Routing Algorithm Based on Trajectory Prediction in Opportunistic Networks
Abstract
:1. Introduction
- Unevenness of opportunities to encounter between nodes. In the opportunistic network, the information interaction occurs only when two nodes enter each other’s communication range. The chance of encountering between the two nodes is unpredictable, which leads to the imbalance of the chances of encountering the nodes.
- Topology structure information is difficult to grasp. The topology of the opportunistic network changes dynamically, and the mobile information of nodes in the network is difficult to obtain accurately and timely.
- Resource constraints. Most of the opportunistic network nodes are portable devices, so the nodes themselves have limitations such as energy, contact time, and storage space.
- Unpredictability of node movement trajectory. The mobile behavior of a node is affected by many external factors, and it is impossible to obtain the precise location information of the node in time.
- (1)
- Constructing the node mobility model based on the historical mobility characteristics of the node. By changing the value of the node’s mobile coordination factor, the possible running speed of the node at the next moment is obtained.
- (2)
- Using the Gaussian process to model the speed probability of different mobile coordination factors, and using the maximum likelihood estimation (EM) algorithm to obtain the model parameters, so that the probability of speed based on historical mobility characteristics is best. On this basis, the node movement distance and node location information are calculated.
- (3)
- Calculating the metric value of the candidate node based on the predicted location information. During the information transmission, the node does not need to store too much routing information, and the network resource consumption is significantly reduced. The use of the location information can effectively avoid loop generation during data delivery and also have strong adaptability to the dynamic network topology change.
- (4)
- The simulation platform ONE simulates a large amount of data and evaluates the performance of the RATP algorithm, with improved transmission success rate, reduced data delay and routing overhead.
2. Related Work
3. RATP
3.1. Trajectory Prediction
3.1.1. Node Mobility Model
3.1.2. Probability of Node Velocity
3.1.3. Node Location
3.1.4. Node Moving Distance
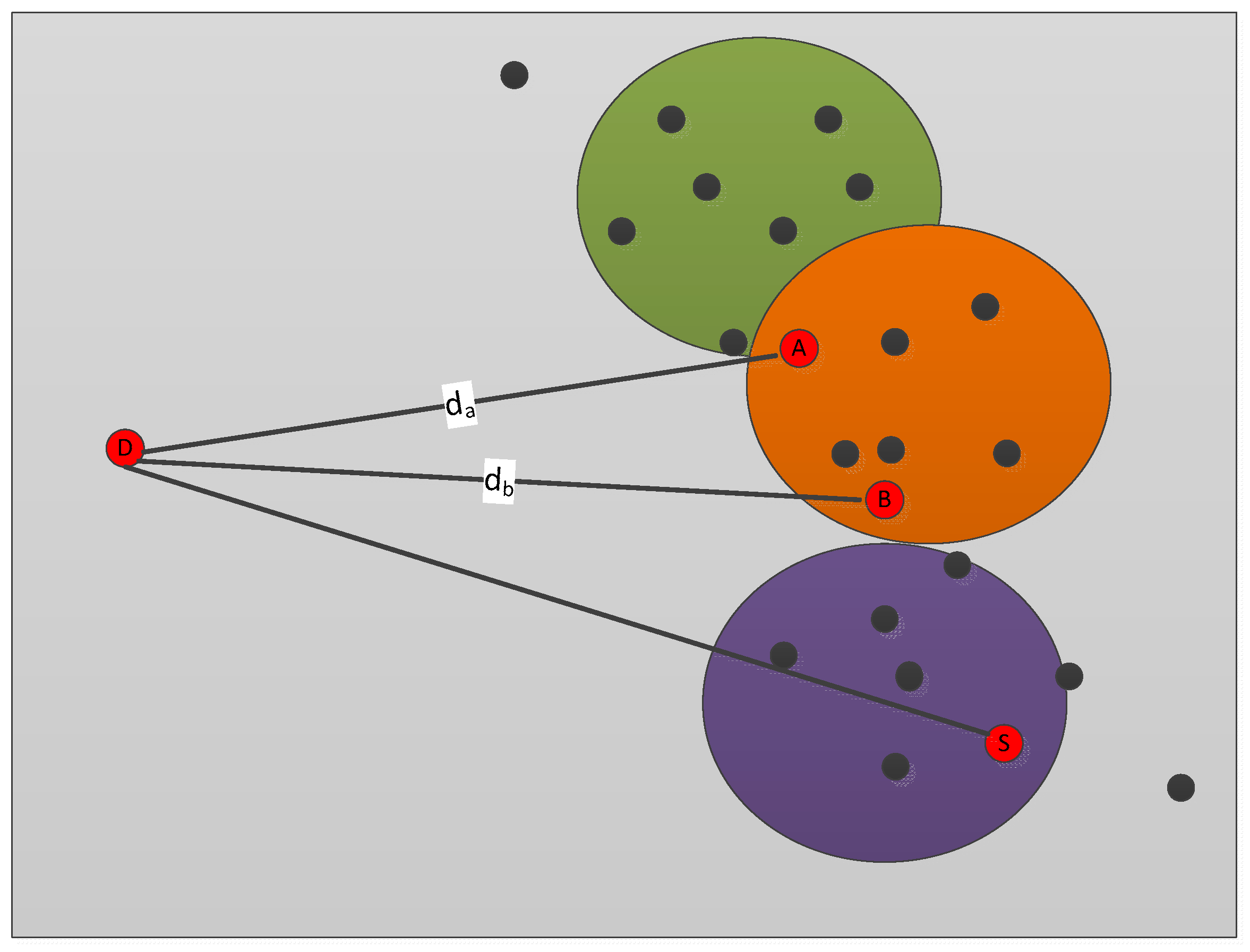
3.2. Data Forwarding Mode
3.3. Algorithm Complexity Analysis
