A Bit Torrent Traffic Optimization Method for Enhancing the Stability of Network Traffic
Abstract
1. Introduction
- (1)
- The concept of traffic relaxation to describe traffic state of network is introduced and used in our improved algorithm.
- (2)
- Peers are selected probabilistically according to the relative magnitude of each peer’s apportioned traffic relaxation in the BT group when selecting peer.
- (3)
- The allocation traffic relaxation and upload rate are simultaneously considered when choosing peer to be choked or unchoked.
- (4)
- We improve the adaptability of the general peer-to-peer simulator (GPS) and realize the simulation of our improved BT protocol.
2. Related Work
3. Our New BT Traffic Optimization Strategy
3.1. Peer Selection Algorithm
3.2. Choking/Unchoking Algorithm
4. Experimental Verification and Analysis
4.1. Experiment Setup and Performance Indicators
4.1.1. General Peer-to-Peer Simulator (GPS) Simulator
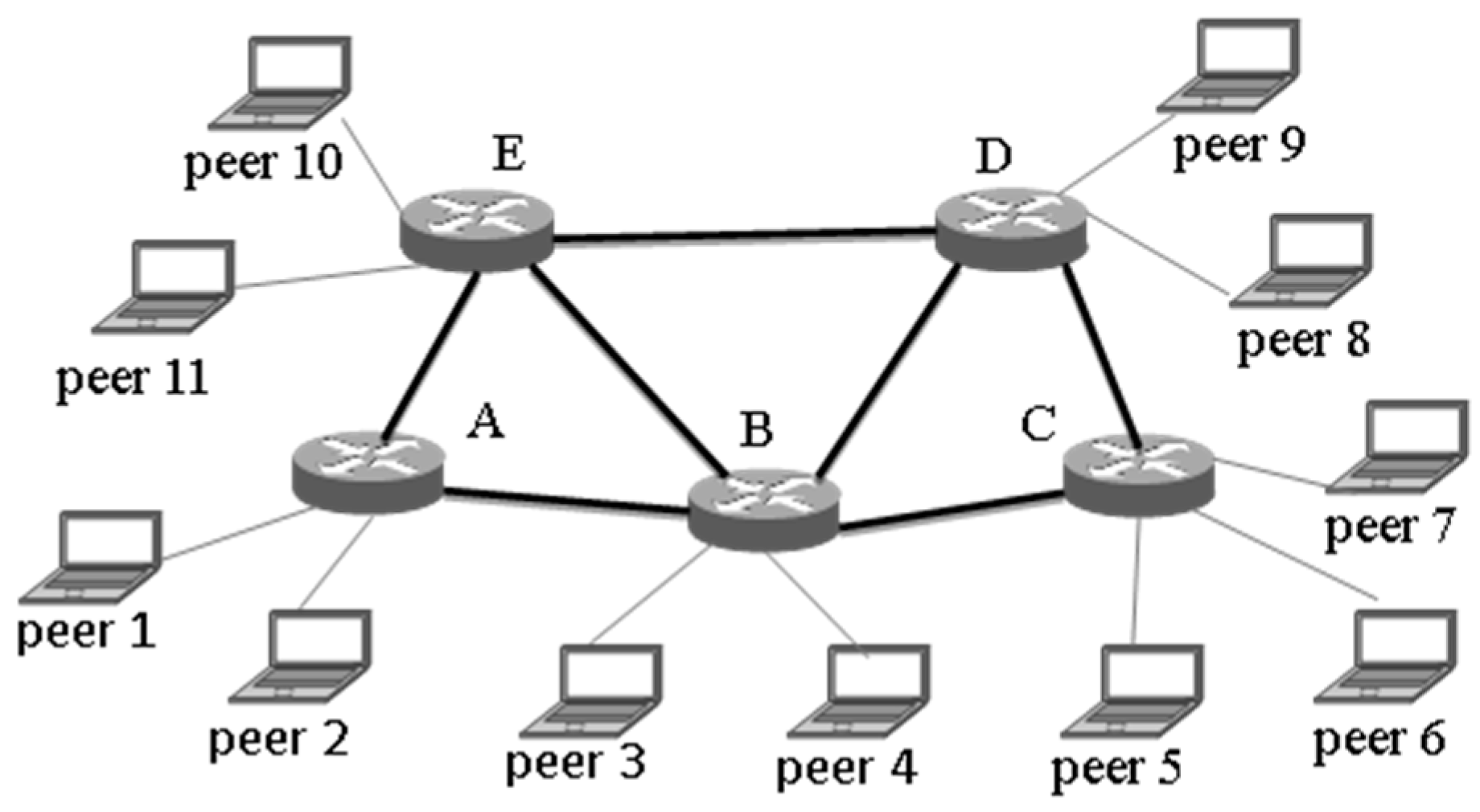
