A Novel Dual Authenticated Encryption Scheme Suitable for Social Networking Services
Abstract
1. Introduction
2. Preliminaries
- (i)
- Bilinearity:e(A1 + B2, P) = e(A1, P)e(B2, P);e(P, A1 + A2) = e(P, A1)e(P, A2);
- (ii)
- Non-degeneracy:Let P be a generator of the group G1. Then we say that e(P, P) would be a generator of the group G2.
- (iii)
- Computability:For any A1, B2∈ G1, there is an efficient algorithm to compute e(A1, B2).
3. Proposed DAE Scheme
3.1. Participated Parties
3.2. Algorithms
3.3. Concrete Construction
| r ⊕ h2(R, σ, Z) | |
| = r ⊕ h2(R, σ, h3(e(xcR, Yb))) | (by Equation (5A)) |
| = r ⊕ h2(R, σ, h3(e(xctP, Yb))) | (by Equation (1)) |
| = r ⊕ h2(R, σ, h3(e(tYc, Yb))) | |
| = r ⊕ h2(R, σ, Z) | (by Equation (3)) |
| = m | (by Equation (4)) |
| R | |
| = tP | (by Equation (1)) |
| = (σ + xah1(m, R))P | (by Equation (2)) |
| = σP + h1(m, R)Ya |
4. Security Proof
4.1. Security Model
4.2. Security Proofs
5. Efficiency
6. Conclusions
Funding
Conflicts of Interest
References
- Diffie, W.; Hellman, M. New Directions in Cryptography. IEEE T. Inform. Theory 1976, IT-22, 644–654. [Google Scholar]
- Hou, F.; Wang, Z.; Tang, Y.; Liu, Z. Protecting Integrity and Confidentiality for Data Communication. In Proceedings of the 9th International Symposium on Computers and Communications (ISCC’04), Alexandria, Egypt, 28 June–1 July 2004; pp. 357–362. [Google Scholar]
- Jacob, J. A Uniform Presentation of Confidentiality Properties. IEEE Trans. Softw. Eng. 1991, 17, 1186–1194. [Google Scholar] [CrossRef]
- Stallings, W. Cryptography and Network Security: Principles and Practices, 7th ed.; Pearson: London, UK, 2017. [Google Scholar]
- Schneider, S. Formal Analysis of a Non-Repudiation Protocol. In Proceedings of the 11th IEEE Computer Security Foundations Workshop, IEEE Press, Rockport, MA, USA, 9–11 June 1998; pp. 54–65. [Google Scholar]
- ElGamal, T. A Public Key Cryptosystem and a Signature Scheme Based on Discrete Logarithms. IEEE Trams. Inf. Theory 1985, IT-31, 469–472. [Google Scholar] [CrossRef]
- Rivest, R.; Shamir, A.; Adleman, L. A Method for Obtaining Digital Signatures and Public-Key Cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Sekhar, M.R. Signatures Scheme with Message Recovery and Its Applications. Int. J. Comput. Math. 2004, 81, 285–289. [Google Scholar]
- Horster, P.; Michel, M.; Peterson, H. Authenticated Encryption Schemes with Low Communication Costs. Electron. Lett. 1994, 30, 1212–1213. [Google Scholar] [CrossRef]
