Anomaly Detection in Blockchain: A Systematic Review of Trends, Challenges, and Future Directions
Abstract
1. Introduction
- We present a bibliometric mapping of blockchain anomaly detection research from 2017 to 2024 based on 363 articles indexed in WoSCC. The analysis outlines the global research landscape, major thematic areas, and the evolution of key topics in this rapidly developing field.
- Using CiteSpace v6.4.R1, we conducted analyses of country and institutional collaboration networks, co-citation networks, references with citation bursts, and keyword co-occurrence. These results uncover the intellectual structure of the field and identify influential authors, leading institutions, and methodological innovations.
- Through keyword timeline and burst detection, we highlight a shift in research focus from foundational mechanisms, such as rule-based and consensus-level detection—to advanced approaches including unsupervised learning, lightweight federated learning, and graph neural networks. These insights help researchers to understand how the field is evolving and where innovation is emerging.
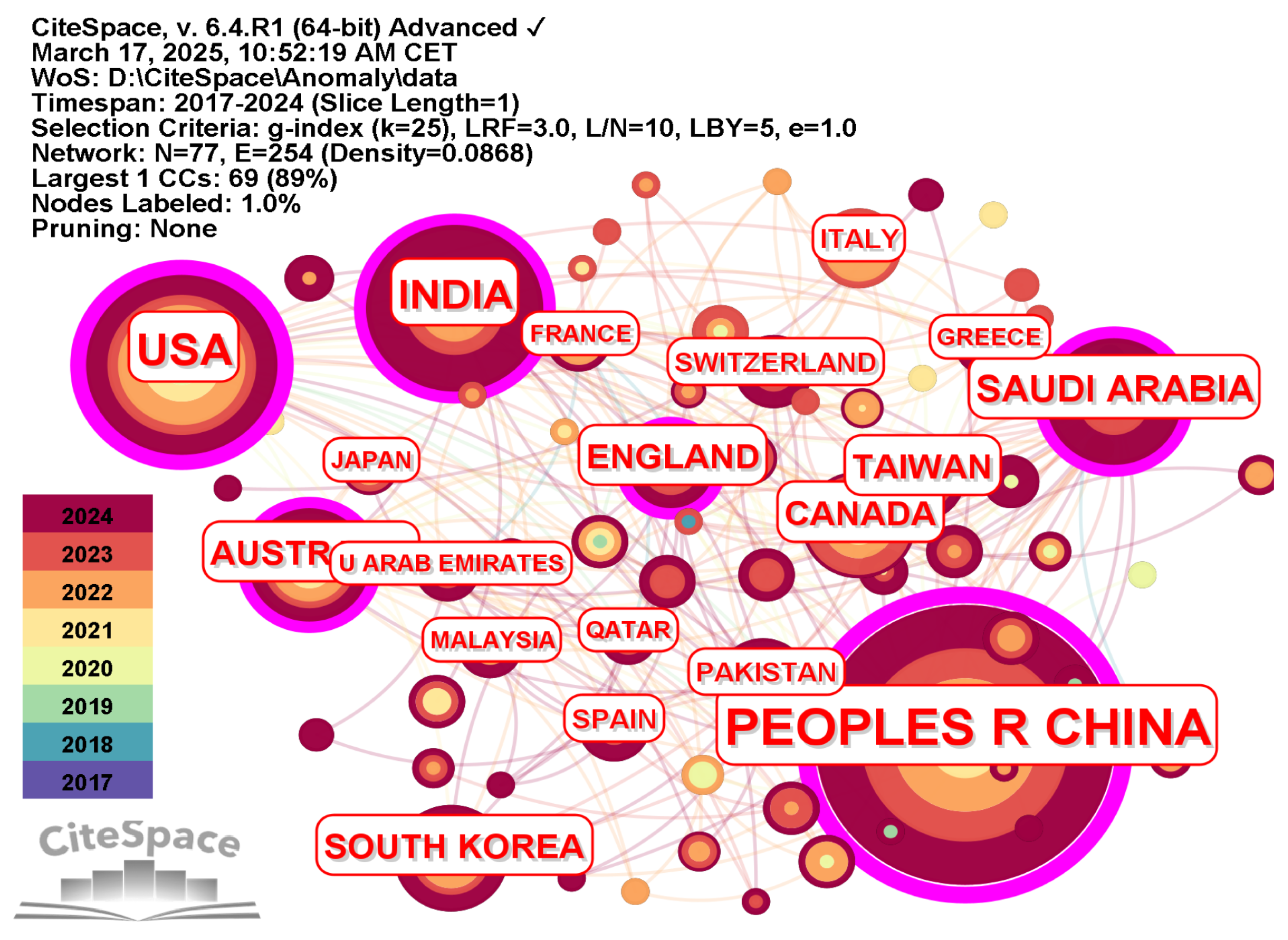
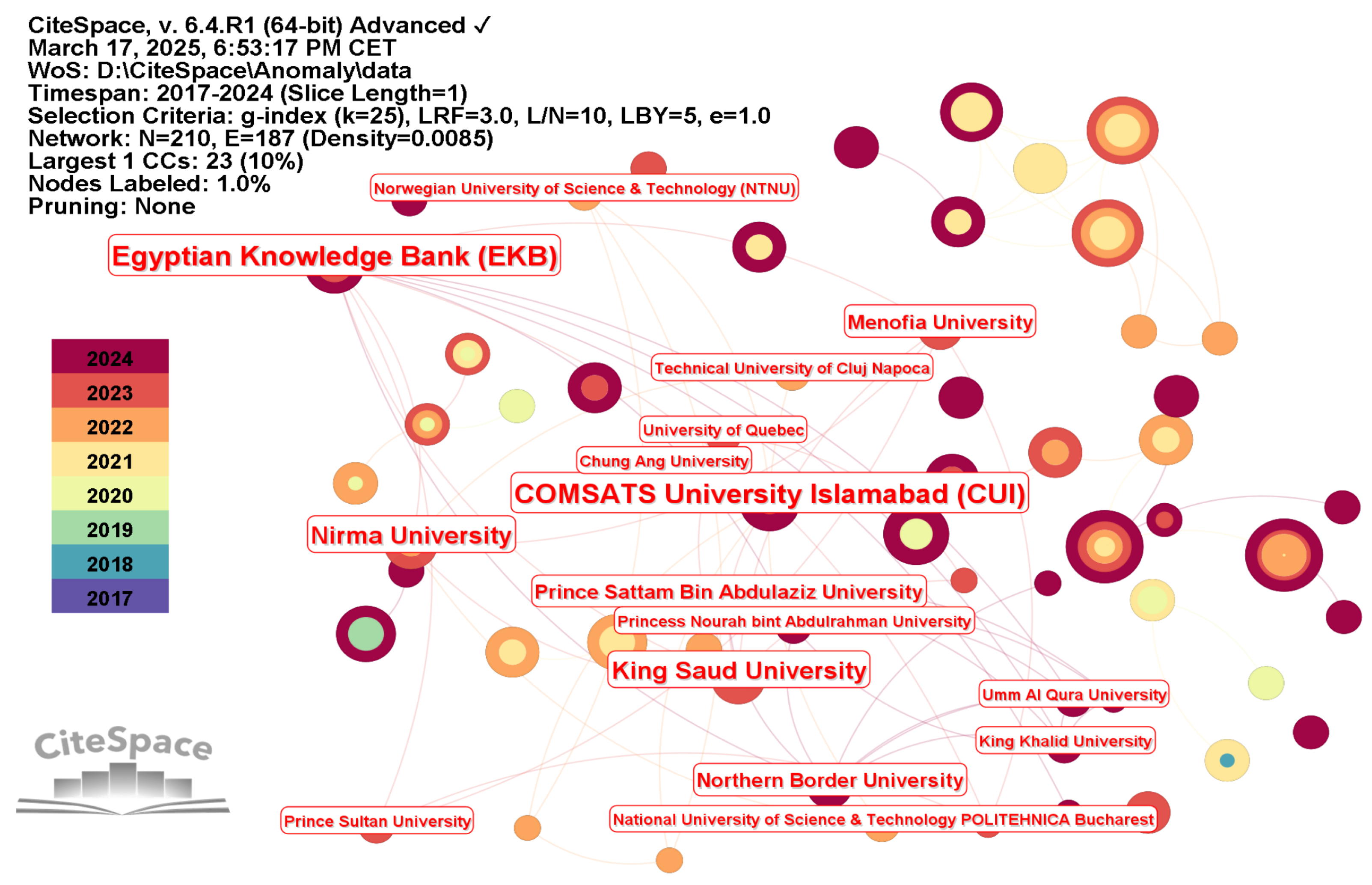
- Our analysis reveals distinct geographical clusters of research activity, with China, the United States, and India dominating publication output. Key institutions identified as major contributors include Beijing University of Posts and Telecommunications (China), Brandon University (Canada), and Nirma University (India). The most productive scholars hail predominantly from Canada, India, and China, collectively forming the core group driving the field’s publication impact.
