Quantum-Key-Distribution (QKD) Networks Enabled by Software-Defined Networks (SDN)
Abstract
Featured Application
Abstract
1. Introduction
2. Progresses in QKD Networks
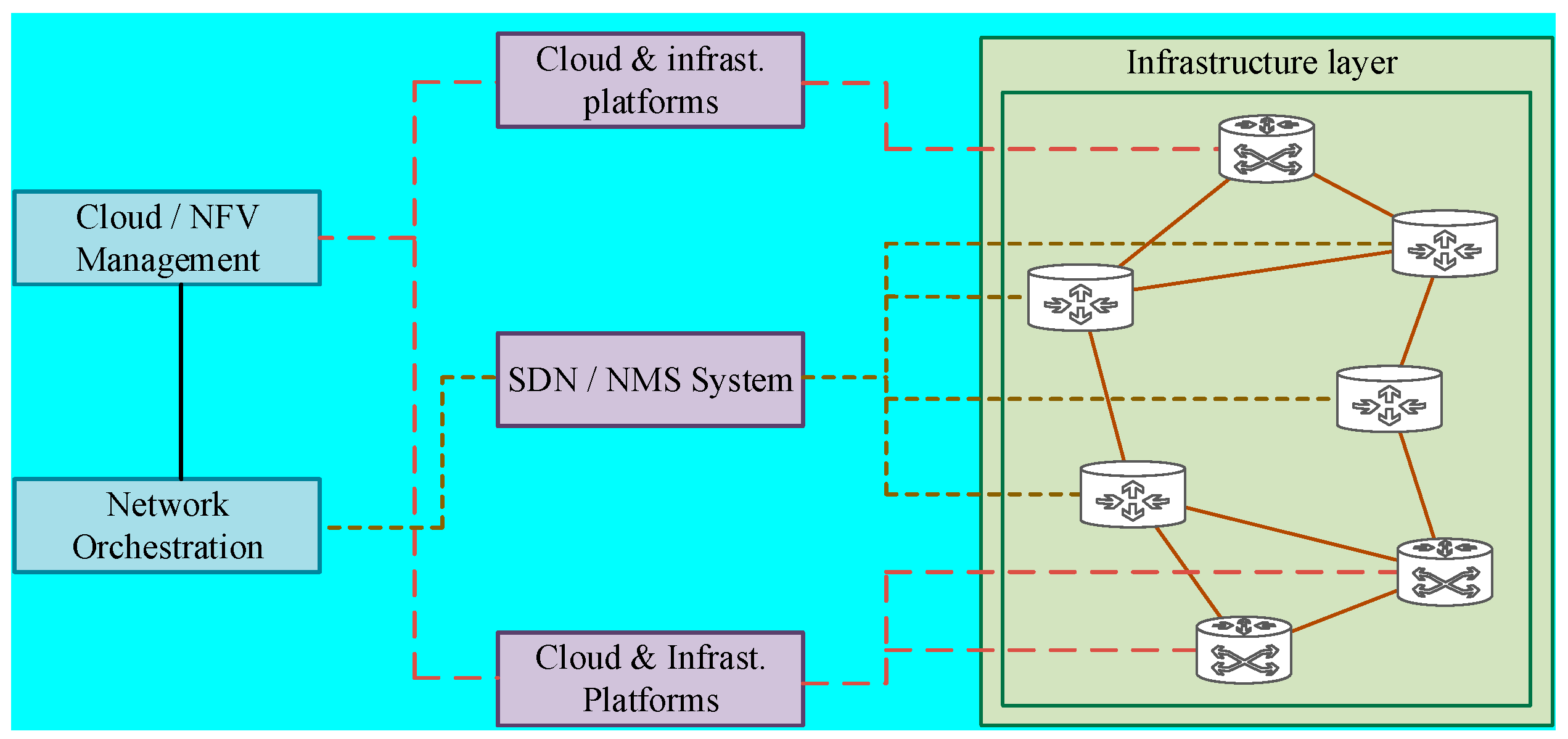
2.1. Researches on Architecture of The Networks
2.2. Researches on Interfaces and Protocols of the Networks
2.3. Experimental Verification of the Networks
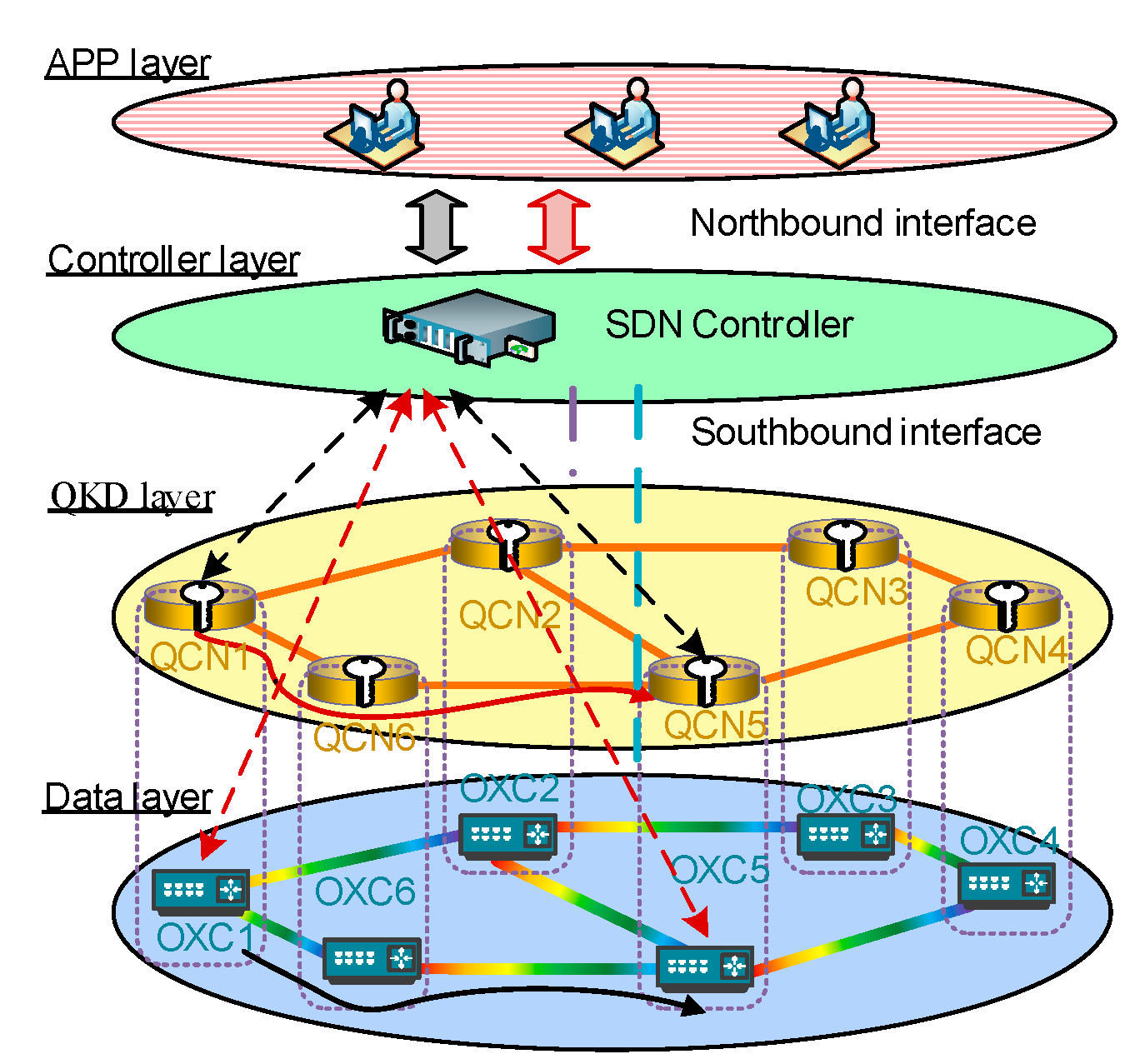
3. Architecture of QKD Network Enabled by SDN
3.1. Application Layer
3.2. Control Layer
3.3. QKD Layer
4. Interfaces and Protocols in QKD Networks Enabled by SDN
4.1. Related Interfaces
4.2. Southbound Interface Protocol
4.3. Northbound Interface Protocol
5. Three-Use Cases in QKD Networks
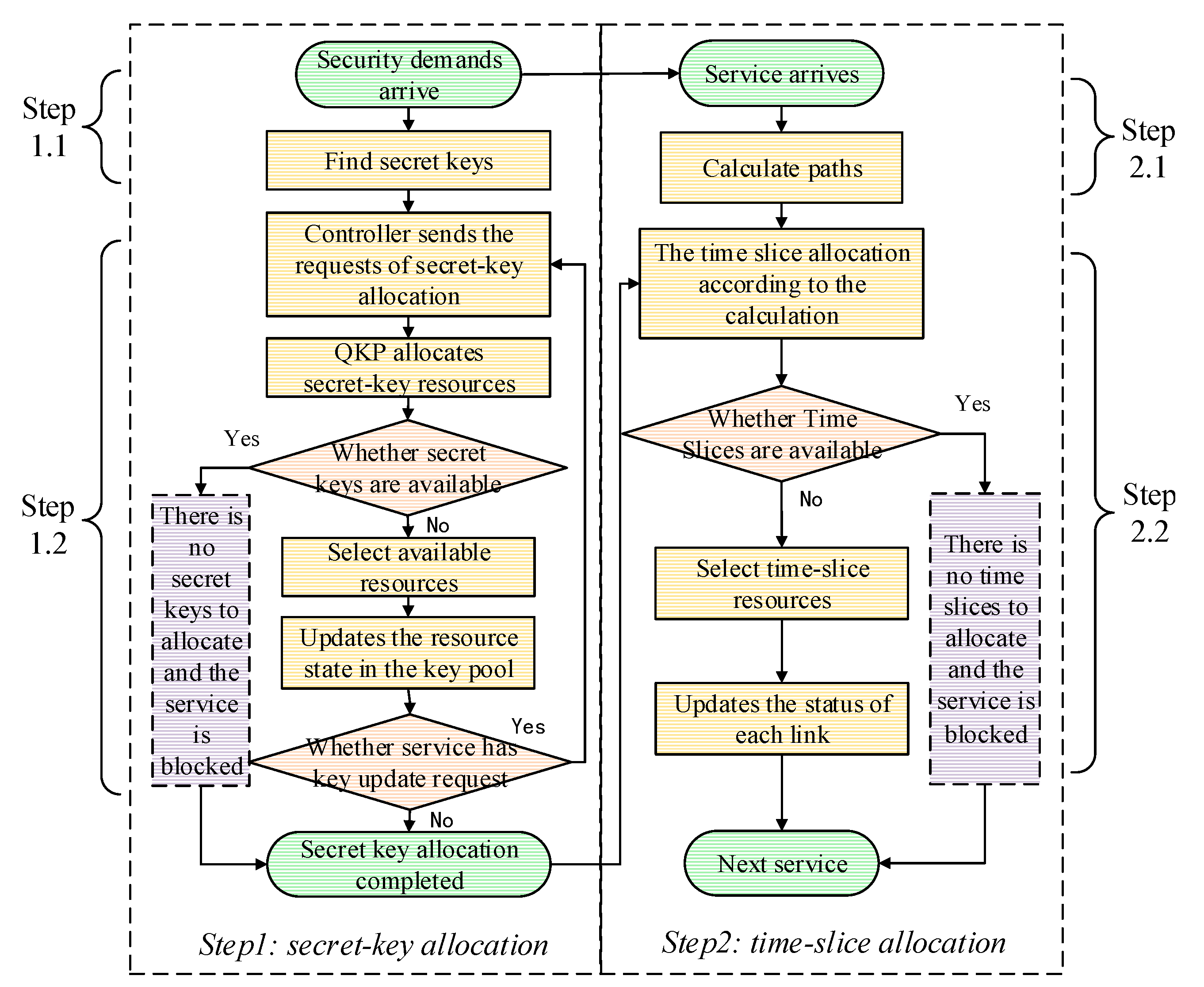
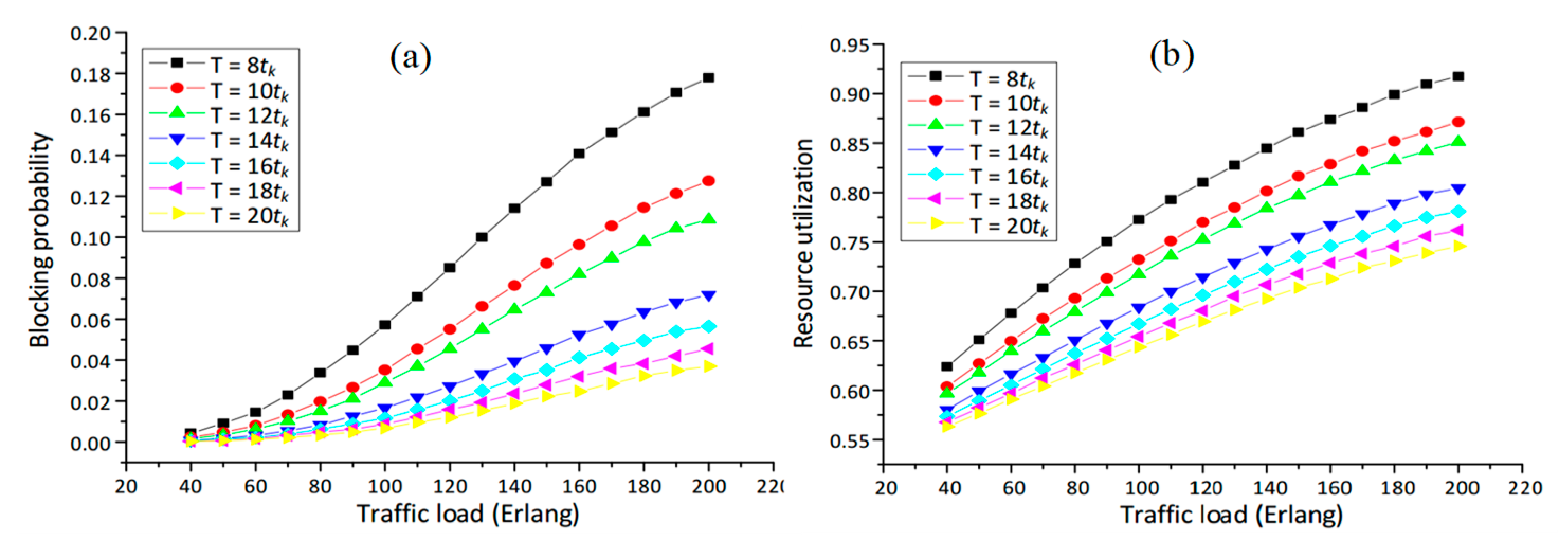
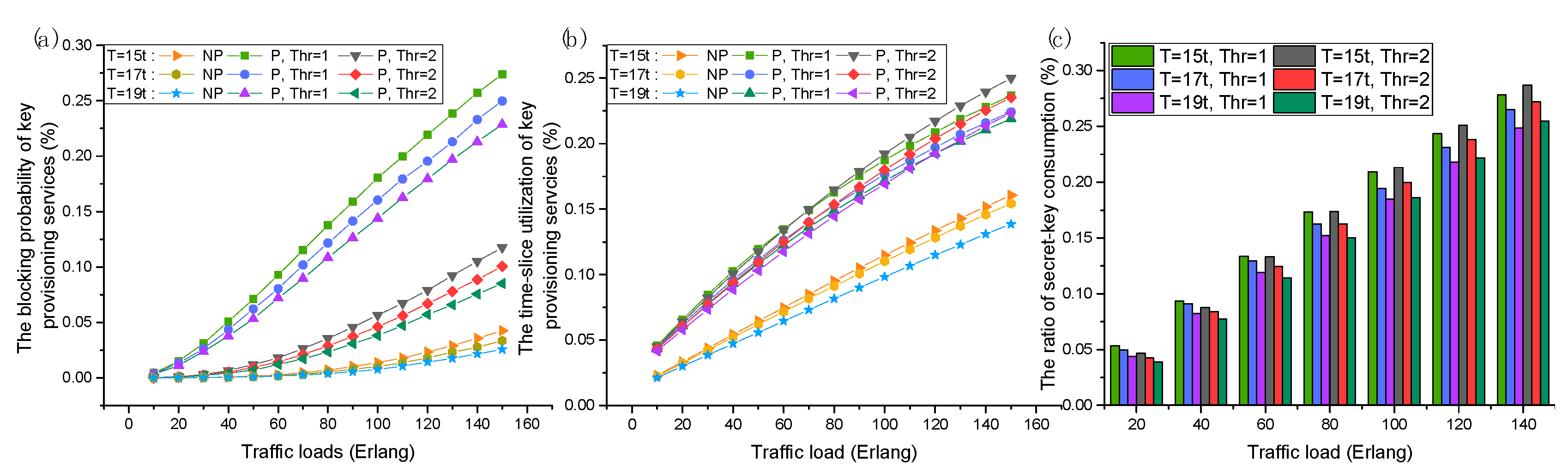
5.1. Resource Allocation in the Networks
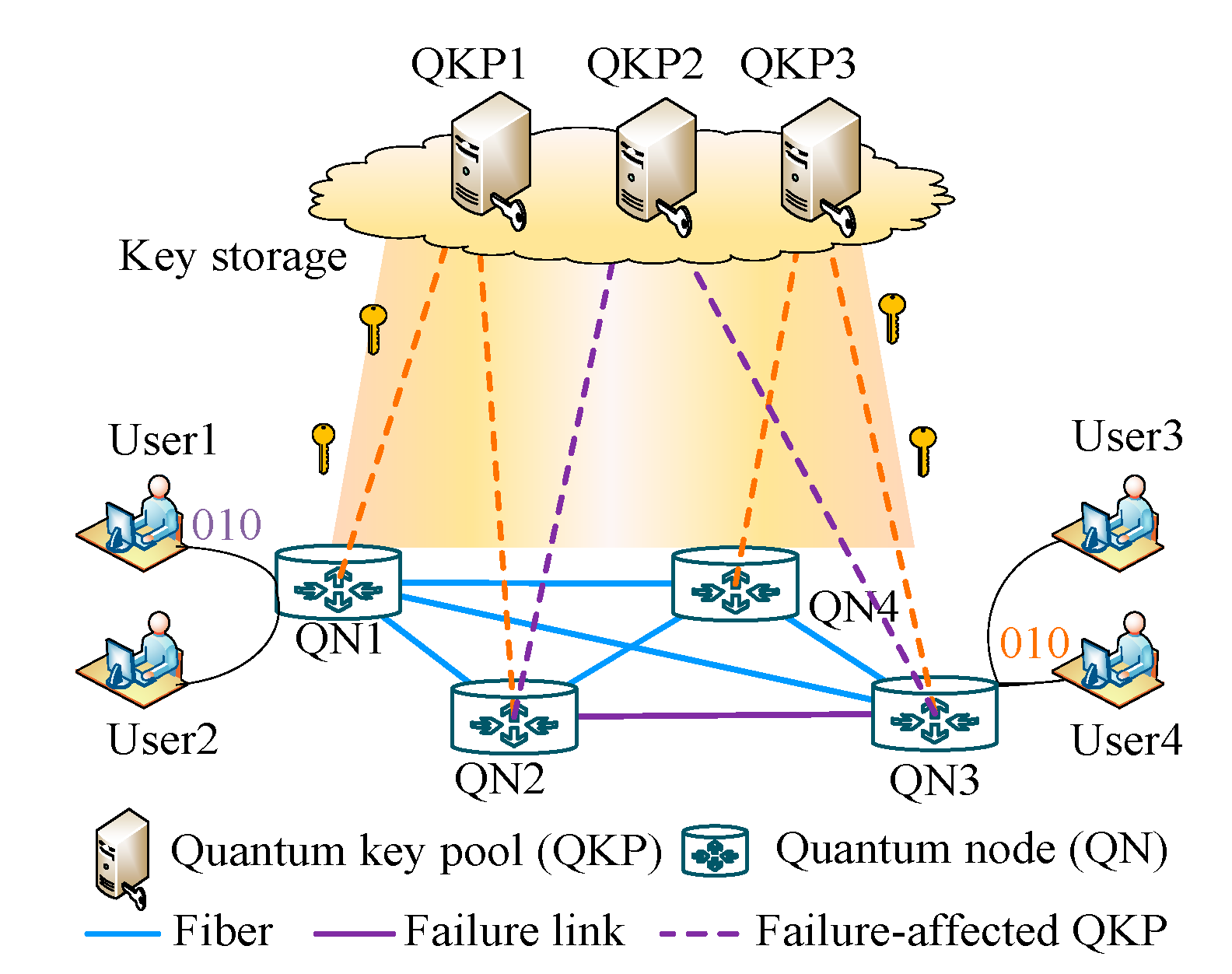
5.2. Construction of QKP in the Networks
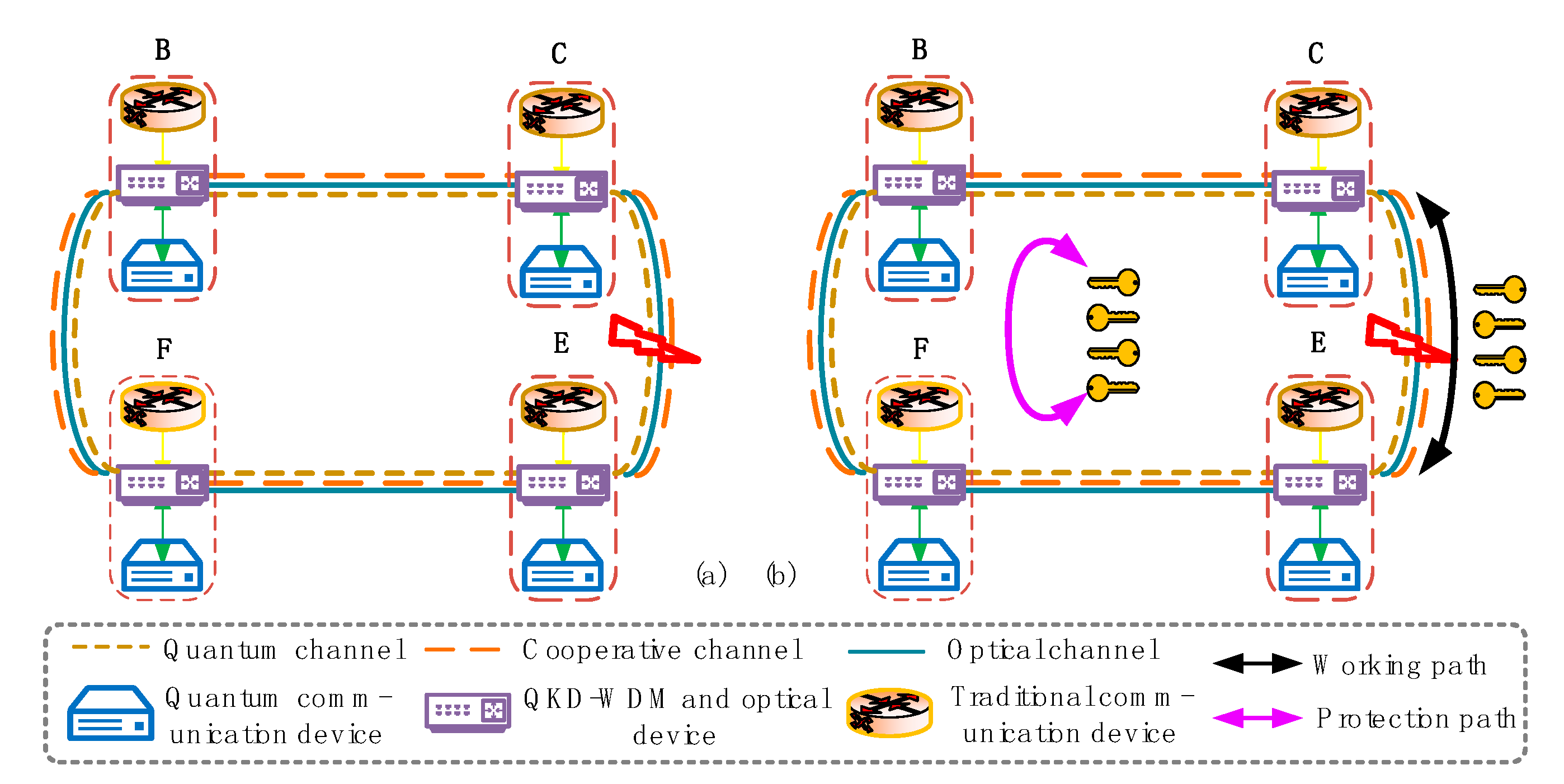
5.3. Survivability of the Networks
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Paul, A.M.D. The Principles of Quantum Mechanics, 3rd ed.; Clarendon Press: Oxford, UK, 1947. [Google Scholar]