- Zheng, Y. Digital Signcryption or How to Achieve Cost(Signature & Encryption) << Cost(Signature) + Cost(Encryption). In Proceedings of the Advances in Cryptology—CRYPTO’97, Santa Barbara, CA, USA, 17–21 August 1997; Springer: Berlin/Heidelberg, Germany, 1997; pp. 165–179. [Google Scholar]
- Petersen, H.; Michels, M. Cryptanalysis and Improvement of Signcryption Schemes. IEE Proc. Comput. Digit. Tech. 1998, 145, 149–151. [Google Scholar] [CrossRef][Green Version]
- Zheng, Y. Signcryption and Its Applications in Efficient Public Key Solutions. In Proceedings of the 1st International Workshop on Information Security (ISW’97), Tatsunokuchi, Japan, 17–19 September 1997; pp. 291–312. [Google Scholar]
- Bellare, M.; Jakobsson, M.; Yung, M. Round-Optimal Zero-Knowledge Arguments Based on any One-Way Function. In Proceedings of the Advances in Cryptology—EUROCRYPT’97, Konstanz, Germany, 11–15 May 1997; Springer: Berlin/Heidelberg, Germany, 1997; pp. 280–305. [Google Scholar]
- Boyen, X. Multipurpose Identity-Based Signcryption—A Swiss Army Knife for Identity-Based Cryptography. In Proceedings of the Advances in Cryptology—CRYPTO’03, Santa Barbara, CA, USA, 17–21 August 2003; Springer: Berlin/Heidelberg, Germany, 2003; pp. 383–399. [Google Scholar]
- Chaum, D. Zero-Knowledge Undeniable Signatures. In Proceedings of the Advances in Cryptology—EUROCRYPT’90, Aarhus, Denmark, 21–24 May 1990; Springer: Berlin/Heidelberg, Germany, 1990; pp. 458–464. [Google Scholar]
- Araki, S.; Uehara, S.; Imamura, K. The Limited Verifier Signature and Its Application. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 1999, E82-A, 63–68. [Google Scholar]
- Wu, T.S.; Hsu, C.L. Convertible Authenticated Encryption Scheme. J. Syst. Softw. 2002, 62, 205–209. [Google Scholar]
- Huang, H.F.; Chang, C.C. An Efficient Convertible Authenticated Encryption Scheme and Its Variant. In Proceedings of the 5th International Conference on Information and Communications Security (ICICS 2003), Huhehaote, China, 10–13 October 2003; pp. 382–392. [Google Scholar]
- Lv, J.; Wang, X.; Kim, K. Practical Convertible Authenticated Encryption Schemes Using Self-Certified Public Keys. Appl. Math. Comput. 2005, 169, 1285–1297. [Google Scholar] [CrossRef]
- Chien, H.Y. Selectively Convertible Authenticated Encryption in the Random Oracle Model. Comput. J. 2008, 51, 419–434. [Google Scholar] [CrossRef]
- Duan, S.; Cao, Z. Efficient and Provably Secure Multi-Receiver Identity-Based Signcryption. In Proceedings of the Australasian Conference on Information Security and Privacy (ACISP’06), Melbourne, Australia, 3–5 July 2006; pp. 195–206. [Google Scholar]
