A Web-Based Honeypot in IPv6 to Enhance Security
Abstract
:1. Introduction
2. Related Works
2.1. Security Situation Awareness
2.2. Honeypot and IPv6
2.3. Access Control and Security Issues in IPv6
3. Design of a Honeypot-Based IPv6 System
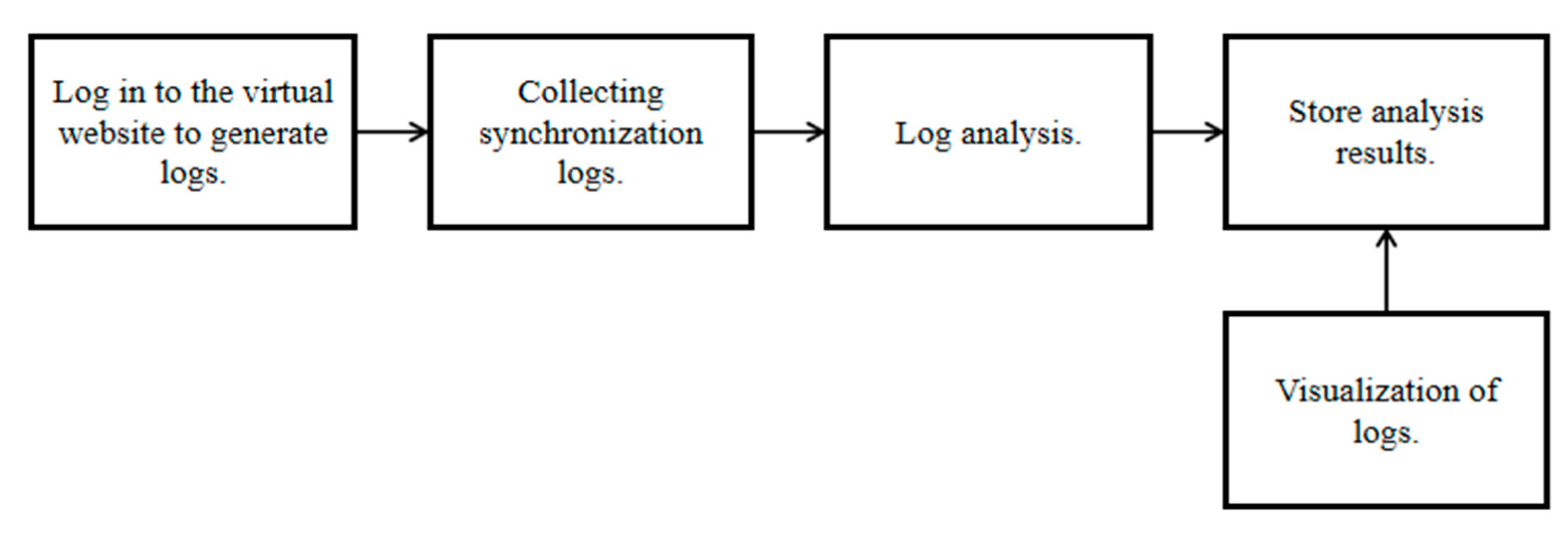
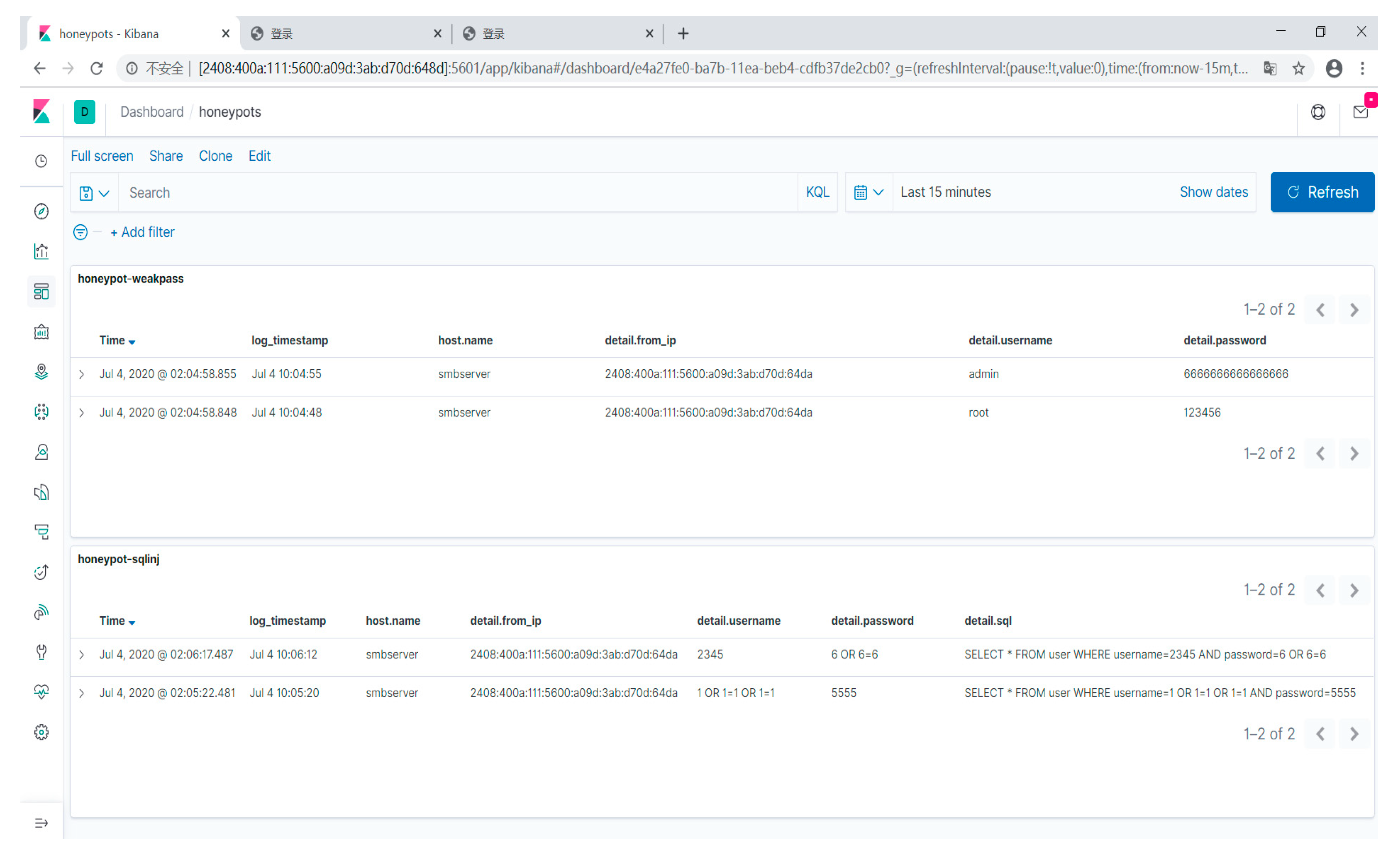
3.1. Fake Website Logs
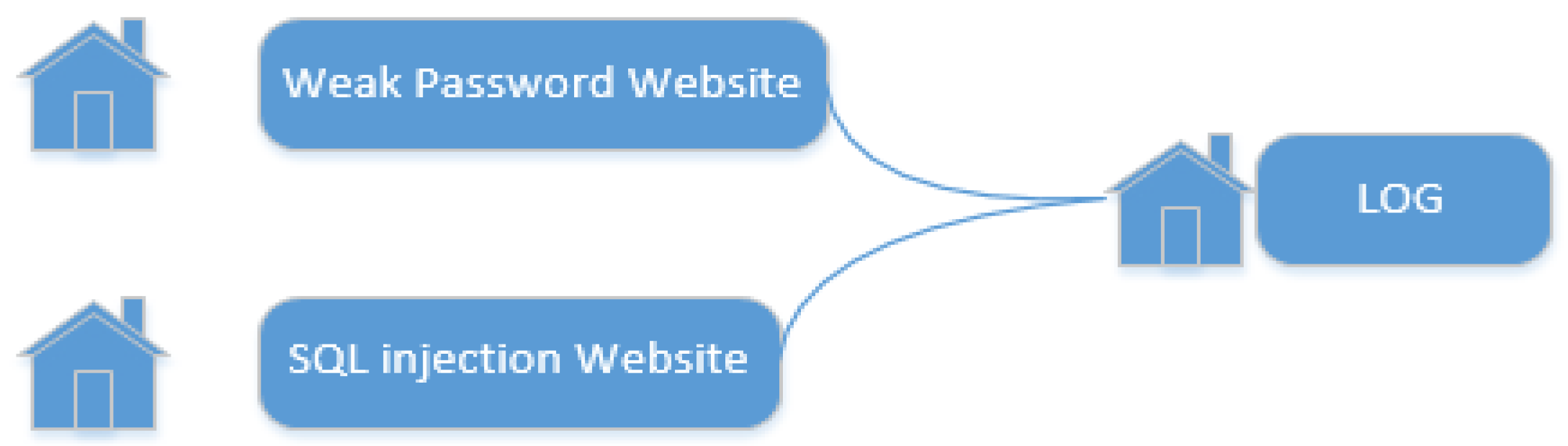
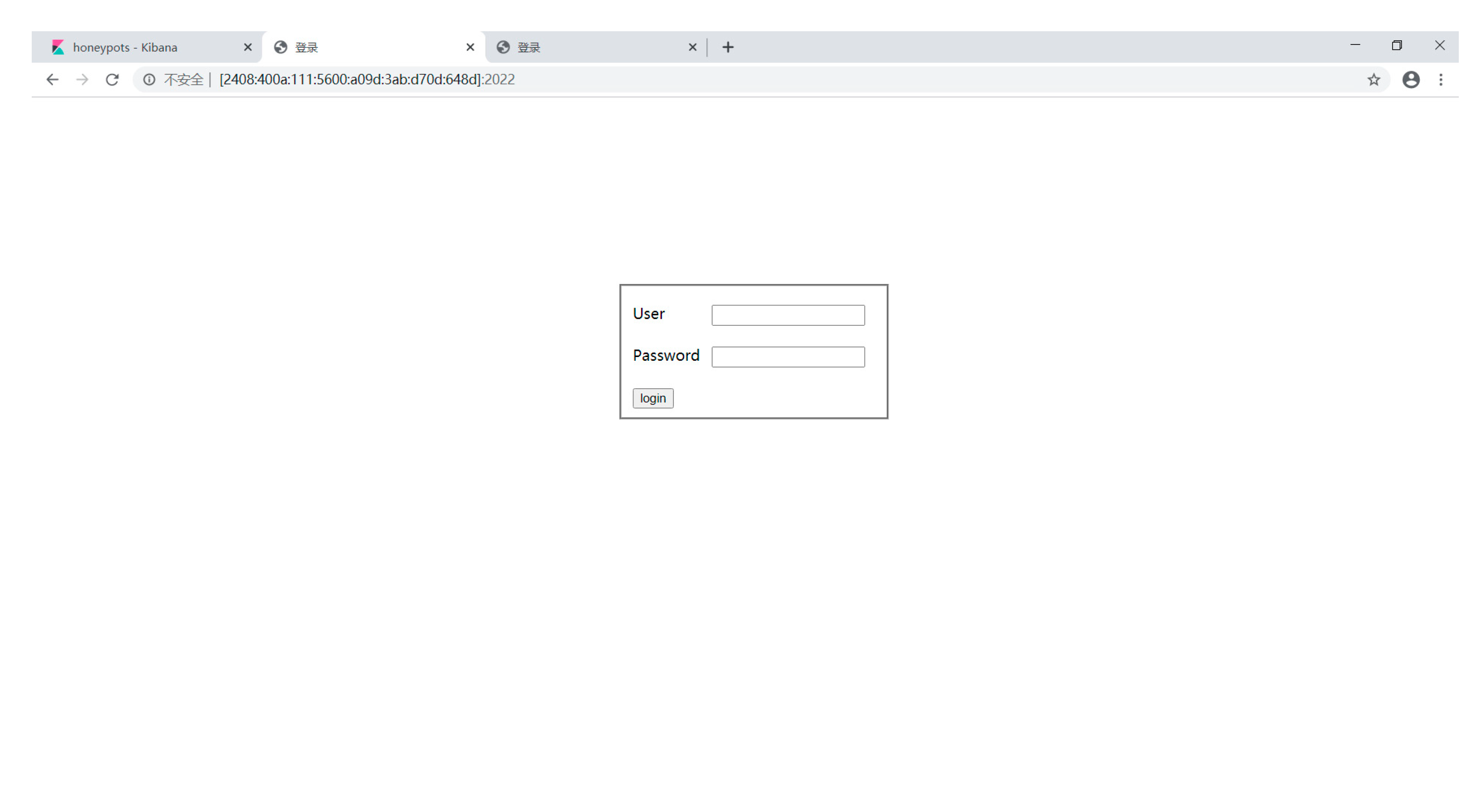
3.2. Weak Password Website Module in the Honeypot
3.3. SQL Injection Website Module in the Honeypot
3.4. Index of Security Situation Awareness (SSI)
4. Experiment and Discussions
4.1. Honeypot Situation Awareness Parts
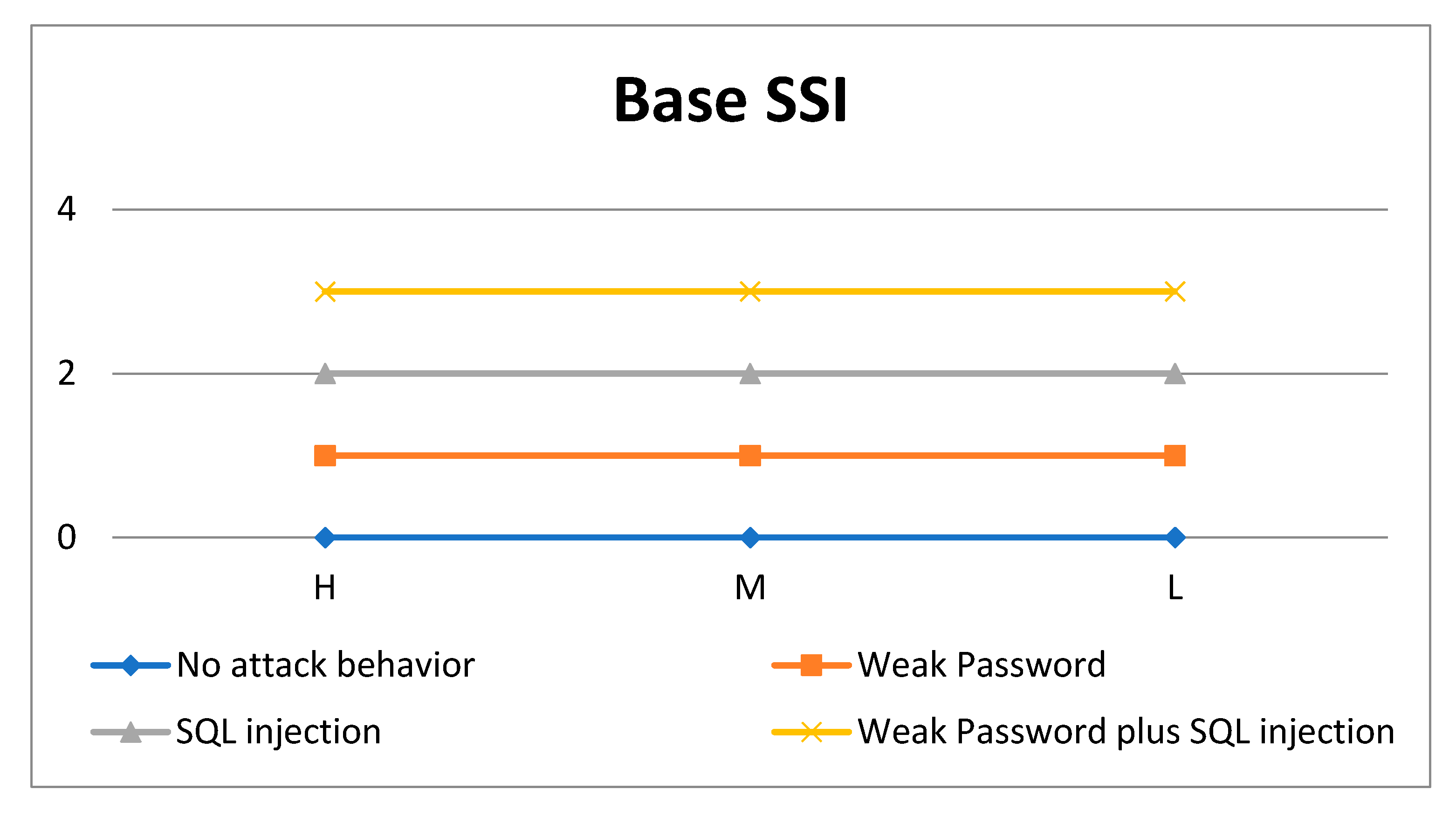
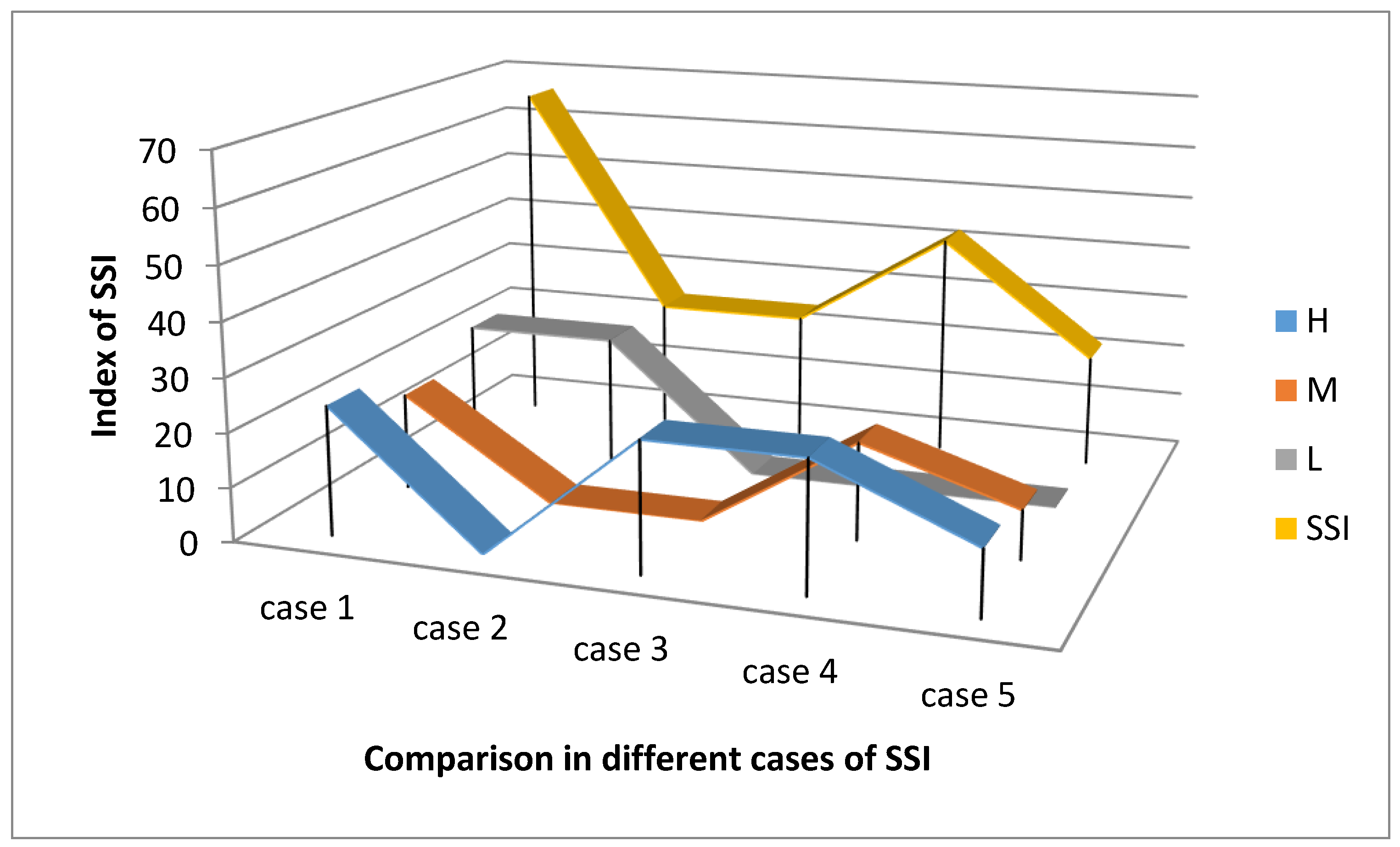
4.2. The Index of Security Situation Awareness
- (1)
- The model presented in this paper can run in an IPv6 network environment;
