A Novel Method for Constructing the S-Box Based on Spatiotemporal Chaotic Dynamics
Abstract
:1. Introduction
- We choose the Non-adjacent Coupled Map Lattices (NCML) [28] spatiotemporal chaos system for constructing the S-box. It has more dynamical features than the traditional CML [29] and the logistic map, such as better randomness, more chaotic sequences, and no periodic windows. Moreover, it can resist the degradation of finite precision computation due to its high dimensional feature, which can increase the randomness of elements in the S-box. Additionally, the NCML chaotic system has been used in secure communication schemes due to its cryptographic features [30,31];
- Since the chaotic sequences generated by the NCML system are independent, we apply these independent chaotic sequences to implement the permutation and shuffle of the S-box, which can improve its BIC property and ability to resist linear password attacks;
- In the comparisons with the former schemes, the simulation and experimental results prove the superior properties of the proposed scheme. This scheme shows that the combination of the spatiotemporal chaotic system and S-box is a recommended approach for encryptions.
2. Preliminaries
- (1)
- Lyapunov exponents evaluate the divergence of nearby orbits and provide a qualitative view of the dynamical system. If a system has at least one positive Lyapunov exponent, the system is certainly in chaotic behaviors. The Lyapunov exponent of each lattice in the NCML system is positive, and between 0.0203 and 0.4351. This means that the NCML system’s dynamics is more complicated, which can resist the degradation under finite precision computation in modern computers.
- (2)
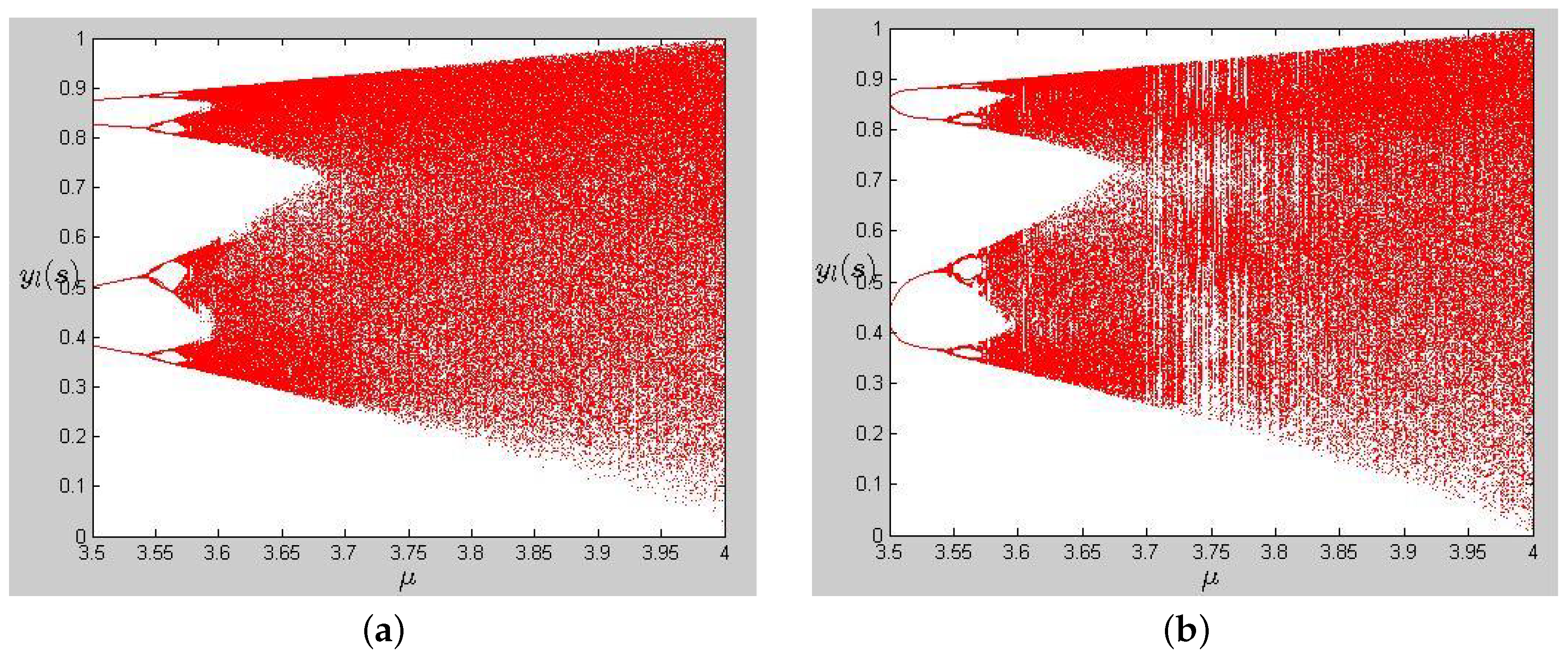
- In the bifurcation diagram of the NCML system, there is no periodic window, as shown in Figure 1a. By contrast, there are periodic windows in the bifurcation diagram of the CML system, as shown in Figure 1b. Therefore, the NCML system is more suitable for cryptography than the CML system due to no periodic windows.
