each surface has a different color. The authentication process consists of the user selecting a digit-color combination. In Mathis et al. [13,15], the user points to the specific digit during the authentication process (from the desired color) with three different methods and presses a trigger button on the hand device to select it. The selection device (HTC VIVE controller) is held in the dominant hand, while the cube pose is controlled by the non-dominant hand (with an HTC VIVE controller). The concept has three modes: the first uses eye gaze to point the desired digit (they use a prefab called VRGazeTrail enabled by Tobii Pro VR SDK) that identifies user gaze at the digit. The second pointing method is the head pose pointing technique, for which the head position is identified as it is linked to an HTC VIVE HMD and tracked by an HTC VIVE Lighthouse tracking system. The third pointing method is performed with a controller, with the dominant hand, using the SteamVR Plugin.
- Graphical passwords: Another application of knowledge-based authentication in immersive virtual reality and in the real world is developed by George et al. [27] by selecting objects in a virtual room to create a 3D graphical password. Users point to a predefined number of objects (four objects in the prototype) in a virtual room; selection should be in the correct order. Selection of objects is performed by pointing the object with a laser and pressing a button. A visual path in the form of a blue line connecting the selected objects is presented to the user. Users are allowed selectiion of the same object more than once, but not consecutively. If the attempt is successful, the blue line turns to green upon completion, or it turns to red if the attempt does not succeed. In addition, haptic feedback is provided in the form of controller vibration (two short times for success and two slow times for failure). The system is evaluated for memorability with 27 users (100% success), for usability with a sample of 48 participants, for security against post hoc attacks with 15 participants and for security against immediate attacks with 25 participants. Post hoc attacks have a success rate of 0% and immediate attacks have a success rate of 12.5%.
- Avatar: A novel method of knowledge-based authentication is presented by Micallef et al. [26] based on the creation of an avatar representing a fictitious person with pseudo-randomly assigned characteristics. The avatar undertakes the role of a known person with the user entering its features to the systems authentication’s questions. This scheme overcomes the problem of attackers guessing the answers to questions like “What is your Mother’s Maiden Name?” (and replaces them with questions like “What was your Avatar’s secondary school?”) as information of the avatar is only known to the user. The avatar’s information is not connected to the user personally, but the user has a bond with the avatar, in an attempt to deal with psychological issues of using it. The user is presented with the avatar’s profile when logging into the system as a method to maintain this bond.
4.2.2. Biometric Methods
- Eye gaze: John et al. [38,40] use eye gaze information, with defocus/subtraction of iris information. Iris recognition is one of the best identifiers for a person, being unique for each person. Therefore, it is highly sensitive information that may be vulnerable, and its use or misuse is a major concern. In John et al. [40], defocus methodology is a Gaussian blur. The researchers evaluate the system with a sample of 15 users. They use a Pupil Labs Pro glasses-based eye tracker to collect eye tracking data and remove frames with eye blinks and motion. They also use virtual avatars for the eye gaze detection. Evaluation results showed that defocus deteriorates correct recognition rate and eye contact of avatars. An element in the work of John et al. [38] adds the possibility to the user to toggle iris track on and off, according to the specific use so as to choose whether to perform iris defocus to prevent attacks by hackers. The iris defocus retains gaze estimation level, while it reduces iris authentication.
- Ball throwing: Miller et al. [33,39], Ajit et al. [34] and Kupin et al. [35] investigate user movement as an authentication method, tracing the movement of the user when throwing a ball in a VR environment. Miller et al. [39] use three VR systems, Oculus Quest, HTC VIVE, and HTC VIVE Cosmos and a sample of 41 users (from a sample of 46, excluding left-handed users). The users have to lift one ball from the pedestal and throw it to a predefined target in the VR environment, using each one of the VR systems. Enrollment is considered as the training phase, which is compared to test use after the training with 10 training samples and 10 test samples per user. Comparisons are made on the features of the trajectories of the movement as within system (train session with second session) and cross-system (among the three used systems) with matches of the left controller and right controller orientations and headset position. Within-system comparisons show that accuracy above 0.90. In the cross-system accuracy, the VIVE system scores better than the other two at 0.85.
