Design and Evaluation of an Augmented Reality Game for Cybersecurity Awareness (CybAR)
Abstract
1. Introduction
2. Literature Review
3. CybAR Game Development
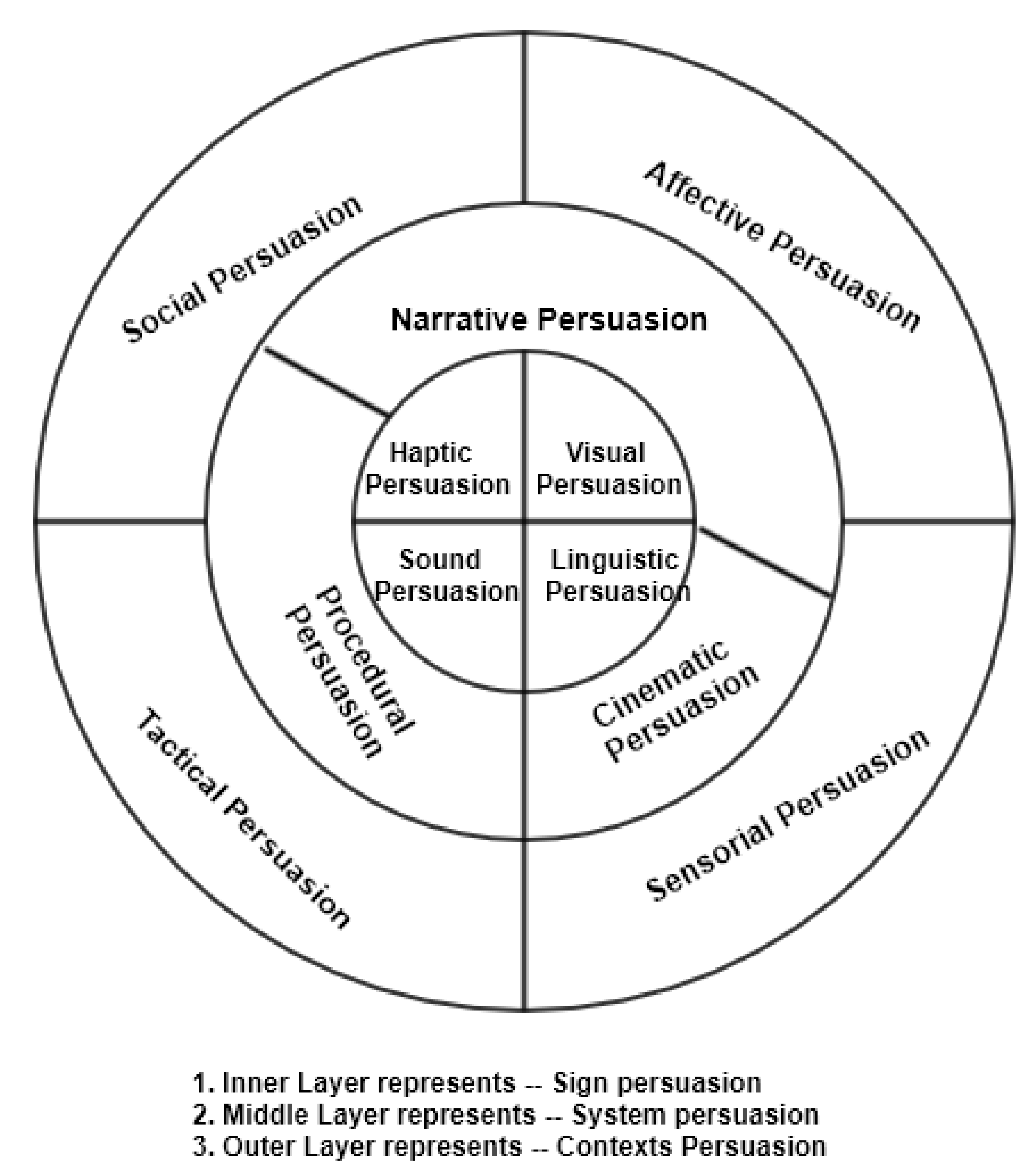
3.1. Game Design Framework
3.2. Game Concept
4. Game Description
4.1. Use Case
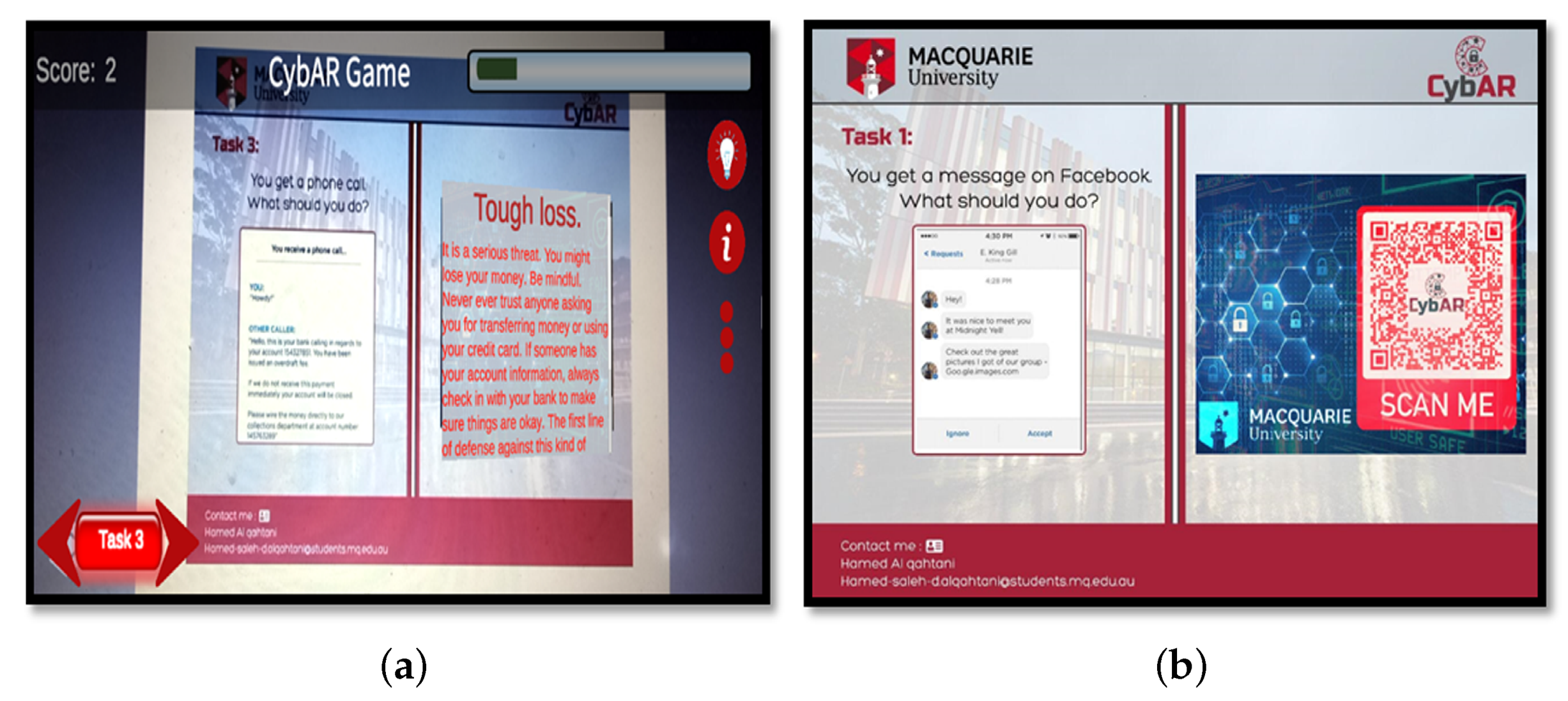
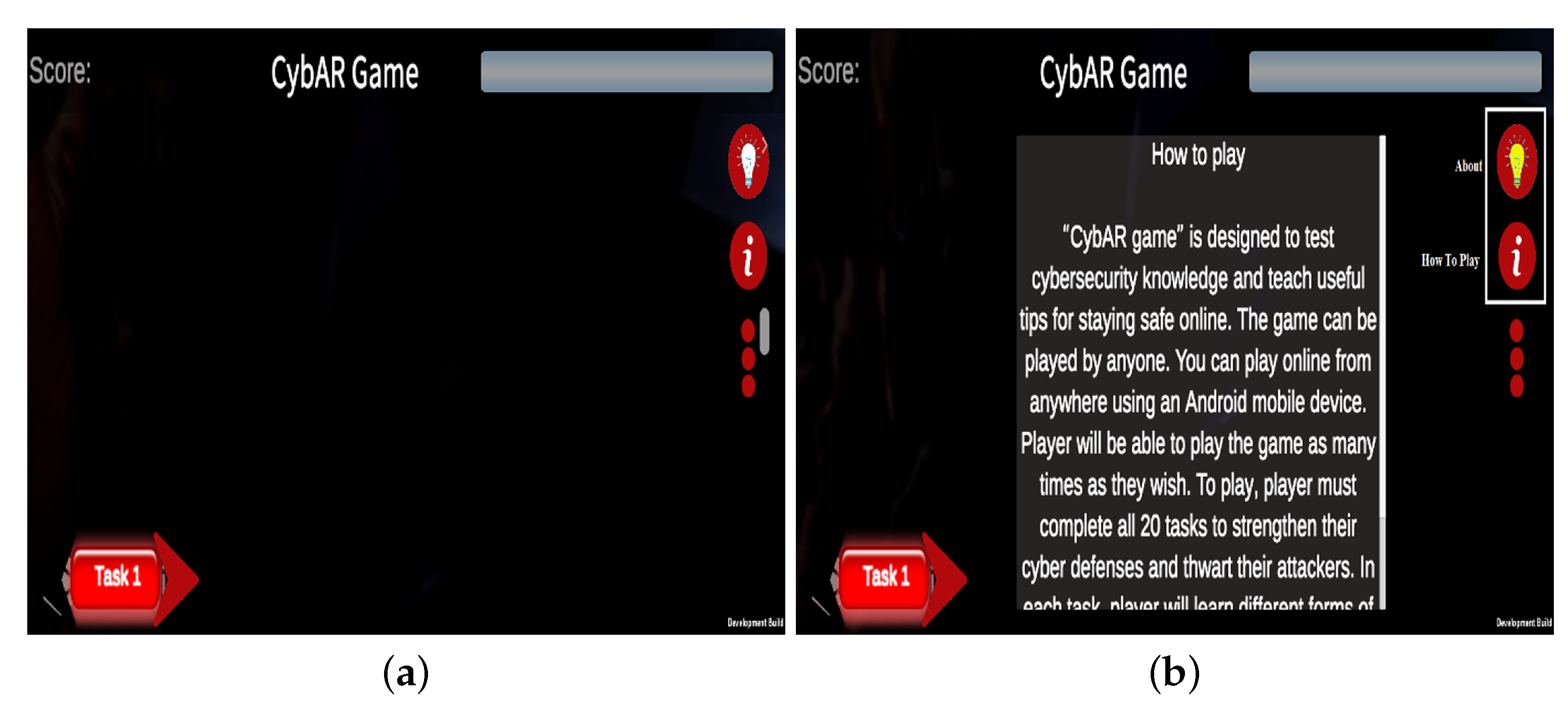
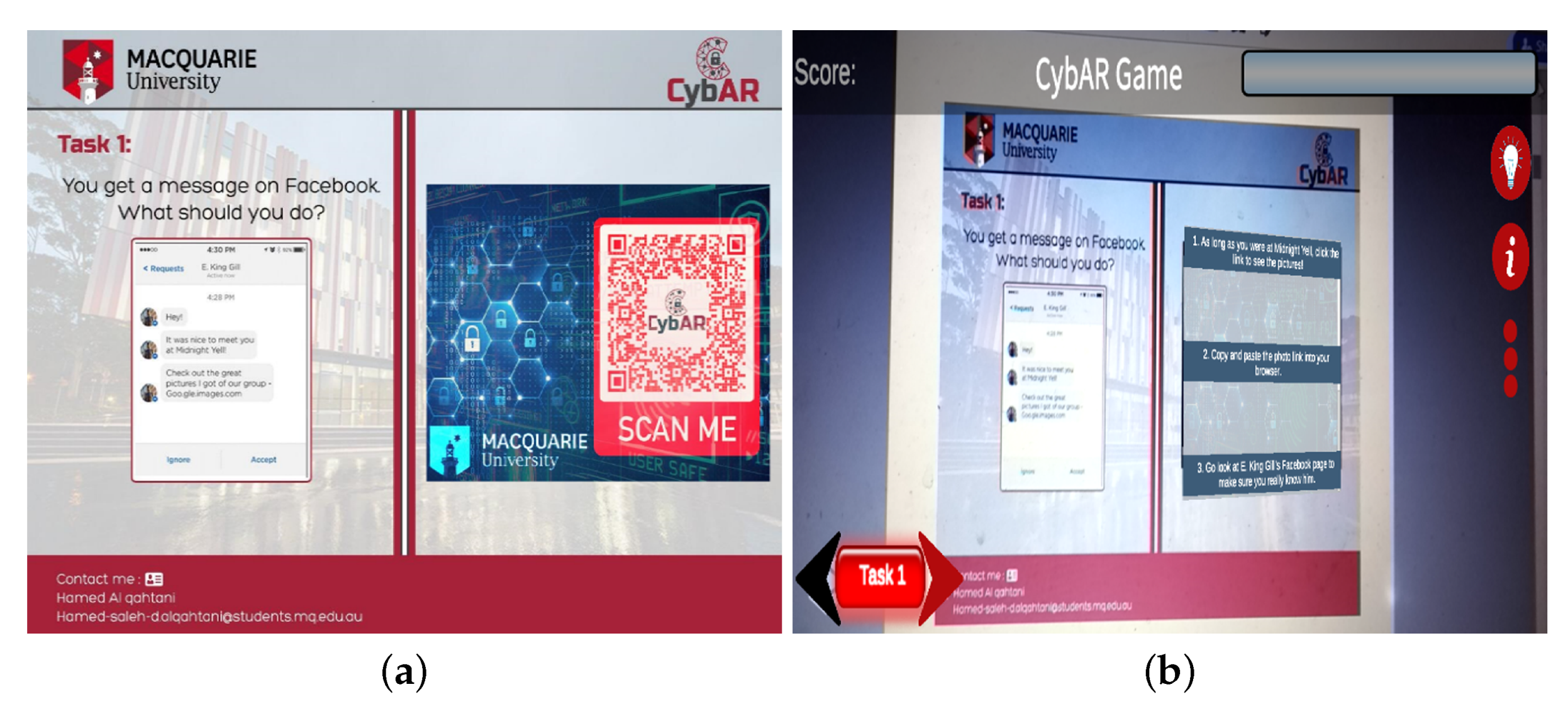
4.2. Tasks
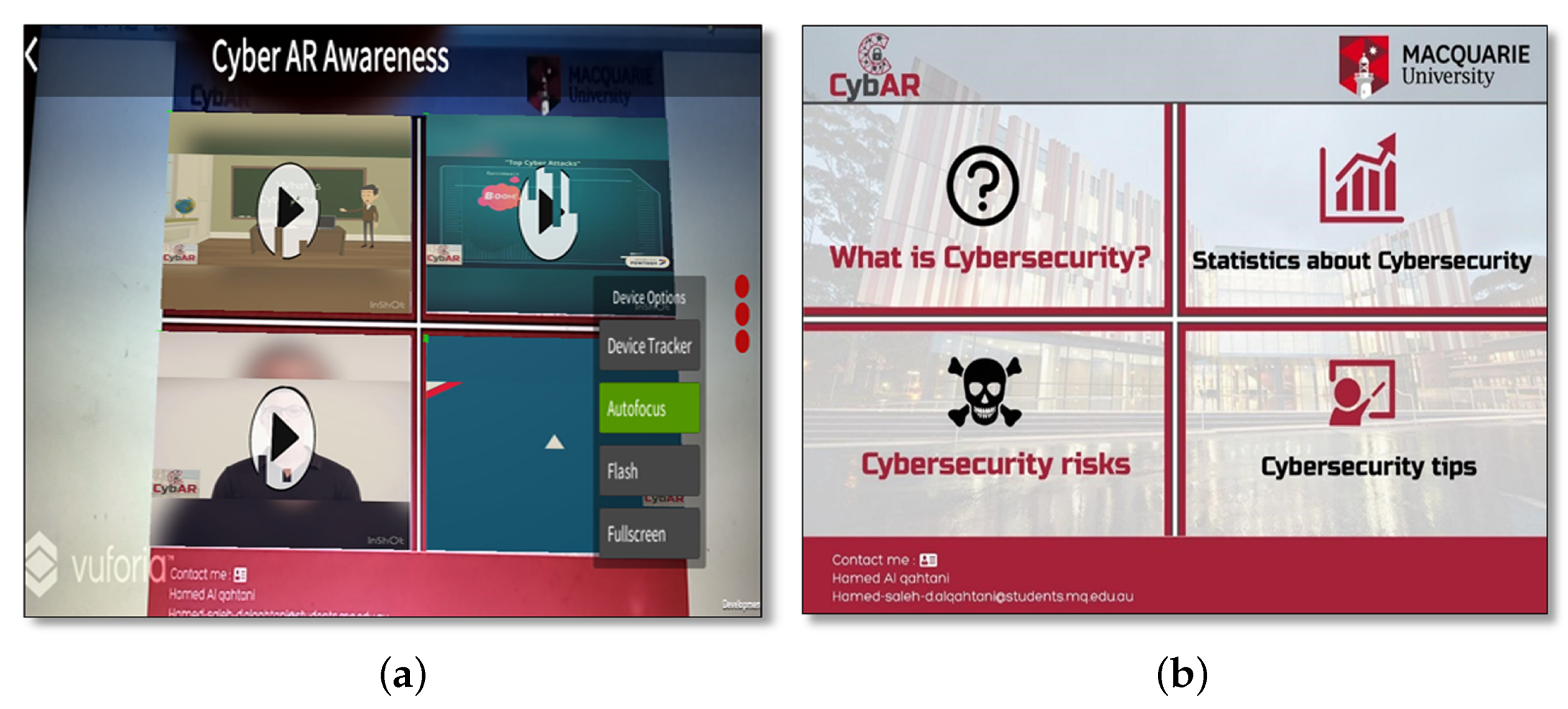
4.3. Mobile Game Design
- Rules: Rules organise the game. Each task was based on rules derived from the game design framework (TTAT). The