- (3)
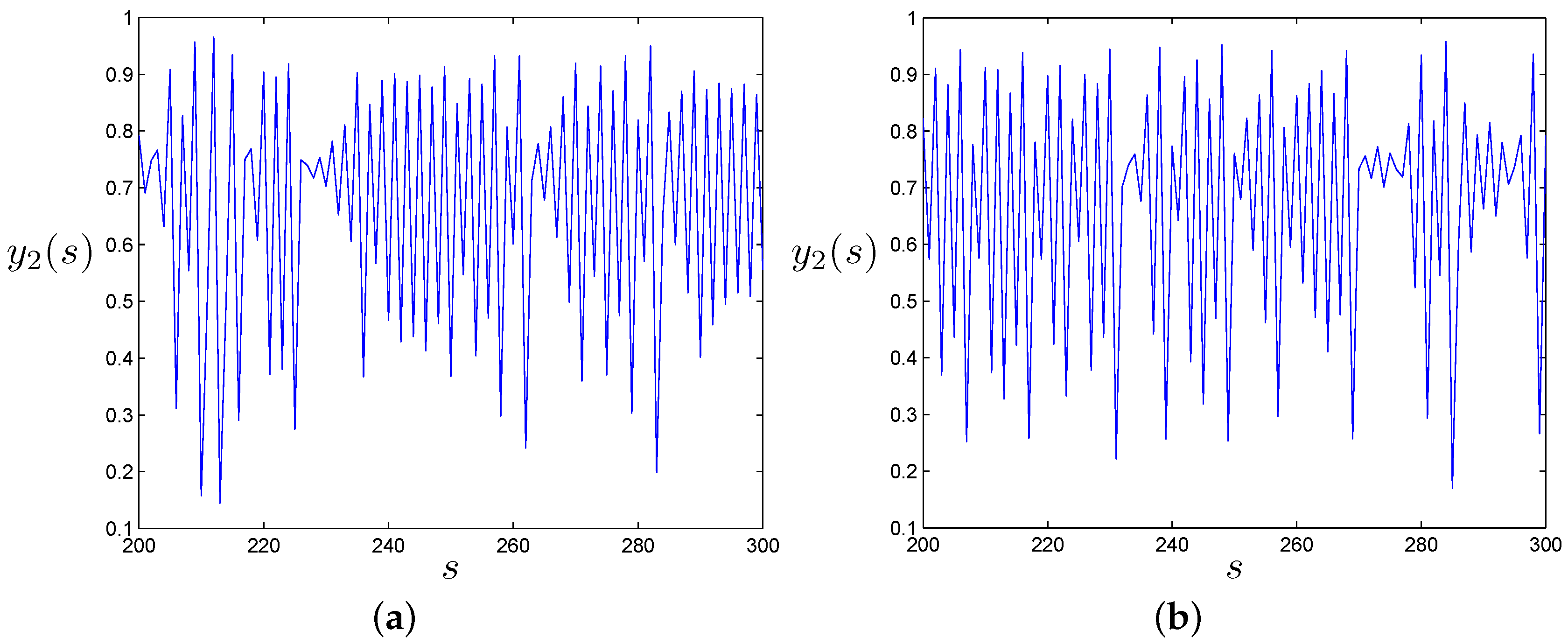
- The chaotic trajectory of NCML system is as random as that of the CML system, as shown in Figure 2. The random chaotic sequences are suitable for the construction of a random S-box.