| Algorithm 1. Routing Algorithm based on Trajectory Prediction—RATP |
| Input: Historical trajectory information of nodes Output: optimal path 1: : the average speed of vehicle since long time movement; 2: : vehicles’ random and independent processes when the vehicles move at infinity; 3: : the mobile coordination factor; 4: the node mobility model: 6: the trajectory probability model: 8: get the speed of the next moment. 9: the vehicle position: 10: if the vehicle driving direction has changed do Equation (15); 11: else: Equation (16); 12: end if 13: the distance of the vehicle moving in time: Equation (18); 14: calculate the metric value of the candidate node based on the predicted location information: 16: end; |
4. Performance Evaluation
4.1. Performance Measurement Parameters
4.2. Results and Discussion
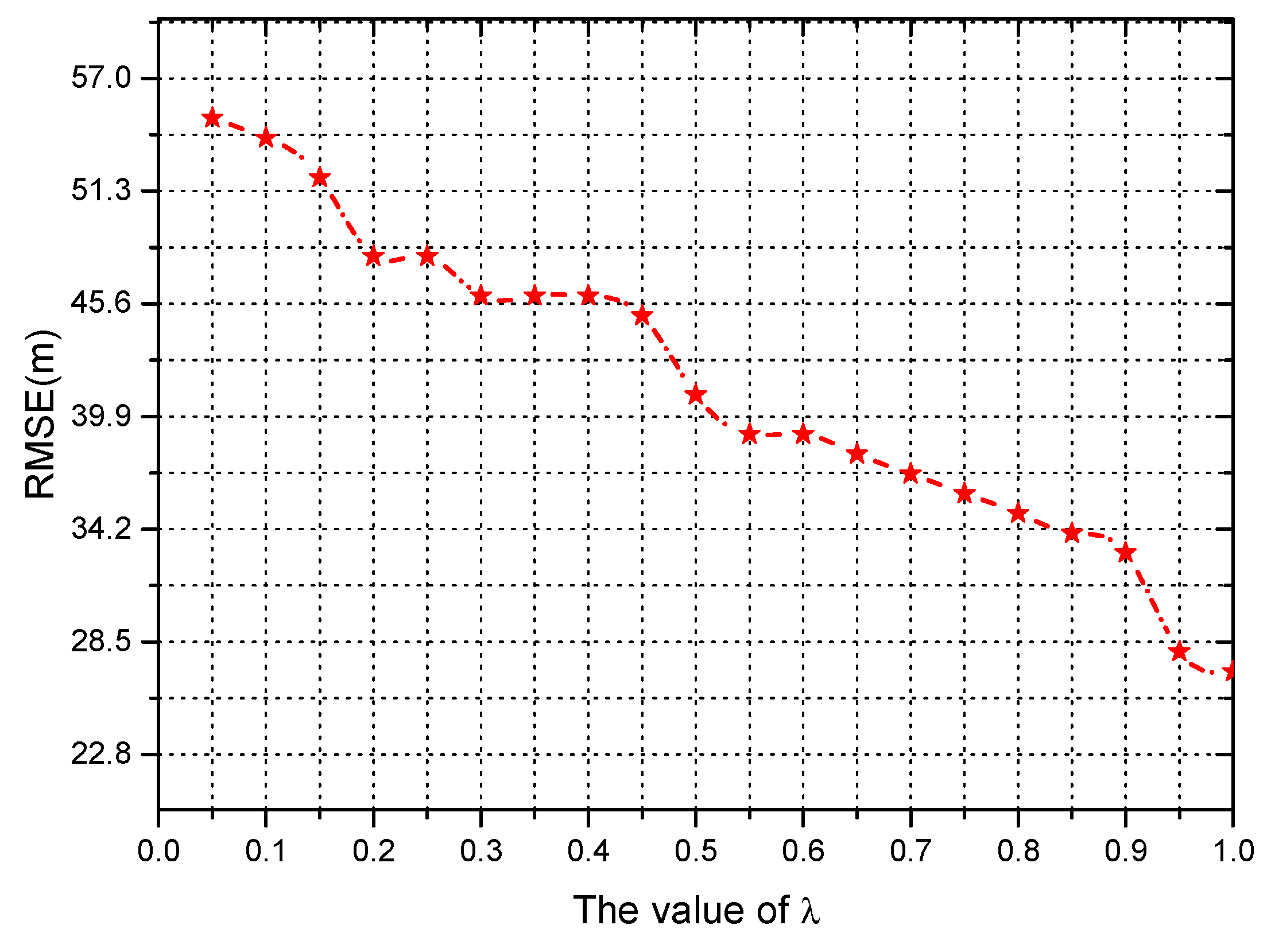
4.2.1. Prediction Error Analysis
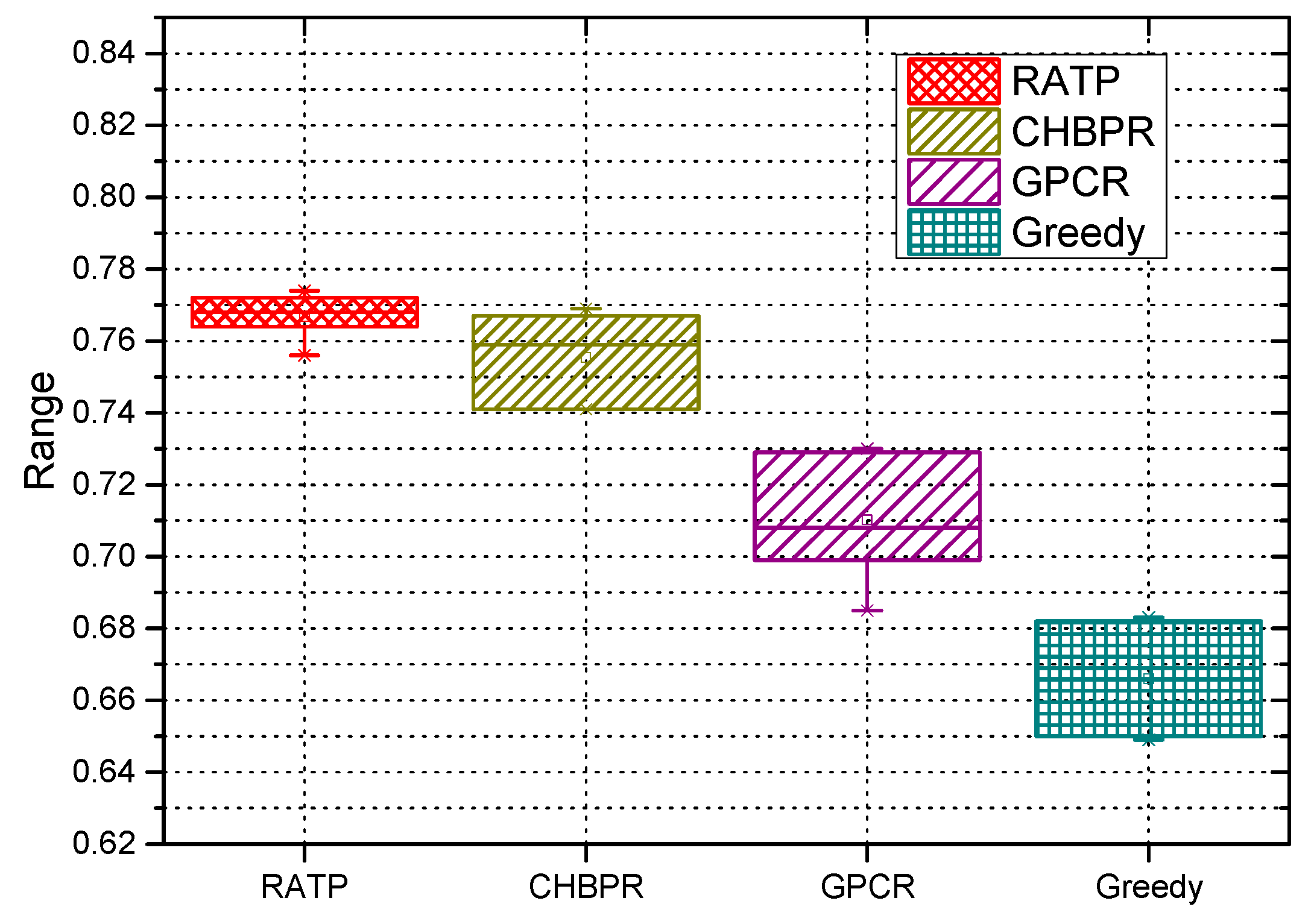
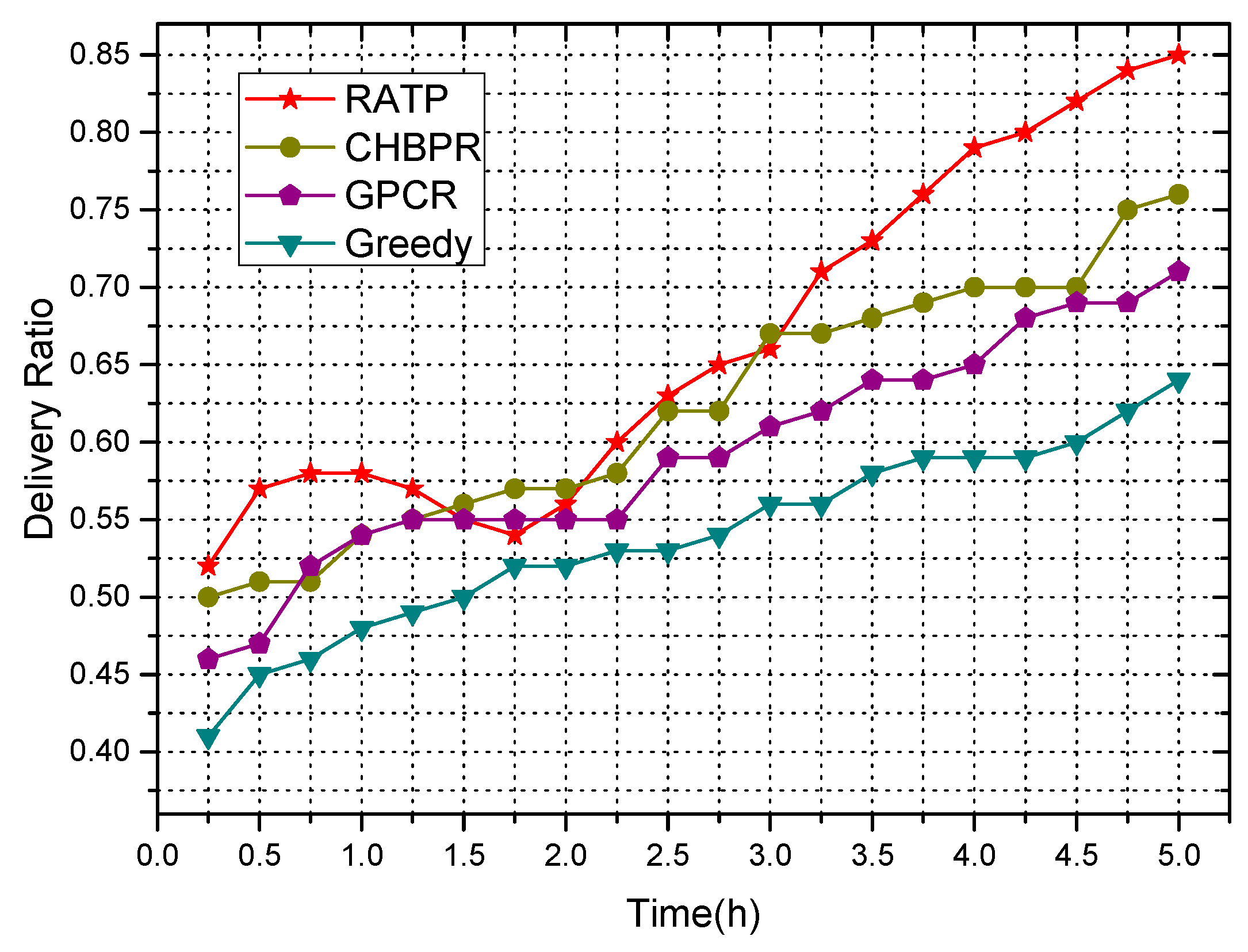
4.2.2. Delivery Ratio
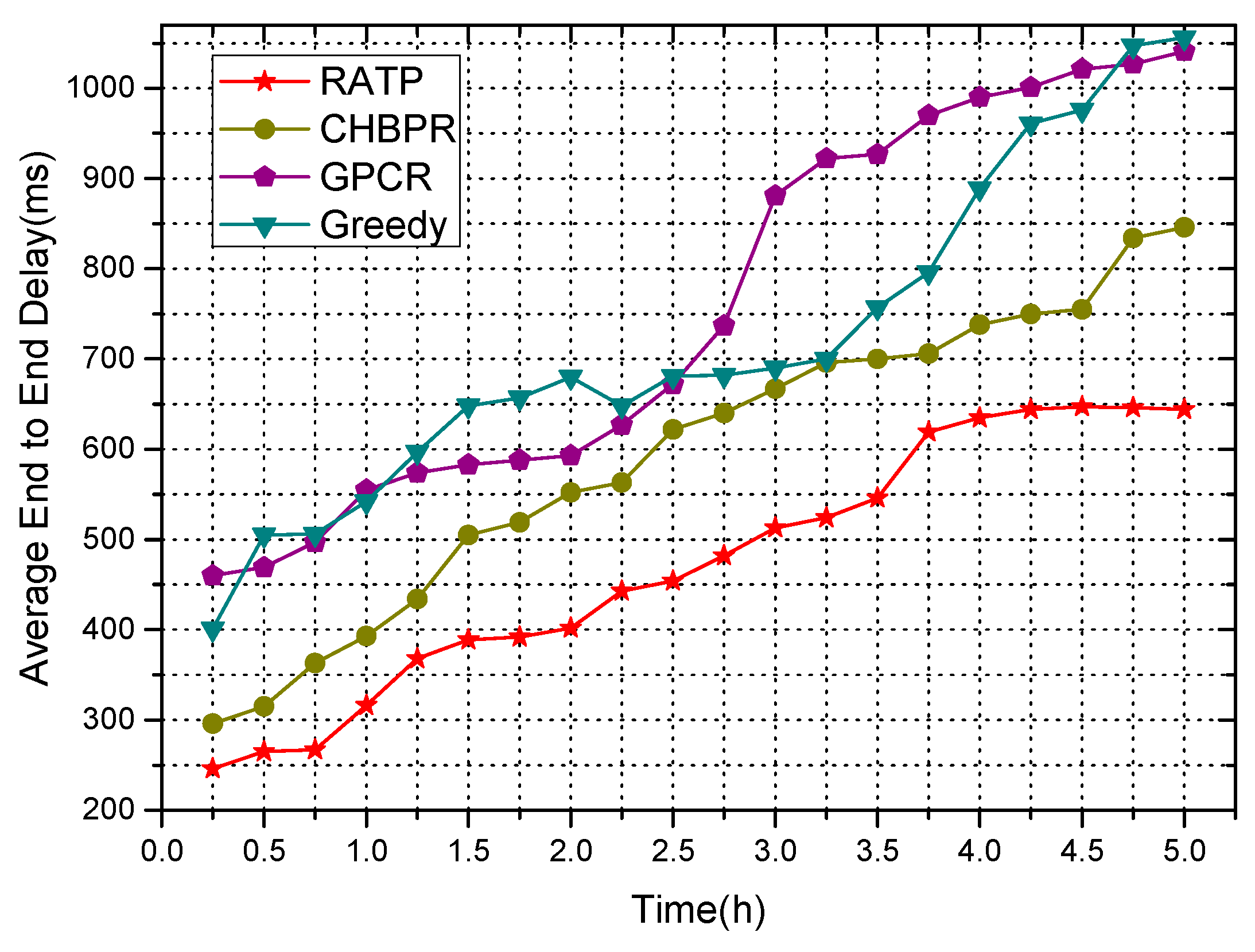
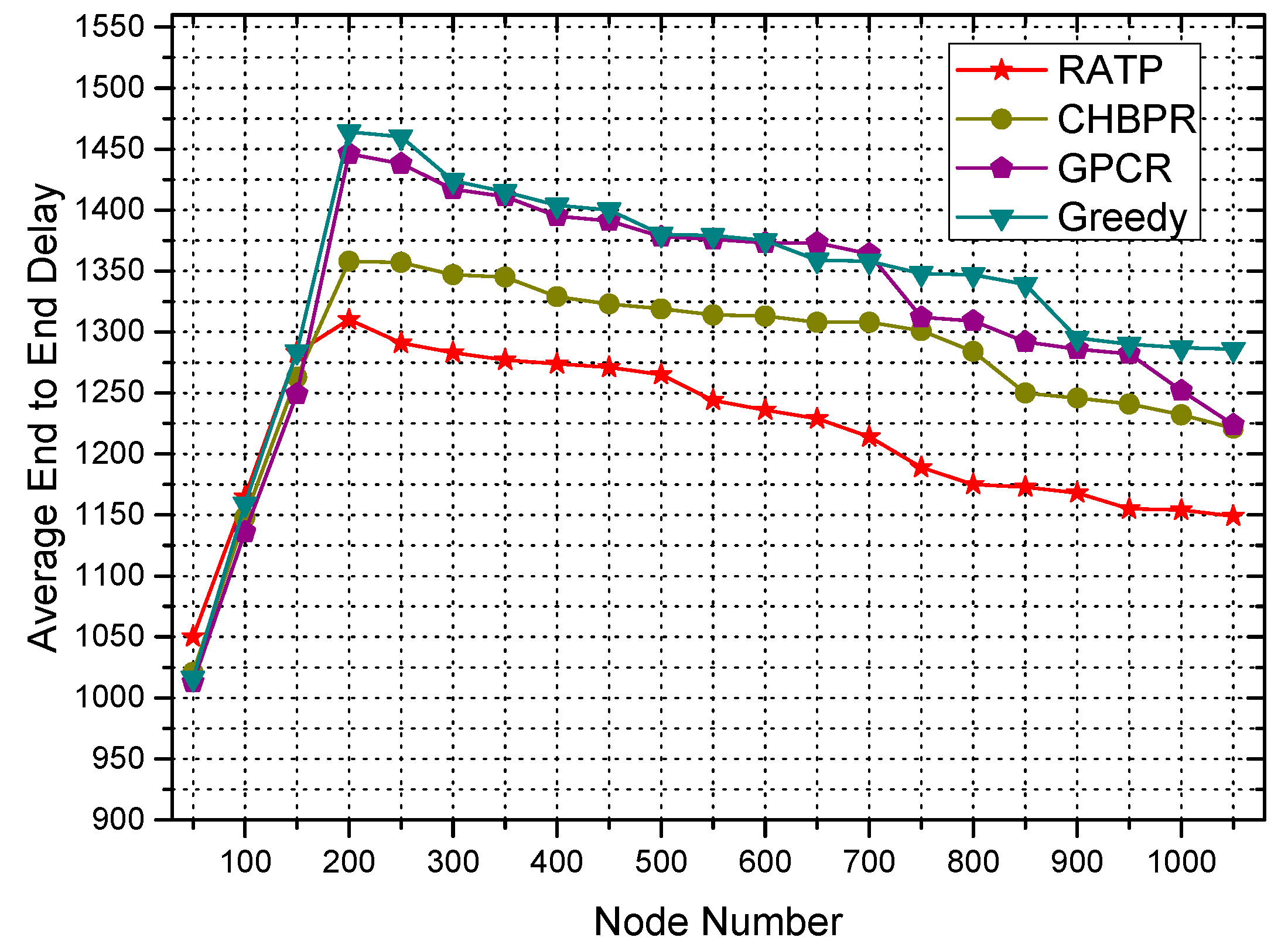
4.2.3. End-to-End Delay
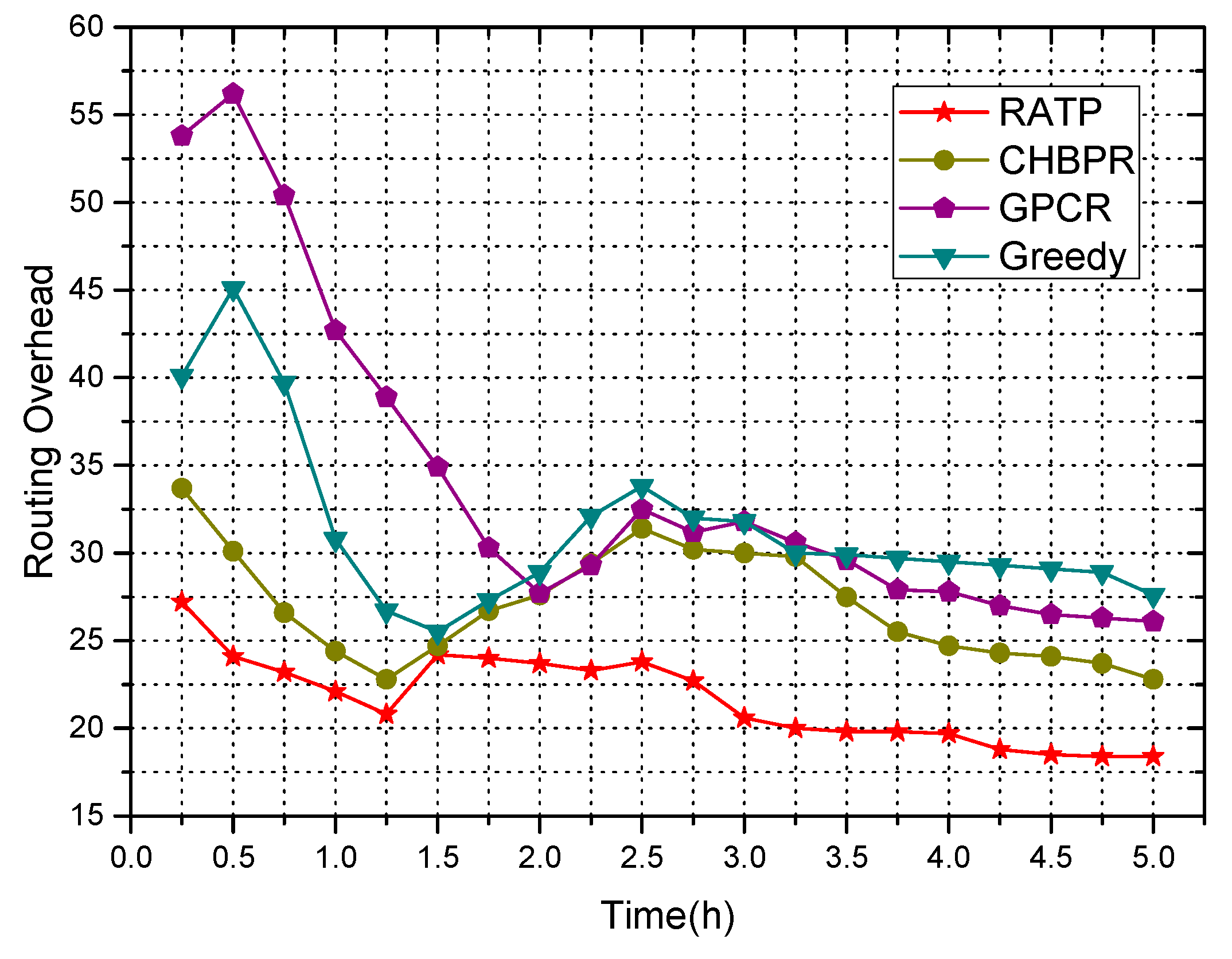
4.2.4. Routing Overhead
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Halikul, L.; Mohamad, A. EpSoc: Social-Based Epidemic-Based Routing Protocol in Opportunistic Mobile Social Network. Mob. Inf. Syst. 2018, 2018, 6462826. [Google Scholar]
