Abstract
In a traditional combination network, each user connects to a unique set of r relays. However, few research efforts have considered the multiaccess combination network problem wherein each unique set of r relays is connected by u users. In this paper, we focus on designing coded caching schemes for a multiaccess combination network. By directly applying the well-known coding method (proposed by Zewail and Yener) for a combination network, a coded caching scheme (called ZY scheme) for multiaccess combination network is obtained. However, its subpacketization has an exponential order with the number of users which leads to high implementation complexity. In order to reduce subpacketization, a direct construction of a coded caching scheme (called the direct scheme) for multiaccess combination network is proposed by means of combinational design theory, where the parameter u must be a combinatorial number. For the arbitrary parameter u, the hybrid construction of a coded caching scheme (called the hybrid scheme) for the multiaccess combination network is proposed based on the direct scheme. Theoretical and numerical analysis shows that the direct scheme and the hybrid scheme have a smaller transmission load for each relay compared with the naive scheme (which is obtained by repeatedly applying the coded caching scheme for a traditional combination network by u times) and have much lower subpacketization compared with the ZY scheme.
1. Introduction
Coded caching, proposed by Maddah-Ali and Niesen (MN) in [1], not only utilizes users’ cache memories to shift some of the network traffic to off-peak hours but also to create multicast opportunities that further reduce network congestion during peak traffic hours. The first coded caching system studied was the following shared-link broadcast network with end-user-caches: there exists a single server with N files with the same length connecting to K users through a shared error-free broadcast link, wherein each user has a cache of size M files. An F-division -coded caching scheme consists of two phases: the placement phase during the off-peak traffic times and delivery phase during peak traffic times. In the placement phase, the server divides each file into F packets (F is referred to as subpacketization) with the same length, and then places some packets of size M files in each user’s cache without knowledge of later users’ demands. If the server directly places some packets in each user’s cache, without coding, the placement is said to be uncoded. Otherwise, the placement is called coded. In the delivery phase, each user’s demand arrives at the server. According to the users’ demands, the server transmits coded packets (XOR of the required packets) in order to satisfy all users’ demands with the help of their caches. The maximum normalized transmission amount over all possible demands is defined as the transmission load R, and the coded caching gain is defined as , where is the transmission load of the conventional uncoded caching scheme. The goal is to design a coded caching scheme with transmission load R and the subpacketization F as small as possible due to the efficiency requirements of transmission and low implementation complexity. The above coded caching model is called a caching or MN caching system, for which Maddah-Ali and Niesen [1] proposed the first coded caching scheme (called the MN scheme) which is optimal under the constraint of uncoded placement and [2]. Yan et al. [3] proposed a combinatorial structure called placement delivery array (PDA) to design a coded caching scheme for the MN caching system. It is worth noting that the MN scheme can be represented by a special PDA which is called the MN PDA.
1.1. Traditional Combination Network Caching System
Compared with the MN caching system, a more practical system wherein users may communicate with the server through intermediate relays has gained attention. Since the analysis of relay networks with arbitrary topologies is challenging, many studies have focused on a symmetric version of this general problem known as combination networks with end-user-caches. The combination network caching system was first proposed in [4] as follows: a server with N files connects H relays (without caches), which in turns connect users, where each user is equipped with a cache of size M files and each user is connected to a unique set of r relays. All links are assumed to be error-free and interference-free. The transmission load for each relay is defined as the maximum normalized transmission amount from the server to each relay over all relays and all possible demands. The objective is to design a coded caching scheme with the transmission load for each relay and the subpacketization as small as possible.
The first two schemes for combination networks were proposed in [4]: one based on uncoded placement and routing in the delivery phase, and the other based on the placement strategy of the MN scheme and a linear code for delivery. The authors in [5] proposed a scheme based on coded placement that effectively splits the combination network into H parallel MN caching systems, each of which serves users using the MN scheme. This scheme works for any parameters H, r and memory ratio and the achieved transmission load for each relay is approximately of the transmission load of MN scheme. Furthermore, it can be used to deal with any relay networks with arbitrary topologies. There are some other studies on improving the transmission load for each relay based on MN scheme; for instance, [6,7,8,9,10,11] etc. Since the subpacketization of the MN scheme exponentially increases with the number of users, all of the above known schemes have high subpacketization, which implies that these schemes not only have high implementation complexity but also cannot be used when the files in the server are not large enough.
In order to design a scheme with low subpacketization for the combination network caching system, the authors in [12] proposed the concept of combinatorial placement delivery array (CPDA) based on PDA which has been widely studied in [13,14]. When r divides H (denoted by ), based on the MN scheme, they proposed a scheme with lower subpacketization while the achieved transmission load for each relay is equal to that of the scheme in [5]. However, its subpacketization still increases exponentially with the number of users. The authors in [15] showed that the strongly coloring PDA in [16] is a CPDA, which is constructed by the strong coloring in the bipartite graph [17]. Consequently, two classes of CPDAs were obtained in [15], which lead to schemes with lower subpacketization and without the limitation of compared with the scheme in [12].
1.2. Multiaccess Combination Network Caching System
It should be noted that all of the above studies are under the assumption that each user is connected to a distinct set consisting of r relays. However, the number of users in a network system may be time-varying [18] in practice. So it always happens that multiple users are connected to the same r relays when the number of users is larger than . Therefore, it is meaningful to study a combination network caching system where multiple users are connected to the same r relays. Assuming that there are exactly u users connected to a unique set of r relays. Such a setting is denoted by an multiaccess combination network caching system.
Clearly, an multiaccess combination network caching system is an combination network caching system, as proposed in [4]. We can therefore generate an multiaccess combination network caching scheme by the repeated application of an combination network caching scheme u times. However, in this naive strategy, not only will the coded caching gain among the users who are connected to the same r relays be omitted, but the coded caching gain among the users who are connected to different relay subsets containing at least one common relay will not be fully considered. In order to make the transmission load for each relay as small as possible, we prefer to design a scheme with the coded caching gain as large as possible. This motivates us to study the multiaccess combination network caching problem, wherein the basic idea is to generate coded caching gain among all the users as large as possible instead of generating coded caching gain only among users who are connected to distinct sets of r relays. Specifically, the following main results are obtained in this paper.
