A Fragile Watermark Scheme for Image Recovery Based on Singular Value Decomposition, Edge Detection and Median Filter
Abstract
:1. Introduction
2. Related Work
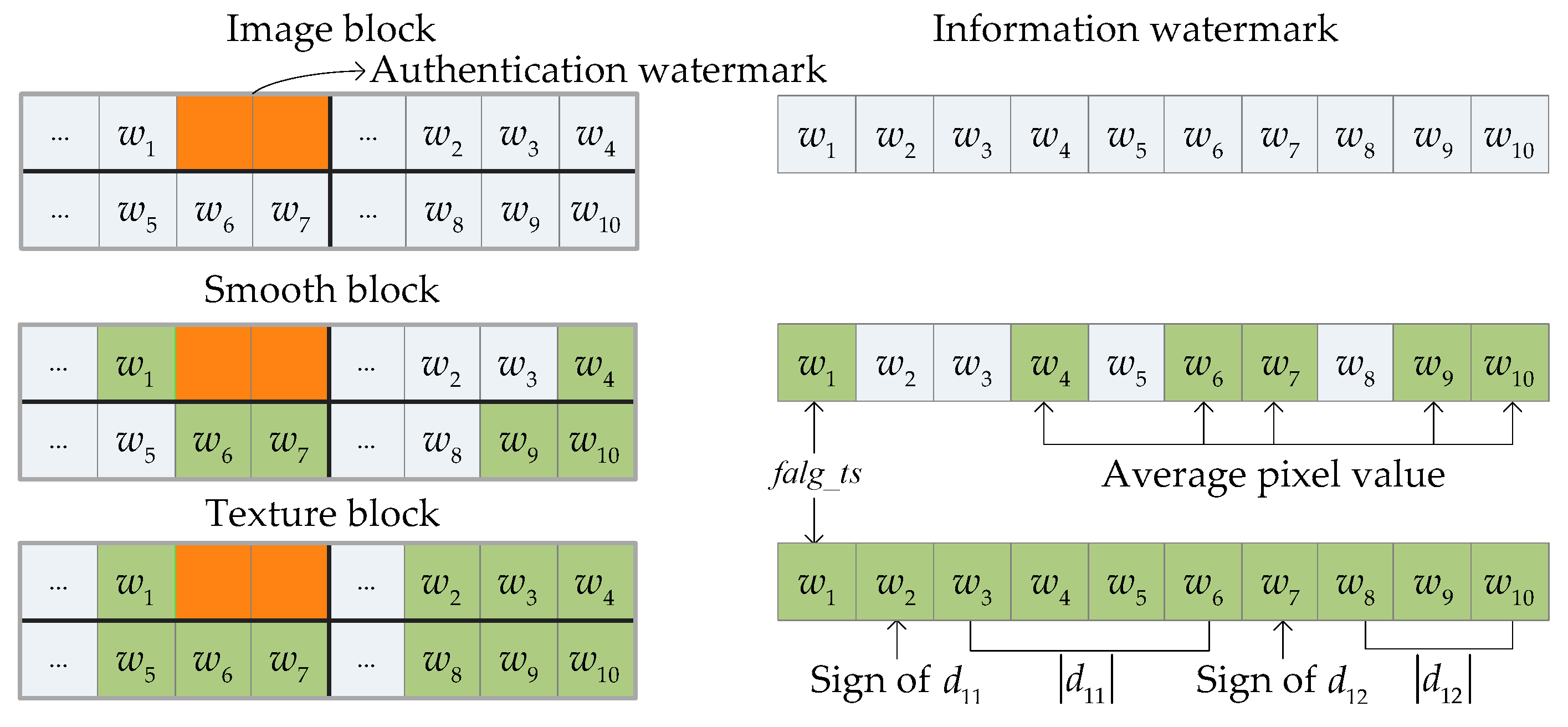
2.1. Brief Introduction to Wang et al.’s Method
2.2. Shortcomings of Wang et al.’s Method
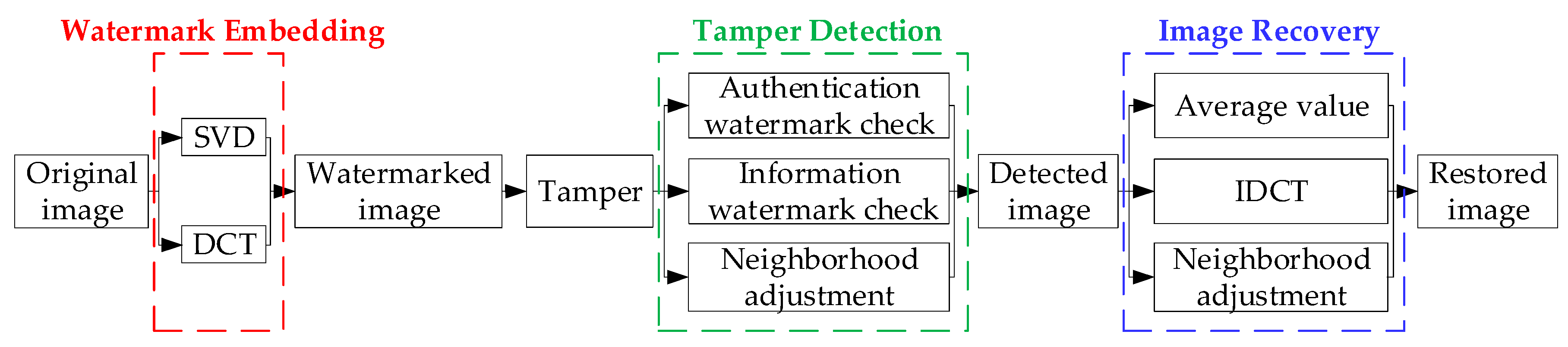
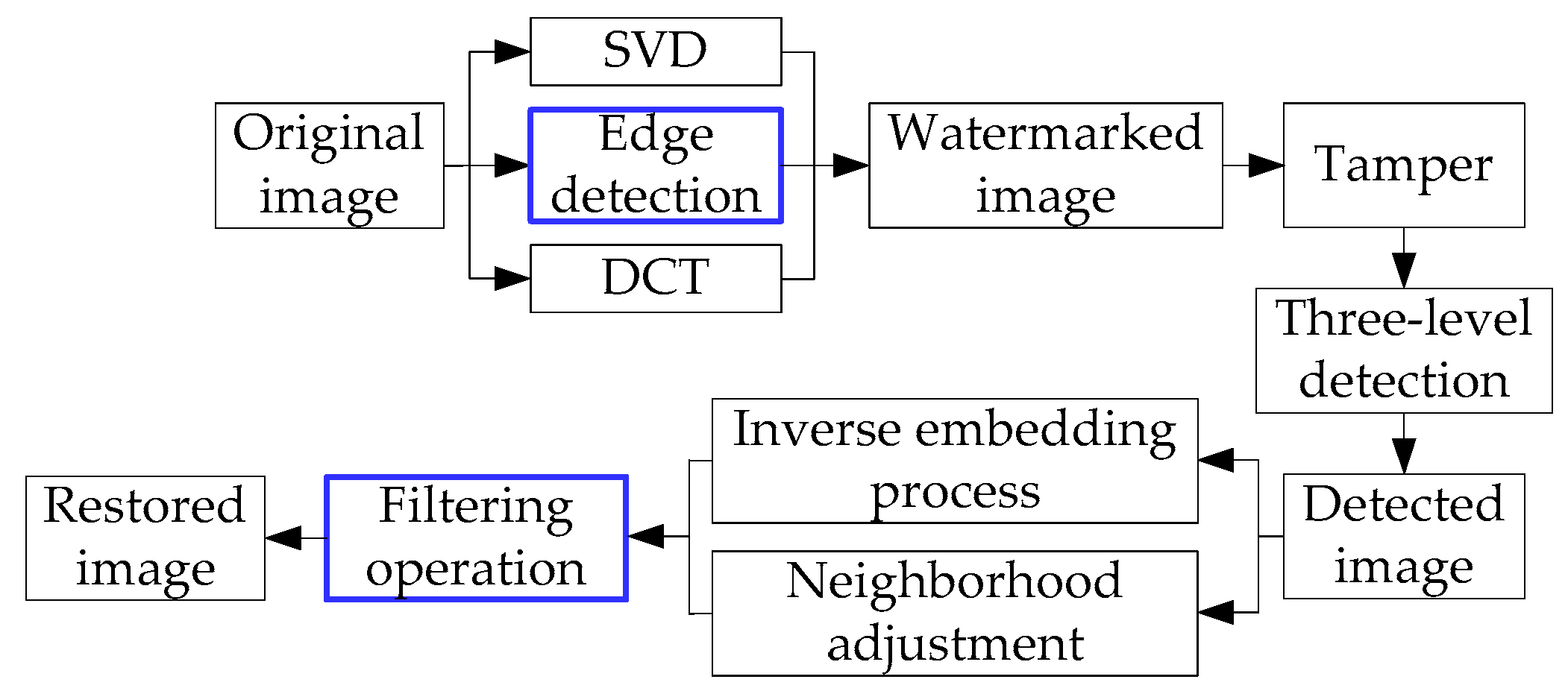
3. The Proposed Method
3.1. Edge Detection
- Step 1. Convolve a Gaussian function and the original image to obtain a smoothed image , as shown in Equations (3) and (4), respectively:where the default value of is 2, represents the pixel position and the operator represents a convolution operation.
- Step 2. Compute the gradient magnitude image and angle images , shown in Equations (5) and (6), respectively:where and represent the partial derivations of image to and , respectively.