- Brain signal: Li et al. [36] use biometric data from brain signals to authenticate the user, in a VR and a natural environment. The researchers use electroencephalography (EEG) to record brain signals of a sample of 32 volunteer participants. The users watch videos in a virtual environment (with a VR headset) and non-virtual environment (using a laptop) while they start from a resting stage. The brain wave data collection device is an EEG with eight channel sensors and e reference sensors with a Cyton board. Authentication test results show an accuracy rate of 75.08% and 71.66% for the Non-VR and VR environments, respectively, when a Statistical Parameters of Signals (SPS) method is used, an accuracy rate of 76.73% and 73.68% when an Autoregressive (AR) model is used and 70.92% for both VR and non-VR when a combination of SPS and the Power Spectral Density (PSD) method is used. Better accuracy rate (80.91%) results are found for 10 s length EEG data with a 75% session overlapping when using the AR and SPS model combination.
- Breathing patterns: Islam et al. [37] base their research for a continuous authentication on respiration patterns, which are distinct for each individual. Measurements of non-contact cardio-respiratory motion can provide an accurate measurement of cardiopulmonary activity, different among people. They use a Doppler radar motion-sensing transceiver to track and transmit a continuous microwave signal and demodulate the echo from the target and dynamic segmentation methods to identify the subjects from their breathing patterns. Experimental trials with six participants result in a 100% classification accuracy overall success rate.
- Haptic-based authentication: Orozco et al. [30] develop a haptic-based authentication system which uses haptic biometric information to authenticate the user in three types of tasks: dialing from a virtual phone, signing a virtual check and solving a virtual maze problem. Their system comprises main subsystems of data acquisition, feature creation and selection and evaluation.
- Ultrasonic-based mapping: Chang et al. [45] introduce MetaEar, an innovative system for continuous biometric authentication using ultrasonic signals sent by head-mounted devices to the human ear. The system leverages the Ear Related Transfer Function (ERTF) to model the unique biometrics of the human ear, including auricle and ear canal characteristics. These characteristics are extracted from the inaudible ultrasonic signals reflected from the ear and are used for user authentication. MetaEar addresses challenges related to static ear features, signal synchronization, and self-interference, proposing solutions such as differential denoising and modeling the ERTF. To ensure user security and prevent replay attacks, it employs a traditional SVM for one-class authentication, achieving an impressive average accuracy over 96.8%.
- Photoplethysmogram: Seok et al. [47] present a novel approach to biometric authentication in the context of head-mounted displays for VR and metaverse applications. Instead of traditional input devices, the study explores the use of wrist-worn photoplethysmogram (PPG) sensors for non-intrusive and continuous authentication. The key innovation is the application of a one-dimensional Siamese network to identify individuals based on unique PPG characteristics. To enhance accuracy and reduce noise, a multicycle averaging method is employed. The authors evaluate the effectiveness of their approach by varying the number of cycles and demonstrate strong results, with an accuracy of 97.23%. The research highlights the potential of PPG as a biometric identifier and underscores the importance of continuous efforts in cybersecurity to ensure the safety of VR and metaverse applications beyond user authentication.
4.2.3. Multi-Factor Methods
5. Discussion
Study Limitations
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Pavithra, A.; Kowsalya, J.; Keerthi Priya, S.; Jayasree, G.; Kiruba Nandhini, T. An Emerging Immersive Technology-A Survey. Int. J. Innov. Res. Growth 2020, 6, 119–130. [Google Scholar]
- Li, J.; Barmaki, R. Trends in Virtual and Augmented Reality Research: A Review of Latest Eye Tracking Research Papers and Beyond. Prepr. Math. Comput. Sci. 2019, 2019090019. [Google Scholar] [CrossRef]
- Rebbani, Z.; Azougagh, D.; Bahatti, L.; Bouattane, O. Definitions and Applications of Augmented/Virtual Reality: A Survey. Int. J. Emerg. Trends Eng. Res. 2021, 9, 279–285. [Google Scholar] [CrossRef]
- LaValle, S.M. Virtual Reality; Cambridge University Press: Cambridge, UK, 2019. [Google Scholar]
- Bonasio, A. Immersive Experiences in Education: New Places and Spaces for Learning. [White Paper]. 2019. Available online: https://edudownloads.azureedge.net/msdownloads/MicrosoftEducation_Immersive_Experiences_Education_2019.pdf (accessed on 1 August 2023).