- (2)
- The security situation of the whole network can measure by deploying a group of honeypots in different security areas of the system.
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Bouras, C.; Gkamas, A.; Primpas, D.; Stamos, K. IPv6 deployment: Real time applications and QoS aspects. Comput. Commun. 2006, 29, 1393–1401. [Google Scholar] [CrossRef]
- Montavont, J.; Roth, D.; Noël, T. Mobile IPv6 in Internet of Things: Analysis, experimentations and optimizations. Ad Hoc Netw. 2014, 14, 15–25. [Google Scholar] [CrossRef]
- Žagar, D.; Grgić, K.; Rimac-Drlje, S. Security aspects in IPv6 networks—Implementation and testing. Comput. Electr. Eng. 2007, 33, 425–437. [Google Scholar] [CrossRef]
- Gomez, C.; Minaburo, A.; Toutain, L.; Barthel, D.; Zuniga, J.C. IPv6 over LPWANs: Connecting Low Power Wide Area Networks to the Internet (of Things). IEEE Wirel. Commun. 2020, 27, 206–213. [Google Scholar] [CrossRef]
- Guangjia, S.; Hui, W.; Hangjun, W. Using multi-address generation and duplicate address detection to prevent DoS in IPv6. IET Commun. 2019, 13, 1390–1396. [Google Scholar] [CrossRef]
- Fernandez, P.J.; Santa, J.; Bernal, F.; Skarmeta, A.F. Securing Vehicular IPv6 Communications. IEEE Trans. Depend. Secure Comput. 2016, 13, 46–58. [Google Scholar] [CrossRef]
- García-Guerrero, E.E.; Inzunza-González, E.; López-Bonilla, O.R.; Cárdenas-Valdez, J.R.; Tlelo-Cuautle, E. Randomness improvement of chaotic maps for image encryption in a wireless communication scheme using PIC-microcontroller via Zigbee channels. Chaos Solitons Fractals 2020, 133, 109646. [Google Scholar] [CrossRef]
