AndroShield: Automated Android Applications Vulnerability Detection, a Hybrid Static and Dynamic Analysis Approach
Abstract
:1. Introduction
2. Background
2.1. Vulnerability Detection Techniques
2.1.1. Static Analysis
- Points-to analysis [4].
- Call-Graph (CG) algorithms.
2.1.2. Dynamic Analysis
2.2. Android Sources and Sinks
3. Related Work
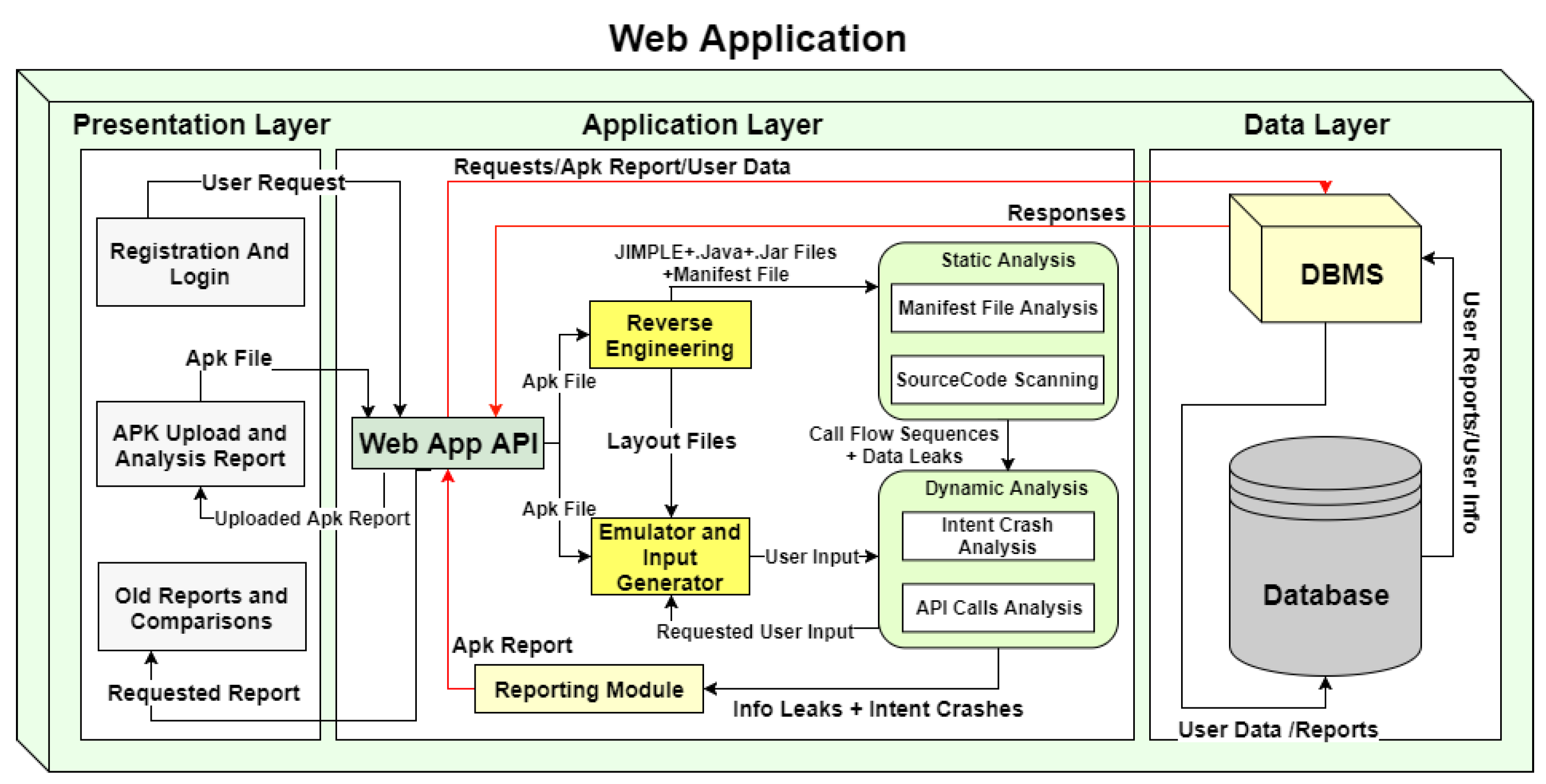
4. Methodology and Architecture
4.1. Proposed Architecture
4.1.1. Application Layer
4.1.2. Presentation Layer
4.1.3. Data Layer
4.2. Methodology
- APK Reverse Engineering: The first step after the APK file is submitted is to de-compile (reverse engineer) it. The aim of this stage is to get the code and the manifest file of the submitted APK file. ApkAnalyzer [42]—an Android SDK command-line tool—was used to perform the reverse engineering task with the help of Soot [21]—a Java optimization framework. It is important to note here that before any application is zipped into the final APK file, the Android program (the Java source code) is compiled into a single DEX (Dalvik Executable) file. Alternatively, it will be compiled into multiple DEX files if the app and the libraries it references exceed 64KB. Then, the DEX file(s) are reversed and then transformed into JAR files—which are compiled Java files. ApkAnalyzer handles this process, it extracts the DEX files from the APK file, then transforms them into Jimple files directly by soot framework that can be used for performing the analysis. The output of this phase includes the code as well as the extracted binary manifest file.
- Decoding Manifest File: The output manifest file is in binary format. At this step, the manifest file is transformed from binary format to XML format.
- Extracting Meta-data: Having the XML version of the manifest file, the following information is extracted:
- Package Name
- Version Name
- Version Code
- Minimum SDK Version
- Target SDK Version
- Debug Mode (Yes/No)
- Backup Mode (Yes/No)
- Test Only Flag (Yes/No)
They are then displayed in the report and some are used as well for Static Analysis phase. - Performing Static Analysis: In this phase, the static analysis uses the reverse engineered code to trace vulnerabilities. During static analysis, the code is analyzed without executing the application. Details of the static analysis are discussed in Section 4.2.1.
