Strategizing Artificial Intelligence Transformation in Smart Ports: Lessons from Busan’s Resilient AI Governance Model
Abstract
1. Introduction
1.1. Background
1.2. Aim of Current Study
1.3. Research Gap Analysis
2. Theory and Method
2.1. Conceptualizing AX in Container Terminals
2.2. Case Observations of Global AI Adoption in Container Terminals
2.3. Theoretical Integration of Resilience and Social Control for Sustainable AX
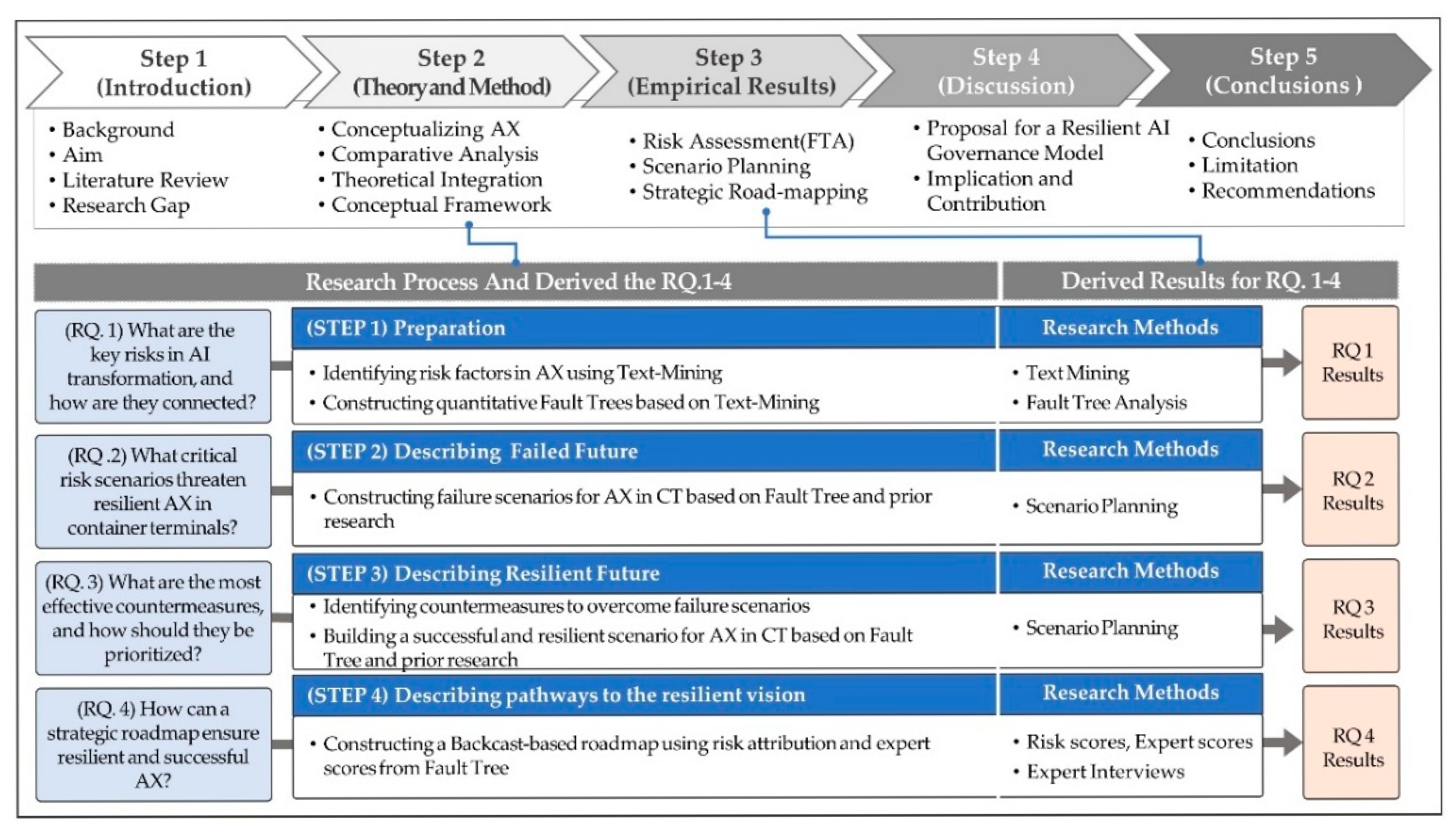
2.4. Methodological and Conceptual Framework
2.4.1. Macro Perspective: Backcasting-Based Research Design
2.4.2. Micro Perspective: Text Mining and Fault Tree Analysis
2.4.3. Analytical Framework of Current Study
- (1)
- We adopted text mining as a research method because the operation and management of container terminals are characterized by the complex and dynamic interconnectedness of various factors, and meaningful risk factors must be objectively derived from a wide range of unstructured data. Text mining is considered a suitable methodology for extracting keywords from significant amounts of data and for identifying correlations between risk factors [51,52]. Additionally, relying solely on the subjective views of experts may cause key risk factors to be overlooked or biased. Therefore, this study quantitatively analyzes potential risk factors related to AX via data-driven analysis. Specifically, NetMiner (version 4.5.1) [56] was used in this study to perform preprocessing and network analysis for text-mining analysis. NetMiner is a software that specializes in unstructured text analysis and social-network analysis. It is a text-mining analysis program used extensively by researchers as it features a Python-based scripting engine that is highly accessible and allows programmatic implementation.
- (2)
- We adopted the FTA as a research method because this study required a systematic analysis of the structural relationships between individual elements, as well as a logical understanding of the system vulnerabilities as a whole, instead of merely a list of the identified risk factors. Because hazards in complex systems do not exert their effects independently but are interconnected to form risk pathways, FTA allows for a systematic modeling of the overall system risk by structuring failure scenarios and tracing the logical paths contributing to major top events [53]. This process extends beyond enumerative risk identification and contributes to the clarification of prioritized response areas for resilience strategy formulation. Additionally, we used Microsoft Office Excel 2016 and Python 3.12.3 to calculate a series of probability statistics for FTA construction.
- (3)
- We adopted the backcasting approach as establishing effective flexible strategies based on current forecasting alone is impossible amid the rapid technological paradigm shift in AI and the uncertainty in the global logistics supply chain. Backcasting involves setting a desired future state, i.e., “resilient AX of domestic container terminals,” as a goal and then tracing the strategic path required to realize the goal backward from the present [46].
- (RQ. 1) What are the key risk factors and relationships identified during the AI paradigm shift?
- (RQ. 2) What are the key risk scenarios that can threaten the resilient AI paradigm shift of container-terminal organizations?
- (RQ. 3) What are the effective countermeasures to overcome the identified risks and scenarios, and how can they be prioritized for implementation?
- (RQ. 4) What strategic backcasting-based execution roadmap can be designed to realize a resilient AI paradigm shift?
