Cybersecurity Awareness Framework for Academia
Abstract
:1. Introduction
1.1. Cybersecurity Awareness—Students in Higher Education
1.2. Cybersecurity Awareness—The Public
1.3. Cybersecurity Awareness—Government Initiatives
1.4. Cybersecurity Awareness—Cyberbullying in Schools
1.5. Cybersecurity Awareness—Content Design and Delivery
1.5.1. Infusing Cybersecurity into Computer Science Curricula or Courses
1.5.2. Cybersecurity Awareness—Delivery Methods
Game-Based Learning
1.6. Cybersecurity Awareness Frameworks
1.7. Security Awareness—Best Practices
- Build an institution-wide culture and participation where decision-making and application of cybersecurity best practices become daily pursuits for end-users at all levels.
- Clearly communicate to upper-level management and all end-users that it is critical to understand the value and purpose of cybersecurity education before implementing training.
- Gauge program success by conducting a comparative study to see if there is a reduction in institutional employee-driven cybersecurity incidents over time.
- Conduct regular, ongoing assessments and training so that end-users are given the benefit of regular cybersecurity education, and the opportunity to learn over time and develop new skills.
- Create a clear link between assessments and training.
- Maintain awareness of cybersecurity best practices for end-users by revisiting topics on a regular basis and incorporating ongoing awareness activities; without reinforcement, the institution must regularly rebuild rather than build upon.
- Be consistent in tracking and reporting progress.
- Keep the end-user motivated and engaged by applying gamification techniques that use rewards and positive reinforcement to raise end-user interest and participation and elevate the effectiveness of your program.
2. Method Used to Design the Cybersecurity Awareness Framework
- The infusion of game-based cybersecurity awareness learning and assessment into the curricula of academic institutions using training modules that are part of students’ study plan.
- The incorporation of continuous improvement practices in cybersecurity awareness.
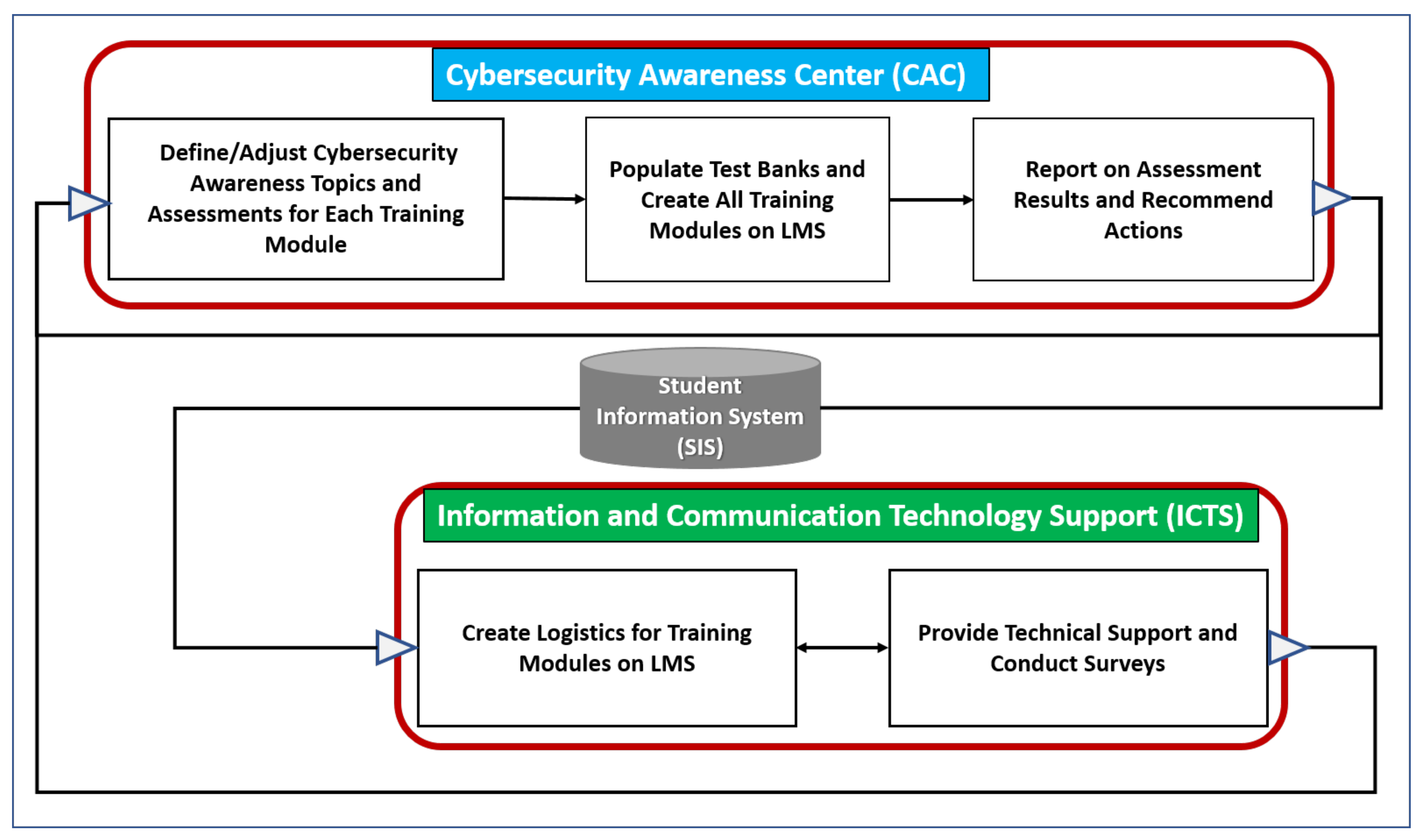
3. Conceptual Cybersecurity Awareness Framework for Academia
- An academic institution’s “information and communication technology support” (ICTS) constituent that manages the learning management system (LMS), coordinates with the student information systems (SISs), provides support during the design of cybersecurity awareness modules by faculty members, and provides support for the assessment of students.