- Performing Dynamic Analysis: Dynamic analysis focuses on tracing vulnerabilities while the application is running. Vulnerabilities, in this case, are not detected by analyzing the code in the static phase. Details of the dynamic analysis are discussed in Section 4.2.2.
- Generating the Report: The final phase is to combine all the information gathered and visualize them in a user-friendly report format.
4.2.1. Static Analysis
Manifest File Analysis
- Backup Flag is considered vulnerable if its value is true. Backup is done by copying the application data (for example, application database and files) to the SD card. Application information on the SD card is less secure than on the mobile phone memory. This is because it is easier to grant write permission on SD cards. Vulnerability risk of enabling backup is estimated Low as the information that is backed up may not have sensitive information to be fully risky.
- Debug Flag is considered vulnerable if its value is true. Android application developers use debug mode to be able to log important fields and verify whether or not they are correct. Unfortunately, forgetting to change the application to be in release mode enables hackers to easily sniff on the application. Vulnerability risk of enabling debug mode is estimated High as a lot of information can be revealed while the application is in debug mode.
- Exported Components (activities and services) are considered vulnerable if they exist. Leaving more components opened to other applications and services requires more interfaces to secure against attacks. A malicious user can fuzz on the interfaces until finding a way to break an interface. Vulnerability risk of exported components is estimated Low as the getaways may be secured and may be the components are exported on purpose not by mistake, so it is not as risky as other vulnerabilities.
- Test Only Flag which is not vulnerable but is used for the dynamic analysis phase indicating that APK will not applicable to execute as it is just part of the application, not the whole application.
