A Privacy-Preserving Protocol for Utility-Based Routing in DTNs
Abstract
:1. Introduction
- We propose a privacy-preserving protocol for utility-based routing PPUR in DTNs. PPUR can protect nodes’ privacy information and collect the encounter information to calculate the real utility value at the same time.
- We achieve the confidentiality and integrity of messages through hashing and digital signature, and then analyze the security.
- Extensive simulations are conducted to demonstrate the efficiency of the proposed routing protocol.
2. Related Work
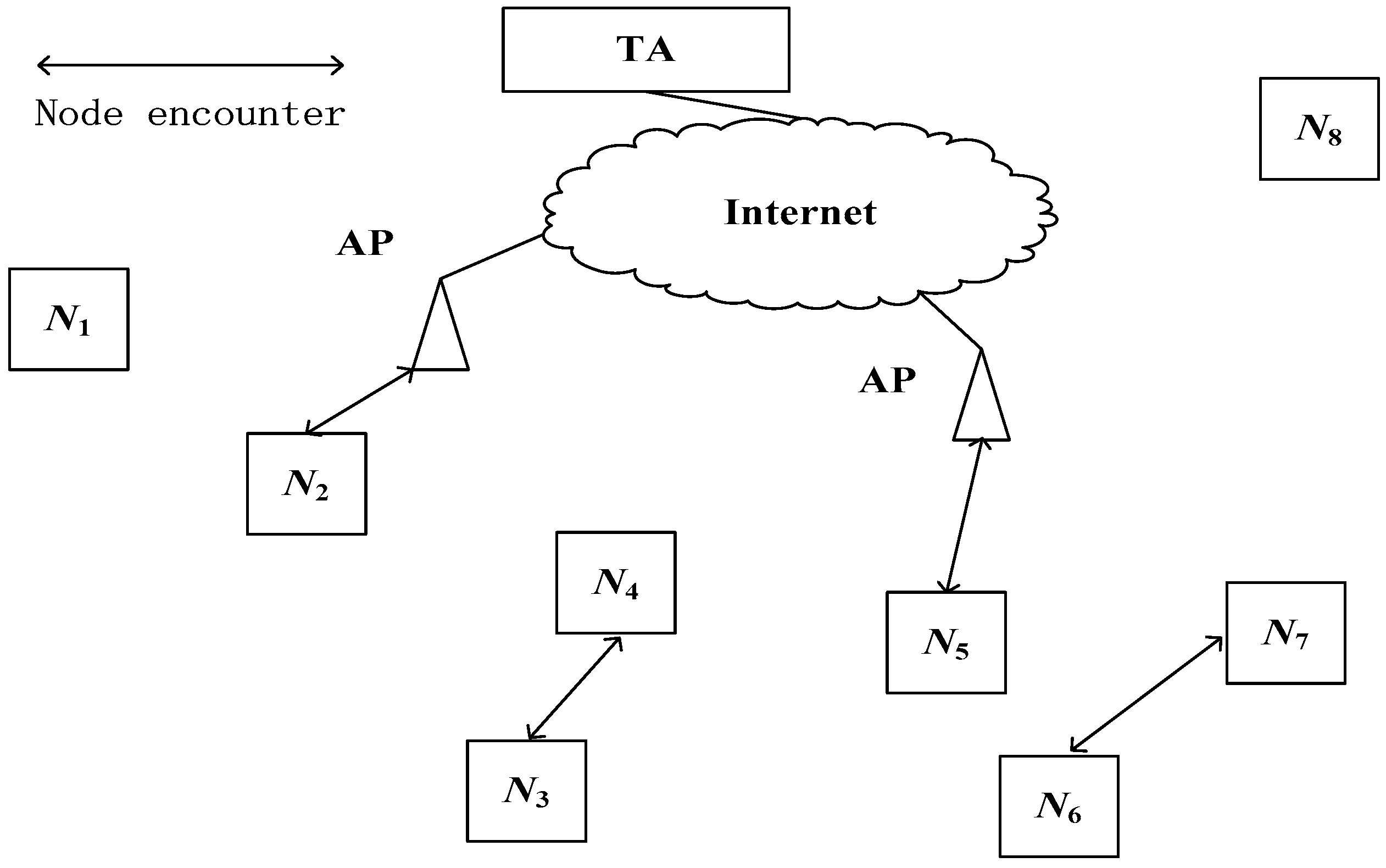
3. System Model
4. System Design of PPUR
4.1. System Setup
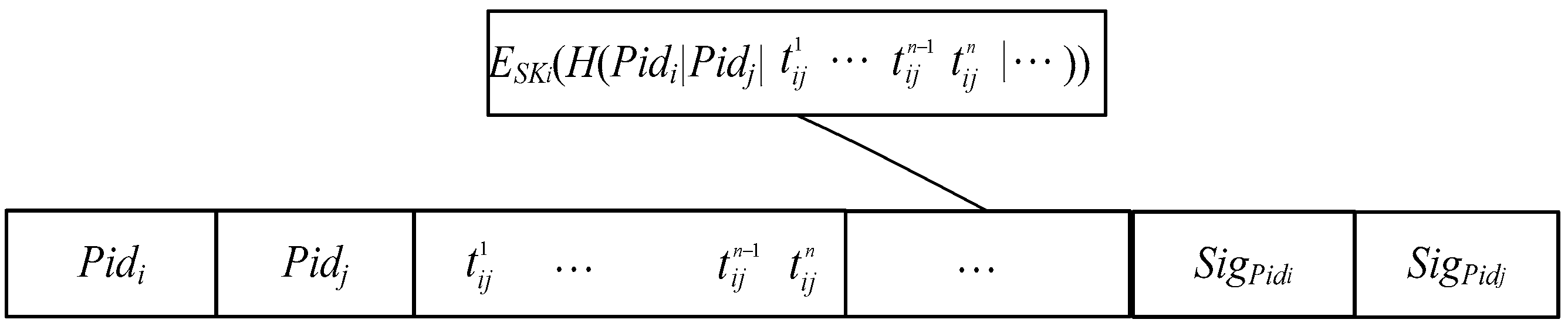
4.2. Generation of Encounter Record Information for Anonymous Nodes
4.3. Collection of Encounter Record Information and Calculation of Real Utility Value
4.4. Anonymous Message Forwarding of Encountering Nodes