- An academic institution’s “cybersecurity awareness center” (CAC) constituent conducts research on the latest cybersecurity awareness trends and related best practices, defines/adjusts the cybersecurity awareness topics and assessments for training modules, populates test banks and creates all training modules on the learning management system (LMS), reports on the assessment results to the student information system (SIS), and recommends actions for further improvements.
4. The Cybersecurity Awareness Center
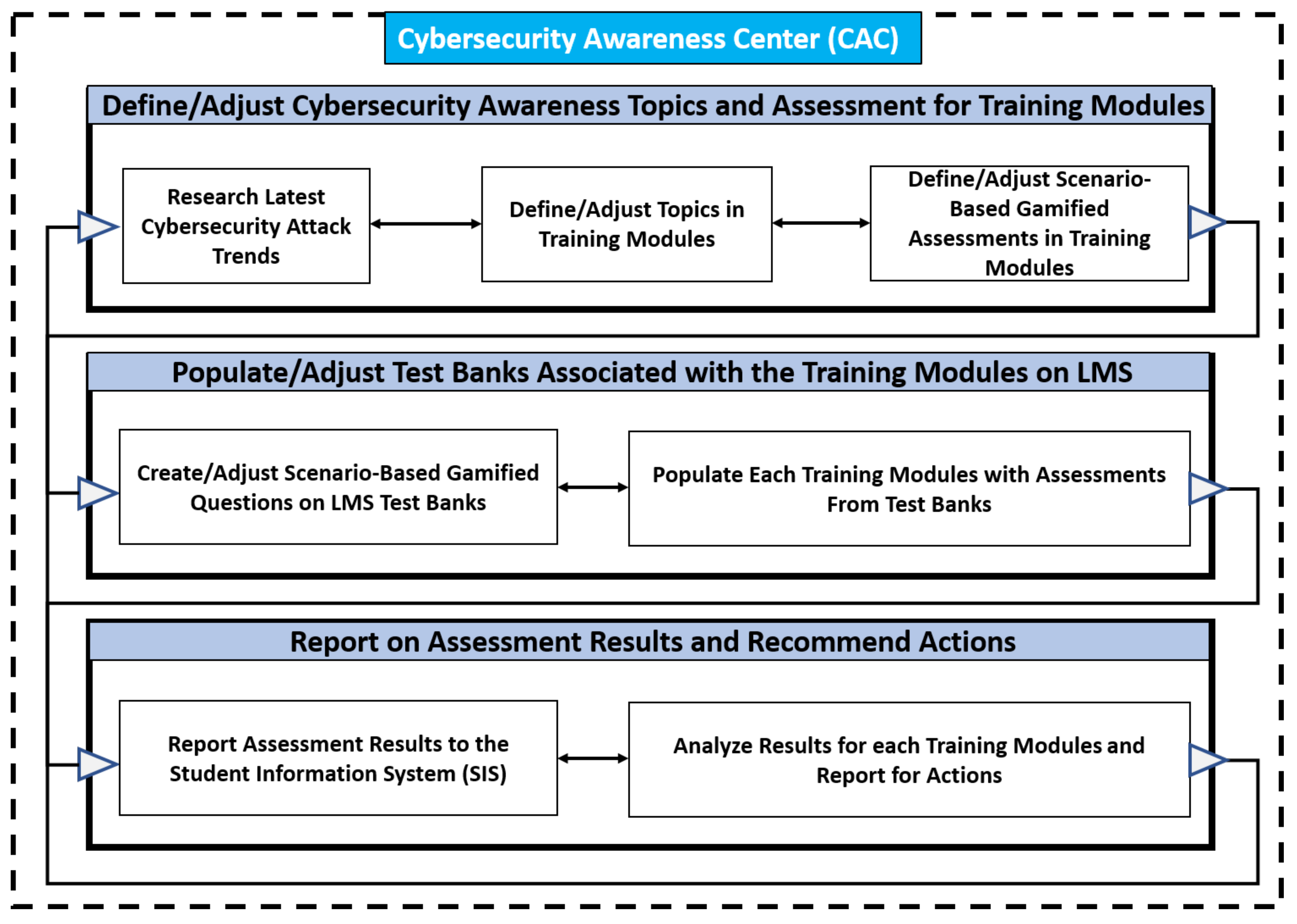
4.1. Phase 1—Define/Adjust Cybersecurity Awareness Topics and Assessments for Training Modules