- We outline open challenges and future research directions in blockchain anomaly detection, including federated learning and privacy-preserving techniques, the integration of multimodal and heterogeneous data sources, the development of explainable and interpretable AI models, real-time adaptive detection systems, cross-domain specialized applications, and the imperative need for standardization and regulatory frameworks.
2. Materials and Methods
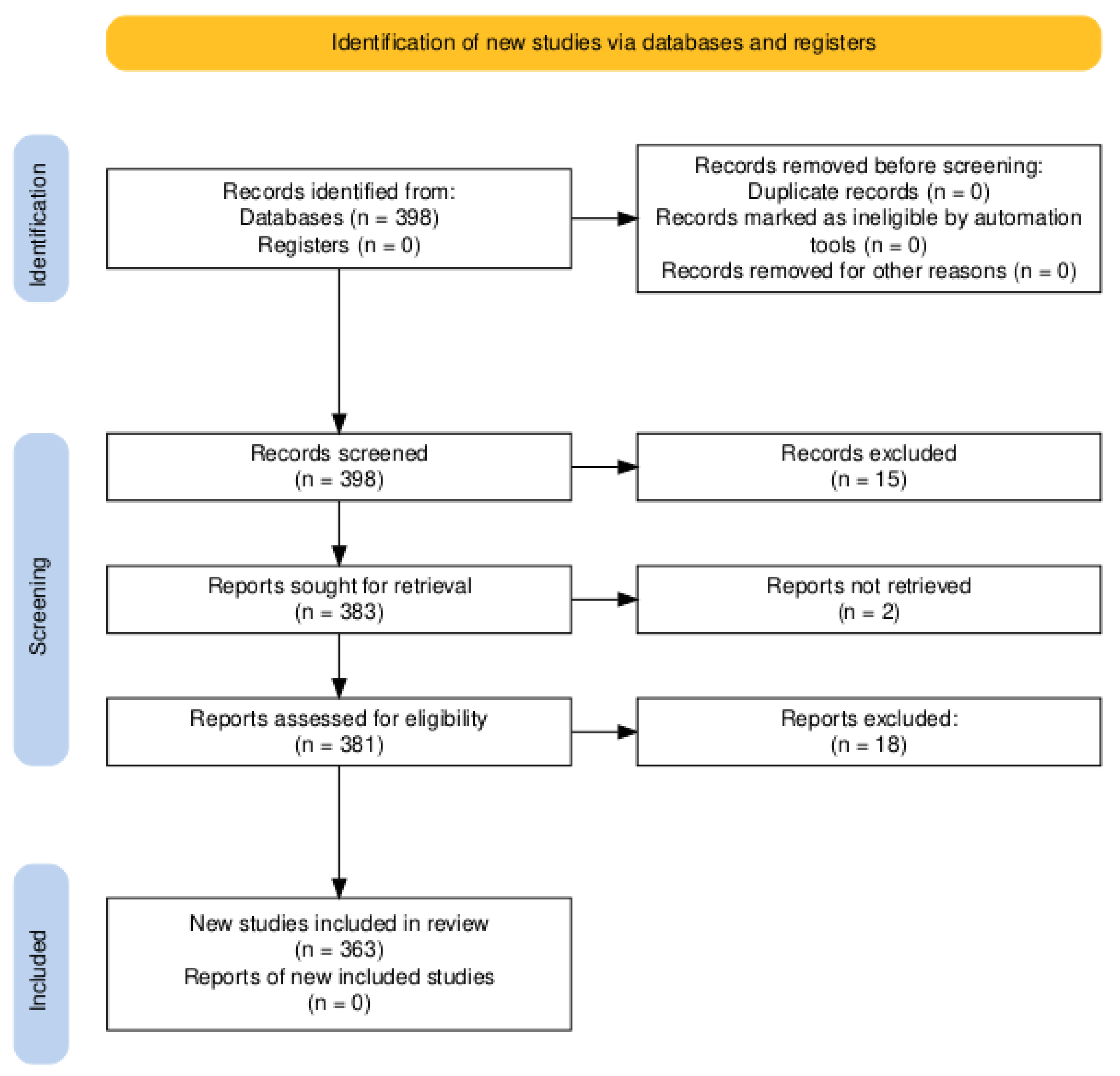
2.1. Data Collection
2.2. Research Methodology
3. Results
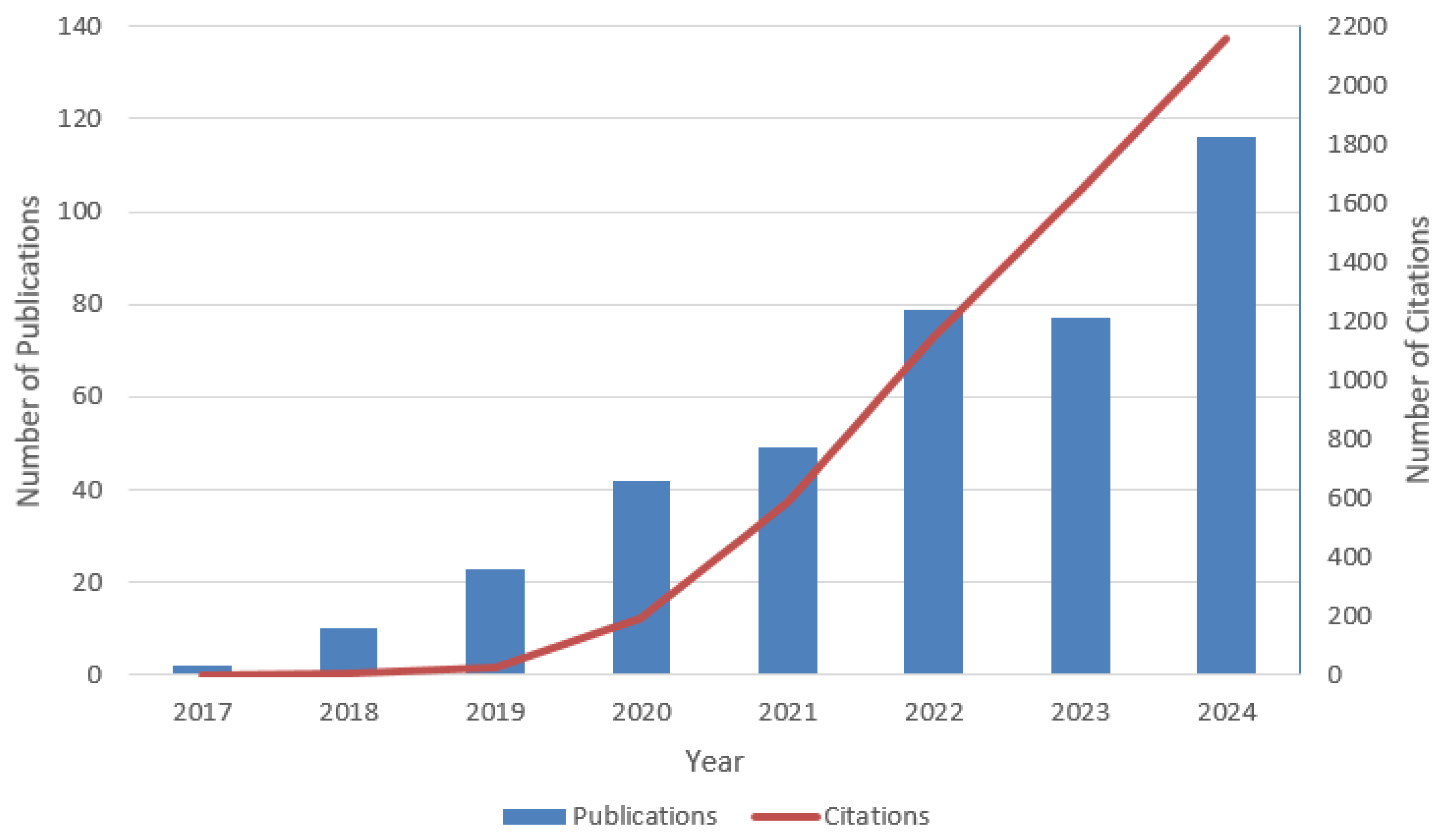
3.1. Assessment of Publication Count
3.2. Analysis of the Collaboration Network Among Countries
3.3. Analysis of the Collaboration Network Involving Leading Institutions
3.4. The Analysis of the Collaboration Network Leading Authors
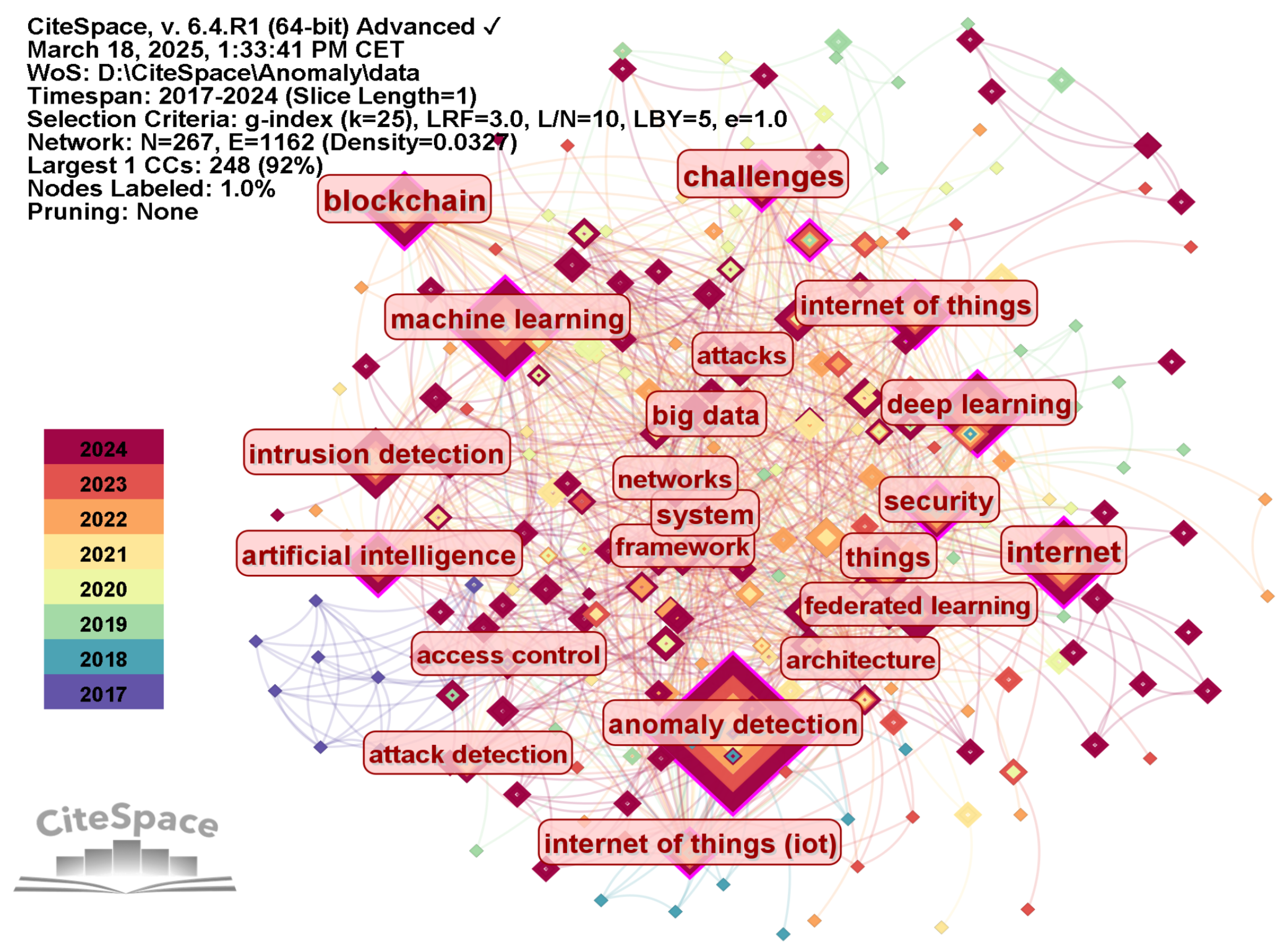
3.5. Keyword Network Analysis

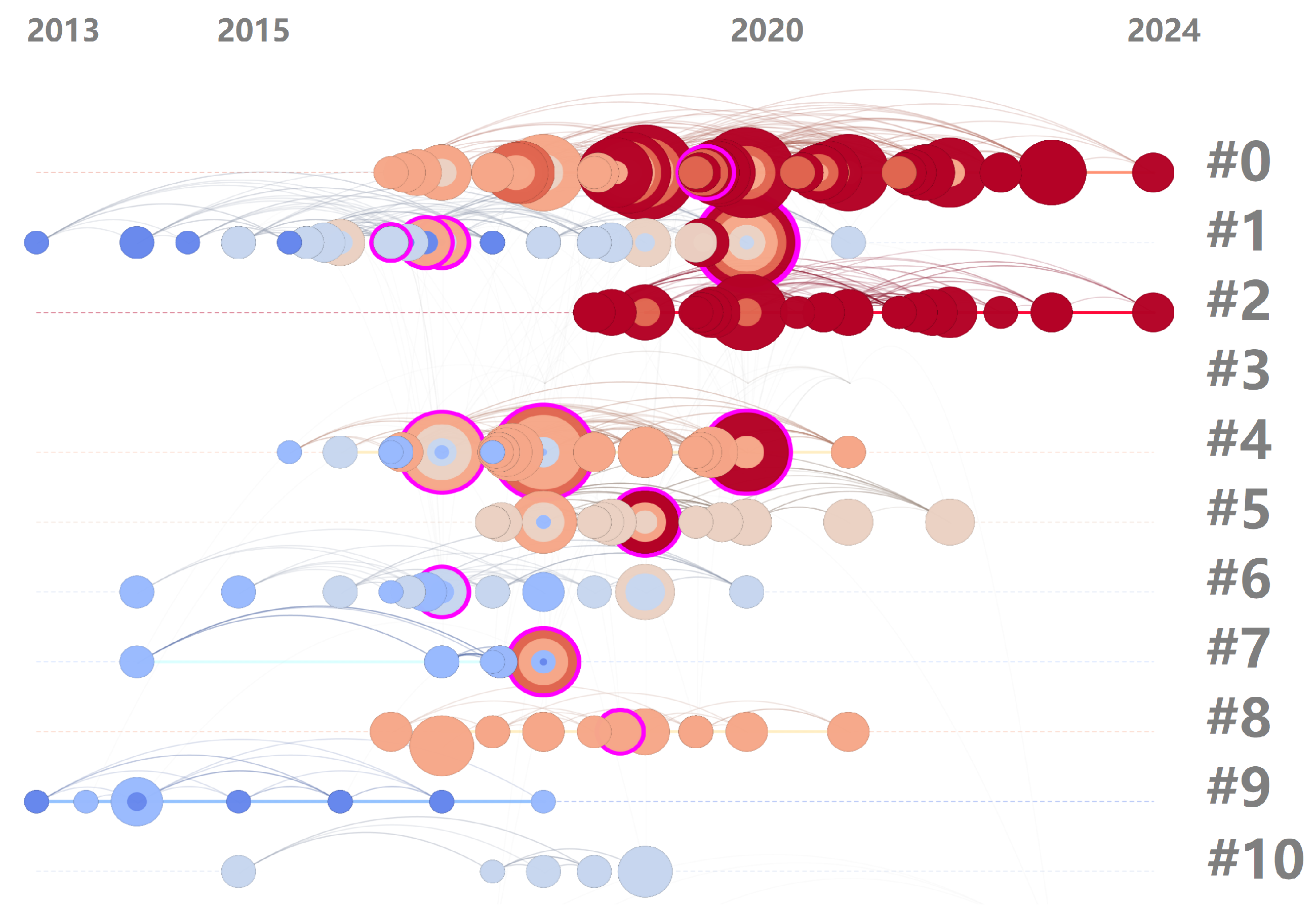
3.6. Research Hotspots and Evolution Trend Analysis
4. Discussion
4.1. Comparative Analysis with the Existing Literature
4.2. Drivers and Implications of Research Trends
4.3. Limitations of the Study
4.4. Open Challenges and Future Directions
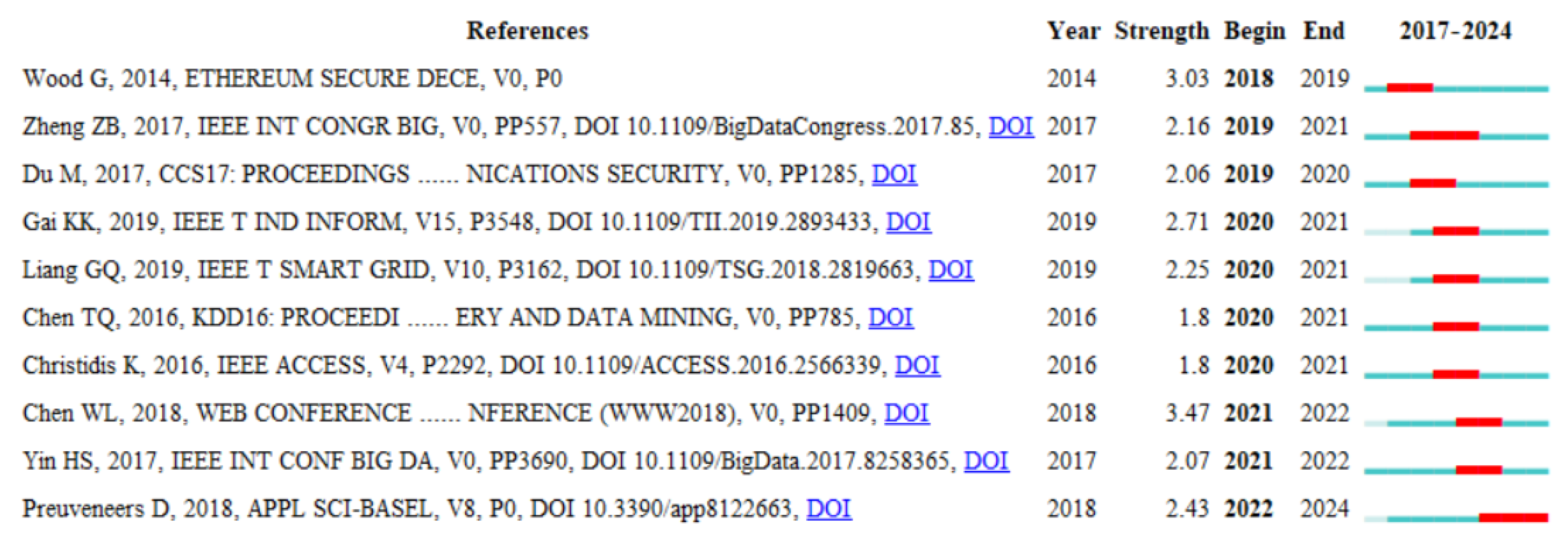
- Federated learning and privacy-preserving technologies. The analysis of the keyword map (Figure 5), timeline map of reference co-citation (Figure 8), citation bursts (Figure 9), and core publications in cluster #2 demonstrates a growing interest in federated learning and highlights open challenges within the context of blockchain security [27,78,79,80,81,82,83,87,90]. Combining blockchain with federated learning offers a unique opportunity to create transparent, auditable anomaly detection models without centralizing training data. However, several open challenges remain, which future research will need to address to advance the domain:
- developing attack-resistant federated models for anomaly detection in scalable blockchain networks;
- implementing differential privacy techniques in federated models to balance detection accuracy with user privacy protection.
- Integration of multimodadata and heterogeneous sources. The analysis of the keyword map (Figure 5), timeline map of reference co-citation (Figure 8), citation bursts (Figure 9), and core publications in clusters related to machine and deep learning (specifically, clusters #0, #3, #4) demonstrates a growing interest in comprehensive approaches to anomaly detection. Current research reveals a significant shift from one-dimensional transaction analysis, based