Source Code Scanning
4.2.2. Dynamic Analysis
Intent Crash Analysis
API Calls Analysis
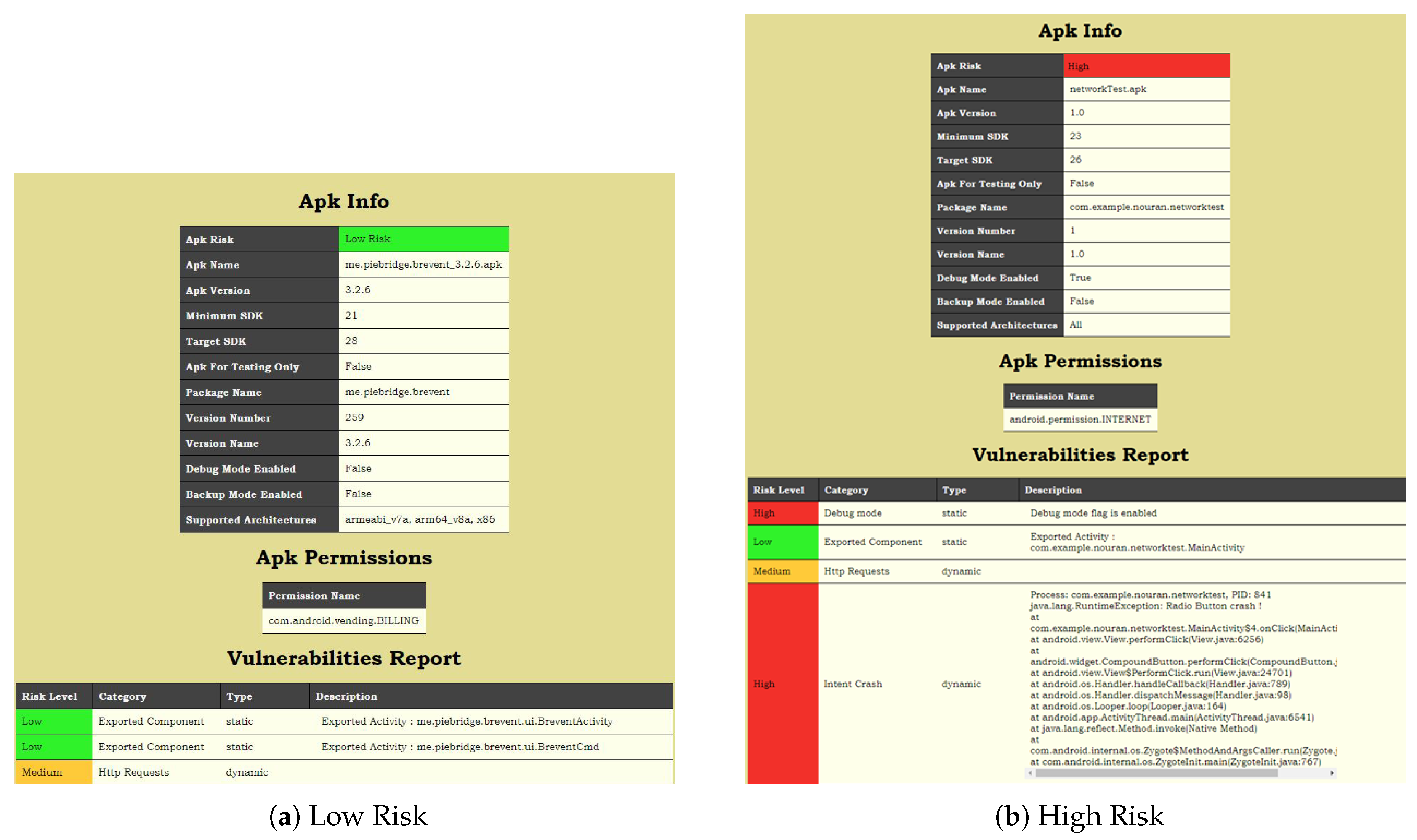
5. Experiments and Results
- httpRequest_crash application: This is a developed application aimed to evaluate HTTP requests and intent crashes detection.Overall App risk: MediumThe detected vulnerabilities are:
- Static: Exported Components, Debug Mode Enabled, Backup Mode Enabled
- Dynamic: Http Requests, Intent Crashes
- TestOnlyFlag: This is a developed application aimed to evaluate static analysis only. Dynamic analysis won’t execute because the application is flagged as Test Only.Overall App risk: MediumThe detected vulnerabilities are:
- Static: Exported Components, Debug Mode Enabled, Backup Mode Enabled
- Ampere: This is one of the applications on the Google Play store. It is used for battery usage and voltage calculation.Overall App risk: MediumThe detected vulnerabilities are:
- Static: Exported Components, Information Leaks
- Brevent: This is one of the applications on the Google Play store. It is used to control other applications that are in the background.Overall App risk: LowThe detected vulnerabilities are:
- Static: Exported Components
- GoIV: This is one of the applications on the Google Play store. It is used alongside Pokemon Go game.Overall App risk: LowThe detected vulnerabilities are:
- Static: Exported Components, Information Leaks
6. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Clement, J. Annual number of mobile app downloads worldwide 2018 | Statista. Available online: https://www.statista.com/statistics/271644/worldwide-free-and-paid-mobile-app-store-downloads/ (accessed on 12 October 2019).