4.1.1. Phase 1/Activity 1: Research Latest Cybersecurity Attack Trends
4.1.2. Phase 1/Activity 2: Define/Adjust Topics in Training Modules
Cybersecurity Awareness Training Module Design Recommendation
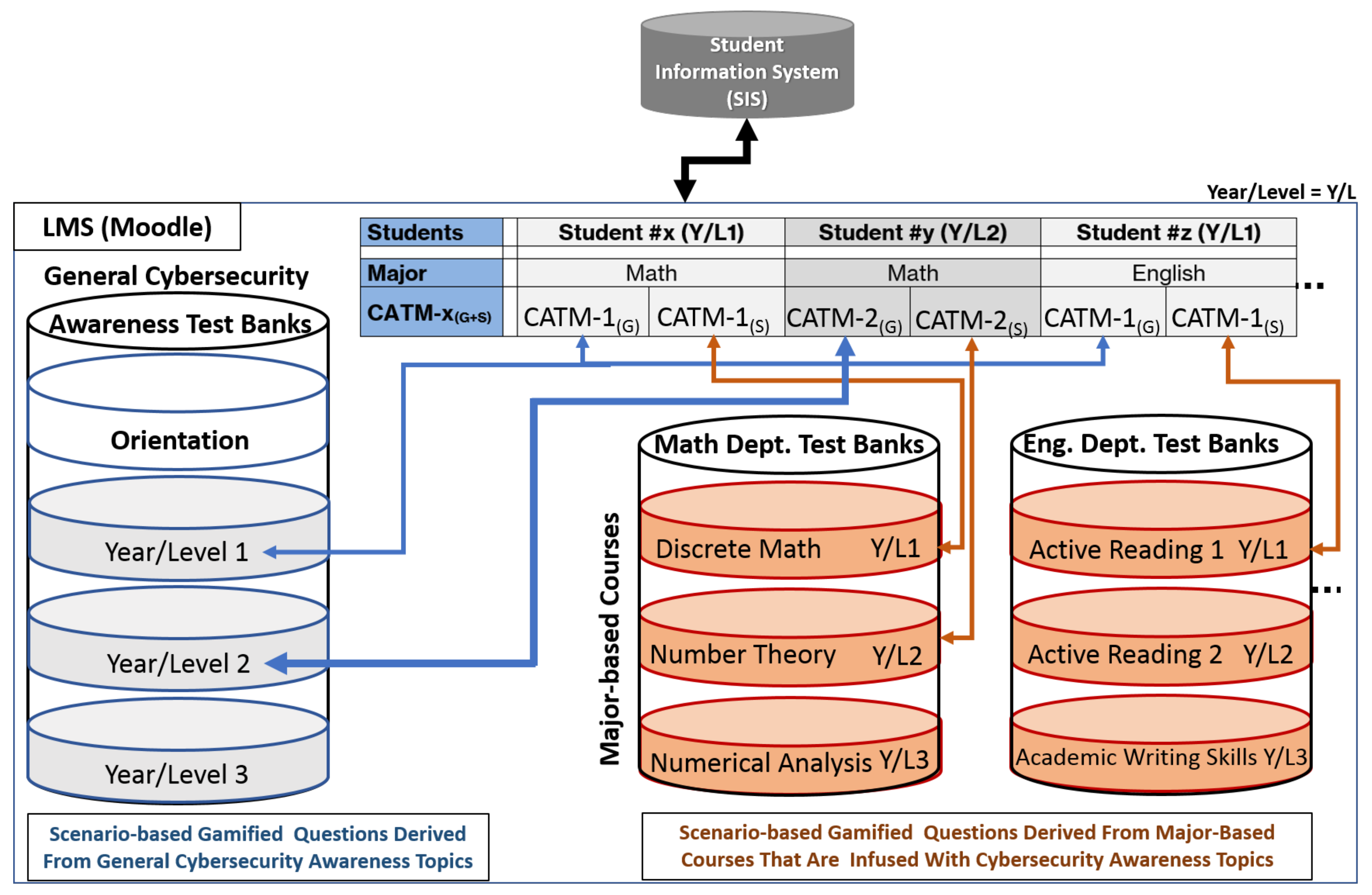
- The first part contains cybersecurity awareness topics and related gamified questions that are general to all students in an academic institution; these are referred to as CATM-x(G). These cybersecurity awareness topics and related gamified questions are appropriately designed for the relevant year. Examples of topics and one gamified question for CATM-1(G) are shown below.