participants were unanimous in their opinion that the game, while being educational and aiming to spread awareness of cybersecurity attacks, should have an evolving format that would keep the player engaged.
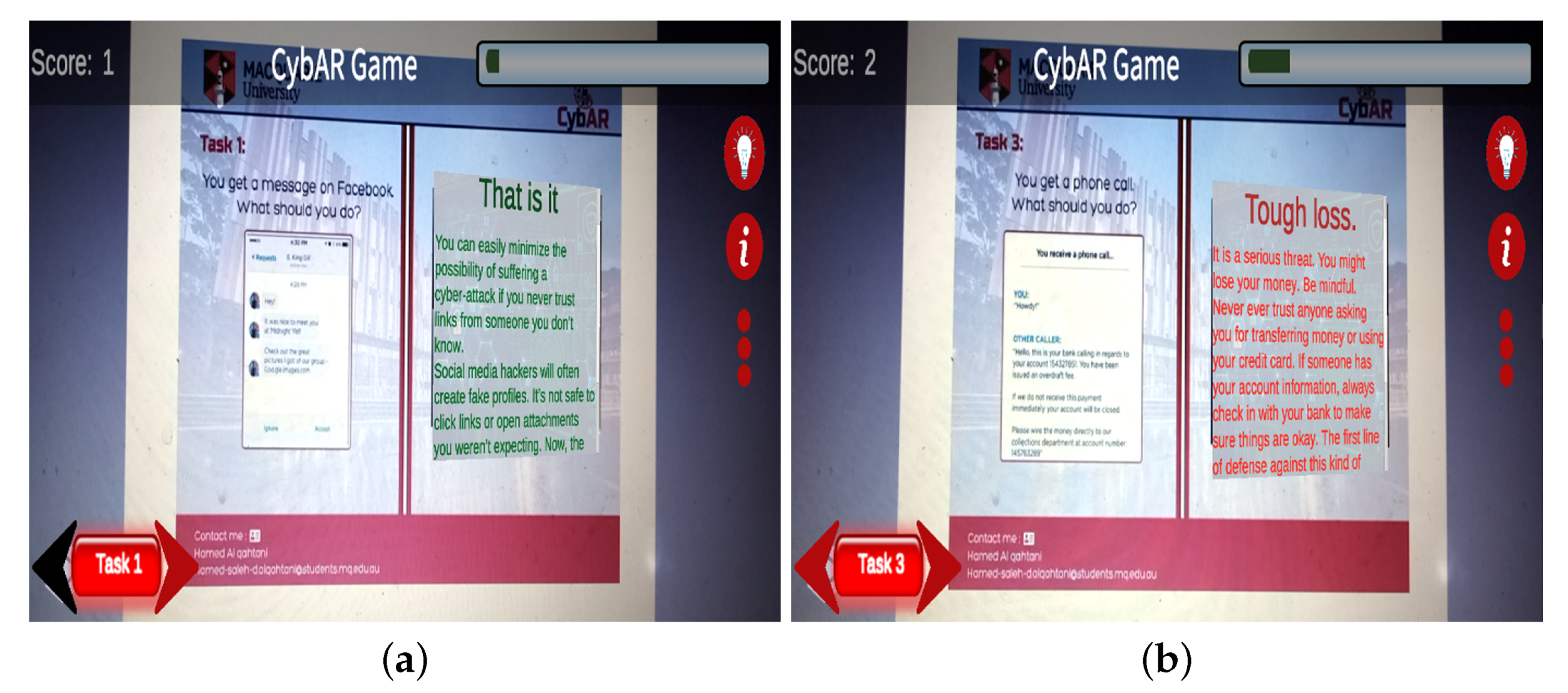
- Goals and objectives: Goals and objectives are what the player works to achieve. The goal is to perform all tasks correctly. This is reflected in the game design by providing three options (one correct, two false) for each task.An important aspect of cybersecurity training is teaching learners to appreciate the risks of a bad decision. Existing training materials often describe these as high-level risks, but do not really show the learner what will happen if something goes wrong. Therefore, CybAR simulates how the player’s decisions lead to various outcomes, both positive and negative. If the player makes a wrong decision, a violation feedback will appear, as shown in Figure 2. Similarly, if the player thinks an unsafe email is a phishing email, the immediate feedback will be that that this decision is correct. This approach helps players reflect on unfamiliar cyberattacks, which helps retain knowledge.