- Lo, H.K.; Curty, M.; Tamaki, K. Secure quantum key distribution. Nat. Photonics 2014, 8, 595–604. [Google Scholar] [CrossRef]
- Wang, W.; Zhao, Y.L.; Yu, X.S.; Chen, B.W.; Zhang, J. Resilient Fiber-based Quantum Key Distribution (QKD) Networks with Secret-key Re-allocation Strategy. In Proceedings of the OFC, San Diego, CA, USA, 3–7 March 2019. [Google Scholar]
- Islam, N.T.; Lim, C.C.W.; Cahall, C.; Kim, J.; Gauthier, D.J. Provably secure and high-rate quantum key distribution with time-bin qudits. Sci. Adv. 2017, 3, 1–6. [Google Scholar] [CrossRef]
- Beatrice, D.L.; Davide, B.; Daniele, C.; Yunhong, D.; Kjeld, D.; Karsten, R.; Leif, O. Experimental demonstration of the DPTS QKD protocol over a 170 km fiber link. Appl. Phys. Lett. 2019, 114. [Google Scholar] [CrossRef]
- Mercian, A.; Mcgarry, M.P.; Reisslein, M.; Kellerer, W. Software defined optical networks (SDONs): A Comprehensive Survey. IEEE Commun. Surv. Tuts 2016, 18, 2738–2786. [Google Scholar]
- Partha, B.; Zhang, S.Q.; Pulak, C.; Sang-Soo, L.; Jong, H.L.; Biswanath, M. Software-defined optical networks (SDONs): A survey. Photonic Netw. Commun. 2014, 28, 4–18. [Google Scholar]