- The second part contains cybersecurity awareness topics and related gamified questions that are specific to each major in an academic institution; these are referred to as CATM-x(S). For example, CATM-1(S) for English majors would contain gamified questions designed by the English instructor based on cybersecurity awareness topics that are infused in a required English course that is associated with CATM-1(S). To elaborate a bit further, an English instructor uses content-based language instruction to teach both English language skills and cybersecurity content. For example, the English instructor would use a newspaper article that is intended for general public consumption and present it in class to teach both English skills and cybersecurity basics that will drive the cybersecurity awareness that will be used to create gamified questions; a task that can be done with the help of a cybersecurity awareness center. These “major-based cybersecurity awareness course topics” will be explained further below.
- I.
- CATM-x(G): CATM-1(G) Material for First-Year Students
- II.
- CATM-x(S): Major-Based Cybersecurity Awareness Course Topics
4.1.3. Phase 1/Activity 3: Define/Adjust Scenario-Based Gamified Assessments in Training Modules
Scenario-Based Questions—Gamified
- A
- You should press the link and make sure the website belongs to Facebook.
- B
- You should verify the email sender and make sure the email is sent from Facebook.
- C
- You should try to find misspelling mistakes in the email to make sure the email is not phishing.
- D
- This is considered a phishing email and you should not press the link as you did not sign up to any website that sent you a verification code.
4.2. Phase 2—Populate Test Banks Associated with the Training Modules on LMS
4.2.1. Phase 2/Activity 1: Create/Adjust Scenario-Based Gamified Questions on LMS Test Banks
4.2.2. Phase 2/Activity 2: Populate Each Training Module with Assessments from Test Banks
4.3. Phase 3—Report on Assessment Results and Recommend Actions
4.3.1. Phase 3/Activity 1: Report Assessment Results to the Student Information System (SIS)
4.3.2. Phase 3/Activity 2: Analyze Results for Each CATM-x(G+S) and Report for Actions
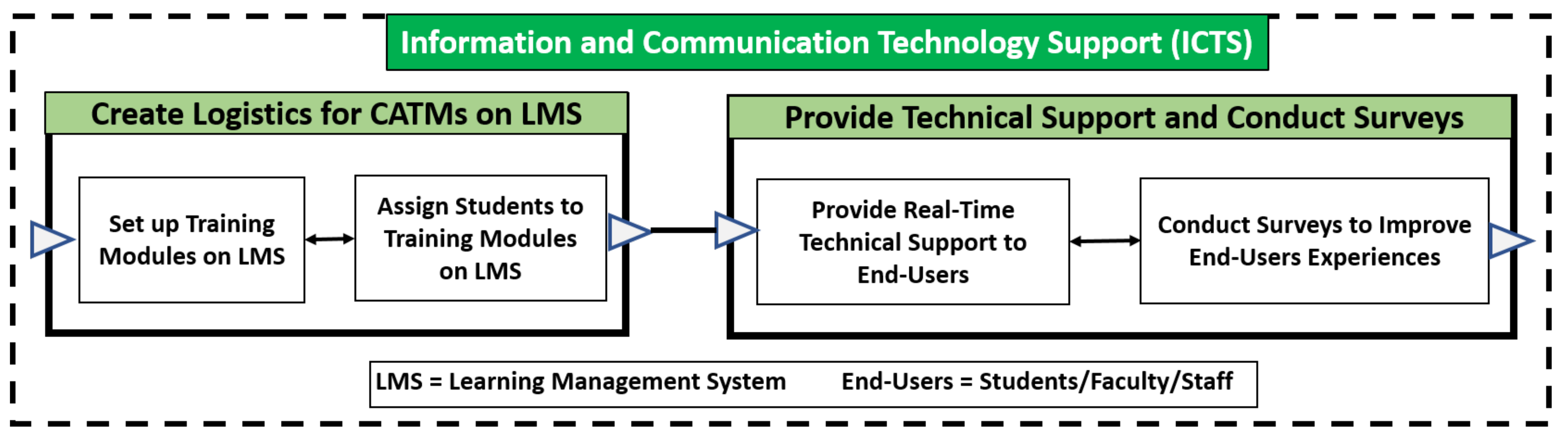
5. Information and Communication Technology Support (ICTS)
5.1. Phase 1—Create Logistics for Training Modules on LMS
5.1.1. Phase 1/Activity 1: Set up Training Modules on LMS
5.1.2. Phase 1/Activity 2: Assign Students to Training Modules on LMS
5.2. Phase 2—Provide Technical Support and Conduct Surveys