- For a message m, if Ni is not the destination node, it gets the utility value calculated by the TA, and then goes to step 3, or else goes to step 2.
- Set the utility value to the max value of 1.
- Ni receives message m if it has a higher utility value.
4.5. Security Analysis
4.5.1. Passive Attack
4.5.2. Active Attack
5. Performance Evaluation
5.1. Simulation Setup
5.2. Performance Comparison
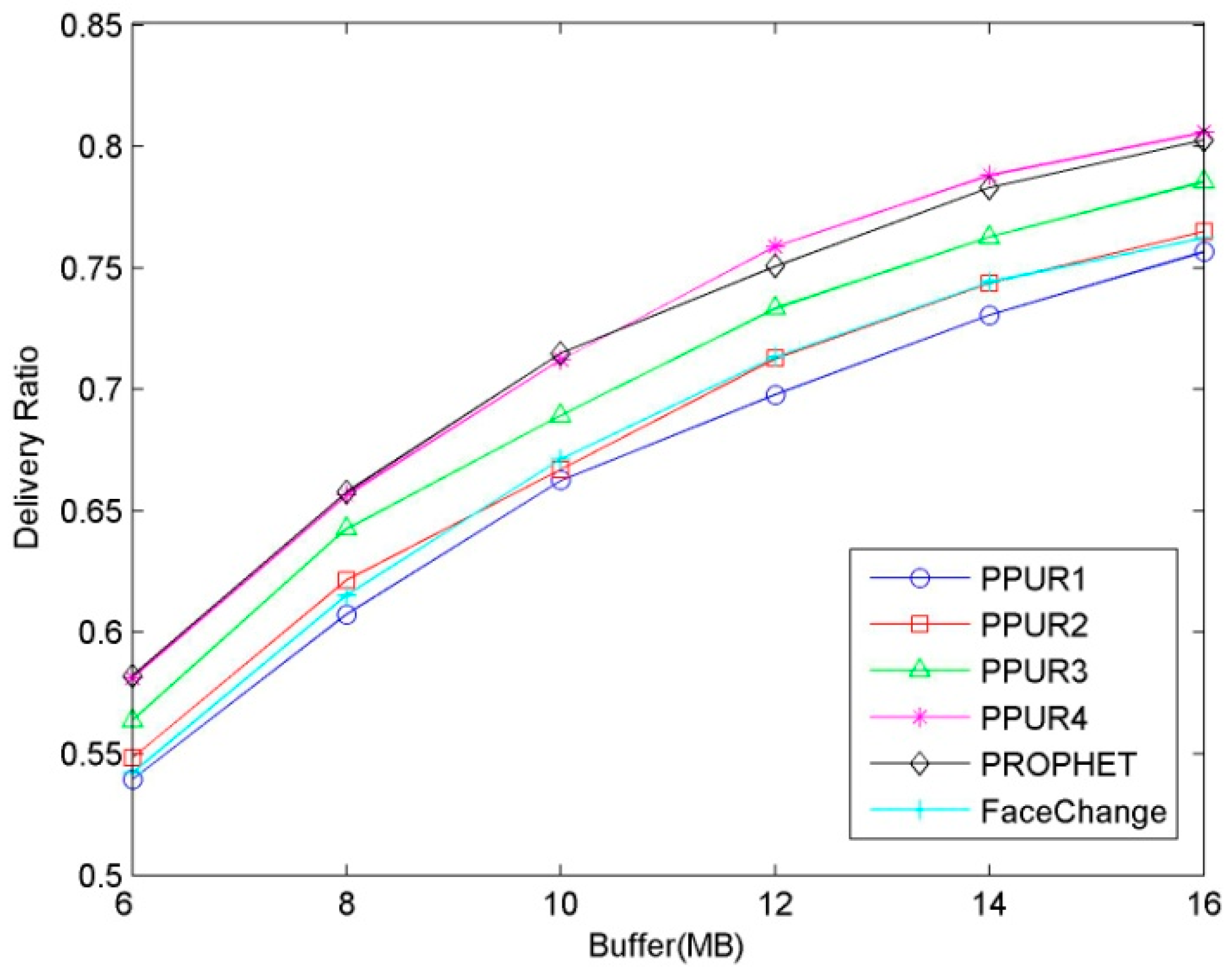
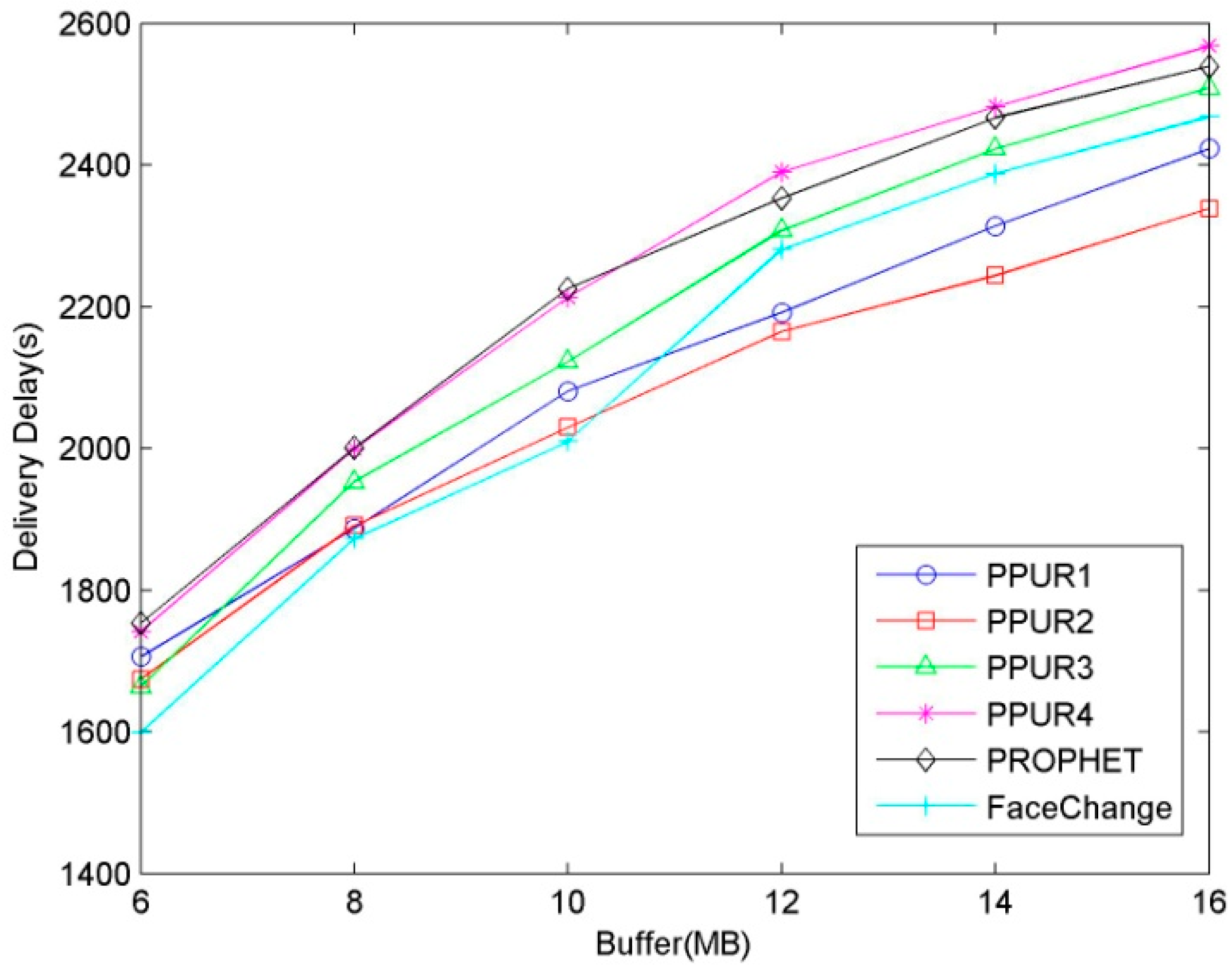
5.2.1. Influence of Buffer Size
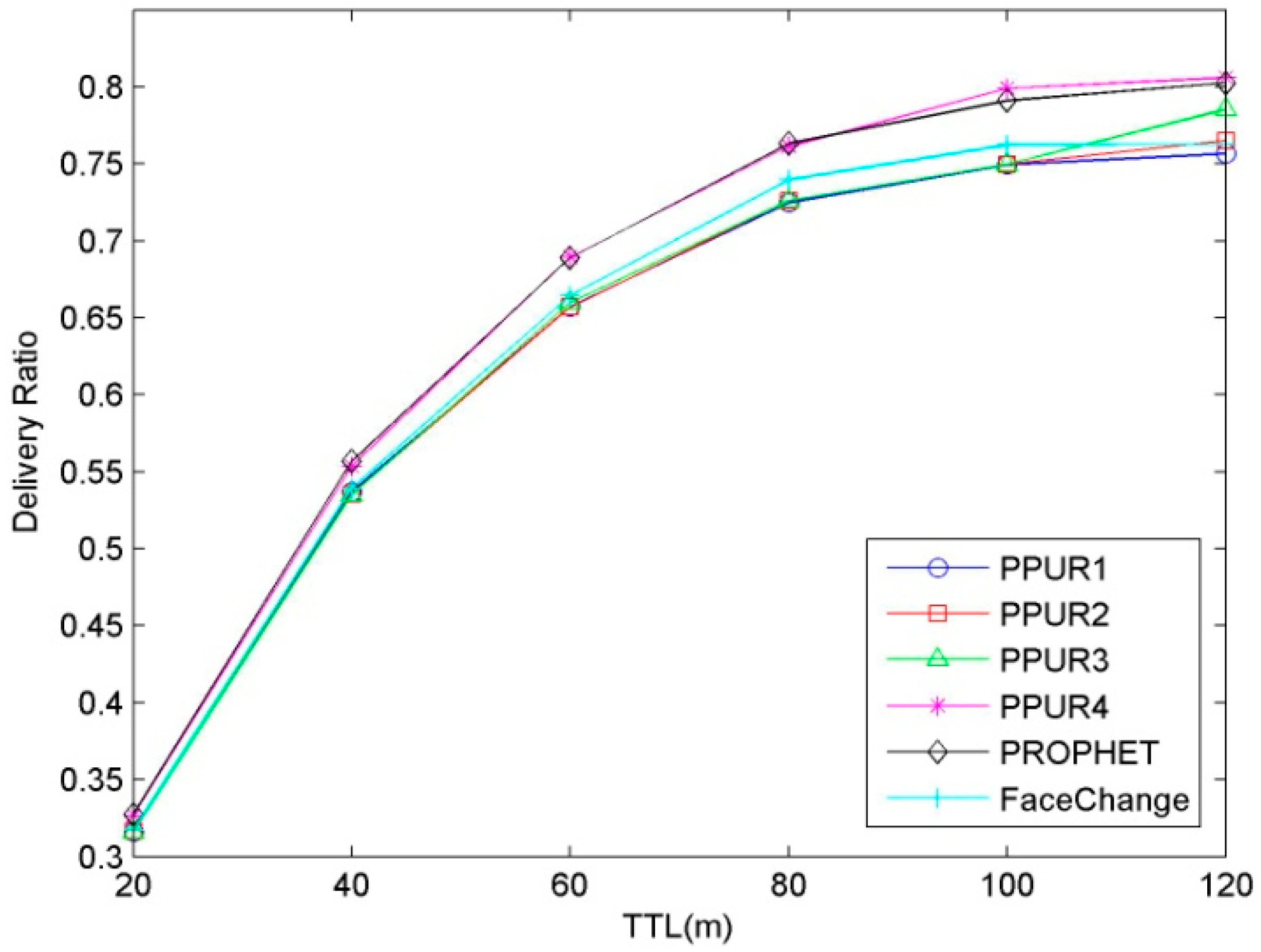
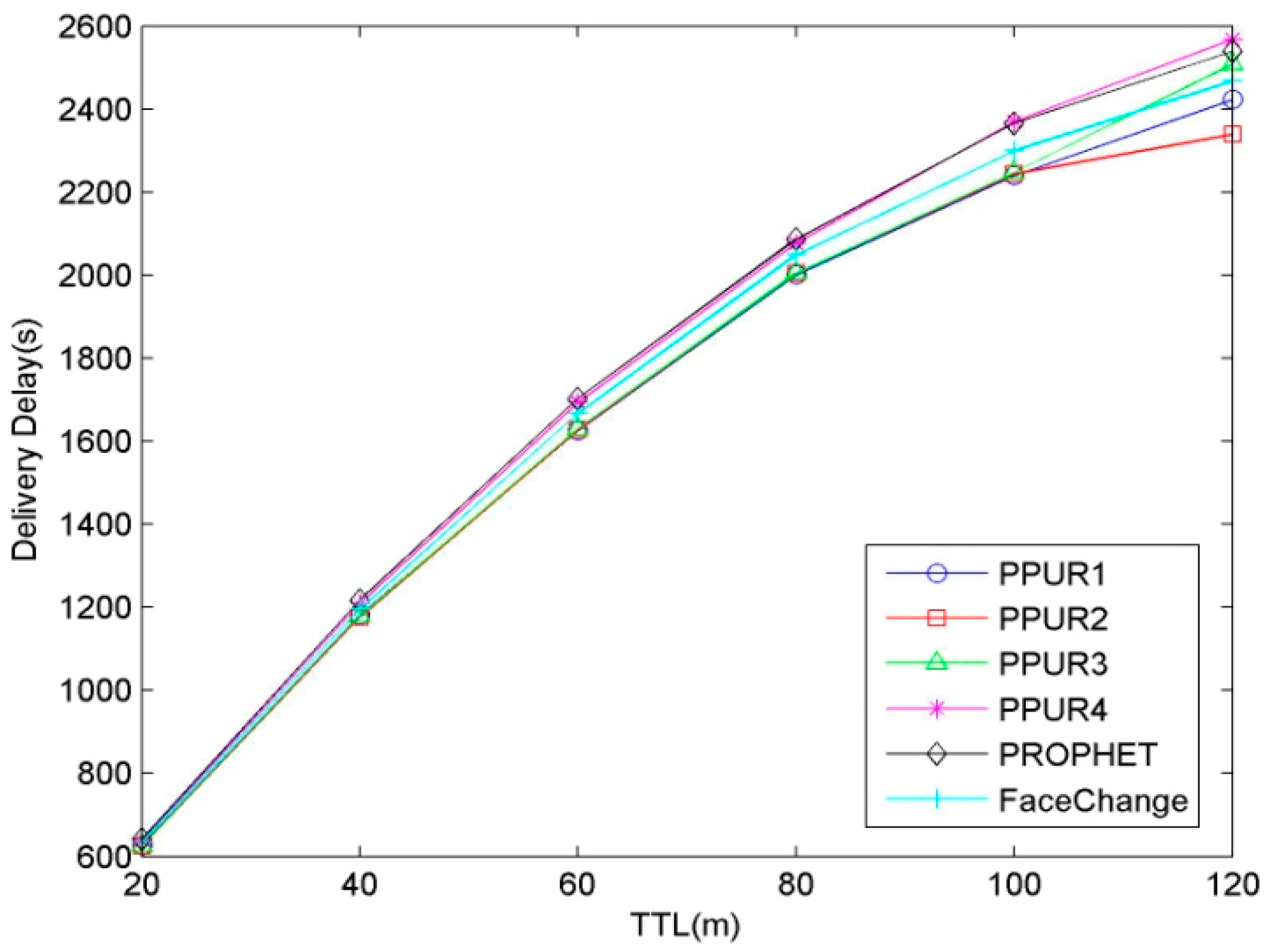
5.2.2. Influence of TTL
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Fall, K. A delay-tolerant network architecture for challenged Internets. In Proceedings of the 2003 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications (SIGCOMM’03), Karlsruhe, Germany, 25–29 August 2003; pp. 27–34. [Google Scholar]
- Lindgren, A.; Doria, A.; Schelen, O. Probabilistic routing in intermittently connected networks. ACM SIGMOBILE Mob. Comput. Commun. Rev. 2003, 7, 19–20. [Google Scholar] [CrossRef]
