1. Introduction
The expanding IoT is affecting multiple industries, with the total number of connected devices anticipated to nearly double, growing from 15.9 billion in 2023 to above 32.1 billion by 2030 [
1]. As these networks grow, they increasingly demand frameworks to support security, scalability, interoperability, and data integrity. Traditional centralized systems face challenges in meeting these needs [
1], particularly in environments with limited resource devices with no central authority. As a distributed digital ledger [
2], blockchain technology offers a tamper-resistant and scalable solution by leveraging cryptographic hashes and decentralized consensus mechanisms to share data securely between IoT systems [
3]. Initially developed to power Bitcoin [
4], blockchain applications have since expanded into numerous sectors, addressing critical needs, such as transaction verification and immutable record storage [
2]. With features such as decentralization, immutability, and robust data protection, blockchains provide a secure, transparent, and trustworthy framework that is well-suited for IoT applications [
5].
Incorporating blockchains into IoT ecosystems enables a decentralized trust model that supports secure peer-to-peer communication among devices without intermediaries. Blockchains’ immutable record-keeping and smart contract [
6] functionalities further strengthen IoT automation and security by ensuring that data remains unaltered once recorded. Integrating blockchains with the IoT boosts transparency and accountability through established audit trails and verifiable transactions, which are critical for supply chain management, smart cities, healthcare, and industrial automation.
This paper offers a comprehensive look at recent research on blockchain applications in the IoT. It explores the diverse blockchain architectures and protocols used in IoT settings and draws attention to significant trends and potential areas for further study. By analyzing the merging of these transformative technologies, this survey provides a perspective on how blockchains can enhance IoT networks, making them more secure, scalable, and transparent. Furthermore, it highlights the role of smart contracts and oracles in automating processes, reducing operational costs, and enabling trustless interaction. The survey also discusses the importance of layer 2 solutions, tokenization, and decentralized data sharing in addressing scalability challenges and fostering data sharing and real-time decision-making across IoT ecosystems.
2. Background
2.1. The Internet of Things (IoT)
The IoT is a collection of Internet-connected devices that are used in personal and industrial settings [
7]. IoT devices can range from sensors and controllers to household appliances [
8]. These devices, often headless with limited network capabilities and security features [
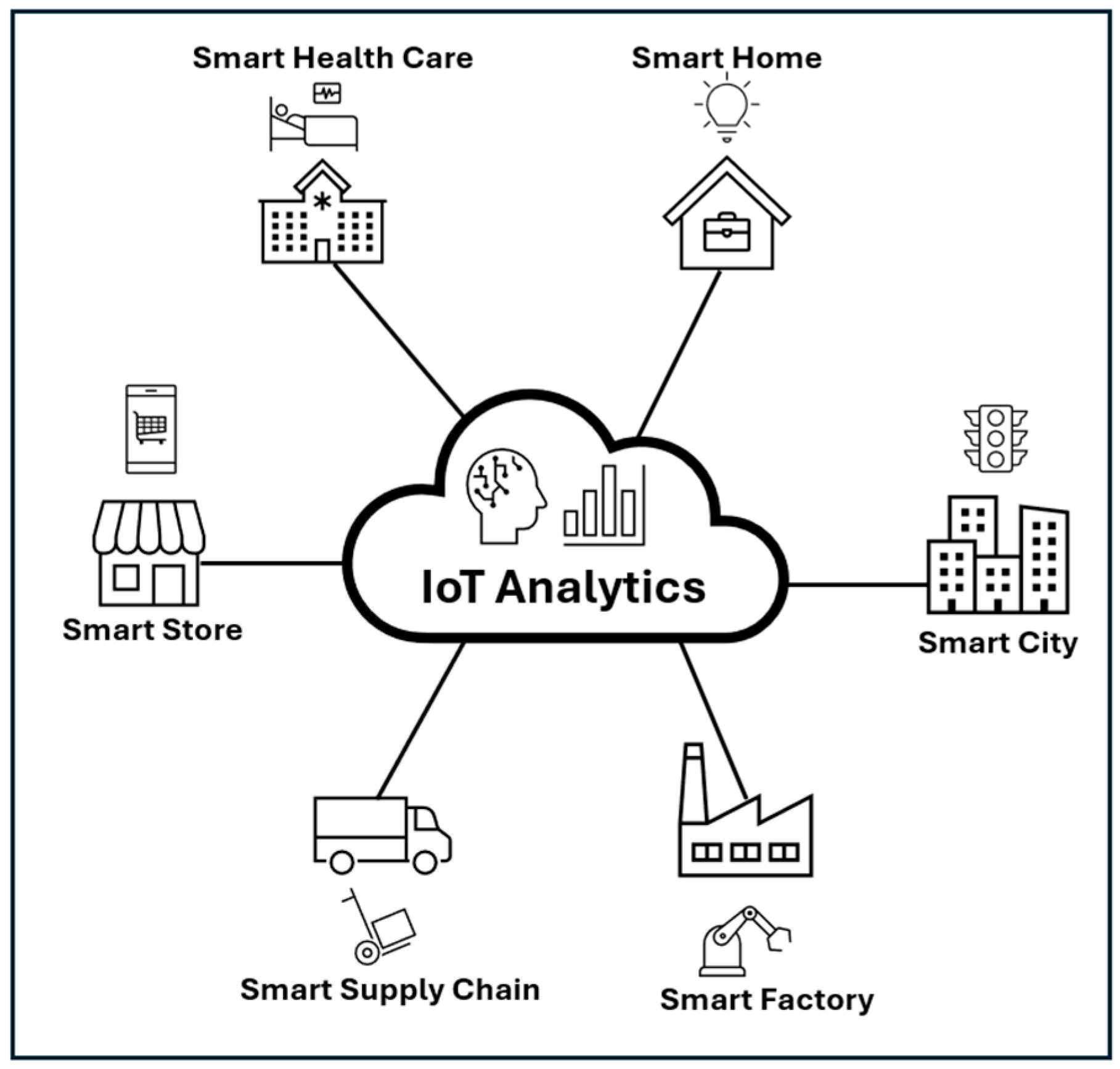
9], continuously collect telemetry and various readings that are fed into monitoring, management, control, and other intelligent systems. AI and AI algorithms can uncover valuable insights by processing and analyzing these data. They identify patterns, trends, and unusual events (anomalies) that can help businesses and organizations make more accurate predictions and informed decisions.
Figure 1 below shows some IoT applications in our daily lives, each of which provides a large amount of data that can be used for data analytics or for AI systems.
2.2. Blockchain
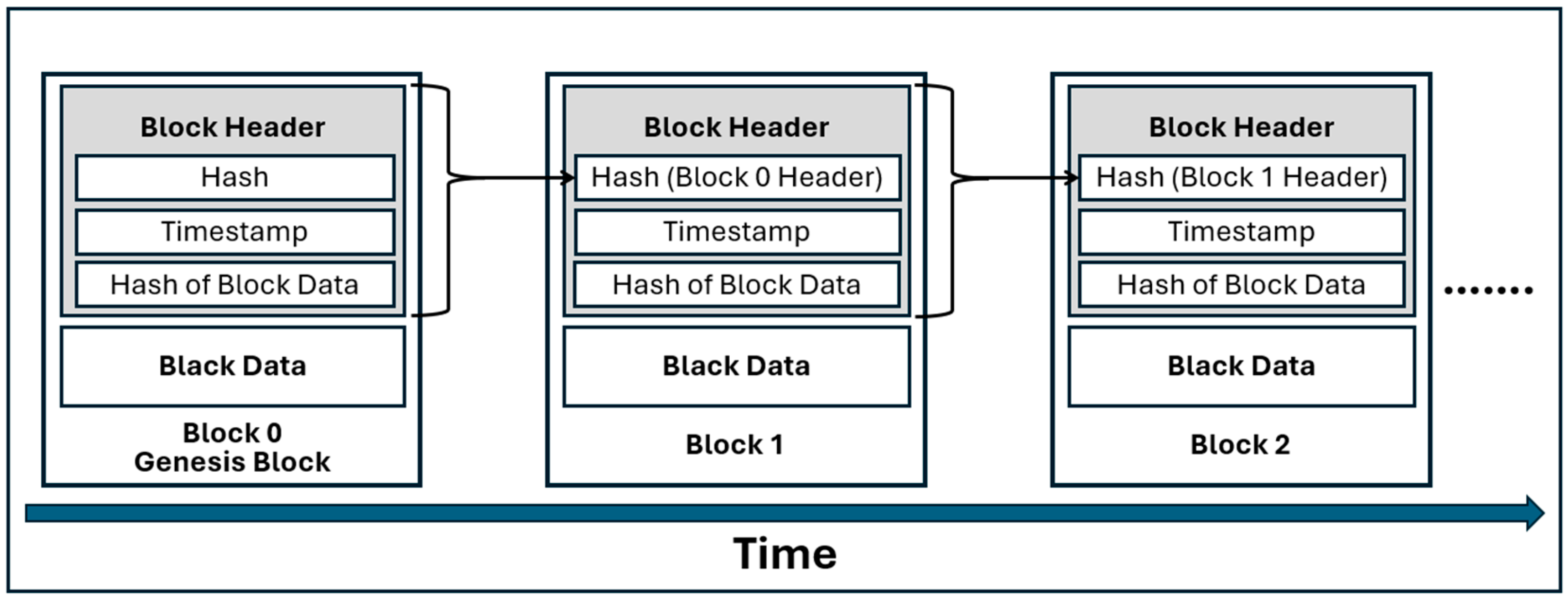
Blockchain technology links blocks by incorporating the hash of the header of each previous block into every new block, thereby creating an unbroken chain [
3]. If a previously added block is modified, its hash changes, causing a ripple effect that alters the hashes of all the subsequent blocks. This structure makes tampering evident: any change to a single block disrupts the entire chain, enabling the network to detect and discard the altered blocks. This method of linking blocks is fundamental to the blockchain’s ability to maintain its data integrity and transparency.
Figure 2 below shows a general blockchain structure, where each block contains a hash from the previous block. This linkage creates a secure and immutable chain, ensuring the integrity of the data within the blockchain. Each block not only holds its own data but also references the hash of the prior block, thereby establishing a chronological order and making it difficult to alter information retroactively. This is a fundamental principle that underpins the security of blockchain technology [
3].
The hash in each block header includes a Merkle Root, which serves as a cryptographic summary of all transactions in that block [
10]. By organizing transactions into a Merkle Tree, blockchain networks ensure efficient verification and data integrity. Any modification to a single transaction alters its hash, propagating changes up the tree and ultimately modifying the Merkle Root, making tampering easily detectable. This structure enables lightweight Simplified Payment Verification (SPV), allowing nodes to confirm transactions without downloading the entire blockchain [
11], enhancing scalability and security in decentralized systems.
Figure 3 below shows a general overview of the Merkle Tree and how it aggregates the hashes of all transactions in the block. This method allows efficient verification of transactions, as changing any transaction at the leaf level alters the corresponding hash and propagates up to the root hash. This structure ensures data integrity and consistency, making it an essential component in blockchain systems.
Because a blockchain is a decentralized system without central authority, nodes or peers in the network must have a process for validating each block before adding it to the chain. This process is known as consensus [
3]. The concept of consensus is a core component of blockchain technology. Specific consensus algorithms require substantial computational resources. Therefore, it is essential to choose an algorithm that aligns with the requirements of the application and capabilities of the nodes in a blockchain network.
Table 1 below shows the common consensus algorithms. Proof-based algorithms, such as Proof of Work (PoW), deliver strong security and fault tolerance but require significant computational resources [
3]. Conversely, voting-based algorithms such as Practical Byzantine Fault Tolerance (PBFT) [
12] use less computational power but generally have lower fault tolerance, making them well-suited for controlled permissioned networks.
Blockchain networks can be public, private, or consortium-based for their access control and participation mechanisms. A public blockchain operates in a permissionless manner, allowing any node to join the network, participate in consensus, and validate data without requiring approval from an administrator or a central authority. Conversely, a private blockchain functions as a permissioned network, where nodes require authorization from an administrator or a central authority to participate [
16]. Consortium blockchains blend the aspects of both private and public blockchains, with multiple organizations jointly managing access to a limited number of nodes to read, write, and validate the data [
17].
Table 2 below presents a comparison of blockchain network types.
While blockchains remain the dominant distributed ledger technology (DLT), alternative models such as IOTA’s Tangle offer a different approach to achieving decentralized consensus, particularly in IoT applications [
18]. By utilizing a Hash Directed Acyclic Graph (DAG), known as Tangle, instead of a blockchain, IOTA eliminates scalability and transaction fee issues, enabling peer-to-peer micropayments for IoT devices. Instead of relying on traditional consensus, unapproved transactions, known as “tips”, must be approved by newly incoming transactions. Each new transaction selects two tips to validate using the Uniform Random Tip Selection strategy, which randomly picks from the available tips. However, this method introduces an issue, as transactions are not evenly distributed over time, leading to potential inefficiencies in approval propagation [
18]. In this survey, we will only discuss blockchain technology and its applications, but IOTA is mentioned here as an alternative to blockchains.
3. Scope of This Survey
This survey categorized blockchain applications in the IoT. As blockchain technology revolutionizes the way devices communicate, automate tasks, exchange messages, and store data, it touches a wide range of products and applications. To help control the subject, the applications covered in this survey are divided into eight areas covered in
Section 4,
Section 5,
Section 6,
Section 7,
Section 8,
Section 9,
Section 10 and
Section 11 of this survey:
Section 8—Blockchain Scalability and Efficiency
Recent surveys on blockchain applications in the IoT have concentrated on specific aspects of the eight areas listed above. In contrast, this survey aimed to examine these areas thoroughly.
Table 3 below compares this survey to similar surveys conducted over the past few years in a selected 12 subjects. In this comparison, we took into consideration the depth of discussion of the subject and the main components covered in these surveys.