- Wu, J.; Chen, Z.; Zhao, M. Weight distribution and community reconstitution based on communities communications in social opportunistic networks. Peer-to-Peer Netw. Appl. 2008, 12, 158–166. [Google Scholar] [CrossRef]
- Huang, F. Research on a Location-Based Routing Protocol E-LAR in Mobile Ad Hoc Networks. Master’s Thesis, Central South University, Changsha, China, June 2009. [Google Scholar]
- Li, J.; Jannotti, J.; De Couto, D.S.; Karger, D.R.; Morris, R. A scalable location service for geographic ad hoc routing. In Proceedings of the 6st Annual International Conference on Mobile Computing and Networking, Boston, MA, USA, 6–11 August 2000; pp. 120–130. [Google Scholar]
- Wang, L.L.; Chen, Z.G.; Wu, J. Vehicle trajectory prediction algorithm in vehicular network. Wirel. Netw. 2018, 1–14. [Google Scholar] [CrossRef]
- Wu, J.; Chen, Z. Human Activity Optimal Cooperation Objects Selection Routing Scheme in Opportunistic Networks Communication. Wirel. Pers. Commun. 2017, 95, 3357–3375. [Google Scholar] [CrossRef]
- Pozza, R.; Nati, M.; Georgoulas, S.; Moessner, K.; Gluhak, A. Neighbor discovery for opportunistic networking in internet of things scenarios: A survey. IEEE Access 2015, 3, 1101–1131. [Google Scholar] [CrossRef]