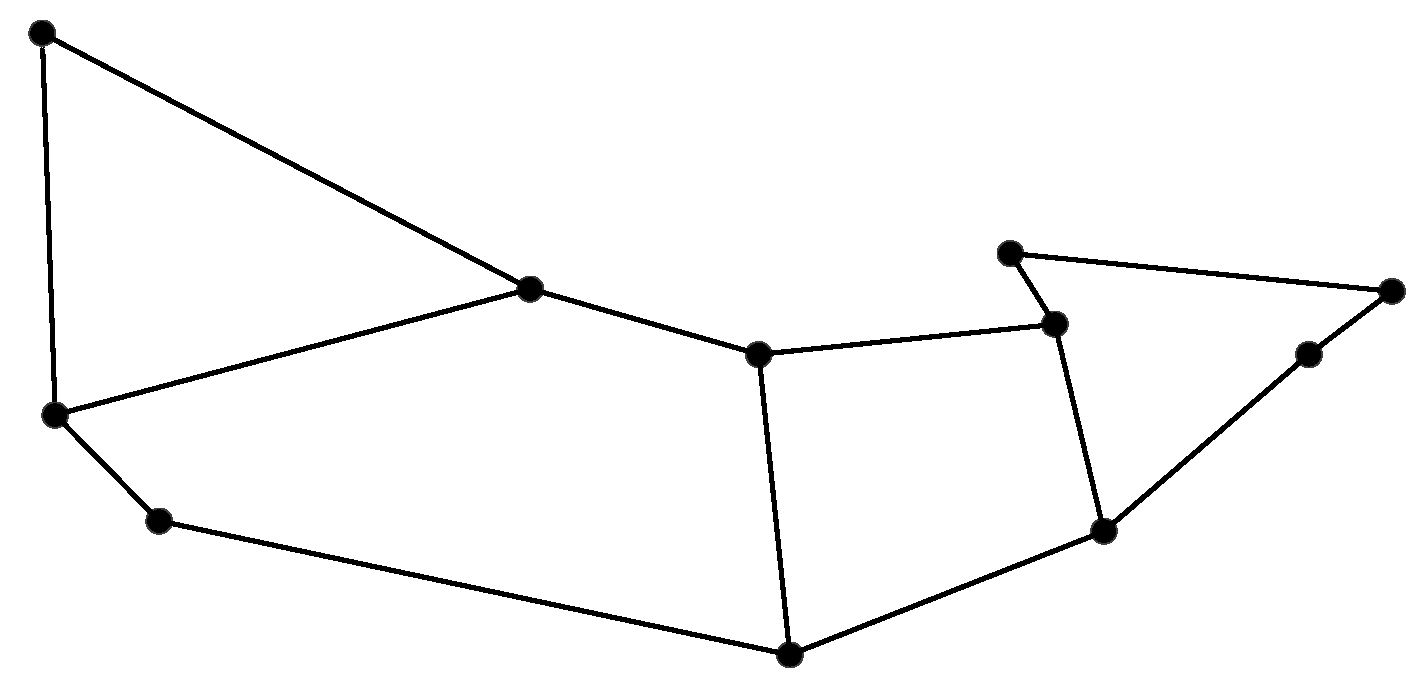
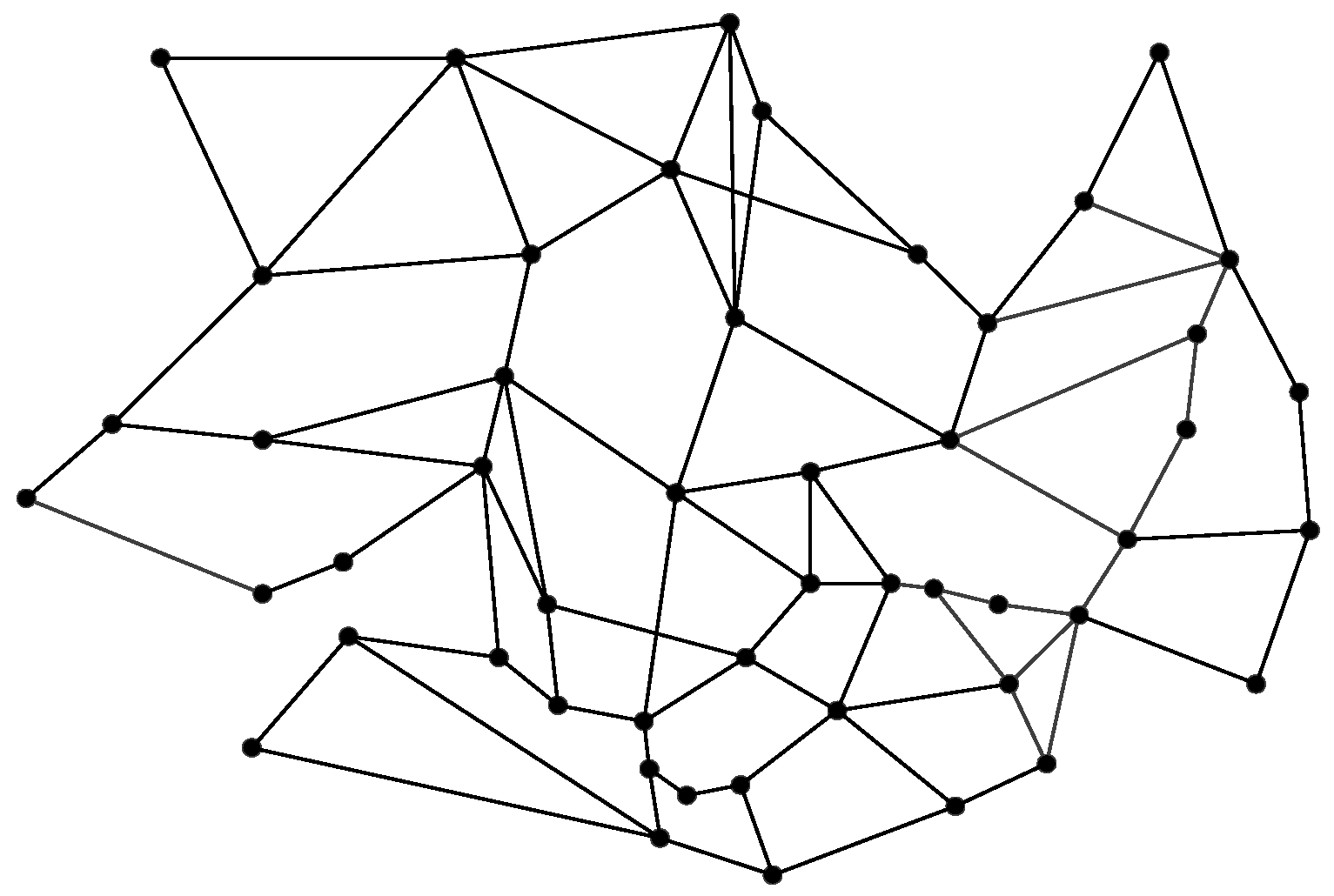
4.1.2. Network Topology
4.1.3. Traffic Matrix
4.1.4. Network Status
4.2. Performance Indicators
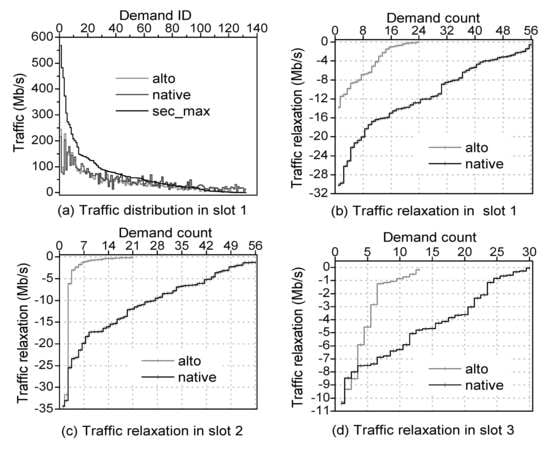
4.3. Experiment Result
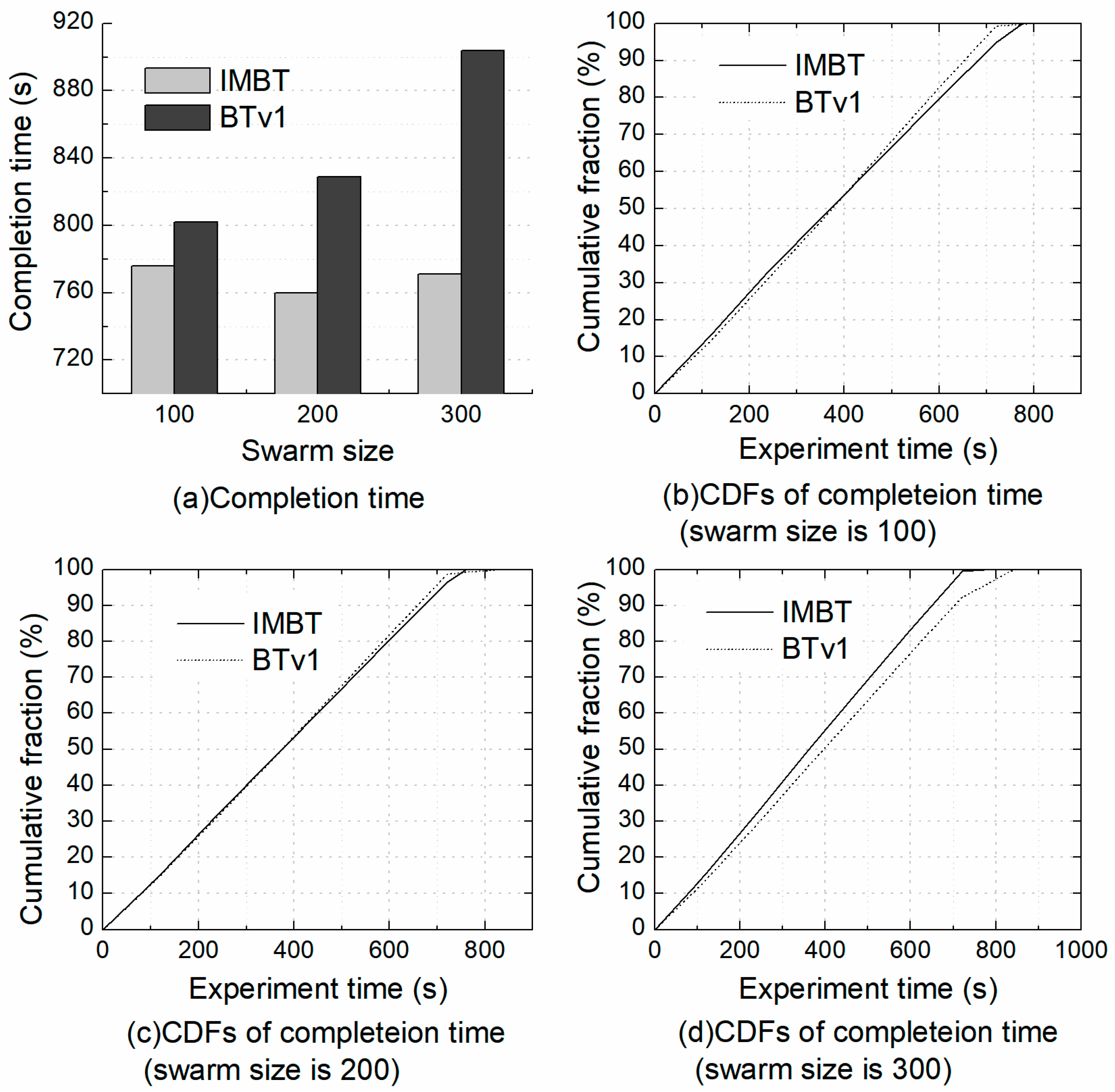
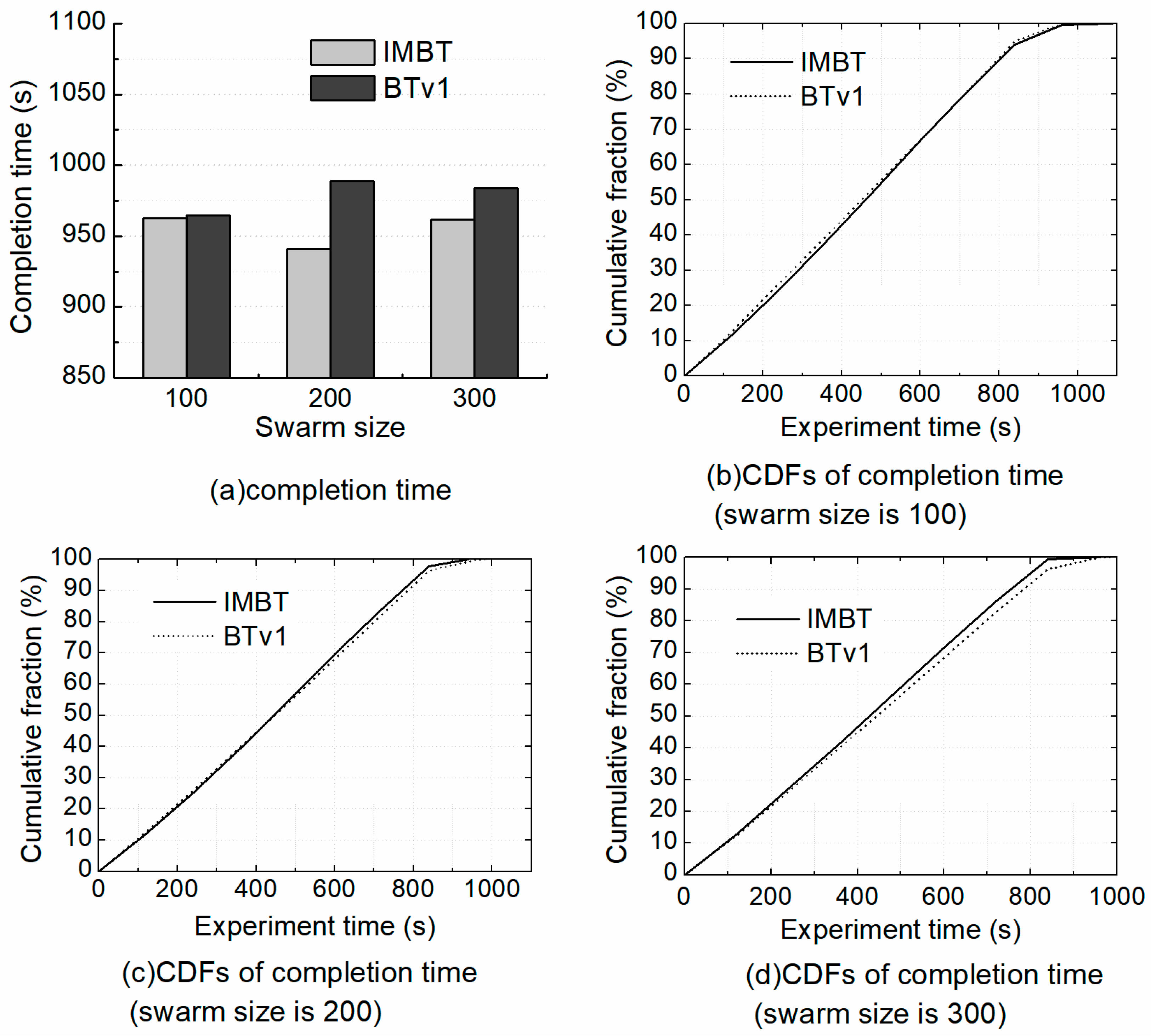