- Rosenblum, L. Virtual and Augmented Reality 2020. IEEE Comput. Graph. Appl. 2000, 20, 38–39. [Google Scholar] [CrossRef]
- Duezguen, R.; Noah, N.; Mayer, P.; Das, S.; Volkamer, M. SoK: A Systematic Literature Review of Knowledge-Based Authentication on Augmented Reality Head-Mounted Displays. In Proceedings of the 17th International Conference on Availability, Reliability and Security (ARES’22), Vienna, Austria, 23–26 August 2022. [Google Scholar] [CrossRef]
- Gaebel, E.; Zhang, N.; Lou, W.; Hou, Y.T. Looks Good To Me: Authentication for Augmented Reality. In Proceedings of the 6th International Workshop on Trustworthy Embedded Devices, Vienna, Austria, 28 October 2016; pp. 57–67. [Google Scholar] [CrossRef]
- Cao, Q.; Xu, F.; Li, H. User Authentication by Gait Data from Smartphone Sensors Using Hybrid Deep Learning Network. Mathematics 2022, 10, 2283. [Google Scholar] [CrossRef]
- Avola, D.; Bigdello, M.J.; Cinque, L.; Fagioli, A.; Marini, M.R. R-SigNet: Reduced space writer-independent feature learning for offline writer-dependent signature verification. Pattern Recognit. Lett. 2021, 150, 189–196. [Google Scholar] [CrossRef]
- Abdelrahman, Y.; Mathis, F.; Knierim, P.; Kettler, A.; Alt, F.; Khamis, M. CueVR: Studying the Usability of Cue-based Authentication for Virtual Reality. In Proceedings of the 2022 International Conference on Advanced Visual Interfaces, Frascati, Rome, Italy, 6–10 June 2022; pp. 1–9. [Google Scholar] [CrossRef]
- Nahar, M.N.; Alsadoon, A.; Prasad, P.W.C.; Giweli, N.; Alsadoon, O.H. An enhanced one-time password with biometric authentication for mixed reality surgical Tele-presence. Multimed. Tools Appl. 2021, 80, 10075–10100. [Google Scholar] [CrossRef]
- Mathis, F.; Williamson, J.H.; Vaniea, K.; Khamis, M. Fast and Secure Authentication in Virtual Reality Using Coordinated 3D Manipulation and Pointing. ACM Trans. Comput.-Hum. Interact. 2021, 28, 1–44. [Google Scholar] [CrossRef]
- Zhu, H.; Jin, W.; Xiao, M.; Murali, S.; Li, M. BlinKey: A Two-Factor User Authentication Method for Virtual Reality Devices. Proc. ACM Interact. Mob. Wearable Ubiquitous Technol. 2020, 4, 1–29. [Google Scholar] [CrossRef]
- Mathis, F.; Williamson, J.; Vaniea, K.; Khamis, M. RubikAuth: Fast and Secure Authentication in Virtual Reality. In Proceedings of the Extended Abstracts of the 2020 CHI Conference on Human Factors in Computing Systems, Honolulu, HI, USA, 25–30 April 2020; pp. 1–9. [Google Scholar] [CrossRef]
- Odeleye, B.; Loukas, G.; Heartfield, R.; Sakellari, G.; Panaousis, E.; Spyridonis, F. Virtually secure: A taxonomic assessment of cybersecurity challenges in virtual reality environments. Comput. Secur. 2023, 124, 102951. [Google Scholar] [CrossRef]
- Jones, J.M.; Duezguen, R.; Mayer, P.; Volkamer, M.; Das, S. A Literature Review on Virtual Reality Authentication. In Proceedings of the Human Aspects of Information Security and Assurance; Furnell, S., Clarke, N., Eds.; Springer International Publishing: Cham, Switzerland, 2021; Volume 613, pp. 189–198. [Google Scholar] [CrossRef]
- George, C.; Khamis, M.; von Zezschwitz, E.; Schmidt, H.; Burger, M.; Alt, F.; Hussmann, H. Seamless and Secure VR: Adapting and Evaluating Established Authentication Systems for Virtual Reality. In Proceedings of the 2017 Workshop on Usable Security, San Diego, CA, USA, 26 February 2017. [Google Scholar] [CrossRef]
- Heruatmadja, C.H.; Meyliana; Hidayanto, A.N.; Prabowo, H. Biometric as Secure Authentication for Virtual Reality Environment: A Systematic Literature Review. In Proceedings of the 2023 International Conference for Advancement in Technology (ICONAT), Goa, India, 24–26 January 2023; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2023; pp. 1–7. [Google Scholar] [CrossRef]