- Cao, Y.; Zhao, Y.L.; Yu, X.S.; Cheng, L.J.; Li, Z.Q.; Liu, G.J.; Zhang, J. Experimental Demonstration of End-to-End Key on Demand Service Provisioning over Quantum Key Distribution Networks with Software Defined Networking. In Proceedings of the OFC, San Diego, CA, USA, 3–7 March 2019. [Google Scholar]
- Cao, Y.; Zhao, Y.L.; Colman-Meixner, C.; Yu, X.S.; Zhang, J. Key on demand (KoD) for software-defined optical networks secured by quantum key distribution (QKD). Opt. Express 2017, 25, 26453–26467. [Google Scholar] [CrossRef] [PubMed]
- Zhao, Y.L.; Cao, Y.; Wang, W.; Wang, H.; Yu, X.S.; Zhang, J.; Massimo, T.; Wu, Y.; Biswanath, M. Resource allocation in optical networks secured by quantum key distribution. IEEE Commun. Mag. 2018, 56, 130–137. [Google Scholar] [CrossRef]
- Cao, Y.; Zhao, Y.L.; Yu, X.S.; Wu, Y. Resource assignment strategy in optical networks integrated with quantum key distribution. J. Opt. Commun. Netw. 2017, 9, 995–1004. [Google Scholar] [CrossRef]
- Cao, Y.; Zhao, Y.L.; Li, J.; Lin, R.; Chen, J.J. Reinforcement Learning Based Multi-Tenant Secret-Key Assignment for Quantum Key Distribution Networks. In Proceedings of the OFC, San Diego, CA, USA, 3–7 March 2019. [Google Scholar]