- Sanders, C.; Smith, J. Chapter 12—Using Canary Honeypots for Detection, in Applied Network Security Monitoring; Sanders, C., Smith, J., Sanders, C., Smith, J., Eds.; Syngress: Boston, MA, USA, 2014; pp. 317–338. [Google Scholar]
- Zhang, W.; Zhang, B.; Zhou, Y.; He, H.; Ding, Z. An IoT Honeynet based on Multi-port Honeypots for Capturing IoT attacks. IEEE Internet Things J. 2019, 7, 3991–3999. [Google Scholar] [CrossRef]
- Eliot, N.; Kendall, D.; Brockway, M. A Flexible Laboratory Environment Supporting Honeypot Deployment for Teaching Real-World Cyber security Skills. IEEE Access 2018, 6, 34884–34895. [Google Scholar] [CrossRef]
- Liu, X.; Yu, J.; Lv, W.; Yu, D.; Wang, Y.; Wu, Y. Network security situation: From awareness to awareness-control. J. Netw. Comput. Appl. 2019, 139, 15–30. [Google Scholar] [CrossRef]
- Zhao, D.; Liu, J. Study on network security situation awareness based on particle swarm optimization algorithm. Comput. Ind. Eng. 2018, 125, 764–775. [Google Scholar] [CrossRef]
- Zhang, H.; Shi, J.; Chen, X. A Multi-Level Analysis Framework in Network Security Situation Awareness. Procedia Comput. Sci. 2013, 17, 530–536. [Google Scholar] [CrossRef]
- Liang, Y.; Wang, H.Q.; Lai, J.B. Quantification of Network Security Situational Awareness Based on Evolutionary Neural Network. In Proceedings of the 2007 International Conference on Machine Learning and Cybernetics, Hong Kong, China, 19–22 August 2007. [Google Scholar]
- Wang, H.; Liang, Y.; Liu, X. Stochastic Game Theoretic Method of Quantification for Network Situational Awareness. In Proceedings of the 2008 International Conference on Internet Computing in Science and Engineering, Harbin, China, 28–29 January 2008. [Google Scholar]
