MoLaBSS: Server-Specific Add-On Biometric Security Layer Model to Enhance the Usage of Biometrics
Abstract
1. Introduction/Background
- We did not find a feasible software solution that could fit in our model on the server-side and mobile device side to test the MoLaBSS.
- Architecturally, it is different, in that it is a software-based and not a hardware-based extra layer of security.
- There is an extra cost associated with hardware replacement/upgrade. A hardware-based extra layer of security may fail if there are any wear-and-tear-related issues.
- Software-based security would be more scalable and flexible to adjust to the fast-changing security dynamics [17].
- This app would send “server ID” only to the verified users to complete the installation of the app; without that, users will not be able to access a particular application. In this, it is very targeted and server-specific and not a generic security layer.
- Most of the methods of user or device authentication emphasize one or a few cryptographic or biometric features. Multimodal biometric systems combine many biometric features to make the authentication more scalable [18], and this app is designed along multimodal lines. It can be used for any of the biometric features captured by smartphones.
2. Related Works
3. Technology and Methods
3.1. An Overview of the Architecture, Technical Design, and Data Flow
3.2. The Main Functions of the App and Its Variables
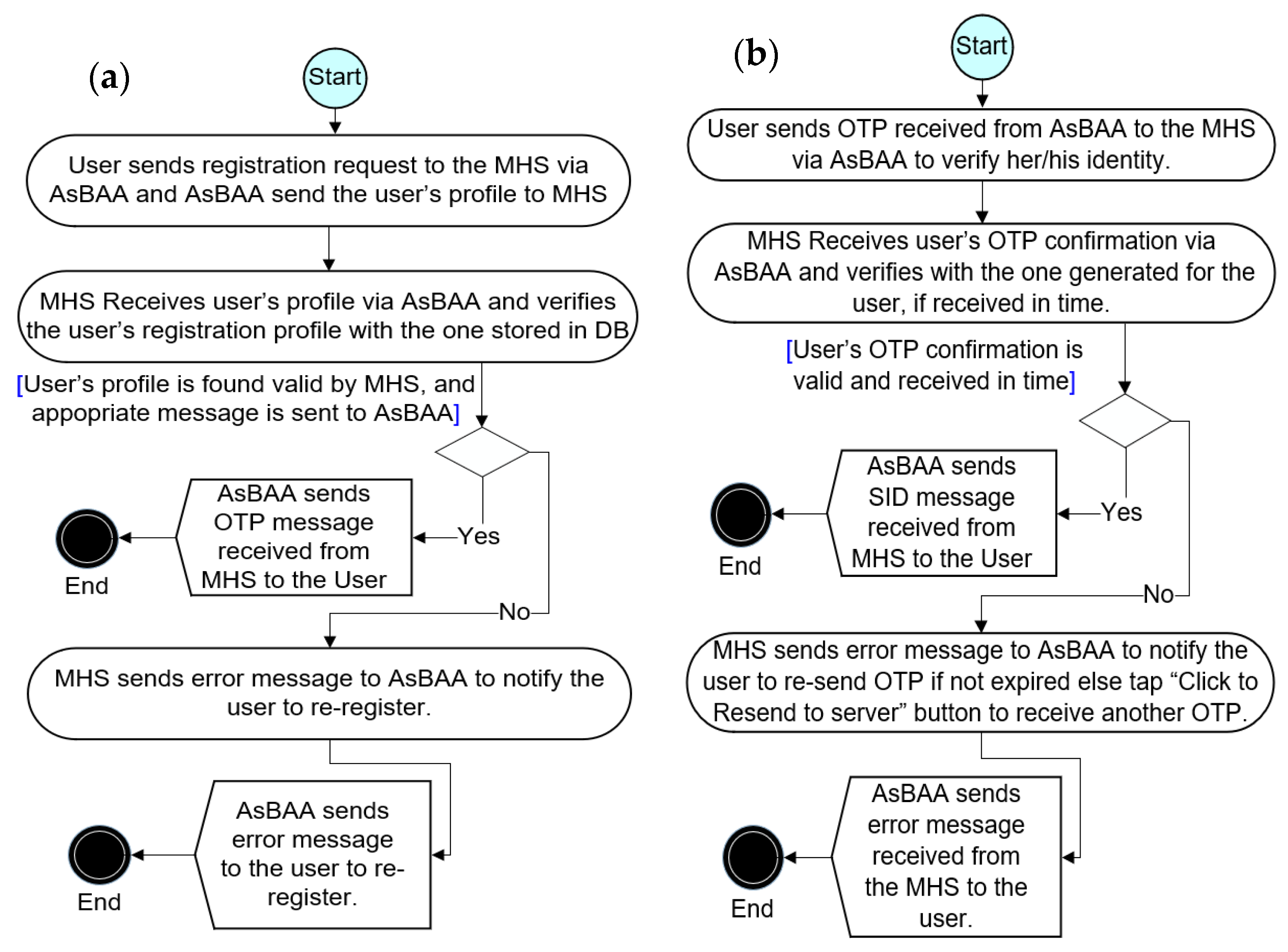