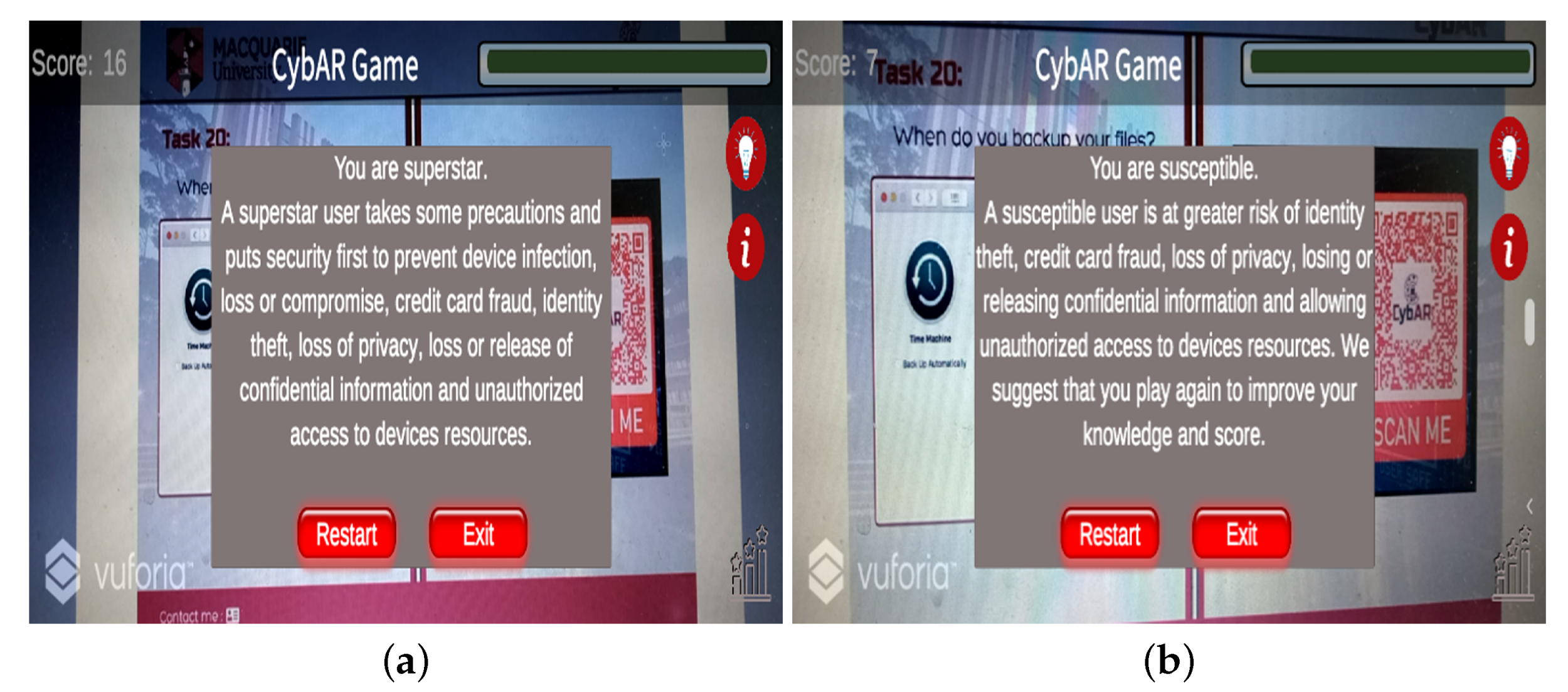
- Outcome and feedback: Outcome and feedback measure progress against goals. The user obtains feedback on the current status in the game. The feedback provides timely opportunities to explain consequences and deliver information. This ability to provide players with immediate and specific feedback based on their decisions optimises learning by explaining how their errors occurred and how their expectations failed [44]. Players also receive positive feedback when they make sound cybersecurity choices.In each task, we apply protection motivation theory [45] in immediate feedback when players accomplish the task. Two PMT-inspired guidelines are designed to trigger more secure behaviour after the task has been completed: If the task is performed correctly, a coping message appears telling the user it is easy to minimise the chances of cyberattacks by making the right decision for the task. For example: “GOOD JOB! It was easy to neglect such tweets because you are aware of cyberattacks. Fake social media profiles are easily created by scammers.” If the task is performed incorrectly, a message warns users that their action could leave them vulnerable to cyberattacks. For example, “Oops. That was not a legit pop up and your account has been hacked” (see Figure 4).
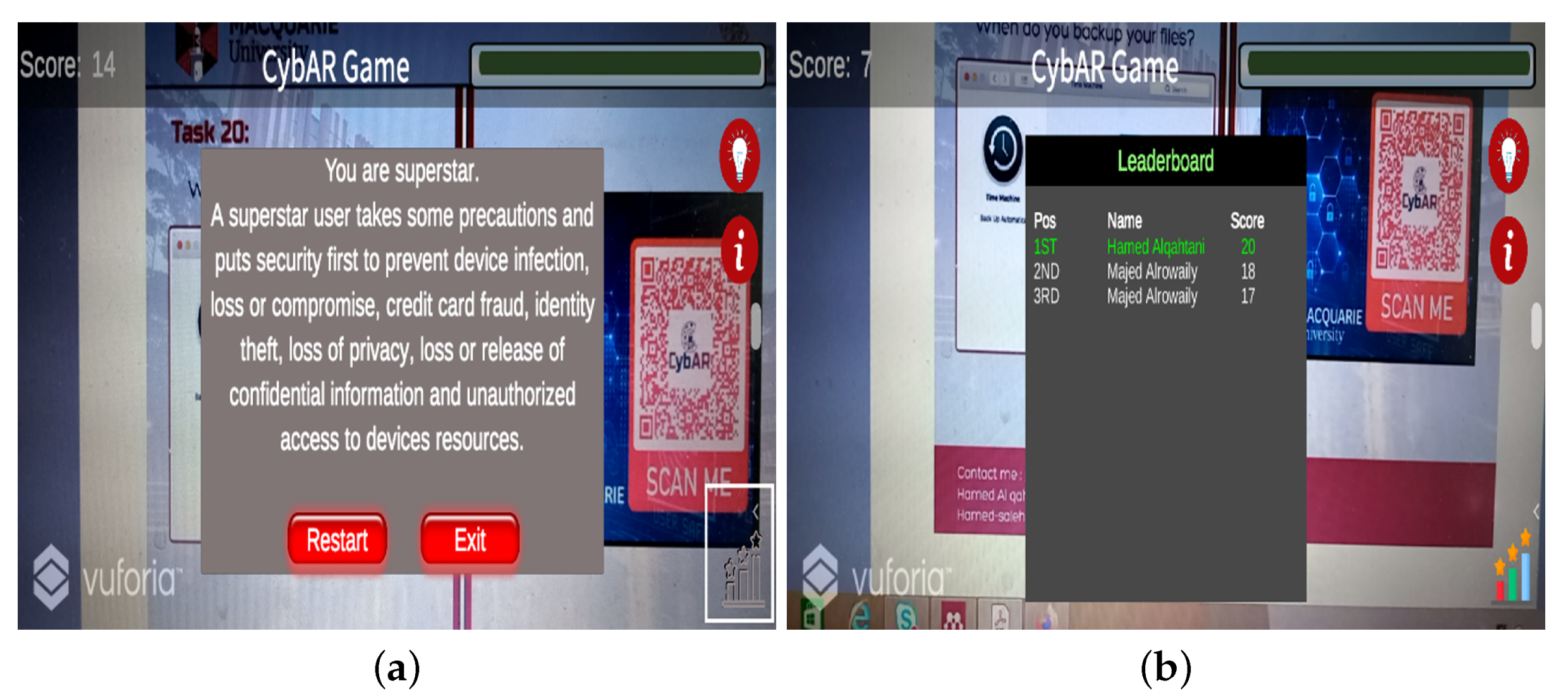
- Rewards: These are addressed in the mobile game design as the opportunity to gain points. The game should incorporate a rewards mechanism to incentivise players and keep their engagement levels high by rewarding them for their performance in the game. In CybAR, rewards are available by completing each task correctly and learning about cybersecurity-related concepts. If the user identifies all decisions correctly while avoiding all incorrect decisions, the player is awarded 20 points (for each attempt it is possible to score 1 point). If the user makes the wrong decisions, each attempt loses one point out of the total points remaining to complete the game. Participants can play the game as many times as they wish until they achieve a winning score. They can continue to play until their score is in the top ten on the leaderboard. If a player’s score is less than 65% (13 points out of 20), he or she is encouraged to replay the game to learn how to be safe online.