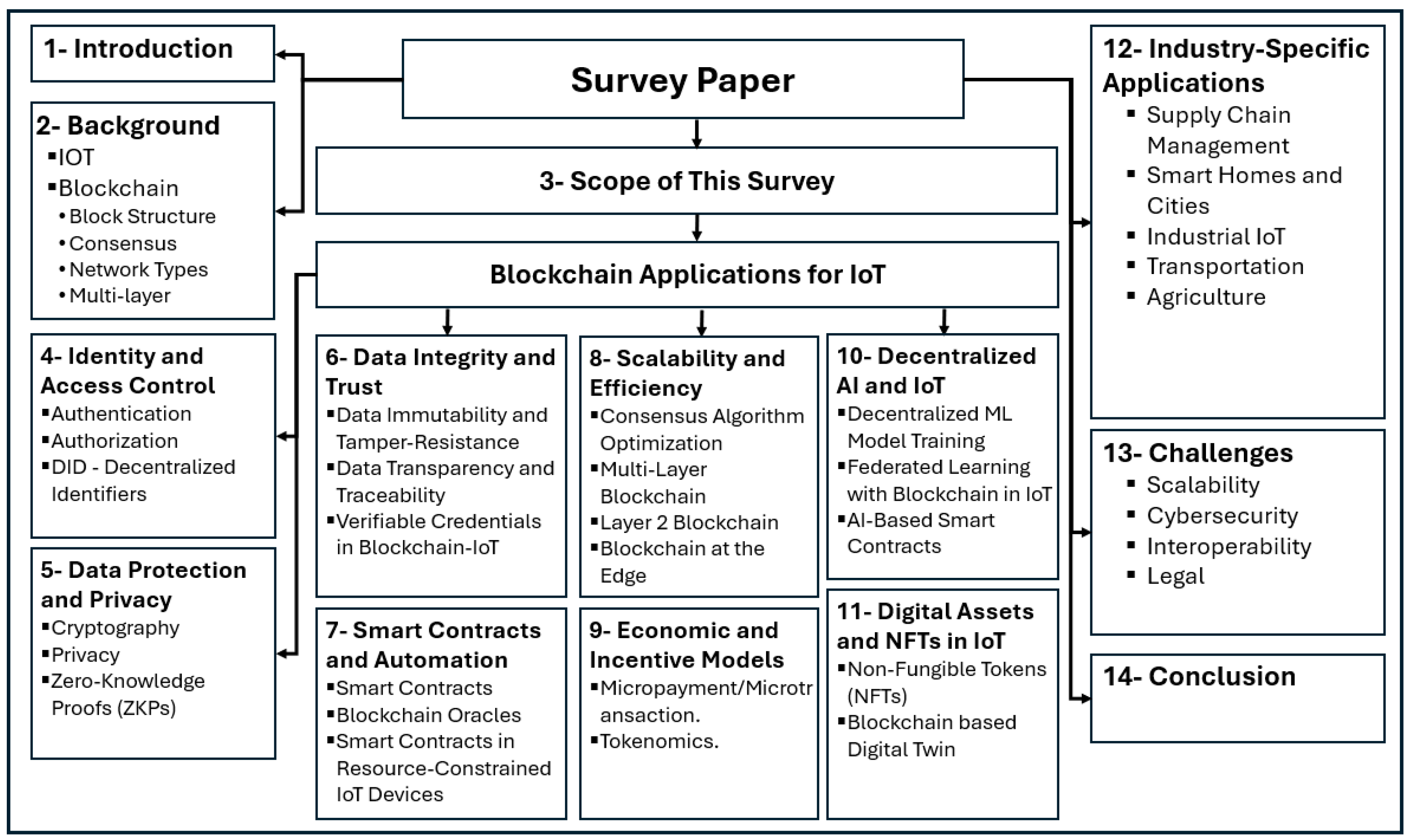
This survey paper is structured into 13 main sections, as illustrated in
Figure 4.
Section 1 introduces the topic, providing an overview of the paper’s objectives.
Section 2 presents background information on IoT and blockchain technologies, establishing a foundation for discussion.
Section 3 defines the scope of this survey and compares it with existing surveys.
Section 5,
Section 6,
Section 7,
Section 8,
Section 9,
Section 10 and
Section 11 explore various blockchain applications in the IoT, while
Section 12 examines industry-specific use cases.
Section 13 identifies key challenges in integrating blockchain technology with the IoT and proposes potential solutions. Finally,
Section 14 concludes the paper, summarizing key findings and future research directions.
4. Identity and Access Control
4.1. Authentication
The trust and authentication process starts by identifying the entity connecting to the blockchain network. While users can authenticate by username/password or multi-factor authentication (MFA), many IoT devices are headless without a traditional user interface. Due to the large number of IoT devices, zero-touch provisioning (ZTP) or low-touch provisioning (LTP) is required to streamline the process and minimize user interaction by identifying the device with one of its hardware characteristics.
In the TCP/IP stack, hardware is identified by the Media Access Control (MAC) address. However, since this MAC address is sent in clear text as part of IP communication and can be easily spoofed, it cannot be considered a way to authenticate IoT devices and identify them securely. To establish a more trusted device identity, digital certificates are used as cryptographic credentials that bind a device to a verifiable identity. These certificates are generated by a trusted authority (such as a Public Key Infrastructure (PKI) or a blockchain-based identity system) and contain essential device attributes, including a unique device identifier, public key, and issuer information.
For certificates to be effective, they must be securely generated, trusted, and stored. Generation involves cryptographic key pair creation, where a device is assigned a private key for signing and a public key for verification. Trust is established through Certificate Authorities (CAs) or decentralized blockchain-based identity frameworks, ensuring that certificates cannot be forged or altered. Storage must also be tamper-resistant, typically secured in Trusted Platform Modules (TPMs) or blockchain ledgers to prevent unauthorized modifications or access.
TPM technology provides a more secure hardware-based authentication method that ensures device identity verification without requiring user interaction. A TPM is based on the ISO/IEC 11889 [
26] standard and functions as a hardware-based security module. It operates as a specialized microcontroller, enhancing device security by integrating cryptographic keys and algorithms for the secure storage of passwords, certificates, encryption keys, and authentication mechanisms [
27]. Many low-cost, resource-limited IoT devices lack a TPM, which restricts this method to devices equipped with a TPM. One approach proposed to address this limitation is the concept of Shadow TPM (SdwTPM) for smart embedded devices (SEDs) in healthcare, where TSEDs (with hardware TPMs) serve as trust anchors for N-TSEDs [
28].
Physical Unclonable Functions (PUFs) present another option for hardware-based authentication. Unlike digital certificates, which require secure storage for private keys, PUFs generate a unique hardware fingerprint derived from the physical characteristics of a device’s silicon. Since this fingerprint is intrinsic to the device and cannot be cloned or extracted, PUFs provide a lightweight, hardware-embedded authentication method without the need for secure key storage. They provide hardware-level security by generating unique, unclonable identities that exploit tiny manufacturing variations in the CMOS that occur naturally during fabrication. These variations are unique to each device, making it impossible to clone or predict their responses. A PUF works by generating a unique response based on its internal physical properties when it receives an input signal (challenge) from a device. This response acts as a hardware fingerprint, which is then verified against a pre-stored reference in a secure database or blockchain to authenticate the device and ensure its legitimacy. PUFs serve as a lightweight authentication alternative for resource-constrained IoT devices, addressing the limitations of traditional cryptographic methods, but it has its challenges also [
29]. PUFs are vulnerable to machine learning-based modeling attacks, where an adversary collects challenge–response pairs (CRPs) and uses ML algorithms to create a software model that accurately predicts responses to new challenges. Optimal PUF designs are needed to produce the maximum number of CRPs necessary for modeling the PUF [
29].
4.2. Authorization
Permissioned blockchain networks provide a secure and decentralized approach to authorizing and registering IoT devices, ensuring that only verified and trusted devices can participate in the network. Unlike public blockchains, which allow anyone to join and interact, permissioned blockchains require explicit approval for devices to be registered and authorized, reducing the risk of malicious actors infiltrating the network.
Before an IoT device can be fully integrated into the network, it must go through a verification process where its identity, origin, and integrity are confirmed. This involves validating unique device credentials, such as cryptographic keys, digital signatures, or hardware-based security identifiers like PUFs. Once verified, the device is formally approved and granted authorization, allowing it to communicate, perform transactions, and interact securely within the ecosystem.
Organizations can adopt either centralized or decentralized identifier (DID) approaches. In a centralized model, a trusted entity or certificate authority (CA) is responsible for issuing and managing device credentials, ensuring that only authorized devices can join the network. While this approach provides a controlled and structured authentication process, it also introduces a single point of failure and scalability limitations. Alternatively, DID frameworks, built on a blockchain or DLT, allow devices to maintain self-sovereign identities, reducing reliance on central authorities. For large-scale deployments, this process becomes increasingly challenging.
To address large-scale and distributed blockchain-based deployment for IoT networks, Singh et al. [
30] suggested that IoT devices should be registered using a blockchain-based digital certificate (blockCert) during the manufacturing stage to ensure secure identity management. The device’s unique identifier (PUF-based ID), MAC address, and manufacturer details are included in this blockCert. Each device then undergoes a multi-tier verification process, where distributors and customers validate its authenticity before deployment. This approach prevents tampering, counterfeiting, and unauthorized device inclusion in the network by leveraging blockchains’ decentralized and immutable nature for trusted device authentication.
4.3. DIDs—Decentralized Identifiers
Decentralized identifiers (DIDs) are a new type of identifier that enable verifiable, decentralized digital identities without relying on centralized registries, identity providers, or CAs. DIDs empower individuals and entities to create and control their own unique identifiers, enhancing privacy, security, and self-sovereignty in digital interactions. Unlike traditional identity systems, where a third party manages identifiers, DIDs operate in a decentralized manner, allowing users to manage authentication, verification, and secure data exchange without requiring approval from external authorities [
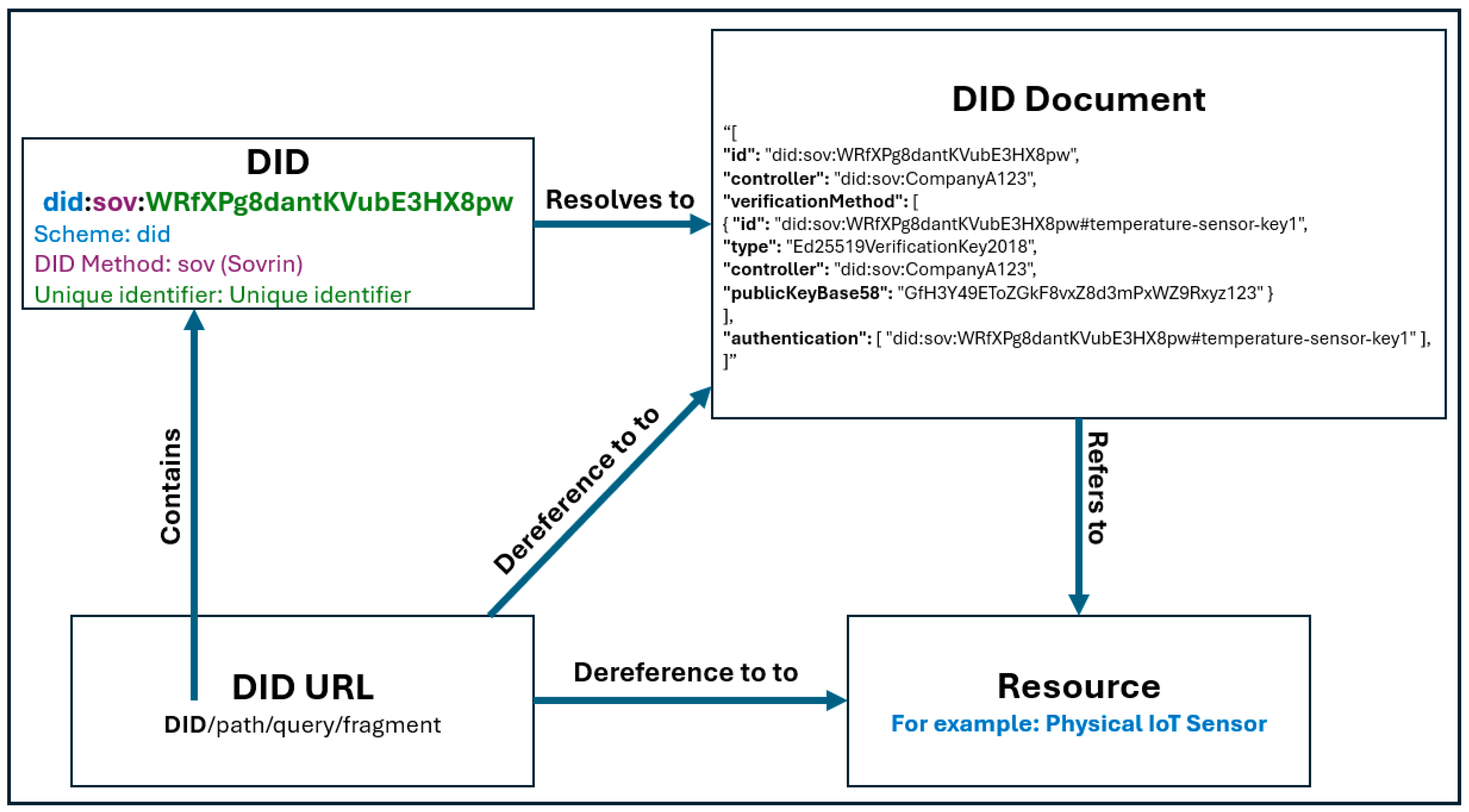
31]. The main components of DID architecture are as follows:
DID: A URI with three components: a scheme, method identifier, and unique identifier. They resolve to DID documents.
DID URLs: A DID URL extends a DID with paths, queries, and fragments, allowing access to specific resources like cryptographic keys or external data.
DID subject: The entity identified by the DID, which can be a person, organization, device, or concept.
DID controller: An entity that manages the DID document, typically using cryptographic keys. It can be the same as the DID subject or different.
Verifiable data registry: A system that records and resolves DIDs. It can be a blockchain, decentralized file system, peer-to-peer network, or database, ensuring trust and security for DID storage and retrieval.
DID documents: These contain data about a DID, including public keys, verification methods, and service endpoints. They enable secure interactions with the DID subject.
DID resolvers and DID resolution: A DID resolver takes a DID as an input and returns a DID document. This process is called DID resolution.
DID URL dereferencers: A DID URL dereferencer converts a DID URL into a specific resource, such as a cryptographic key or service endpoint.
Figure 5 below shows a sample DID and DID document based on decentralized identifiers (DIDs) v1.0 W3C Recommendation, dated 19 July 2022 [
31]. The figure illustrates the relationship between key components involved in the DID ecosystem, highlighting how different elements interact to establish secure and verifiable identities.
DIDs can replace traditional certificate-based authentication [
32]. This approach mitigates risks such as identity spoofing, unauthorized access, and reliance on centralized authorities, ensuring a more secure and scalable IoT authentication framework.
Hyperledger Indy [
33] is a blockchain framework for decentralized identity (DID) management. It offers tools to create self-sovereign identity (SSI) systems, allowing individuals and organizations to manage digital identities without centralized authorities. It is part of The Hyperledger Foundation [
15], now under LF Decentralized Trust, the Linux Foundation’s main organization promoting innovation in decentralized technologies.
5. Data Protection and Privacy
5.1. Cryptography
In cryptography and cybersecurity, encryption, key exchange, and trust are foundational elements crucial for safeguarding data confidentiality, which, together with integrity and availability, comprise the three critical pillars of cybersecurity (CIA).