- (4)
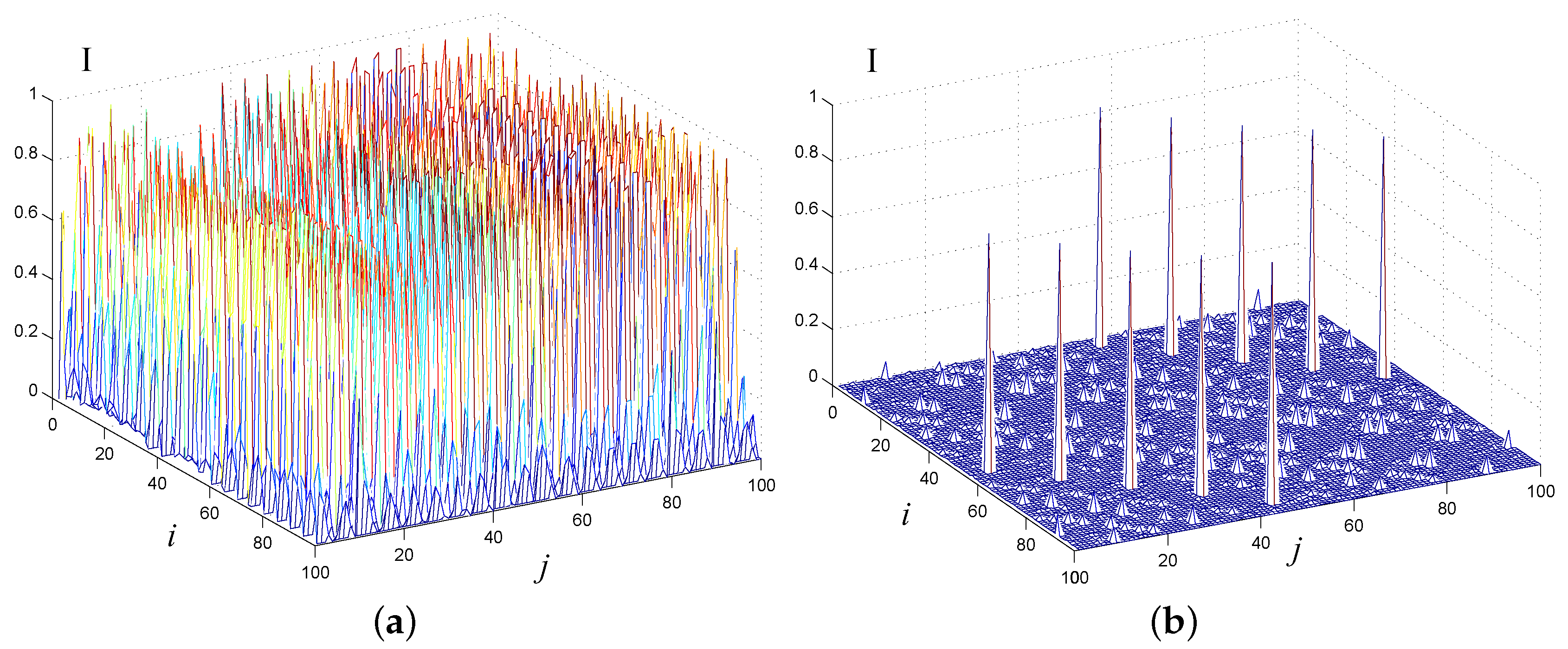
- The NCML chaotic system has very small mutual information values between chaotic trajectories. Mutual information can be used to evaluate the independence of two chaotic trajectories (named and ), which is defined as:
3. The Proposed Method for Constructing the S-Box
- Step 1.
- Iterating Equation (2), we obtain N chaotic sequences.
- Step 2.
- Using the chaotic sequence , we construct a new sequence by:where and denotes the (100 + i)th value of the 10th sequence of N chaotic sequences.
- Step 3.
- Putting the elements of in ascending order, we get a sorted sequence and an address sequence satisfying .
- Step 4.
- Reconvert the sequence to a matrix .
- Step 5.
- We get the values of u and v by:where and the relations of satisfy the Arnold cat map expressed by:
- Step 6.
- With the help of Equation (6), we swap the values of and .