- Wang, H.; Zhao, Y.L.; Yu, X.S.; Ma, Z.Z.; Wang, J.Q.; Avishek, N.; Yi, L.T.; Zhang, J. Protection Schemes for Key Services in Optical Networks Secured by Quantum Key Distribution (QKD). J. Opt. Commun. Netw. 2018, 3, 67–78. [Google Scholar] [CrossRef]
- Cao, Y.; Zhao, Y.L.; Wu, Y.; Yu, X.S.; Zhang, J. Time-scheduled quantum key distribution (QKD) over WDM networks. J. Lightwave Technol. 2018, 36, 3382–3395. [Google Scholar] [CrossRef]
- Alejandro, A.; Emilio, H.-S.; Paul, A.H.; Jaume, M.; Alasdair, B.P.; Philip, S.; Jake, E.K.; Chris, E.; John, G.R.; Mark, G.T.; et al. Secure NFV Orchestration Over an SDN-Controlled Optical Network with Time-Shared Quantum Key Distribution Resources. J. Lightwave Technol. 2017, 35, 1357–1362. [Google Scholar]
- Aguado, M.A.; Martín, A.V.; López, D.R.; Peev, M.; Martínez, M.J.; Rosales, B.J.L.; Iglesia, F.; Gómez, M.; Hugues, S.E.; Lord, A.; et al. Quantum-Aware Software Defined Networks. In Proceedings of the QCrypt 2016, Washington, DC, USA, 12–16 September 2016. [Google Scholar]
- Yu, W.; Zhao, B.; Yan, Z. Software defined quantum key distribution network. In Proceedings of the ICCC, Chengdu, China, 13–16 December 2017. [Google Scholar]