3. Empirical Results
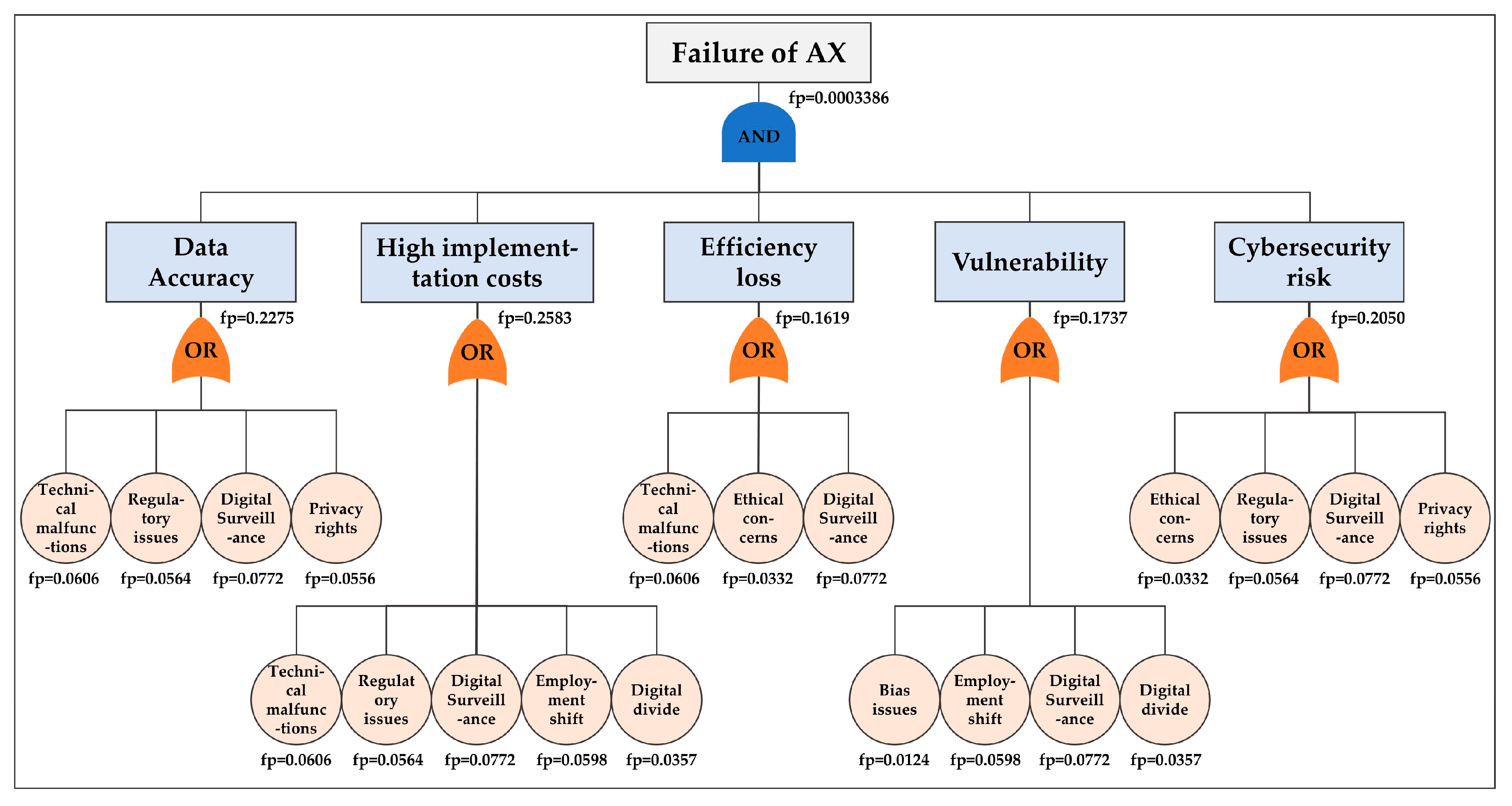
3.1. Risk Assessment: FTA of AX Failures
- (1)
- We set “failure of AX” as the top-level event. Intermediate events were derived by analyzing degree, betweenness, and eigenvector centrality indicators for the 13 core risk factors identified in advance. Centrality analysis was performed to measure the strength of connections between nodes, the degree of intermediary roles in the network, and the degree of closeness to influential nodes. Based on the analysis, five items were identified as intermediate events: data accuracy, high implementation costs, efficiency loss, vulnerability, and cybersecurity risk. The remaining eight items were categorized as primary events (Table 3). The basic events constituted the actual risk occurrence units, and each intermediate event was organized as a set of basic events based on semantic association.
- (2)
- We used the results of co-occurrence frequency analysis between keywords to set the gate types. Specifically, keyword combinations with a co-occurrence frequency exceeding 30 were set as AND gates, and those with fewer than 30 were set as OR gates. For example, keyword combinations such as (data accuracy–efficiency Loss), (data accuracy–high implementation costs), (data accuracy–technical malfunctions), (data accuracy–vulnerability), (data accuracy–digital surveillance), and (efficiency loss–high implementation costs) were connected by an AND gate. Based on these criteria, all intermediate and primary events were organized as AND and OR gates, respectively.
- (3)
- We quantitatively analyzed the constructed fault-tree structure. Specifically, we estimated the occurrence probability of each basic event and then performed failure-contribution analysis. The probability of occurrence was estimated using the results of text-mining analysis to calculate the percentage of document occurrence for each basic event. These probability values were calculated based on the frequency of occurrence of key risk factors within the literature-based unstructured data obtained in this study and were used as the basis for the quantitative defect-tree analysis.
3.2. Scenario Planning: Failure and Success Futures
3.2.1. Envisioning a Failed-AX Future
- The scenario in which AI systems cause data-accuracy problems is as follows: The AI system may fail to accurately obtain data pertaining to cargo stowage, vessel arrival, and departure management because of technical issues [59,60]. Consequently, the sensor signals are incomplete and server instability issues occur, thus resulting in the accumulation of database errors. Subsequently, the surveillance system (digital surveillance) cannot distinguish between normal and error data; moreover, it automatically executes incorrect unloading commands [61], and the lack of a recovery system causes errors in the cascade. Additionally, AI systems obtain additional personal information and terminal user logs during the recovery process, which results in privacy-rights issues [11]. Consequently, shipowners, shippers, and port workers lose confidence in AI systems, terminal unions demand operational overhauls, and port regulators impose sanctions owing to data accuracy and bias issues (Regulatory Issues) [62]. Eventually, AI-based operating systems will collapse, and terminals will be at risk of reverting to conventional manual operations.
- A scenario exists in which AI systems exacerbate the problem of high implementation costs. The system incurs significant fixed and variable costs in performing terminal automation, AGV operation, and IoT infrastructure deployment [63,64]. Additionally, the difficulty in securing high-level digital professionals reduces system reliability, thus resulting in delays and failures in the introduction of AI systems, particularly in small- and medium-sized ports. Consequently, AX is centered on large-hub container terminals, whereas small- and medium-sized ports are not considered for AX, thus widening the digital divide. Simultaneously, AI systems promote human-resource redeployment and employment shifts, whereas intensified data surveillance causes ethical issues and regulatory uncertainties, thus decelerating the overall momentum of AX.
