Attention Paid to Privacy Policy Statements
Abstract
1. Private Information
2. Privacy Policy Statement
Ignorance of Privacy Policy Statements
3. Protective Behaviour
4. Theory of Planned Behaviour
TPB Components
5. Privacy Calculus
6. Research
6.1. Materials and Methods
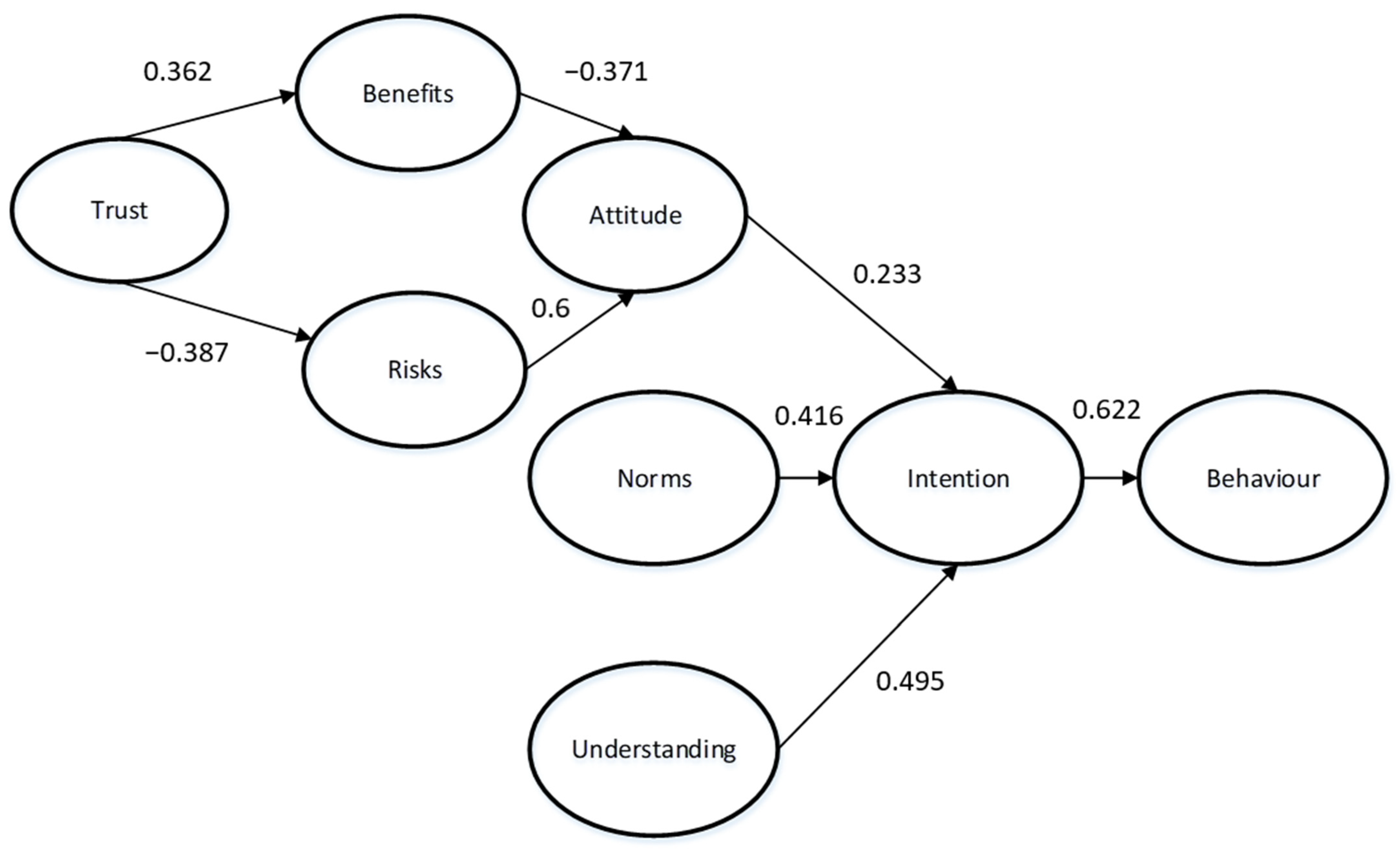
6.2. Results
7. Discussion
8. Contributions and Implications
9. Limitations and Future Research
10. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Culnan, M.J. Policy to avoid a privacy disaster. J. Assoc. Inf. Syst. 2019, 20. [Google Scholar] [CrossRef]
- Janssen, M.; van der Voort, H.; Wahyudi, A. Factors influencing big data decision-making quality. J. Bus. Res. 2017, 70, 338–345. [Google Scholar] [CrossRef]
- Erevelles, S.; Fukawa, N.; Swayne, L. Big data consumer analytics and the transformation of marketing. J. Bus. Res. 2016, 69, 897–904. [Google Scholar] [CrossRef]
- Janssen, M.; van den Hoven, J. Big and open linked data (BOLD) in government: A challenge to transparency and privacy? Gov. Inf. Q. 2015, 32, 363–368. [Google Scholar] [CrossRef]
- TRUSTe Smart Privacy for Smartphones: Understanding and Delivering the Protection Consumers Want. 2011. Available online: www.truste.com (accessed on 24 March 2021).