- Shi, L.; Li, Y.; Liu, T.; Liu, J.; Shan, B.; Chen, H. Dynamic Distributed Honeypot Based on Blockchain. IEEE Access 2019, 7, 72234–72246. [Google Scholar] [CrossRef]
- Fan, W.; Du, Z.; Smith-Creasey, M.; Fernández, D. HoneyDOC: An Efficient Honeypot Architecture Enabling All-Round Design. IEEE J. Sel. Areas Commun. 2019, 37, 683–697. [Google Scholar] [CrossRef]
- Paradise, A.; Shabtai, A.; Puzis, R.; Elyashar, A.; Elovici, Y.; Roshandel, M.; Peylo, C. Creation and Management of Social Network Honeypots for Detecting Targeted Cyber Attacks. IEEE Trans. Comput. Soc. Syst. 2017, 4, 65–79. [Google Scholar] [CrossRef]
- La, Q.D.; Quek, T.Q.; Lee, J.; Jin, S.; Zhu, H. Deceptive Attack and Defense Game in Honeypot-Enabled Networks for the Internet of Things. IEEE Internet Things J. 2016, 3, 1025–1035. [Google Scholar] [CrossRef]
- Kishimoto, K.; Ohira, K.; Yamaguchi, Y.; Yamaki, H.; Takakura, H. An Adaptive Honeypot System to Capture IPv6 Address Scans. In Proceedings of the 2012 International Conference on Cyber Security, Washington, DC, USA, 14–16 December 2012. [Google Scholar]
- Schindler, S.; Schnor, B.; Kiertscher, S.; Scheffler, T.; Zack, E. HoneydV6: A low-interaction IPv6 honeypot. In Proceedings of the 2013 International Conference on Security and Cryptography (SECRYPT), Reykjavik, Iceland, 29–31 July 2013. [Google Scholar]
- Schindler, S.; Schnor, B.; Kiertscher, S.; Scheffler, T.; Zack, E. IPv6 Network Attack Detection with HoneydV6. Commun. Comput. Inf. 2013, 456, 252–269. [Google Scholar]
- Honeypot Architectures for IPv6 Networks. Available online: https://www.cs.uni-potsdam.de/bs/research/docs/thesis/2016/schindler.pdf (accessed on 2 September 2020).