- Burgess, J.; Gallagher, B.; Jensen, D. MaxProp: Routing for vehicle-based disruption-tolerant networking. In Proceedings of the INFOCOM 2006, Barcelona, Spain, 23–29 April 2006; pp. 1–11. [Google Scholar]
- Balasubramanian, A.; Levine, B.N.; Venkataramani, A. DTN routing as a resource allocation problem. In Proceedings of the SIGCOMM 2007, Kyoto, Japan, 27–31 August 2007; pp. 373–384. [Google Scholar]
- Hui, P.; Crowcroft, J.; Yoneki, E. Bubble Rap: Social-based forwarding in delay-tolerant networks. IEEE Trans. Mob. Comput. 2011, 10, 1576–1589. [Google Scholar] [CrossRef]
- Elizabeth, M.; Haahr, M. Social network analysis for information flow in disconnected delay-tolerant MANETs. IEEE Trans. Mob. Comput. 2009, 8, 606–621. [Google Scholar]
- Wu, J.X.; Huang, L.S. Homing spread: community home based multi-copy routing in mobile social networks. In Proceedings of the INFOCOM 2013, Turin, Italy, 14–19 April 2013; pp. 2319–2327. [Google Scholar]
- Kate, A.; Zaverucha, G.; Hengartner, U. Anonymity and security in delay tolerant networks. In Proceedings of the IEEE SecureComm, Nice, France, 17–21 September 2007; pp. 504–513. [Google Scholar]
- Lu, R.X.; Lin, X.D.; Shen, X.M. SPRING: A social-based privacy-preserving packet forwarding protocol for vehicular delay tolerant networks. In Proceedings of the IEEE INFOCOM2010, San Diego, CA, USA, 14–19 March 2010; pp. 1–9. [Google Scholar]
- Chen, K.; Shen, H.Y. FaceChange: Attaining neighbor node anonymity in mobile opportunistic social networks with fine-grained control. IEEE/ACM Trans. Netw. 2017, 25, 1176–1189. [Google Scholar] [CrossRef]
- Zakharya, S.; Benslimane, A. On location-privacy in opportunistic mobile networks, a survey. J. Netw. Comput. Appl. 2018, 103, 157–170. [Google Scholar] [CrossRef]
- Lu, X.; Hui, P.; Towsley, D. Anti-localization anonymous routing for delay tolerant network. Comput. Netw. 2010, 54, 1899–1910. [Google Scholar] [CrossRef]