on individual data types, to an all-encompassing approach that considers diverse aspects of blockchain data [26,33,55,56,61,66,67,68,73,91,95,96,97,98,100,101,103,140]. This shift underscores the need for integrating heterogeneous data to enhance the effectiveness of detecting complex anomalies that might be unnoticeable when analyzing only one type of information. Achieving such integration in blockchain anomaly detection requires robust systems capable of securely managing and processing diverse datasets. In this context, innovative data storage and processing systems such as SecuDB [141], LedgerDB [142], and VeDB [143] can play a pivotal role. These technologies provide a high level of security, data integrity, and verifiability, which are critically important for identifying deviations from normal behavior in decentralized environments. Future research in this direction may include the following:
- developing algorithms that simultaneously analyze on-chain and off-chain data for comprehensive anomaly detection;
- creating systems that integrate blockchain data with traditional financial transactions to detect cross-platform fraud schemes;
- applying natural language processing methods to analyze smart contracts along with user behavioral patterns;
- leveraging secure database technologies to provide scalable and tamper-resistant analytics platforms.
- Explainable AI and interpretable detection models. The results of our study demonstrate a clear shift from basic security mechanisms to sophisticated machine learning and graph neural network approaches in blockchain anomaly detection. Specifically, some publications in clusters related to machine and deep learning (e.g., clusters #0, #3, #4) reveal a growing interest in employing these advanced methods [66,67,68,69,70,99,106]. Many research studies use ensemble learning and explainable AI for fraud detection in blockchain transactions, indicating the growing importance of interpretability in AI-based security solutions [65,144,145,146,147]. This direction highlights the need for transparency in complex models, such as those used in deep and unsupervised learning, so that their decisions are understandable to security experts. Future research will likely pay more attention to the following:
- developing anomaly detection models with built-in mechanisms for interpreting results;
- creating intuitive visual explanations for identified anomalies to help security experts make informed decisions;
- combining expert knowledge and algorithmic approaches to form hybrid detection systems with improved interpretability.