- Stephenson, S.; Pal, B.; Fan, S.; Fernandes, E.; Zhao, Y.; Chatterjee, R. SoK: Authentication in Augmented and Virtual Reality. In Proceedings of the 2022 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 23–26 May 2022; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2022; pp. 267–284. [Google Scholar] [CrossRef]
- Kitchenham, B.; Charters, S. Guidelines for Performing Systematic Literature Reviews in Software Engineering; Keele University: Newcastle, UK, 2007. [Google Scholar]
- Fink, A. Conducting Research Literature Reviews: From the Internet to Paper, 2nd ed.; Sage Publications: Thousand Oaks, CA, USA, 2005. [Google Scholar]
- Moher, D.; Liberati, A.; Tetzlaff, J.; Altman, D.G. Preferred reporting items for systematic reviews and meta-analyses: The PRISMA statement. BMJ 2009, 339, b2535. [Google Scholar] [CrossRef] [PubMed]
- Boland, A.; Dickson, R.; Cherry, G. Doing a Systematic Review: A Student’s Guide; SAGE Publications Ltd.: London, UK, 2017. [Google Scholar]
- Islam, M.R.; Lee, D.; Jahan, L.S.; Oakley, I. GlassPass: Tapping Gestures to Unlock Smart Glasses. In Proceedings of the 9th Augmented Human International Conference, Seoul, Republic of Korea, 7–9 February 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Micallef, N.; Just, M. Using avatars for improved authentication with challenge questions. In Proceedings of the SECURWARE 2011, Nice/Saint Laurent du Var, France, 21–27 August 2011; pp. 121–124. [Google Scholar]
- George, C.; Khamis, M.; Buschek, D.; Hussmann, H. Investigating the Third Dimension for Authentication in Immersive Virtual Reality and in the Real World. In Proceedings of the 2019 IEEE Conference on Virtual Reality and 3D User Interfaces (VR), Osaka, Japan, 23–27 March 2019; pp. 277–285. [Google Scholar] [CrossRef]
- Kumar, A.; Lee, L.H.; Chauhan, J.; Su, X.; Hoque, M.A.; Pirttikangas, S.; Tarkoma, S.; Hui, P. PassWalk: Spatial Authentication Leveraging Lateral Shift and Gaze30th ACM International Conference on Multimedia, Lisboa, Portugal, 10–14 October 2022; Association for Computing Machinery, Inc.: New York, NY, USA, 2022; pp. 952–960. [CrossRef]
- Wang, J.; Gao, B.; Tu, H.; Liang, H.N.; Liu, Z.; Luo, W.; Weng, J. Secure and Memorable Authentication Using Dynamic Combinations of 3D Objects in Virtual Reality. Int. J. Hum.-Interact. 2023, 1–19. [Google Scholar] [CrossRef]
- Orozco, M.; Graydon, M.; Shirmohammadi, S.; El Saddik, A. Experiments in haptic-based authentication of humans. Multimed. Tools Appl. 2008, 37, 73–92. [Google Scholar] [CrossRef][Green Version]
- Zhang, Z.; Zhang, M.; Chang, Y.; Esche, S.; Chassapis, C. A Virtual laboratory system with biometric authentication and remote proctoring based on facial recognition. Comput. Educ. J. 2016, 16, 74–84. [Google Scholar]
- Zhou, Z.; Mingshao, Z.; Yizhe, C.; Esche, S.; Chassapis, C. A virtual laboratory combined with biometric authentication and 3D reconstruction. In Proceedings of the ASME 2016 International Mechanical Engineering Congress and Exposition, Phoenix, AZ, USA, 11–17 November 2016; Volume 5. [Google Scholar]
- Miller, R.; Ajit, A.; Kholgade Banerjee, N.; Banerjee, S. Realtime Behavior-Based Continual Authentication of Users in Virtual Reality Environments. In Proceedings of the 2019 IEEE International Conference on Artificial Intelligence and Virtual Reality (AIVR), San Diego, CA, USA, 9–11 December 2019; pp. 253–2531. [Google Scholar] [CrossRef]
- Ajit, A.; Banerjee, N.K.; Banerjee, S. Combining Pairwise Feature Matches from Device Trajectories for Biometric Authentication in Virtual Reality Environments. In Proceedings of the 2019 IEEE International Conference on Artificial Intelligence and Virtual Reality (AIVR), San Diego, CA, USA, 9–11 December 2019; pp. 9–97. [Google Scholar] [CrossRef]
- Kupin, A.; Moeller, B.; Jiang, Y.; Banerjee, N.K.; Banerjee, S. Task-Driven Biometric Authentication of Users in Virtual Reality (VR) Environments. In MultiMedia Modeling; Kompatsiaris, I., Huet, B., Mezaris, V., Gurrin, C., Cheng, W.H., Vrochidis, S., Eds.; Springer International Publishing: Cham, Switzerland, 2019; Volume 11295, pp. 55–67. [Google Scholar] [CrossRef]