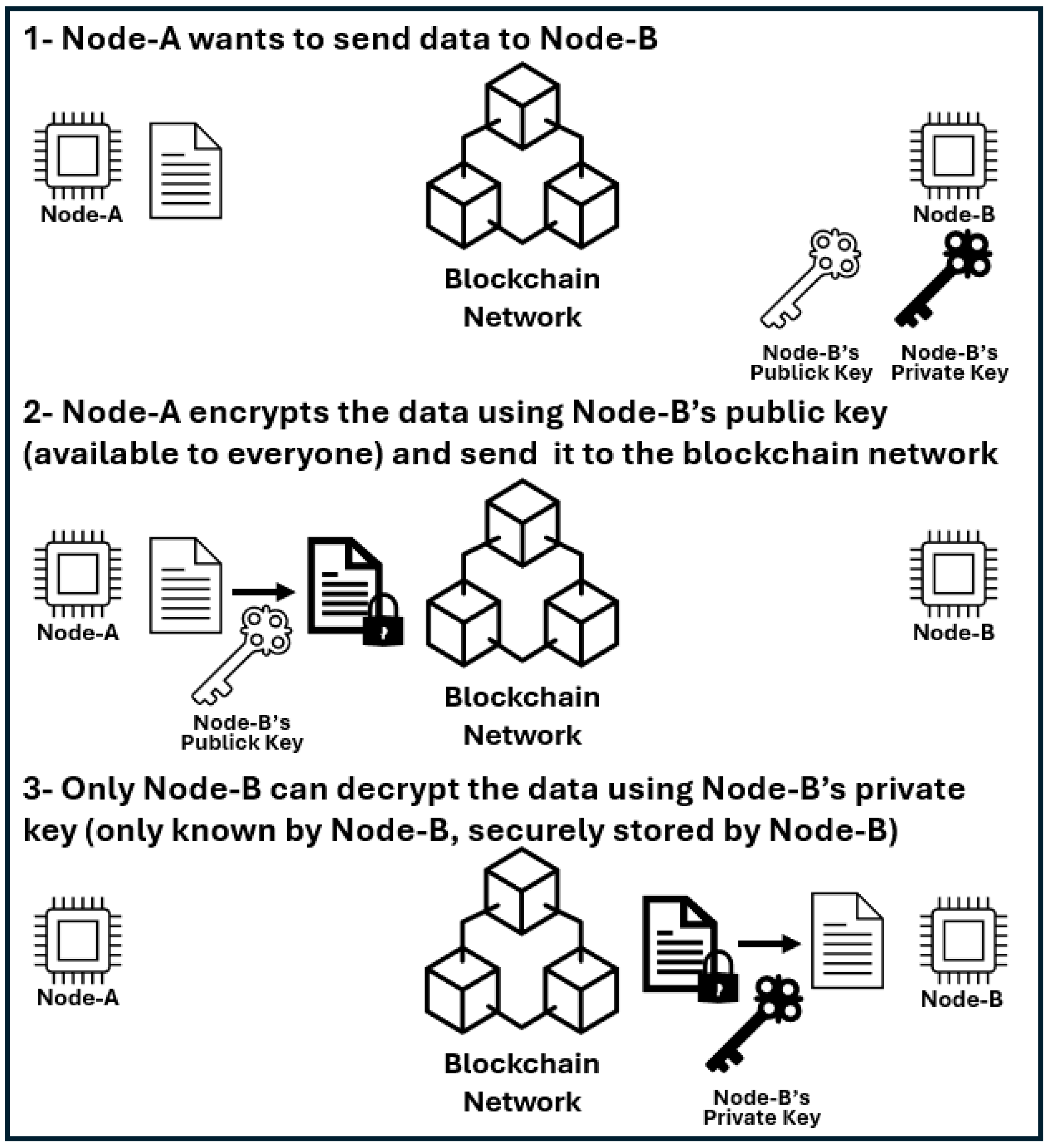
The standard model for establishing trust on the Internet is the PKI, which uses a “chain of trust” approach. This chain links certificates and digital signatures in a structured, hierarchical manner, beginning with a trusted root authority and extending to end-entity certificates. The PKI relies on asymmetric encryption: data are encrypted with a public key, which is publicly available, while only the corresponding private key, kept secure, can decrypt them.
Figure 6 below shows the concept of public and private keys. In the first step, Node-A intends to send data to Node-B. Both nodes are part of the blockchain ecosystem and possess a pair of cryptographic keys: a public key (available to all nodes) and a private key (securely stored in the node that owns it). In the second step, Node-A encrypts the data using Node-B’s public key, which is openly available to everyone on the blockchain network. The encrypted data are then sent to the blockchain network, ensuring that even if intercepted, the information remains secure and unreadable. In the final step, when Node-B receives the data, only Node-B can decrypt the data using its private key, which is securely stored and not shared. This process ensures that even though the data are transmitted through a public blockchain, only the intended recipient can access and read it, thereby maintaining confidentiality and data integrity.
Public and private key pairs can be used in digital signatures, providing authentication, integrity, and non-repudiation in secure communications. Digital signatures operate by having the private key sign a message, while the public key verifies the signature. This process ensures that the message comes from a trusted source and has not been tampered with. The process of digital signature is described in
Figure 7 below. The steps are:
- -
Node-A generates a hash of the message;
- -
It then encrypts the hash using its private key, creating a digital signature;
- -
The message and the digital signature are sent through the blockchain network to Node-B;
- -
Node-B receives the signed message from the blockchain network;
- -
It recomputes the hash from the received message;
- -
Then, it decrypts the digital signature using Node-A’s public key, obtaining the original hash;
- -
If both hashes match, it confirms the message is authentic and untampered.
Figure 7.
Digital signature process.
Figure 7.
Digital signature process.
While the RSA cryptographic algorithm is a common choice on the Internet, its large key sizes make it computationally expensive. More efficient alternatives like ECDSA and EdDSA, based on elliptic curve cryptography (ECC), offer faster processing and reduced key sizes, making them ideal for blockchain transactions, IoT authentication, and secure messaging.
Table 4 below compares these three algorithms and their applicability to IoT devices.
Although effective, the PKI is inherently centralized, so blockchain systems needed to establish an equivalent model for cryptography and trust that leverages decentralization. To avoid the reliance on a central root certificate authority to establish trust between nodes in the blockchain, DIDs are widely used in blockchains for secure, self-sovereign IoT device identification. Multiple frameworks and services were developed to provide a decentralized alternative to the PKI [
34], which is consistent with the decentralized nature of the blockchain.
To overcome the resource limitations of IoT devices, various approaches tackle issues with certificate registration and key sizes. A fog layer is a practical solution that shifts computational tasks from IoT devices, reducing their processing load. This architecture upholds data privacy, immutability, and traceability without relying on external authority. In this setup, a dual blockchain system generates public and private keys for IoT devices, enabling secure and mutually authenticated communication across the network [
35]. An alternative approach involves using a lightweight certificate; for example, it can be combined with a self-signing mechanism, which is then stored on the blockchain by an LRA [
25].
Quantum computing poses a significant threat to traditional blockchain security, necessitating advanced protective measures. One approach is to use Dual-Factor Quantum-Safe Blockchain (DFQSB) architecture to mitigate these risks. By integrating post-quantum cryptography (PQC) and quantum key distribution (QKD), this model ensures secure blockchain transactions against potential quantum attacks, particularly in IoT environments [
36]. Castiglione et al. proposed the Dilithium-5 algorithm as a robust post-quantum digital signature scheme designed to secure IoT devices against quantum attacks. It is based on lattice-based cryptography. The algorithm is particularly suited for low-power devices due to its efficient key generation, signing, and verification processes. The integration of hardware acceleration further enhances performance, making it feasible for resource-constrained IoT environments [
37].
5.2. Privacy
Data privacy refers to an entity’s ability to control its access to data. Blockchain technology is designed to make all transactions visible to participants. However, privacy can be achieved to a certain extent using one of the following approaches:
- -
Signatures and cryptography using a different key per transacting counterparty [
38];
- -
Private blockchains [
38];
- -
Smart contracts [
39]: Smart contracts can be used in multiple ways in IoT systems. They can be used to control the ownership of an object [
40] or privacy-preserving access control using techniques such as the NFT [
39]. They can also control access to resources on the blockchain using the attribute-based access control (ABAC) model [
41], which is a dynamic and adaptable method that grants or restricts user access based on various attributes related to the user, resources, environment, or specific actions. This access-control mechanism is organized into four main components: users, resources, access requests, and permission removal.
5.3. Zero-Knowledge Proofs (ZKPs)
The ZKP is a concept in cryptography that allows one party (the prover) to prove to another party (the verifier) that they know a certain piece of information without revealing what that information is. This idea was first introduced by Goldwasser et al. in 1985 [
42]. The key properties of a ZKP are [
43] as follows:
Completeness: If both the prover and verifier follow the protocol correctly, the verifier will, with high probability, accept a valid proof;
Zero-knowledge: The verifier does not gain any additional knowledge about the prover’s secret aside from the fact that the statement is true;
Soundness: A dishonest prover cannot convince the verifier to accept a false statement as true.
ZKPs can be interactive or non-interactive, each with distinct applications in cryptographic verification [
44]. Interactive ZKPs (IZKPs) require a three-phase protocol:
Witness phase: The prover first generates a proof;
Challenge phase: The verifier issues a set of challenges;
Response phase: The prover responds to these challenges, allowing the verifier to accept or reject the proof.
This back-and-forth interaction ensures security but may be inefficient for blockchain applications. In contrast, non-interactive ZKPs (NIZKPs) streamline the process by eliminating the need for multiple rounds of communication. Instead, they involve three steps:
Setup, where a proving key (PK) and verification key (VK) are generated;
Prover, where the proof is created using the PK;
Verifier, where the VK is used to validate the proof.
Non-interactive ZKPs have gained popularity in blockchain applications, particularly in anonymous payments, identity protection, cross-chain interoperability, and off-chain computation verification.
On a blockchain, proofs are recorded in a shared ledger, which can pose a risk to privacy if verifiers can share proofs with unauthorized third parties. To address this, Chi1 et al. proposed a Blockchain Designated Verifier Proof (BDVP) scheme to enhance privacy in blockchain applications using ZKPs [
43]. Unlike traditional ZKPs, where a verifier can share a proof with third parties, BDVPs allow the verifier to forge a fake proof, making it impossible for outsiders to determine whether the prover actually possesses the secret. This ensures non-transferability of the proof, protecting the prover’s privacy even if the proof is recorded on a blockchain. The scheme also incorporates post-quantum security using lattice-based cryptography, making it resistant to quantum attacks while maintaining efficiency.
6. Data Integrity and Trust
6.1. Data Immutability and Tamper Resistance
Each block in a blockchain contains the hash of the header of the previous block, thereby creating a connected chain. Suppose a block is tampered with, and its hash changes, triggering a cascading effect on the hashes of all subsequent blocks. This mechanism makes tampering with the blockchain readily detectable, as even a tiny modification disrupts the integrity of the entire chain, enabling the system to reject the altered blocks. This characteristic is fundamental to blockchain security, with immutability reinforced by conditions such as maintaining the longest chain and verifying multiple blocks before validating a transaction [
3].
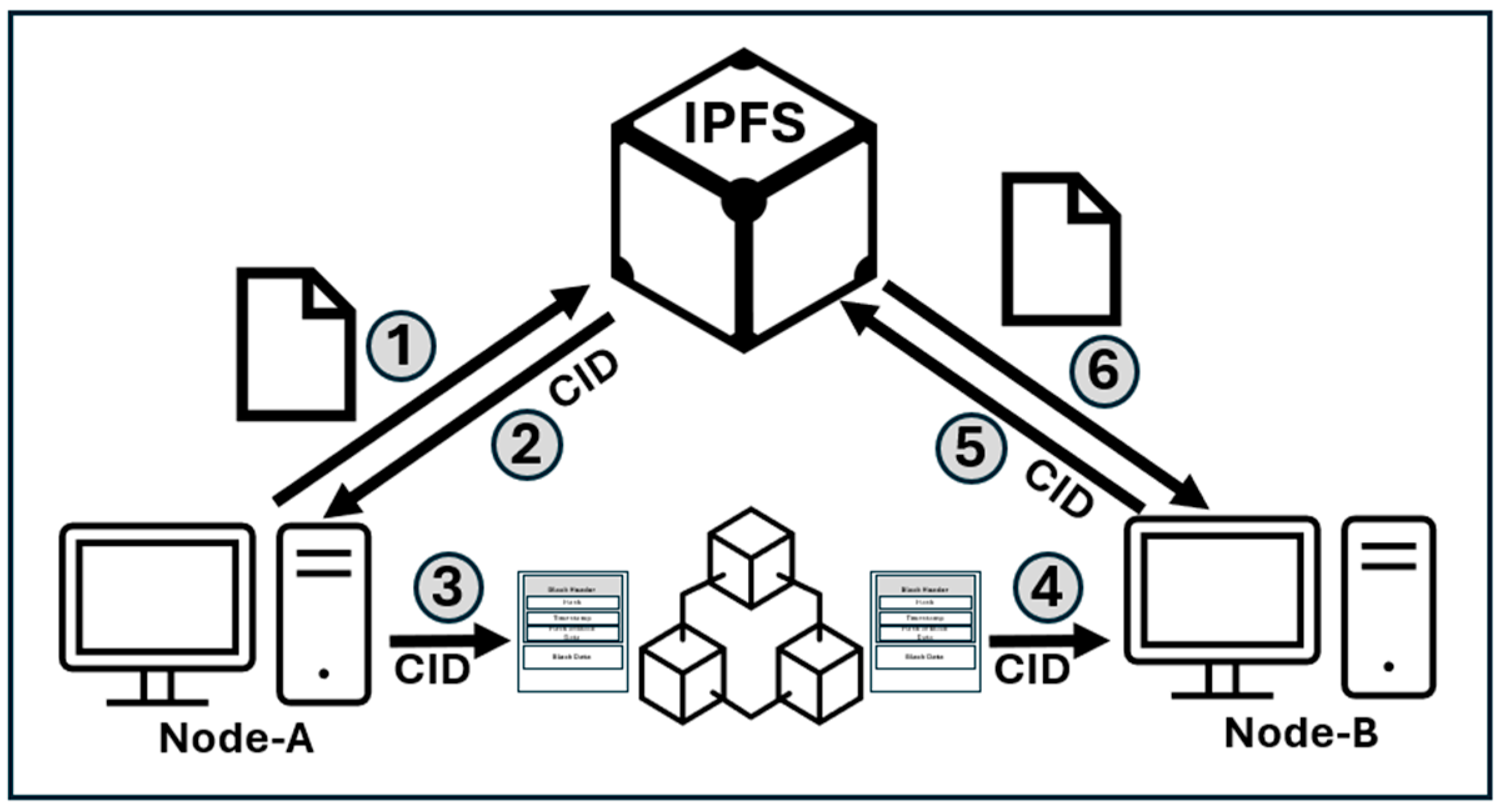
When sharing data via a blockchain, only the hash digest of large datasets is typically stored in the chain to prevent excessive growth. The data reside off-chain in shared databases like the InterPlanetary File System (IPFS). The IPFS is a decentralized protocol for storing and sharing files. It uses hashing to create unique identifiers called Content Identifiers (CIDs) based on the content of a file. CIDs ensure data integrity and immutability, allowing efficient file retrieval across distributed nodes without relying on centralized servers, thereby enhancing resilience and scalability. This on-chain hash serves as a fingerprint, ensuring that any alterations to off-chain data are immediately detectable.