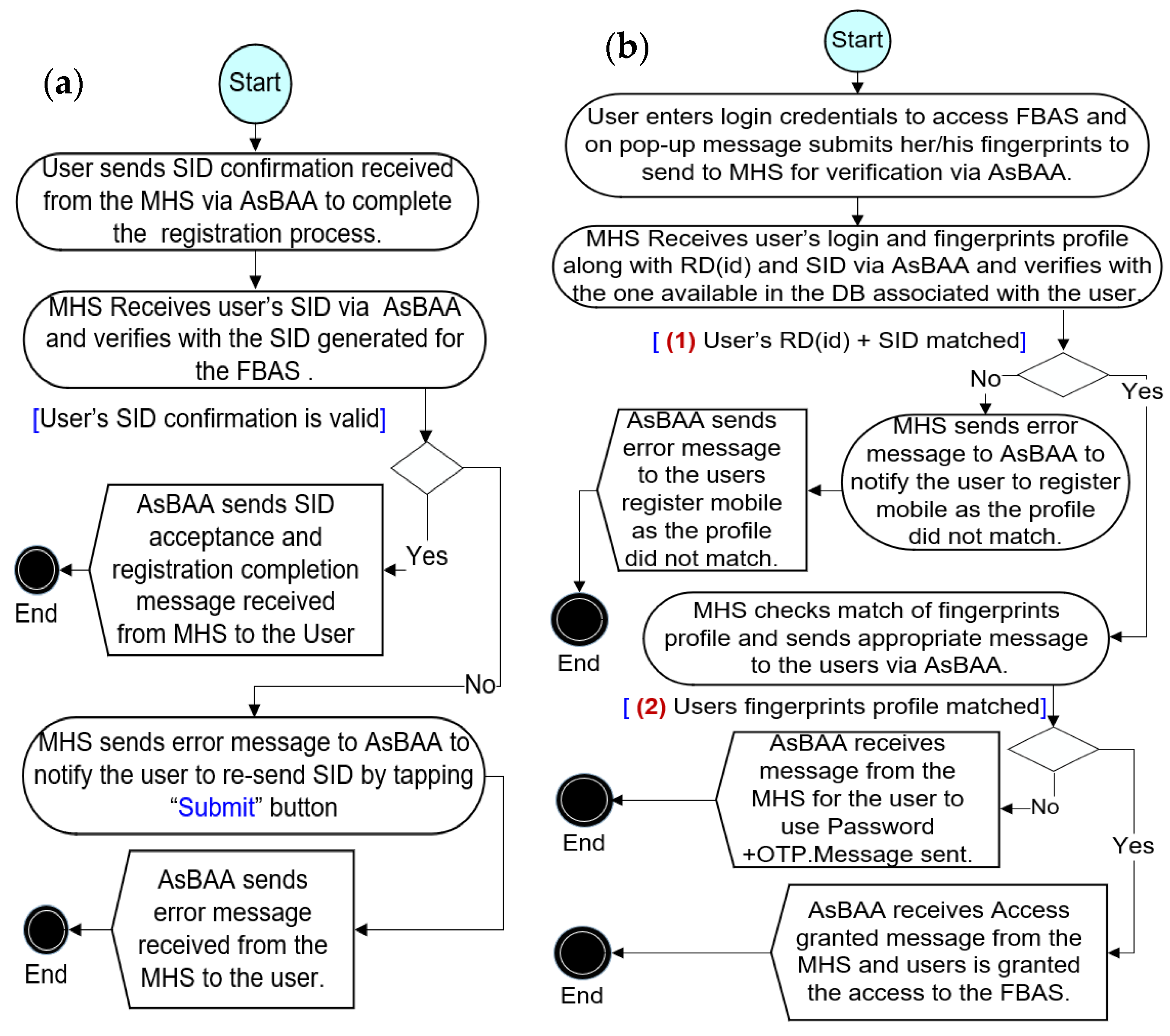
3.3. The Authentication Process of the Bio-Guard App
- UID + P + O or
- UID + B
- UID + B+ SCI(ID) or
- UID + P + O + SCI(ID)
- UID +P +O or
- UID + B
4. Experimentation
4.1. The Methodology of Test Population Sampling
4.2. Testing Environment
4.3. Performance Test of the App
4.4. Design, Functionality and Usefulness Test of the App
4.4.1. Experiment 1
4.4.2. Experiment 2
4.4.3. Experiment 3
4.4.4. Experiment 4
4.4.5. Experiment 5
4.4.6. Experiment 6
4.4.7. Experiment 7
4.4.8. Experiment 8
4.4.9. Experiment 9
4.4.10. Experiment 10
4.5. Overall Usability Evaluation of the App on the SUS Scales
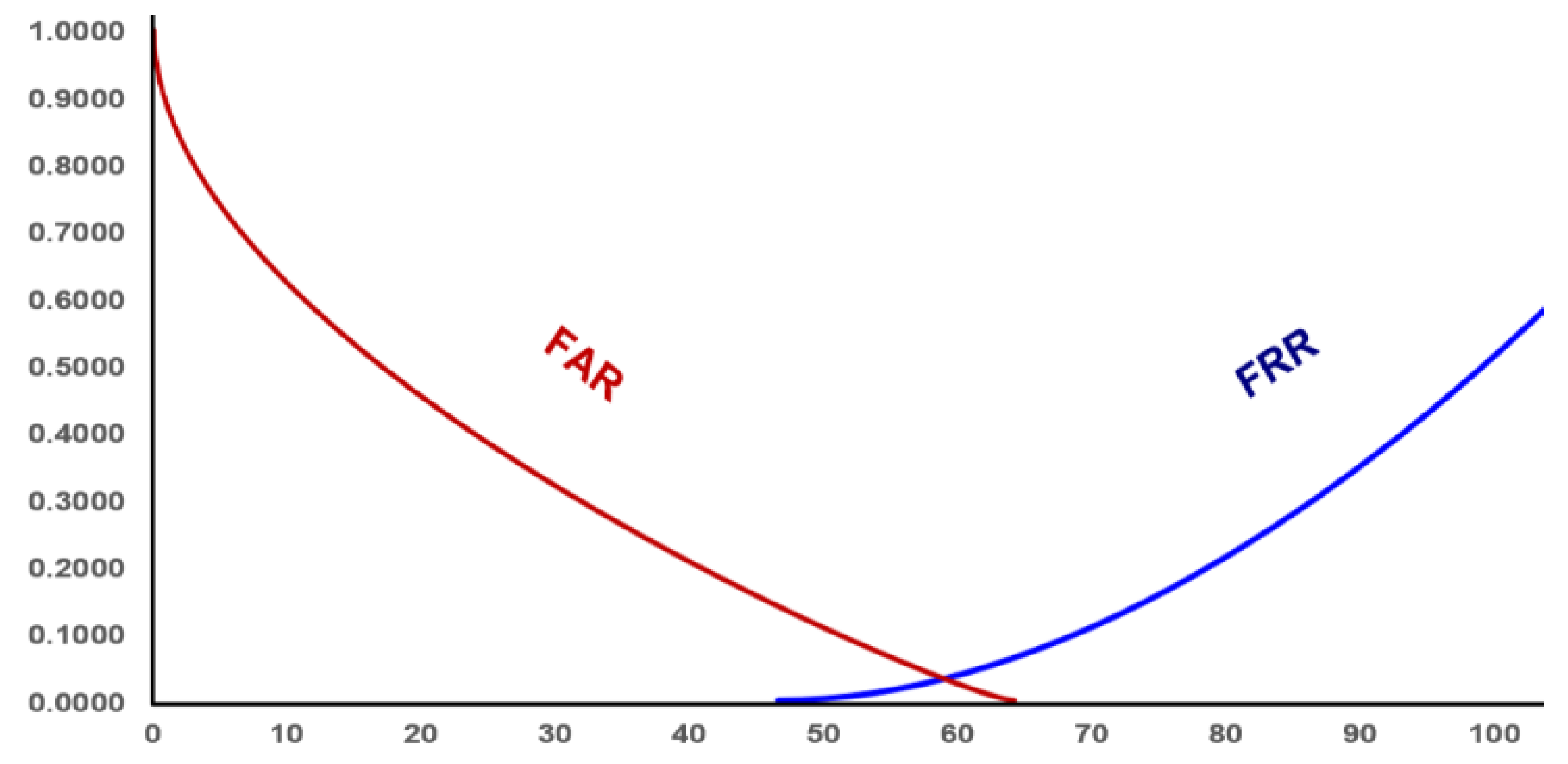
4.6. Test for False Rejection Rate (FRR), False Acceptance Rate (FAR), and Equal Error Rate (EER)
4.7. National-Level Survey to Test the Success of the MoLaBSS in a Realistic Hospital Environment
5. Analysis of the Experimental Outcomes and National level Survey Results
- (a)
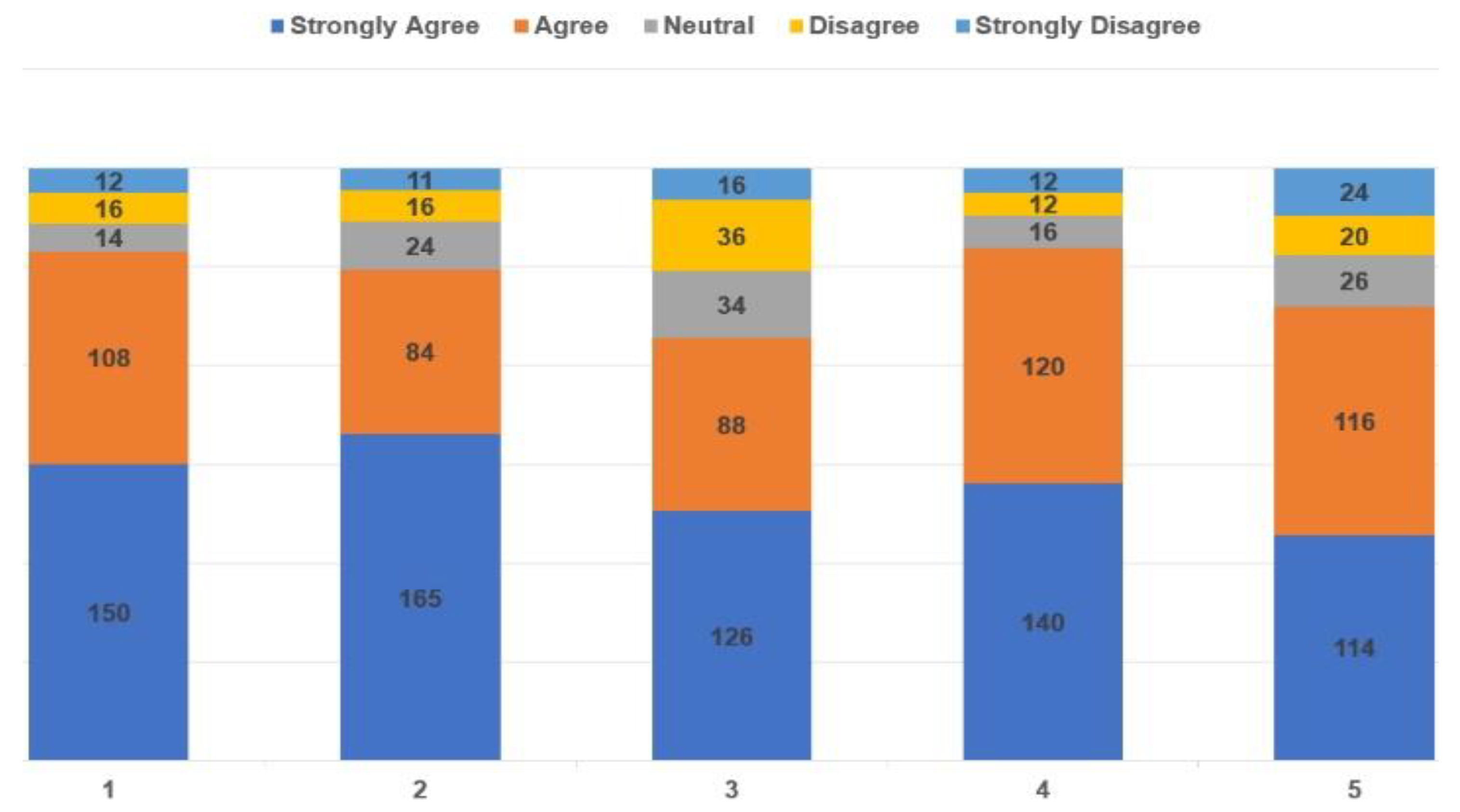
- Question 1: 86% (258 out of 300) of the users agreed that they felt more confident to use web-based applications via biometric devices when they saw that the testers could not login to the FBAS using the fingerprint sensor of an unregistered mobile device (MD:4.5, SD: 1.04).
- (b)
- Question 2: 83% (249 out of 300) of the users that responded agreed or strongly agreed that the concept of getting the server-side installation ID (SID) on the verification of the OTP is very useful for prompt action (MD: 5, SD: 1.16).