- Ponemon Institute, LLC. The State of Mobile Application Insecurity; Technical Report; Ponemon Institute, Sponsored by IBM: Great Lakes, MI, USA, 2015. [Google Scholar]
- Wang, X.; Zhu, S.; Zhou, D.; Yang, Y. Droid-AntiRM: Taming Control Flow Anti-analysis to Support Automated Dynamic Analysis of Android Malware. In Proceedings of the 33rd Annual Computer Security Applications Conference, Orlando, FL, USA, 4–8 December 2017; pp. 350–361. [Google Scholar]
- Li, L.; Bissyandé, T.F.; Papadakis, M.; Rasthofer, S.; Bartel, A.; Octeau, D.; Klein, J.; Traon, L. Static analysis of android apps: A systematic literature review. Inf. Softw. Technol. 2017, 88, 67–95. [Google Scholar] [CrossRef] [Green Version]
- Meng, Z.; Xiong, Y.; Huang, W.; Miao, F.; Jung, T.; Huang, J. Divide and Conquer: Recovering Contextual Information of Behaviors in Android Apps around Limited-quantity Audit Logs. arXiv 2018, arXiv:1809.07036. [Google Scholar]
- Wei, F.; Roy, S.; Ou, X. Amandroid: A precise and general inter-component data flow analysis framework for security vetting of Android apps. ACM Trans. Priv. Secur. (TOPS) 2018, 21, 14. [Google Scholar] [CrossRef]
- Dean, J.; Grove, D.; Chambers, C. Optimization of object-oriented programs using static class hierarchy analysis. In Proceedings of the European Conference on Object-Oriented Programming, Åarhus, Denmark, 7–11 August 1995; pp. 77–101. [Google Scholar]
- Bacon, D.F.; Sweeney, P.F. Fast static analysis of C++ virtual function calls. ACM Sigplan Not. 1996, 31, 324–341. [Google Scholar] [CrossRef] [Green Version]
- Sundaresan, V.; Hendren, L.; Razafimahefa, C.; Vallée-Rai, R.; Lam, P.; Gagnon, E.; Godin, C. Practical Virtual Method Call Resolution for Java; ACM: New York, NY, USA, 2000; Volume 35. [Google Scholar]
- Andersen, L.O. Program Analysis and Specialization for the C Programming Language. Ph.D. Thesis, University of Cophenhagen, Copenhagen, Denmark, 1994. [Google Scholar]
- Steensgaard, B. Points-to analysis in almost linear time. In Proceedings of the 23rd ACM SIGPLAN-SIGACT Symposium on Principles of Programming Languages, St. Petersburg Beach, FL, USA, 21–24 January 1996; pp. 32–41. [Google Scholar]
- Mohanty, H.; Mohanty, J.; Balakrishnan, A. Trends in Software Testing; Springer: Berlin/Heidelberg, Germany, 2017. [Google Scholar]
- Mahmood, R.; Esfahani, N.; Kacem, T.; Mirzaei, N.; Malek, S.; Stavrou, A. A whitebox approach for automated security testing of Android applications on the cloud. In Proceedings of the 7th International Workshop on Automation of Software Test, Zurich, Switzerland, 2–3 June 2012; pp. 22–28. [Google Scholar]
- Godefroid, P.; Kiezun, A.; Levin, M.Y. Grammar-based Whitebox Fuzzing. In Proceedings of the 29th ACM SIGPLAN Conference on Programming Language Design and Implementation, Tucson, AZ, USA, 7–13 June 2008; ACM: New York, NY, USA, 2008; pp. 206–215. [Google Scholar] [CrossRef]