- By using the idea proposed in [5], a scheme (called the ZY scheme) for the multiaccess combination network is obtained, which works for any parameters H, r, u and any memory ratio , and the achieved transmission load for each relay is approximately of the transmission load of MN scheme since the coded caching gain among the users who are connected to the same relay is fully considered. However, its subpacketization exponentially increases with the number of users.
- In order to reduce subpacketization, we omit the coded caching gain among the users who are connected to the same r relays and consider the coded caching gain among the users who are connected to different relay subsets containing at least one common relay as much as possible, and directly construct a CPDA from the view point of combinatorial design theory, which leads to a new scheme (called the direct scheme) for the multiaccess combination network with lower subpacketization. Since some special combinatorial structure is used in this scheme, the parameter u has to be a combinatorial number.
- For arbitrary parameter u, based on the proposed direct scheme and the MN PDA, a hybrid construction of CPDA is proposed which leads to a new scheme (called the hybrid scheme) for the multiaccess combination network. It is worth noting that the hybrid scheme not only has the same coded caching gain among the users who are connected to different relay subsets containing at least one common relay as the direct scheme, but also fully considers the coded caching gain among the users who are connected to the same r relays by increasing some subpacketization.
The rest of this paper is organized as follows. In Section 2, the traditional combination network caching system is extended to the multiaccess combination network caching system, and the concepts of PDA and CPDA are briefly reviewed. In Section 3, three schemes for the multiaccess combination network are proposed. In Section 4, performance analysis is provided. Finally, a conclusion is given in Section 5 while some proofs are provided in the Appendix A and Appendix B.
2. Preliminaries
In this section, the multiaccess combination network caching system and the concepts of PDA and CPDA are introduced. First, the following notations are useful in this paper.
- , .
- denotes the least non-negative residue of a modulo q. if , otherwise .
- For any set and for any positive integer r with , , i.e., is the collection of r-sized subsets of , where denotes the cardinality of a set.
- Given an array with alphabet , we define and for any integer a, where .
- For any two vectors and with the same length, is the number of coordinates in which and differ, is the weight of , i.e., the number of nonzero coordinates of . For example, if and , then and .
- For any vector with length H and for any nonempty subset , is a vector with length obtained by taking only the coordinates with subscript . For example, if and , then .
2.1. Placement Delivery Array
Yan et al. [3] proposed a combinatorial structure, called placement delivery array (PDA) to characterize the placement phase and delivery phase of a scheme for the MN caching system simultaneously.
Definition 1.
(PDA, [3]) For positive integers K, F, Z and S, anarray, , composed of a specific symbol “∗” called star and S integers in, is called aplacement delivery array (PDA) if it satisfies the following conditions:
- C1.
- Each column has exactly Z stars.
- C2.
- Each integer in occurs at least once.
- C3.
- For any two distinct entries and , is an integer only if
- a. , , i.e., they lie in distinct rows and distinct columns; and
- b. , i.e., the corresponding subarray formed by rows and columns must be of the following form
Example 1.
It is easy to verify that the following array is a PDA,
The first PDA was proposed by Maddah-Ali and Niesen in [1,3].
Lemma 1.
(MN PDA, MN scheme [1,3]) For any positive integers K, M and N with , if is an integer, there exists a PDA, which leads to a coded caching scheme (MN scheme) with subpacketization and transmission load for the MN caching system.
2.2. Multiaccess Combination Network Caching System
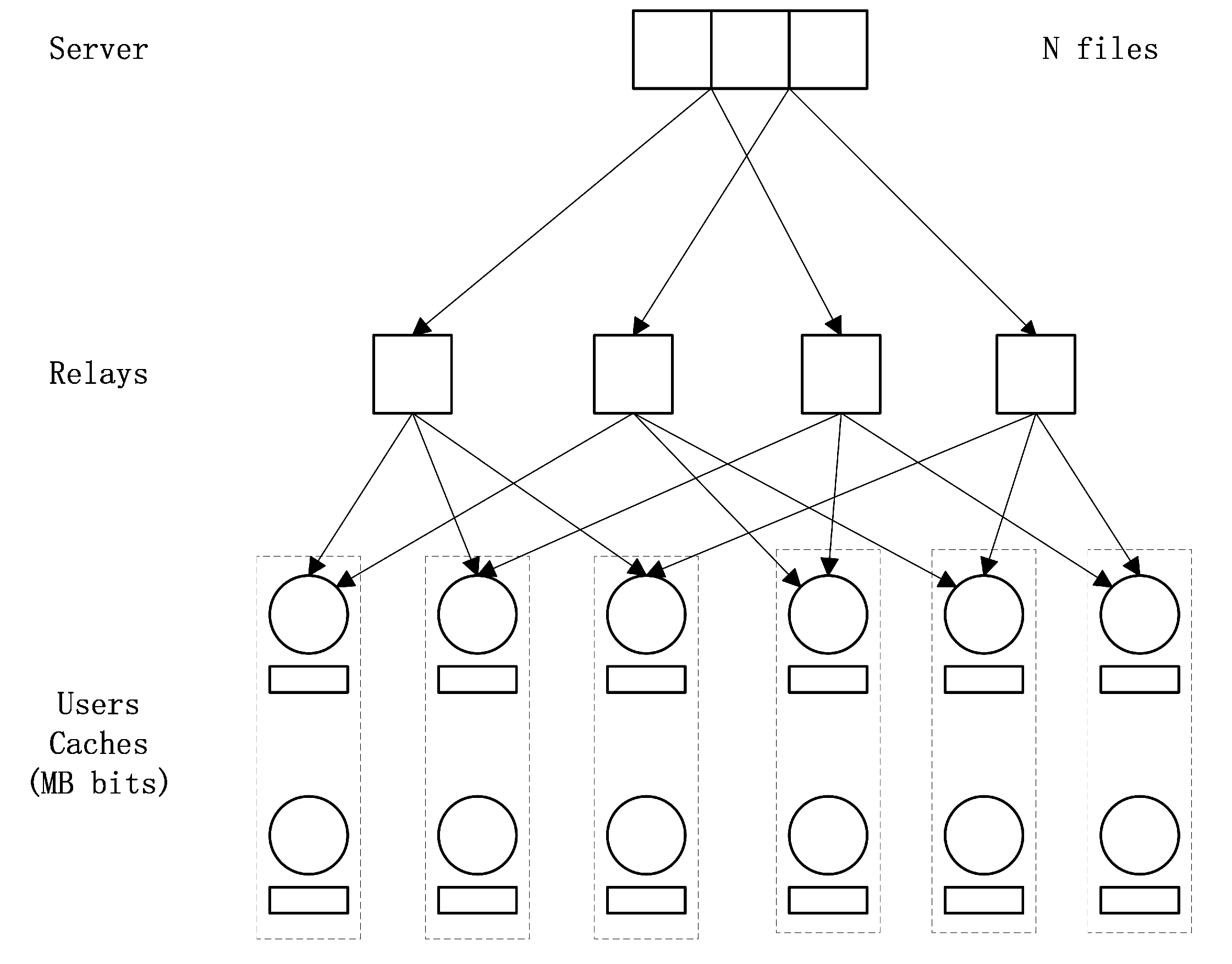
We consider an multiaccess combination network caching system (see Figure 1) in which a server containing N files , each of which is uniformly distributed in for some positive integer B, connects H relays through H error-free and interference-free links. Each set of r relays connects u users, so that the total number of users is . Each user has a storage capacity of size M files where and all relays have no cache memory. Each relay h could broadcast the intermediate signals from the server to the users who are connected to it. The users are denoted by and user is connected to relay h if and only if . The set of relays which connect user is denoted by .