- (c)
- Question 3: 71.33% (214 out of 300) of the users that responded agreed or strongly agreed that, with this kind of “add-on” extra layer of security, biometric technologies could be more convenient and reliable than password-based access systems (MD: 4, SD: 1.22).
- (d)
- Question 4: 86.66% (260 out of 300) of the users that responded agreed or strongly agreed that the MoLaBSS could make access to personal information more secure (MD: 4, SD: 0.99).
- (e)
- Question 5: 76.66% (230 out of 300) of the users that responded agreed or strongly agreed that the MoLaBSS could be useful for many groups of people (MD: 4, SD: 1.21).
- (f)
- Overall, the survey results for the success of MoLaBSS are very favorable, with an average of 80.66% of the testers responding with agree or strongly agree to the above five survey questions.
6. Discussion on Implementation Opportunities and Challenges
6.1. Authentication/Validation Challenges
6.2. Training, Awareness and Adaptation Challenges
6.3. Security and Privacy Challenges
7. Conclusions and Future Perspectives
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Appendix A
References
- Spirina, K. Biometric Authentication: The Future of IoT Security Solutions, 5 July 2018. 2020 IoTEVOLUTIONWORLD. Available online: https://www.iotevolutionworld.com/iot/articles/438690-biometric-authentication-future-iot-security-solutions.htm (accessed on 3 June 2020).