- Li, S.; Savaliya, S.; Marino, L.; Leider, A.M.; Tappert, C.C. Brain Signal Authentication for Human-Computer Interaction in Virtual Reality. In Proceedings of the 2019 IEEE International Conference on Computational Science and Engineering (CSE) and IEEE International Conference on Embedded and Ubiquitous Computing (EUC), New York, NY, USA, 1–3 August 2019; pp. 115–120. [Google Scholar] [CrossRef]
- Islam, S.M.M.; Rahman, A.; Prasad, N.; Boric-Lubecke, O.; Lubecke, V.M. Identity Authentication System using a Support Vector Machine (SVM) on Radar Respiration Measurements. In Proceedings of the 2019 93rd ARFTG Microwave Measurement Conference (ARFTG), Boston, MA, USA, 7 June 2019; pp. 1–5. [Google Scholar] [CrossRef]
- John, B.; Koppal, S.; Jain, E. EyeVEIL: Degrading iris authentication in eye tracking headsets. In Proceedings of the 11th ACM Symposium on Eye Tracking Research &Applications, Denver, CO, USA, 25–28 June 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Miller, R.; Banerjee, N.K.; Banerjee, S. Within-System and Cross-System Behavior-Based Biometric Authentication in Virtual Reality. In Proceedings of the 2020 IEEE Conference on Virtual Reality and 3D User Interfaces Abstracts and Workshops (VRW), Atlanta, GA, USA, 22–26 March 2020; pp. 311–316. [Google Scholar] [CrossRef]
- John, B.; Jorg, S.; Koppal, S.; Jain, E. The Security-Utility Trade-off for Iris Authentication and Eye Animation for Social Virtual Avatars. IEEE Trans. Vis. Comput. Graph. 2020, 26, 1880–1890. [Google Scholar] [CrossRef]
- Sivasamy, M.; Sastry, V.; Gopalan, N. VRCAuth: Continuous Authentication of Users in Virtual Reality Environment Using Head-Movement. In Proceedings of the 2020 5th International Conference on Communication and Electronics Systems (ICCES), Coimbatore, India, 10–12 June 2020; pp. 518–523. [Google Scholar] [CrossRef]
- Bhalla, A.; Sluganovic, I.; Krawiecka, K.; Martinovic, I. MoveAR: Continuous Biometric Authentication for Augmented Reality Headsets. In Proceedings of the 7th ACM Cyber-Physical System Security Workshop, Hong Kong, China, 7 June 2021; pp. 41–52. [Google Scholar]
- Lohr, D.; Komogortsev, O.V. Eye Know You Too: Toward Viable End-to-End Eye Movement Biometrics for User Authentication. IEEE Trans. Inf. Forensics Secur. 2022, 17, 3151–3164. [Google Scholar] [CrossRef]
- Islam, S.M.M.; Boric-Lubecke, O.; Lubecke, V.M. Identity Authentication in Two-Subject Environments Using Microwave Doppler Radar and Machine Learning Classifiers. IEEE Trans. Microw. Theory Tech. 2022, 70, 5063–5076. [Google Scholar] [CrossRef]
- Chang, Z.; Wang, L.; Li, B.; Liu, W. MetaEar: Imperceptible Acoustic Side Channel Continuous Authentication Based on ERTF. Electronics 2022, 11, 3401. [Google Scholar] [CrossRef]
- Jang, H.; Park, S.; Woo, J.; Ha, J.; Kim, L. Authentication System Based on Event-related Potentials Using AR Glasses. In Proceedings of the 2023 11th International Winter Conference on Brain-Computer Interface (BCI), Gangwon, Republic of Korea, 20–22 February 2023; pp. 1–4. [Google Scholar] [CrossRef]
- Seok, C.L.; Song, Y.D.; An, B.S.; Lee, E.C. Photoplethysmogram Biometric Authentication Using a 1D Siamese Network. Sensors 2023, 23, 4634. [Google Scholar] [CrossRef]
- Wang, R.; Huang, L.; Wang, C. Low-effort VR Headset User Authentication Using Head-reverberated Sounds with Replay Resistance. In Proceedings of the 2023 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 22–25 May 2023; pp. 3450–3465. [Google Scholar] [CrossRef]
- Alsulaiman, F.; El Saddik, A. Three-Dimensional Password for More Secure Authentication. IEEE Trans. Instrum. Meas. 2008, 57, 1929–1938. [Google Scholar] [CrossRef]