- Scenarios exist where AI systems cause operational inefficiencies, including insufficiently trained or unoptimized AI systems that result in frequent errors in core port operations such as ship scheduling, stevedoring, and yard operation optimization [65,66,67]. Consequently, the vessel waiting time increases, the overall operational productivity of terminals decreases, and the global logistics flows are severely disrupted. Additionally, excessive data acquisition increases transmission delays and exposure to hacking, while AI systems fail to clarify accountability in the decision-making process, thus resulting in a decline in organizational trust and increased conflict among stakeholders.
- AI systems are vulnerable to adversarial cyberattacks and high-dimensional data distortion [68], particularly when biased algorithms are applied, which can adversely affect a particular shipper or shipping company [69]. Such biases can severely undermine system-wide reliability, and cybersecurity vulnerabilities in the digital surveillance-based infrastructure can cause cascading damage, including logistics data breaches, terminal system paralysis, and cargo transportation delays. Additionally, AI systems pose a greater risk of causing worker displacement, widening the digital divide between regions, and spreading social resistance [63,70].
- Scenarios exist in which AI systems increase cybersecurity risk. Systems obtain and process sensitive information such as maritime, cargo, and ship-location data on a large scale, thus rendering them prime targets for hackers [9,10]. Information obtained through digital surveillance systems is exposed to external hacking attacks, and attacks that exploit vulnerabilities in AI systems are common [71]. Additionally, the lack of privacy regulations exacerbates institutional imbalances [72], and the lack of accountability in AI decision-making processes results in confidence loss toward shipping companies, shippers, and logistics companies, which severely threatens the sustainability of AX in container terminals.
3.2.2. Envisioning a Resilient Future for AX
- The strategic scenario for AI systems to overcome the issue of data accuracy is as follows: AI systems operate reliably based on standardized structures and automatic recovery capabilities. This involves real-time error detection and redundant designs that proactively prevent data-quality degradation in the data exchanged between ports and ships, ship-to-ship logistics, port-to-shore logistics, and ship-to-shore logistics. Digital surveillance systems have shifted to a privacy-centric design, thus minimizing the acquisition of sensitive information and resolving privacy-related conflicts through coordination within a governance framework through the participation of various stakeholders. AI systems institutionalize data authentication and audit procedures to gain trust from internal and external stakeholders, which consequently enhances the reliability and sustainability of smart-port operations.
- The strategic scenario for AI systems to overcome the issue of high implementation costs is as follows: The system attracts strategic investments and subsidy support from local governments to ease the burden of initial implementation costs and optimizes the fixed cost structure by jointly utilizing infrastructure among small- and medium-sized ports. Workers engaged in conventional port stevedoring will be transformed into digitally applied professionals through AI-driven retraining and job-transformation programs. Additionally, container-terminal operators and logistics companies can promptly implement AI infrastructure and facility investments based on clear legal and institutional guidelines. This systematic approach will enable AX to expand not only to large ports but also to small- and medium-sized ports, thus reducing digital inequality in the port industry.
- The strategic scenario for AI systems to overcome operational inefficiency losses is as follows: AI models make accurate and rapid decisions through high-quality data-driven learning and recover from errors without cascading delays using automatic recovery and redundancy schemes. Surveillance systems actively adopt permission-based access, encryption, and anonymization technologies to protect privacy and ensure social acceptance. Simultaneously, the AI-integrated management platform is utilized to monitor operations and improve problems based on ethical standards and accountability systems, thereby increasing the efficiency and reliability of digital port operations.
- The strategic scenario for AI systems to overcome the issue of system vulnerability is as follows: The AI system internalizes a multireview algorithmic structure and an ethics-based decision-making system to prevent biased algorithms, whereas the cybersecurity system enhances threat detection, security authentication, and anonymous data-processing technologies to support continuous and reliable port operations. Additionally, port workers adapt proactively to AI systems through job transformation and capacity-building programs, thus reducing labor unrest and resistance. Digital-infrastructure subsidies and transition deferral schemes for small- and medium-sized ports supported by national and public authorities have been realized to promote equity and resilience during the nationwide AI transition.
- The strategic scenario for AI systems to overcome cybersecurity risks is as follows: AI systems adopt “security by design” from the beginning of their development, thus internalizing privacy and access control policies. All data obtained are anonymized and encrypted to prevent leakage and misuse, and surveillance systems are securely operated based on a policy-based design and ethical evaluation criteria. Real-time intrusion detection and response systems are implemented to respond promptly to external cyberattacks, and regulatory agencies are constantly updating AI cybersecurity technology standards to strengthen corporate security certification and accountability structures. Additionally, the AI-integrated management platform prevents ethical risks through internal and external monitoring, thus enabling container-terminal companies to establish a world-class AI-based port-operation system characterized by safety, reliability, and accountability.
3.3. Roadmap: Strategic Roadmapping Toward a Resilient Future
3.3.1. Prioritization of Strategic Measures and Roadmap Structuring
3.3.2. Strategic Roadmap for Resilient AI Paradigm Shift in Container-Terminal Operations
- (1)
- The short-term strategy aims to initially stabilize the AI system. Privacy-protection and data-management systems should be established urgently, such that AI systems in container terminals can operate reliably and securely. Additionally, a multilayered cybersecurity certification system that considers the specificities of container-terminal operations must be introduced to ensure system security and reliability. Furthermore, cybersecurity budgets must be secured proactively from the early stages, and research and development (R&D) must be conducted on security solutions to strengthen long-term stability. These measures minimize the risks that may arise in the early development stages of AI systems and serve as a foundation for stable digital operations.
- (2)
- The medium-term strategy aims to optimize AI systems and establish a foundation for human–AI collaboration. AI systems must improve their prediction accuracy and operational efficiency through continuous learning and algorithm optimization based on high-quality data, as well as secure the ability to detect system errors early and respond promptly via a real-time monitoring system. Additionally, a collaborative process between humans and AI systems should be designed to enable flexible responses to unpredictable situations, and an integrated risk-management system should be established in advance to analyze and manage the ethical and social risks that may arise in the AI decision-making process. Moreover, an integrated AI management platform with an independent review system should be introduced to ensure the balance and ethics of AI system operations, and digital human rights and ethical standards should be strengthened to secure the trust of stakeholders.
- (3)
- The long-term strategy aims to complete the AI paradigm shift in the port logistics industry based on AI systems and secure leading competitiveness in the global market. To achieve this, one must optimize the integration between the existing port operation and AI systems as well as strengthen scalability and connectivity via standardization and a database (DB) management system. Additionally, one must minimize system operation risks by establishing automatic recovery functions and redundant infrastructure (cloud-on-premises integration) when errors occur in AI systems. For example, cooperation between the Ministry of Oceans and Fisheries (government), the port authority, and private container-terminal operators should be encouraged to provide continuous financial support for AI infrastructure. Legal frameworks should be established to support the spread of AI technology across industries, and financial risk-management systems should be established through third-party certification of AI systems and insurance systems for unexpected risks.