- Janssen, M.; Kuk, G. The challenges and limits of big data algorithms in technocratic governance. Gov. Inf. Q. 2016, 33, 371–377. [Google Scholar] [CrossRef]
- Morey, T.; Forbath, T.; Schoop, A. Customer data: Designing for transparency and trust. Harv. Bus. Rev. 2015, 93, 96–105. [Google Scholar]
- Drinkwater, D. Does a Data Breach Really affect Your Firm’s Reputation. Available online: http://www.csoonline.com/article/3019283/data-breach/does-a-data-breach-reallyaffect-your-firm-s-reputation.html2016 (accessed on 24 March 2021).
- Bansal, G.; ‘Mariam’ Zahedi, F.; Gefen, D. The Role of Privacy Assurance Mechanisms in Building Trust and the Moderating Role of Privacy Concern. Eur. J. Inf. Syst. 2015, 24, 624–644. [Google Scholar] [CrossRef]
- Dinev, T.; Hart, P. An extended privacy calculus model for e-commerce transactions. Inf. Syst. Res. 2006, 17, 61–80. [Google Scholar] [CrossRef]
- Joinson, A.N.; Reips, U.-D.; Buchanan, T.; Schofield, C.B.P. Privacy, trust, and self-disclosure online. Hum.-Comput. Interact. 2010, 25, 1–24. [Google Scholar] [CrossRef]
- Xu, H.; Dinev, T.; Smith, J.; Hart, P. Information privacy concerns: Linking individual perceptions with institutional privacy assurances. J. Assoc. Inf. Syst. 2011, 12, 798–824. [Google Scholar] [CrossRef]
- Chua, H.N.; Herbland, A.; Wong, S.F.; Chang, Y. Compliance to personal data protection principles: A study of how organizations frame privacy policy notices. Telemat. Inform. 2017, 34, 157–170. [Google Scholar] [CrossRef]
- Liu, C.; Arnett, K. An examination of privacy policies in Fortune 500 Web sites. Mid-Am. J. Bus. 2002, 17, 13–22. [Google Scholar] [CrossRef]
- Cate, F.H. The failure of fair information practice principles. In Consumer Protection in the Age of the Information Economy; Winn, J.K., Ed.; Ashgate Publishing: Surrey, UK, 2006; pp. 343–379. [Google Scholar]
- Adler, R.S. The last best argument for eliminating reliance from express warranties: “Real-world” consumers don’t read warranties. South Carol. Law Rev. 1994, 45, 429. [Google Scholar]
- Obar, J.A.; Oeldorf, H.A. The biggest lie on the Internet: Ignoring the privacy policies and terms of service policies of social networking services. Inf. Commun. Soc. 2018, 23, 128–147. [Google Scholar] [CrossRef]
- Federal Trade Commission. Protecting Consumer Privacy in an Era of Rapid Change. Federal Trade Commission Report. 2012. Available online: https://www.ftc.gov/reports/protecting-consumer-privacy-era-rapid-change-recommendations-businesses-policymakers (accessed on 24 March 2021).
- Bakos, Y.; Marotta-Wurgler, F.; Trossen, D.R. Does anyone read the fine print? Consumer attention to standard-form contracts. J. Leg. Stud. 2014, 43, 1–35. [Google Scholar] [CrossRef]
- Barocas, S.; Nissenbaum, H.F. On Notice: The Trouble with Notice and Consent. Proceedings of the Engaging Data Forum: The First International Forum on the Application and Management of Personal Electronic Information. Available online: https://ssrn.com/abstract=2567409 (accessed on 24 March 2021).