- Lu, D.; Huang, D.; Deng, Y.; Alshamrani, A. Multifactor User Authentication with In-Air-Handwriting and Hand Geometry. In Proceedings of the 2018 International Conference on Biometrics (ICB), Gold Coast, Australia, 20–23 February 2018; pp. 255–262. [Google Scholar] [CrossRef]
- Funk, M.; Marky, K.; Mizutani, I.; Kritzler, M.; Mayer, S.; Michahelles, F. LookUnlock: Using Spatial-Targets for User-Authentication on HMDs. In Proceedings of the Extended Abstracts of the 2019 CHI Conference on Human Factors in Computing Systems, Glasgow, Scotland, UK, 4–9 May 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Mathis, F.; Fawaz, H.I.; Khamis, M. Knowledge-driven Biometric Authentication in Virtual Reality. In Proceedings of the Extended Abstracts of the 2020 CHI Conference on Human Factors in Computing Systems, Honolulu, HI, USA, 25–30 April 2020; pp. 1–10. [Google Scholar] [CrossRef]
- Lu, Y.; Gao, B.; Long, J.; Weng, J. Hand Motion with Eyes-free Interaction for Authentication in Virtual Reality. In Proceedings of the 2020 IEEE Conference on Virtual Reality and 3D User Interfaces Abstracts and Workshops (VRW), Atlanta, GA, USA, 22–26 March 2020; pp. 714–715. [Google Scholar] [CrossRef]
- Wazir, W.; Khattak, H.A.; Almogren, A.; Khan, M.A.; Ud Din, I. Doodle-Based Authentication Technique Using Augmented Reality. IEEE Access 2020, 8, 4022–4034. [Google Scholar] [CrossRef]
- Yang, K.; Zhang, Z.; Youliang, T.; Ma, J. A Secure Authentication Framework to Guarantee the Traceability of Avatars in Metaverse. IEEE Trans. Inf. Forensics Secur. 2023, 18, 3817–3832. [Google Scholar] [CrossRef]
| Reference (RQ1) | Year | Type of Authentication (RQ2) | System Name | Immersive Technology | User Sample Size | Success Rate (RQ3) | Error Rate/Attack Success (RQ3) | Tools/Hardware Used (RQ4) | Main Strengths and Weaknesses (RQ5) |
|---|---|---|---|---|---|---|---|---|---|
| Knowledge-based methods | |||||||||
| Micallef et al. [26] | 2011 | Knowledge-based (avatar) | VR | 100% | Not applicable | Ability of participants to recall information associated with their Avatar | |||
| George [27] | 2019 | Knowledge-based (3D graphical password) | RoomLock | VR | 48 | 0% post hoc attacks 12.5% immediate attacks 12.5% shoulder surfing rate | Oculus Go HTC VIVE controller | High level of security, usability, and memorability | |
| Mathis et al. [15] | 2020 | Knowledge-based (Rubik cube) | RubikAuth | VR | 23 | 98.91% | 1.48% attack 0% eye gaze 2.22% head pose | HTC VIVE controller and HMD | Controller tapping is significantly faster than head pose and eye gaze |
| Mathis et al. [13] | 2021 | Knowledge-based (Rubik cube) | RubikAuth | VR | 15 + 23 | 90.80% correct entries | HTC VIVE controller and HMD | 3D passwords in a cube offer large password space, and high resistance of RubikAuth to observation attacks | |
| Kumar et al. [28] | 2022 | Knowledge-based (body-centric graphical password) | PassWalk | MR (AR, VR) | 22 | 1.1% observation attacks | Microsoft HoloLens 1 | A keyboard-less authentication system that offers a new combination of multi-modal inputs, i.e., head-gazes and footsteps, highly accurate, secure to observation attacks (98.9% resistance) | |
| Wang et al. [29] | 2023 | Knowledge-based (3D graphical password) | VR | 36 | 97.78% enter accuracy 97.92% memory accuracy | 0% shoulder surfing attack 4.17% MITR (Man-In-The-Room) attack | HTC VIVE Pro | Utilization of a dynamic combination of multi-attribute authentication methods (3D objects and their attributes) for VR | |
| Biometric methods | |||||||||
| Orozco et al. [30] | 2008 | Biometric (haptic based) | VR | 45 | 86.6–90.9% | 0.4% false identification | Haptic interface (not specified) | Haptic methods that will become more common in the near feature | |
| Zhang et al. [31] | 2016 | Biometric (facial recognition) | VR | 30 | 63–100% according to criteria | Depth camera (not specified) | Macroscopic authentication is more suitable for virtual proctoring than microscopic authentication | ||