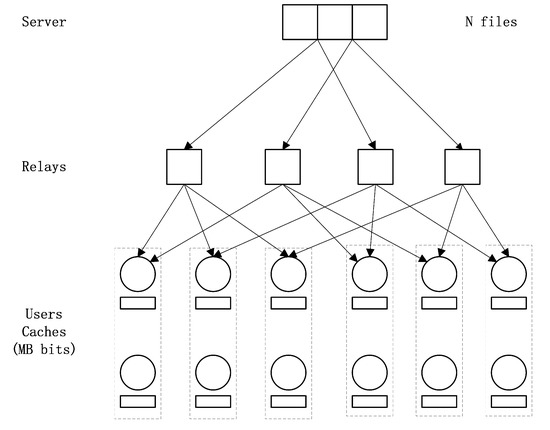
Figure 1.
A multiaccess combination network with , , .
An F-division multiaccess combination network caching scheme contains the two following phases.
- Placement phase: Each file is divided into F packets of equal size. Then, each user directly accesses the file library and stores some packets or linear combinations of some packets of the N files in its cache. The set of cached packets by user is denoted by whose size is at most M files. That is, for each user , there exists a function to generate the cache contents . Let .
- Delivery phase: Assume that each user randomly requests one file from the file library . The demand vector is represented by , which implies that the user requests the file where . Given , the server sends a message of size bits to relay . Then, relay forwards to its connecting users. User can recover its desired file by with the help of . This phase can be represented by the following encoding functions and decoding functions.
- -
- The H encoding functions: For each relay ,generates the transmitted message from the server to the relay h. It is a function of the library , the cached contents of all users and the demand vector .
- -
- The K decoding functions: For each user ,decodes the requested file of user from all messages received by user and its own cache, i.e.,
The transmission load for each relay is defined as
2.3. Combinatorial Placement Delivery Array
Definition 2.
(CPDA, [12]) For any positive integers H, r and u with , a PDA is called a combinatorial placement delivery array (CPDA) if it satisfies the following condition.
- C4.
- All the columns can be labeled by such that for any , the intersection of the first coordinate of all column labels satisfying that s appears in column , denoted by , is not empty.
The definition of CPDA is proposed based on the definition of PDA. Thus, a CPDA must be a PDA. However, the converse does not necessarily hold since CPDA has another requirement, i.e., the condition C4. The detailed discussion of the relationship between PDA and CPDA could be found in [15]. Based on a CPDA, a scheme for the multiaccess combination network can be obtained by using Algorithm 1.
| Algorithm 1 Caching scheme based on CPDA in [15] |
| procedure Placement(, ) |
| 2: Split each file into packets, i.e., . |
| for do |
| 4: |
| end for |
| 6: end procedure |
| procedure Delivery() |
| 8: for do |
| ; |
| 10: ,; |
| Divide into sub-packets, i.e., ; |
| 12: for do |
| Server sends to relay ; |
| 14: Relay broadcasts to its connecting users; |
| end for |
| 16: end for |
| end procedure |
From Algorithm 1, a CPDA can be intuitively explained as follows.
- Each row represents the index of the jth packet of all files and each column represents user . If , then user has cached the jth packet of all files. The condition C1 of Definition 1 therefore implies that each user caches files.
- If is an integer, it means that the jth packet of all files is not stored by user . Then, the XOR of the requested packets indicated by s is generated by the server at time slot s, denoted by . If the set defined in the condition C4 of Definition 2 is where , then is divided into sub-packets, i.e., . Finally, for any , the server sends to relay and relay forwards to its connecting users. The subpacketization is therefore at most . The condition C4 of Definition 2 guarantees that user can receive the whole message since user is connected to each relay in . The condition C3 of Definition 1 guarantees that user can recover its requested packet indicated by s from since it has cached all the other packets in message except its requested one. The occurrence number of integer s in denoted by is the coded caching gain at time slot s since message is useful for users.
- The condition C2 of Definition 1 implies that the number of messages sent by the server is exactly S. If the size of is a constant for each , assume that , and if the number of containing h is a constant for each relay , assume that ; then, we have . The transmission load for each relay is therefore .
Lemma 2.
([15]) Given a CPDA for any positive integers H, r and u with , we have an multiaccess combination network caching scheme with memory ratio and subpacketization . Moreover, if the size of , which is defined in Definition 2, is a constant for each and if the number of containing h is a constant for each relay , the transmission load for each relay is .