- Abomhara, M.; Køien, G. Cybersecurity and the Internet of Things: Vulnerabilities, threats, intruders and attacks. J. Cyber Secur. 2015, 4, 65–88. [Google Scholar] [CrossRef]
- Ramírez-López, F.; Varela-Vaca, Á.J.; Ropero, J.; Luque, J.; Carrasco, A. A Framework to Secure the Development and Auditing of SSL Pinning in Mobile Applications: The Case of Android Devices. Entropy 2019, 21, 1136. [Google Scholar] [CrossRef]
- Jalali, M.; Kaiser, J.P.; Jarrett, M.; Ghaffarzadegan, N. Cybersecurity in Hospitals: A Systematic, Organizational Perspective. J. Med. Internet Res. 2018, 20, e10059. [Google Scholar] [CrossRef]
- Cherqi, O.; Mezzour, G.; Ghogho, M.; El Koutbi, M. Analysis of Hacking Related Trade in the Darkweb. In Proceedings of the 2018 IEEE International Conference on Intelligence and Security Informatics (ISI), Miami, FL, USA, 9–11 November 2018; pp. 79–84. [Google Scholar]
- Richard, G. Most Common and Hackable Passwords on the Internet, 12 September 2013. Available online: https://www.telegraph.co.uk/technology/internet-security/10303159/Most-common-and-hackable-passwords-on-the-internet.html (accessed on 3 June 2020).
- Yıldırım, M.; Mackie, I. Encouraging users to improve password security and memorability. Int. J. Inf. Secur. 2019, 18, 741–759. [Google Scholar] [CrossRef]
- O’Connor, F. What Happens If Your Biometrics Are Stolen? Veridium Ltd.: London, UK, 2019; Available online: https://www.veridiumid.com/blog/biometric-mythbusters-stolen-fingerprints-mean-identity-theft/ (accessed on 3 June 2020).
- Joy, K. Biometrics in Healthcare: How It Keeps Patients and Data Safe? 23 December 2019. Available online: https://healthtechmagazine.net/article/2019/12/biometrics-healthcare-how-it-keeps-patients-and-data-safe-perfcon (accessed on 3 June 2020).
- Varela-Vaca, Á.J.; Gasca, R.M.; Ceballos, R.; Gómez-López, M.T.; Torres, P. CyberSPL: A Framework for the Verification of Cybersecurity Policy Compliance of System Configurations Using Software Product Lines. Appl. Sci. 2019, 9, 5364. [Google Scholar] [CrossRef]
- Arthur, C. iPhone 5S Fingerprint Sensor Hacked by Germany’s Chaos Computer Club. The Gaurdian, 23 Sepember 2013. Available online: https://www.theguardian.com/technology/2013/sep/22/apple-iphone-fingerprint-scanner-hacked (accessed on 3 June 2020).
- Razaghpanah, A.; Sundaresan, S.; Niaki, A.A.; Amann, J.; Vallina-Rodriguez, N.; Gill, P. Studying TLS usage in Android apps. In Proceedings of the 13th International Conference on Emerging Technologies. (CoNEXT 2017), Ingeon, Korea, 12–15 December 2017; pp. 350–362. [Google Scholar]
- Hacking Responsible for 83% of Breached Healthcare Records in January. HIPAA Journal, Last modified 1 March 2018. Available online: https://www.hipaajournal.com/hacking-responsible-83-breached-healthcarerecords-january (accessed on 3 June 2020).
- Srinivasan, A.; Nguyen, A.; Tarlecki, R. STUMP–STalling offline password attacks Using pre-hash ManiPulations. In Proceedings of the 2015 IEEE 21st International Conference on Parallel and Distributed Systems (ICPADS), Melbourne, Australia, 14–17 December 2015; pp. 306–313. [Google Scholar]
- McDonough, B.R. Cyber Smart: Five Habits to Protect Your Family, Money, and Identity from Cyber Criminals; John Wiley & Sons: Hoboken, NJ, USA, 2019. [Google Scholar]
- Kapko, M.; Finnegan, M. What is Windows Hello? Microsoft’s Biometrics Security System Explained. Computerworld. 26 November 2018. Available online: https://www.computerworld.com/article/3244347/what-is-windows-hello-microsofts-biometrics-security-system-explained.html (accessed on 3 June 2020).
- Avinash, S.; Wu, J.; Shi, J. Secure android covert channel with robust survivability to service provider restrictions. Int. J. Secur. Netw. 2017, 12, 27–39. [Google Scholar]
- Gavrilova, M.L.; Monwar, M. Multimodal Biometrics and Intelligent Image Processing for Security Systems; IGI Global: Hershey, PA, USA, 2013; pp. 48–148. [Google Scholar] [CrossRef]
- Cheng, J. Securing IP Surveillance Cameras in the IoT Ecosystem. Trend Micro IoT Security. 18 April 2018. Available online: https://www.trendmicro.com/vinfo/mx/security/news/internet-of-things/securing-ip-surveillance-cameras-in-the-iot-ecosystem (accessed on 3 June 2020).