- Li, Z.; Shen, H.Y.A. Direction Based Geographic Routing Scheme for Intermittently Connected Mobile Networks. In Proceedings of the 8th International Conference on Embedded and Ubiquitous Computing, Shanghai, China, 17–20 December 2008; pp. 359–365. [Google Scholar]
- Ko, Y.B.; Vaidya, N.H. Location·aided routing (LAR) in mobile ad hoe networks. Wirel. Netw. J. 2000, 6, 307–321. [Google Scholar] [CrossRef]
- Wu, K.; Harms, J. Location trace aided routing in mobile ad hoe networks. In Proceedings of the 9th Intemational Conference on Computer Communications and Networks, Las Vegas, NV, USA, 16–18 October 2000; pp. 354–359. [Google Scholar]
- Karp, B.; Kung, H.T. GPSR: Greedy perimeter stateless routing for wireless networks. In Proceedings of the 6th Annual International Conference on Mobile Computing and Networking, Boston, MA, USA, 6–11 August 2000; pp. 243–254. [Google Scholar]
- Huang, C. The Simulation of Grid Location Service Routing Protocol Mobile Ad Hoc Networks. Master’s Thesis, Xidian University of Electronic Technology, Xi’an, China, June 2007. [Google Scholar]
- Stavroulaki, V.; Tsagkaris, K.; Logothetis, M.; Georgakopoulos, A.; Demestichas, P.; Gebert, J.; Filo, M. Opportunistic Networks. IEEE Veh. Technol. Mag. 2011, 6, 52–59. [Google Scholar] [CrossRef]