- Step 3. Apply non-maximum suppression to the gradient magnitude image.
- Step 4. Use double threshold and connectivity analysis to detect and link the edges.
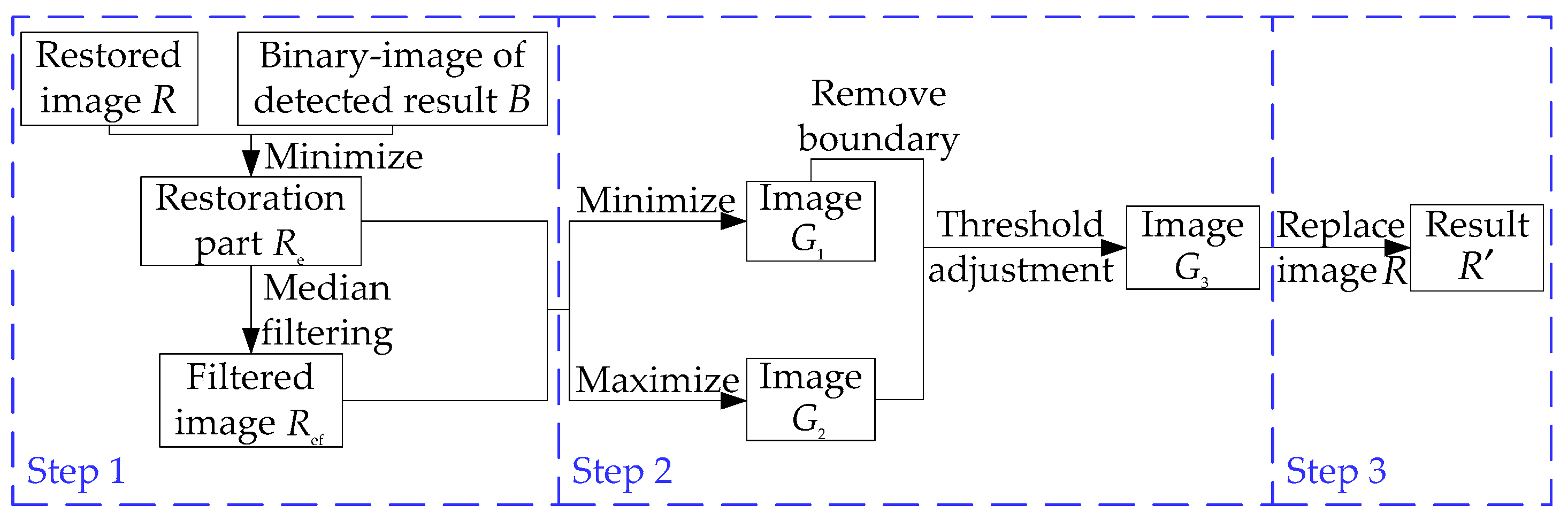
3.2. Filtering Operation
- Step 1. The restored image is obtained by performing the inverse embedding process. The binary image highlights the tampered area detected by the proposed method. To extract the actual restored area in image , a minimum operation is performed on image and image , generating image , which has a black background except for the restored area. Then, median filtering is applied to image and we obtain the filtered image , which is highly smoothed. However, at the boundaries (i.e., where the black background and the restored areas meet) the original restored pixels are replaced by those with values closer to those of the background, which introduces noise.
- Step 2. The minimum and maximum operations are performed on image and image , generating the images and image , respectively. Image contains lower pixel values, including the replaced boundary, while image contains higher pixel values. After removing the boundary, image is combined with image to generate image using a manually selected threshold as presented in detail in Section 4.3.
- Step 3. After the previous two steps, image not only smooths the noisy areas but also retains the texture and edge information. The final result, , is obtained by replacing the restored pixels in image with the corresponding pixels in image .