- Edalat, E.; Sadeghiyan, B.; Ghassemi, F. ConsiDroid: A Concolic-based Tool for Detecting SQL Injection Vulnerability in Android Apps. arXiv 2018, arXiv:1811.10448. [Google Scholar]
- Majumdar, R.; Sen, K. Hybrid Concolic Testing. In Proceedings of the 29th International Conference on Software Engineering; IEEE Computer Society: Washington, DC, USA, 2007; pp. 416–426. [Google Scholar] [CrossRef]
- McMinn, P. Search-Based Software Testing: Past, Present and Future. In Proceedings of the 2011 IEEE Fourth International Conference on Software Testing, Verification and Validation Workshops, Berlin, Germany, 21–25 March 2011; IEEE Computer Society: Washington, DC, USA, 2011; pp. 153–163. [Google Scholar] [CrossRef]
- Rasthofer, S.; Arzt, S.; Bodden, E. A Machine-Learning Approach for Classifying and Categorizing Android Sources and Sinks. In Proceedings of the 2014 Network and Distributed System Security (NDSS) Symposium, NDSS 2014, San Diego, CA, USA, 23–26 February 2014. [Google Scholar]
- Ostorlab. Ostorlab - Continuous Mobile Application Security Testing. Available online: https://www.ostorlab.co/ (accessed on 12 October 2019).
- LinkedIn. Tool to Look for Several Security Related Android Application Vulnerabilities. Available online: https://github.com/linkedin/qark (accessed on 6 December 2018).
- Group, S.R. Soot—A Java Optimization Framework. Available online: https://github.com/Sable/soot (accessed on 20 November 2018).
- Acpm. Inspeckage: Android Package Inspector—Dynamic Analysis with Api Hooks, Start Unexported Activities and More. (Xposed Module). Available online: https://github.com/ac-pm/Inspeckage (accessed on 6 December 2018).
- Tungstwenty; Rovo89. Xposed Module Repository. 2014. Available online: https://repo.xposed.info/module/de.robv.android.xposed.installer (accessed on 12 October 2019).
- Tumbleson, C.; Wiśniewski, R. Apktool—A Tool for Reverse Engineering 3rd Party, Closed, Binary Android Apps. Available online: https://ibotpeaches.github.io/Apktool/ (accessed on 6 December 2018).
- Gruver, B. Smali: Smali/Baksmali. Available online: https://github.com/JesusFreke/smali (accessed on 6 December 2018).
- Deshotels, L.; Notani, V.; Lakhotia, A. DroidLegacy: Automated Familial Classification of Android Malware. In Proceedings of ACM SIGPLAN on Program Protection and Reverse Engineering Workshop, San Diego, CA, USA, 22–24 January 2014; ACM: New York, NY, USA, 2014; pp. 3:1–3:12. [Google Scholar] [CrossRef]
- Group, S.S.E. FlowDroid: FlowDroid Static Data Flow Tracker. Available online: https://github.com/secure-software-engineering/FlowDroid (accessed on 20 November 2018).
- Li, L. Soot-Infoflow-Android-Iccta: Inter-Component Communication Taint Analysis for Android. Available online: https://github.com/lilicoding/soot-infoflow-android-iccta (accessed on 6 December 2018).