- Lin, C.R.; Gerla, M. Adaptive clustering for mobile wireless networks. IEEE J. Sel. Areas Commun. 1997, 15, 1265–1275. [Google Scholar] [CrossRef]
- Tsiropoulou, E.E.; Mitsis, G.; Papavassiliou, S. Interest-aware energy collection & resource management in machine to machine communications. Ad Hoc Netw. 2018, 68, 48–57. [Google Scholar]
- Tsiropoulou, E.E.; Paruchuri, S.T.; Baras, J.S. Interest, energy and physical-aware coalition formation and resource allocation in smart IoT applications. In Proceedings of the 2017 51st Annual Conference on Information Sciences and Systems (CISS), Baltimore, MD, USA, 22–24 March 2017; pp. 1–6. [Google Scholar]
- Basagni, S.; Chlamtac, I.; Syrotiuk, V.R.; Woodward, B.A. A distance routing effect algorithm for mobility (DREAM). In Proceedings of the 4th Annual ACM/IEEE International Conference on Mobile Computing and Networking, Dallas, TX, USA, 25–30 October 1998; pp. 76–84. [Google Scholar]
- Bamrah, A.; Woungang, I.; Barolli, L.; Dhurandher, S.K.; Carvalho, G.H.; Takizawa, M. A Centrality-Based History Prediction Routing Protocol for Opportunistic Networks. In Proceedings of the International Conference on Complex, Intelligent, and Software Intensive Systems (CISIS), Fukuoka, Japan, 6–8 July 2016. [Google Scholar]