- Nissenbaum, H. Privacy in Context: Technology, Policy, and the Integrity of Social Life; Bibliovault OAI Repository, the University of Chicago Press: Chicago, IL, USA, 2010. [Google Scholar]
- Cate, F.H.; Mayer-Schönberger, V. Notice and consent in a world of Big Data. Int. Data Priv. Law 2013, 3, 67–73. [Google Scholar] [CrossRef]
- Meinert, D.; Peterson, D.; Criswell, J.; Crossland, M. Privacy policy statements and consumer willingness to provide personal information. JECO 2006, 4, 1–17. [Google Scholar] [CrossRef]
- Phelps, J.; Glen, N.; Elizabeth, F. Privacy Concerns and Consumer Willingness to Provide Personal Information. J. Public Policy Mark. 2000, 19, 27–41. [Google Scholar] [CrossRef]
- Tsai, J.Y.; Serge, E.; Lorrie, C.; Alessandro, A. The Effect of Online Privacy Information on Purchasing Behavior: An Experimental Study. Inf. Syst. Res. 2011, 22, 254–268. [Google Scholar] [CrossRef]
- Tang, Z.; Hu, Y.J.; Michael, D.S. Gaining Trust Through Online Privacy Protection: Self-Regulation, Mandatory Standards, or Caveat Emptor. J. Manag. Inf. Syst. 2008, 24, 153–173. [Google Scholar] [CrossRef]
- Calo, R. Against Notice Skepticism in Privacy (and Elsewhere). Notre Dame Law Rev. 2012, 87, 1027–1072. [Google Scholar]
- Martin, K. Transaction Costs, Privacy, and Trust: The Laudable Goals and Ultimate Failure of Notice and Choice to Respect Privacy Online. First Monday 2013, 18. Available online: http://firstmonday.org/ojs/index.php/fm/article/view/4838/3802 (accessed on 11 August 2020). [CrossRef]
- Sheehan, K.B. In Poor Health: An Assessment of Privacy Policies at Direct-to-Consumer Web Sites. J. Public Policy Mark. 2005, 24, 273–283. [Google Scholar] [CrossRef]
- Milner, C.; Culnan, M.J.; Greene, H. Longitudinal Assessment of Online Privacy Notice Readability. J. Public Policy Mark. 2006, 25, 238–249. [Google Scholar] [CrossRef]
- Nemati, H.R.; Van Dyke, T.P. Do Privacy Statements Really Work? The Effect of Privacy Statements and Fair Information Practices on Trust and Perceived Risk in E-Commerce. Int. J. Inf. Secur. Priv. 2009, 3, 45–64. [Google Scholar] [CrossRef][Green Version]
- Martin, K. Privacy Notices as Tabula Rasa: An Empirical Investigation into how Complying with a Privacy Notice is Related to Meeting Privacy Expectations Online. J. Public Policy Mark. 2015, 34, 210–227. [Google Scholar] [CrossRef]
- Lebek, B.; Uffen, J.; Neumann, M.; Hohler, B.H.; Breitner, M. Information security awareness and behavior: A theory-based literature review. Manag. Res. Rev. 2014, 37, 1049–1092. [Google Scholar] [CrossRef]
- Ajzen, I. The theory of planned behavior. Organ. Behav. Hum. Decis. Processes. 1991, 50, 179–211. [Google Scholar] [CrossRef]
- Ajzen, I. The theory of planned behavior: Reactions and reflections. Psychol. Health 2011, 26, 1113–1127. [Google Scholar] [CrossRef] [PubMed]
- Fishbein, M.; Ajzen, I. Predicting and Changing Behavior: The Reasoned Action; Taylor & Francis: Abingdon, UK, 2010. [Google Scholar]
- Carter, S.; Yeo, A.C.-M. Mobile apps usage by Malaysian business undergraduates and postgraduates: Implications for consumer behaviour theory and marketing practice. Int. Res. 2016, 26, 733–757. [Google Scholar] [CrossRef]
- Cheung, M.F.Y.; To, W.M. Service co–creation in social media: An extension of 649 the theory of planned behavior. Computers Hum. Behav. 2016, 65, 260–266. [Google Scholar] [CrossRef]