- Alejandro, A.; Victor, L.; Jesus, M.-M.; Momtchil, P.; Diego, L.; Vicente, M. Hybrid conventional and quantum security for software defined and virtualized networks. IEEE/OSA J. Opt. Commun. Netw. 2017, 9, 819–825. [Google Scholar]
- Alejandro, A.; Victor, L.; Jesus, M.-M.; Momtchil, P.; Diego, L.; Vicente, M. Virtual network function deployment and service automation to provide end-to-end quantum encryption. IEEE/OSA J. Opt. Commun. Netw. 2018, 10, 421–430. [Google Scholar]
- Dasari, V.R.; Sadlier, R.J.; Geerhart, B.E.; Snow, N.A.; Williams, B.P.; Humble, T.S. Software-defined network abstractions and configuration interfaces for building programmable quantum networks. In Proceedings of the SPIE 10212, Advanced Photon Counting Techniques XI, Anaheim, CA, USA, 5 May 2017; p. 102120U. [Google Scholar]
- Travis, S.H.; Ronald, J.S.; Brian, P.W.; Ryan, C.P. Software-defined quantum network switching. In Proceedings of the SPIE 10652, Disruptive Technologies in Information Sciences, Orlando, FL, USA, 9 May 2018; p. 106520B. [Google Scholar]
- Chistyakov, V.V.; Sadov Oleg, L.; Vasiliev, A.B.; Egorov, V.I.; Kompaniets, M.V.; Fedchenkov, P.V.; Lazo, O.I.; Shevel, A.E.; Buldakov, N.V.; Gleim, A.V.; et al. Software-defined subcarrier wave quantum networking operated by OpenFlow protocol. arXiv 2017, arXiv:arXiv170909081C. [Google Scholar]