- Benslimane, A.; Radenkovic, M.; Zakhary, S. Efficient location privacy-aware forwarding in opportunistic mobile networks. IEEE Trans. Veh. Technol. 2014, 63, 893–906. [Google Scholar]
- Shi, C.; Luo, X.; Traynor, P. Arden: Anonymous networking in delay tolerant networks. Ad Hoc Networks 2012, 10, 918–930. [Google Scholar] [CrossRef]
- Guo, L.K.; Zhang, C.; Yue, H. PSaD: A privacy-preserving social assisted mobile content dissemination scheme in DTNs. IEEE Trans. Mob. Comput. 2014, 13, 2903–2918. [Google Scholar] [CrossRef]
- Cai, Z.P.; He, Z.B.; Guan, X. Collective data-sanitization for preventing sensitive information inference attacks in social networks. IEEE Trans. Depend. Secure Comput. 2018, 15, 577–590. [Google Scholar] [CrossRef]
- Zhang, L.; Song, J.; Pan, J.P. A privacy-preserving and secure framework for opportunistic routing in DTNs. IEEE Trans. Veh. Technol. 2016, 65, 7684–7697. [Google Scholar] [CrossRef]
- Bakiras, S.; Troja, E.; Xu, X.H. An anonymous messaging system for delay tolerant networks. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar]
- Miao, J.W.; Hasan, O.; Mokhtar, S.B. 4PR: Privacy preserving routing in mobile delay tolerant networks. Comput. Netw. 2016, 111, 17–28. [Google Scholar] [CrossRef]
- Chen, K.; Shen, H.Y. Distributed privacy-protecting routing in DTN: Concealing the information indispensable in routing. In Proceedings of the 14th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), San Diego, CA, USA, 12–14 June 2017; pp. 1–9. [Google Scholar]
- Magaia, N.; Borrego, C.; Pereira, P. ePRIVO: An enhanced privacy-preserving opportunistic routing protocol for vehicular delay-tolerant networks. IEEE Trans. Veh. Technol. 2018, 67, 11154–11168. [Google Scholar] [CrossRef]
- Yao, A.C. Protocols for secure computations. In Proceedings of the FOCS, Washington, DC, USA, 3–5 November 1982; pp. 160–164. [Google Scholar]
- Keranen, A.; Ott, J.; Karkkainen, T. The ONE simulator for DTN protocol evaluation. In Proceedings of the 2nd International Conference on Simulation Tools and Techniques, Rome, Italy, 2–9 March 2009; pp. 1–10. [Google Scholar]


© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jiang, Q.; Deng, K.; Zhang, L.; Liu, C. A Privacy-Preserving Protocol for Utility-Based Routing in DTNs. Information 2019, 10, 128. https://doi.org/10.3390/info10040128
Jiang Q, Deng K, Zhang L, Liu C. A Privacy-Preserving Protocol for Utility-Based Routing in DTNs. Information. 2019; 10(4):128. https://doi.org/10.3390/info10040128
Chicago/Turabian StyleJiang, Qingfeng, Kun Deng, Lei Zhang, and Chun Liu. 2019. "A Privacy-Preserving Protocol for Utility-Based Routing in DTNs" Information 10, no. 4: 128. https://doi.org/10.3390/info10040128
APA StyleJiang, Q., Deng, K., Zhang, L., & Liu, C. (2019). A Privacy-Preserving Protocol for Utility-Based Routing in DTNs. Information, 10(4), 128. https://doi.org/10.3390/info10040128