4.3.1. Completion Time
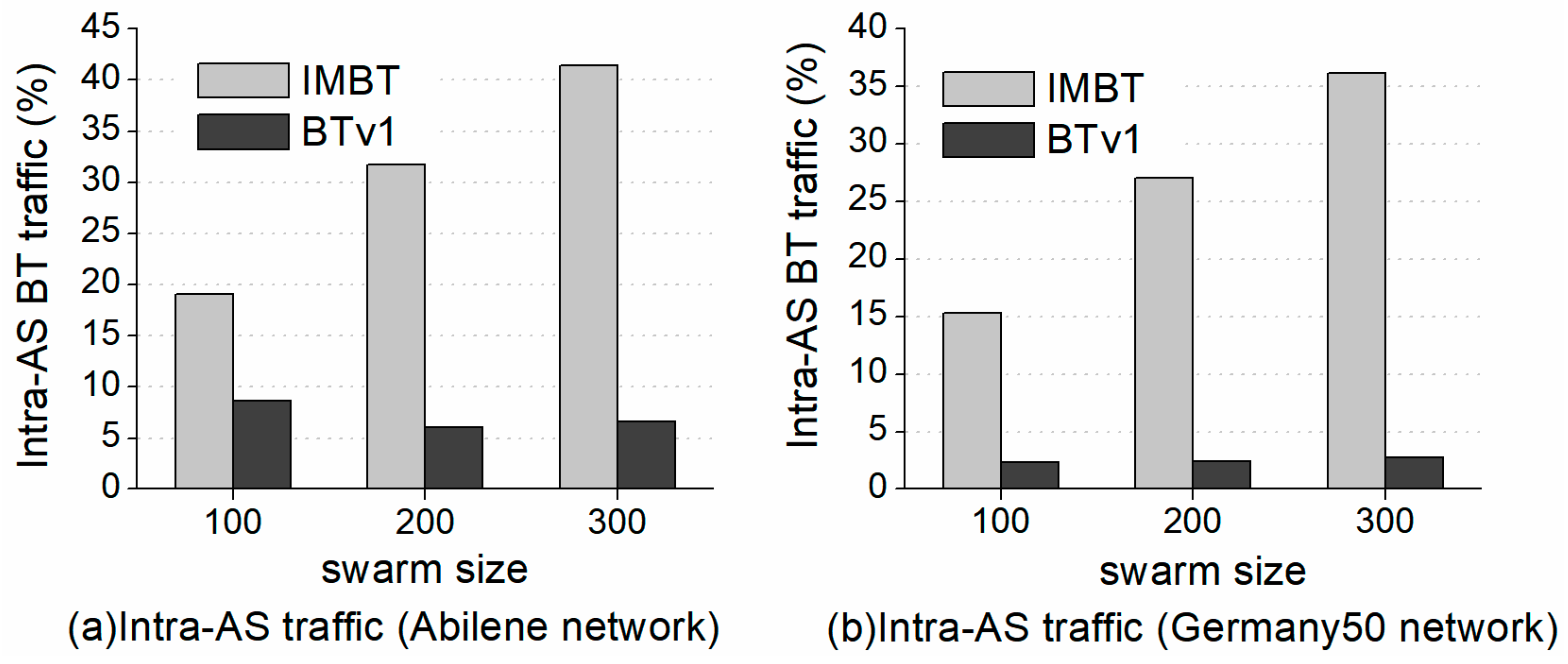
4.3.2. Intra-Domain Traffic
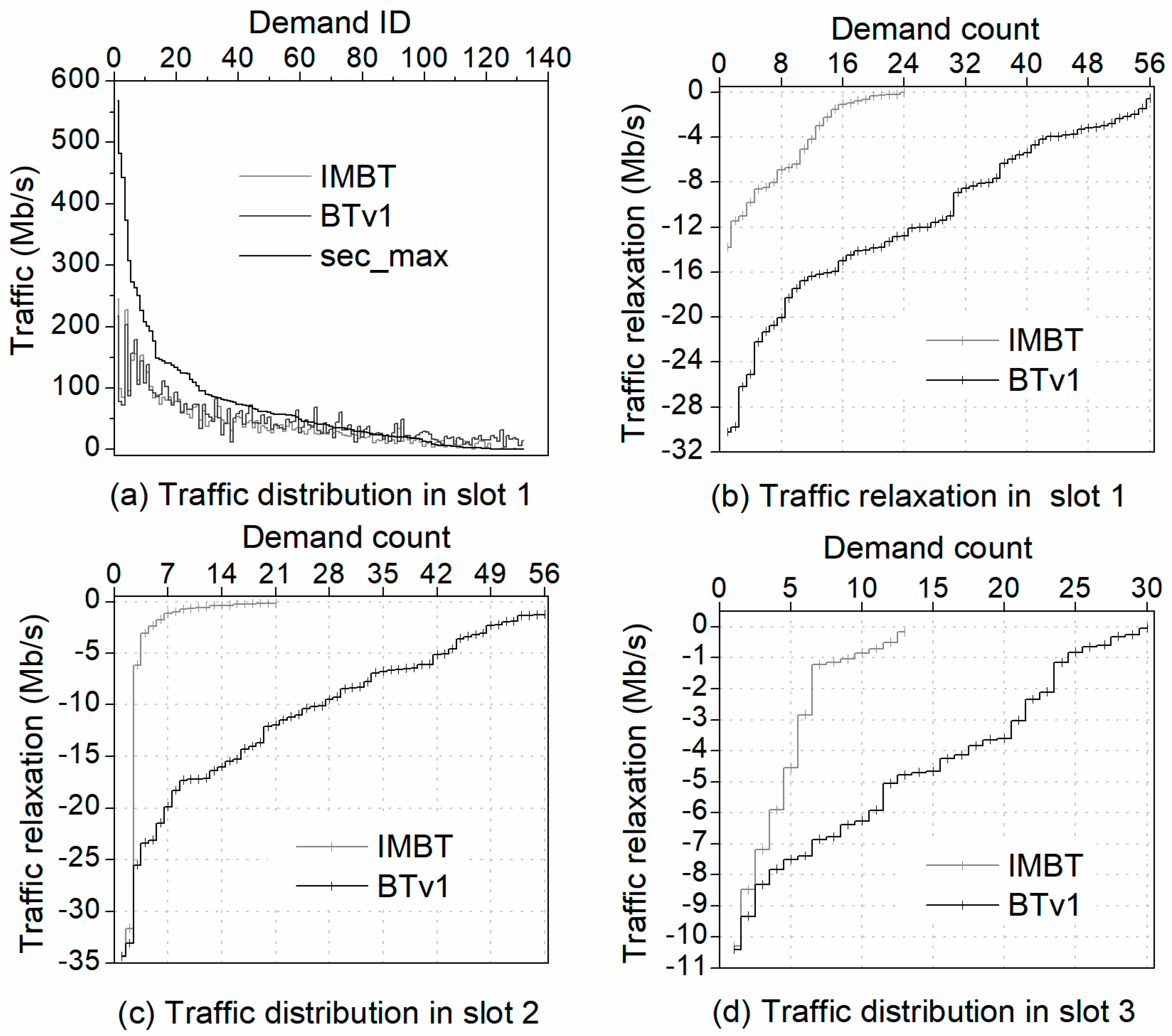
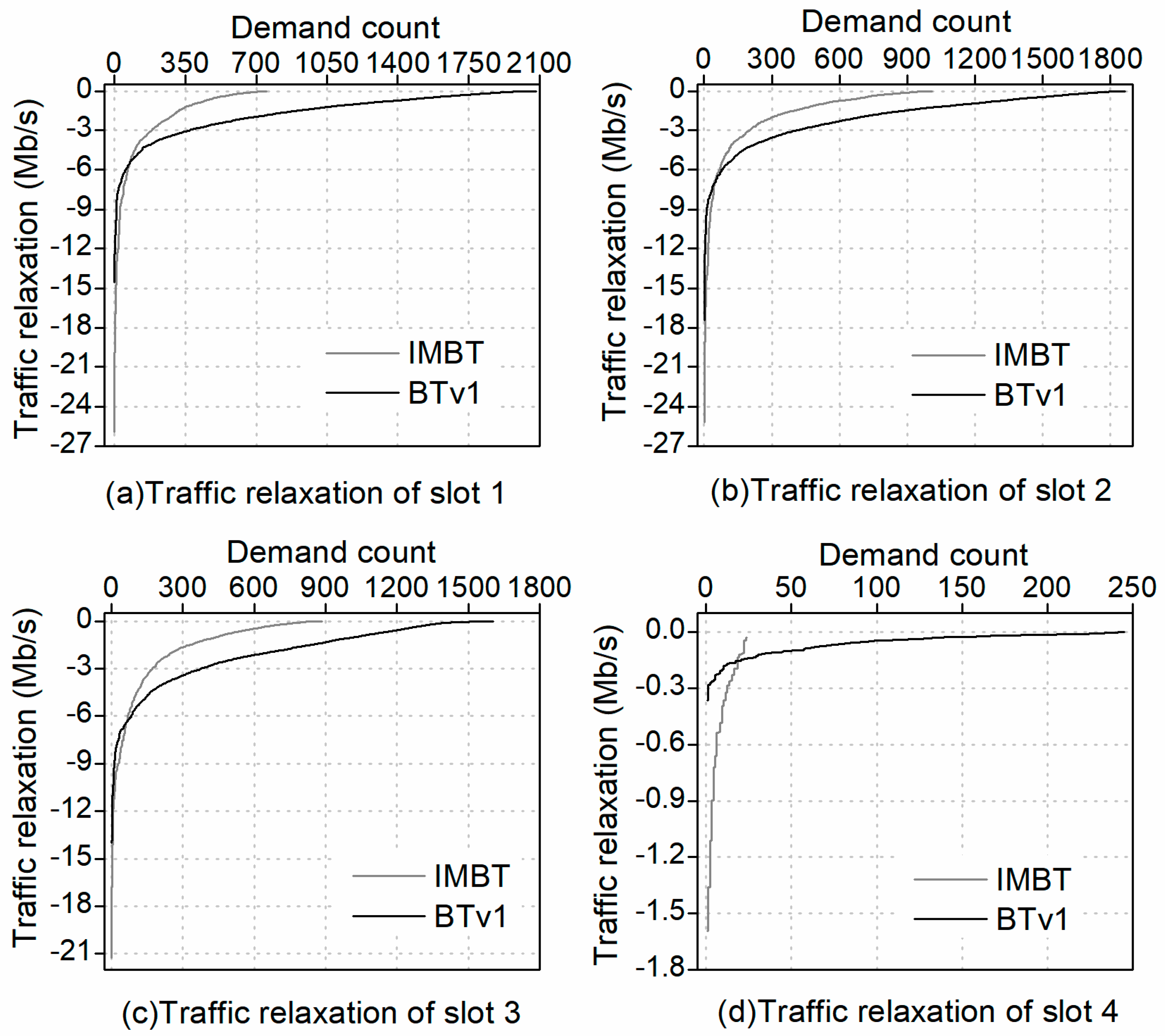
4.3.3. Traffic Relaxation
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Wang, Q.; Lu, P. Research on application of artificial intelligence in computer network technology. Int. J. Pattern Recognit. Artif. Intell. 2019, 33, 1959015. [Google Scholar] [CrossRef]
- Alshawwa, I.A.; Al-Shawwa, M.O.; Abu-Naser, S.S. An Intelligent Tutoring System for Learning Computer Network CCNA. 2019. Available online: http://dstore.alazhar.edu.ps/xmlui/handle/123456789/129 (accessed on 19 November 2019).