5.2.1. Phase 2/Activity 1: Provide Real-Time Technical Support to End-Users
5.2.2. Phase 2/Activity 2: Conduct Usability Surveys to Improve End-Users Experiences
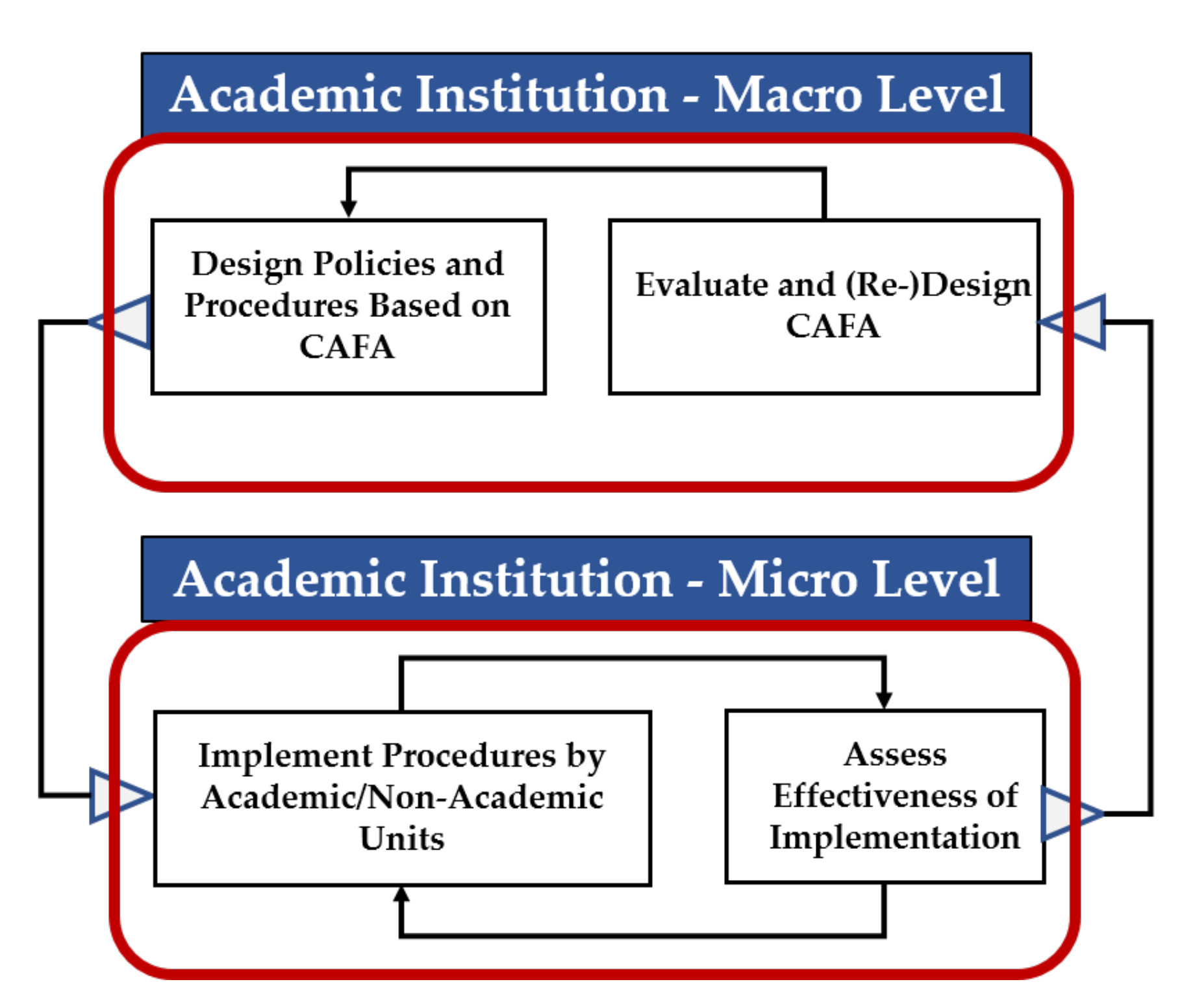
6. Discussion
6.1. Academic Institution Macro Level
6.1.1. Unit—Evaluate and (Re-)Design CAFA
6.1.2. Unit—Design Policies and Procedures Based on CAFA
6.2. Educational Institution Micro Level
6.2.1. Module—Implement Procedures by Academic/Non-Academic Units
6.2.2. Unit—Assess Effectiveness of Implementation
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- McCrohan, K.F.; Engel, K.; Harvey, J.W. Influence of Awareness and Training on Cyber Security. J. Internet Commer. 2010, 9, 23–41. [Google Scholar] [CrossRef]
- Troia, V. The Cybersecurity Framework as an Effective Information Security Baseline: A Qualitative Exploration. ProQuest Diss. Theses 2018, 10933040. [Google Scholar]
- Siddiqui, Z.; Zeeshan, N. A Survey on Cybersecurity Challenges and Awareness for Children of all Ages. In Proceedings of the 2020 International Conference on Computing, Electronics & Communications Engineering (iCCECE), Southend, UK, 17–18 August 2020; pp. 131–136. [Google Scholar] [CrossRef]
- Alharbi, T.; Tassaddiq, A. Assessment of Cybersecurity Awareness Among Students of Majmaah University. Big Data Cogn. Comput. 2021, 5, 23. [Google Scholar] [CrossRef]
- Garba, A.; Sirat, M.B.; Hajar, S.; Dauda, I.B. Cyber Security Awareness Among University Students: A Case Study. Sci. Proc. Ser. 2020, 2, 82–86. [Google Scholar] [CrossRef]
- Moallem, A. Cyber Security Awareness Among College Students. In Advances in Intelligent Systems and Computing; Springer: Berlin/Heidelberg, Germany, 2019; Volume 782, pp. 79–87. [Google Scholar] [CrossRef]
- Garba, A.A.; Jeribi, F.; Al-Shourbaji, I.; Alhameed, M.; Reegu, F.; Alim, S. An Approach to Weigh Cybersecurity Awareness Questions in Academic Institutions Based on Principle Component Analysis: A Case Study of Saudi Arabia. Int. J. Sci. Technol. Res. 2021, 10, 319–326. [Google Scholar]
- Slusky, L.; Partow-Navid, P. Students Information Security Practices and Awareness. J. Inf. Priv. Secur. 2012, 8, 3–26. [Google Scholar] [CrossRef]
- Ahlan, A.R.; Lubis, M.; Lubis, A.R. Information Security Awareness at the Knowledge-Based Institution: Its Antecedents and Measures. Proc. Comput. Sci. 2015, 72, 361–373. [Google Scholar] [CrossRef] [Green Version]
- Al-Alawi, A.I.; Al-Kandari, S.M.H.; Abdel-Razek, R.H. Evaluation of Information Systems Security Awareness in Higher Education: An Empirical Study of Kuwait University. J. Innov. Bus. Best Pract. 2016, 1–24. [Google Scholar] [CrossRef] [Green Version]