Figure 8 below shows the general steps of the IPFS process.
Node-A uploads the file to the IPFS, which is split into chunks, and a unique CID is generated based on the hash value;
IPFS stores a file distributed across the IPFS network for decentralized storage. It sends CID to Node-A.
Node-A records the CID in the blockchain, which is saved in a blockchain transaction/smart contract to ensure its immutability and traceability;
Node B retrieves the CID from the blockchain. Node-B queries the blockchain to obtain the CID associated with the file.
Node-B requests a file from the IPFS and uses the CID to fetch the file from the IPFS network.
Node-B verifies and downloads the file, and its integrity is checked against the CID before it is reassembled and used.
Figure 8.
General steps of IPFS file storage and retrieval.
Figure 8.
General steps of IPFS file storage and retrieval.
To achieve end-to-end data integrity, additional measures are often required to secure the entire data pipeline beyond the blockchain network, thereby addressing potential vulnerabilities at each stage [
45].
6.2. Data Transparency and Traceability
Data transparency and traceability refer to the ability to observe and track the origin and movement of data throughout their lifecycles. As a decentralized storage system, a blockchain offers a high level of tamper resistance and includes mechanisms that prevent synchronization discrepancies across the network. This inherent reliability has made blockchains particularly valuable in industries that require secure and verifiable records, and their use is already widely recognized and adopted within the financial sector [
46]. The decentralized and immutable nature of blockchains ensures data transparency and traceability and provides secure, verifiable, and tamper-proof records across various industries.
One application of blockchain traceability is to enhance the protection and tracking of original intellectual achievements, such as patents and copyrights. A blockchain-based service architecture can address challenges in intellectual property management, including confirming ownership, tracing transactions, and distributing rewards among contributors. By utilizing decentralized storage, immutable records, smart contracts, and timestamping, the system enables secure registration, transparent transfer histories, and automated incentive mechanisms [
47]. Simulations demonstrate blockchains’ ability to detect tampering, ensure data integrity, and support efficient querying of achievement records [
47].
6.3. Verifiable Credentials in Blockchain–IoT Systems
Verifiable Credentials (VCs) are digitally signed credentials that allow entities, such as IoT devices, users, or organizations, to prove claims about their identity, capabilities, or permissions without relying on a centralized authority. Many VCs utilize DIDs and software implementations of this model must be capable of resolving DIDs. DID-based URLs serve as identifiers for various entities involved in credential management, including subjects, issuers, holders, credential status lists, cryptographic keys, and other machine-readable information linked to a verifiable credential [
48].
To support Verifiable Credential (VC) validation, a verifiable data registry (VDR) is used to store and manage DIDs, public keys, and credential metadata. A VDR can be implemented on distributed ledger technologies (DLTs) like blockchains, ensuring tamper-proof and decentralized identity records. Alternatively, it can be stored in external databases or decentralized storage solutions, allowing flexible and scalable identity management. Examples of verifiable data registries include trusted databases, decentralized databases, government ID databases, and distributed ledgers. Often, more than one type of verifiable data registry is used within an ecosystem, providing redundancy and interoperability across different identity management systems [
48].
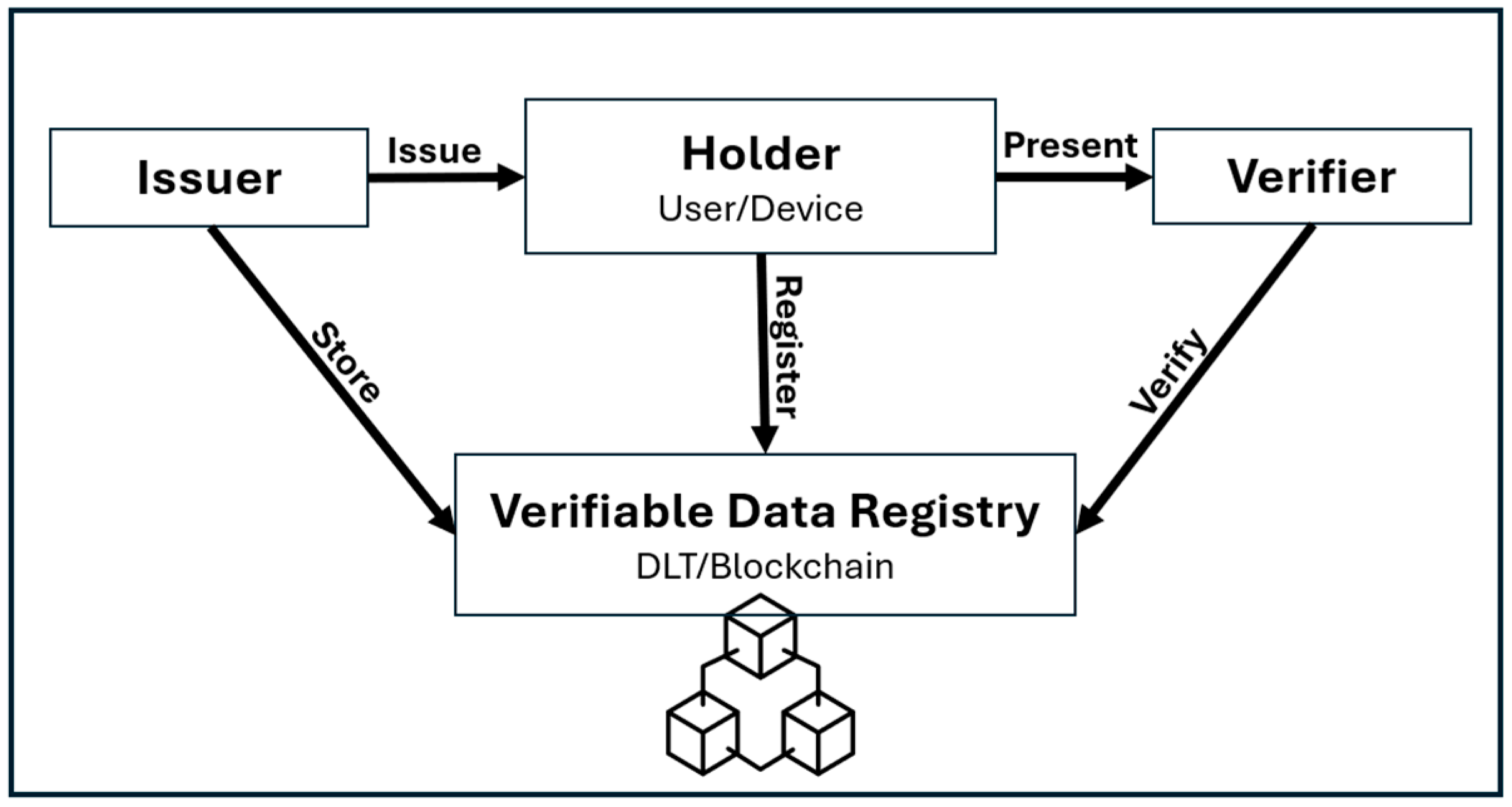
A Verifiable Credential (VC) ecosystem operates within a trust triangle consisting of three primary entities, the issuer, holder, and verifier, along with a verifiable data registry, such as a blockchain [
49].
Figure 9 below shows the relationship between the three components below and the VRD:
The issuer is responsible for generating and assigning credentials that confirm specific information about a subject;
The holder securely stores these credentials and presents them to a verifier;
The verifier validates the claims against a verifiable data registry to ensure authenticity.
Smart contracts play a critical role in the issuance, verification, and revocation of Verifiable Credentials (VCs) by automating credential management on decentralized networks [
32,
49].
Figure 9.
Verifiable Credentials framework.
Figure 9.
Verifiable Credentials framework.
7. Smart Contracts and Automation
7.1. Smart Contracts
Smart contracts are a fundamental aspect of blockchain technology that enables the creation of decentralized applications (dApps) that operate independently of any single authority. DApps are applications built on blockchain networks that provide transparency, security, and decentralization, thereby allowing users to interact directly without intermediaries. Smart contracts are crucial for functioning decentralized autonomous organizations (DAOs) and Decentralized Finance (DeFi). DAOs are member-governed organizations that operate based on smart contract rules, whereas DeFi refers to blockchain-based financial systems that offer services, such as lending, trading, and payments, without traditional financial institutions [
50].
Smart contracts can be categorized into three main types [
51]:
Primary smart contracts: These operate within a single blockchain and are used for automation, transactions, staking, and token management;
Oracle smart contracts: These facilitate the integration of off-chain data, allowing blockchain systems to interact with external information sources;
Bridge smart contracts: These enable cross-chain communication, making it possible to exchange assets and data seamlessly between different blockchains.
Hasnaoui et al. proposed the utilization of AI-driven classification to sort smart contracts into these three distinct categories [
51]. This approach uses machine learning models to analyze opcode patterns, thereby enabling automated classification and enhancing security within blockchain ecosystems. The following sections of this survey will offer a more detailed discussion on the concepts of oracles and multi-layer blockchains.
By using smart contracts, devices can automatically engage based on predefined criteria, thereby eliminating the need for manual actions or third parties. This streamlines operations and reduces costs [
52].
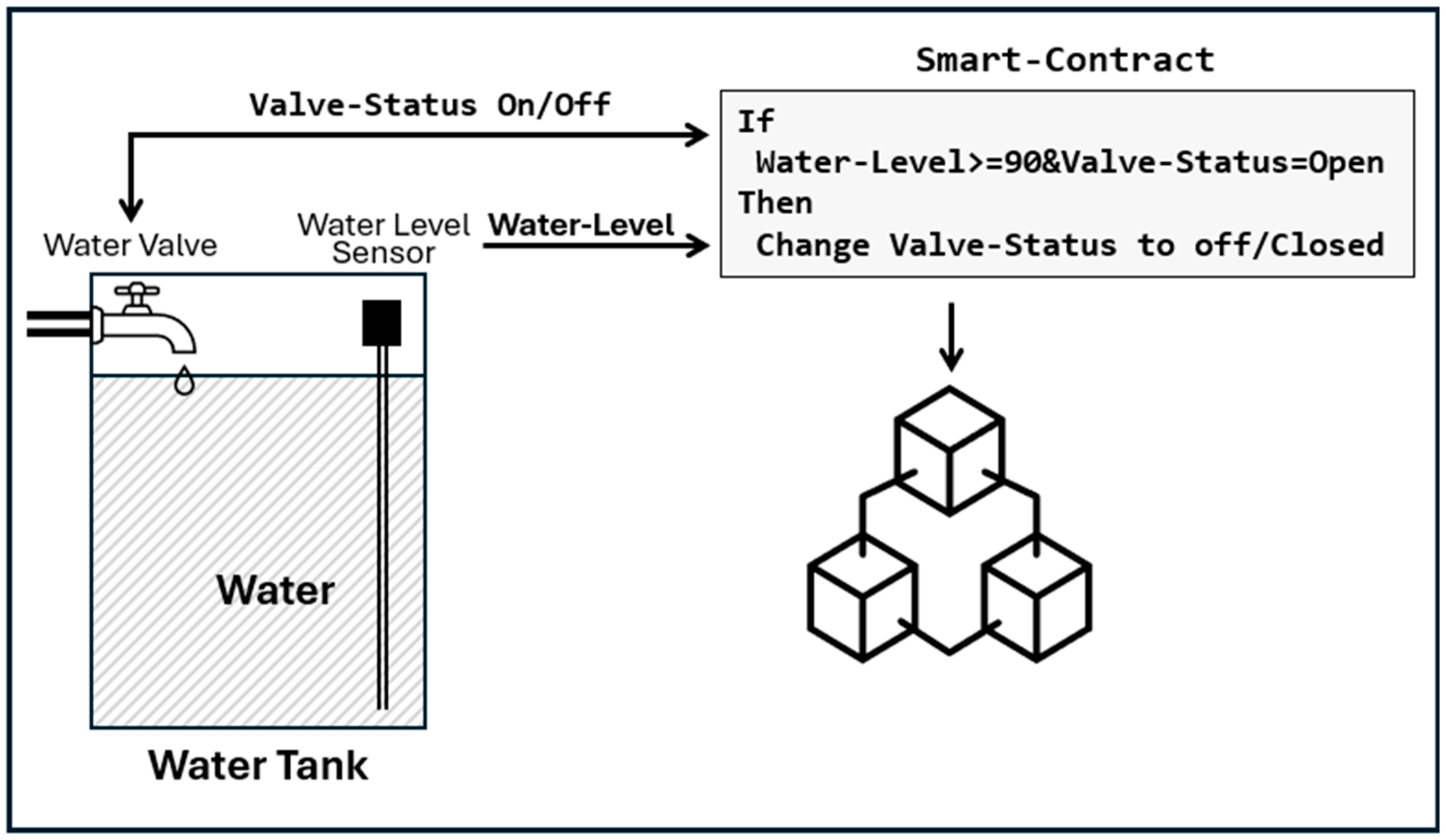
Figure 10 below shows a simple smart contract that monitors the water level in a tank and closes the valve when the water level is 90% or higher. The logic of this contract is as follows:
Water level sensor: A device that measures the current water level in the tank and provides real-time data;
If Water-Level is greater than or equal to 90% and the Valve-Status is “open,” the smart contract executes a command to close the valve (valve status = closed).
Smart contracts can achieve more complex automation tasks and collect inputs from multiple sources to trigger actions or contracts based on user requirements.
In addition to automating tasks, smart contracts can be set up to trigger authentication by enforcing predefined access rules and verifying identity attributes on the blockchain. These contracts serve as decentralized gatekeepers, permitting only authorized entities to perform specific actions [
53]. Storing credentials in a blockchain, even when hashed or encrypted, may raise security concerns and complicate password modification. This is why the concept of ZKPs can be applied for privacy preservation while taking advantage of smart contracts for payment and authentication [
54].
Another application of smart contracts involves linking multiple blockchain networks and establishing the rules for information transfer between them. These cross-chain smart contracts can be deployed through gateways to trigger events that initiate cross-chain interactions. The concept of ZKPs can be leveraged here also to authenticate transactions without revealing user identity [
44].
Like any code or software, smart contracts need updates to fix bugs, enhance security, and add new functionalities. However, their immutable nature poses challenges for upgrades, often necessitating workarounds such as proxy contracts, data segregation, or redeployment. Traditional upgrade methods add complexity and security risks, making well-structured and seamless solutions vital. One proposed method introduces the gotoContract variable, allowing function redirection to upgraded contract versions without disrupting existing operations. This approach ensures data integrity, reduces manual interventions, and improves contract maintainability [
55].
7.2. Blockchain Oracles
In a blockchain, oracles are external services or mechanisms that provide smart contracts with real-world data or external information that cannot be accessed independently. Oracles act as bridges between the blockchain and off-chain systems, enabling smart contracts to interact with data outside the blockchain ecosystem.