3.3. Main Process of Tamper Detection and Recovery
4. Experimental Results and Analysis
4.1. Performance in Watermark Embedding
4.2. Analysis of Different Tampering Test Results
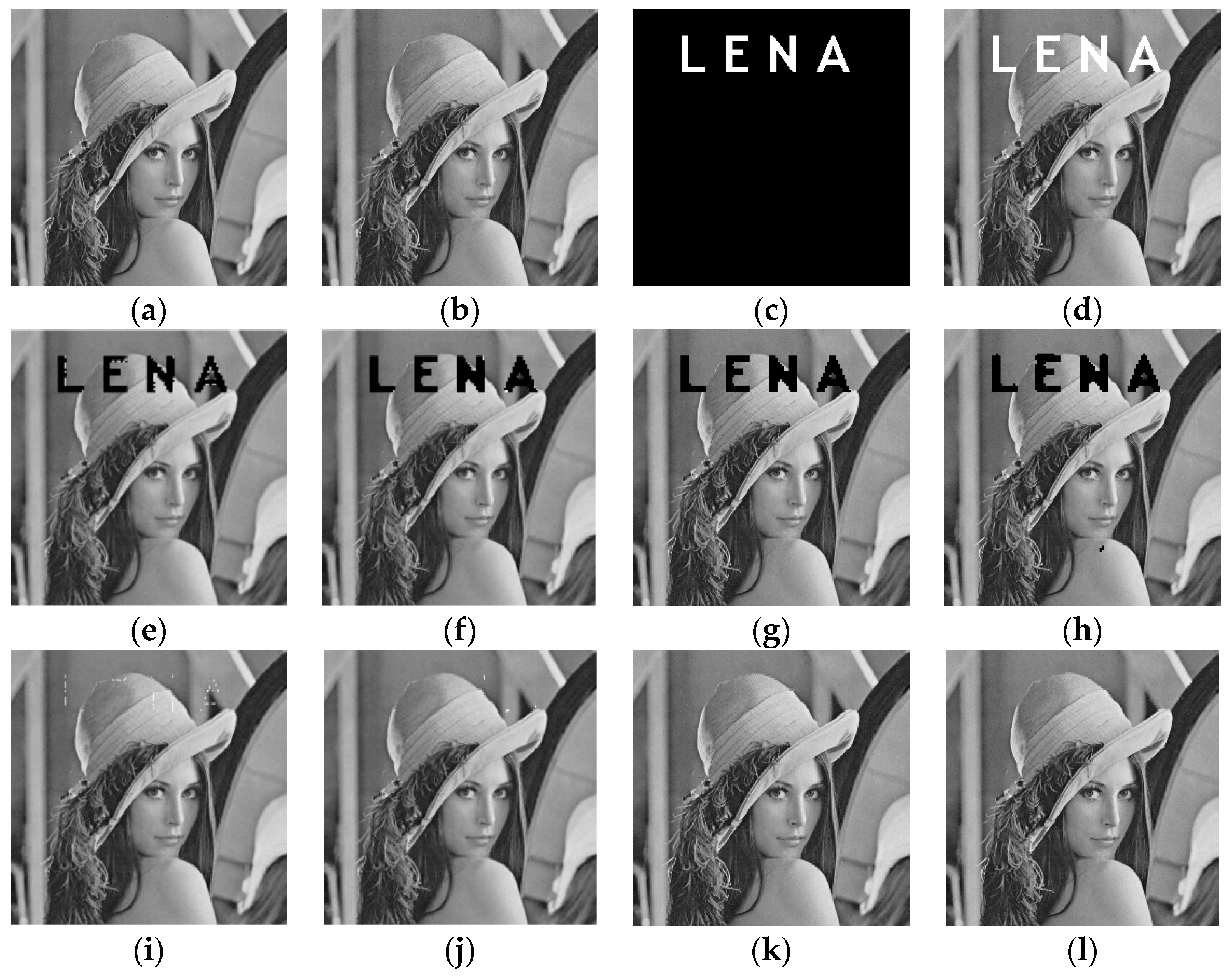
4.2.1. Text Addition Attack
4.2.2. Copy-Move Attack
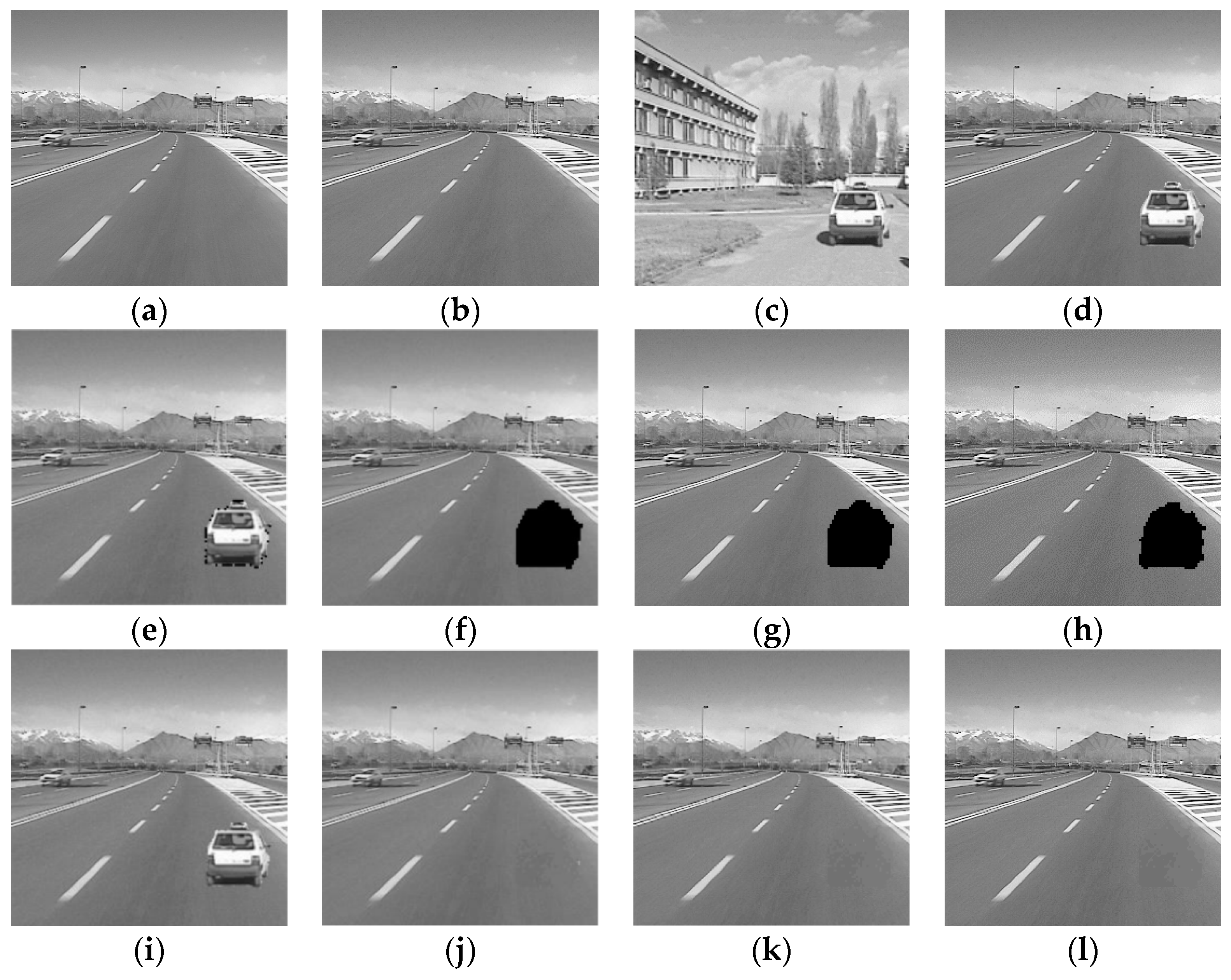
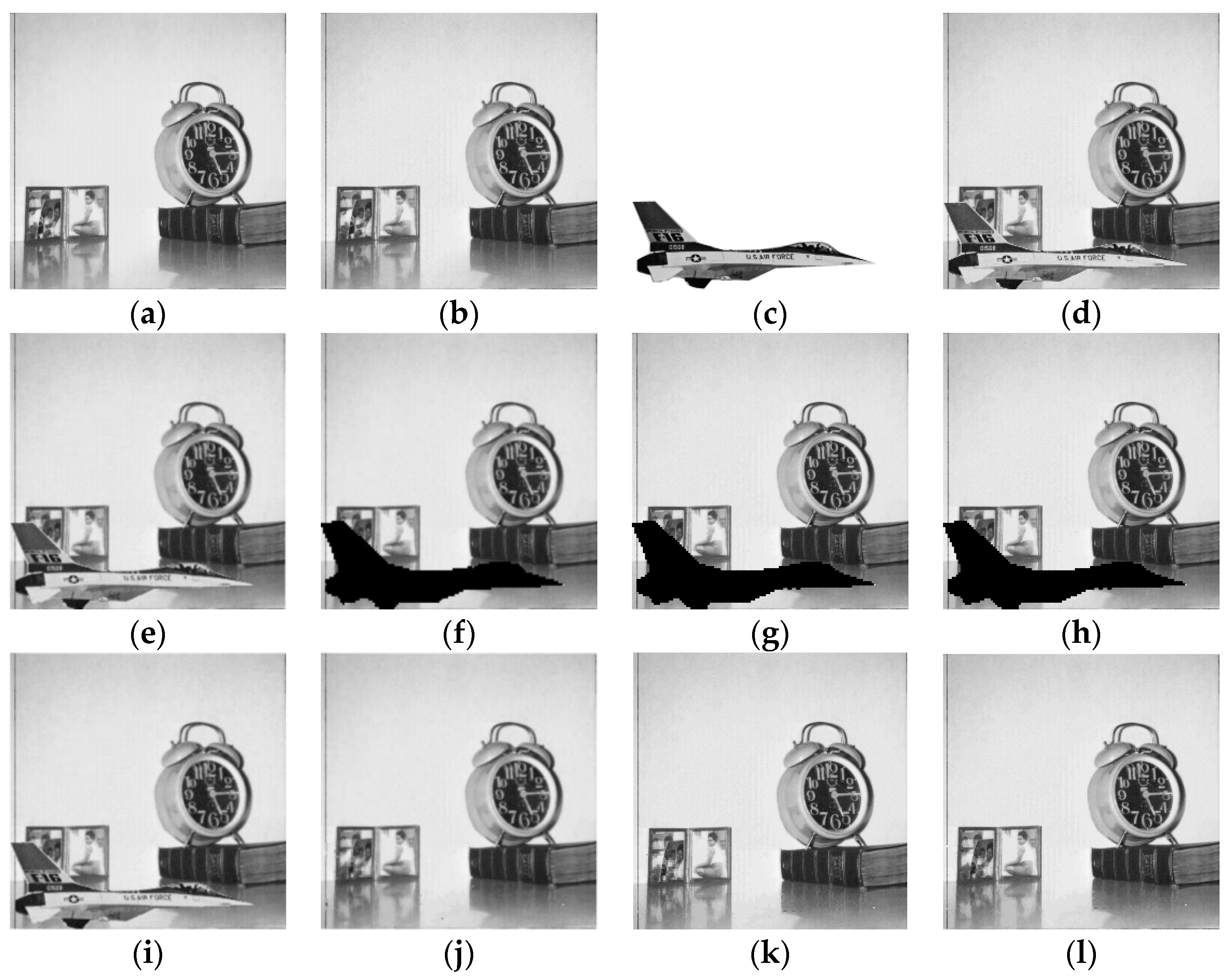
4.2.3. Splicing Attack
4.2.4. Image Deletion Attack
4.2.5. Content-Only Attack
4.2.6. Large Area Attack
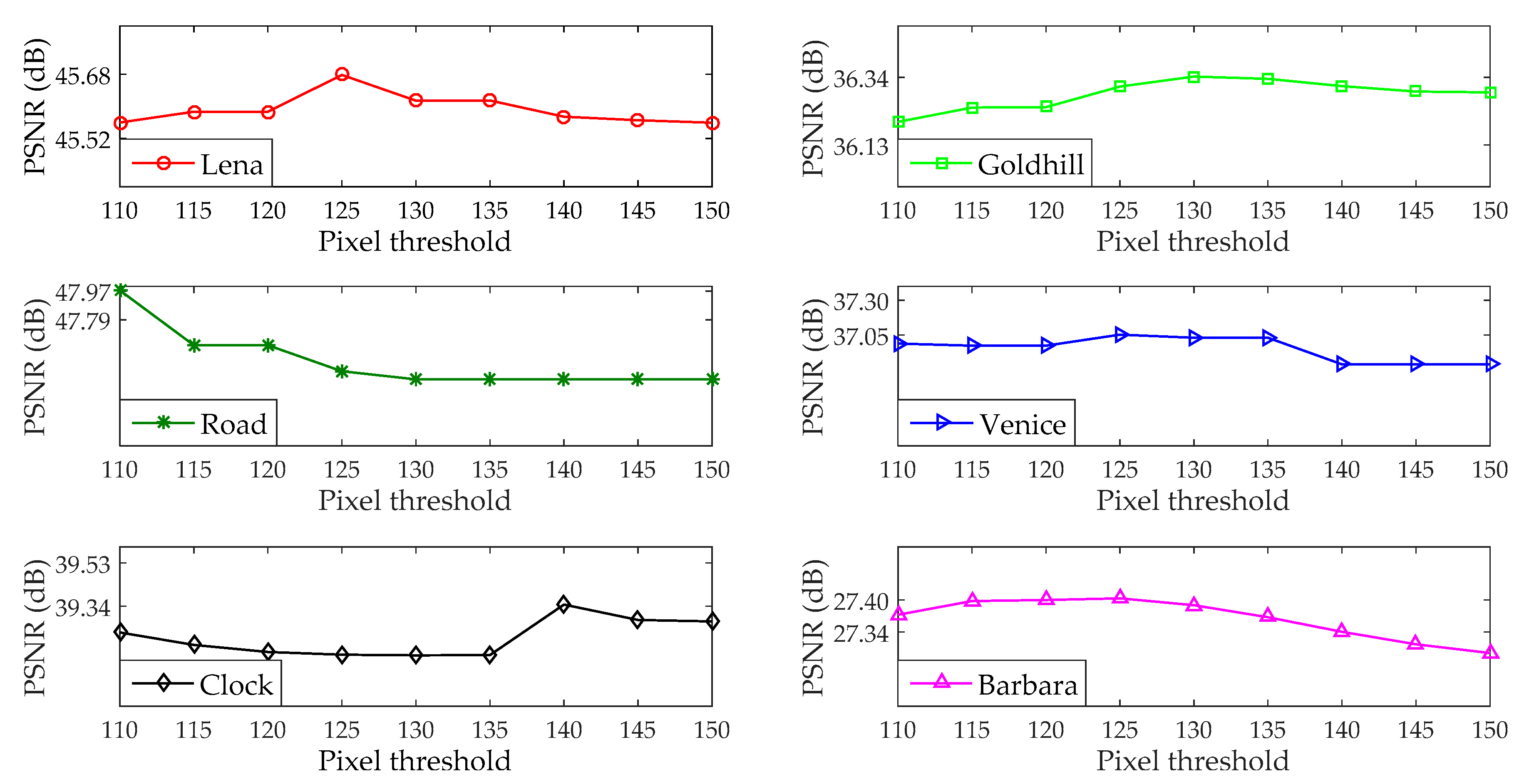
4.3. Selection of Threshold in Filtering Operation
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Singh, D.; Singh, S.K. DCT based efficient fragile watermarking scheme for image authentication and restoration. Multimed. Tools Appl. 2017, 76, 953–977. [Google Scholar] [CrossRef]
- Shivani, S.; Singh, D.; Agarwal, S. DCT based approach for tampered image detection and recovery using block wise fragile watermarking scheme. In Proceedings of the 6th Iberian Conference on Pattern Recognition and Image Analysis, Funchal, Portugal, 5–7 June 2013; Lecture Notes in Computer Science. Springer: Berlin, Germany, 2013; Volume 7887, pp. 640–647. [Google Scholar]
- Roy, S.; Pal, A.K. A blind DCT based color watermarking algorithm for embedding multiple watermarks. AEU Int. J. Electron. Commun. 2017, 72, 149–161. [Google Scholar] [CrossRef]