4. Randomness Tests of the Constructed S-Box
5. Performance Analysis of the Constructed S-Box
5.1. Bijective Property
5.2. Nonlinearity
5.3. Strict Avalanche Criterion
5.4. Output Bits Independence Criterion
5.5. The Equiprobable Input/Output XOR Distribution
5.6. Linear Approximation Probability
6. Conclusions and Future Research
Author Contributions
Funding
Conflicts of Interest
References
- Berry, M.V.; Lewis, Z.V.; Nye, J.F. On the Weierstrass-Mandelbrot fractal function. Proc. R. Soc. Lond. 1980, 370, 459–484. [Google Scholar] [CrossRef]
- Guariglia, E. Entropy and Fractal Antennas. Entropy 2016, 18, 84. [Google Scholar] [CrossRef]
- Guido, R.C.; Addison, P.S.; Walker, J. Introducing wavelets and time–frequency analysis. IEEE Eng. Med. Biol. Mag. 2009, 28, 13. [Google Scholar] [CrossRef] [PubMed]
- Guariglia, E. Harmonic Sierpinski Gasket and Applications. Entropy 2018, 20, 714. [Google Scholar] [CrossRef]
- Webster, A.F.; Tavares, S.E. On the design of S-boxes. In Advances in Cryptology, Proceedings of the Conference on the Theory and Application of Cryptographic Techniques (CRYPTO_85), Santa Barbara, CA, USA, 18–22 August 1985; Springer: Berlin/Heidelberg, Germany, 1986; pp. 523–534. [Google Scholar]
- Detombe, J.; Tavares, S. Constructing large cryptographically strong S-boxes. In Advances in Cryptology, Proceedings of the International Workshop on the Theory and Application of Cryptographic Techniques (AUSCRYPT ’92), Gold Goast, QLD, Australia, 13–16 December 1992; Springer: Berlin/Heidelberg, Germany, 1992; pp. 165–181. [Google Scholar]
- Biham, E.; Shamir, A. Differential cryptanalysis of DES-like cryptosystems. J. Cryptol. 1991, 4, 3–72. [Google Scholar] [CrossRef]
- Dawson, M.H.; Tavares, S.E. An expanded set of S-box design criteria based on information theory and its relation to differential-like attacks. In Advances in Cryptology, Proceedings of the Workshop on the Theory and Application of of Cryptographic Techniques (EURO-CRYPT_91), Brighton, UK, 8–11 April 1991; Springer: Berlin/Heidelberg, Germany, 1991; pp. 352–367. [Google Scholar]
- Matsui, M. Linear cryptanalysis method of DES cipher. In Advances in Cryptology, Proceedings of the Workshop on the Theory and Application of of Cryptographic Techniques (EURO-CRYPT_93), Lofthus, Norway, 23–27 May 1993; Springer: Berlin/Heidelberg, Germany, 1994; pp. 386–397. [Google Scholar]
- Adams, C.; Tavares, S. Good S-boxes are easy to find. In Advances in Cryptology, Proceedings of the Conference on the Theory and Application of Cryptology (CRYPTO_89), Santa Barbara, CA, USA, 20–24 August 1989; Springer: New York, NY, USA, 1989; pp. 612–615. [Google Scholar]
- Jakimoski, G.; Kocarev, L. Chaos and cryptography: Block encryption ciphers based on chaotic maps. IEEE Trans. Circuits Syst. I Fundam. Theory Appl. 2001, 48, 163–169. [Google Scholar] [CrossRef]
- Amigó, J.M.; Szczepanski, J.; Kocarev, L. A chaos-based approach to the design of cryptographically secure substitutions. Phys. Lett. A 2005, 343, 55–60. [Google Scholar] [CrossRef]
- Tang, G.; Liao, X.; Chen, Y. A novel method for designing S-boxes based on chaotic maps. Chaos Solitons Fractals 2005, 23, 413–419. [Google Scholar] [CrossRef]