| Zhou et al. [32] | 2016 | Biometric (facial recognition) | VR | 63–100% according to criteria | Camera (not specified) | The virtual proctor can provide high accuracy in detecting suspicious behavior—the value of the threshold needs to be appropriately configured | |||
| Miller et al. [33] | 2019 | Biometric (ball throwing) | VR | 33 | 80% accuracy 84.36% attack resistance | Oculus Quest, HTC VIVE, and HTC VIVE Cosmos | Protection against session hijacking and external intruder detection | ||
| Ajit et al. [34] | 2019 | Biometric (ball throwing) | VR | 33 | 93.03% | HTC VIVE | Study provides results for position and orientation—using orientation only provides the best results | ||
| Kupin et al. [35] | 2019 | Biometric (ball throwing) | VR | 14 | 90% to 92.86% | HTC VIVE headset and hand controllers | Work can be extended with more controllers, not unique trajectories and cognitive components | ||
| Li et al. [36] | 2019 | Biometric (brain signal) | VR | 32 | 79.22%, 79.55%, 80.91% for different methods | 8-channel EEG sensors 2 reference sensors with Cyton board | No significant difference between the accuracy rates for VR and Non-VR EEG data | ||
| Islam et al. [37] | 2019 | Biometric (breathing patterns) | VR | 6 | 100% | Microwave Doppler radar | A valuable method to overcome limitations of existing traditional authentication systems | ||
| John et al. [38] | 2019 | Biometric (eye gaze) | VR | 5 | 80% | Pupil Labs eye tracker (Pupil Pro 2016, 30 Hz) | Easy-to-use method with a good ease/security trade-off | ||
| Miller et al. [39] | 2020 | Biometric (ball throwing) | VR | 41 | 90% and higher | Oculus Quest, HTC VIVE, and HTC VIVE Cosmos | High within-system accuracy— cross-system accuracy is lower | ||
| John et al. [40] | 2020 | Biometric (eye gaze) | VR | 15 | 60.1% true positive rate 39.9% false negative rate | Pupil Labs Pro glasses-based eye tracker | Recognition rate from 79% dropped to 7% with defocus | ||
| Sivasamy et al. [41] | 2020 | Biometric (head movement) | VRCAuth | VR | 40 + 48 | 99.6–99.98% | HMD (not specified) with accelerometer and gyroscope | LMT and PART classifiers/algorithms work more effectivelu and efficiently | |
| Bhalla et al. [42] | 2021 | Biometric (head movement) | MoveAR | AR | 5 | 92.675% accuracy score | 11% EER | Microsoft HoloLens | It is possible to authenticate AR head-mounted display users from their head movements and gestures |
| Lohr et al. [43] | 2022 | Biometric (eye gaze) | EKYT (Eye Know You Too) | MR (AR, VR) | 59 | 1-in-10,000 false accept. rate | 3.66% EER on a reading task with 5 s long | EyeLink 1000 eye tracker | The first to approach a level of authentication performance using eye gaze acceptable for real-world use |
| Islam et al. [44] | 2022 | Biometric (breathing patterns) | VR | 20 | 98.33% and 97.5% for single- and two-subject experiments | Microwave Doppler radar | This work demonstrates its efficacy in the presence of two equidistant subjects in the radar field of view, a major hurdle for practical authentication applications | ||
| Chang et al. [45] | 2022 | Biometric (ultrasonic-based mapping—ear) | MetaEar | AR | 17 | 96.48% average accuracy | Smartphone (Android) | Modeling and authenticating human ear ERTF (Ear Related Transfer Function) biometrics using FMCW (Frequency-Modulated Continuous Wave) ultrasonics | |
| Jang et al. [46] | 2023 | Biometric (brain signals) | AR | 20 | 100% accuracy using LSVM and KNN models | Microsoft HoloLens 2 | Demonstrates the feasibility of using EEG-based event-related potentials (ERPs) in combination with augmented reality (AR) glasses for highly secure and reliable biometric authentication | ||