- Dhurandher, S.K.; Woungang, I.; Rajendra, A.; Ghaie, P.; Chatzimisios, P. A Centrality-based ACK Forwarding Mechanism for E_cient Routing in Opportunistic Networks. In Proceedings of the International Conference on Cyber Physical Systems, IoT and Sensors Networks (Cyclone 2015), Rome, Italy, 26 October 2015. in press. [Google Scholar]
- Yu, Y.; Govindan, R.; Estrin, D. Geographic and Energy-Aware Routing: A Recursive Data Dissemination Protocol for Wireless Sensor Networks; UCLA Computer Science Department Technical Report; UCLA Computer Science Department: Los Angeles, CA, USA, 2001. [Google Scholar]
- Kamal, J.M.M.; HASAN, M.; Griffiths, A.; Yu, H. Prediction-based Opportunistic Greedy Routing for Vehicular Ad Hoc Networks. In Proceedings of the 16th International Conference on Automation and Computing, Birmingham, UK, 11 September 2010. [Google Scholar]
- Finn, G.G. Routing and Addressing Problems in Large Metropolitan-Scale Internetworks; ISI Research Report ISU/RR; Advanced Research Projects Agency (DOD): Washington, DC, USA, 1987. [Google Scholar]
- Zou, X.; Cao, Y.; Liu, X.; Gao, X. DPSO-Based Clustering Routing Approach for WSN. J. Wuhan Univ. 2008, 54, 99–103. [Google Scholar]