- Aghili, S.F.; Mala, H.; Shojafar, M.; Peris-Lopez, P. LACO: Lightweight Three-Factor Authentication, Access Control and Ownership Transfer Scheme for E-Health Systems in IoT. Futur. Gener. Comput. Syst. 2019, 96, 410–424. [Google Scholar] [CrossRef]
- Meng, W.; Wong, D.S.; Furnell, S.; Zhou, J. Surveying the Development of Biometric User Authentication on Mobile Phones. IEEE Commun. Surv. Tutor. 2014, 17, 1268–1293. [Google Scholar] [CrossRef]
- Chen, Y.; Sun, J.; Zhang, R.; Zhang, Y.; Yimin, C. Your song your way: Rhythm-based two-factor authentication for multi-touch mobile devices. In Proceedings of the 2015 IEEE Conference on Computer Communications (INFOCOM), Hong Kong, China, 26 April–1 May 2015; pp. 2686–2694. [Google Scholar]
- Ferrag, M.A.; Maglaras, L.; Derhab, A.; Janicke, H. Authentication schemes for smart mobile devices: Threat models, countermeasures, and open research issues. Telecommun. Syst. 2019, 73, 317–348. [Google Scholar] [CrossRef]
- He, D.; Bu, J.; Chan, S.; Chen, C.; Yin, M. Privacy-Preserving Universal Authentication Protocol for Wireless Communications. IEEE Trans. Wirel. Commun. 2010, 10, 431–436. [Google Scholar] [CrossRef]
- Li, W.; Gu, Q.; Zhao, Y.; Wang, P. Breaking Two Remote User Authentication Systems for Mobile Devices. In Proceedings of the 2017 IEEE 3rd International Conference on Big Data Security on Cloud (Bigdatasecurity), Ieee International Conference on High Performance and Smart Computing (HPSC), and Ieee International Conference on Intelligent Data and Security (IDS), Beijing, China, 26–28 May 2017; pp. 37–42. [Google Scholar]
- Traore, I.; Woungang, I.; Nakkabi, Y.; Obaidat, M.S.; Ahmed, A.A.E.; Khalilian, B. Dynamic Sample Size Detection in Learning Command Line Sequence for Continuous Authentication. IEEE Trans. Syst. Man Cybern. 2012, 42, 1343–1356. [Google Scholar] [CrossRef] [PubMed]
- Mondal, S.; Bours, P. Continuous Authentication in a real world settings. In Proceedings of the 2015 Eighth International Conference on Advances in Pattern Recognition (ICAPR), Kolkata, India, 4–7 January 2015; pp. 1–6. [Google Scholar]
- Buduru, A.B.; Yau, S.S. An Effective Approach to Continuous User Authentication for Touch Screen Smart Devices. In Proceedings of the 2015 IEEE International Conference on Software Quality, Reliability and Security, Vancouver, BC, Canada, 3–5 August 2015; pp. 219–226. [Google Scholar]
- Mondal, S.; Bours, P. Continuous authentication and identification for mobile devices: Combining security and forensics. In Proceedings of the 2015 IEEE International Workshop on Information Forensics and Security (WIFS), Rome, Italy, 16–19 November 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Aghili, S.F.; Mala, H.; Peris-Lopez, P. Securing Heterogeneous Wireless Sensor Networks: Breaking and Fixing a Three-Factor Authentication Protocol. Sensors 2018, 18, 3663. [Google Scholar] [CrossRef] [PubMed]
- Damaševičius, R.; Maskeliūnas, R.; Kazanavicius, E.; Woźniak, M. Combining Cryptography with EEG Biometrics. Comput. Intell. Neurosci. 2018, 2018, 1867548. [Google Scholar] [CrossRef] [PubMed]
- Wu, G.; Wang, J.; Zhang, Y.; Jiang, S. A Continuous Identity Authentication Scheme Based on Physiological and Behavioral Characteristics. Sensors 2018, 18, 179. [Google Scholar] [CrossRef] [PubMed]
- Bamasag, O.O.; Youcef-Toumi, K. Towards continuous authentication in the Internet of Things based on secret Sharing Scheme. In Proceedings of the WESS’15: Workshop on Embedded Systems Security, Amsterdam, The Netherlands, 4–9 October 2015; pp. 1–8. [Google Scholar]
- Vhaduri, S.; Poellabauer, C. Multi-Modal Biometric-Based Implicit Authentication of Wearable Device Users. IEEE Trans. Inf. Forensics Secur. 2019, 14, 3116–3125. [Google Scholar] [CrossRef]
- Li, S.Z.; Jain, A. Encyclopedia of Biometrics; Chapter Passive Biometrics; Springer: Boston, MA, USA, 2009; pp. 46–65. [Google Scholar] [CrossRef]
- Olanrewaju, L.; Oyebiyi, O.; Misra, S.; Maskeliūnas, R.; Damaševičius, R. Secure Ear Biometrics Using Circular Kernel Principal Component Analysis, Chebyshev Transform Hashing and Bose–Chaudhuri–Hocquenghem Error-Correcting Codes, January 2020. Available online: https://link.springer.com/article/10.1007%2Fs11760-019-01609-y (accessed on 3 June 2020).
- Damaševičius, R.; Maskeliūnas, R.; Venckauskas, A.; Woźniak, M. Smartphone User Identity Verification Using Gait Characteristics. Symmetry 2016, 8, 100. [Google Scholar] [CrossRef]
- Spanakis, E.G.; Spanakis, M.; Karantanas, A.; Marias, K. Secure access to patient’s health records using SpeechXRays, a multi-channel biometrics platform for user authentication. In Proceedings of the annual international conference of the IEEE Engineering in Medicine and Biology Society, Orlando, FL, USA, 16–20 August 2016; pp. 2541–2544. [Google Scholar]
- Spanakis, M.; Manikis, G.; Porwal, S.; Spanakis, E.G. Developing a context-dependent tuning framework of multi-channel biometrics that combine audio-visual characteristics for secure access in the eHealth platform for osteoarthritis management. In Proceedings of the 7th EAI International Conference on Wireless Mobile Communication and Healthcare, Vienna, Austria, 14–15 November 2017. [Google Scholar]
- McCool, C.; Marcel, S.; Hadid, A.; Pietikäinen, M.; Matějka, P.; Cernock, J.; Poh, N.; Kittler, J.; Larcher, A.; Lévy, C.; et al. Bi-Modal Person Recognition on a Mobile Phone: Using Mobile Phone Data. In Proceedings of the 2012 IEEE International Conference on Multimedia and Expo Workshops, Melbourne, Australia, 9–13 July 2012; pp. 635–640. [Google Scholar]
- Manikis, G.C.; Spanakis, M.; Spanakis, E.G. Personalized Mobile eHealth Services for Secure User Access Through a Multi Feature Biometric Framework. Int. J. Reliab. Qual. E-Healthc. 2019, 8, 40–51. [Google Scholar] [CrossRef]
- Syed, Z.; Helmick, J.; Banerjee, S.; Cukic, B. Touch gesture-based authentication on mobile devices: The effects of user posture, device size, configuration, and inter-session variability. J. Syst. Softw. 2019, 149, 158–173. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Maglaras, L.; Janicke, H.; Jiang, J.; Shu, L. Authentication Protocols for Internet of Things: A Comprehensive Survey. Secur. Commun. Netw. 2017, 2017, 6563953. [Google Scholar] [CrossRef]
- Jain, A.K.; Ross, A. Bridging the gap: From biometrics to forensics. Philos. Trans. R. Soc. B Biol. Sci. 2015, 370, 20140254. [Google Scholar] [CrossRef]
- Fernández-Cerero, D.; Varela-Vaca, Á.J.; Fernández-Montes, A.; Gómez-López, M.T.; Alvárez-Bermejo, J.A. Measuring data-centre workflows complexity through process mining: The Google cluster case. J. Supercomput. 2019, 76, 2449–2478. [Google Scholar] [CrossRef]
- Juned, M. How to Get Current GPS Coordinates Location Android Programmatically. Available online: https://www.android-examples.com/get-current-gps-coordinates-location-android-programmatically (accessed on 3 June 2020).