- Real-time and adaptive detection systems. The increasing complexity of fraud schemes and the rapid evolution of attack methods fundamentally necessitate the development of anomaly detection systems that operate in real-time. This need is not merely theoretical but is clearly demonstrated by the characteristics and demands of various application domains, as reflected in several prominent co-citation clusters (#1, #5, #6, #7, #8, #10). For instance, in the publications associated with cluster #1 [71,73,77], which focus on cryptocurrency networks, the speed and unpredictability of attacks necessitate immediate detection and rapid, adaptive responses to emerging malicious behaviors. A similar urgency is evident in sustainable smart cities (cluster #5) [107,108,109,110,111,112] and industrial networks (cluster #6) [58,113,116,117], where massive volumes of real-time data are continuously generated by IoT and IIoT devices. In such environments, timely and adaptive anomaly detection is critical to ensure the uninterrupted operation of essential infrastructure and safeguard public safety. The situation is even more acute in the domain of smart contracts (cluster #7) [98,124,125], where anomalies such as vulnerabilities or malicious executions can result in immediate and irreversible financial damages. Moreover, the emergence of 5G advanced networks (cluster #8) [126,130], characterized by ultra-low latency and high throughput, both enables and necessitates the deployment of anomaly detection systems that can match the network’s speed and complexity. These systems must be capable of processing vast data flows with minimal delay while maintaining high detection accuracy. Lastly, the publications in cluster #10 [98,133,134] highlight that highly dynamic and heterogeneous ecosystems require continuous anomaly identification and response mechanisms that can adapt in real time to evolving threats, device malfunctions, or behavioral deviations. Despite the lack of pronounced representation in recent citation bursts, the shift toward real-time, adaptive anomaly detection is a critical direction for practical applications of academic research. Moving forward, this entails the following:
- implementing incremental learning methods to continuously adapt models to new types of attacks;
- developing early warning systems capable of detecting anomalies at the formation stage;
- creating distributed monitoring systems that minimize detection latency without compromising accuracy.