- Ou, Y.; Hugues-Salas, E.; Ntavou, F.; Wang, R.; Bi, Y.; Yan, S.Y.; Kanellos, G.; Nejabati, R.; Simeonidou, D. Field-Trial of Machine Learning-Assisted Quantum Key Distribution (QKD) Networking with SDN. In Proceedings of the ECOC 2018, Roma, Italy, 23–27 September 2018. [Google Scholar]
- Hugues-Salas, E.; Ntavou, F.; Ou, Y.; Kennard, J.E.; White, C.; Gkounis, D.; Nikolovgenis, K.; Kanellos, G.; Erven, C.; Lord, A.; et al. Experimental Demonstration of DDoS Mitigation over a Quantum Key Distribution (QKD) Network Using Software Defined Networking (SDN). In Proceedings of the OFC 2018, San Diego, CA, USA, 11–15 March 2018. [Google Scholar]
- Varnava, C.; Stevenson, R.M.; Nilsson, J.; Skiba-Szymanska, J.; Dzurňák, B.; Lucamarini, M.; Penty, R.V.; Farrer, I.; Ritchie, D.A.; Shields, A.J. An entangled-LED-driven quantum relay over 1km. NPJ Quantum Inform. 2016, 2, 16006. [Google Scholar] [CrossRef]
- Stacey, W.; Annabestani, R.; Xiongfeng, M.; Lütkenhaus, N. The Security of Quantum Key Distribution using a Simplified Trusted Relay. Phys. Rev. A 2014, 91, 1–11. [Google Scholar] [CrossRef]