- Taha, N.; Dahabiyeh, L. College Students Information Security Awareness: A Comparison Between Smartphones and Computers. Educ. Inf. Technol. 2021, 26, 1721–1736. [Google Scholar] [CrossRef]
- Aloul, F.A. The Need for Effective Information Security Awareness. J. Adv. Inf. Technol. 2012, 3, 176–183. [Google Scholar] [CrossRef]
- Garba, A.A.; Siraj, M.M.; Othman, S.H.; Musa, M.A. A Study on Cybersecurity Awareness Among Students in Yobe State University, Nigeria: A Quantitative Approach. Int. J. Emerg. Technol. 2020, 11, 41–49. [Google Scholar]
- Aliyu, M.; Abdallah, N.A.O.; Lasisi, N.A.; Diyar, D.; Zeki, A.M. Computer Security and Ethics Awareness Among IIUM Students: An Empirical Study. In Proceedings of the 3rd International Conference on Information and Communication Technology for the Moslem World (ICT4M), Jakarta, Indonesia, 13–14 December 2010. [Google Scholar] [CrossRef]
- Senthilkumar, K.; Easwaramoorthy, S. A Survey on Cyber Security Awareness Among College Students in Tamil Nadu. IOP Conf. Ser. Mater. Sci. Eng. 2017, 263, 042043. [Google Scholar] [CrossRef]
- Chandarman, R.; van Niekerk, B. Students’ Cybersecurity Awareness at a Private Tertiary Educational Institution. Afr. J. Inf. Commun. 2017, 20, 133–155. [Google Scholar] [CrossRef] [Green Version]
- ALArifi, P.A.L.; Tootell, A.; Hyland, P. Information Security Awareness in Saudi Arabia. In Proceedings of the 2012 International Conference on Information Resources Management (CONF-IRM), Linz, Austria, 21–23 May 2020; Volume 57. [Google Scholar]
- Alotaibi, M.; Furnell, F.; Stengel, S.; Papadaki, I. A Survey of Cyber-Security Awareness in Saudi Arabia. In Proceedings of the 11th International Conference for Internet Technology and Secured Transactions, Barcelona, Spain, 5–7 December 2016; pp. 154–158. [Google Scholar]
- Al-Janabi, S.; Al-Shourbaji, I. A Study of Cyber Security Awareness in Educational Environment in the Middle East. J. Inf. Knowl. Manag. 2016, 15, 1650007. [Google Scholar] [CrossRef]
- NIST-USA. National Initiative for Cybersecurity Education. Available online: https://www.nist.gov/itl/applied-cybersecurity/nice (accessed on 27 September 2021).
- UK Government. The UK Cyber Security Strategy—Protecting and Promoting the UK in a Digital World. Available online: https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/60961/uk-cyber-security-strategy-final.pdf (accessed on 27 September 2021).