- Cross-domain integration and specialized applications. The analysis of the keyword map (Figure 5), the timeline map of reference co-citation (Figure 8), and the core publications in clusters #5, #6, and #10 reveals a consistent and accelerating trend toward the specialization of anomaly detection methods tailored to distinct application domains within the blockchain security ecosystem. In particular, publications in cluster #5 emphasize the integration of blockchain-based security mechanisms into smart city infrastructures [107,110]. The convergence of diverse IoT devices and public service networks necessitates anomaly detection approaches that are domain-aware and capable of responding to complex interdependencies between systems. Cluster #6 publications [58,113,116,117] focus on the implementation of anomaly detection in operational technology and industrial control system environments. These settings, characteristic of Industry 4.0, require context-specific models that support real-time monitoring and low-latency decision-making. Cluster #10 publications [98,133,134] address the distinct challenges of securing resource-constrained IoT devices that operate within or alongside blockchain frameworks. Given the heterogeneous nature of IoT ecosystems and their vulnerability to both device-level and network-level threats, this area underscores the need for lightweight, efficient, and adaptive anomaly detection methods. These thematic concentrations point toward several key directions for future research:
- developing specialized anomaly detection models for industrial blockchain systems in the context of Industry 4.0;
- creating lightweight algorithms for resource-constrained IoT devices in blockchain networks;
- integrating blockchain security with traditional critical infrastructure security systems.
- Standardization and regulatory frameworks. Numerous review studies [31,36,38,105,133] consistently highlight persistent challenges, open questions, and the lack of unified methodologies, all of which hinder the large-scale adoption and interoperability of anomaly detection systems across different blockchain platforms. This fragmentation not only complicates technical integration but also impairs collective efforts to combat cyber threats in blockchain ecosystems. Moreover, research focusing on anomaly detection within highly regulated or financially sensitive domains—such as finance, emergency management, healthcare, cybersecurity, and critical energy infrastructure—emphasizes the urgent need for international cooperation [19,69,96,103,125,147,148]. In these sectors, combating cybercrime, including fraud and anomalous behavior, is a critical priority. Addressing this challenge requires the establishment of harmonized regulatory frameworks and international standards that can ensure the effectiveness and interoperability of anomaly detection systems, regardless of their underlying architecture or blockchain platform. Accordingly, future research and policy development should prioritize the following:
- developing harmonized methodologies for evaluating the effectiveness of anomaly detection systems in blockchain;
- forming international standards for the interoperability of anomaly detection systems across different blockchain platforms.
4.5. Main Findings
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Payandeh, R.; Delbari, A.; Fardad, F.; Helmzadeh, J.; Shafiee, S.; Ghatari, A.R. Unraveling the potential of blockchain technology in enhancing supply chain traceability: A systematic literature review and modeling with ISM. Blockchain Res. Appl. 2024, 6, 100240. [Google Scholar] [CrossRef]
- Rajasekaran, A.S.; Azees, M.; Al-Turjman, F. A comprehensive survey on blockchain technology. Sustain. Energy Technol. Assessments 2022, 52, 102039. [Google Scholar] [CrossRef]
- Bennet, D.; Maria, L.; Sanjaya, Y.P.A.; Zahra, A.R.A. Blockchain technology: Revolutionizing transactions in the digital age. ADI J. Recent Innov. 2024, 5, 192–199. [Google Scholar] [CrossRef]
- Javaid, M.; Haleem, A.; Singh, R.P.; Suman, R.; Khan, S. A review of Blockchain Technology applications for financial services. BenchCouncil Trans. Benchmarks, Stand. Eval. 2022, 2, 100073. [Google Scholar] [CrossRef]
- Moosavi, J.; Naeni, L.M.; Fathollahi-Fard, A.M.; Fiore, U. Blockchain in supply chain management: A review, bibliometric, and network analysis. Environ. Sci. Pollut. Res. 2021, 1–15. [Google Scholar] [CrossRef]
- Ghosh, P.K.; Chakraborty, A.; Hasan, M.; Rashid, K.; Siddique, A.H. Blockchain application in healthcare systems: A review. Systems 2023, 11, 38. [Google Scholar] [CrossRef]
- Rejeb, A.; Rejeb, K.; Appolloni, A.; Jagtap, S.; Iranmanesh, M.; Alghamdi, S.; Alhasawi, Y.; Kayikci, Y. Unleashing the power of internet of things and blockchain: A comprehensive analysis and future directions. Internet Things Cyber-Phys. Syst. 2024, 4, 1–18. [Google Scholar] [CrossRef]
- Cheshun, V.; Muliar, I.; Yatskiv, V.; Shevchuk, R.; Kulyna, S.; Tsavolyk, T. Safe Decentralized Applications Development Using Blockchain Technologies. In Proceedings of the 2020 10th International Conference on Advanced Computer Information Technologies (ACIT), Deggendorf, Germany, 16–18 September 2020; pp. 800–805. [Google Scholar] [CrossRef]
- Shevchuk, R.; Lishchynskyy, I.; Ciura, M.; Lyzun, M.; Kozak, R.; Kasianchuk, M. Application of Blockchain Technology in Emergency Management Systems: A Bibliometric Analysis. Appl. Sci. 2025, 15, 5405. [Google Scholar] [CrossRef]
- Lukić, I.; Köhler, M.; Krpić, Z.; Švarcmajer, M. Advancing Smart City Sustainability Through Artificial Intelligence, Digital Twin and Blockchain Solutions. Technologies 2025, 13, 300. [Google Scholar] [CrossRef]
- Singh, S.; Hosen, A.S.; Yoon, B. Blockchain security attacks, challenges, and solutions for the future distributed iot network. IEEE Access 2021, 9, 13938–13959. [Google Scholar] [CrossRef]
- Kuznetsov, O.; Sernani, P.; Romeo, L.; Frontoni, E.; Mancini, A. On the integration of artificial intelligence and blockchain technology: A perspective about security. IEEE Access 2024, 12, 3881–3897. [Google Scholar] [CrossRef]
- Aggarwal, S.; Kumar, N. Attacks on blockchain. In Advances in Computers; Elsevier: Amsterdam, The Netherlands, 2021; Volume 121, pp. 399–410. [Google Scholar]
- Mahtani, U.S. Fraudulent practices and blockchain accounting systems. J. Account. Ethics Public Policy 2022, 23, 97. [Google Scholar]
- Shevchuk, R.; Martsenyuk, V. Neural networks toward cybersecurity: Domaine map analysis of state-of-the-art challenges. IEEE Access 2024, 12, 81265–81280. [Google Scholar] [CrossRef]
- Krause, D. The $1.4 Billion Bybit Hack: Cybersecurity Failures and the Risks of Cryptocurrency Deregulation. 2025. Available online: https://ssrn.com/abstract=5150171 (accessed on 30 March 2025).
- Partz, H. Atomic Wallet Faces Lawsuit over $100M Crypto Hack Losses: Report. 2025. Available online: https://cointelegraph.com/news/crypto-atomic-wallet-faces-class-action-over-100m-crypto-hack-losses (accessed on 30 March 2025).
- Chainalysis. The Chainalysis 2025 Crypto Crime Report. 2025. Available online: http://go.chainalysis.com/2025-Crypto-Crime-Report.html (accessed on 30 March 2025).