- Stephanie, W.; David, E.; Ronald, H. Quantum internet: A vision for the road ahead. Science 2019, 362, 1–9. [Google Scholar]
- McCormick, C.F.; Marino, A.M.; Boyer, V.; Lett, P.D. Strong low-frequency quantum correlations from a four-wave-mixing amplifier. Phys. Rev. A 2008, 78, 043816. [Google Scholar] [CrossRef]
- Boris, K.; Charles, C.W.L.; Raphael, H.; Nicolas, G.; Ming, J.L.; Daniel, N.; Bruno, S.; Rob, T.; Hugo, Z. Provably Secure and Practical Quantum Key Distribution over 307 km of Optical Fibre. Nat. Photon. 2015, 9, 163–168. [Google Scholar]
- Beatrice, D.L.; Davide, B.; Daniele, C.; Francesco, D.R. Record-High Secret Key Rate for Joint Classical and Quantum Transmission Over a 37-Core Fiber. In Proceedings of the IPC, Hilton Palacio del Rio, San Antonio, TX, USA, 4–7 December 2018. [Google Scholar]
- Ken-ichiro, Y.; Mikio, F.; Akihiro, T.; Seigo, T.; Yoshihiro, N.; Akihisa, T.; Shigehito, M.; Taro, Y.; Zhen, W.; Masahide, S.; et al. High-speed wavelength-division multiplexing quantum key distribution system. Opt. Lett. 2012, 37, 223–225. [Google Scholar]