In a PDA, a star not contained in any subarray shown as (1) in C3-b of Definition 1 is called useless. The authors in [19] pointed out that useless stars not only make no contribution to reducing the transmission load but also result in high subpacketization. If each column of a PDA has useless stars, the authors in [19] improved the scheme in [16] by deleting all the useless stars and using an maximum distance separable (MDS) code [20] for some prime power q, and came up with a new coded caching scheme with a smaller transmission load and subpacketization than the original scheme in [16] for the same number of users and memory ratio. In fact, this idea also works for the multiaccess combination network caching system.
Lemma 3.
Given a CPDA for any positive integers H, r and u with , assume that there exist useless stars in each column of . Then, we have an multiaccess combination network caching scheme with memory ratio and subpacketization . If the size of , which is defined in Definition 2, is a constant for each integer and if the number of containing h is a constant for each relay , the transmission load for each relay is .
Proof.
Assume that is a CPDA wherein each column has useless stars, delete the useless stars in each column and we obtain a new array . Clearly each column of has blanks, stars and integers. Based on , we modify the placement strategy in Algorithm 1 as follows: the server divides each file into equal-sized packets and then encodes them using an MDS code for some prime power q. The resulting encoded packets are denoted by , , …, for each file where . Using the caching strategy in Lines 3–5 in Algorithm 1, each user caches . Clearly, the memory ratio of each user is . Now, let us consider its subpacketization and transmission load for each relay. For any request vector in the delivery phase, we use the same delivery strategy as in Algorithm 1. Then, each user can obtain exactly required coded packets. From the property of an MDS code, each user can recover its requested file. Since the size of is a constant for each integer and the number of containing h is a constant for each relay , the transmission load for each relay is . □
Remark 1.
Given a CPDA , if each column of has useless stars, then the scheme in Lemma 3 has a smaller memory ratio and subpacketization than the scheme in Lemma 2 since and always hold for any positive integer . It is worth noting that for the scheme in Lemma 3, the operation field must be ; hence, the size of each packet must be approximately bits in length. This implies that the size of each file in the server must be more than bits.
3. The Schemes for the Multiaccess Combination Network
In this section, we will propose three coded caching schemes for the multiaccess combination network caching system. The first one is directly obtained from the idea in [5]. The second one is from a direct construction of CPDA via combinatorial design theory and the third one is from a hybrid construction of CPDA based on the CPDA directly constructed before and the MN PDA.
3.1. ZY Scheme
Since the scheme in [5] can be used to deal with any relay networks with arbitrary topologies, it also works for the multiaccess combination network caching setting. Specifically, from the idea in [5], we can obtain an multiaccess combination network caching scheme as follows. Firstly, the server divides each file into r packets and then encodes them into H coded packets by an MDS code for some prime power q. Denote the hth coded packet of all files by . It is worth noting that the size of each coded packet is bits. Secondly, for each relay h, by taking the hth coded packet of all files as the file library and using the MN scheme, the server sends all required coded signals to relay h, and relay h forwards them to its connecting users. Let , and then each user caches exactly bits since each user is just connected to r relays. Thus, the transmission load for each relay is . That is the following result.
Lemma 4.
(ZY scheme) For any positive integers H, r, u, M and N with and , let , if is an integer, we have an multiaccess combination network caching scheme with subpacketization and transmission load for each relay .
It is easy to verify that the transmission load for each relay of the ZY scheme is approximately of the transmission load of the MN scheme. However, the subpacketization of the ZY scheme is exponential in order with , which may lead to high implementation complexity and infeasibility in reality. Therefore, reducing the subpacketization while slightly increasing the transmission load for each relay as the tradeoff is very meaningful.
3.2. The Direct Scheme
In this section, we propose a direct construction of CPDA by means of combinatorial design theory, which leads to a multiaccess combination network caching scheme with much lower subpacketization than the ZY scheme in Lemma 4.
Construction 1.
For any positive integers H, r, a, ω and λ with and , let the row index set and the column index set be
respectively. An array with , and is defined as
where is defined as
and
Clearly, we have from (3).
Example 2.

When , , , and , the array generated by Construction 1 is shown in Table 1.

Table 1.
The CPDA with , , and .
For instance, when and , since , we have from (5), then from (3) and (4), we have , abbreviated as . It is easy to verify that the array in Table 1 is a CPDA which leads to an multiaccess combination network caching scheme with , memory ratio , subpacketization , and transmission load for each relay . In this case, the subpacketization and transmission load for each relay of the ZY scheme in Lemma 4 are and , respectively.
In general, the array generated by Construction 1 is a CPDA, wherein each column has the same number of useless stars. Hence, from Lemma 3, we have the following result, whose proof could be found in Appendix A.
Theorem 1.
(The direct scheme) For any positive integers H, r, a, ω and λ with and , there exists a CPDA with and , where , . This can lead to an multiaccess combination network caching scheme whose memory ratio, subpacketization and transmission load for each relay are
respectively, where and .
Remark 2.
- When , from Theorem 1, we can obtain an , CPDA which is exactly the strongly coloring PDA in [16] by the fact .
- The row index set in (2) is determined by the value of a. In fact, can be chosen more flexibly. For example, let and for any positive integer , when , and , according to (3)–(5), a CPDA can be obtained, which is shown in Table 2.
 Table 2. The CPDA.
Table 2. The CPDA. - From the proof of Theorem 1 in Appendix A, the scheme from the CPDA generated by Construction 1 omits the coded caching gain among the users who are connected to the same r relays.
3.3. The Hybrid Scheme
From Theorem 1, an multiaccess combination network caching scheme can be obtained. However, it has a limitation of the parameter u, i.e., . In this subsection, we will propose a hybrid construction of CPDA for any parameter u based on a PDA and a CPDA. Let us use an example to illustrate the main idea of the construction.
Example 3.
Given the CPDA with , , , and the PDA as follows,
by replacing each entry in , i.e., where , , with an array , where for any integer x, we can obtain the following CPDA with and .