- Jiang, C.; Zhao, W.; Sun, X.; Zhang, K.; Zheng, R.; Qu, W. The effects of the self and social identity on the intention to microblog: An extension of the theory of planned behavior. Comput. Human Behav. 2016, 64, 754–759. [Google Scholar] [CrossRef]
- Kim, E.; Lee, J.A.; Sung, Y.; Choi, S.M. Predicting selfie-posting behavior on social networking sites: An extension of theory of planned behavior. Comput. Human Behav. 2016, 62, 116–123. [Google Scholar] [CrossRef]
- Li, M.; Dong, Z.Y.; Chen, X. Factors influencing consumption experience of mobile commerce: A study from experiential view. Internet Res. 2012, 22, 120–141. [Google Scholar] [CrossRef]
- Fishbein, M.; Ajzen, I. Belief, Attitude, Intention, and Behavior: An Introduction to Theory and Research; Addison-Wesley: Boston, MA, USA, 1975. [Google Scholar]
- Masur, P.K.; Scharkow, M. Disclosure management on social network sites: Individual privacy perceptions and user-directed privacy strategies. Soc. Media. Soc. 2016, 2. [Google Scholar] [CrossRef]
- Culnan, M.J.; Armstrong, P.K. Information privacy concerns, procedural fairness, and impersonal trust: An empirical investigation. Organ. Sci. 1999, 1, 104–115. [Google Scholar] [CrossRef]
- Trepte, S.; Reinecke, L.; Ellison, N.B.; Quiring, O.; Yao, M.Z.; Ziegele, M. A Cross-Cultural Perspective on the Privacy Calculus. Soc. Media Soc. 2017, 3, 1. [Google Scholar] [CrossRef]
- Phelps, J.; D’Souza, G.; Nowak, G. Antecedents and consequences of consumer privacy concerns: An empirical investigation. J. Interact. Mark. 2001, 15, 2–17. [Google Scholar] [CrossRef]
- Cases, A.; Fournier, C.; Dubois, P.; Tanner, J., Jr. Web site spill over to e-mail campaigns: The role of privacy, trust and shoppers attitudes. J. Bus. Res., 2010, 63, 993–999. [Google Scholar] [CrossRef]
- Chellappa, R.K.; Sin, R.G. Personalization versus privacy: An empirical examination of the online consumer’s dilemma. Inf. Technol. Manag. 2005, 6, 181–202. [Google Scholar] [CrossRef]
- Turow, J.; Nir, L. The Internet and the Family 2000: The View from Parents, the View from Kids; The Annenberg Public Policy Center: Philadelphia, PA, USA, 2000. [Google Scholar]
- Youn, S. Teenagers’ perception of online privacy and coping behaviors: A risk-benefit appraisal approach. J. Broadcast. Electron. Media 2005, 1, 86–110. [Google Scholar] [CrossRef]
- Hsu, M.-H.; Kuo, F.-Y. The effect of organization-based self-esteem and deindividuation in protecting personal information privacy. J. Bus. Ethics 2003, 4, 305–320. [Google Scholar] [CrossRef]
- LaRose, R.; Rifon, N.J. Promoting I-safety: Effects of privacy warnings and privacy seals on risk assessment and online privacy behaviour. J. Consum. Aff. 2007, 1, 127–149. [Google Scholar] [CrossRef]
- Anderson, C.L.; Agarwal, R. The digitization of healthcare: Boundary risks, emotion, and consumer willingness to disclose personal health information. Inf. Syst. Res. 2011, 22, 469–490. [Google Scholar] [CrossRef]
- Bansal, G.; Zahedi, F.; Gefen, D. The impact of personal dispositions on information sensitivity, privacy concern and trust in disclosing health information online. Decis. Support Syst. 2010, 49, 138–150. [Google Scholar] [CrossRef]
- Malhotra, N.K.; Kim, S.S.; Agarwal, J. Internet users’ information privacy concerns (IUIPC): The construct, the scale, and a causal model. Inf. Syst. Res. 2004, 15, 336–355. [Google Scholar] [CrossRef]
- Krasnova, H.; Veltri, N.F.; Gunther, O. Self-disclosure and privacy calculus on social networking sites: The role of culture. Bus. Inf. Syst. Eng. 2012, 4, 127–135. [Google Scholar] [CrossRef]