- Ali, W.N.A.W.; Ni, T.Q.; Idrus, S.Z.S. Social Media Cyberbullying: Awareness and Prevention through Anti Cyberbully Interactive Video (ACIV). J. Phys. Conf. Ser. 2020, 1529, 032071. [Google Scholar] [CrossRef]
- Valcke, T.; Keer, M.W.; Schellens, H. Long-term Study of Safe Internet Use of Young Children. Comput. Educ. 2011, 57, 1292–1305. [Google Scholar] [CrossRef]
- Al Shamsi, A.A. Effectiveness of Cyber Security Awareness Program for Young Children: A Case Study in UAE. Int. J. Inf. Technol. Lang. Stud. 2019, 3, 8–29. [Google Scholar] [CrossRef]
- Kruger, H.; Drevin, L.; Steyn, T. A Vocabulary Test to Assess Information Security Awareness. Inf. Manag. Comput. Secur. 2010, 18, 316–327. [Google Scholar] [CrossRef] [Green Version]
- Null, L. Integrating Security Across the Computer Science Curriculum. J. Comput. Sci. Coll. 2004, 19, 170–178. [Google Scholar]
- Curricula, C. The Joint Task Force on Computing Curricula IEEE Computer Society Association for Computing Machinery. 2001. Available online: https://www.acm.org/binaries/content/assets/education/curricula-recommendations/cc2001.pdf (accessed on 25 September 2021).
- Siraj, S.G.A.; Taylor, B.; Kaza, S. Integrating Security in the Computer Science Curriculum. ACM Inroads 2015, 6, 77–81. [Google Scholar] [CrossRef]
- Taylor, B.; Kaza, S. Security Injections@Towson: Integrating Secure Coding into Introductory Computer Science Courses. ACM Trans. Comput. Educ. 2016, 16, 1–20. [Google Scholar] [CrossRef]
- Weiss, M.; Richard, S.; Ambareen, M.; Jens, H.; Elizabeth, T.; Blair, K.; Sidd, L. Building and Supporting a Community of CS Educators Teaching Cybersecurity in 2017 (Abstract Only). In Proceedings of the 2017 ACM SIGCSE Technical Symposium, Seattle, WA, USA, 8–11 March 2017. [Google Scholar] [CrossRef]
- Weiss, A.C.R.; Mache, J.; Hawthorne, E.; Siraj, A.; Taylor, B.; Kaza, S. Integrating Hands-on Cybersecurity Exercises into the Curriculum in 2021. In Proceedings of the 52nd ACM Technical Symposium on Computer Science Education, Virtual Event, 13–20 March 2021; p. 1358. [Google Scholar] [CrossRef]
- Dai, J. Situation Awareness-Oriented Cybersecurity Education. In Proceedings of the 2018 IEEE Frontiers in Education Conference, San Jose, CA, USA, 3–6 October 2018; IEEE: Manhattan, NY, USA, 2018. [Google Scholar] [CrossRef]
- Wang, J.; Brylow, D.; Perouli, D. Implementing cybersecurity into the Wisconsin K-12 classroom. In Proceedings of the 2019 IEEE 43rd Annual Computer Software and Applications Conference (COMPSAC), Milwaukee, WI, USA, 15–19 July 2019; Volume 2, pp. 312–317. [Google Scholar] [CrossRef]
- Sobel, A.; Parrish, A.; Raj, R.K. Curricular Foundations for Cybersecurity. Computer 2019, 52, 14–17. [Google Scholar] [CrossRef]
- Blair, J.R.S.; Chewar, C.M.; Raj, R.K.; Sobiesk, E. Infusing Principles and Practices for Secure Computing Throughout an Undergraduate Computer Science Curriculum. In Proceedings of the ACM Conference on Innovation and Technology in Computer Science Education ITiCSE, Trondheim, Norway, 15–19 June 2020; pp. 82–88. [Google Scholar] [CrossRef]
- Abawajy, J. User Preference of Cyber Security Awareness Delivery Methods. Behav. Inf. Technol. 2014, 33, 237–248. [Google Scholar] [CrossRef]
- Socrative. Available online: www.socrative.com (accessed on 6 June 2021).
- Eow, B.; Wanzah, Y.L.; Rosnaini, W.A.; Roselan, M. Computer Games Development and Appreciative Learning Approach in Enhancing Students’ Creative Perception. Comput. Educ. 2010, 54, 146–161. [Google Scholar] [CrossRef]
- Laszka, A.; Felegyhazi, M.; Buttyan, L. A Survey of Interdependent Information Security Games. ACM Comput. Surv. 2014, 47, 23. [Google Scholar] [CrossRef] [Green Version]
- Bente, J.; Breuer, G. Why so serious? On the Relation of Serious Games & Learning. J. Comput. Game Cult. 2010, 4, 7–24. [Google Scholar]
- Kahoot. Available online: https://kahoot.com/ (accessed on 6 June 2021).
- Rajendran, D.P.D.; Rangaraja, P.S. An e-ADR (elaborated action design research) Approach Towards Game-based Learning in Cybersecurity Incident Detection and Handling. In Proceedings of the Hawaii International Conference on System Sciences, Wailea, HI, USA, 7–10 January 2020. [Google Scholar] [CrossRef] [Green Version]
- CyberCIEGE. Center for Cybersecurity and Cyber Operations. Available online: https://nps.edu/web/c3o/cyberciege (accessed on 5 July 2021).