- Hsu, C.L.; Lin, H.Y. Convertible Authenticated Encryption Scheme with Hierarchical Access Control. Appl. Math. Inf. Sci. 2014, 8, 1239–1246. [Google Scholar] [CrossRef]
- Lee, C.C.; Hwang, M.S.; Tzeng, S.F. A New Convertible Authenticated Encryption Scheme Based on the ElGamal Cryptosystem. Int. J. Found. Comput. Sci. 2009, 20, 351–359. [Google Scholar] [CrossRef]
- Lin, H.Y.; Hsu, C.L. A Novel Identity-Based Key-Insulated Convertible Authenticated Encryption Scheme. Int. J. Found. Comput. Sci. 2011, 22, 739–756. [Google Scholar] [CrossRef]
- Lin, H.Y.; Hsu, C.L.; Huang, S.K. Improved Convertible Authenticated Encryption Scheme with Provable Security. Inf. Process. Lett. 2011, 111, 661–666. [Google Scholar] [CrossRef]
- Lin, H.Y.; Wu, T.S.; Huang, S.K. An Efficient Strong Designated Verifier Proxy Signature Scheme for Electronic Commerce. J. Inf. Sci. Eng. 2012, 28, 771–785. [Google Scholar]
- Luo, M.; Wen, Y.; Zhao, H. A Certificate-Based Signcryption Scheme. In Proceedings of the 2008 International Conference on Computer Science and Information Technology, Singapore, 29 August–2 September 2008; pp. 17–23. [Google Scholar]
- Wu, T.S.; Chen, Y.S.; Lin, H.Y.; Chang, T.K. Authenticated Encryption Scheme Based on Paillier System with Verifiable Public Keys. Commun. Comput. Secur. 2012, 2, 1–5. [Google Scholar] [CrossRef]
- Wu, T.S.; Lin, H.Y. Efficient Self-Certified Proxy CAE Scheme and Its Variants. J. Syst. Softw. 2009, 82, 974–980. [Google Scholar] [CrossRef]
- Wu, T.S.; Lin, H.Y. Secure Convertible Authenticated Encryption Scheme Based on RSA. Informatica 2009, 33, 481–486. [Google Scholar]
- Wu, T.S.; Lin, H.Y.; Ting, P.Y. A Publicly Verifiable PCAE Scheme for Confidential Applications with Proxy Delegation. Trans. Emerg. Telecommun. Technol. 2012, 23, 172–185. [Google Scholar] [CrossRef]
- Wu, T.S.; Lin, H.Y.; Tsao, S.H.; Ting, P.Y. On the Construction of DL-Based Convertible Authenticated Encryption Scheme with Message Linkages. Information 2013, 16, 7983–7994. [Google Scholar]
- Hsu, C.L.; Lin, H.Y. New Identity-Based Key-Insulated Convertible Multi-Authenticated Encryption Scheme. J. Netw. Comput. Appl. 2011, 34, 1724–1731. [Google Scholar] [CrossRef]
- Lu, C.F.; Hsu, C.L.; Lin, H.Y. Provably Convertible Multi-Authenticated Encryption Scheme for Generalized Group Communications. Inf. Sci. 2012, 199, 154–166. [Google Scholar] [CrossRef]
- Lin, H.Y. Group-Oriented Data Access Structure Using Threshold-CAE Scheme and Its Extension. Inf. Technol. Control 2014, 43, 252–263. [Google Scholar] [CrossRef]
- Pointcheval, D.; Stern, J. Security Arguments for Digital Signatures and Blind Signatures. J. Cryptol. 2000, 13, 361–369. [Google Scholar] [CrossRef]