- Lochert, C.; Mauve, M.; Füßler, H.; Hartenstein, H. Geographic routing in city sce-narios. Mob. Comput. Commun. Rev. 2005, 9, 69–72. [Google Scholar] [CrossRef]
- Jerbi, M.; Meraihi, R.; Senouci, S.M.; Ghamri-Doudane, Y. GyTAR: Improved greedy traffic aware routing protocol for vehicular ad hoc networks in city environments. In Proceedings of the International Workshop on Vehicular Ad Hoc Networks, Los Angeles, CA, USA, 29 September 2006; pp. 88–89. [Google Scholar]


© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zou, P.; Zhao, M.; Wu, J.; Wang, L. Routing Algorithm Based on Trajectory Prediction in Opportunistic Networks. Information 2019, 10, 49. https://doi.org/10.3390/info10020049
Zou P, Zhao M, Wu J, Wang L. Routing Algorithm Based on Trajectory Prediction in Opportunistic Networks. Information. 2019; 10(2):49. https://doi.org/10.3390/info10020049
Chicago/Turabian StyleZou, Peijun, Ming Zhao, Jia Wu, and Leilei Wang. 2019. "Routing Algorithm Based on Trajectory Prediction in Opportunistic Networks" Information 10, no. 2: 49. https://doi.org/10.3390/info10020049
APA StyleZou, P., Zhao, M., Wu, J., & Wang, L. (2019). Routing Algorithm Based on Trajectory Prediction in Opportunistic Networks. Information, 10(2), 49. https://doi.org/10.3390/info10020049