- Dinev, T.; Hart, P. Privacy concerns and levels of information exchange: An empirical investigation of intended e-services. E–Serv. J. 2006, 3, 25–59. [Google Scholar] [CrossRef]
- Davis, F.D.; Bagozzi, R.P.; Warshaw, P.R. User acceptance of computer technology: A comparison of two theoretical models. Manag. Sci. 1989, 8, 982–1003. [Google Scholar] [CrossRef]
- Butler, J.K. Toward understanding and measuring the conditions of trust: Evolution of the conditions of trust inventory. J. Manag. 1991, 17, 643–663. [Google Scholar] [CrossRef]
- Mayer, R.C.; Davis, J.H.; Schoorman, F.D. An integrative model of organizational trust. Acad. Manag. Rev. 1995, 20, 709–734. [Google Scholar] [CrossRef]
- Doney, P.M.; Cannon, J.P. An examination of the nature of trust in buyer-seller relationships. J. Mark. 1997, 61, 35–51. [Google Scholar]
- Flavian, C.; Guinaliu, M. Consumer trust, perceived security, and privacy policy: Three basic elements of loyalty to a website. Ind. Manag. Data Syst. 2006, 106, 601–620. [Google Scholar] [CrossRef]
- McKinsey Company. TrueGen: Generation Z and Its Implications for Companies. Available online: https://www.mckinsey.de/~/media/McKinsey/Industries/Consumer%20Packaged%20Goods/Our%20Insights/True%20Gen%20Generation%20Z%20and%20its%20implications%20for%20companies/Generation-Z-and-its-implication-for-companies.pdf (accessed on 8 March 2021).
- Harris, P.; Rettie, R.; Cheung, C.K. Adoption and usage of m-commerce: A cross-696 cultural comparison of Hong Kong and the United Kingdom. J. Electron. Commer. Res. 2005, 6, 210–224. [Google Scholar]
- Chin, W.W.; Marcolin, B.L.; Newsted, P.R. A partial least squares latent variable modeling approach for measuring interaction effects: Results from a monte carlo simulation study and an electronic–mail emotion/adoption study. Inf. Syst. Res. 2003, 14, 189–217. [Google Scholar] [CrossRef]
- Hansen, J.M.; Levin, M.A. The effect of apathetic motivation on employees’ intentions to use social media for businesses. J. Bus. Res. 2016, 69, 6058–6066. [Google Scholar] [CrossRef]
- Wold, H.O. Soft modeling: The basic design and some extensions. In Systems under Indirect Observations, Part II; Wold, H.O., Jöreskog, K.G., Eds.; Elsevier Science Ltd.: Amsterdam, The Netherlands, 1982; pp. 1–54. [Google Scholar]
- Henseler, J.; Ringle, C.M.; Sinkovics, R.R. The use of partial least squares path modelling in international marketing. In Advances in International Marketing; Sinkovics, R.R., Ghauri, P.N., Eds.; Emerald: Bingley, UK, 2009; pp. 277–319. [Google Scholar]
- Wold, S.; Sjostrom, M.; Eriksson, L. PLS-regression: A basic tool of chemometrics. Chemom. Intell. Lab. Syst. 2001, 58, 109–130. [Google Scholar] [CrossRef]
- Fornell, C.; Larcker, D. A Second Generation of Multivariate Analysis: Classification of Methods and Implications for Marketing Research. Rev. Mark. 1987, 1, 407–450. [Google Scholar]
- Nunnally, J.C.; Ira, H.B. The Assessment of Reliability. Psychom. Theory 1994, 3, 248–292. [Google Scholar]
- Hair, J.; Black, W.; Babin, B.; Anderson, R. Multivariate Data Analysis: A Global Perspective. Pearson 2010. [Google Scholar]
- Smith, J.H.; Milberg, S.J.; Burke, S.J. Information privacy: Measuring individuals’ concerns about organizational practices. MIS Q. 1996, 2, 167–196. [Google Scholar] [CrossRef]
- Mayer, R.C.; Davis, J.H. The effect of the performance appraisal system on trust for management. J. Appl. Psychol. 1999, 1, 123–136. [Google Scholar] [CrossRef]