- Kovalchuk, O.; Shevchuk, R.; Banakh, S. Cryptocurrency crime risks modeling: Environment, e-commerce, and cybersecurity issue. IEEE Access 2024, 12, 50673–50688. [Google Scholar] [CrossRef]
- Turksen, U.; Benson, V.; Adamyk, B. Legal implications of automated suspicious transaction monitoring: Enhancing integrity of AI. J. Bank. Regul. 2024, 25, 359–377. [Google Scholar] [CrossRef]
- Adamyk, B.; Benson, V.; Adamyk, O.; Liashenko, O. Risk Management in DeFi: Analyses of the Innovative Tools and Platforms for Tracking DeFi Transactions. J. Risk Financ. Manag. 2025, 18, 38. [Google Scholar] [CrossRef]
- Hafid, A.; Hafid, A.S.; Samih, M. A tractable probabilistic approach to analyze sybil attacks in sharding-based blockchain protocols. IEEE Trans. Emerg. Top. Comput. 2022, 11, 126–136. [Google Scholar] [CrossRef]
- Arifeen, M.M.; Al Mamun, A.; Ahmed, T.; Kaiser, M.S.; Mahmud, M. A blockchain-based scheme for sybil attack detection in underwater wireless sensor networks. In Proceedings of the International Conference on Trends in Computational and Cognitive Engineering: Proceedings of TCCE 2020; Springer: Berlin/Heidelberg, Germany, 2021; pp. 467–476. [Google Scholar]
- Xu, J.J. Are blockchains immune to all malicious attacks? Financ. Innov. 2016, 2, 25. [Google Scholar] [CrossRef]
- König, L.; Unger, S.; Kieseberg, P.; Tjoa, S.; Blockchains, J.R.C. The Risks of the Blockchain A Review on Current Vulnerabilities and Attacks. J. Internet Serv. Inf. Secur. 2020, 10, 110–127. [Google Scholar]
- Du, M.; Li, F.; Zheng, G.; Srikumar, V. Deeplog: Anomaly detection and diagnosis from system logs through deep learning. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017; pp. 1285–1298. [Google Scholar]
- Preuveneers, D.; Rimmer, V.; Tsingenopoulos, I.; Spooren, J.; Joosen, W.; Ilie-Zudor, E. Chained anomaly detection models for federated learning: An intrusion detection case study. Appl. Sci. 2018, 8, 2663. [Google Scholar] [CrossRef]
- Sayadi, S.; Rejeb, S.B.; Choukair, Z. Anomaly detection model over blockchain electronic transactions. In Proceedings of the 2019 15th International Wireless Communications & Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 895–900. [Google Scholar]
- Farrugia, S.; Ellul, J.; Azzopardi, G. Detection of illicit accounts over the Ethereum blockchain. Expert Syst. Appl. 2020, 150, 113318. [Google Scholar] [CrossRef]
- Apiecionek, Ł.; Karbowski, P. Fuzzy Neural Network for Detecting Anomalies in Blockchain Transactions. Electronics 2024, 13, 4646. [Google Scholar] [CrossRef]
- Hassan, M.U.; Rehmani, M.H.; Chen, J. Anomaly detection in blockchain networks: A comprehensive survey. IEEE Commun. Surv. Tutor. 2022, 25, 289–318. [Google Scholar] [CrossRef]
- Mounnan, O.; Manad, O.; Boubchir, L.; El Mouatasim, A.; Daachi, B. A review on deep anomaly detection in blockchain. Blockchain Res. Appl. 2024, 5, 100227. [Google Scholar] [CrossRef]
- Cholevas, C.; Angeli, E.; Sereti, Z.; Mavrikos, E.; Tsekouras, G.E. Anomaly detection in blockchain networks using unsupervised learning: A survey. Algorithms 2024, 17, 201. [Google Scholar] [CrossRef]
- Chithanuru, V.; Ramaiah, M. An anomaly detection on blockchain infrastructure using artificial intelligence techniques: Challenges and future directions—A review. Concurr. Comput. Pract. Exp. 2023, 35, e7724. [Google Scholar] [CrossRef]
- Tien, H.T.; Tran-Trung, K.; Hoang, V.T. Blockchain-data mining fusion for financial anomaly detection: A brief review. Procedia Comput. Sci. 2024, 235, 478–483. [Google Scholar] [CrossRef]
- Liu, Z.; Gao, H.; Lei, H.; Liu, Z.; Liu, C. Blockchain anomaly transaction detection: An overview, challenges, and open issues. In Proceedings of the International Conference on Information Science, Communication and Computing, Chongqing, China, 2–5 June 2023; Springer: Berlin/Heidelberg, Germany, 2023; pp. 126–140. [Google Scholar]
- Li, X.; Jiang, P.; Chen, T.; Luo, X.; Wen, Q. A survey on the security of blockchain systems. Future Gener. Comput. Syst. 2020, 107, 841–853. [Google Scholar] [CrossRef]
- Xu, T.; Liu, Z.; Gao, H.; Lei, H.; Ma, Q. Anomaly Detection on Blockchain in Financial Fields: A Comprehensive Survey. In Proceedings of the 2024 4th International Conference on Computer Communication and Artificial Intelligence (CCAI), Xi’an, China, 24–26 May 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 199–207. [Google Scholar]
- Clarivate. Web of Science—Web of Science Group. 2025. Available online: https://clarivate.com/academia-government/scientific-and-academic-research/research-discovery-and-referencing/web-of-science/ (accessed on 10 March 2025).
- Falagas, M.E.; Pitsouni, E.I.; Malietzis, G.A.; Pappas, G. Comparison of PubMed, Scopus, web of science, and Google scholar: Strengths and weaknesses. FASEB J. 2008, 22, 338–342. [Google Scholar] [CrossRef]
- Martín-Martín, A.; Thelwall, M.; Orduna-Malea, E.; Delgado López-Cózar, E. Google Scholar, Microsoft Academic, Scopus, Dimensions, Web of Science, and OpenCitations’ COCI: A multidisciplinary comparison of coverage via citations. Scientometrics 2021, 126, 871–906. [Google Scholar] [CrossRef]
- Sohrabi, C.; Franchi, T.; Mathew, G.; Kerwan, A.; Nicola, M.; Griffin, M.; Agha, M.; Agha, R. PRISMA 2020 statement: What’s new and the importance of reporting guidelines. Int. J. Surg. 2021, 88, 105918. [Google Scholar] [CrossRef] [PubMed]
- Moher, D.; Liberati, A.; Tetzlaff, J.; Altman, D.G. Preferred reporting items for systematic reviews and meta-analyses: The PRISMA statement. BMJ 2009, 339. [Google Scholar] [CrossRef]
- Haddaway, N.R.; Page, M.J.; Pritchard, C.C.; McGuinness, L.A. PRISMA2020: An R package and Shiny app for producing PRISMA 2020-compliant flow diagrams, with interactivity for optimised digital transparency and Open Synthesis. Campbell Syst. Rev. 2022, 18, e1230. [Google Scholar] [CrossRef] [PubMed]
- Peng, C.; Xia, F.; Naseriparsa, M.; Osborne, F. Knowledge graphs: Opportunities and challenges. Artif. Intell. Rev. 2023, 56, 13071–13102. [Google Scholar] [CrossRef]
- Lin, M.; Chen, Y.; Chen, R. Bibliometric analysis on Pythagorean fuzzy sets during 2013–2020. Int. J. Intell. Comput. Cybern. 2021, 14, 104–121. [Google Scholar] [CrossRef]
- Zhang, J.; Quoquab, F. Documenting the knowledge of pro-environmental travel behaviour research: A visual analysis using CiteSpace. J. Tour. Futur. 2022, 10, 277–298. [Google Scholar] [CrossRef]
- Behl, R.; Sharma, S. Will Cryptocurrency Become the Future of Digital India? A Comparative Study of Generation Y and Z to Identify the Intention to Adopt Cryptocurrency. In Corporate Democracy, Open Innovation, and Growth: Business Transformation in Developing Economies; Springer: Berlin/Heidelberg, Germany, 2024; pp. 183–207. [Google Scholar]
- Wired. Saudi Arabia Unveils More Than $6.4 bn in Technology and Startup Investment at LEAP22. 2022. Available online: https://www.thenationalnews.com/business/technology/2022/02/01/saudi-arabia-unveils-more-than-64bn-in-technology-and-start-up-investment-at-leap/ (accessed on 17 March 2025).
- MSCA Digital Finance. Anomaly and Fraud Detection in Blockchain Networks. 2024. Available online: https://www.digital-finance-msca.com/blockchain?utm_source=chatgpt.com (accessed on 11 March 2025).
- Austrian Institute of Technology. Project to Prevent Criminal Use of Blockchain Technology Launched by International Consortium. 2017. Available online: https://www.interpol.int/ar/1/1/2017/Project-to-prevent-criminal-use-of-blockchain-technology-launched-/by-international-consortium (accessed on 17 March 2025).
- Ontochain. A New Software Ecosystem for Trusted, Traceable and Transparent Ontological Knowledge. 2025. Available online: https://ontochain.ngi.eu/ (accessed on 17 March 2025).