- El’arbi, M.; Amar, C.B. Image authentication algorithm with recovery capabilities based on neural networks in the DCT domain. IET Image Process. 2014, 8, 619–626. [Google Scholar] [CrossRef]
- Molina-Garcia, J.; Reyes-Reyes, R.; Ponomaryov, V.; Cruz-Ramos, C. Watermarking algorithm for authentication and self-recovery of tampered images using DWT. In Proceedings of the 9th International Kharkiv Symposium on Physics and Engineering of Microwaves, Millimeter and Submillimeter Waves, Kharkiv, Ukraine, 20–24 June 2016; pp. 1–4. [Google Scholar]
- Al-Otum, H.M. Semi-fragile watermarking for grayscale image authentication and tamper detection based on an adjusted expanded-bit multiscale quantization-based technique. J. Vis. Commun. Image Represent. 2014, 25, 1064–1081. [Google Scholar] [CrossRef]
- Wang, C.Y.; Zhang, H.; Zhou, X. A self-recovery fragile image watermarking with variable watermark capacity. Appl. Sci. 2018, 8, 548. [Google Scholar] [CrossRef]
- Tong, X.J.; Liu, Y.; Zhang, M.; Chen, Y. A novel chaos-based fragile watermarking for image tampering detection and self-recovery. Signal Process. Image Commun. 2013, 28, 301–308. [Google Scholar] [CrossRef]
- Chen, F.; He, H.J.; Tai, H.M.; Wang, H.X. Chaos-based self-embedding fragile watermarking with flexible watermark payload. Multimed. Tools Appl. 2014, 72, 41–56. [Google Scholar] [CrossRef]