- Juned, M. How to Get Facebook Login User Data ID, First Name, Last Name, Email, Gender, Link, Locale and Account Verified Status Programmatically, May 2017. Available online: https://www.android-examples.com/facebook-login-graph-api-get-user-info (accessed on 3 June 2020).
- Configuring Identix Biometric Authentication. Available online: https://docs.oracle.com/cd/F49540_01/DOC/network.815/a67766/07_ident.htm (accessed on 3 March 2019).
- Using the Fingerprint Certificate Mapper. Available online: https://docs.oracle.com/cd/E19476-01/821-0506/using-fingerprint-cert-mapper.html (accessed on 5 June 2019).
- Device Fingerprinting and Identification, Oracle Adaptive Access Manager (OAAM). Available online: https://docs.oracle.com/cd/E40329_01/admin.1112/e60557/finger.htm#AAMAD6186 (accessed on 5 June 2019).
- Roy, T.K.; Roy, T.K. Fingerprint Acquisition & Verification on Mobile Devices. In Proceedings of the 2018 International Conference on Computer, Communication, Chemical, Material and Electronic Engineering (IC4ME2), Rajshahi, Bangladesh, 8–9 February 2018; pp. 1–5. [Google Scholar]
- Perla, R.J.; Provost, L.P. Judgment sampling: A health care improvement perspective. Qual. Manag. Healthc. 2012, 21, 169–175. [Google Scholar] [CrossRef] [PubMed]
- Phan, K.A.; Tari, Z.; Bertok, P. A benchmark on soap’s transport protocols performance for mobile applications. In Proceedings of the 2006 ACM Symposium on Applied Computing–SAC’06, Dijon, France, 23–27 April 2006. [Google Scholar] [CrossRef]
- Oliveira, W.; Oliveira, R.; Castor, F. A Study on the Energy Consumption of Android App Development Approaches. In Proceedings of the 2017 IEEE/ACM 14th International Conference on Mining Software Repositories (MSR), Buenos Aires, Argentina, 20–21 May 2017; pp. 42–52. [Google Scholar] [CrossRef]
- Afzaal, M.; Usman, M.; Fong, A.C. Tourism Mobile App with Aspect-Based Sentiment Classification Framework for Tourist Reviews. IEEE Trans. Consum. Electron. 2019, 65, 233–242. [Google Scholar] [CrossRef]
- Brooke, J. SUS: A Quick and Dirty Usability Scale; Jordan, P.W., Thomas, B., Weerdmeester, B.A., McClelland, I.L., Eds.; Usability Evaluation in Industry; Taylor & Francis: London, UK, 1996. [Google Scholar]
- Nishaan Bio-Guard_Biometrics_App, 2019. Copyright: GitHub, Inc., 2019. Available online: https://github.com/NishaanGHac/Bio-Guard_Biometrics_app (accessed on 3 June 2020).