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An overview of blockchain technology: Architecture, consensus, and future trends. In Proceedings of the 2017 IEEE international congress on big data (BigData congress), Honolulu, HI, USA, 25–30 June 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 557–564. [Google Scholar]
- Chen, W.; Zheng, Z.; Cui, J.; Ngai, E.; Zheng, P.; Zhou, Y. Detecting ponzi schemes on ethereum: Towards healthier blockchain technology. In Proceedings of the 2018 World Wide Web Conference, Lyon, France, 23–27 April 2018; pp. 1409–1418. [Google Scholar]
- Yin, H.S.; Vatrapu, R. A first estimation of the proportion of cybercriminal entities in the bitcoin ecosystem using supervised machine learning. In Proceedings of the 2017 IEEE International Conference on Big Data (Big Data), Boston, MA, USA, 11–14 December 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 3690–3699. [Google Scholar]
- Liang, G.; Weller, S.R.; Luo, F.; Zhao, J.; Dong, Z.Y. Distributed blockchain-based data protection framework for modern power systems against cyber attacks. IEEE Trans. Smart Grid 2018, 10, 3162–3173. [Google Scholar] [CrossRef]
- Gai, K.; Wu, Y.; Zhu, L.; Qiu, M.; Shen, M. Privacy-preserving energy trading using consortium blockchain in smart grid. IEEE Trans. Ind. Informatics 2019, 15, 3548–3558. [Google Scholar] [CrossRef]
- Christidis, K.; Devetsikiotis, M. Blockchains and smart contracts for the internet of things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Chen, T.; Guestrin, C. XGBoost: A scalable tree boosting system. In Proceedings of the 22nd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, San Francisco, CA, USA, 13–17 August 2016; ACM: New York, NY, USA, 2016; pp. 785–794. [Google Scholar]
- Chen, W.; Zheng, Z.; Ngai, E.C.H.; Zheng, P.; Zhou, Y. Exploiting blockchain data to detect smart ponzi schemes on ethereum. IEEE Access 2019, 7, 37575–37586. [Google Scholar] [CrossRef]
- Hisham, S.; Makhtar, M.; Aziz, A.A. Combining multiple classifiers using ensemble method for anomaly detection in blockchain networks: A comprehensive review. Int. J. Adv. Comput. Sci. Appl. 2022, 13, 8. [Google Scholar] [CrossRef]
- Kamišalić, A.; Kramberger, R.; Fister, I., Jr. Synergy of blockchain technology and data mining techniques for anomaly detection. Appl. Sci. 2021, 11, 7987. [Google Scholar] [CrossRef]
- Kabla, A.H.H.; Anbar, M.; Manickam, S.; Al-Amiedy, T.A.; Cruspe, P.B.; Al-Ani, A.K.; Karuppayah, S. Applicability of intrusion detection system on Ethereum attacks: A comprehensive review. IEEE Access 2022, 10, 71632–71655. [Google Scholar] [CrossRef]
- Kamran, M.; Rehan, M.M.; Nisar, W.; Rehan, M.W. AHEAD: A Novel Technique Combining Anti-Adversarial Hierarchical Ensemble Learning with Multi-Layer Multi-Anomaly Detection for Blockchain Systems. Big Data Cogn. Comput. 2024, 8, 103. [Google Scholar] [CrossRef]
- Hasan, M.; Rahman, M.S.; Janicke, H.; Sarker, I.H. Detecting anomalies in blockchain transactions using machine learning classifiers and explainability analysis. Blockchain Res. Appl. 2024, 5, 100207. [Google Scholar] [CrossRef]
- Podgorelec, B.; Turkanović, M.; Karakatič, S. A machine learning-based method for automated blockchain transaction signing including personalized anomaly detection. Sensors 2019, 20, 147. [Google Scholar] [CrossRef]
- Ashfaq, T.; Khalid, R.; Yahaya, A.S.; Aslam, S.; Azar, A.T.; Alsafari, S.; Hameed, I.A. A machine learning and blockchain based efficient fraud detection mechanism. Sensors 2022, 22, 7162. [Google Scholar] [CrossRef]
- Li, X.; Yang, Y.; Li, B.; Li, M.; Zhang, J.; Li, T. Blockchain cryptocurrency abnormal behavior detection based on improved graph convolutional neural networks. In Proceedings of the 2023 International Conference on Data Security and Privacy Protection (DSPP), Xi’an, China, 16–18 October 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 216–222. [Google Scholar]
- Behdadnia, T.; Thoelen, K.; Zobiri, F.; Deconinck, G. Spatial-temporal graph neural network for detecting and localizing anomalies in pmu networks. In Proceedings of the European Dependable Computing Conference, Leuven, Belgium, 8–11 April 2024; Springer: Berlin/Heidelberg, Germany, 2024; pp. 75–82. [Google Scholar]
- Apostolaki, M.; Zohar, A.; Vanbever, L. Hijacking bitcoin: Routing attacks on cryptocurrencies. In Proceedings of the 2017 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–24 May 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 375–392. [Google Scholar]
- Dai, Y.; Xu, D.; Zhang, K.; Maharjan, S.; Zhang, Y. Deep reinforcement learning and permissioned blockchain for content caching in vehicular edge computing and networks. IEEE Trans. Veh. Technol. 2020, 69, 4312–4324. [Google Scholar] [CrossRef]
- Rahouti, M.; Xiong, K.; Ghani, N. Bitcoin concepts, threats, and machine-learning security solutions. IEEE Access 2018, 6, 67189–67205. [Google Scholar] [CrossRef]
- Alkadi, O.; Moustafa, N.; Turnbull, B. A review of intrusion detection and blockchain applications in the cloud: Approaches, challenges and solutions. IEEE Access 2020, 8, 104893–104917. [Google Scholar] [CrossRef]
- Belhadi, A.; Djenouri, Y.; Srivastava, G.; Lin, J.C.W. SS-ITS: Secure scalable intelligent transportation systems. J. Supercomput. 2021, 77, 7253–7269. [Google Scholar] [CrossRef]
- Shao, W.; Wang, Z.; Wang, X.; Qiu, K.; Jia, C.; Jiang, C. LSC: Online auto-update smart contracts for fortifying blockchain-based log systems. Inf. Sci. 2020, 512, 506–517. [Google Scholar] [CrossRef]
- Hu, Z.; Yu, X.; Liu, L.; Zhang, Y.; Yu, H. ASOD: An Adaptive Stream Outlier Detection Method Using Online Strategy. J. Cloud Comput. 2024, 13, 120. [Google Scholar] [CrossRef]
- Pokhrel, S.R.; Yang, L.; Rajasegarar, S.; Li, G. Robust Zero Trust Architecture: Joint Blockchain based Federated learning and Anomaly Detection based Framework. In Proceedings of the SIGCOMM Workshop on Zero Trust Architecture for Next Generation Communications, Sydney, Australia, 4–8 August 2024; pp. 7–12. [Google Scholar]
- Wang, X.; Liu, W.; Lin, H.; Hu, J.; Kaur, K.; Hossain, M.S. AI-empowered trajectory anomaly detection for intelligent transportation systems: A hierarchical federated learning approach. IEEE Trans. Intell. Transp. Syst. 2022, 24, 4631–4640. [Google Scholar] [CrossRef]
- Cui, L.; Qu, Y.; Xie, G.; Zeng, D.; Li, R.; Shen, S.; Yu, S. Security and privacy-enhanced federated learning for anomaly detection in IoT infrastructures. IEEE Trans. Ind. Informatics 2021, 18, 3492–3500. [Google Scholar] [CrossRef]
- Liu, S.; Shang, Y. Federated learning with anomaly client detection and decentralized parameter aggregation. In Proceedings of the 2022 52nd Annual IEEE/IFIP International Conference on Dependable Systems and Networks Workshops (DSN-W), Baltimore, MD, USA, 27–30 June 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 37–43. [Google Scholar]
- Arazzi, M.; Nicolazzo, S.; Nocera, A. A fully privacy-preserving solution for anomaly detection in iot using federated learning and homomorphic encryption. Inf. Syst. Front. 2023, 27, 367–390. [Google Scholar] [CrossRef]