- Chen, G.; Chen, Y.; Liao, X. An extended method for obtaining S-boxes based on three-dimensional chaotic baker maps. Chaos Solitons Fractals 2007, 31, 571–579. [Google Scholar] [CrossRef]
- Wang, Y.; Wong, K.W.; Liao, X.; Xiang, T. A block cipher with dynamic S-boxes based on tent map. Commun. Nonlinear Sci. Numer. Simul. 2009, 14, 3089–3099. [Google Scholar] [CrossRef]
- Özkaynak, F.; Özer, A.B. A method for designing strong S-boxes based on chaotic Lorenz system. Phys. Lett. A 2010, 374, 3733–3738. [Google Scholar] [CrossRef]
- Hussain, I.; Shah, T.; Gondal, M.A. A novel approach for designing substitution-boxes based on nonlinear chaotic algorithm. Nonlinear Dyn. 2012, 70, 1791–1794. [Google Scholar] [CrossRef]
- Khan, M.; Shah, T.; Mahmood, H.; Gondal, M.A. An efficient method for the construction of block cipher with multi-chaotic systems. Nonlinear Dyn. 2013, 71, 489–492. [Google Scholar] [CrossRef]
- Lambić, D. A novel method of S-box design based on chaotic map and composition method. Chaos Solitons Fractals 2014, 58, 16–21. [Google Scholar] [CrossRef]
- Liu, G.; Yang, W.; Liu, W.; Dai, Y. Designing S-boxes based on 3-D four-wing autonomous chaotic system. Nonlinear Dyn. 2015, 82, 1867–1877. [Google Scholar] [CrossRef]
- Belazi, A.; Ellatif, A.A.A. A simple yet efficient S-box method based on chaotic sine map. Optik 2017, 130, 1438–1444. [Google Scholar] [CrossRef]
- Belazi, A.; Khan, M.; El-Latif, A.A.A.; Belghith, S. Efficient cryptosystem approaches: S-boxes and permutation substitution-based encryption. Nonlinear Dyn. 2017, 87, 337–361. [Google Scholar] [CrossRef]
- Ullah, A.; Jamal, S.S.; Shah, T. A novel construction of substitution box using a combination of chaotic maps with improved chaotic range. Nonlinear Dyn. 2017, 88, 2757–2769. [Google Scholar] [CrossRef]
- Khan, M.; Shah, T.; Mahmood, H.; Gondal, M.A.; Hussain, I. A novel technique for the construction of strong S-boxes based on chaotic Lorenz systems. Nonlinear Dyn. 2012, 70, 2303–2311. [Google Scholar] [CrossRef]
- Al Solami, E.; Ahmad, M.; Volos, C.; Najam Doja, M.; Mohd Sufyan Beg, M. A New Hyperchaotic System-Based Design for Efficient Bijective Substitution-Boxes. Entropy 2018, 20, 525. [Google Scholar] [CrossRef]
- Zhang, Y.Q.; Wang, X.Y. Analysis and improvement of a chaos-based symmetric image encryption scheme using a bit-level permutation. Nonlinear Dyn. 2014, 77, 687–698. [Google Scholar] [CrossRef]
- Li, C.; Lin, D.; Lü, J.; Hao, F. Cryptanalyzing an image encryption algorithm based on autoblocking and electrocardiography. IEEE MultiMedia 2018. [Google Scholar] [CrossRef]
- Zhang, Y.Q.; Wang, X.Y. Spatiotemporal chaos in Arnold coupled logistic map lattice. Nonlinear Anal. Model. Control 2013, 4, 526–541. [Google Scholar]
- Kaneko, K. Theory and Applications of Coupled Map Lattices, 1st ed.; Wiley: New York, NY, USA, 1993. [Google Scholar]
- Zhang, Y.Q.; Wang, X.Y. A new image encryption algorithm based on non-adjacent coupled map lattices. Appl. Soft Comput. J. 2015, 26, 10–20. [Google Scholar] [CrossRef]
- Zhang, Y.; Wang, X.; Liu, L.; Liu, J. Fractional order spatiotemporal chaos with delay in spatial nonlinear coupling. Int. J. Bifurc. Chaos 2018, 28, 1850020. [Google Scholar] [CrossRef]