- Jeff Sauro, M.E. Assuring Usability with the System the System Usability Scale (SUS), 2 February 2011. Available online: https://measuringu.com/sus/ (accessed on 3 June 2020).
- Jorgensen, Z.; Yu, T. On mouse dynamics as a behavioral biometric for authentication. In Proceedings of the 6th ACM Symposium on Development and Analysis of Intelligent VehicularNetworks and Applications–DIVANet’17; Association for Computing Machinery (ACM): New York, NY, USA, 2011; pp. 476–482. [Google Scholar]
- Lee, D.; Park, J.; Song, M. An App-Based Authoring System for Personalized Sensory Stimulation of Children With Developmental Disabilities. IEEE Access 2017, 5, 10583–10593. [Google Scholar] [CrossRef]
- Bangor, A.; Kortum, P.; Miller, J. Determining what individual SUS scores mean: Adding an adjective rating scale. J. Usability Study 2009, 4, 114–123. [Google Scholar]
- Conn, S. Gartner Identifies the Top 10 Internet of Things Technologies for 2017 and 2018, 23 February 2016. Available online: https://www.gartner.com/en/newsroom/press-releases/2016-02-23-gartner-identifies-the-top-10-internet-of-things-technologies-for-2017-and-2018 (accessed on 3 June 2020).


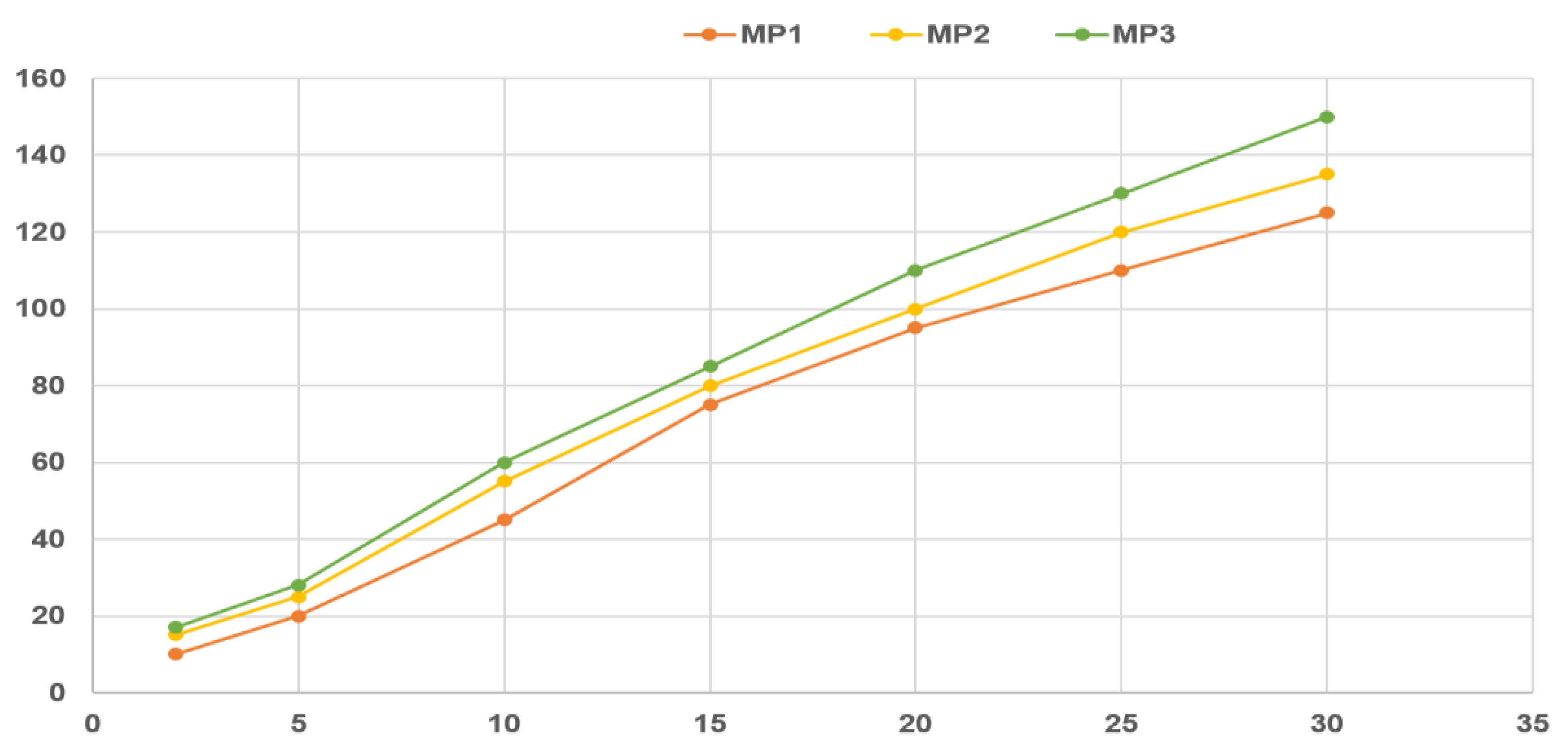
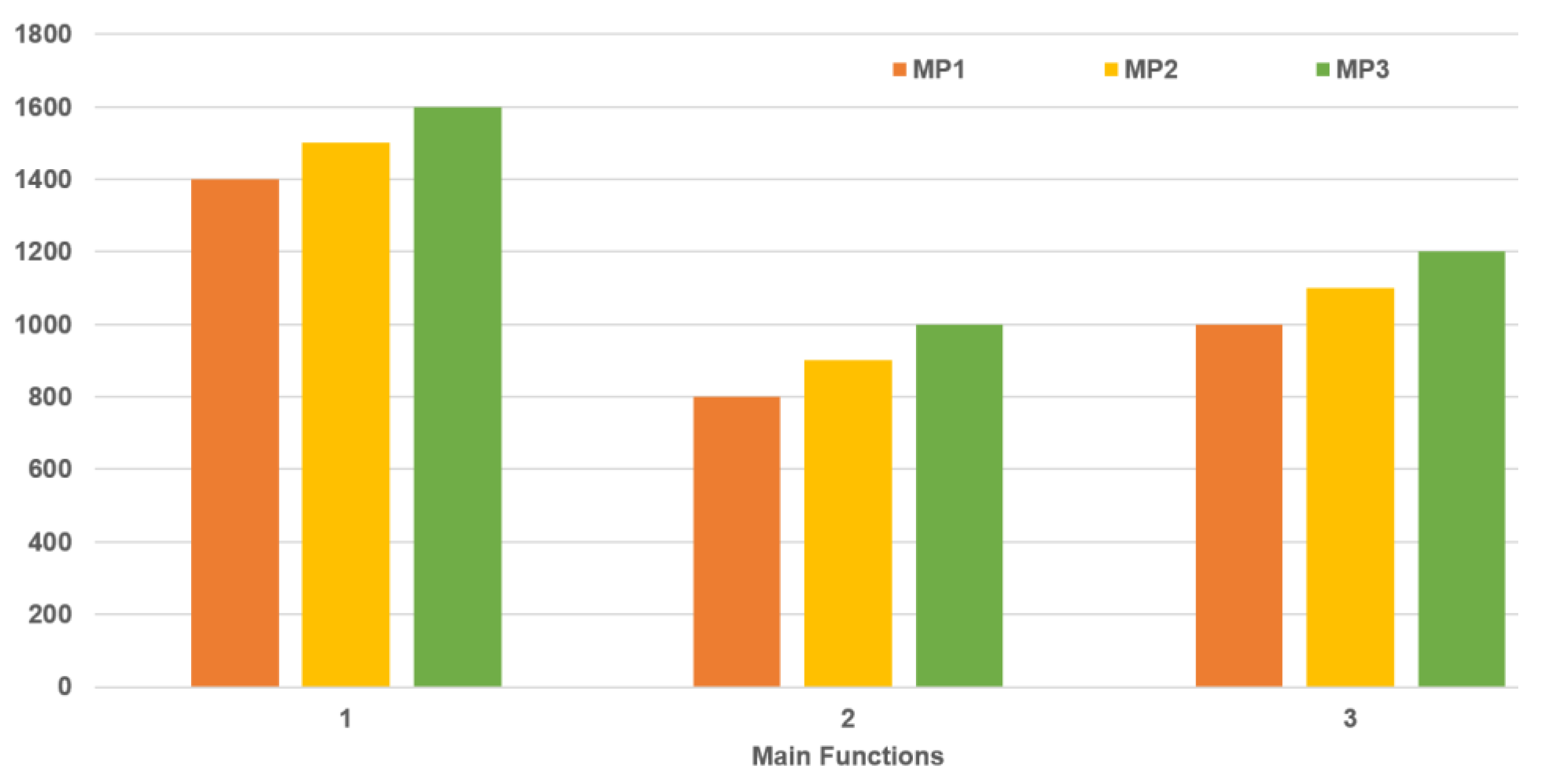
| Mobile Phone | Year Made | HDD Capacity | RAM in GB | CPU in GHz | Battery in (mAh) |
|---|---|---|---|---|---|
| MP1 | 2019 | 32 | 16 | 2.3 Octa-core Quad | 3000 |
| MP2 | 2018 | 16 | 8 | 1.4 Quad-Core | 2000 |
| MP3 | 2017 | 8 | 4 | 1.2 Quad-Core | 2000 |
| Expt Q1. It was easy to install, register, and complete the setup of the app. |
| Expt Q2. It was difficult to register to the “Bio-Guard” app via Google account. |
| Expt Q3. Getting the server-side installation ID (SID1) was quick, on verification of the OTP2. |
| Expt Q4. It was difficult to load the app on the screen after a single tap of the “Bio-Guard” icon. |
| Expt Q5. The visual clarity and alignment of the app on the screen was good and convenient to use after it loaded on a single tap of the “Bio-Guard” icon. |
| Expt Q6. It was difficult to remotely log in to the FBAS3 application and access the personal profile via the fingerprint sensor of the mobile, after installing the “Bio-Guard” app. |
| Expt Q7. I felt more confident in the “Bio-Guard” app when I could not log in to the FBAS, using the fingerprint sensor of an unregistered mobile. |