4. Discussion
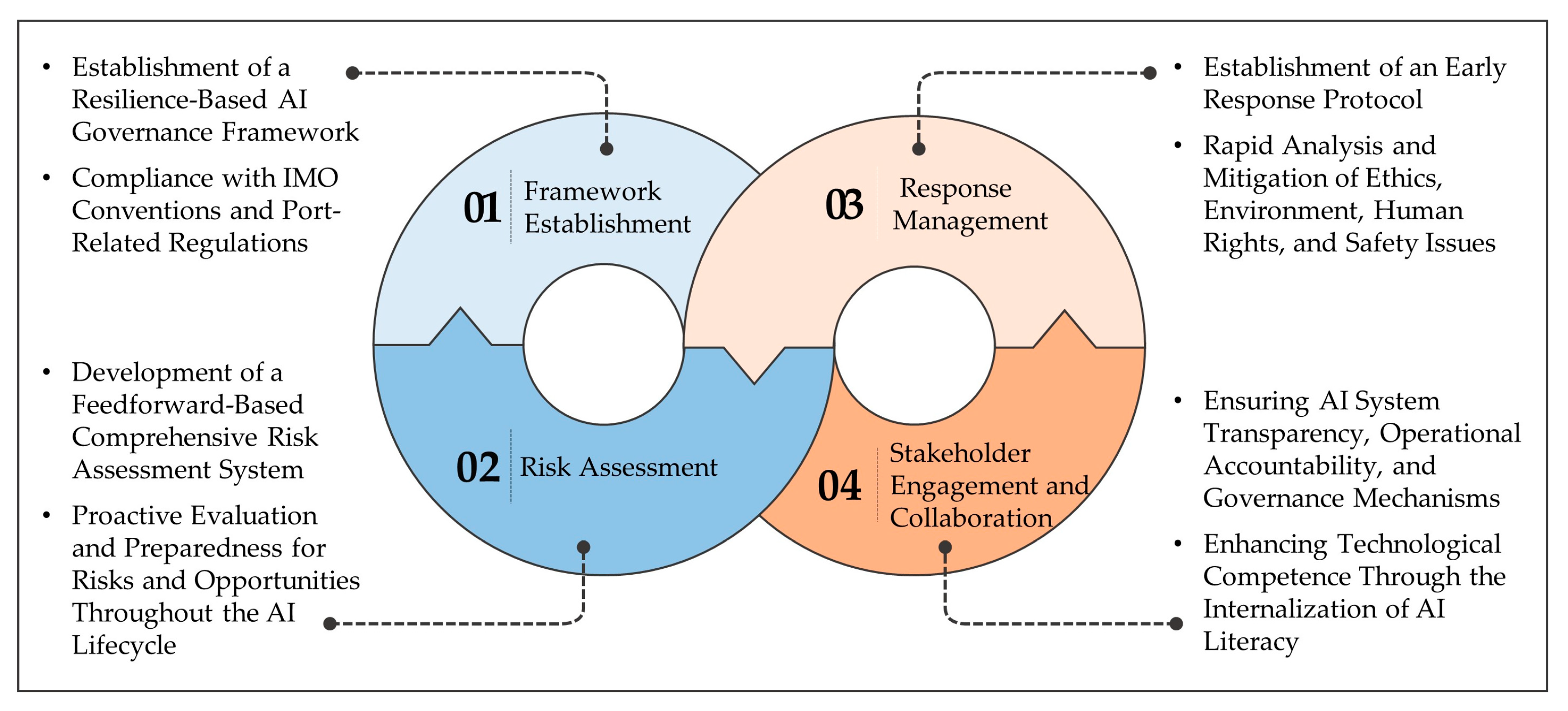
4.1. Proposal for Resilient AI Governance Model and Its Organizational Role
- (1)
- Domestic container-terminal companies should establish an AX management system based on compliance and policy responses that faithfully reflect the regulations of the International Maritime Organization (IMO) and global technical standards. This includes the IMO’s MASS Regulatory Scoping Exercise, the EU’s AI Act and Data Act, and each country’s maritime and privacy laws (e.g., GDPR). Additionally, key international and national laws and policies, such as the EU AI Act and Data Act, national maritime laws, privacy laws (GDPR), and the IMO Cyber Risk Management Guidelines, should be proactively integrated and reflected to help container-terminal companies proactively identify and prevent legal risks that may arise during their AI paradigm shift to ensure global regulatory responsiveness and system reliability. The AI governance system should ensure institutional consistency and global acceptance of the AI paradigm shift by simultaneously strengthening the regulatory-monitoring system, policy-response protocols, and external cooperation channels to respond actively to the changing policy environment.
- (2)
- Domestic container-terminal companies should establish a feedforward-based all-around AX risk assessment system to predict and respond to potential risks that may arise when implementing strategic tasks based on AI governance. AI systems should repeatedly and systematically evaluate risk factors at every stage of port-logistics management, vessel scheduling, cargo handling, and system maintenance, and establish preemptive response strategies through maritime data-based risk modeling. In particular, they should establish a risk-management system based on an integrated AI platform that integrates real-time maritime data acquisition, analysis, and prediction capabilities to detect and prevent system failures, cyberattacks, and ethical issues at an early stage.
- (3)
- Under the AI governance system, container-terminal companies should establish a proactive early-response system to respond promptly to ethical, human-rights, environmental, and safety issues that may arise during the AI paradigm shift. The early-response system should apply a machine-learning-based early-warning system to detect abnormalities in real time and activate various scenario-based response manuals based on success and failure to prevent the proliferation of problems. Additionally, by accumulating and analyzing recurring errors and risk data to continuously optimize response protocols, the system should strengthen both resilience and sustainability during the AI paradigm shift.
- (4)
- Container-terminal companies should establish an operating system based on transparency and accountability to establish an AI governance system. The progress of the AI paradigm shift, the manner in which maritime data are utilized, and key decision-making procedures should be clearly disclosed to all stakeholders, and the relevant parties should be clearly defined for each step of the implementation. Additionally, AI literacy should be internalized as an essential competency for all employees, from the CEO of the container terminal to on-site managers and operators. The strategic goals of AX should be communicated and practiced throughout the organization via systematic education and training.
4.2. Implications and Contributions
- (1)
- This study defined the AI paradigm shift of domestic container-terminal companies as a process that fundamentally reorganizes the entire strategy, structure, operation system, and human resource management, instead of merely adopting technology. In particular, it emphasized that the AI system transforms the entire process of port operation into a data-based decision-making system and that container-terminal companies must simultaneously innovate not only the technological infrastructure but also the organizational culture, leadership, and decision-making methods.