It is easy to verify that the scheme from creates broadcast opportunities among the users who are connected to the same r relays, since .
Mathematically, the construction is given as follows.
Construction 2.
Suppose that there exists a CPDA , , and a PDA , , , the array , , , is defined as
Let us return to Example 3, where , since , we have from (10); when , since and , we have from (10).
By Construction 2, we have the following result, whose proof could be found in Appendix B.
Theorem 2.
Given a CPDA and a PDA , there always exists a CPDA . If each set for (denoted by ) where has the same size μ and the number of containing h is a constant for each , and if there are useless stars in each column of , then leads to an multiaccess combination network caching scheme with memory ratio , subpacketization and transmission load for each relay .
From Theorem 2, the following result can be obtained based on the CPDA in Theorem 1 and the MN PDA for any with .
Theorem 3.
(The hybrid scheme) For any positive integers H, r, a, ω, λ, and with , and , there exists an multiaccess combination network caching scheme, whose memory ratio, subpacketization and transmission load for each relay are
respectively, where , , and .
4. Performance Analysis
In this section, we compare the direct scheme in Theorem 1 and the hybrid scheme in Theorem 3 with the ZY scheme in Lemma 4 and the naive scheme of repeatedly using the scheme in [19] (referred to as the naive scheme).
4.1. Analytic Comparison of the Direct Scheme and the Hybrid Scheme with ZY Scheme
Since it is difficult to give an analytic comparison of the direct scheme and the hybrid scheme with the ZY scheme for general parameters and , we focus on the case of . In this case, the memory ratio, subpacketization and transmission load for each relay of the direct scheme are
respectively, from (6)–(8); and from (11)–(13). The hybrid scheme has a memory ratio, subpacketization and transmission load for each relay as follows,
While the ZY scheme has a subpacketization and transmission load for each relay as follows,
Therefore, we have
and
when H is large enough. Furthermore, we have
Clearly, for the direct scheme and the hybrid scheme, the transmission load for each relay is just multiplied while the subpacketization is exponentially reduced compared to the ZY scheme. Moreover, it is easy to verify that and , i.e., the growth of multiple transmission loads for each relay is much less than the reduction exponent of the subpacketization in the direct scheme and hybrid scheme.