- Dhole, V.S.; Patil, N.N. Self embedding fragile watermarking for image tampering detection and image recovery using self recovery blocks. In Proceedings of the International Conference on Computing Communication Control and Automation, Pune, India, 26–27 February 2015; pp. 752–757. [Google Scholar]
- Dadkhah, S.; Abd Manaf, A.; Hori, Y.; Hassanien, A.E.; Sadeghi, S. An effective SVD-based image tampering detection and self-recovery using active watermarking. Signal Process. Image Commun. 2014, 29, 1197–1210. [Google Scholar] [CrossRef]
- Zhang, H.; Wang, C.Y.; Zhou, X. Fragile watermarking for image authentication using the characteristic of SVD. Algorithms 2017, 10, 27. [Google Scholar] [CrossRef]
- Hsu, C.S.; Tu, S.F. Image tamper detection and recovery using adaptive embedding rules. Measurement 2016, 88, 287–296. [Google Scholar] [CrossRef]
- Sarreshtedari, S.; Akhaee, M.A.; Abbasfar, A. Source–channel coding-based watermarking for self-embedding of JPEG images. Signal Process. Image Commun. 2018, 62, 106–116. [Google Scholar] [CrossRef]
- Fan, M.Q.; Wang, H.X. An enhanced fragile watermarking scheme to digital image protection and self-recovery. Signal Process. Image Commun. 2018, 66, 19–29. [Google Scholar] [CrossRef]