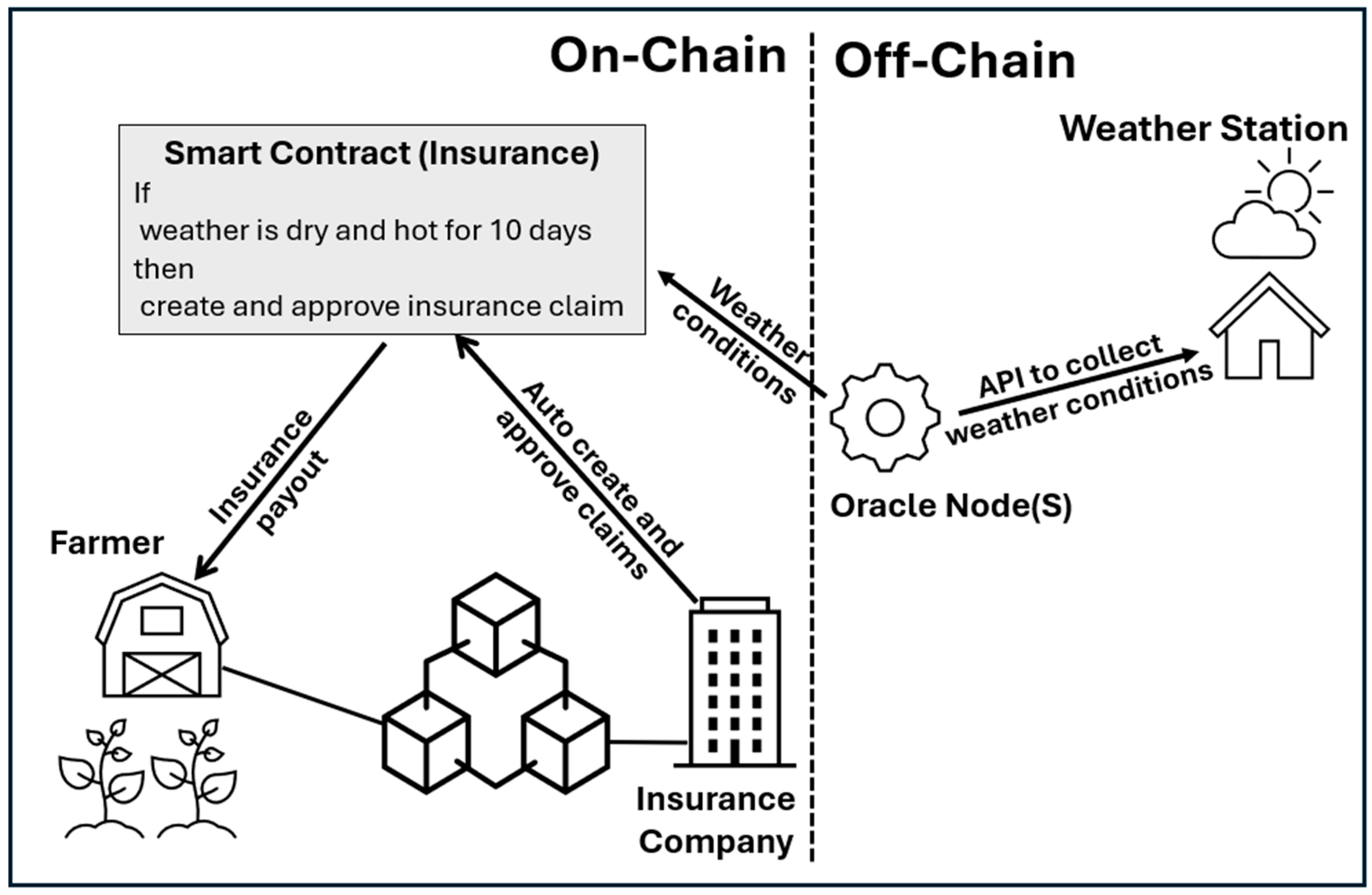
For example, oracles in smart home applications can read off-peak hours from local utility companies and feed them to smart contracts in a blockchain to control the appliance operation time.
Figure 11 below shows the logic of this example. The on-chain part includes a smart contract on the blockchain that controls the washing machine’s status (on/off) depending on the electricity rate. If the rate from the utility company is off-peak, the washing machine turns on; otherwise, it stays off. The off-chain part involves the utility company providing electricity rate data via an API, which is fetched by an oracle node and sent to the blockchain. The oracle acts as a bridge, ensuring that real-world data are securely fed into the blockchain for automated decision-making.
7.3. Smart Contracts in Resource-Constrained IoT Devices
Deploying smart contracts on IoT devices presents significant challenges due to their resource-constrained nature. Unlike traditional computing environments, IoT devices often have limited processing power, memory, and storage, making running complex smart contract operations difficult. To deploy smart contracts efficiently in IoT networks, it is essential to optimize the smart contract code to reduce computational overhead and gas costs. Additionally, offloading the processing of smart contracts or parts of their execution to other nodes in the network, such as edge or cloud nodes, can significantly improve performance and resource efficiency.
Updating smart contracts frequently is essential due to code bugs and evolving application requirements. However, traditional methods are inefficient, as they require recompilation and redeployment on the blockchain. This process involves proposing a deployment transaction, waiting for consensus, and then executing the redeployed bytecode through an invocation transaction, which is time-consuming and resource intensive. Existing blockchain architectures, like the Ethereum Virtual Machine (EVM), lack direct support for modifying deployed bytecode. As a result, even minor changes require complete recompilation and redeployment, leading to significant latency and high computational overhead. Li et al. (2022) introduced an optimization mechanism called ATOM for executing smart contracts in IoT systems [
56]. ATOM optimizes smart contract updates and execution in blockchain-based IoT by eliminating costly redeployments. It uses prebuilt bytecode templates to replace recompilation, reducing update latency by 62.7%. Its Application-Oriented Instructions (AoIs) minimize storage needs by 70% and gas usage by 90%. Instead of full redeployment, ATOM modifies bytecode at the instruction level, reducing ledger size and costs.
Another approach suggested by Su et al. is delaying smart contract instantiation in IoT-based blockchain networks to conserve resources [
57]. Traditional preinstantiated smart contracts consume memory and processing power even when idle, which is inefficient for resource-constrained IoT devices. To address this, they propose three methods: Instant Instantiation, where contracts are created only when first invoked and terminated when out of scope; Postinstantiation (Lazy Instantiation), which further delays instantiation until a critical function explicitly requires it, caching non-essential requests; and the Wrapping Variable Mechanism, which hides instantiation details for optimized execution.
8. Blockchain Scalability and Efficiency
8.1. Consensus Algorithm Optimization
Ferrag et al. provide a comprehensive comparison of the available consensus algorithms for blockchain-based IoT security, analyzing their impact on latency, scalability, computation, and attack resistance [
58]. The study evaluates mechanisms such as PoW, PoS, Byzantine Fault Tolerance (BFT), and Delegated Proof of Stake (DPoS), highlighting their suitability for different IoT environments. BFT-based algorithms provide low latency, which is required for IoT applications, but have high computation costs and are vulnerable to 33% attacks, where an attacker controlling more than 33% of the total validating power can disrupt consensus, halt the network, or manipulate transactions. These algorithms can be used in private, permissioned networks where the number of devices and the users who can connect are controlled.
One enhancement to PBFT is PBFT-Pipeline, which aims to address the high latency and communication complexity inherent in traditional PBFT. PBFT-Pipeline achieves this by introducing a pipelined processing approach that allows multiple consensus phases to be executed concurrently rather than sequentially. However, despite its improvements, PBFT-Pipeline still faces challenges when dealing with real-time IoT applications. The high network traffic and communication load can hinder performance when transaction rates spike. One approach to achieving the real-time communication required for the IoT is the Random Cluster PBFT (RC-PBFT) consensus algorithm [
59]. In this method, consensus is reached within randomly selected clusters in the blockchain and the results are propagated throughout the entire network. RC-PBFT is designed to meet the specific demands of IoT and real-time applications, offering both the security benefits of a blockchain and the speed and scalability necessary to process transactions or blocks generated by IoT devices efficiently. RC-PBFT reduces response time from over 200 ms to about 10 ms, making it more suitable for real-time IoT blockchain applications.
Two consensus algorithms can be implemented in a hybrid approach to effectively balance efficiency and security, especially in resource-constrained IoT environments. For example, Huang et al. suggested a PoS and PoW Hybrid Consensus that leverages the strengths of both algorithms to address the limitations of each. In this approach, PoS blocks are generated by users with limited computational resources, known as minters, who constitute the majority of users in edge environments. These PoS blocks process and store most of the transactions efficiently, ensuring low latency and real-time performance, which is crucial for IoT applications. To encourage participation and support network sustainability, a portion of the transaction fees is rewarded to the block minters. On the other hand, PoW blocks are generated by users with more substantial computational capabilities, known as miners, and follow the traditional PoW approach of solving cryptographic puzzles to validate transactions. The inclusion of PoW blocks strengthens security by adding computational challenges that deter malicious activities. By combining both PoS and PoW within the hybrid model, the system achieves a practical balance of lightweight, fast transaction processing and robust security, making it suitable for heterogeneous IoT environments [
60].
8.2. Multi-Layer Blockchain
A blockchain can be implemented in a multi-layer architecture by connecting several private networks to a public blockchain [
61]. In this multi-layered architecture, users can control which data are shared on the public blockchain through access control policies that can be enforced by a smart contract. A multi-layer approach can enhance performance by implementing various blockchain technologies across different layers, each chosen to leverage its unique advantages. In this architecture, the blockchain is a medium for securely storing non-sensitive information, such as access control lists (ACLs) and metadata, and facilitating data exchange. The tamper-resistant nature of the blockchain ensures that this information remains protected against unauthorized modifications [
62].
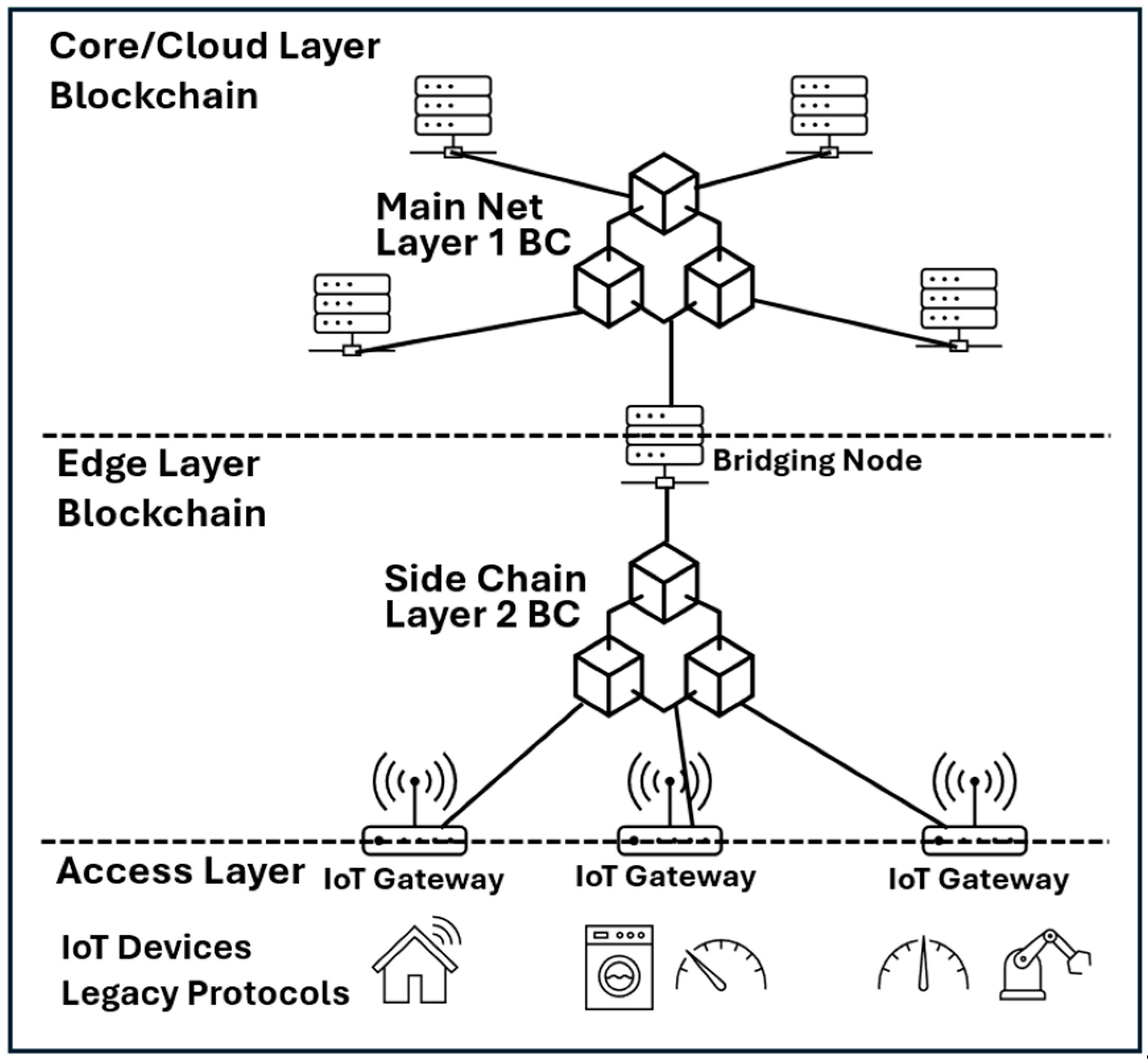
Figure 12 below illustrates this blockchain architecture. The layer 1 blockchain serves as the core network, whereas the layer 2 blockchains handle additional computation and scaling. Bridging nodes connect layer 2 to layer 1, keeping the blocks local for privacy, security, and performance. Only essential transactions are bridged to the main chain, reducing congestion and optimizing efficiency.
Given that many IoT devices are limited by constrained computational power, storage, communication speed, and energy, a multi-layer approach is essential for IoT blockchain deployment. These devices often lack resources for intensive blockchain operations such as consensus mechanisms and encryption. IoT devices can benefit from blockchains’ enhanced security and transparency without being overtaxed by offloading these tasks to more capable layers. This approach supports a scalable, efficient, and secure IoT network that can address the limitations of resource-constrained devices.
Figure 13 below shows a multi-layer blockchain system designed for IoT integration.
- -
At the access layer, IoT devices (e.g., home appliances and sensors) connect through IoT gateways, which manage communication via legacy protocols;
- -
The edge layer uses a sidechain (layer 2 blockchain) to process local transactions and reduce latency and computation load at the core layer, supported by bridging nodes that transfer data to the upper core–cloud layer;
- -
The core layer utilizes a Main Net (Layer 1 blockchain) for global consensus, high-security storage, and interoperability.
Figure 13.