- (2)
- This study revealed that establishing a resilience-based strategy is essential for responding to various risks and uncertainties that may inevitably arise during the AI paradigm shift. Unlike the DX phase, the AI paradigm shift can continuously generate complex and dynamic risk factors (e.g., cybersecurity threats, algorithm bias, and system errors). This implies the necessity to develop a resilience-centered response system with preemptive risk detection and recovery capabilities.
- (3)
- A resilience-based AI governance system was designed in this study, which is necessary to successfully promote AI transition, thus differentiating this study from previous ones. A global regulatory response system that integrates social control and new governance theories should be developed to internally strengthen ethics and accountability, as well as to externally comply with the IMO’s Autonomous Ship Regulatory Framework (MASS RSE), the EU AI Act and Data Act, the GDPR, and the IMO Cyber Risk Management Guidelines.
- (4)
- This study emphasized that the AI paradigm shift is not limited to technological innovation but requires fundamental changes in organizational culture and mindset. Container-terminal companies should minimize resistance to organizational transformation and maximize acceptance by implementing a strategy for internalizing AI literacy at the company-wide level, learning from successes and failures through initial pilot projects, and then gradually imparting the knowledge gained throughout the organization.
- (5)
- This study proposed a method to overcome the limitations of the existing feedback-centered post-response system and integrated a feedforward-based predictive risk management system into an AI transformation strategy. In particular, a structure was systemized to detect and prevent possible failures in an AI system in advance through real-time data analysis, an early-warning system was established, and a predictive maintenance system was introduced.
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Kop, M. Shaping the Law of AI: Transatlantic Perspectives. Stanford-Vienna Transatlantic Technology Law Forum, 2020. TTLF Working Papers. Available online: https://law.stanford.edu/publications/no-65-shaping-the-law-of-ai-transatlantic-perspectives/ (accessed on 15 January 2025).
- Pathak, M. Data Governance Redefined: The Evolution of EU Data Regulations from the GDPR to the DMA, DSA, DGA, Data Act and AI Act. 2024. Available online: https://edpl.lexxion.eu/article/EDPL/2024/1/8 (accessed on 15 January 2025).
- Global Maritime Trends Barometer. Lloyd’s Register. 2025. Available online: https://www.lr.org/en/knowledge/research/global-maritime-trends/ (accessed on 15 January 2025).
- Peretz-Andersson, E.; Torkar, R. Empirical AI transformation research: A systematic mapping study and future agenda. E-Inform. Softw. Eng. J. 2022, 16, 220108. [Google Scholar] [CrossRef]
- Nguyen, H.-S.; Huynh, C.-D.; Bui, N.-Q. Digital transformation for shipping container terminals using automated container code recognition. TELKOMNIKA 2023, 21, 535–544. [Google Scholar] [CrossRef]
- Safuan, S.; Syafira, A. Artificial Intelligence in Indonesian Ports: Opportunities and Challenges. Trans. Marit. Sci. 2024, 13, 1–17. [Google Scholar] [CrossRef]
- He, X.; Hu, W.; Li, W.; Hu, R. Digital transformation, technological innovation, and operational resilience of port firms in case of supply chain disruption. Mar. Pollut. Bull. 2023, 190, 114811. [Google Scholar] [CrossRef]
- Ren, X.; Shen, J.; Feng, Z.; Wang, X.; An, K. The Impact of Digital Development on Port Security Resilience—An Empirical Study from Chinese Provinces. Sustainability 2024, 16, 2385. [Google Scholar] [CrossRef]
- Samonte, M.J.C.; Laurenio, E.N.B.; Lazaro, J.R.M. Enhancing Port and Maritime Cybersecurity Through AI-Enabled Threat Detection and Response. In Proceedings of the 2024 8th International Conference on Smart Grid and Smart Cities (ICSGSC), Shanghai, China, 25–27 October 2024; pp. 412–420. [Google Scholar]
- Ilieva, R.; Stoilova, G. Challenges of AI-Driven Cybersecurity. In Proceedings of the 2024 XXXIII International Scientific Conference Electronics (ET), Sozopol, Bulgaria, 17–19 September 2024; pp. 1–4. [Google Scholar]
- Cadet, E.; Osundare, O.S.; Ekpobimi, H.O.; Samira, Z.; Wondaferew, Y. AI-powered threat detection in surveillance systems: A real-time data processing framework. Open Access Res. J. Eng. Technol. 2024, 7, 31–45. [Google Scholar] [CrossRef]
- Chang, W.; Li, N.; Zhao, Y. Resilience of regional container port network: Based on projection correlation and dynamic spatial Markov Chain. Marit. Policy Manag. 2024, 52, 764–780. [Google Scholar] [CrossRef]
- Bawa, Z.; Rathore, K.S. Corporate Governance in the Era of Digital Transformation: Evaluating the Impact of Emerging Technologies on Organizational Strategies. Bus. Mark. Financ. Open 2024, 1, 46–63. [Google Scholar]
- De Haes, S.; Caluwe, L.; Huygh, T.; Joshi, A. Governing Digital Transformation: Guidance for Corporate Board Members; Management for Professionals; Springer International Publishing: Cham, Switzerland, 2020; ISBN 978-3-030-30266-5. [Google Scholar]
- Liu, Q.; Liu, J.; Gong, C. Digital transformation and corporate innovation: A factor input perspective. Manag. Decis. Econ. 2023, 44, 2159–2174. [Google Scholar] [CrossRef]
- Korachi, Z.; Bounabat, B. Integrated methodological framework for digital transformation strategy building (IMFDS). Int. J. Adv. Comput. Sci. Appl. 2019, 10, 242–250. [Google Scholar] [CrossRef]
- Korachi, Z.; Bounabat, B. General approach for formulating a digital transformation strategy. J. Comput. Sci. 2020, 16, 493–507. [Google Scholar]
- Gong, C.; Ribiere, V. Developing a unified definition of digital transformation. Technovation 2021, 102, 102217. [Google Scholar] [CrossRef]
- Sivasami, K.; Thangalakshmi, S.; Bhoite, A.; Soni, H.; Seth, K. Data Analysis and Artificial Intelligence in The Marine Sector. REST J. Data Anal. Artif. Intell. 2024, 3, 85–91. [Google Scholar] [CrossRef]
- Ceyhun, G.Ç. Recent Developments of Artificial Intelligence in Business Logistics: A Maritime Industry Case; Hacioglu, U., Ed.; Digital Business Strategies in Blockchain Ecosystems. Contributions to Management Science; Springer: Cham, Switzerland, 2020. [Google Scholar]
- Lawrence, H. State-of-the-Art Artificial Intelligence in the Port and Container Terminal Industry. Available online: https://portlogistics.akquinet.com/port-logistics-blog/blogpost-details/state-of-the-art-artificial-intelligence-in-the-port-and-container-terminal-industry (accessed on 22 May 2025).