- Charles, H.B.; Gilles, B. Quantum cryptography: Public key distribution and coin tossing. In Proceedings of the IEEE International Conference Computers, Systems, and Signal Processing, Bangalore, India, 9–12 December 1984. [Google Scholar]
- Davide, B.; Jesper, B.C.; Mario, A.U.C.; Yunhong, D.; Søren, F.; Karsten, R.; Leif, K.O. Two-dimensional distributed-phase-reference protocol for quantum key distribution. Sci. Rep. 2016, 6, 36756. [Google Scholar]



© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, H.; Zhao, Y.; Nag, A. Quantum-Key-Distribution (QKD) Networks Enabled by Software-Defined Networks (SDN). Appl. Sci. 2019, 9, 2081. https://doi.org/10.3390/app9102081
Wang H, Zhao Y, Nag A. Quantum-Key-Distribution (QKD) Networks Enabled by Software-Defined Networks (SDN). Applied Sciences. 2019; 9(10):2081. https://doi.org/10.3390/app9102081
Chicago/Turabian StyleWang, Hua, Yongli Zhao, and Avishek Nag. 2019. "Quantum-Key-Distribution (QKD) Networks Enabled by Software-Defined Networks (SDN)" Applied Sciences 9, no. 10: 2081. https://doi.org/10.3390/app9102081
APA StyleWang, H., Zhao, Y., & Nag, A. (2019). Quantum-Key-Distribution (QKD) Networks Enabled by Software-Defined Networks (SDN). Applied Sciences, 9(10), 2081. https://doi.org/10.3390/app9102081