Example of multi-layer blockchain in IoT.
Figure 13.
Example of multi-layer blockchain in IoT.
The introduction of the edge layer offloads computational tasks from resource-constrained devices to more powerful edge servers or cloud data centers, significantly enhancing system performance and reducing latency [
63]. This shift not only alleviates the processing burden on end devices but also improves the quality of service (QoS) and user experience by enabling real-time processing and analytics closer to the data source. Offloading computational tasks allows for the dynamic allocation of resources, optimizing energy consumption while maintaining high performance. Furthermore, it reduces network bandwidth usage by processing data locally whenever possible, rather than transmitting large volumes to centralized cloud data centers. This approach is particularly beneficial in applications like the IoT, smart cities, and autonomous systems, where rapid data processing and low latency are critical [
63].
8.3. Layer 2 Blockchain
In addition to multi-layer architectures, layer 2 blockchain scaling solutions provide another approach for improving blockchain scalability by processing transactions off the main chain while leveraging the security of the main blockchain. These techniques are designed to reduce congestion and increase transaction throughput without compromising decentralization or security.
Table 5 below shows a comparison between the layer 2 solutions and the multi-layer option.
8.4. Blockchain at the Edge
Blockchains can be combined with edge computing to improve the efficiency and security of computation offloading in IoT environments. Xu et al. suggested a blockchain-enabled computation offloading method, named BeCome [
64], that leverages blockchain technology to maintain data integrity during task offloading while employing advanced algorithms to optimize resource allocation and minimize energy consumption. Through extensive simulations, the study demonstrates that BeCome outperforms traditional methods in terms of resource utilization, load balancing, offloading time, and energy efficiency [
64].
Another approach is to offload both consensus mining tasks and data processing tasks in blockchain-empowered mobile edge computing (MEC) environments using deep reinforcement learning. Qiu et al. [
65] proposed the DRGO (Deep Reinforcement Learning with Genetic Optimization) algorithm, which optimizes real-time offloading decisions by formulating the problem as a Markov Decision Process (MDP). To efficiently offload mining tasks, the algorithm leverages edge computing devices (ECDs) as mining nodes, where blockchain mining tasks are dynamically distributed to nearby edge nodes to reduce latency and computational load. This innovative approach effectively balances computation offloading for blockchain mining and data processing tasks, making it well-suited for dynamic and resource-intensive MEC environments. However, one drawback is that the algorithm is designed around a Proof of Work (PoW)-based consensus mechanism, which is generally resource-intensive and less suitable for the permissioned or lightweight blockchain networks commonly used in MEC settings.
9. Economic and Incentive Models
9.1. Micropayment/Microtransaction
The rise of blockchain technology and the IoT has revolutionized micropayments, enabling small-value transactions between devices. These transactions are crucial in IoT ecosystems, where Machine-to-Machine (M2M) automated payments drive efficiency and functionality.
Micropayments rely heavily on off-chain payment channels to address scalability and costs. Transactions begin with an agreement between participants to lock a predefined cryptocurrency in a blockchain-based smart contract, thus creating a direct channel. Once the channel is established, parties exchange off-chain messages to conduct transactions that are later finalized in the chain. This approach reduces transaction costs and processing time, making it ideal for real-time IoT use cases, such as smart vehicles paying tolls or IoT devices purchasing bandwidths.
DLTs such as blockchain networks and Tangle are foundational for many micropayment solutions. Initiatives such as IOTA’s Tangle showcase DLT’s ability to enable feeless and scalable micropayments tailored for the IoT. Despite these advancements, DLT remains in its exploratory stage for large-scale implementation, with no global standard in place [
66].
Micropayments powered by a blockchain and the IoT have the potential to transform industries by enabling autonomous, cost-effective, and efficient transactions, thus paving the way for a more connected digital future. However, achieving scalability and standardization remains a critical challenge. Micropayments can revolutionize various applications, such as pay-per-use, dynamic pricing, and subscription-based IoT systems. For example, smart appliances can autonomously pay for energy or maintenance services based on real-time usage data. Additionally, by integrating layer 2 solutions, such as payment channels, micropayment systems can achieve faster transaction speeds and reduced costs, thereby overcoming the inherent limitations of the blockchain. These systems also enhance transparency and security and foster trust among users and service providers.
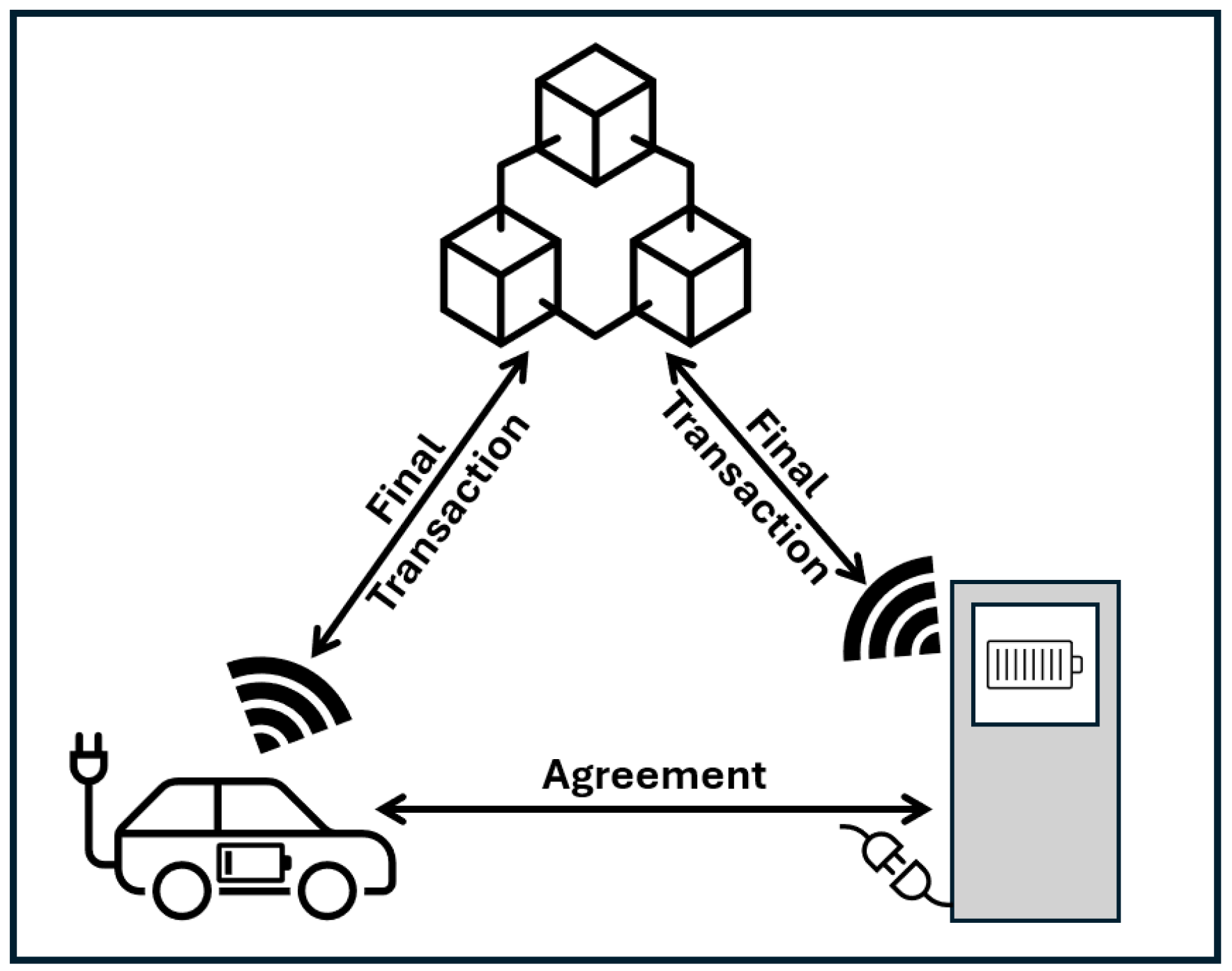
Figure 14 below illustrates a decentralized micropayment system for the IoT. It shows an electric vehicle and a charging station, forming an agreement for energy usage. After completing the transactions, the final settlement is recorded on the blockchain to ensure secure and trustless payment verification. This process emphasizes automated M2M interactions.
9.2. Tokenomics
Digital money is pivotal in advancing the Internet of Things (IoT), particularly in addressing the significant capital and operational costs associated with building and maintaining IoT networks. These costs often make it impractical for a single centralized entity to sustain such networks, prompting the emergence of community-owned and community-operated solutions [
67].
Tokenomics refers to the design and management of blockchain token systems that enable secure, decentralized transactions, incentives, and value exchanges. Fractionalization is the process of dividing an asset into smaller and more manageable parts or units, allowing multiple parties to own, trade, or use portions of the asset. By enabling fractionalization, tokenomics divides assets into smaller units, facilitating the micropayments that are essential for autonomous value exchange between IoT devices. These transactions are executed seamlessly using smart contracts, thereby ensuring both efficiency and scalability. Tokenomics introduces atomic settlement, a mechanism by which assets are exchanged only when specific conditions are met, thereby enabling secure and instantaneous transactions [
68]. By addressing economic and operational challenges, tokenomics fosters scalable and decentralized networks, thereby positioning itself as a cornerstone of future IoT systems.
9.3. Incentivizing IoT Participation
The concept of incentivizing IoT participation has garnered increasing attention as stakeholders seek scalable and cost-effective solutions to support the growing demand for connectivity. While blockchain technology has introduced innovative ways to secure and manage data, its potential to foster community-driven IoT networks remains underexplored, and token incentives can be used to motivate device owners and operators to contribute their resources, such as bandwidth, storage, and coverage, to the network infrastructure. By offering rewards in the form of tokens or cryptocurrencies, these decentralized physical infrastructure networks (DePINs) create an economic model that aligns individual participation with collective network growth.
DePINs enable community-driven ownership and governance, fostering a collaborative and sustainable model. At the core of DePINs is the integration of physical and digital resources, combining physical infrastructure—such as wireless networks, IoT devices, or data storage systems—with blockchain technology to create self-sustaining ecosystems. A DePIN operates through decentralized governance mechanisms like Decentralized Autonomous Organizations (DAOs), allowing stakeholders to make collective decisions without a central authority. To encourage participation, the DePIN utilizes token-based incentives, rewarding individuals or entities that contribute resources such as bandwidth, storage, or computing power. This model not only promotes economic viability but also ensures fairness and transparency through blockchains’ immutable ledgers [
69].
One DePIN-based network is Helium, which leverages blockchain technology to incentivize the deployment and maintenance of wireless hotspots. These hotspots provide LoRaWAN and 5G coverage for IoT devices and mobile users, rewarding participants with HNT tokens through a unique consensus mechanism called Proof of Coverage, which ensures reliable and legitimate network coverage. By distributing the responsibility of network expansion to the community, Helium significantly reduces the capital expenditure typically required for traditional telecom infrastructure, fostering rapid and widespread network growth. The network supports diverse applications such as smart city solutions, environmental monitoring, logistics tracking, and personal device connectivity, demonstrating the versatility and scalability of its decentralized model [
70].
One application of incentivizing network participation is crowdsourcing, particularly in the context of edge-assisted mobile crowdsensing (EMCS), where data are collected from a large number of distributed mobile devices. Traditional incentive mechanisms for participant engagement often rely on centralized platforms, which are incompatible with the decentralized nature of edge environments. To address this, Ying et al. [
71] proposed CHASER, an incentive mechanism designed for blockchain-based EMCS (BEMCS) systems. CHASER satisfies critical requirements such as budget balance, truthfulness, individual rationality, and high social welfare, making it effective at attracting and retaining participants. It also enhances security and privacy by using asymmetric encryption for data confidentiality and Zero-Knowledge Succinct Non-Interactive Argument of Knowledge (zk-SNARK) to ensure participant anonymity and discourage malicious behavior. Experimental results show that CHASER achieves a competitive ratio of approximately 0.8 and a task completion rate exceeding 0.8, highlighting its robustness and efficiency in large-scale decentralized crowdsourcing environments [
71].
10. Decentralized AI and IoT
10.1. Privacy-Preserving Decentralized ML Model Training
Privacy-preserving in AI and ML means implementing strategies and technologies that protect sensitive data while still enabling powerful analytics and model training. In the context of machine learning as a service (MLaaS), it involves employing privacy-enhancing techniques that ensure data confidentiality throughout the entire AI lifecycle. Techniques such as homomorphic encryption (HE), Secure Multi-Party Computation (MPC), differential privacy (DP), federated learning (FL), and Trusted Execution Environments (TEEs) are employed to protect data without compromising on the performance and efficiency of AI models. The goal of privacy-preserving machine learning (PPML) is to build secure and effective systems where the data remain confidential, even while being processed by untrusted servers or third-party service providers [
72].
Another blockchain application in the IoT is PPML, particularly in smart cities, where sensitive data from IoT devices must be processed securely. A recent framework, SecureSVM, demonstrates this application by enabling support vector machine (SVM) training on encrypted IoT data stored in a blockchain network [
73]. SecureSVM leverages a blockchain’s decentralized structure to store encrypted IoT data from multiple providers. Homomorphic encryption allows SVM classifiers to be trained directly on the encrypted data. This approach addresses critical challenges in IoT applications, including data privacy, ownership, and integrity, by securely enabling polynomial operations and comparisons that are necessary for SVM algorithms.