- Awasthi, S.K.; Singh, Y.N. Simplified Biased Contribution Index (SBCI): A mechanism to make P2P network fair and efficient for resource sharing. J. Parallel Distrib. Comput. 2019, 124, 106–118. [Google Scholar] [CrossRef]
- Essaid, M.; Park, S.; Ju, H. Visualising Bitcoin’s Dynamic P2P Network Topoogy and Performance. In Proceedings of the 2019 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Seoul, Korea, 14–17 May 2019; pp. 141–145. [Google Scholar]
- Padmavathi, M.; Suresh, R.M. Secure P2P Intelligent Network Transaction using Litecoin. Mob. Netw. Appl. 2019, 24, 318–326. [Google Scholar] [CrossRef]
- Puthusseri, K.S.; Shetty, A.; Patil, M.; Devadkar, K.K. Storage and Availability Aware Fragment Placement for P2P Storage Systems. In Proceedings of the 2019 International Conference on Communication and Signal Processing (ICCSP), Tamil Nadu, India, 4–6 April 2019; pp. 867–871. [Google Scholar]
- Zhang, Q.Y.; Wang, X.W.; Huang, M.; Li, K.Q.; Das, S.K. Software defined networking meets information centric networking: A survey. IEEE Access 2018, 6, 39547–39563. [Google Scholar] [CrossRef]
- Kim, H.; Feamster, N. Improving network management with software defined networking. IEEE Commun. Mag. 2013, 51, 114–119. [Google Scholar] [CrossRef]
- Cox, J.H.; Chung, J.; Donovan, S.; Ivey, J.; Clark, R.J.; Riley, G.; Owen, H.L. Advancing software-defined networks: A survey. IEEE Access 2017, 5, 25487–25526. [Google Scholar] [CrossRef]
- Jimson, E.R.; Nisar, K.; Hijazi, M.H.A. The State of the Art of Software Defined Networking (SDN): Network Management Solution in Current Network Architecture Using the SDN. Int. J. Inf. Commun. Technol. Hum. Dev. (IJICTHD) 2018, 10, 44–60. [Google Scholar] [CrossRef]
- Mostafaei, H.; Lospoto, G.; Brandimartey, A.; Di Lallo, R.; Rimondini, M.; Di Battista, G. SDNS: Exploiting sdn and the dns to exchange traffic in a federated network. In Proceedings of the 2017 IEEE Conference on Network Softwarization (NetSoft), Bologna, Italy, 3–7 July 2017; pp. 1–5. [Google Scholar]
- Mostafaei, H.; Lospoto, G.; di Lallo, R.; Rimondini, M.; Di Battista, G. Sdnetkit: A testbed for experimenting sdn in multi-domain networks. In Proceedings of the 2017 IEEE Conference on Network Softwarization (NetSoft), Bologna, Italy, 3–7 July 2017; pp. 1–6. [Google Scholar]
- Soule, A.; Nucci, A.; Cruz, R.; Leonardi, E.; Taft, N. How to identify and estimate the largest traffic matrix elements in a dynamic environment. ACM SIGMETRICS Perform. Eval. Rev. 2004, 32, 73–84. [Google Scholar] [CrossRef]
- Cao, J.; Cleveland, W.S.; Lin, D.; Sun, D.X. Internet traffic tends toward Poisson and independent as the load increases. In Nonlinear Estimation and Classification; Springer: New York, NY, USA, 2003; pp. 83–109. [Google Scholar]
- Wu, Y.; Guo, B.; Shen, Y.; Wang, J.; Liu, X. Green virtual topology design algorithm based on constraint-based routing. J. Commun. 2014, 35, 112–123. [Google Scholar]
- Wu, Y.; Guo, B.; Shen, Y.; Wang, J.; Liu, X. Toward energy-proportional Internet core networks: An energy-minimized routing and virtual topology design for Internet protocol layer. Int. J. Commun. Syst. 2015, 28, 513–533. [Google Scholar] [CrossRef]
- Nucci, A.; Sridharan, A.; Taft, N. The problem of synthetically generating IP traffic matrices: Initial recommendations. Comput. Commun. Rev. 2005, 35, 19–31. [Google Scholar] [CrossRef]
- Karagiannis, T.; Rodriguez, P.; Papagiannaki, K. Should internet service providers fear peerassisted content distribution? In Proceedings of the Internet Measurement Conference, Berkeley, CA, USA, 19–21 October 2005; pp. 1–14. [Google Scholar]