- Cao, X.; Kou, W.; Du, X. A Pairing-Free Identity-Based Authenticated Key Agreement Protocol with Minimal Message Exchanges. Inf. Sci. 2010, 180, 2895–2903. [Google Scholar] [CrossRef]
- Lee, J.S.; Chang, J.H.; Lee, D.H. Forgery Attacks on Kang et al.’s Identity-Based Strong Designated Verifier Signature Scheme and Its Improvement with Security Proof. Comput. Electr. Eng. 2010, 36, 948–954. [Google Scholar] [CrossRef]
- Islam, S.K.H.; Biswas, G.P. Provably Secure Certificateless Strong Designated Verifier Signature Scheme Based on Elliptic Curve Bilinear Pairings. J. King Saud Univ.-Comput. Inf. Sci. 2013, 25, 51–61. [Google Scholar]
- Chen, Y.; Zhao, Y.; Xiong, H.; Yue, F. A Certificateless Strong Designated Verifier Signature Scheme with Non-delegatability. Int. J. Netw. Secur. 2017, 19, 573–582. [Google Scholar]
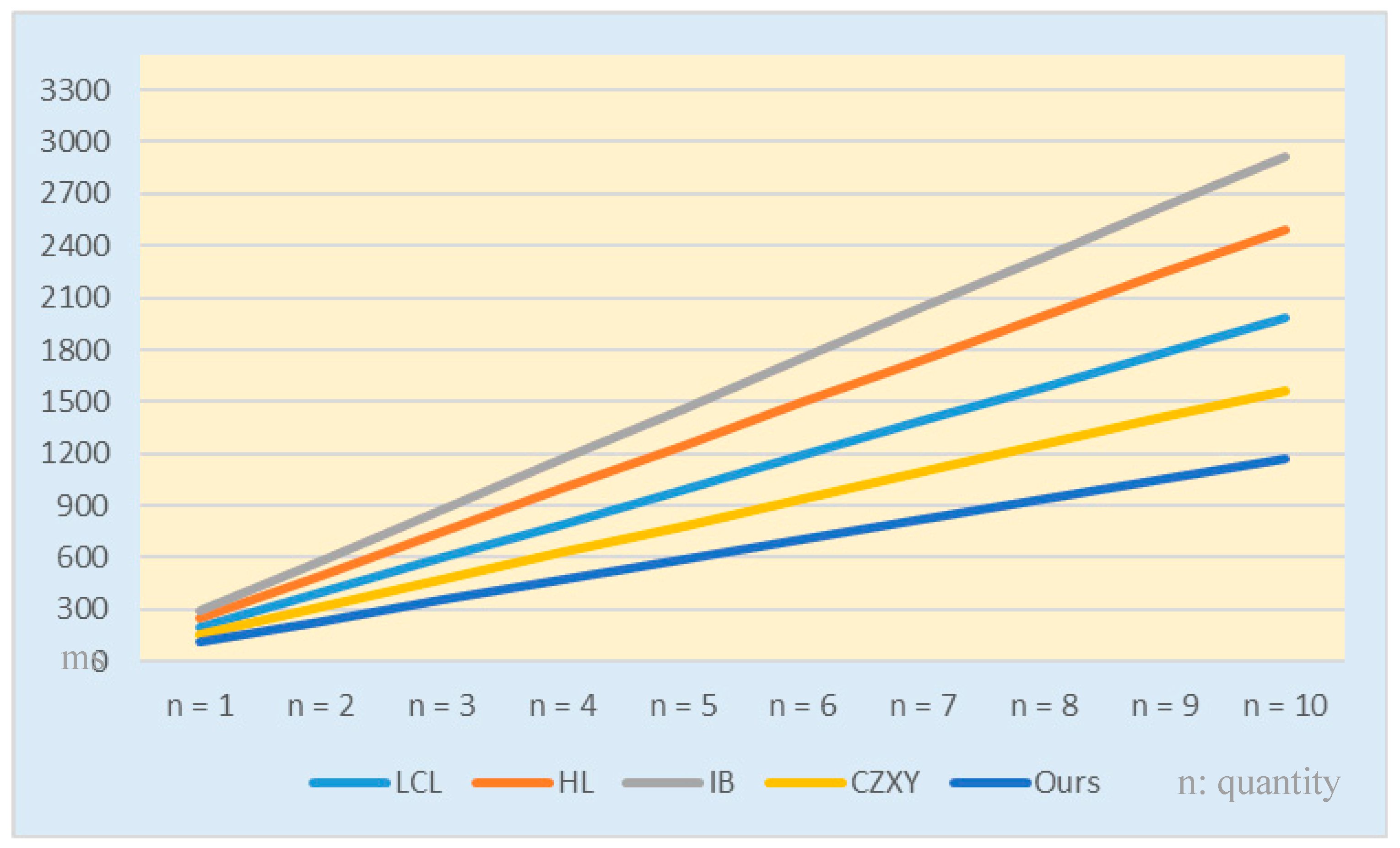
| Symbol | Description | Approximate Running Time |
|---|---|---|
| TB | the computational time of a bilinear pairing operation | 20.01 ms |
| TE | the computational time of an exponentiation in G2 | 11.20 ms |
| TM | the computational time of a pairing-based scalar multiplication | 6.38 ms |
| Scheme | Computational Costs of Sender | Computational Costs of Each Recipient | Total Computational Costs |
|---|---|---|---|
| LCL | 4TB + 4TM (≈211.12 ms) | 2TB + TM (≈46.4 ms) | 8TB + 6TM (≈198.36 ms) |
| HL | 2TB + 8TM (≈91.06 ms) | 3TB + 3TM (≈79.17 ms) | 8TB + 14TM (≈249.4 ms) |
| IB | 6TB + 6TM + 2TE (≈198.74 ms) | TB + TM + TE (≈46.59 ms) | 8TB + 8TM + 4TE (≈291.92 ms) |
| CZXY | 2TB + 6TM (≈78.3 ms) | TB + 3TM (≈39.15 ms) | 4TB + 12TM (≈156.6 ms) |
| Ours | TB + 3TM (≈39.15 ms) | TB + 3TM (≈39.15 ms) | 3TB + 9TM (≈117.45 ms) |
| LCL | HL | IB | CZXY | Ours | |
|---|---|---|---|---|---|
| Ciphertext Length (Byte) | 256 | 384 | 256 | 296 | 148 |
© 2019 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lin, H.-Y. A Novel Dual Authenticated Encryption Scheme Suitable for Social Networking Services. Appl. Sci. 2019, 9, 1452. https://doi.org/10.3390/app9071452
Lin H-Y. A Novel Dual Authenticated Encryption Scheme Suitable for Social Networking Services. Applied Sciences. 2019; 9(7):1452. https://doi.org/10.3390/app9071452
Chicago/Turabian StyleLin, Han-Yu. 2019. "A Novel Dual Authenticated Encryption Scheme Suitable for Social Networking Services" Applied Sciences 9, no. 7: 1452. https://doi.org/10.3390/app9071452
APA StyleLin, H.-Y. (2019). A Novel Dual Authenticated Encryption Scheme Suitable for Social Networking Services. Applied Sciences, 9(7), 1452. https://doi.org/10.3390/app9071452