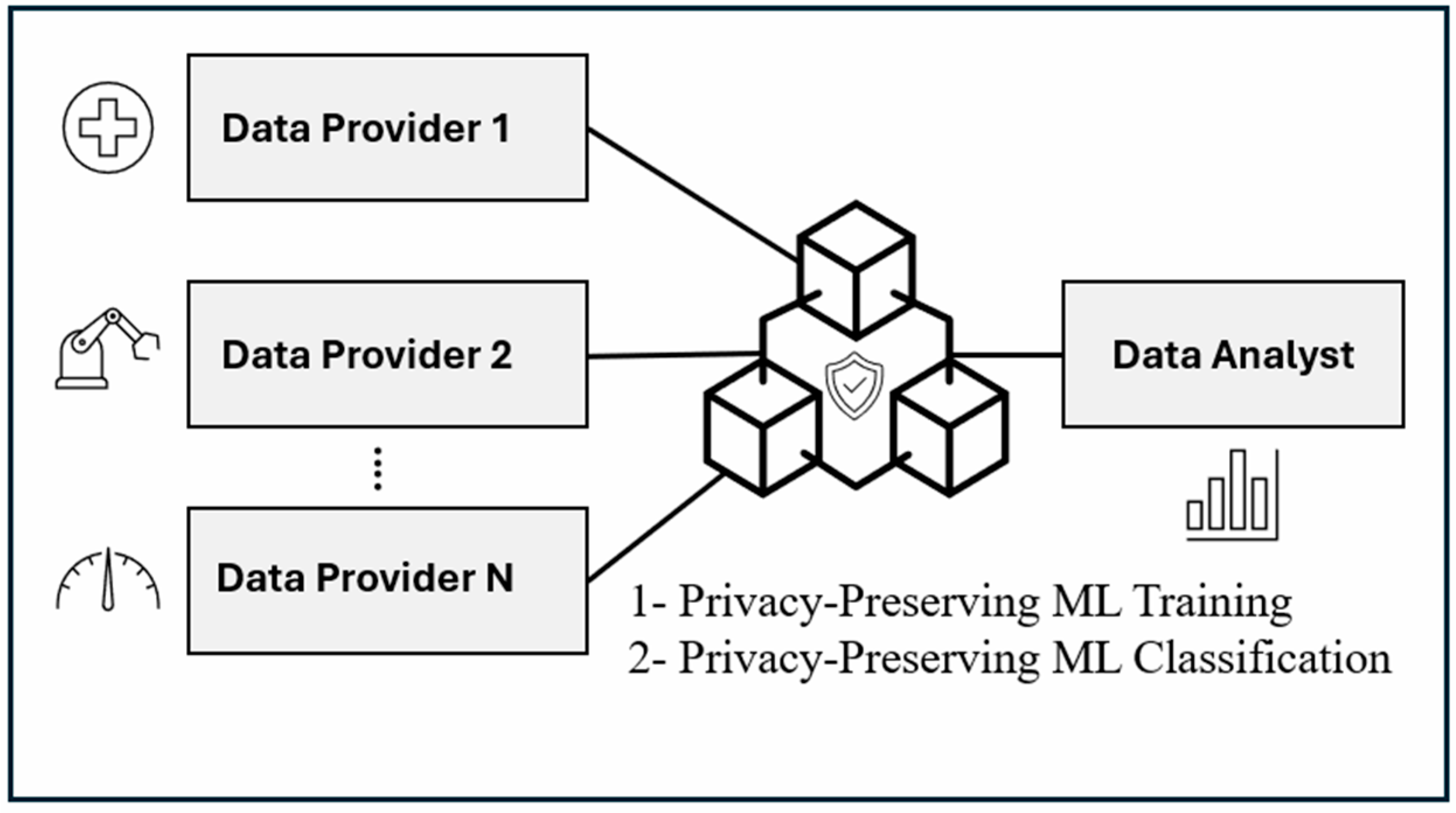
Experiments conducted with SecureSVM demonstrated that SVM classifiers can be effectively trained while preserving data privacy and security, making it a scalable solution for privacy-focused applications in IoT networks. This framework highlights blockchains’ potential to support secure, decentralized machine learning solutions that meet IoT systems’ unique privacy requirements and computational constraints within smart cities.
Figure 15 below shows a block diagram for this system, with the blockchain connecting providers to a data analyst for model training and for classification.
10.2. Federated Learning with Blockchains in the IoT
Federated learning is a decentralized machine learning approach that enables collaborative model training while maintaining data privacy. Instead of sharing raw data, it allows multiple parties to train models locally and only exchange model updates, ensuring sensitive information remains protected. This approach prevents data exposure while still enabling organizations to benefit from collective learning, making it particularly valuable in privacy-sensitive applications.
Blockchain-enabled federated learning (BFL) is an emerging approach to secure and decentralized federated learning, leveraging blockchains to maintain data integrity and accountability. However, BFL faces several critical challenges that can hinder its effectiveness. The first major challenge lies in the model validation process, which involves recruiting distributed validators to evaluate local models. This process is often slow and resource-intensive, creating a significant bottleneck in system performance. The second challenge is related to the incentive system, as blockchains are transparent by nature, which may inadvertently expose sensitive cost information from participants, posing privacy risks. Additionally, the practice of sharing local model updates without adequate protection can lead to data eavesdropping or inference attacks, compromising the confidentiality of participant data. To tackle these issues, Ying et al. [
65] proposed BIT-FL, a blockchain-enabled incentivized and secure federated learning framework. BIT-FL incorporates a loop-based sharded consensus algorithm to expedite model validation, a randomized incentive mechanism with differential privacy to protect cost information, and Gaussian noise to secure local model updates. Experimental evaluations demonstrate that BIT-FL not only enhances efficiency and privacy preservation but also improves robustness against adversarial attacks, making it highly suitable for real-world decentralized federated learning applications.
By integrating federated learning into a permissioned blockchain, this approach enhances security during the data-sharing process without relying on centralized trust. The numerical results in [
74] demonstrate that the blockchain-powered data-sharing scheme effectively safeguards sensitive information while enabling collaborative learning. The synergy between blockchains and federated learning offers a promising solution for secure and intelligent data exchange in the IoT. However, ensuring efficient data privacy protection through blockchains remains an open challenge, requiring further exploration of potential security threats and the development of more advanced privacy-preserving mechanisms.
10.3. AI-Based Smart Contracts
Traditional smart contracts in blockchains consist of a set of rules and conditions that trigger actions based on specific events. AI can be integrated into this logic for a more advanced decision-making process. This concept includes an off-chain component for model training. The resulting model is then inserted into the smart contract to make predictions on-chain [
75].
One application of AI-based smart contracts is in Goal-Oriented Semantic Networks in the 6G automotive sector, where blockchain technology enhances security and automation in Connected and Autonomous Vehicles (CAVs). AI-driven smart contracts enable vehicles to interpret real-time sensor data and execute autonomous decisions based on predefined objectives, such as traffic management, emergency response, and collision avoidance. By integrating semantic filtering and deep reinforcement learning (DRL), these contracts ensure that only meaningful, goal-relevant data are processed, significantly reducing communication overhead and improving efficiency. Furthermore, blockchain-based smart contracts enhance trust and data integrity by securing vehicle-to-vehicle (V2V) and vehicle-to-infrastructure (V2I) transactions, enabling seamless and reliable vehicular operations in the next-generation Intelligent Transport Systems (ITSs) [
76].
11. Digital Assets and NFTs in the IoT
11.1. NFTs
NFTs have revolutionized IoT analytics by providing secure data ownership, management, and monetization frameworks. IoT analytics rely on vast datasets generated by connected devices to derive actionable insights. Tokenization enables these datasets to be represented as digital tokens in the blockchain. Each token signifies ownership or access rights, allowing IoT device owners to monetize their data in decentralized marketplaces while maintaining control and transparency. For instance, a factory’s IoT sensors that monitor production metrics can tokenize real-time data, which can be sold to analytics providers for operational insights. NFTs are uniquely suited for representing proprietary datasets, storing metadata, and ownership details to ensure the authenticity of data streams used in analytics. These technologies enhance data liquidity, decentralize data-sharing ecosystems, and reduce reliance on intermediaries, thus enabling more efficient analytics. By integrating Physically Unclonable Functions (PUFs), IoT systems can further enhance security and trust by generating unique hardware-based identifiers for devices, ensuring data authenticity and tamper resistance [
77].
Multiple tokenization standards exist in the blockchain. ERC-20 [
78], ERC-721 [
79], and ERC-1155 [
80] are Ethereum-token standards. ERC-20 defines fungible tokens (e.g., cryptocurrencies), whereas ERC-721 handles NFTs. ERC-1155 supports both fungible and non-fungible tokens within a single contract and offers greater flexibility and efficiency, particularly for gaming, marketplaces, and multi-asset applications in Ethereum. The process of minting an NFT varies depending on the marketplace and the blockchain used. Each platform (e.g., OpenSea, Rarible, or Ocean Protocol) offers different options for defining ownership rights (exclusive, non-exclusive, royalties, etc.), whereas the blockchain (e.g., Ethereum, Polygon, or Solana) determines the transaction speed, costs (gas fees), and scalability. These factors affect how an NFT is created, stored, and traded.
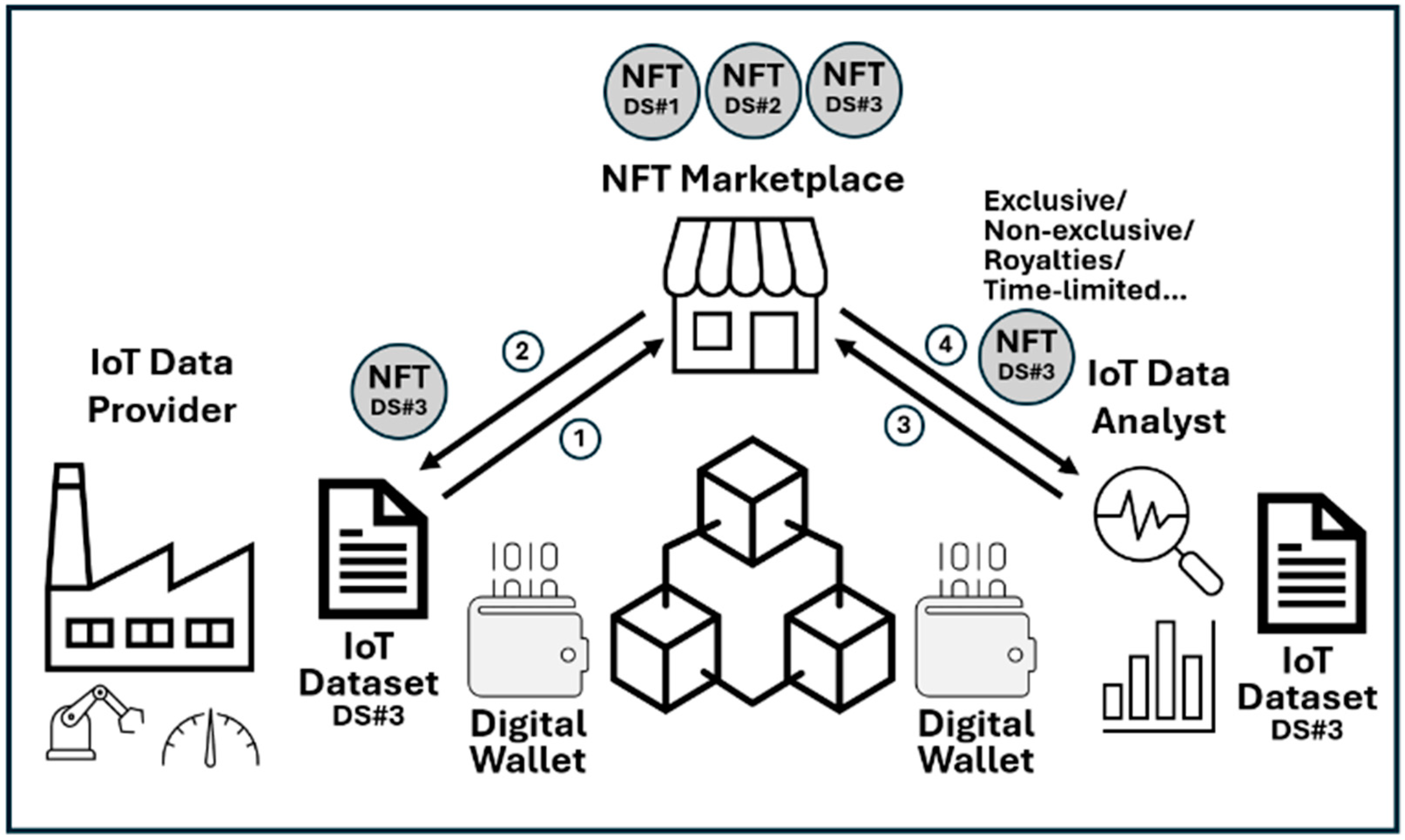
Figure 16 below shows the general steps of NFT minting and trading processes.
IoT data provider mints the dataset as an NFT;
IoT data provider lists the NFT on the marketplace;
Data analysts view NFTs available in the NFT marketplace and buy NFTs for the required dataset. It should be noted that this process has several options:
- ▪
Exclusive: Buyer owns the dataset fully;
- ▪
Non-exclusive: Seller can sell the dataset multiple times;
- ▪
Royalties: Seller receives percentage from any future sale;
- ▪
Time-limited access;
Buyer receives the NFT and uses the dataset for analytics.
Figure 16.
General NFT minting process.
Figure 16.
General NFT minting process.
One example of using NFTs to share data is the Ocean Protocol, which offers a blockchain-based data-sharing marketplace where IoT datasets are tokenized and traded securely. Its unique Compute-to-Data feature allows analytics to be performed on datasets without exposing raw data, thereby ensuring privacy and compliance [
81].
11.2. Blockchain-Based Digital Twin
A digital twin is a virtual replica of a physical object, system, or process that is continuously updated with real-time data, enabling monitoring, simulation, and predictive analysis. They are used in manufacturing, healthcare, smart cities, and aerospace sectors, enhancing decision-making, efficiency, and automation.
Creating a digital twin in many applications requires collaboration among multiple domains and stakeholders, including designers, manufacturers, maintenance personnel, and users. This cross-stage, multi-enterprise cooperation involves integrating various data sources, such as design drawings, geometric models, process plans, and operational data, into a synchronized digital twin model. However, this process faces security challenges because of the involvement of multiple parties who may not fully trust one another. Ensuring data integrity, traceability, and uniqueness is essential to maintain consensus among stakeholders [
82]. Blockchains secure and manage data from IoT devices and digital twins by enabling a decentralized, transparent system for secure, real-time data sharing and verification. This is crucial for handling large-scale IoT data efficiently [
83].
One example is the implementation of digital twins for construction projects [
84]. Blockchain technology provides a framework for tracking file signatures, ensuring authenticity, and preventing tampering. Smart contracts automate construction processes, from project approvals to payments, reducing delays and disputes. By self-executing agreements, blockchain technology streamlines workflows, fosters trust, and improves collaboration.
12. Industry-Specific Applications of Blockchains in the IoT
The integration of blockchain technology with the Internet of Things (IoT) has led to the emergence of various applications that enhance security, transparency, and efficiency across multiple domains. This section reviews the key applications of blockchains in the IoT, highlighting their advantages, challenges, and potential future directions.