- Yang, P.; Xu, L. On tradeoffs between cross-ISP P2P traffic and P2P streaming performance. Comput. Netw. 2011, 55, 4033–4042. [Google Scholar] [CrossRef]
- Liu, Y.; Xiao, L.; Liu, X.; Ni, L.M.; Zhang, X. Location awareness in unstructured peer-to-peer systems. IEEE Trans. Parallel Distrib. Syst. 2005, 6, 163–174. [Google Scholar]
- Ren, S.; Tan, E.; Luo, T.; Chen, S.; Guo, L.; Zhang, X. TopBT: A topology-aware and infrastructure-independent BitTorrent client. In Proceedings of the IEEE INFOCOM, San Diego, CA, USA, 15–19 March 2010. [Google Scholar]
- Zhou, R. P2P traffic optimization based P2P cache (in Chinese). Telecommun. Netw. Tech. 2009, 1, 11–15. [Google Scholar]
- Hefeeda, M.; Saleh, O. Traffic modeling and proportional partial caching for peer-to-peer systems. IEEE/ACM Trans. Netw. 2008, 16, 1447–1460. [Google Scholar] [CrossRef]
- Aggarwal, V.; Feldmann, A.; Scheidler, C. Can ISPs and P2P Systems Co-Operate for Improved[22]Performance? ACM SIGCOMM Comput. Commun. Rev. 2007, 37, 29–40. [Google Scholar] [CrossRef]
- Bruni, L.; Giacomazzi, P.; Poli, A. Performance optimization of the BitTorrent protocol in the framework of P4P IETF ALTO. In Proceedings of the IWCMC 2013, Sardinia, Italy, 1–5 July 2013; pp. 431–436. [Google Scholar]
- Gurbani, V.K.; Hilt, V.; Rimac, I.; Tomsu, M.; Marocco, E. A Survey of Research on the Application-layer Traffic Optimization Problem and the Need for Layer Cooperation. IEEE Commun. Mag. 2009, 47, 107–112. [Google Scholar] [CrossRef]
- Madhyastha, H.V.; Isdal, T.; Piatek, M.; Dixon, C.; Anderson, T.; Krishnamurthy, A.; Venkataramani, A. iPlane: An information plane for distributed services. In Proceedings of the 7th Symposium on Operating Systems Design and Implementation, Seattle, WA, USA, 6–8 November 2006; USENIX Association: Berkeley, CA, USA, 2006. [Google Scholar]
- Zhang, G.; Tang, M.; Cheng, S.; Zhang, G.; Song, H.; Cao, J.; Yang, J. P2P traffic optimization. Sci. China Inf. Sci. 2012, 55, 1475–1492. [Google Scholar] [CrossRef]
- Chokkalingam, A.; Riyaz, F. BitTorrent Protocol Specification v 1.0. CSI 5321. 2004. Available online: cs.ecs.baylor.edu/~donahoo/classes/5321/projects/bittorrent/BitTorrent%20Protocol%20Specification.doc (accessed on 20 November 2019).
- Yang, W.; Abu-Ghazaleh, N. GPS: A general peer-to-peer simulator and its use for modeling BitTorrent. In Proceedings of the 13th IEEE International Symposium on Modeling, Analysis, and Simulation of Computer and Telecommunication Systems, Atlanta, GA, USA, 27–29 September 2005; pp. 425–432. [Google Scholar]
- Orlowski, S.; Wessaly, R.; Pioro, M.; Tomaszewski, A. SNDlib 1.0—Survivable network design library. Networks 2010, 55, 276–286. [Google Scholar] [CrossRef]


© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, D.; Zhang, Y.; Jia, S.; Liu, D.; Jin, Y.; Wu, Y. A Bit Torrent Traffic Optimization Method for Enhancing the Stability of Network Traffic. Information 2019, 10, 361. https://doi.org/10.3390/info10120361
Li D, Zhang Y, Jia S, Liu D, Jin Y, Wu Y. A Bit Torrent Traffic Optimization Method for Enhancing the Stability of Network Traffic. Information. 2019; 10(12):361. https://doi.org/10.3390/info10120361
Chicago/Turabian StyleLi, Deguang, Yongxin Zhang, Shijie Jia, Dong Liu, Yanling Jin, and Yuansheng Wu. 2019. "A Bit Torrent Traffic Optimization Method for Enhancing the Stability of Network Traffic" Information 10, no. 12: 361. https://doi.org/10.3390/info10120361
APA StyleLi, D., Zhang, Y., Jia, S., Liu, D., Jin, Y., & Wu, Y. (2019). A Bit Torrent Traffic Optimization Method for Enhancing the Stability of Network Traffic. Information, 10(12), 361. https://doi.org/10.3390/info10120361