- Lalla-Ruiz, E. Intelligent management of seaside logistic operations at maritime container terminals. 4OR-Q J Oper Res. 2017, 15, 217–218. [Google Scholar] [CrossRef]
- Knatz, G.; Notteboom, T.; Pallis, A.A. Container terminal automation: Revealing distinctive terminal characteristics and operating parameters. Marit. Econ. Logist. 2022, 24, 537. [Google Scholar] [CrossRef]
- Port of Tanjung Pelepas to use AI to Improve Efficiency and Optimise Scheduling—APM Terminals. Available online: https://www.apmterminals.com/en/news/news-releases/2022/220725-port-of-tanjung-pelepas-to-use-ai-to-improve-efficiency-and-optimise-scheduling (accessed on 22 May 2025).
- AI-powered auto gate system goes live in ATI’s Batangas Port. Available online: https://www.dpworld.com/news/releases/ai-powered-auto-gate-system-goes-live-in-atis-batangas-port/ (accessed on 15 January 2025).
- CMPort’s Green Port Development Strategy; International Association of Ports and Harbors (IAPH): Tokyo, Japan, 2020.
- Psa Unveils Sustainability Report and New Corporate Purpose (03/October/2019); PSA International: Singapore, 2019.
- Yoon, I. BPA, Operator of Busan Port, Shares Digital Transformation Achievements—Develops AI-Based Forecasting System. Available online: https://www.businesspost.co.kr/BP?command=article_view&num=348303 (accessed on 22 May 2025).
- Kosiek, J.; Kaizer, A.; Salomon, A.; Sacharko, A. Analysis of modern port technologies based on literature review. TransNav Int. J. Mar. Navig. Saf. Sea Transp. 2021, 15, 667–674. [Google Scholar] [CrossRef]
- APM Terminals Achieves Zero Box Tipping Incidents at Tangier Terminal Via AI Weather Prediction Tool—Container News. Available online: https://container-news.com/apm-terminals-achieves-zero-box-tipping-incidents-at-tangier-terminal-via-ai-weather-prediction-tool/ (accessed on 22 May 2025).
- PSA Singapore. PSA Innovates with OptETruck, a Digital Solution for Singapore’s Haulier Sector to Achieve Fleet Optimisation and a Greener Footprint. 2023. Available online: https://www.singaporepsa.com/2023/07/26/psa-innovates-with-optetruck-a-digital-solution-for-singapores-haulier-sector-to-achieve-fleet-optimisation-and-a-greener-footprint/ (accessed on 15 January 2025).
- DP WORLD. Leading ports and terminals tech solutions revealed at Expo 2020. Available online: https://www.dpworld.com/news/releases/leading-ports-terminals-tech-solutions-revealed-at-expo-2020/ (accessed on 15 January 2025).
- APM Terminals Maasvlakte II powers up for digital expansion. Available online: https://www.apmterminals.com/en/news/news-releases/2024/241025-maasvlakte-konecranes-order (accessed on 22 May 2025).
- DP World Yarımca Started Implementing ISO 27001. Available online: https://www.dpworld.com/en/turkiye/news/news/19dpworldiso27001 (accessed on 22 May 2025).
- PORTNET. Available online: https://www.portnet.com/public/home (accessed on 22 May 2025).
- China Merchants Port Group Co., Ltd. Interim Report 2024; China Merchants Port Group: Hongkong, China, 2024. [Google Scholar]
- Smith, D.; Fischbacher, M. The changing nature of risk and risk management: The challenge of borders, uncertainty and resilience. Risk Manag. 2009, 11, 1–12. [Google Scholar] [CrossRef]
- Liu, J.; Qi, Y.; Lyu, W. Port resilience in the post-COVID-19 era. Ocean. Coast. Manag. 2023, 238, 106565. [Google Scholar] [CrossRef]
- Zhou, C.; Xu, J.; Miller-Hooks, E.; Zhou, W.; Chen, C.-H.; Lee, L.H.; Chew, E.P.; Li, H. Analytics with digital-twinning: A decision support system for maintaining a resilient port. Decis. Support Syst. 2021, 143, 113496. [Google Scholar] [CrossRef]
- United Nations Sustainable Development Goals. Available online: https://www.undp.org/sustainable-development-goals (accessed on 22 May 2025).
- Ghazaleh, M.A. Smartening up ports digitalization with artificial intelligence (AI): A study of artificial intelligence business drivers of smart port digitalization. Manag. Econ. Rev. 2023, 8, 78–97. [Google Scholar] [CrossRef]
- Gerrero-Molina, M.-I.; Vásquez-Suárez, Y.-A.; Valdés-Mosquera, D.-M. Smart, green, and sustainable: Unveiling technological trajectories in maritime port operations. IEEE Access 2024, 12, 47713–47723. [Google Scholar] [CrossRef]
- O’reilly, C.A.; Chatman, J.A. Culture as social control: Corporations, cults, and commitment. Res. Organ. Behav. 1996, 18, 157–200. [Google Scholar]
- Son, H.-S. A Study on the Governance of the Intelligent Information Society by Digital Transformation. J. Civ. Eng. Build. Technol. 2021, 49, 199–230. [Google Scholar] [CrossRef]
- Quist, J.; Vergragt, P. Past and future of backcasting: The shift to stakeholder participation and a proposal for a methodological framework. Futures 2006, 38, 1027–1045. [Google Scholar] [CrossRef]
- Bibri, S.E.; Krogstie, J. Generating a vision for smart sustainable cities of the future: A scholarly backcasting approach. Eur. J. Futures Res. 2019, 7, 5. [Google Scholar] [CrossRef]
- Dreborg, K.H. Essence of backcasting. Futures 1996, 28, 813–828. [Google Scholar] [CrossRef]
- Quist, J. Backcasting for a Sustainable Future: The Impact After 10 Years; Eburon Uitgeverij BV: Utrecht, The Netherlands, 2007. [Google Scholar]
- Robèrt, K.-H.; Schmidt-Bleek, B.; De Larderel, J.A.; Basile, G.; Jansen, J.L.; Kuehr, R.; Thomas, P.P.; Suzuki, M.; Hawken, P.; Wackernagel, M. Strategic sustainable development—Selection, design and synergies of applied tools. J. Clean. Prod. 2002, 10, 197–214. [Google Scholar] [CrossRef]
- Kishita, Y.; McLellan, B.C.; Giurco, D.; Aoki, K.; Yoshizawa, G.; Handoh, I.C. Designing backcasting scenarios for resilient energy futures. Technol. Forecast. Soc. Change 2017, 124, 114–125. [Google Scholar] [CrossRef]
- Brown, D.E. Text mining the contributors to rail accidents. IEEE Trans. Intell. Transp. Syst. 2015, 17, 346–355. [Google Scholar] [CrossRef]
- Verma, A.; Maiti, J. Text-document clustering-based cause and effect analysis methodology for steel plant incident data. Int. J. Inj. Control Saf. Promot. 2018, 25, 416–426. [Google Scholar] [CrossRef]
- Stamatelatos, M.; Vesely, W.; Dugan, J.; Fragola, J.; Minarick, J.; Railsback, J. Fault Tree Handbook with Aerospace Applications; NASA: Washington DC, USA, 2002. [Google Scholar]
- Kabir, S. An overview of fault tree analysis and its application in model based dependability analysis. Expert Syst. Appl. 2017, 77, 114–135. [Google Scholar] [CrossRef]
- Jang, S.-M.; Park, M.-G. A Study on the Fault Analysis and Security Assessment for Smart Card Management System. J. Korea Multimed. Soc. 2014, 17, 52–59. [Google Scholar] [CrossRef][Green Version]
- NetMiner, Version 4.5.0. Available online: https://www.netminer.com/kr/ (accessed on 22 May 2025).