- Flankerhqd. JAADAS: Joint Advanced Defect Assesment for Android Applications. Available online: https://github.com/flankerhqd/JAADAS (accessed on 6 December 2018).
- Androguard. Reverse Engineering, Malware and Goodware Analysis of Android Applications … and More (ninja !). Available online: https://github.com/androguard/androguard (accessed on 6 December 2018).
- Framework, M.S. MobSF. Available online: https://github.com/MobSF/Mobile-Security-Framework-MobSF (accessed on 6 December 2018).
- Au, K.W.Y.; Zhou, Y.F.; Huang, Z.; Lie, D. Pscout: Analyzing the android permission specification. In Proceedings of the 2012 ACM Conference on Computer and Communications Security, Raleigh, NC, USA, 16–18 October 2012; pp. 217–228. [Google Scholar]
- TACIXAT. CFGScanDroid: Control Flow Graph Scanning for Android. Available online: https://github.com/TACIXAT/CFGScanDroid (accessed on 6 December 2018).
- Li, L.; Bissyandé, T.F.; Octeau, D.; Klein, J. DroidRA: Taming Reflection to Support Whole-Program Analysis of Android Apps. In Proceedings of the The 2016 International Symposium on Software Testing and Analysis (ISSTA 2016), Saarbrücken, Germany, 18–20 July 2016. [Google Scholar]
- Maldroid. Maldrolyzer: Simple Framework to Extract “Actionable” Data from Android Malware (C&Cs, Phone Numbers etc.). Available online: https://github.com/maldroid/maldrolyzer (accessed on 6 December 2018).
- Merlo, A.; Georgiu, G.C. RiskInDroid: Machine Learning-Based Risk Analysis on Android. In Proceedings of the ICT Systems Security and Privacy Protection: 32nd IFIP TC 11 International Conference, SEC 2017, Rome, Italy, 29–31 May 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 538–552. [Google Scholar] [CrossRef] [Green Version]
- Debize, T. Androwarn: Yet Another Static Code Analyzer for Malicious Android Applications. Available online: https://github.com/maaaaz/androwarn (accessed on 6 December 2018).
- Rastogi, V.; Chen, Y.; Enck, W. AppsPlayground: Automatic security analysis of smartphone applications. In Proceedings of the third ACM conference on Data and Application Security and Privacy, San Antonio, TX, USA, 18–20 February 2013; pp. 209–220. [Google Scholar]
- XposedBridge. The Java Part of the Xposed Framework. Available online: https://github.com/rovo89/XposedBridge (accessed on 6 December 2018).
- Idanr. CuckooDroid—Automated Android Malware Analysis with Cuckoo Sandbox. Available online: https://github.com/idanr1986/cuckoo-droid (accessed on 6 December 2018).
- Sandbox, C. Automated Malware Analysis. Available online: https://cuckoosandbox.org/ (accessed on 6 December 2018).
- Developers, A. Apkanalyzer. Available online: https://developer.android.com/studio/command-line/apkanalyzer (accessed on 20 November 2018).
- Group, S.S.E. SuSi: SuSi—Our Tool to Automatically Discover Sources and Sinks in the Android Framework. Available online: https://github.com/secure-software-engineering/SuSi (accessed on 20 November 2018).