- Röpke, R.; Schroeder, U. The Problem with Teaching Defence Against the Dark Arts: A Review of Game-based Learning Applications and Serious Games for Cyber Security Education. In Proceedings of the 11th International Conference on Computer Supported Education, Heraklion, Greece, 2–4 May 2019. [Google Scholar] [CrossRef]
- Mio, C.; Ventura-Medina, E.; João, E. Scenario-based eLearning to Promote Active Learning in Large Cohorts: Students’ Perspective. Comput. Appl. Eng. Educ. 2019, 27, 894–909. [Google Scholar] [CrossRef]
- Lupiana, D. Development of A Framework to Leverage Knowledge Management Systems to Improve Security Awareness. 2008. Dissertations. 6. Available online: https://arrow.tudublin.ie/scschcomdis/6 (accessed on 7 September 2021).
- Shen, L. The Nist Cybersecurity Framework: Overview and Potential Impacts. J. Internet Law 2014, 18, 3–6. [Google Scholar]
- Kortjan, N.; von Solms, R. A Conceptual Framework for Cyber Security Awareness and Education in SA. South Afr. Comput. J. 2014, 52, 29–41. [Google Scholar] [CrossRef] [Green Version]
- Katsantonis, N.M.; Kotini, I.; Fouliras, P.; Mavridis, I. Conceptual Framework for Developing Cyber Security Serious Games. In Proceedings of the 2019 IEEE Global Engineering Education Conference (EDUCON), Dubai, United Arab Emirates, 8–11 April 2019; pp. 872–881. [Google Scholar] [CrossRef]
- Tirumala, S.S.; Valluri, M.R.; Babu, G.A. A Survey On Cybersecurity Awareness Concerns, Practices and Conceptual Measures. In Proceedings of the 2019 International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 23–25 January 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Peker, Y.K.; Ray, L.; da Silva, S. Online Cybersecurity Awareness Modules for College and High School Students. In Proceedings of the 2018 National Cyber Summit (NCS), Huntsville, AL, USA, 5–7 June 2018; pp. 24–33. [Google Scholar] [CrossRef]
- Schreider, T. Building an Effective Cybersecurity Program, 2nd ed.; Rothstein Publishing: Brookfield, CT, USA, 2019. [Google Scholar]
| Topic | Sub-Topics | Outcomes to be Measured |
|---|---|---|
| Hacking | Hacking definitions, types of hackers, types of cybercrimes, and ethical hacking |
|
| Social Engineering Attacks | Social engineering attacks definitions, common types of social engineering attacks |
|
| Phishing | Definition of phishing, protect your personal information, recognize false links, recognize false emails |
|
| Pretexting | Definition of pretexting attacks, examples of fabricated scenarios used in pretexting |
|
| Baiting | Describe the proper definition of baiting attacks, differentiate between baiting and pretexting, protecting your login credentials |
|
| Quid Pro Quo | Describe the proper definition of quid pro quo attacks, differentiate between baiting and quid pro quo |
|
| Tailgating | Describe the proper definition of tailgating attacks, examples of tailgating attempts and their results |
|
| Rogue | Describe the proper definition of rogue attacks, examples of rogue attempts and their results |
|
| Strong Password Requirements | Describe the password construction requirements, password protection standards, and associated risks |
|
| Email Security | Understand the email usage risks, opening attachment risks, and sender identification |
|
| Securing Mobile Devices | Mobile security requirements, relevant built-in security features, and issues associated with hacked devices |
|
| Destroying Sensitive Data | Consequences of inappropriate data disposal, steps to destroy out-of-date sensitive data |
|
| Malware Protection | Malware classifications, definitions for anti-virus software, types of virus-caused damages, best practices to prevent malware |
|
| CATM-x(S) | Math Major | English Major |
|---|---|---|
| CATM-1(S) | Discrete Math | Active Reading 1 |
| CATM-2(S) | Number Theory | Active Reading 2 |
| CATM-3(S) | Numerical Analysis | Academic Writing Skills |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khader, M.; Karam, M.; Fares, H. Cybersecurity Awareness Framework for Academia. Information 2021, 12, 417. https://doi.org/10.3390/info12100417
Khader M, Karam M, Fares H. Cybersecurity Awareness Framework for Academia. Information. 2021; 12(10):417. https://doi.org/10.3390/info12100417
Chicago/Turabian StyleKhader, Mohammed, Marcel Karam, and Hanna Fares. 2021. "Cybersecurity Awareness Framework for Academia" Information 12, no. 10: 417. https://doi.org/10.3390/info12100417
APA StyleKhader, M., Karam, M., & Fares, H. (2021). Cybersecurity Awareness Framework for Academia. Information, 12(10), 417. https://doi.org/10.3390/info12100417