- Bassham, L.E., III; Rukhin, A.L.; Soto, J.; Nechvatal, J.R.; Smid, M.E.; Barker, E.B.; Leigh, S.D.; Levenson, M.; Vangel, M.; Banks, D.L.; et al. SP 800-22 Rev. 1a. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications. Appl. Phys. Lett. 2010, 22, 1645–1679. [Google Scholar]
- Wang, Y.; Xie, Q.; Wu, Y.; Du, B. A Software for S-box Performance Analysis and Test. In Proceedings of the International Conference on Electronic Commerce and Business Intelligence, Beijing, China, 6–7 June 2009; pp. 125–128. [Google Scholar]
- Cusick, T.W.; Stǎnicǎ, P. Cryptographic Boolean Functions and Applications; Academic Press: San Diego, CA, USA, 2009. [Google Scholar]

| 161 | 239 | 162 | 99 | 116 | 136 | 222 | 234 | 215 | 134 | 208 | 26 | 237 | 108 | 238 | 66 |
| 179 | 209 | 45 | 51 | 249 | 37 | 137 | 168 | 195 | 114 | 221 | 98 | 149 | 115 | 194 | 25 |
| 65 | 35 | 127 | 39 | 6 | 12 | 146 | 94 | 135 | 144 | 104 | 48 | 198 | 2 | 118 | 83 |
| 175 | 93 | 11 | 253 | 182 | 102 | 252 | 19 | 197 | 248 | 233 | 167 | 235 | 10 | 185 | 123 |
| 170 | 3 | 199 | 250 | 92 | 218 | 90 | 228 | 109 | 178 | 42 | 206 | 72 | 217 | 160 | 193 |
| 15 | 78 | 101 | 124 | 24 | 151 | 176 | 7 | 113 | 41 | 181 | 203 | 80 | 46 | 131 | 138 |
| 28 | 69 | 224 | 23 | 190 | 85 | 147 | 247 | 254 | 16 | 84 | 225 | 145 | 20 | 244 | 130 |
| 204 | 61 | 55 | 103 | 31 | 91 | 60 | 79 | 143 | 227 | 243 | 241 | 76 | 174 | 5 | 40 |
| 47 | 212 | 192 | 22 | 1 | 111 | 121 | 112 | 119 | 186 | 126 | 251 | 205 | 62 | 189 | 50 |
| 34 | 96 | 163 | 125 | 82 | 59 | 70 | 38 | 57 | 216 | 133 | 67 | 152 | 223 | 165 | 75 |
| 157 | 188 | 154 | 246 | 88 | 202 | 52 | 87 | 81 | 158 | 210 | 184 | 240 | 226 | 105 | 142 |
| 164 | 245 | 4 | 32 | 86 | 128 | 120 | 71 | 14 | 13 | 18 | 110 | 33 | 53 | 150 | 56 |
| 68 | 29 | 242 | 17 | 187 | 139 | 229 | 155 | 21 | 141 | 207 | 214 | 255 | 169 | 166 | 100 |
| 36 | 191 | 77 | 54 | 27 | 49 | 180 | 230 | 148 | 30 | 232 | 95 | 213 | 132 | 89 | 159 |
| 219 | 236 | 201 | 107 | 44 | 173 | 8 | 64 | 211 | 172 | 183 | 43 | 97 | 220 | 106 | 58 |
| 129 | 156 | 140 | 117 | 73 | 63 | 153 | 171 | 0 | 9 | 196 | 231 | 177 | 122 | 74 | 200 |
| NIST-800-22 Tests | p-Value | Result |
|---|---|---|
| Frequency Test | 1.000000 | SUCCESS |
| Block Frequency Test | 0.102530 | SUCCESS |
| Cumulative Sums Test | 0.984155 | SUCCESS |
| Runs Test | 0.658531 | SUCCESS |
| Longest Run of Ones Test | 1.000000 | SUCCESS |
| Rank Test | 0.481248 | SUCCESS |
| Discrete Fourier Transform Test | 0.208675 | SUCCESS |
| Nonperiodic Template Matchings Test | 0.844144 | SUCCESS |
| Overlapping Template Matchings Test | 0.282761 | SUCCESS |
| Approximate Entropy Test | 0.024931 | SUCCESS |
| Serial Test | 0.645337 | SUCCESS |
| Linear Complexity Test | 0.481431 | SUCCESS |
| Random Excursions Test | TEST NOT APPLICABLE | |
| Random Excursions Variant Test | TEST NOT APPLICABLE | |
| Universal Statistical Test | TEST NOT APPLICABLE |
| S-Boxes | Max | Min | Average |
|---|---|---|---|
| The obtained S-box | 108 | 102 | 104.5 |
| S-box based on CML | 106 | 100 | 103 |
| S-box proposed in [11] | 108 | 100 | 103.25 |
| S-box proposed in [13] | 109 | 103 | 104.88 |
| S-box proposed in [14] | 106 | 100 | 103 |