4.2. Numerical Comparison
The numerical comparison of the direct scheme and the hybrid scheme with the ZY scheme is given in Table 3. It is easy to see from Table 3 that and , which coincides with the analytic comparison.

Table 3.
Numerical comparison of the direct scheme and the hybrid scheme when with the ZY scheme.
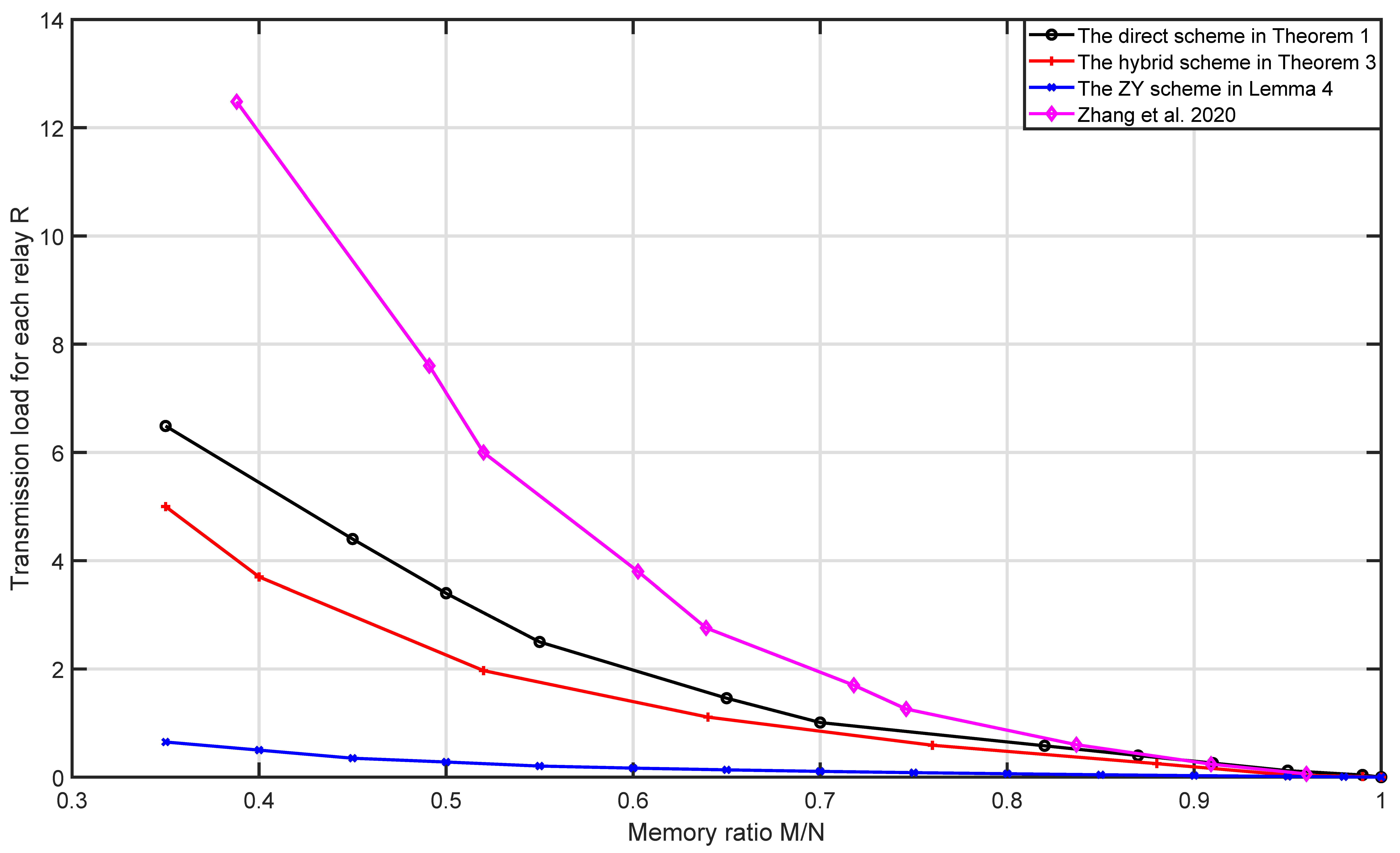
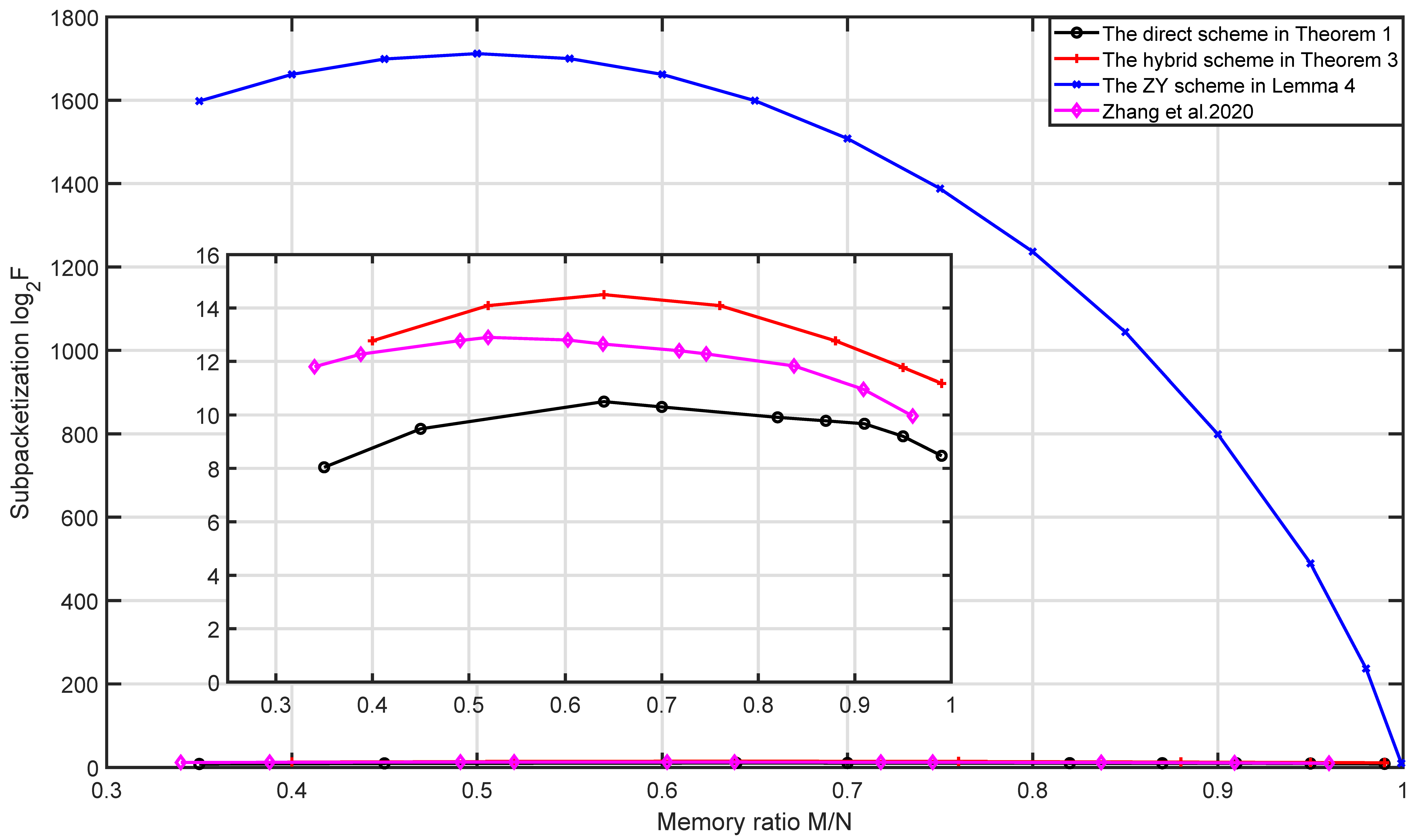
Finally, when , , and , the memory–load and memory–subpacketization tradeoffs are given in Figure 2. From Figure 2, we can see that for the same number of users and memory ratio, the schemes with transmission load for each relay from small to large are the ZY scheme, the hybrid scheme, the direct scheme and the naive scheme. This is because ZY scheme fully utilizes the multicast opportunities among the users who are connected to the same relay, then its coded caching gain is the largest, so it has the minimum transmission load for each relay; the direct scheme and the naive scheme only utilize the multicast opportunities among the users who are connected to different sets of r relays, while omitting the multicast opportunities among the users who are connected to the same r relays; however, the direct scheme more efficiently utilizes the multicast opportunities among the users who are connected to different sets of r relays than the naive scheme, so the transmission load for each relay of the direct scheme is lower than that of the naive scheme; the hybrid scheme not only utilizes the multicast opportunities among the users who are connected to different sets of r relays as the direct scheme, but also utilizes the multicast opportunities among the users who are connected to the same r relays, so its transmission load for each relay is lower than that of the direct scheme. From Figure 2, we can see that for the same number of users and memory ratio, the schemes with subpacketization from small to large are the direct scheme, the naive scheme, the hybrid scheme and the ZY scheme. Therefore, the direct scheme and the hybrid scheme have significant advantages in subpacketization compared with the ZY scheme and have significant advantages in transmission load for each relay compared with the naive scheme. Moreover, the subpacketization of the direct scheme is lower than that of the naive scheme.