- Interaction: Interaction is the social aspect in the game design. This is accomplished by providing immediate feedback, a progress bar and scores. Players are able to view their progress. According to the focus group participants, the player’s progress should be contextualised in relation to the remaining game threats to convince them that successfully completing the game is an achievable target. They also recommended that players should not feel they were navigating away from the game when feedback was provided.
5. Implementation and Development Cycles
5.1. Development Cycles
5.2. User Interfaces
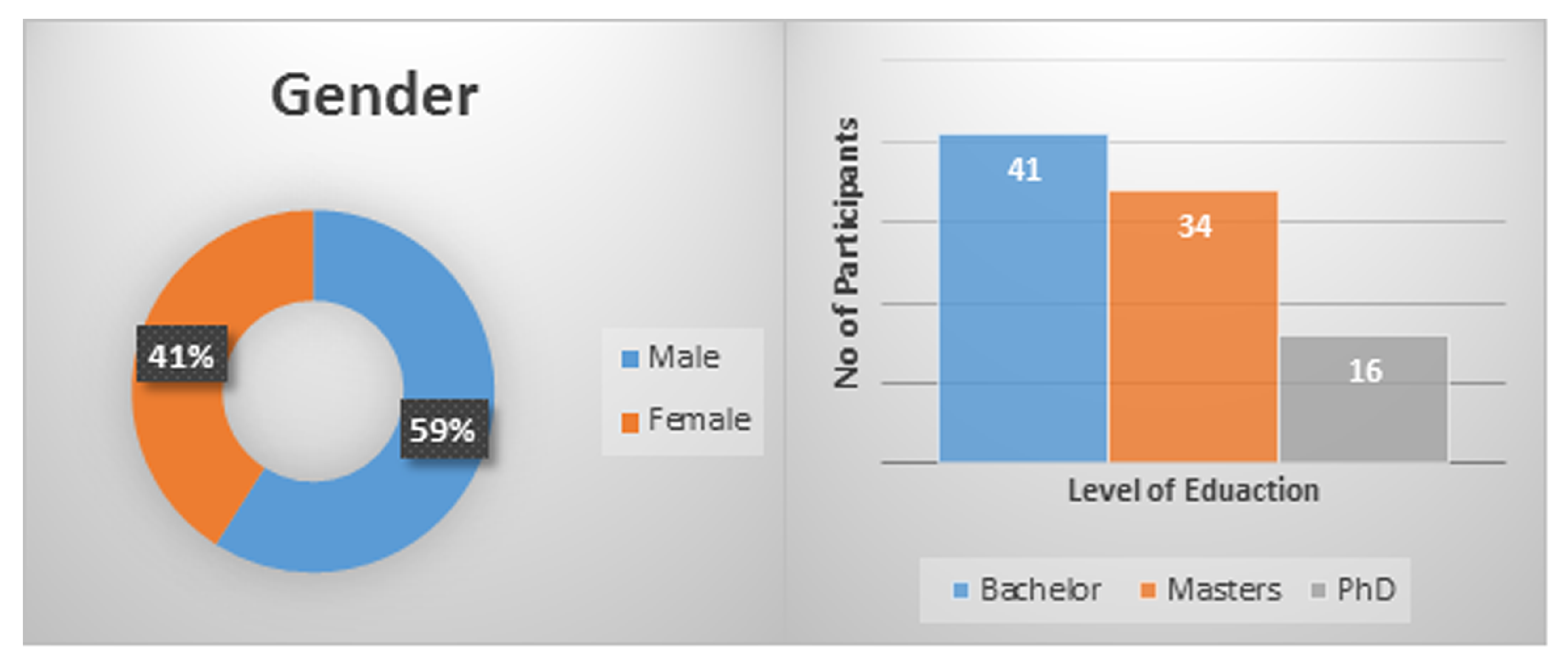
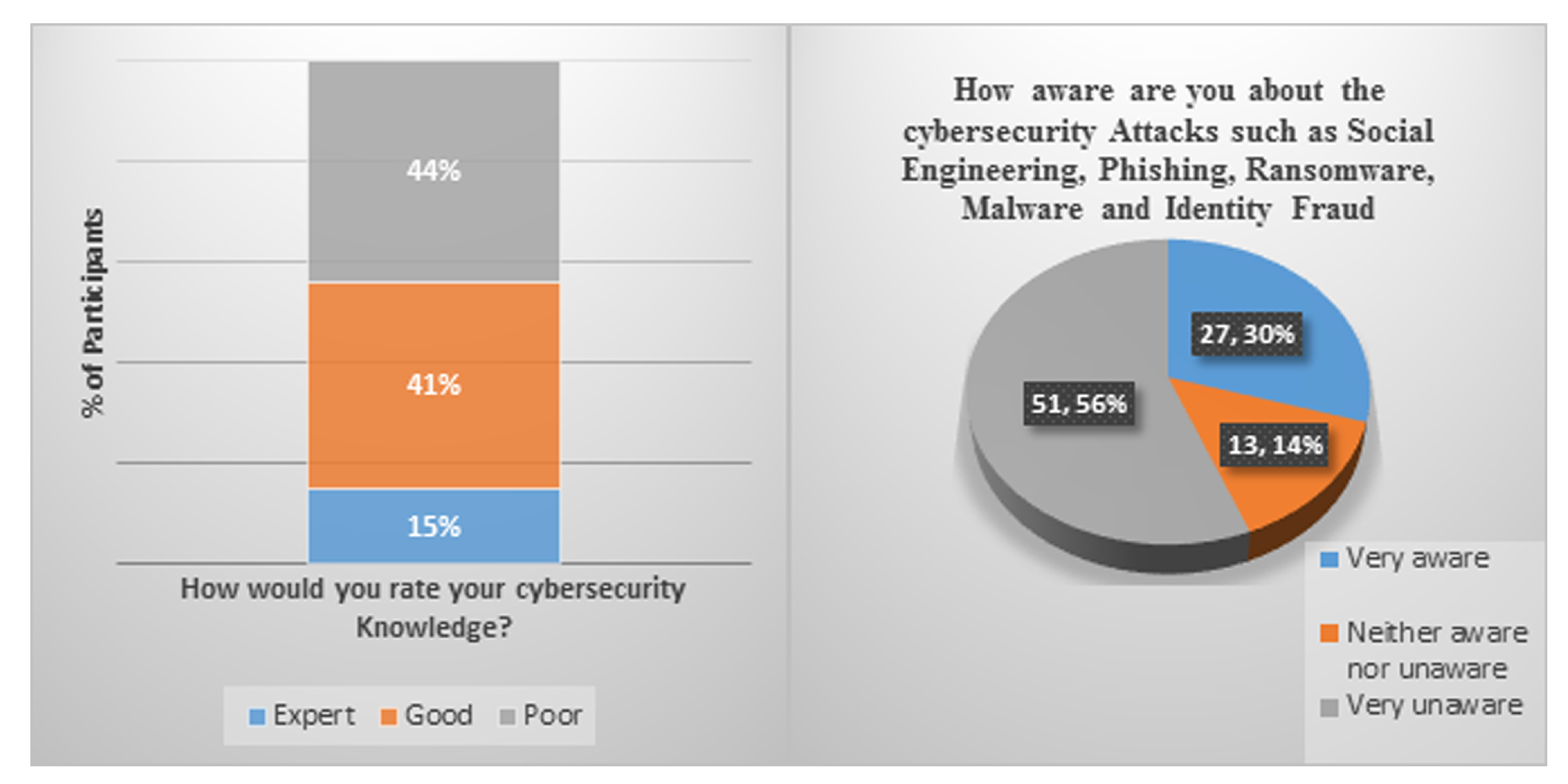
6. Research Methodology
CybAR Evaluation
7. Results and Analysis
8. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Moallem, A. Cybersecurity Awareness Among Students and Faculty; CRC Press: Boca Raton, FL, USA, 2019. [Google Scholar]
- Dhamija, R.; Tygar, J.D.; Hearst, M. Why phishing works. In Proceedings of the SIGCHI conference on Human Factors in Computing Systems; ACM: New York, NY, USA, 2006; pp. 581–590. [Google Scholar]
- Hui, C.P. How to study home users. In TKK T-110.5190, Seminar on Internetworking; Citeseer: Princeton, NJ, USA, 2007. [Google Scholar]
- Ciampa, M. Security Awareness: Applying Practical Security in Your World; Cengage Learning: Boston, MA, USA, 2013. [Google Scholar]
- Howard, D.; Prince, K. Security 2020: Reduce Security Risks This Decade; Wiley Publishing: Hoboken, NJ, USA, 2010. [Google Scholar]
- Al-Janabi, S.; Al-Shourbaji, I. A study of cyber security awareness in educational environment in the middle east. J. Inf. Knowl. Manag. 2016, 15, 1650007. [Google Scholar] [CrossRef]
- Alotaibi, F.; Furnell, S.; Stengel, I.; Papadaki, M. A review of using gaming technology for cyber-security awareness. Int. J. Inf. Secur. Res. (IJISR) 2016, 6, 660–666. [Google Scholar] [CrossRef]
- Conway, D.; Taib, R.; Harris, M.; Yu, K.; Berkovsky, S.; Chen, F. A qualitative investigation of bank employee experiences of information security and phishing. In Proceedings of the Thirteenth Symposium on Usable Privacy and Security ({SOUPS} 2017), Santa Clara, CA, USA, 12–14 July 2017; pp. 115–129. [Google Scholar]
- Kumaraguru, P.; Sheng, S.; Acquisti, A.; Cranor, L.F.; Hong, J. Teaching Johnny not to fall for phish. ACM Trans. Internet Technol. (TOIT) 2010, 10, 7. [Google Scholar] [CrossRef]
- Brooks, F.M.; Chester, K.L.; Smeeton, N.C.; Spencer, N.H. Video gaming in adolescence: factors associated with leisure time use. J. Youth Stud. 2016, 19, 36–54. [Google Scholar] [CrossRef]
- Connolly, T.M.; Boyle, E.A.; MacArthur, E.; Hainey, T.; Boyle, J.M. A systematic literature review of empirical evidence on computer games and serious games. Comput. Educ. 2012, 59, 661–686. [Google Scholar] [CrossRef]
- Shumaker, R. Virtual and Mixed Reality-Systems and Applications: International Conference, Virtual and Mixed Reality 2011, Held as Part of HCI International 2011, Orlando, FL, USA, 9–14 July 2011, Proceedings; Springer: Berlin, Germany, 2011; Volume 6774. [Google Scholar]
- Read, J.L.; Shortell, S.M. Interactive games to promote behavior change in prevention and treatment. JAMA 2011, 305, 1704–1705. [Google Scholar] [CrossRef]
- Burke, J.W.; McNeill, M.; Charles, D.K.; Morrow, P.J.; Crosbie, J.H.; McDonough, S.M. Optimising engagement for stroke rehabilitation using serious games. Vis. Comput. 2009, 25, 1085. [Google Scholar] [CrossRef]
- Deterding, S.; Dixon, D.; Khaled, R.; Nacke, L. From game design elements to gamefulness: Defining gamification. In Proceedings of the 15th International Academic MindTrek Conference: Envisioning Future Media Environments; ACM: New York, NY, USA, 2011; pp. 9–15. [Google Scholar]
- Wen, Z.A.; Lin, Z.; Chen, R.; Andersen, E. What. Hack: Engaging Anti-Phishing Training through a Role-playing Phishing Simulation Game. In Proceedings of the 2019 CHI Conference on Human Factors in Computing Systems; ACM: New York, NY, USA, 2019; p. 108. [Google Scholar]
- Alqahtani, H.; Kavakli, M. iMAP-CampUS (an Intelligent Mobile Augmented Reality Program on Campus as a Ubiquitous System): A Theoretical Framework to Measure User’s Behavioural Intention. In Proceedings of the 9th International Conference on Computer and Automation Engineering; ACM: New York, NY, USA, 2017; pp. 36–43. [Google Scholar]
- Alqahtani, H.; Kavakli, M. iMAP-CampUS: Developing an Intelligent Mobile Augmented Reality Program on Campus as a Ubiquitous System. In Proceedings of the 9th International Conference on Computer and Automation Engineering; ACM: New York, NY, USA, 2017; pp. 1–5. [Google Scholar]
- Alqahtani, H.; Kavakli, M.; Sheikh, N.U. Analysis of the Technology Acceptance Theoretical Model in Examining Users Behavioural Intention to Use an Augmented Reality App (IMAP-Campus). Int. J. Eng. Manag. Res. (IJEMR) 2018, 8, 37–49. [Google Scholar] [CrossRef]