- Lu, C.S.; Liao, H.Y.M. Multipurpose watermarking for image authentication and protection. IEEE Trans. Image Process. 2001, 10, 1579–1592. [Google Scholar] [PubMed]
- Lee, T.Y.; Lin, S.D. Dual watermark for image tamper detection and recovery. Pattern Recognit. 2008, 41, 3497–3506. [Google Scholar] [CrossRef]
- Qian, Z.X.; Feng, G.R.; Ren, Y.L. Fragile watermarking for color image recovery based on color filter array interpolation. In Proceedings of the 11th International Conference on Web-Age Information Management, Jiuzhaigou, China, 15–17 July 2010; Lecture Notes in Computer Science. Springer: Berlin, Germany, 2010; Volume 6184, pp. 537–543. [Google Scholar]
- Chetan, K.R.; Shivananda, N. A new fragile watermarking approach for tamper detection and recovery of document images. In Proceedings of the 3rd International Conference on Advances in Computing, Communications and Informatics, New Delhi, India, 24–27 September 2014; pp. 1494–1498. [Google Scholar]
- Yu, X.Y.; Wang, C.Y.; Zhou, X. Review on semi-fragile watermarking algorithms for content authentication of digital images. Future Internet 2017, 9, 56. [Google Scholar]
- Canny, J. A computational approach to edge detection. IEEE Trans. Pattern Anal. Mach. Intell. 1986, 8, 679–698. [Google Scholar] [CrossRef] [PubMed]
- CVG-UGR Image Database. Available online: http://decsai.ugr.es/cvg/dbimagenes/ (accessed on 26 July 2019).