| S-box proposed in [16] | 106 | 100 | 103.25 |
| S-box proposed in [17] | 108 | 102 | 104.75 |
| S-box proposed in [18] | 108 | 98 | 103 |
| S-box proposed in [19] | 112 | 108 | 109.25 |
| S-box proposed in [20] | 108 | 104 | 105.8 |
| S-box proposed in [21] | 110 | 102 | 105.5 |
| S-box proposed in [22] | 108 | 102 | 105.25 |
| S-box 2 proposed in [23] | 108 | 102 | 106 |
| S-box proposed in [24] | 106 | 96 | 103 |
| S-box proposed in [25] | 110 | 106 | 108.5 |
| 0.4844 | 0.5313 | 0.4844 | 0.4688 | 0.4844 | 0.5000 | 0.5938 | 0.4844 |
| 0.4219 | 0.4688 | 0.5313 | 0.5000 | 0.4688 | 0.4531 | 0.4531 | 0.4531 |
| 0.5469 | 0.5469 | 0.4531 | 0.4688 | 0.5156 | 0.5469 | 0.5156 | 0.4688 |
| 0.4844 | 0.4375 | 0.5000 | 0.4375 | 0.4688 | 0.5625 | 0.6406 | 0.4375 |
| 0.5000 | 0.5156 | 0.4688 | 0.5000 | 0.5313 | 0.5000 | 0.5313 | 0.4688 |
| 0.4688 | 0.5313 | 0.5781 | 0.4844 | 0.4844 | 0.4844 | 0.5000 | 0.4531 |
| 0.5000 | 0.4688 | 0.5000 | 0.5000 | 0.5313 | 0.4531 | 0.4688 | 0.4688 |
| 0.5000 | 0.5313 | 0.5469 | 0.5156 | 0.4688 | 0.5469 | 0.4844 | 0.5781 |
| S-Boxes | Max | Min | Mean |
|---|---|---|---|
| The obtained S-box | 0.6406 | 0.4219 | 0.4980 |
| S-box based on CML | 0.6250 | 0.3750 | 0.5015 |
| S-box proposed in [11] | 0.5938 | 0.3750 | 0.5059 |
| S-box proposed in [13] | 0.5703 | 0.3984 | 0.4966 |
| S-box proposed in [14] | 0.6094 | 0.4219 | 0.5000 |
| S-box proposed in [16] | 0.5938 | 0.4219 | 0.5049 |
| S-box proposed in [17] | 0.5938 | 0.3906 | 0.5056 |
| S-box proposed in [18] | 0.5938 | 0.4063 | 0.5012 |
| S-box proposed in [19] | 0.5937 | 0.4375 | 0.5012 |
| S-box proposed in [20] | 0.5938 | 0.4219 | 0.4976 |
| S-box proposed in [21] | 0.5625 | 0.4375 | 0.5000 |
| S-box proposed in [22] | 0.5313 | 0.4297 | 0.4956 |
| S-box 2 proposed in [23] | - | - | 0.5020 |
| S-box proposed in [24] | 0.6250 | 0.3906 | 0.5039 |
| S-box proposed in [25] | 0.5937 | 0.4062 | 0.5017 |
| - | 106 | 106 | 106 | 106 | 104 | 102 | 104 |
| 106 | - | 100 | 100 | 106 | 104 | 108 | 102 |
| 106 | 100 | - | 106 | 108 | 106 | 104 | 108 |
| 106 | 100 | 106 | - | 100 | 104 | 108 | 104 |
| 106 | 106 | 108 | 100 | - | 104 | 108 | 106 |
| 104 | 104 | 106 | 104 | 104 | - | 102 | 102 |
| 102 | 108 | 104 | 108 | 108 | 102 | - | 106 |
| 104 | 102 | 108 | 104 | 106 | 102 | 106 | - |
| - | 0.5332 | 0.4785 | 0.5117 | 0.5215 | 0.5059 | 0.5137 | 0.5078 |
| 0.5332 | - | 0.5117 | 0.5078 | 0.5137 | 0.5332 | 0.5137 | 0.5039 |
| 0.4785 | 0.5117 | - | 0.5195 | 0.5000 | 0.5098 | 0.5039 | 0.5098 |
| 0.5117 | 0.5078 | 0.5195 | - | 0.4961 | 0.5137 | 0.4922 | 0.5059 |
| 0.5215 | 0.5137 | 0.5000 | 0.4961 | - | 0.4766 | 0.5020 | 0.5020 |
| 0.5059 | 0.5332 | 0.5098 | 0.5137 | 0.4766 | - | 0.4902 | 0.5117 |
| 0.5137 | 0.5137 | 0.5039 | 0.4922 | 0.5020 | 0.4902 | - | 0.5195 |
| 0.5078 | 0.5039 | 0.5098 | 0.5059 | 0.5020 | 0.5117 | 0.5195 | - |
| S-Boxes | BIC-SAC | BIC-Nonlinearity |
|---|---|---|
| The obtained S-box | 0.5075 | 104.64 |
| S-box based on CML | 0.5039 | 103.57 |
| S-box proposed in [11] | 0.5031 | 104.29 |
| S-box proposed in [13] | 0.5044 | 102.96 |
| S-box proposed in [14] | 0.5024 | 103.14 |
| S-box proposed in [16] | 0.5010 | 103.71 |
| S-box proposed in [17] | 0.5022 | 104.07 |