- Lave, J.; Wenger, E. Situated Learning: Legitimate Peripheral Participation; Cambridge University Press: Cambridge, UK, 1991. [Google Scholar]
- Markouzis, D.; Fessakis, G. Interactive Storytelling and Mobile Augmented Reality Applications for Learning and Entertainment A rapid prototyping perspective. In Proceedings of the 9th International Conference on Interactive Mobile Communication, Technologies and Learning (IMCL2015), Thessaloniki, Greece, 19–20 November 2015. [Google Scholar]
- Bower, M.; Howe, C.; McCredie, N.; Robinson, A.; Grover, D. Augmented Reality in education–cases, places and potentials. Educ. Media Int. 2014, 51, 1–15. [Google Scholar] [CrossRef]
- Thompson, M.F.; Irvine, C.E. CyberCIEGE scenario design and implementation. In Proceedings of the 2014 {USENIX} Summit on Gaming, Games, and Gamification in Security Education (3GSE 14), San Diego, CA, USA, 18 August 2014. [Google Scholar]
- Liang, H.; Xue, Y. Avoidance of information technology threats: A theoretical perspective. MIS Q. 2009, 71–90. Available online: https://www.jstor.org/stable/20650279 (accessed on 20 February 2020). [CrossRef]
- Liang, H.; Xue, Y. Understanding security behaviors in personal computer usage: A threat avoidance perspective. J. Assoc. Inf. Syst. 2010, 11, 394–413. [Google Scholar] [CrossRef]
- Misra, G.; Arachchilage, N.A.G.; Berkovsky, S. Phish Phinder: A Game Design Approach to Enhance User Confidence in Mitigating Phishing Attacks. arXiv 2017, arXiv:1710.06064. [Google Scholar]
- Stevens, T. Global Cybersecurity: New Directions in Theory and Methods. Politics Gov. 2018, 6, 1–4. [Google Scholar] [CrossRef]
- Kassicieh, S.; Lipinski, V.; Seazzu, A.F. Human centric cyber security: what are the new trends in data protection? In Proceedings of the IEEE 2015 Portland International Conference on Management of Engineering and Technology (PICMET), Portland, OR, USA, 2–6 August 2015; pp. 1321–1338. [Google Scholar]
- Sheng, S.; Magnien, B.; Kumaraguru, P.; Acquisti, A.; Cranor, L.F.; Hong, J.; Nunge, E. Anti-phishing phil: the design and evaluation of a game that teaches people not to fall for phish. In Proceedings of the 3rd Symposium on Usable Privacy and Security; ACM: New York, NY, USA, 2007; pp. 88–99. [Google Scholar]
- Arachchilage, N.A.G.; Love, S.; Beznosov, K. Phishing threat avoidance behaviour: An empirical investigation. Comput. Hum. Behav. 2016, 60, 185–197. [Google Scholar] [CrossRef]
- Kirlappos, I.; Sasse, M.A. Security education against phishing: A modest proposal for a major rethink. IEEE Secur. Priv. 2011, 10, 24–32. [Google Scholar] [CrossRef]
- Yasin, A.; Liu, L.; Li, T.; Wang, J.; Zowghi, D. Design and preliminary evaluation of a cyber Security Requirements Education Game (SREG). Inf. Softw. Technol. 2018, 95, 179–200. [Google Scholar] [CrossRef]
- Jin, G.; Tu, M.; Kim, T.H.; Heffron, J.; White, J. Game based cybersecurity training for high school students. In Proceedings of the 49th ACM Technical Symposium on Computer Science Education; ACM: New York, NY, USA, 2018; pp. 68–73. [Google Scholar]
- Gondree, M.; Peterson, Z.N. Valuing security by getting [d0x3d!]: Experiences with a network security board game. In Proceedings of the Presented at Part of the 6th Workshop on Cyber Security Experimentation and Test, Washington, DC, USA, 12 August 2013. [Google Scholar]
- Denning, T.; Lerner, A.; Shostack, A.; Kohno, T. Control-Alt-Hack: The design and evaluation of a card game for computer security awareness and education. In Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security; ACM: New York, NY, USA, 2013; pp. 915–928. [Google Scholar]
- Williams, L.; Meneely, A.; Shipley, G. Protection poker: The new software security “game”. IEEE Secur. Priv. 2010, 8, 14–20. [Google Scholar] [CrossRef]
- Mirkovic, J.; Peterson, P.A. Class capture-the-flag exercises. In Proceedings of the 2014 {USENIX} Summit on Gaming, Games, and Gamification in Security Education (3GSE 14), San Diego, CA, USA, 18 August 2014. [Google Scholar]
- Azuma, R.T. A survey of augmented reality. Presence Teleoperators Virtual Environ. 1997, 6, 355–385. [Google Scholar] [CrossRef]
- Hendrix, M.; Al-Sherbaz, A.; Bloom, V. Game based cyber security training: Are serious games suitable for cyber security training? Int. J. Serious Games 2016, 3. [Google Scholar] [CrossRef]
- Kurkovsky, S. Engaging students through mobile game development. In ACM SIGCSE Bulletin; ACM: New York, NY, USA, 2009; Volume 41, pp. 44–48. [Google Scholar]
- Wong, J.K.; Sheth, J.N. Explaining intention-behavior discrepancy—A paradigm. ACR N. Am. Adv. 1985. Available online: www.acrwebsite.org/volumes/6419/volumes/v12/NA-12 (accessed on 20 February 2020).