| Seok et al. [47] | 2023 | Biometric (Photoplethysmogram) | VR | 35 | 97.23% accuracy | 3.57% EER | Photoplethysmogram sensor | Noise reduction and information preservation through multicycle averaging; system accuracy not affected by the number of enrolled subjects; potential significant performance deterioration when using noisy data | |
| Wang et al. [48] | 2023 | Biometric (ultrasonic-based mapping—head) | VR | 30 | 98.87% (99.33% for the mobile phone VR) | Meta Quest (Samsung Galaxy S8) | Low-effort authentication system leveraging head-reverberated sounds, for current VR headsets, without kernel or hardware modifications | ||
| Multi-factor methods | |||||||||
| Alsulaiman et al. [49] | 2008 | Multi-factor | VR | 30 | Any input device: mouse, keyboard, fingerprint scanner, iris scanner, stylus, card reader, and microphone | High user acceptance and huge password space | |||
| Gaebel et al. [8] | 2016 | Multi-factor | LGTM | AR | 100 | 1m: 60–100% 2m: 30–75% 3m: 23–50% | 1m: 0.722m (mean err.) 2m:1.654m (mean err.) 3m: 2.321m (mean err.) | AR headsets SpotFi | Wireless localization can be a useful tool for authentication |
| Lu et al. [50] | 2018 | Multi-factor | VR | 100 | 0.6% EER (without spoofing attack) 3.4% EER (with spoofing) | Leap Motion controller | Hand gesture has a potential in user authentication | ||
| Funk et al. [51] | 2019 | Multi-factor | LookUnlock | AR | 15 | 3.7–5.9% | HMD (not specified) | High level of resistance to shoulder-surfing attacks | |
| Zhu et al. [14] | 2020 | Multi-factor | BlinKey | VR | 50 | 14.6% EER | HTC VIVE Pro with a Pupil Labs eye tracker | Robust against various types of attacks—high usability | |
| Mathis et al. [52] | 2020 | Multi-factor | RubikBiom | VR | 23 | 98.91% | HTC VIVE (2160 × 1200 px) and SteamVR Plugin for controller communication | Knowledge-driven behavioral biometric authentication increases security | |
| Lu et al. [53] | 2020 | Multi-factor | VR | 10 | Not mentioned | Not mentioned | The user can authenticate the VR system while performing another task simultaneously | ||
| Wazir et al. [54] | 2020 | Multi-factor | AR | 20 + 20 | 50% | Smartphone | Satisfactory results in terms of ease to use, interaction, effectiveness, and security | ||
| Nahar et al. [12] | 2021 | Multi-factor | MR (AR, VR) | 20 | 84.36% | IRIS imaging device (not specified) | System can be used in surgical telepresence | ||
| Abdelrahman et al. [11] | 2022 | Multi-factor | CueVR | VR | 20 | 1/10 to 1/5 successful attacks (n = PIN length) | HTC VIVE Pro headset, using the SteamVR plugin Laserpointer Trackpad Motion Controller | Among the 3 pointing methods Laserpointer, two-handed Trackpad and two-handed Motion Controller, the Laserpointer was the least secure input method, but the most preferred by the users | |
| Yang et al. [55] | 2023 | Multi-factor | VR | iris public datasets | Raspberry Pi 4B for simulation | A two-factor authentication framework which guarantees the virtual–physical traceability that tracks an avatar in virtual space to its manipulator in the physical world | |||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Anastasaki, I.; Drosatos, G.; Pavlidis, G.; Rantos, K. User Authentication Mechanisms Based on Immersive Technologies: A Systematic Review. Information 2023, 14, 538. https://doi.org/10.3390/info14100538
Anastasaki I, Drosatos G, Pavlidis G, Rantos K. User Authentication Mechanisms Based on Immersive Technologies: A Systematic Review. Information. 2023; 14(10):538. https://doi.org/10.3390/info14100538
Chicago/Turabian StyleAnastasaki, Ioanna, George Drosatos, George Pavlidis, and Konstantinos Rantos. 2023. "User Authentication Mechanisms Based on Immersive Technologies: A Systematic Review" Information 14, no. 10: 538. https://doi.org/10.3390/info14100538
APA StyleAnastasaki, I., Drosatos, G., Pavlidis, G., & Rantos, K. (2023). User Authentication Mechanisms Based on Immersive Technologies: A Systematic Review. Information, 14(10), 538. https://doi.org/10.3390/info14100538