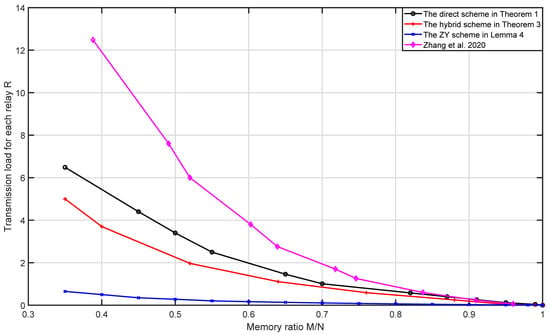
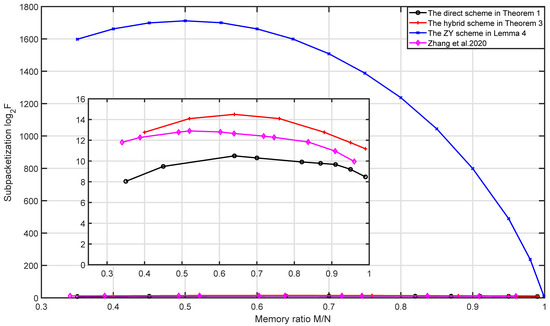
Figure 2.
Comparison of the direct scheme and the hybrid scheme with the ZY scheme and the naive scheme when , , .
5. Conclusions
In this paper, we extended a traditional combination network to an multiaccess combination network, where each r relay connects u users jointly, and proposed three schemes for such a network, i.e., the ZY scheme, the direct scheme and the hybrid scheme. The transmission load for each relay of ZY scheme obtained from the idea in [5] is approximately of the transmission load of MN scheme, but its subpacketization exponentially increases with the number of users. The direct scheme obtained by a direct construction of CPDA has significant advantages in subpacketization compared with the ZY scheme, whereas the parameter u must be a combinational number. The hybrid scheme obtained by a hybrid construction of CPDA works for the arbitrary parameter u as well as has significant advantages in subpacketization compared with the ZY scheme. In addition, the direct scheme and the hybrid scheme have significant advantages in transmission load for each relay compared with the naive scheme, which is obtained by repeatedly using the scheme in [19] u times. Moreover, the subpacketization of the direct scheme is lower than that of the naive scheme.
It is worth noting that the hybrid construction is based on a given CPDA and PDA and the memory ratio of the resulting CPDA is greater than that of the original CPDA. It is of great significance to look for a direct construction of CPDA which works for the arbitrary parameter u.
Author Contributions
Conceptualization, L.H., J.W., M.C., Q.D. and B.Z.; methodology, L.H. and M.C.; validation, L.H. and M.C.; formal analysis, L.H. and J.W.; investigation, L.H. and J.W.; data curation, L.H.; writing—original draft preparation, L.H. and M.C.; writing—review and editing, L.H., M.C. and J.W.; supervision, M.C., J.W., Q.D. and B.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the Natural Science Foundation of China under Grant (No.62061004, No.62076214), the Guangxi Natural Science Foundation (No.2021JJD170057, No.2021JJB110029, No.2021JJD170045), and in part by the Guangxi Bagui Scholar Teams for Innovation and Research Project, and the Guangxi Talent Highland Project of Big Data Intelligence and Application.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| MN | Maddah-Ali and Niesen |
| ZY | Zewail and Yener scheme |
| PDA | Placement Delivery Array |
| CPDA | Combinatorial Placement Delivery Array |
Appendix A. Proof of Theorem 1
Proof.
Let the array generated by Construction 1 be where and . For any nonstar entry occurring in , there exists some and such that . Let where is the subset of such that for each and is the subset of such that for each . Let , then since . In addition, and . This implies that . Let and , then .
We will then prove that the array satisfies the conditions of Definition 2. Let us consider C1 of Definition 1 first. For any column label , without loss of generality, assume that satisfying and . Let with . From (3), there are
vectors satisfying , where is the number of subvectors satisfying ; is the number of subvectors satisfying ; and is the number of subvectors satisfying . Thus, there are stars in each column. Therefore, the condition C1 holds.
For any two distinct entries, say and , assume that . Denote
If , we have from (3). Then, we have since
This contradicts our hypothesis: it implies that for any r-relay set , each non-star entry in occurs at most once in the columns of where and . Thus, the multicast opportunities among the users who are connected to the same r relays are not utilized. We therefore have , and then there must exist two distinct integers, say i, , satisfying and . Without loss of generality, assume that and . From Construction 1, we have and . From (3)–(5), we have and . Then, and hold since . We therefore have from (3). Clearly, holds. Thus, the condition C3 of Definition 1 holds.
Furthermore, this implies that each useful star satisfies . In other words, each star satisfying is useless. Similarly to (A1), there are exactly vectors satisfying , where and . Deleting the useless stars, there are exactly stars in each column.
For any non-star entry occurring in , assume that ; from Construction 1, we have , , for each and for each . Since where is the subset of such that for each , and is the subset of , such that for each , we have . Then, since and . Thus, and since . Since and , we have .
For any and for each vector with wt, let us consider any possible coordinate sets and such that (1) each coordinate of is zero; (2) each coordinate of is one; and (3) and . Let . We will then prove that occurs in . Without loss of generality, assume that , and , and . That is,
Define
It is easy to check that for any , we have , and there is an H-dimensional vector f defined as
satisfying , then , and . Consequently, we have by Construction 1.
Furthermore, appears times in . Since the intersection of any element of and any element of is empty, we have . This implies that the set . Recall that is the intersection of the first coordinate of all column labels satisfying that appears in column , i.e., , where is the set of relays which connect user . The condition C4 of Definition 2 holds.
From the above analysis, there are
different non-star entries in . The condition C2 of Definition 1 holds.
Hence, is a CPDA with the parameters in Theorem 1. For each non-star entry in , since , we have , which is a constant. We will then prove that for each relay , the number of containing h is also a constant. In fact, the number of containing relay h is exactly
which is also a constant. From Lemma 3, Theorem 1 is proved. □
Appendix B. Proof of Theorem 2
Proof.
Firstly, we will prove that the array generated by Construction 2 is a , , CPDA. Clearly, is a array. Furthermore, each column of has stars since each column of has stars and each column of has stars. There are integers in since there are integers in and there are integers in . Conditions C1 and C2 of Definition 1 hold.