- de la Hera Conde-Pumpido, T. A Conceptual Model for the Study of Persuasive Games. 2013. Available online: https://repub.eur.nl/pub/110458/ (accessed on 20 February 2020).
- Rittle-Johnson, B.; Koedinger, K.R. Comparing Instructional Strategies for Integrating Conceptual and Procedural Knowledge. In Proceedings of the 24th annual meeting of the North American Chapters of the International Group for the Psychology of Mathematics Education, Athens, GA, USA, 26–29 October 2002. [Google Scholar]
- Gee, J.P. Deep learning properties of good digital games: How far can they go? In Serious Games; Routledge: Abingdon, UK, 2009; pp. 89–104. [Google Scholar]
- Rogers, R.W. A protection motivation theory of fear appeals and attitude change1. J. Psychol. 1975, 91, 93–114. [Google Scholar] [CrossRef] [PubMed]
- Scholefield, S.; Shepherd, L.A. Gamification Techniques for Raising Cyber Security Awareness. arXiv 2019, arXiv:1903.08454. [Google Scholar]
- Findley, M.R. The relationship between student learning styles and motivation during educational video game play. Int. J. Online Pedagog. Course Des. (IJOPCD) 2011, 1, 63–73. [Google Scholar] [CrossRef][Green Version]
- Giannakas, F.; Kambourakis, G.; Gritzalis, S. CyberAware: A mobile game-based app for cybersecurity education and awareness. In Proceedings of the IEEE 2015 International Conference on Interactive Mobile Communication Technologies and Learning (IMCL), Thessaloniki, Greece, 19–20 November 2015; pp. 54–58. [Google Scholar]
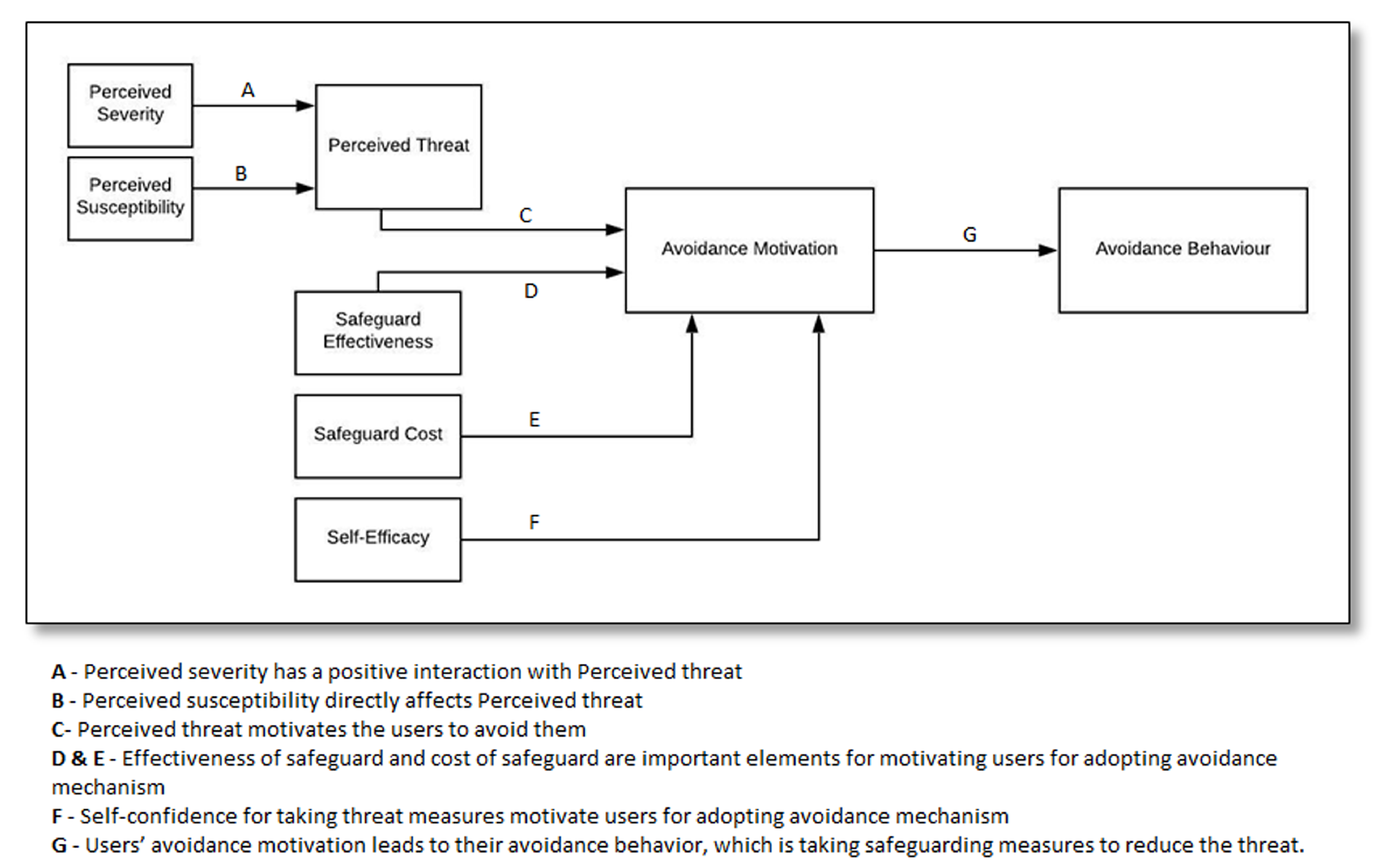


| Elements of the Game Design Framework | Game Design Sketch |
|---|---|
| Perceived Susceptibility: An individual’s subjective probability that a cyber attack will negatively affect him or her [24,25]. | Each task displayed in the game is associated with a potential cybersecurity threat which appears as a case study in the game. The game player’s job is to perform the tasks correctly; each task performance is followed by immediate positive or negative feedback. This element of the game design addresses the user’s awareness of susceptibility to the cybersecurity threat. |
| Perceived Severity: The extent to which an individual perceives that negative consequences caused by a cyberattack will be severe [24]. | If the game player makes the incorrect decision, each wrong attempt loses one point out of a total of 20 points needed to complete the game. This develops awareness of the severity of the cybersecurity threat. |
| Perceived Threat: The extent to which an individual perceives the cybersecurity threat as dangerous or harmful [24,25]. | The main goal of the game player is to avoid potential cybersecurity threats in real life, therefore he or she should be aware of the various ways in which hackers can operate. This represents the development of threat perception in the game design, and negative feedback shows the damaging consequences of hacking. |