- Arzt, S.; Rasthofer, S.; Fritz, C.; Bodden, E.; Bartel, A.; Klein, J.; Le Traon, Y.; Octeau, D.; McDaniel, P. Flowdroid: Precise Context, Flow, Field, Object-Sensitive and Lifecycle-Aware Taint Analysis for Android Apps; ACM Sigplan Notices; ACM: New York, NY, USA, 2014; Volume 49, pp. 259–269. [Google Scholar]
- Reps, T.; Horwitz, S.; Sagiv, M. Precise interprocedural dataflow analysis via graph reachability. In Proceedings of the 22nd ACM SIGPLAN-SIGACT Symposium on Principles of Programming Languages, San Francisco, CA, USA, 23–25 January 1995; pp. 49–61. [Google Scholar]
- Bauereiß, T.; Greiner, S.; Herda, M.; Kirsten, M.; Li, X.; Mantel, H.; Mohr, M.; Perner, M.; Schneider, D.; Tasch, M. RIFL 1.1: A Common Specification Language for Information-Flow Requirements; Technical Report, Technical report TUD-CS-2017-0225; TU Darmstadt: Darmstadt, Germany, 2017. [Google Scholar]
- Gu, J.; Shen, S. CVE-2017-0780: Denial-of-Service Vulnerability Can Crash Android Messages App—TrendLabs Security Intelligence Blog, Mobile Threat Response Team. 2017. Available online: https://blog.trendmicro.com/trendlabs-security-intelligence/cve-2017-0780-denial-service-vulnerability-android-messages-app/ (accessed on 9 October 2019).
- HackingLoops. Android Exploitation Bypassing Android Permission Model. Available online: https://www.hackingloops.com/android-exploitation-bypassing-android-permission-model/ (accessed on 12 October 2019).
- Melamed, T. Hacking Android Apps Through Exposed Components. 2017. Available online: https://www.linkedin.com/pulse/hacking-android-apps-through-exposed-components-tal-melamed/ (accessed on 10 October 2019).
- Developers, A. Android Debug Bridge (adb). Available online: https://developer.android.com/studio/command-line/adb (accessed on 20 November 2018).
- Project, T.H. Droidbot: A Lightweight Test Input Generator for Android. Similar to Monkey, But with More Intelligence and Cool Features! Available online: https://github.com/honeynet/droidbot (accessed on 20 November 2018).
- Wikipedia. Strace. Available online: https://en.wikipedia.org/wiki/Strace (accessed on 20 November 2018).
- Fritz, C.; Arzt, S.; Rasthofer, S. DroidBench: A micro-Benchmark Suite to Assess the Stability of Taint-Analysis Tools for Android. Secure Software Engineering Group at Paderborn University and Fraunhofer IEM. Available online: https://github.com/secure-software-engineering/DroidBench (accessed on 8 October 2019).
| Feature | Tool(s) | Type | Covered |
|---|---|---|---|
| Reverse APK File and Flatten Classes | APKtool [24]/backsmali [25]/DroidLegacy [26] | Static | Yes |
| Detect Potential Leaks of Sensitive Information on Inter-Component and Intra-Component Data Flow | FlowDroid [27]/IccTA [28]/JAADAS [29] | Static | Yes |
| Improperly Protected Exported Components detection | QARK [20] | Static | Yes |
| Enable Backups Feature detection | QARK | Static | Yes |
| Debuggable App Mode detection | QARK | Static | Yes |
| Exported Activities and Services detection | QARK | Static | Yes |
| Information Gathering | Androguard [30]/Inspckage [22] | Static/Dynamic | Yes |
| Detect Native SSL Bypass | MobSF [31] | Static | |
| Detect Web-view SSL Bypass | MobSF | Static | |
| Detect Remote Web-view Debugging/Execution (Java Script) | MobSF/QARK | Static | |
| Detect Hard Coded Secrets | MobSF | Static | |
| Detect Root Detection | MobSF | Static | |
| Extracts the Permission Specification from Android OS | PSCout [32] | Static | |
| Comparing CFG Signatures to the Control Flow Graphs of Android Methods (For Detecting Malware) | CFGScanDroid [33] | Static | |
| Taming Reflection | DroidRA [34] | Static | |