12.1. Supply Chain Management
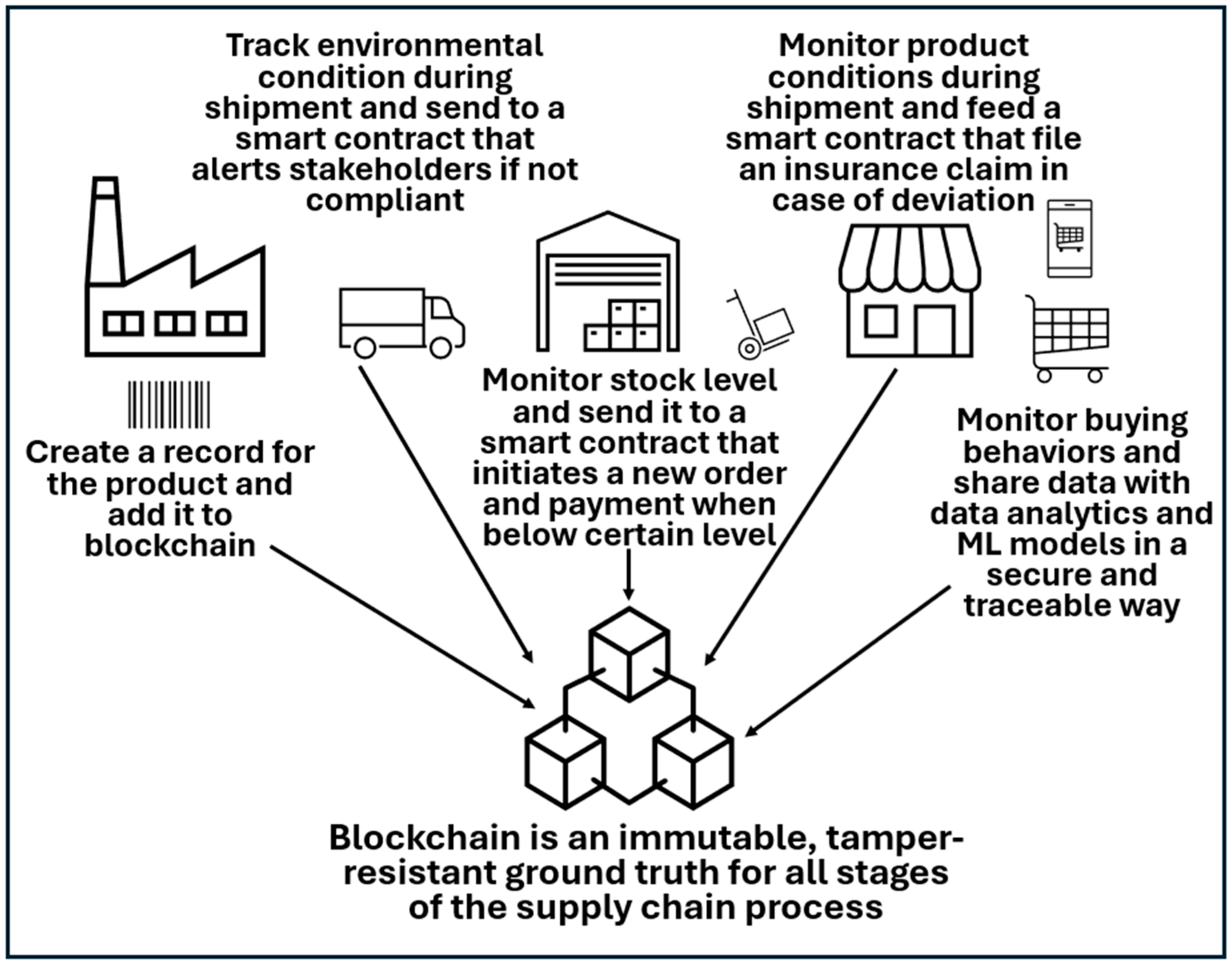
One of the most prominent applications of blockchain technology in the IoT is supply chain management. Blockchain-based IoT systems enable end-to-end visibility in supply chains by securely recording data from IoT sensors during the logistics journey. Each transaction, from manufacturing to delivery, is logged immediately to ensure traceability and transparency. Smart contracts automate payments upon delivery or quality confirmation, thereby reducing manual intervention and disputes. Additionally, smart contracts can be utilized to track IoT-enabled devices and monitor specific conditions such as temperature, humidity, or location during the shipment process. If predefined conditions are not satisfied (e.g., if a temperature-sensitive product exceeds its acceptable range), the smart contract can automatically trigger notifications or penalties. This ensures compliance with agreed-upon terms, enhances accountability, and minimizes losses caused by negligence or environmental factors.
The blockchain also serves as the ground truth for shipment tracking and condition monitoring. It acts as a decentralized ledger in which all stakeholders, including manufacturers, logistics providers, and customers, can access reliable tamper-proof records. These records provide a single source of truth for disputes, claims, and audits, offering unparalleled transparency regarding the movement and handling of goods.
Figure 17 below illustrates how blockchains and the IoT enhance transparency, automation, and security in supply chains.
12.2. Smart Homes and Cities
Another notable application is in smart homes and cities, where blockchains can facilitate secure interactions between IoT devices. IoT devices in smart homes and cities such as smart meters, waste management systems, and traffic controllers generate massive amounts of data. Blockchains ensure the integrity and privacy of data, allowing secure interaction among devices without a centralized authority. For instance, a blockchain-enabled energy-trading platform in a smart grid allows households to trade excess energy securely. Oracles and smart contracts enhance these systems by automating payments and integrating real-world data into blockchain-based applications. Oracles fetch data, such as real-time energy prices, device utilization metrics, or environmental conditions, from external sources and feed them into the blockchain. This enables smart contracts to make informed decisions based on actual data, as in the following examples.
- ▪
Payments for energy usage or waste collection can be automated based on real-time consumption data;
- ▪
Smart contracts can optimize resource utilization by adjusting operations in response to pricing or demand fluctuations, such as shifting energy-intensive tasks to off-peak hours to reduce costs;
- ▪
Traffic systems can dynamically reroute vehicles to improve the traffic flow and reduce fuel consumption and emissions.
Blockchains can enhance cybersecurity in IoT systems by addressing unique challenges such as data integrity and device authentication [
85]. By implementing a blockchain-based architecture, smart home devices can autonomously manage data exchanges while ensuring that interactions are secure and tamper-proof [
86]. This application is particularly relevant as the number of connected devices continues to grow, necessitating robust security measures to protect against hacking and data breach [
87].
12.3. The Industrial IoT (IIoT)
In industrial environments, IoT sensors track equipment performance and production metrics. Blockchains can enhance the IIoT by ensuring tamper-proof data logging, enabling predictive maintenance, and creating audit trials for compliance. In addition, blockchains can facilitate secure and private data-sharing with data analytics providers. Using encryption and permissioned access mechanisms, a blockchain ensures that sensitive industrial data are accessible only to authorized entities. Analytics providers can access anonymized or aggregated data stored in the blockchain, thereby preserving privacy and enabling valuable insights. This secure framework encourages collaboration between industrial operators and analytics firms, leading to improved decision-making and operational efficiency.
NFTs offer a novel way to monetize and distribute data. Industrial data such as equipment performance metrics or production insights can be tokenized as NFTs and sold over the blockchain. This approach enables data owners to monetize valuable datasets while maintaining transparency and control. By purchasing NFTs, analytics providers can access high-quality datasets to enhance their models and machine-learning algorithms, resulting in better outcomes in predictive maintenance, quality control, and supply chain optimization.
Smart contracts play a critical role in automating industrial functions and optimizing costs. For instance, smart contracts can dynamically update based on real-life electricity rates obtained from oracles. This allows industrial systems to shift energy-intensive tasks to times when electricity rates are lower, thereby significantly reducing operational costs. By automating such energy-optimization processes, blockchain-based systems can enhance the efficiency and sustainability of industrial environments.
12.4. Transportation
Blockchains and the IoT can power autonomous vehicles by securing communication among vehicles, infrastructure, and cloud platforms. Smart contracts facilitate toll payments, parking fees, or even peer-to-peer car sharing without intermediaries. For instance, a charging station can dynamically adjust pricing based on demand and vehicles equipped with blockchain wallets can execute payments instantly and securely. This eliminates the need for centralized billing systems and ensures a seamless, automated user experience.
Payment channels are instrumental in enhancing the scalability of these applications. Payment channels, a type of layer 2 solution, allow multiple transactions to occur off-chain between two parties, with only the final state recorded on the blockchain. This reduces the load on the main blockchain network, enabling it to handle high volumes of micropayments for tolls, parking, and charging without congestion or high transaction fees, as shown in the following examples.
- ▪
A vehicle can use a payment channel to prepay for multiple small transactions (e.g., tolls on a long trip), settling the total on-chain only when the channel is closed;
- ▪
Parking or charging providers can aggregate payments across multiple vehicles, reducing operational overhead.
12.5. Agriculture
IoT sensors in agriculture monitor soil conditions, weather, and crop health. Blockchains can store this data securely, facilitating transparent supply chains for organic production and fair-trade certifications. In addition, blockchain-based insurance contracts powered by smart contracts and oracles offer a transformative solution for agricultural risk management. Oracles fetch real-time weather data, such as temperature, rainfall, or drought indices, and feed them into the blockchain. Smart contracts use these data to evaluate predefined conditions, such as the following:
- ▪
High temperatures that exceed thresholds for crop safety;
- ▪
Low rainfall rates that indicate drought conditions.
When these conditions are satisfied, the smart contract automatically triggers an insurance claim. This eliminates the need for manual processing, reduces delays, and ensures that farmers promptly receive compensation. For example, if rainfall in a specific region drops below a critical level, the smart contract can verify the data from the oracle, validate the claim, and instantly pay the insured farmer. This approach is explained in
Figure 18 below and benefits both insurers and farmers:
- ▪
For insurers, automated claims reduce administrative costs and the risk of disputes because the process relies on objective and verifiable data;
- ▪
For farmers, payments are processed faster, providing financial relief during critical periods and minimizing the impact of crop losses.
Figure 18.
Blockchain and IoT in agriculture.
Figure 18.
Blockchain and IoT in agriculture.
12.6. Healthcare
Blockchains can effectively mitigate the risks of cyberattacks and data breaches in IoT systems within the healthcare sector by establishing a decentralized, tamper-resistant, and transparent data management framework. The integration of blockchain technology into healthcare IoT environments addresses critical security challenges by leveraging immutable ledgers to ensure data integrity and secure communication between interconnected devices [
88]. Through the use of multichain blockchain architecture, healthcare systems can implement robust access control mechanisms using smart contracts, which define granular permissions for devices and stakeholders, thereby reducing unauthorized access and manipulation of sensitive patient data. Moreover, consensus mechanisms embedded within blockchain networks enhance data validation processes, maintaining the accuracy and authenticity of medical records while eliminating single points of failure that are common in traditional centralized systems [
88].
In another example, multi-blockchain architecture can be leveraged to overcome the limitations of traditional centralized electronic medical record (EMR) systems that are prone to data breaches and inefficiencies in multiparty data sharing [
89]. This innovative approach combines a consortium main chain with multiple sidechains to securely store public and private medical data while optimizing data retrieval through the use of the JSON format. An improved Practical Byzantine Fault Tolerant (PBFT) consensus mechanism enhances the network’s resilience against dishonest nodes, ensuring higher consensus efficiency and data integrity. Additionally, integrating role-based access control (RBAC) with smart contracts provides dynamic and delegable permissions, giving patients greater control over their medical information while facilitating secure data access for healthcare professionals and institutions. By adopting this architecture, healthcare systems can achieve a secure, efficient, and scalable solution for managing sensitive medical data [
89].
13. Challenges
Despite these advantages, the integration of blockchains with the IoT presents challenges, particularly in terms of scalability and performance. The scalability limitations of blockchain networks can hinder their effectiveness in low-power IoT sensor networks that often require real-time data processing [
90]. Additionally, the energy consumption associated with blockchain operations can be a significant barrier to its widespread adoption in resource-constrained IoT environments [
91]. Addressing these challenges is essential for the successful deployment of blockchain technology in IoT applications.
One significant challenge lies in consensus algorithms, which have high communication overhead, particularly in systems that utilize PBFT. While PBFT is effective in smaller networks, its scalability diminishes as the number of nodes increases, leading to performance bottlenecks due to the time required for node communication and consensus [
92]. These limitations can hinder the adoption of blockchain technology in applications with high-frequency transactions, such as microgrid power trading, where the demand for quick and efficient processing of numerous low-value transactions is critical [
93].
Additionally, the traditional Proof of Work (PoW) consensus mechanism is criticized for its extreme energy consumption, rendering it less sustainable and practical [
94]. Although alternatives like PoS and DPoS offer more energy-efficient methods, they introduce new scalability challenges and potential centralization issues, impacting the distributed nature of blockchain systems [
95].
Blockchain technology is also vulnerable to cybersecurity attacks aimed at targeting distributed ledgers and their consensus algorithms. Singh et al. (2021) explored the security challenges of blockchain-based IoT networks, highlighting vulnerabilities such as 51% attacks, double-spending, Sybil attacks, and private key security threats, while also proposing countermeasures to enhance blockchain resilience in distributed IoT environments [
96].
Interoperability is another challenge with blockchains, as different blockchain networks operate on varied data structures, scalability models, and consensus mechanisms, despite their shared reliance on a decentralized peer-to-peer (P2P) framework. The lack of interoperability leads to fragmented industrial ecosystems, restricted information exchange, and isolated blockchain networks that hinder seamless collaboration. To enhance blockchain adoption, efforts should focus on enabling cross-chain data integration and standardization. Key initiatives addressing this issue include the Enterprise Ethereum Alliance, ITU-T, ISO, SWIFT, and W3C, which are working towards developing interoperability frameworks to bridge the gaps between disparate blockchain systems [
97].
Blockchain technology faces legal and regulatory challenges. Understanding how blockchain technology functions is crucial for developing effective regulations. Many nations are integrating blockchains into regulatory frameworks that address centralization, data privacy, jurisdictional issues, and smart contract governance. Additionally, legal and technological approaches interact, where cost-effective technical solutions may replace legal mechanisms in governance. Blockchains’ role in smart contracts and decentralized databases is reshaping legal and administrative boundaries, promoting new governance models that enhance efficiency, fairness, and legal certainty [
98].
14. Conclusions
This survey underscores the significant role of blockchain technology in revolutionizing IoT systems by addressing challenges related to security, privacy, scalability, and operational efficiency. The integration of blockchains and the IoT offers transformative capabilities, enabling decentralized data management, trustless automation, and enhanced transparency. By leveraging tools, such as smart contracts, decentralized ledgers, and tokenization, blockchain technology enhances the overall functionality and trustworthiness of IoT ecosystems across various industries. Industry-specific applications, such as supply chain management, healthcare, and smart environments, demonstrate blockchains’ potential to optimize operations, ensure regulatory compliance, and foster innovation.
However, despite their numerous advantages, blockchain-based IoT systems face several challenges, including scalability, energy consumption, and interoperability. The emergence of layer 2 scaling solutions such as payment channels, rollups, and plasma offer promising avenues for overcoming these limitations by reducing on-chain congestion and transaction costs. Additionally, a hybrid architecture that combines blockchains with edge and cloud computing can enhance processing efficiency and support the IoT’s data-intensive demands.
Moreover, the development of standardized protocols and interoperable frameworks is essential for fostering global blockchain-based IoT ecosystems. Policy-makers, developers, and industry stakeholders must collaborate to address regulatory barriers, ensure data sovereignty, and develop scalable solutions tailored for diverse applications. As these technologies continue to evolve, blockchains have become the backbone of next-generation Internet of Things (IoT) systems, driving innovation, efficiency, and trust across interconnected industries.
In summary, while significant progress has been made, the future of blockchain-enabled IoT systems lies in addressing the current challenges and leveraging advancements in complementary technologies. Such efforts will ultimately pave the way for a secure, scalable, and interconnected digital landscape.