| Expt Q8. I lost confidence in using fingerprint sensors to remotely access my record after I received a notification when I logged in to the FBAS from another mobile device via OTP 2. |
| Expt Q9. All the box fields and buttons of the “Bio-Guard” app functioned with ease and as expected. |
| Expt Q10. It was difficult to close the app with a single tap of the “home/close” button of the mobile device. |
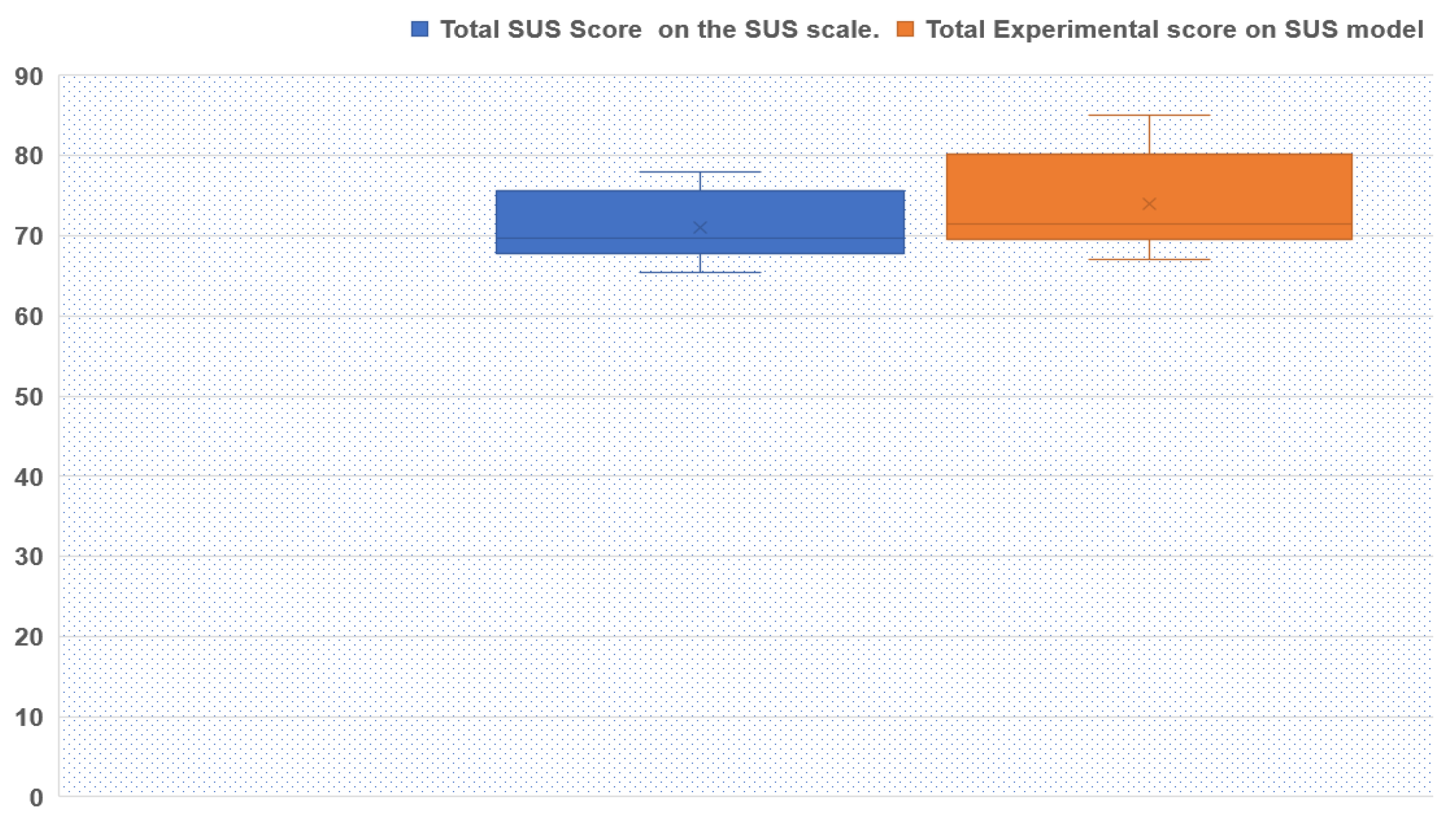
| Average/Mean SUS rating score of 110 Users | 71.2 |
| Average/Mean Experimental rating score on 110 users on SUS modeled experiment, performed for the Bio-Guard app | 73.95 |
| Std Dev of SUS rating score of 110 Users | 4.342 |
| STD Dev Experimental rating score on 110 users on SUS modeled experiment, performed for the Bio-Guard app | 5.941 |
| (1) I felt more confident to use web-based applications via biometric devices when I saw that the testers could not login to the FBAS using the fingerprint sensor of an unregistered mobile device. |
| (2) The concept of getting the server-side installation ID (SID) only on the verification of the OTP is very useful for prompt preventive action. |
| (3) I think with this kind of add-on extra layer of security; biometric technologies can be more convenient and reliable than password-based access systems. |
| (4) I think MoLaBSS can make access to personal information more secure. |
| (5) After watching the performance of the Bio-Guard app, I think MoLaBSS can be useful for many groups of people. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Singh, B.; Singh, N. MoLaBSS: Server-Specific Add-On Biometric Security Layer Model to Enhance the Usage of Biometrics. Information 2020, 11, 308. https://doi.org/10.3390/info11060308
Singh B, Singh N. MoLaBSS: Server-Specific Add-On Biometric Security Layer Model to Enhance the Usage of Biometrics. Information. 2020; 11(6):308. https://doi.org/10.3390/info11060308
Chicago/Turabian StyleSingh, Bhanu, and Nirvisha Singh. 2020. "MoLaBSS: Server-Specific Add-On Biometric Security Layer Model to Enhance the Usage of Biometrics" Information 11, no. 6: 308. https://doi.org/10.3390/info11060308
APA StyleSingh, B., & Singh, N. (2020). MoLaBSS: Server-Specific Add-On Biometric Security Layer Model to Enhance the Usage of Biometrics. Information, 11(6), 308. https://doi.org/10.3390/info11060308