| Extract “Actionable” Data from Android Malware | Madrolyzer [35] | Static | |
| Compute a Risk Value Based on Apps’ permissions | RiskInDroid [36] | Static | |
| API Misuse analysis | JAADAS | Static | |
| Local-Denial-of-Service analysis | JAADAS/Androwarn [37] | Static | |
| Bound Service Vulnerability detection | QARK | Static | |
| Content Provider Vulnerability detection | QARK | Static | |
| Static Tapjacking Mitigation detection | QARK | Static | |
| Improper SSL x.509 Certificate detection/validation | QARK | Static | |
| Notifying the Use of Sticky Intents | QARK | Static | |
| Weak/Improper Cryptography Use detection | QARK | Static | |
| Private Keys Embedded in the Source Code detection | QARK | Static | |
| Insecure Broadcast Intents detection | QARK | Static | |
| Insecurely Created Pending Intents detection | QARK | Static | |
| Outdated API Versions detection | QARK | Static | |
| Creation of World-Readable or World-Writeable Files detection | QARK | Static | |
| Fuzz Testing | AppsPlayGround [38] | Dynamic | Yes |
| Event Triggering | AppsPlayGround | Dynamic | Yes |
| Analyze Network Traffic | Inspckage | Dynamic | Yes |
| Insecure Network Requests (HTTP Requests) detection | - | Dynamic | Yes |
| Intent Crash detection | - | Dynamic | Yes |
| Method Hooking/Replacing | XposedBridge [39] | Dynamic | |
| Malware Sandboxing | cuckooDroid [40]/cuckoo sandbox [41] | Dynamic | |
| Track Privacy-Sensitive Information Leakage | AppsPlayGround | Dynamic | |
| Sensitive API monitoring | AppsPlayGround | Dynamic | |
| Intelligent UI execution | AppsPlayGround | Dynamic | |
| Prevent Sandbox detection | AppsPlayGround/cuckooDroid | Dynamic | |
| Kernel Level monitoring | AppsPlayGround | Dynamic | |
| Perform a Combination of Symoblic and Concrete Execution on the Application | ConDroid | Dynamic |
| Sources APIs Categories | Sinks APIs Categories |
|---|---|
| NETWORK_INFORMATION | NETWORK |
| LOCATION_INFORMATION | SMS |
| UNIQUE_IDENTIFIER | LOG |
| MICROPHONE | FILE |
| BLUETOOTH_INFORMATION | APPLICATION |
| FILE_INFORMATION | |
| CALENDAR_INFORMATION | |
| BROWSER_INFORMATION | |
| ACCOUNT_INFORMATION | |
| SYSTEM_SETTINGS | |
| APPLICATION |
| Vulnerability | Vulnerability Security Risk | Impact on User/App | Overall |
|---|---|---|---|
| Insecure Network Request | High | Medium | High |
| Information Leak | Low | Medium | Medium |
| Intent Crashes | High | High | High |
| Debug Flag | High | Medium | High |
| Exported Components | Low | Low | Low |
| Back-up Flag | Medium | Low | Low |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Amin, A.; Eldessouki, A.; Magdy, M.T.; Abdeen, N.; Hindy, H.; Hegazy, I. AndroShield: Automated Android Applications Vulnerability Detection, a Hybrid Static and Dynamic Analysis Approach. Information 2019, 10, 326. https://doi.org/10.3390/info10100326
Amin A, Eldessouki A, Magdy MT, Abdeen N, Hindy H, Hegazy I. AndroShield: Automated Android Applications Vulnerability Detection, a Hybrid Static and Dynamic Analysis Approach. Information. 2019; 10(10):326. https://doi.org/10.3390/info10100326
Chicago/Turabian StyleAmin, Amr, Amgad Eldessouki, Menna Tullah Magdy, Nouran Abdeen, Hanan Hindy, and Islam Hegazy. 2019. "AndroShield: Automated Android Applications Vulnerability Detection, a Hybrid Static and Dynamic Analysis Approach" Information 10, no. 10: 326. https://doi.org/10.3390/info10100326
APA StyleAmin, A., Eldessouki, A., Magdy, M. T., Abdeen, N., Hindy, H., & Hegazy, I. (2019). AndroShield: Automated Android Applications Vulnerability Detection, a Hybrid Static and Dynamic Analysis Approach. Information, 10(10), 326. https://doi.org/10.3390/info10100326