For any two distinct entries and , if , then all entries are integers and from (10). Since and , we have and . Then, from the definition of PDA and CPDA, we have that (1) either or holds; (2) either or holds. Since and are two distinct entries, and cannot hold simultaneously, which implies that either or holds. Consequently, we have from (10). The condition C3 of Definition 1 holds.
For any , assume that s appears times in , say
then
from (10). Assume that for each , we have . Since is a CPDA, from condition C4 of Definition 2, the set is not empty. Then, is not empty and the condition C4 of Definition 2 holds. Hence, the array is a CPDA.
Secondly, if is a constant for each and the number of containing h is a constant for each , say for each , then we have for each where and for each . If there are useless stars in each column of , there are useless stars in each column of . From Lemma 3, leads to an multiaccess combination network caching scheme with memory ratio , subpacketization and transmission load for each relay .□
References
- Maddah-Ali, M.A.; Niesen, U. Fundamental Limits of Caching. IEEE Trans. Informat. Theory 2014, 60, 2856–2867. [Google Scholar] [CrossRef] [Green Version]
- Wan, K.; Tuninetti, D.; Piantanida, P. An index coding approach to caching with uncoded cache placement. IEEE Trans. Informat. Theory 2020, 66, 1318–1332. [Google Scholar] [CrossRef]
- Yan, Q.; Cheng, M.; Tang, X.; Chen, Q. On the placement delivery array design for centralized coded caching scheme. IEEE Trans. Informat. Theory 2017, 63, 5821–5833. [Google Scholar] [CrossRef] [Green Version]
- Ji, M.; Wong, M.F.; Tulino, A.M.; Llorca, J.; Caire, G.; Effros, M.; Langberg, M. On the fundamental limits of caching in combination networks. In Proceedings of the 2015 IEEE 16th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC), Stockholm, Sweden, 28 June–1 July 2015; pp. 695–699. [Google Scholar] [CrossRef]
- Zewail, A.A.; Yener, A. Coded caching for combination networks with cache-aided relays. In Proceedings of the 2017 IEEE ISIT, Aachen, Germany, 25–30 June 2017; pp. 2433–2437. [Google Scholar] [CrossRef]
- Wan, K.; Ji, M.; Piantanida, P.; Tuninetti, D. On the Benefits of Asymmetric Coded Cache Placement in Combination Networks with End-User Caches. In Proceedings of the 2018 IEEE ISIT, Vail, CO, USA, 17–22 June 2018; pp. 1550–1554. [Google Scholar] [CrossRef] [Green Version]
- Wan, K.; Ji, M.; Piantanida, P.; Tuninetti, D. Caching in Combination Networks: Novel Multicast Message Generation and Delivery by Leveraging the Network Topology. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar] [CrossRef] [Green Version]
- Wan, K.; Ji, M.; Piantanida, P.; Tuninetti, D. Combination Networks with Caches: Novel Inner and Outer Bounds with Uncoded Cache Placement. arXiv:1701.06884v1 [cs.IT] 24 Jan 2017. Available online: https://arxiv.org/abs/1701.06884v1 (accessed on 11 March 2022).
- Wan, K.; Tuninetti, D.; Piantanida, P.; Ji, M. On Combination Networks with Cache-aided Relays and Users. In Proceedings of the WSA 2018: 22nd International ITG Workshop on Smart Antennas, Bochum, Germany, 14–16 March 2018; pp. 1–7. [Google Scholar]
- Wan, K.; Tuninetti, D.; Ji, M.; Piantanida, P. A Novel Asymmetric Coded Placement in Combination Networks with End-User Caches. In Proceedings of the 2018 Information Theory and Applications Workshop (ITA), San Diego, CA, USA, 11–16 February 2018; pp. 1–5. [Google Scholar] [CrossRef] [Green Version]
- Elkordy, A.R.; Motahari, A.S.; Nafie, M.; G¨¹nd¨¹z, D. Cache-Aided Combination Networks With Interference. IEEE Trans. Wirel. Commun. 2020, 19, 148–161. [Google Scholar] [CrossRef]
- Yan, Q.; Wigger, M.; Yang, S. Placement Delivery Array Design for Combination Networks with Edge Caching. In Proceedings of the 2018 IEEE ISIT, Vail, CO, USA, 17–22 June 2018; pp. 1555–1559. [Google Scholar] [CrossRef] [Green Version]
- Cheng, M.; Li, J.; Tang, X.; Wei, R. Linear Coded Caching Scheme for Centralized Networks. IEEE Trans. Informat. Theory 2021, 67, 1732–1742. [Google Scholar] [CrossRef]
- Cheng, M.; Wang, J.; Zhong, X.; Wang, Q. A Framework of Constructing Placement Delivery Arrays for Centralized Coded Caching. IEEE Trans. Informat. Theory 2021, 67, 7121–7131. [Google Scholar] [CrossRef]
- Cheng, M.; Li, Y.; Zhong, X.; Wei, R. Improved Constructions of Coded Caching Schemes for Combination Networks. IEEE Trans. Commun. 2020, 68, 5965–5975. [Google Scholar] [CrossRef]
- Yan, Q.; Tang, X.; Chen, Q.; Cheng, M. Placement delivery array design through strong edge coloring of bipartite graphs. IEEE Commun. Lett. 2018, 22, 236–239. [Google Scholar] [CrossRef] [Green Version]
- Quinn, J.J.; Benjamin, A.T. Strong chromatic index of subset graphs. J. Graph Theory 1997, 24, 267–273. [Google Scholar] [CrossRef]
- Zhang, Q.; Zheng, L.; Cheng, M.; Chen, Q. On the Dynamic Centralized Coded Caching Design. IEEE Trans. Commun. 2020, 68, 2118–2128. [Google Scholar] [CrossRef] [Green Version]
- Zhang, M.; Cheng, M.; Wang, J.; Zhong, X.; Chen, Y. Improving Placement Delivery Array Coded Caching Schemes With Coded Placement. IEEE Access 2020, 8, 217456–217462. [Google Scholar] [CrossRef]
- van Lint, J.H. Introduction to Coding Theory; Springer: Berlin/Helderburg, Germany, 1999. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).