| Perceived Safeguard Effectiveness: The individual’s assessment of the potential effectiveness of a safeguarding measure against a cybersecurity threat [24,30]. | If a player finds it difficult to identify if something is suspicious or not, the player can complete the task, learn the expected consequences and replay later. The feedback provides tips on how to identify cyberattacks. This element addresses safeguard effectiveness in the game design. |
| Perceived Safeguard Cost: This refers to the physical and cognitive costs, such as time, money, inconvenience and mental effort, required to use the safeguard measure [24,41]. | When the game player scores less than 65%, he or she is asked to replay the game. This feature of the game design addresses the costs involved in the safeguard. |
| Self-Efficacy: Individuals’ confidence in adopting the safeguard measure [24,25,26]. | The game is designed to educate users in safe online behaviour. The player is with a series of tasks, each of which is associated with a different form of cybersecurity attack. As the player moves from task to task through the game, he or she gains conceptual knowledge of how to identify cyberthreats, thus helping to develop self-efficacy. |
| Item | Questions |
|---|---|
| Q1 | CybAR game is an effective method of learning cybersecurity related concepts. |
| Q2 | CybAR game helps me to learn more about cybersecurity attacks from mistakes. |
| Q3 | CybAR game is a fun method of learning cybersecurity. |
| Q4 | CybAR game has motivated me to learn more about cybersecurity. |
| Q5 | CybAR game is easy to understand and play. |
| Q6 | CybAR game mimics a real-life cybersecurity scenario in a presentable way. |
| Q7 | I am motivated to play CybAR game in future. |
| No | Questions | Mean |
|---|---|---|
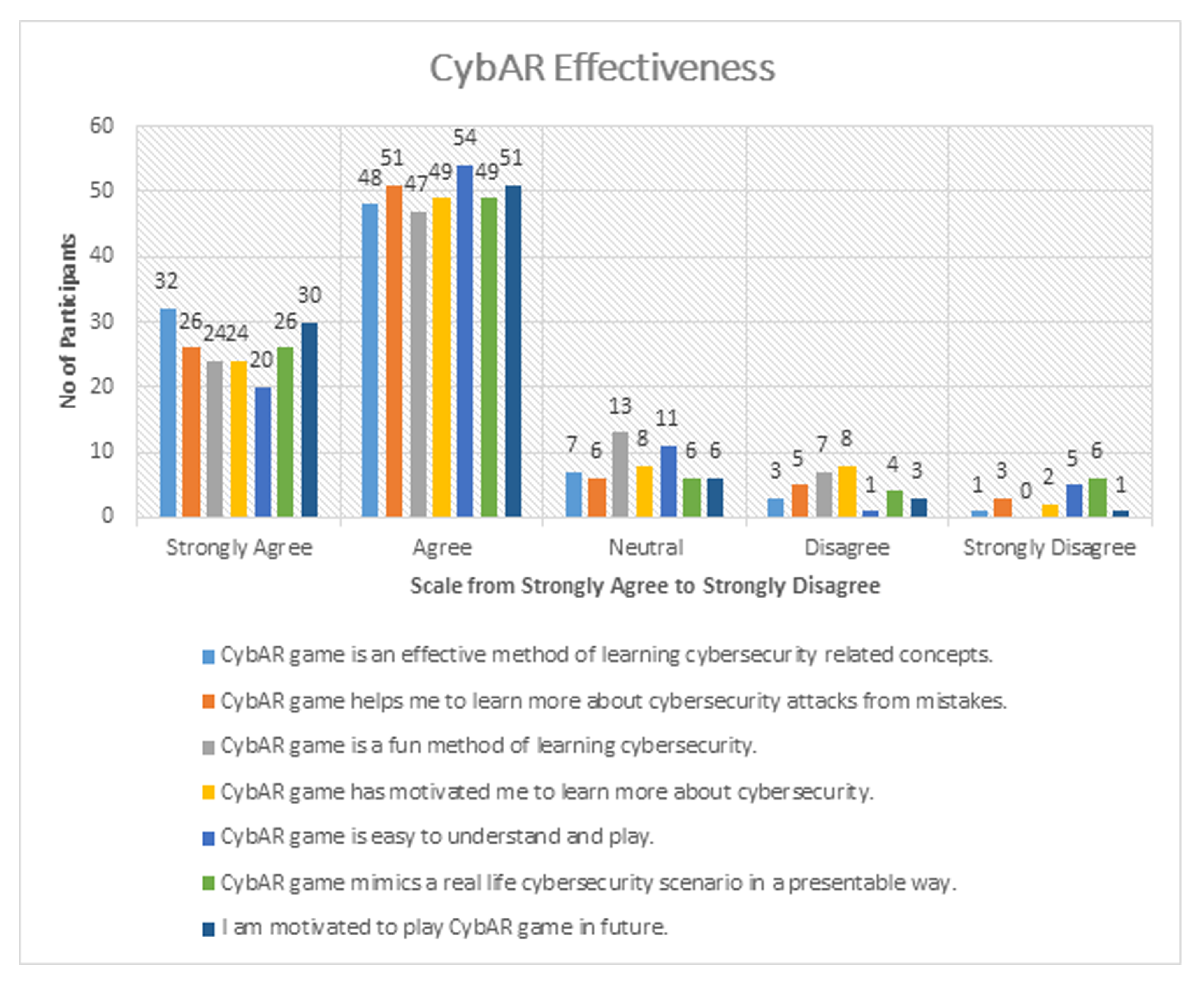
| 1 | CybAR game is an effective method of learning cybersecurity related oncepts. | 4.18 |
| 2 | CybAR game helps me to learn more about cybersecurity attacks from mistakes. | 4.01 |
| 3 | CybAR game is a fun method of learning cybersecurity. | 3.97 |
| 4 | CybAR game has motivated me to learn more about cybersecurity. | 3.93 |
| 5 | CybAR game is easy to understand and play. | 3.91 |
| 6 | CybAR game mimics a real life cybersecurity scenario in a presentable way. | 3.93 |
| 7 | I am motivated to play CybAR game in future. | 4.16 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alqahtani, H.; Kavakli-Thorne, M. Design and Evaluation of an Augmented Reality Game for Cybersecurity Awareness (CybAR). Information 2020, 11, 121. https://doi.org/10.3390/info11020121
Alqahtani H, Kavakli-Thorne M. Design and Evaluation of an Augmented Reality Game for Cybersecurity Awareness (CybAR). Information. 2020; 11(2):121. https://doi.org/10.3390/info11020121
Chicago/Turabian StyleAlqahtani, Hamed, and Manolya Kavakli-Thorne. 2020. "Design and Evaluation of an Augmented Reality Game for Cybersecurity Awareness (CybAR)" Information 11, no. 2: 121. https://doi.org/10.3390/info11020121
APA StyleAlqahtani, H., & Kavakli-Thorne, M. (2020). Design and Evaluation of an Augmented Reality Game for Cybersecurity Awareness (CybAR). Information, 11(2), 121. https://doi.org/10.3390/info11020121