- Heirman, W.; Walrave, M. Ponnet Predicting Adolescents' Disclosure of Personal Information in Exchange for Commercial Incentives: An Application of an Extended Theory of Planned Behavior. Cyberpsychol. Beha. Soc. Netw. 2013, 16, 81–87. [Google Scholar] [CrossRef]
- Saeri, A.K.; Ogilvie, C.; La Macchia, S.T.; Smith, J.R.; Louis, W.R. Predicting Facebook Users’ Online Privacy Protection: Risk, Trust, Norm Focus Theory, and the Theory of Planned Behavior. J. Soc. Psychol. 2014, 154, 52–369. [Google Scholar] [CrossRef] [PubMed]
- Wang, E.S.T. Effects of Brand Awareness and Social Norms on User-Perceived Cyber Privacy Risk. Int. J. Electron. Commer. 2019, 23, 272–293. [Google Scholar] [CrossRef]
- Hassan, L.M.; Shiu, E.; Shaw, D. Who Says There is an Intention–Behaviour Gap? Assessing the Empirical Evidence of an Intention–Behaviour Gap in Ethical Consumption. J. Bus. Ethics 2016, 136, 219–236. [Google Scholar] [CrossRef]
- Ling, R.; Yttri, B. Hyper-coordination via mobile phone in Norway. In Perpetual Contact; Katz, J.E., Aakhus, M., Eds.; Cambridge University Press: New York, NY, USA, 2002. [Google Scholar]
- Postman, N. Amusing Ourselves to Death: Public Discourse in the Age of Show Business; Penguin: London, UK, 1985; ISBN 0-670-80454-1. [Google Scholar]
- Shrum. The Psychology of Entertainment Media: Blurring the Lines between Entertainment and Persuasion; Routledge: Abingdon, UK, 2012. [Google Scholar]
- Schaub, F.; Balebako, R.; Cranor, L.F. Designing effective privacy notices and controls. IEEE Int. Comput. 2017, 21, 70–77. [Google Scholar] [CrossRef]
- Turow, J.; Hennessy, M.; Draper, N. The Tradeoff Fallacy: How Marketers Are Misrepresenting American Consumers and Opening Them Up to Exploitation; Tech. Rep.; Annenberg School for Communication, University of Pennsylvania: Philadelphia, PA, USA, 2015. [Google Scholar]
- Acquisti, A.; Brandimarte, L.; Loewenstein, G. Privacy and human behavior in the age of information. Science 2015, 347, 509–514. [Google Scholar] [CrossRef] [PubMed]
- Metzger, M.J. Communication privacy management in electronic commerce. J. Comput.-Mediat. Commun. 2007, 12, 335–361. [Google Scholar] [CrossRef]
- Harding, W.T.; Reed, A.J.; Gray, R.L. Cookies and Web Bugs: What They are and How They Work Together. Inf. Syst. Manag. 2001, 18, 17–24. [Google Scholar] [CrossRef]

| Code | Factors |
|---|---|
| Trust | |
| T1 | I would allow an online service to influence an important issue |
| T2 | I would allow an online service to influence my future |
| T3 | I would like to control the functioning of online services |
| T4 | I would let an online service decide an important problem |
| Privacy disclosure risks | |
| R1 | I fear that online services store my personal data |
| R2 | I fear that the policies against errors in private data do not work sufficiently |
| R3 | I fear that my online personal data are used for other purposes than stated |
| R4 | I fear that my online personal data are accessible to unauthorised persons |
| R5 | I fear that by combining various personal data new facts can be revealed |
| R6 | I fear that the automatic functioning of online services may lead to decisions harmful to privacy |
| Privacy disclosure benefits | |
| B1 | I welcome cheaper products and services (discounts) in exchange for private information |
| B2 | I welcome personalised services in exchange for private information |
| B3 | I welcome higher popularity in exchange for private information |
| B4 | I welcome more relevant offers and proposals in exchange for private information |