- Zuzcak, M.; Sochor, T. Application of Honeypots in IPv6 Networks. In AIP Conference Proceedings; AIP Publishing LLC: Melville, NY, USA, 2015. [Google Scholar]
- Zobal, L.; Kolar, D.; Fujdiak, R. Current State of Honeypots and Deception Strategies in Cybersecurity. In Proceedings of the 2019 11th International Congress on Ultra Modern Telecommunications and Control Systems and Workshops (ICUMT), Dublin, Ireland, 28–30 October 2019; pp. 1–9. [Google Scholar]
- Masood, A.; Ghafoor, A.; Mathur, A. Conformance Testing of Temporal Role-Based Access Control Systems. IEEE Trans. Depend. Secure Comput. 2010, 7, 144–158. [Google Scholar] [CrossRef]
- Uddin, M.; Islam, S.; Al-Nemrat, A. A dynamic access control model using authorising workflow and task-role based access control. IEEE Access 2019, 7, 166676–166689. [Google Scholar] [CrossRef]
- Liu, Q.; Zhang, H.; Wan, J.; Chen, X. An Access Control Model for Resource Sharing Based on the Role-Based Access Control Intended for Multi-Domain Manufacturing Internet of Things. IEEE Access 2017, 5, 7001–7011. [Google Scholar] [CrossRef]
- Xu, C.; Wang, Y.; Wei, Q.; Wang, Q. A Novel Trust Model Based on Temporal Historical Data for Access Control. In Proceedings of the 2009 International Conference on Computational Intelligence and Security, Beijing, China, 11–14 December 2009. [Google Scholar]
- Hussein, D.; Bertin, E.; Frey, V. A Community-Driven Access Control Approach in Distributed IoT Environments. IEEE Commun. Mag. 2017, 55, 146–153. [Google Scholar] [CrossRef]
- Mahalle, P.N.; Thakre, P.A.; Prasad, N.R.; Prasad, R. A fuzzy approach to trust based access control in internet of things. In Proceedings of the Wireless VITAE 2013, Atlantic City, NJ, USA, 24–27 June 2013. [Google Scholar]
- Gu, K.; Zhang, L.; Wang, Z.; Kong, Y. Comparative studies of IPv6 tunnel security. In Proceedings of the 2017 13th International Conference on Natural Computation, Fuzzy Systems and Knowledge Discovery (ICNC-FSKD), Guilin, China, 29–31 July 2017. [Google Scholar]
- Rochim, A.F.; Aziz, M.A.; Fauzi, A. Design Log Management System of Computer Network Devices Infrastructures Based on ELK Stack. In Proceedings of the 2019 International Conference on Electrical Engineering and Computer Science (ICECOS), Batam Island, Indonesia, 2–3 October 2019. [Google Scholar]
- Shemlse Gebremedhin Kassa, CISA, CEH. 1 May 2017 ISACA JOURNAL. Available online: https://www.isaca.org/resources/isaca-journal/issues/2017/volume-3/it-asset-valuation-risk-assessment-and-control-implementation-model (accessed on 2 September 2020).
| Impact on Business | |||||
|---|---|---|---|---|---|
| Very Low | Low | Medium | High | Very High | |
| Factor | 1 | 2 | 3 | 4 | 5 |
| a | b | c | |
|---|---|---|---|
| case 1 | 2 | 2 | 4 |
| case 2 | 0 | 0 | 4 |
| case 3 | 2 | 0 | 0 |
| case 4 | 2 | 2 | 0 |
| case 5 | 1 | 1 | 0 |
| x | y | z | |
|---|---|---|---|
| Weighting Factor | 4 | 3 | 2 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, K.; Tong, M.; Yang, D.; Liu, Y. A Web-Based Honeypot in IPv6 to Enhance Security. Information 2020, 11, 440. https://doi.org/10.3390/info11090440
Wang K, Tong M, Yang D, Liu Y. A Web-Based Honeypot in IPv6 to Enhance Security. Information. 2020; 11(9):440. https://doi.org/10.3390/info11090440
Chicago/Turabian StyleWang, Keyong, Mengyao Tong, Dequan Yang, and Yuhang Liu. 2020. "A Web-Based Honeypot in IPv6 to Enhance Security" Information 11, no. 9: 440. https://doi.org/10.3390/info11090440
APA StyleWang, K., Tong, M., Yang, D., & Liu, Y. (2020). A Web-Based Honeypot in IPv6 to Enhance Security. Information, 11(9), 440. https://doi.org/10.3390/info11090440