- Paraskevas, A.; Madas, M.; Zeimpekis, V.; Fouskas, K. Smart ports in industry 4.0: A systematic literature review. Logistics 2024, 8, 28. [Google Scholar] [CrossRef]
- Ruijters, E.; Stoelinga, M. Fault tree analysis: A survey of the state-of-the-art in modeling, analysis and tools. Comput. Sci. Rev. 2015, 15, 29–62. [Google Scholar] [CrossRef]
- Neretin, O.; Kharchenko, V.; Fesenko, H. Multi-source analysis of AI vulnerabilities: Methodology and algorithms of data collection. In Proceedings of the 2023 IEEE 12th International Conference on Intelligent Data Acquisition and Advanced Computing Systems: Technology and Applications (IDAACS), Dortmund, Germany, 7–9 September 2023; Volume 1, pp. 972–977. [Google Scholar]
- Li, Z.; Yi, W.; Chen, J. Accuracy of training data and model outputs in Generative AI: CREATe Response to the Information Commissioner Office Consultation. arXiv 2024, arXiv:2407.13072. [Google Scholar] [CrossRef]
- Bangad, N.; Jayaram, V.; Krishnappa, M.S.; Banarse, A.R.; Bidkar, D.M.; Nagpal, A.; Parlapalli, V. A Theoretical Framework for AI-driven data quality monitoring in high-volume data environments. Int. J. Comput. Eng. Technol. 2024, 15, 618–636. [Google Scholar] [CrossRef]
- Mallela, I.R.; Aravind, S.; Salunkhe, V.; Goel, P.; Tharan, O. Explainable AI for Compliance and Regulatory Models. Int. J. Res. Publ. Semin. 2024, 11, 319–339. [Google Scholar]
- Xu, H.; Liu, J.; Xu, X.; Chen, J.; Yue, X. The impact of AI technology adoption on operational decision-making in competitive heterogeneous ports. Transp. Res. Part E Logist. Transp. Rev. 2024, 183, 103428. [Google Scholar] [CrossRef]
- Amaugo, O. Impact of AI Adoption on Business Process Automation and Competitiveness in Manufacturing Industry in Nigeria. Int. J. Res. Innov. Soc. Sci. 2024, 8, 5321–5330. [Google Scholar] [CrossRef]
- Sun, C.; Tong, Q.; Yang, W.; Zhang, W. DiReDi: Distillation and Reverse Distillation for AIoT Applications. IEEE Open J. Comput. Soc. 2024, 5, 748–760. [Google Scholar] [CrossRef]
- Poudel, B.; Neloy, M.S.; Chirawu, A.M. Combat Efficiency and Effectiveness of AI-driven Multisensory Search-and-Destroy Agent. N. Am. Acad. Res. (NAAR) J. 2021, 4, 42–54. [Google Scholar]
- Ahrens, J.; Strufe, M.; Ahrens, L.; Schotten, H.D. An AI-driven Malfunction Detection Concept for NFV Instances in 5G. arXiv 2018. [Google Scholar] [CrossRef]
- Bortolussi, L.; Sanguinetti, G. Intrinsic Geometric Vulnerability of High-Dimensional Artificial Intelligence. arXiv 2019. [Google Scholar] [CrossRef]
- Abdulllah, S.M. Artificial intelligence (AI) and its associated ethical issues. ICR J. 2019, 10, 124–126. [Google Scholar] [CrossRef]
- Chang, P.-C.; Zhang, W.; Cai, Q.; Guo, H. Does AI-Driven Technostress Promote or Hinder Employees’ Artificial Intelligence Adoption Intention? A Moderated Mediation Model of Affective Reactions and Technical Self-Efficacy. Psychol. Res. Behav. Manag. 2024, 17, 413–427. [Google Scholar] [CrossRef] [PubMed]
- Shahana, A.; Hasan, R.; Farabi, S.F.; Akter, J.; Mahmud, M.A.A.; Johora, F.T.; Suzer, G. AI-driven cybersecurity: Balancing advancements and safeguards. J. Comput. Sci. Technol. Stud. 2024, 6, 76–85. [Google Scholar] [CrossRef]
- Bocayuva, M. Cybersecurity in the European Union port sector in light of the digital transformation and the COVID-19 pandemic. WMU J. Marit. Aff. 2021, 20, 173–192. [Google Scholar] [CrossRef]
- Yossi, S. The Multi-Faceted Threat of Single-Point Failures. Available online: https://www.linkedin.com/pulse/multi-faceted-threat-single-point-failures-yossi-sheffi-3v7ie (accessed on 21 May 2025).