- Shi, H.; Wang, X.H.; Li, M.C. Secure variable-capacity self-recovery watermarking scheme. Multimed. Tools Appl. 2017, 76, 6941–6972. [Google Scholar] [CrossRef]







| Test Images | PSNR (dB) | SSIM | ||||||
|---|---|---|---|---|---|---|---|---|
| Wang et al. [7] | Proposed | Wang et al. [7] | Proposed | Wang et al. [7] | Proposed | Wang et al. [7] | Proposed | |
| Lena | 8561 | 8372 | 7823 | 8012 | 39.82 | 39.74 | 0.9636 | 0.9985 |
| Goldhill | 5038 | 4637 | 11,346 | 11,747 | 38.91 | 39.08 | 0.9734 | 0.9984 |
| Car1 | 10,516 | 9998 | 5868 | 6386 | 40.41 | 40.07 | 0.9650 | 0.9978 |
| Car2 | 13,572 | 12,872 | 2812 | 3512 | 42.20 | 40.76 | 0.9627 | 0.9981 |
| Venice | 6062 | 5758 | 10,322 | 10,626 | 39.15 | 39.21 | 0.9627 | 0.9993 |
| Clock | 12,366 | 11,842 | 4018 | 4542 | 41.22 | 40.49 | 0.9575 | 0.9991 |
| Airplane | 10,946 | 10,673 | 5438 | 5711 | 40.56 | 40.40 | 0.9629 | 0.9986 |
| Barbara | 7321 | 7163 | 9063 | 9221 | 39.52 | 39.42 | 0.9697 | 0.9987 |
| Indexes | Tong et al. [8] | Chen et al. [9] | Wang et al. [7] | Proposed |
|---|---|---|---|---|
| PSNR (dB) | 35.01 | 40.85 | 45.52 | 45.68 |
| SSIM | 0.8441 | 0.8559 | 0.9925 | 0.9930 |
| Indexes | Tong et al. [8] | Chen et al. [9] | Wang et al. [7] | Proposed |
|---|---|---|---|---|
| PSNR (dB) | 25.90 | 35.05 | 36.13 | 36.34 |
| SSIM | 0.6861 | 0.7910 | 0.9925 | 0.9930 |
| Indexes | Tong et al. [8] | Chen et al. [9] | Wang et al. [7] | Proposed |
|---|---|---|---|---|
| PSNR (dB) | 24.76 | 47.17 | 47.79 | 47.97 |
| SSIM | 0.8016 | 0.8390 | 0.9925 | 0.9930 |
| Indexes | Tong et al. [8] | Chen et al. [9] | Wang et al. [7] | Proposed |
|---|---|---|---|---|
| PSNR (dB) | 35.19 | 35.21 | 37.27 | 37.05 |
| SSIM | 0.7194 | 0.7911 | 0.9925 | 0.9930 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xie, X.; Wang, C.; Li, M. A Fragile Watermark Scheme for Image Recovery Based on Singular Value Decomposition, Edge Detection and Median Filter. Appl. Sci. 2019, 9, 3020. https://doi.org/10.3390/app9153020
Xie X, Wang C, Li M. A Fragile Watermark Scheme for Image Recovery Based on Singular Value Decomposition, Edge Detection and Median Filter. Applied Sciences. 2019; 9(15):3020. https://doi.org/10.3390/app9153020
Chicago/Turabian StyleXie, Xuan, Chengyou Wang, and Meiling Li. 2019. "A Fragile Watermark Scheme for Image Recovery Based on Singular Value Decomposition, Edge Detection and Median Filter" Applied Sciences 9, no. 15: 3020. https://doi.org/10.3390/app9153020
APA StyleXie, X., Wang, C., & Li, M. (2019). A Fragile Watermark Scheme for Image Recovery Based on Singular Value Decomposition, Edge Detection and Median Filter. Applied Sciences, 9(15), 3020. https://doi.org/10.3390/app9153020