| S-box proposed in [18] | 0.4989 | 104.07 |
| S-box proposed in [19] | - | 108.21 |
| S-box proposed in [20] | 0.5032 | 104.5 |
| S-box proposed in [21] | 0.4970 | 103.78 |
| S-box proposed in [22] | 0.4996 | 103.8 |
| S-box 2 proposed in [23] | 0.5050 | 103 |
| S-box proposed in [24] | 0.5010 | 100.36 |
| S-box proposed in [25] | 0.5006 | 104 |
| 6 | 6 | 6 | 8 | 6 | 6 | 8 | 6 | 6 | 6 | 8 | 6 | 6 | 6 | 8 | 6 |
| 6 | 8 | 8 | 6 | 6 | 6 | 6 | 6 | 6 | 6 | 6 | 6 | 8 | 6 | 6 | 8 |
| 6 | 6 | 8 | 6 | 8 | 6 | 6 | 6 | 6 | 6 | 6 | 8 | 6 | 6 | 8 | 8 |
| 8 | 6 | 6 | 6 | 6 | 8 | 6 | 6 | 6 | 8 | 6 | 6 | 8 | 6 | 8 | 6 |
| 4 | 6 | 6 | 8 | 8 | 6 | 8 | 6 | 6 | 6 | 10 | 8 | 6 | 6 | 8 | 6 |
| 6 | 6 | 6 | 6 | 8 | 8 | 6 | 6 | 6 | 8 | 6 | 6 | 8 | 10 | 6 | 6 |
| 8 | 6 | 6 | 8 | 6 | 8 | 6 | 6 | 6 | 6 | 6 | 8 | 8 | 6 | 8 | 6 |
| 6 | 6 | 6 | 6 | 8 | 8 | 6 | 6 | 6 | 8 | 6 | 8 | 8 | 8 | 8 | 6 |
| 8 | 6 | 8 | 6 | 6 | 6 | 8 | 6 | 8 | 8 | 6 | 8 | 6 | 6 | 6 | 8 |
| 8 | 8 | 6 | 8 | 6 | 8 | 6 | 6 | 6 | 6 | 12 | 10 | 8 | 8 | 10 | 6 |
| 8 | 10 | 8 | 6 | 6 | 6 | 6 | 6 | 6 | 6 | 8 | 6 | 6 | 8 | 8 | 6 |
| 6 | 8 | 6 | 6 | 8 | 8 | 8 | 8 | 8 | 8 | 8 | 6 | 6 | 8 | 8 | 6 |
| 8 | 6 | 10 | 6 | 8 | 6 | 6 | 6 | 8 | 6 | 6 | 8 | 6 | 6 | 6 | 8 |
| 6 | 6 | 4 | 6 | 6 | 6 | 8 | 6 | 8 | 6 | 8 | 8 | 6 | 6 | 6 | 6 |
| 6 | 8 | 8 | 6 | 8 | 6 | 6 | 8 | 6 | 6 | 8 | 6 | 8 | 6 | 6 | 6 |
| 8 | 6 | 6 | 8 | 6 | 8 | 6 | 6 | 6 | 8 | 6 | 6 | 8 | 8 | 6 | - |
| S-Boxes | MaxDP |
|---|---|
| The obtained S-box | 0.0469 |
| S-box based on CML | 0.0391 |
| S-box proposed in [11] | 0.0469 |
| S-box proposed in [13] | 0.0391 |
| S-box proposed in [14] | 0.0547 |
| S-box proposed in [16] | 0.0391 |
| S-box proposed in [17] | 0.0469 |
| S-box proposed in [18] | 0.0469 |
| S-box proposed in [20] | 0.0391 |
| S-box proposed in [21] | 0.0468 |
| S-box proposed in [22] | 0.0391 |
| S-box 2 proposed in [23] | 0.0469 |
| S-box proposed in [24] | 0.0391 |
| S-Boxes | MaxLP |
|---|---|
| The obtained S-box | 0.1250 |
| S-box based on CML | 0.1406 |
| S-box proposed in [11] | 0.1250 |
| S-box proposed in [13] | 0.1328 |
| S-box proposed in [14] | 0.1328 |
| S-box proposed in [16] | 0.1328 |
| S-box proposed in [17] | 0.1250 |
| S-box proposed in [18] | 0.1484 |
| S-box proposed in [21] | 0.1250 |
| S-box proposed in [22] | 0.1562 |
| S-box 2 proposed in [23] | 0.1250 |
| S-box proposed in [24] | 0.1484 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, L.; Zhang, Y.; Wang, X. A Novel Method for Constructing the S-Box Based on Spatiotemporal Chaotic Dynamics. Appl. Sci. 2018, 8, 2650. https://doi.org/10.3390/app8122650
Liu L, Zhang Y, Wang X. A Novel Method for Constructing the S-Box Based on Spatiotemporal Chaotic Dynamics. Applied Sciences. 2018; 8(12):2650. https://doi.org/10.3390/app8122650
Chicago/Turabian StyleLiu, Liyan, Yingqian Zhang, and Xingyuan Wang. 2018. "A Novel Method for Constructing the S-Box Based on Spatiotemporal Chaotic Dynamics" Applied Sciences 8, no. 12: 2650. https://doi.org/10.3390/app8122650
APA StyleLiu, L., Zhang, Y., & Wang, X. (2018). A Novel Method for Constructing the S-Box Based on Spatiotemporal Chaotic Dynamics. Applied Sciences, 8(12), 2650. https://doi.org/10.3390/app8122650