| Operator | Country | Technology | Policy and Strategy | Education |
|---|---|---|---|---|
| APM Terminal | Denmark |
|
|
|
| DP World | Dubai |
|
|
|
| PSA International | Singapore |
|
|
|
| China Merchant Port | China |
|
|
|
| Dongwon Global Container, Busan | Korea |
|
|
|
| No. | Source | Target | Weight | Rank |
|---|---|---|---|---|
| 1 | AI | Data accuracy | 406 | 6 |
| 2 | AI | Employment shift | 405 | 7 |
| 3 | AI | High implementation costs | 270 | 12 |
| 4 | AI | Efficiency loss | 134 | 19 |
| 5 | AI | Cybersecurity risk | 125 | 22 |
| 6 | AI | Regulatory issues | 107 | 27 |
| 7 | AI | Vulnerability | 106 | 28 |
| 8 | AI | Digital surveillance | 91 | 32 |
| 9 | AI | Ethical concerns | 84 | 36 |
| 10 | AI | Privacy rights | 79 | 37 |
| 11 | AI | Technical malfunctions | 74 | 44 |
| 12 | AI | Digital divide | 71 | 49 |
| 13 | AI | Bias issues | 58 | 72 |
| Keyword | Event Type | Frequency of Occurrence | Total Number of Documents | Fault Probability (FP) | Birnbaum Importance |
|---|---|---|---|---|---|
| Failure of AX | Top event | - | - | 0.0003386 | - |
| Data accuracy | Intermediate event | 316 | 1205 | 0.262 | - |
| High implementation costs | Intermediate event | 172 | 1205 | 0.143 | - |
| Efficiency loss | Intermediate event | 136 | 1205 | 0.113 | - |
| Vulnerability | Intermediate event | 107 | 1205 | 0.089 | - |
| Cybersecurity risk | Intermediate event | 83 | 1205 | 0.069 | - |
| Digital surveillance | Basic event | 93 | 1205 | 0.077 | 0.00804 |
| Employment shift | Basic event | 72 | 1205 | 0.060 | 0.00280 |
| Technical malfunctions | Basic event | 73 | 1205 | 0.061 | 0.00429 |
| Regulatory issues | Basic event | 68 | 1205 | 0.056 | 0.00377 |
| Privacy rights | Basic event | 67 | 1205 | 0.056 | 0.00266 |
| Digital divide | Basic event | 43 | 1205 | 0.036 | 0.00273 |
| Ethical concerns | Basic event | 40 | 1205 | 0.033 | 0.00325 |
| Bias issues | Basic event | 15 | 1205 | 0.012 | 0.00163 |
| No. | Strategy | R | A | Score | Step | ||
|---|---|---|---|---|---|---|---|
| 1 | Establish privacy-protection and data-management systems | 0.008 | 3.774 | 1 | 1 | 1 | Short |
| 2 | Strengthen cybersecurity certification system for port terminals | 0.005 | 3.698 | 0.614 | 0.889 | 0.751 | Short |
| 3 | Strengthen R&D for cybersecurity solutions | 0.008 | 3.415 | 1 | 0.472 | 0.736 | Short |
| 4 | Secure initial cybersecurity budget | 0.008 | 3.34 | 1 | 0.361 | 0.681 | Short |
| 5 | Design AI–human cooperation process | 0.004 | 3.642 | 0.355 | 0.806 | 0.58 | Middle |
| 6 | Establish a red-team organization to balance decision making | 0.002 | 3.717 | 0.196 | 0.917 | 0.556 | Middle |
| 7 | Monitor AI systems in real time | 0.004 | 3.528 | 0.462 | 0.639 | 0.551 | Middle |
| 8 | Introduce AI-algorithm optimization system | 0.004 | 3.528 | 0.462 | 0.639 | 0.551 | Middle |
| 9 | Expand in-house training opportunities to internalize new technologies | 0.003 | 3.623 | 0.248 | 0.778 | 0.513 | Middle |
| 10 | Establish a strategy for phased introduction of AI systems | 0.003 | 3.623 | 0.238 | 0.778 | 0.508 | Middle |
| 11 | Activate existing workforce reassignment and job-transition programs | 0.003 | 3.566 | 0.248 | 0.694 | 0.471 | Middle |
| 12 | Introduce AI-risk (human rights, safety, security, etc.) analysis system | 0.003 | 3.528 | 0.27 | 0.639 | 0.454 | Middle |
| 13 | Perform quality control and optimization for AI decision making | 0.004 | 3.396 | 0.462 | 0.444 | 0.453 | Middle |
| 14 | Establish AI human-rights impact assessments and ethical guidelines | 0.003 | 3.547 | 0.217 | 0.667 | 0.442 | Middle |
| 15 | Enhance transparency of AI governance activities and expand stakeholder engagement | 0.003 | 3.472 | 0.312 | 0.556 | 0.434 | Middle |
| 16 | Introduce AI-related insurance and third-party certification systems | 0.004 | 3.321 | 0.388 | 0.333 | 0.361 | Long |
| 17 | Analyze AI-related legal systems | 0.004 | 3.302 | 0.388 | 0.306 | 0.347 | Long |
| 18 | Optimize the integration of AI systems with existing systems | 0.003 | 3.396 | 0.238 | 0.444 | 0.341 | Long |
| 19 | Perform AI-based system standardization and DB management | 0.001 | 3.491 | 0 | 0.583 | 0.292 | Long |
| 20 | Manage automatic AI error recovery and redundant systems | 0.004 | 3.151 | 0.462 | 0.083 | 0.273 | Long |
| 21 | Activate infrastructure investment attraction (establishment of funds, funds, etc.) | 0.003 | 3.283 | 0.238 | 0.278 | 0.258 | Long |
| Distinctions | Contents | |
|---|---|---|
| Vision | Sustainable, innovative, and resilient AX of container terminals based on resilient-AI governance | |
| Goal | Short term | Initially stabilize AX and creation of cybersecurity foundation |
| Mid term | Stabilize AI system and establish ethics and governance system | |
| Long term | Complete AI infrastructure and policy foundation, and strengthen global competitiveness | |
 | ||
| Step | Strategies | |
| Short term (1–2 years) | [Private] Establish privacy-protection and data-management systems [Public and private] Strengthen cybersecurity certification system for port terminals [Public and private] Strengthen R&D for cybersecurity solutions [Public] Secure initial cybersecurity budget | |
| Mid term (3–5 years) | [Private] Design AI–human cooperation process [Private] Establish red-team organization to balance decision making [Private] Monitor AI systems in real time [Private] Introduce AI-algorithm optimization system [Private] Expand in-house training opportunities to internalize new technologies [Public and private] Establish a strategy for phased introduction of AI systems [Public and private] Activate existing workforce-reassignment and job-transition programs [Public and private] Introduce AI risk (human rights, safety, security, etc.) analysis system [Private] Perform quality control and optimization for AI decision-making [Public] Establish AI human-rights impact assessments and ethical guidelines [Public and private] Enhance transparency of AI governance activities and expand stakeholder engagement | |
| Long term (5–10 years) | [Public] Introduce AI-related insurance and third-party certification systems [Public] Analyze AI-related legal systems [Private] Optimize the integration of AI systems with existing systems [Public and private] Perform AI-based system standardization and DB management [Private] Manage automatic AI error recovery and redundant systems [Public] Activate infrastructure-investment attraction (e.g., establishment of funds) | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, J.-m.; Sim, M.-s.; Kim, Y.-s.; Lim, H.-r.; Lee, C.-h. Strategizing Artificial Intelligence Transformation in Smart Ports: Lessons from Busan’s Resilient AI Governance Model. J. Mar. Sci. Eng. 2025, 13, 1276. https://doi.org/10.3390/jmse13071276
Lee J-m, Sim M-s, Kim Y-s, Lim H-r, Lee C-h. Strategizing Artificial Intelligence Transformation in Smart Ports: Lessons from Busan’s Resilient AI Governance Model. Journal of Marine Science and Engineering. 2025; 13(7):1276. https://doi.org/10.3390/jmse13071276
Chicago/Turabian StyleLee, Jeong-min, Min-seop Sim, Yul-seong Kim, Ha-ram Lim, and Chang-hee Lee. 2025. "Strategizing Artificial Intelligence Transformation in Smart Ports: Lessons from Busan’s Resilient AI Governance Model" Journal of Marine Science and Engineering 13, no. 7: 1276. https://doi.org/10.3390/jmse13071276
APA StyleLee, J.-m., Sim, M.-s., Kim, Y.-s., Lim, H.-r., & Lee, C.-h. (2025). Strategizing Artificial Intelligence Transformation in Smart Ports: Lessons from Busan’s Resilient AI Governance Model. Journal of Marine Science and Engineering, 13(7), 1276. https://doi.org/10.3390/jmse13071276