| Attitude towards reading the privacy policy statements | |
| AT1 | Reading privacy statements is unfavourable—favourable |
| AT2 | Reading privacy statements is useless—useful |
| AT3 | Reading privacy statements is a bad idea—good idea |
| AT4 | Reading privacy statements is unimportant—important |
| AT5 | Reading privacy statements is unnecessary—necessary |
| Subjective norms | |
| NORM1 | People who are important to me think I should read the privacy statements |
| NORM2 | People who are important to me would approve of my reading privacy policy statements |
| NORM3 | People who are important to me read privacy statements |
| NORM4 | The rules of online behaviour that I follow say I should read the privacy policy of online services |
| Understanding the privacy policy statements | |
| UND1 | I understand the privacy policy statements |
| UND2 | I am well informed on the privacy policy statements |
| UND3 | I am ready to invest time into understanding the privacy policy statements |
| UND4 | I am ready to invest effort into understanding the privacy policy statements |
| Intention to read privacy policy statements | |
| INT1 | I plan to read the PPS (privacy policy statements) |
| INT2 | I would like to read the PPS |
| INT3 | I am resolved to read the PPS |
| BEH | I read the privacy policy statements |
| Code | Mean | SD | Cronbach’s Alpha |
|---|---|---|---|
| Trust | 0.882 | ||
| T1 | 2.44 | 1.2 | |
| T2 | 2.67 | 1.66 | |
| T3 | 2.26 | 1.34 | |
| T4 | 2.07 | 1.09 | |
| Risks | 0.895 | ||
| R1 | 3.91 | 1.16 | |
| R2 | 3.74 | 1.03 | |
| R3 | 3.71 | 1.00 | |
| R4 | 3.61 | 1.21 | |
| R5 | 3.37 | 1.27 | |
| R6 | 3.39 | 1.35 | |
| Benefits | 0.869 | ||
| B1 | 2.23 | 1.3 | |
| B2 | 1.98 | 1.2 | |
| B3 | 1.75 | 0.96 | |
| B4 | 2.26 | 1..34 | |
| Attitude | 0.882 | ||
| AT1 | 3.43 | 1.27 | |
| AT2 | 3.86 | 1.22 | |
| AT3 | 4.07 | 1.16 | |
| AT4 | 3.95 | 1.3 | |
| AT5 | 3.94 | 1.27 | |
| Norms | 0..79 | ||
| NORM1 | 2..93 | 0..87 | |
| NORM2 | 3.61 | 1.02 | |
| NORM3 | 2.28 | 0.78 | |
| NORM4 | 3.74 | 0.96 | |
| Understanding | 0.825 | ||
| UND1 | 2.98 | 1.07 | |
| UND2 | 2.82 | 0.99 | |
| UND3 | 2.16 | 1.13 | |
| UND4 | 1.67 | 1.16 | |
| Intention | 0.785 | ||
| INT1 | 3.04 | 0.92 | |
| INT2 | 3.56 | 1.41 | |
| INT3 | 2.81 | 1.12 | |
| Behaviour | |||
| BEH | 2.76 | 1.24 |
| Trust | Risks | Benefits | Attitude | Norms | Understanding | Intention | Behaviour | |
|---|---|---|---|---|---|---|---|---|
| Trust | 0.693 | |||||||
| Risks | −0.387 | 0.655 | ||||||
| Benefits | 0.362 | −0.079 | 0.715 | |||||
| Attitude | −0.385 | 0.629 | −0.418 | 0.68 | ||||
| Norms | −0.354 | 0.213 | −0.034 | 0.34 | 0.605 | |||
| Understanding | −0.059 | 0.127 | 0.072 | 0.153 | 0.169 | 0.656 | ||
| Intention | −0.507 | 0.359 | −0.124 | 0.451 | 0.579 | 0.602 | 0.699 | |
| Behaviour | −0.429 | 0.274 | −0.039 | 0.253 | 0.455 | 0.297 | 0.622 | 1 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sigmund, T. Attention Paid to Privacy Policy Statements. Information 2021, 12, 144. https://doi.org/10.3390/info12040144
Sigmund T. Attention Paid to Privacy Policy Statements. Information. 2021; 12(4):144. https://doi.org/10.3390/info12040144
Chicago/Turabian StyleSigmund, Tomáš. 2021. "Attention Paid to Privacy Policy Statements" Information 12, no. 4: 144. https://doi.org/10.3390/info12040144
APA StyleSigmund, T. (2021). Attention Paid to Privacy Policy Statements. Information, 12(4), 144. https://doi.org/10.3390/info12040144