- Lu, Y.; Huang, X.; Dai, Y.; Maharjan, S.; Zhang, Y. Blockchain and federated learning for privacy-preserved data sharing in industrial IoT. IEEE Trans. Ind. Inform. 2019, 16, 4177–4186. [Google Scholar] [CrossRef]
- Derhab, A.; Guerroumi, M.; Gumaei, A.; Maglaras, L.; Ferrag, M.A.; Mukherjee, M.; Khan, F.A. Blockchain and random subspace learning-based IDS for SDN-enabled industrial IoT security. Sensors 2019, 19, 3119. [Google Scholar] [CrossRef] [PubMed]
- Mothukuri, V.; Khare, P.; Parizi, R.M.; Pouriyeh, S.; Dehghantanha, A.; Srivastava, G. Federated-learning-based anomaly detection for IoT security attacks. IEEE Internet Things J. 2021, 9, 2545–2554. [Google Scholar] [CrossRef]
- Alsaedi, A.; Moustafa, N.; Tari, Z.; Mahmood, A.; Anwar, A. TON_IoT telemetry dataset: A new generation dataset of IoT and IIoT for data-driven intrusion detection systems. IEEE Access 2020, 8, 165130–165150. [Google Scholar] [CrossRef]
- Ali, S.; Li, Q.; Yousafzai, A. Blockchain and federated learning-based intrusion detection approaches for edge-enabled industrial IoT networks: A survey. Ad Hoc Netw. 2024, 152, 103320. [Google Scholar] [CrossRef]
- Messinis, S.; Temenos, N.; Protonotarios, N.E.; Rallis, I.; Kalogeras, D.; Doulamis, N. Enhancing Internet of Medical Things security with artificial intelligence: A comprehensive review. Comput. Biol. Med. 2024, 170, 108036. [Google Scholar] [CrossRef]
- Alzoubi, Y.I.; Mishra, A.; Topcu, A.E. Research trends in deep learning and machine learning for cloud computing security. Artif. Intell. Rev. 2024, 57, 132. [Google Scholar] [CrossRef]
- Park, J.H.; Yotxay, S.; Singh, S.K.; Park, J.H. PoAh-enabled federated learning architecture for DDoS attack detection in IoT networks. Hum.-Centric Comput. Inf. Sci. 2024, 14, 1–25. [Google Scholar]
- Wijesekara, P.A.D.S.N.; Gunawardena, S. A review of blockchain technology in knowledge-defined networking, its application, benefits, and challenges. Network 2023, 3, 343–421. [Google Scholar] [CrossRef]
- Rico-Pena, J.J.; Arguedas-Sanz, R.; Lopez-Martin, C. Models used to characterise blockchain features. A systematic literature review and bibliometric analysis. Technovation 2023, 123, 102711. [Google Scholar] [CrossRef]
- Alkadi, O.; Moustafa, N.; Turnbull, B.; Choo, K.K.R. A deep blockchain framework-enabled collaborative intrusion detection for protecting IoT and cloud networks. IEEE Internet Things J. 2020, 8, 9463–9472. [Google Scholar] [CrossRef]
- Dey, S. Securing majority-attack in blockchain using machine learning and algorithmic game theory: A proof of work. In Proceedings of the 2018 10th Computer Science and Electronic Engineering (CEEC), Colchester, UK, 19–21 September 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 7–10. [Google Scholar]
- Salah, K.; Rehman, M.H.U.; Nizamuddin, N.; Al-Fuqaha, A. Blockchain for AI: Review and open research challenges. IEEE Access 2019, 7, 10127–10149. [Google Scholar] [CrossRef]
- Song, A.; Seo, E.; Kim, H. Anomaly VAE-transformer: A deep learning approach for anomaly detection in decentralized finance. IEEE Access 2023, 11, 98115–98131. [Google Scholar] [CrossRef]
- Ge, B.; Bao, J.; Li, B.; Mou, X.; Zhao, J.; Liu, X. Img: Deep representation graph learning for anomaly detection in industrial control system. J. Signal Process. Syst. 2024, 96, 555–567. [Google Scholar] [CrossRef]
- Demertzis, K.; Iliadis, L.; Tziritas, N.; Kikiras, P. Anomaly detection via blockchained deep learning smart contracts in industry 4.0. Neural Comput. Appl. 2020, 32, 17361–17378. [Google Scholar] [CrossRef]
- Zkik, K.; Sebbar, A.; Fadi, O.; Kamble, S.; Belhadi, A. Securing blockchain-based crowdfunding platforms: An integrated graph neural networks and machine learning approach. Electron. Commer. Res. 2024, 24, 497–533. [Google Scholar] [CrossRef]
- Mathew, S.S.; Hayawi, K.; Dawit, N.A.; Taleb, I.; Trabelsi, Z. Integration of blockchain and collaborative intrusion detection for secure data transactions in industrial IoT: A survey. Clust. Comput. 2022, 25, 4129–4149. [Google Scholar] [CrossRef]
- Khonde, S.R.; Ulagamuthalvi, V. Hybrid intrusion detection system using blockchain framework. EURASIP J. Wirel. Commun. Netw. 2022, 2022, 58. [Google Scholar] [CrossRef]
- Liang, W.; Xiao, L.; Zhang, K.; Tang, M.; He, D.; Li, K.C. Data fusion approach for collaborative anomaly intrusion detection in blockchain-based systems. IEEE Internet Things J. 2021, 9, 14741–14751. [Google Scholar] [CrossRef]
- Zheng, G.; Ni, Q.; Lu, Y. Privacy-Aware Anomaly Detection and Notification Enhancement for VANET Based on Collaborative Intrusion Detection System. IEEE Trans. Intell. Transp. Syst. 2024, 25, 21172–21182. [Google Scholar] [CrossRef]
- Al-E’mari, S.; Anbar, M.; Sanjalawe, Y.; Manickam, S.; Hasbullah, I. Intrusion detection systems using blockchain technology: A review, issues and challenges. Comput. Syst. Sci. Eng. 2022, 40, 87–112. [Google Scholar] [CrossRef]
- Meng, W.; Tischhauser, E.W.; Wang, Q.; Wang, Y.; Han, J. When intrusion detection meets blockchain technology: A review. IEEE Access 2018, 6, 10179–10188. [Google Scholar] [CrossRef]
- Signorini, M.; Pontecorvi, M.; Kanoun, W.; Di Pietro, R. BAD: A blockchain anomaly detection solution. IEEE Access 2020, 8, 173481–173490. [Google Scholar] [CrossRef]
- Kumar, P.; Gupta, G.P.; Tripathi, R. TP2SF: A Trustworthy Privacy-Preserving Secured Framework for sustainable smart cities by leveraging blockchain and machine learning. J. Syst. Archit. 2021, 115, 101954. [Google Scholar] [CrossRef]
- Kumar, R.; Tripathi, R. DBTP2SF: A deep blockchain-based trustworthy privacy-preserving secured framework in industrial internet of things systems. Trans. Emerg. Telecommun. Technol. 2021, 32, e4222. [Google Scholar] [CrossRef]
- Kumar, R.; Kumar, P.; Tripathi, R.; Gupta, G.P.; Gadekallu, T.R.; Srivastava, G. SP2F: A secured privacy-preserving framework for smart agricultural Unmanned Aerial Vehicles. Comput. Netw. 2021, 187, 107819. [Google Scholar] [CrossRef]
- Reyna, A.; Martín, C.; Chen, J.; Soler, E.; Díaz, M. On blockchain and its integration with IoT. Challenges and opportunities. Future Gener. Comput. Syst. 2018, 88, 173–190. [Google Scholar] [CrossRef]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Turnbull, B. Towards the development of realistic botnet dataset in the Internet of Things for network forensic analytics: Bot-IoT dataset. Future Gener. Comput. Syst. 2019, 100, 779–796. [Google Scholar] [CrossRef]
- Chaabouni, N.; Mosbah, M.; Zemmari, A.; Sauvignac, C.; Faruki, P. Network Intrusion Detection for IoT Security Based on Learning Techniques. IEEE Commun. Surv. Tutor. 2019, 21, 2671–2701. [Google Scholar] [CrossRef]
- Chen, L.; Kuang, X.; Xu, A.; Yang, Y.; Suo, S. Anomaly Detection on Time-series Logs for Industrial Network. In Proceedings of the 2020 3rd International Conference on Smart BlockChain (SmartBlock), Zhengzhou, China, 23–25 October 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 81–86. [Google Scholar]
- Chen, L.; Lv, H.; Fan, K.; Yang, H.; Kuang, X.; Xu, A.; Yang, Y. A survey: Machine learning based security analytics approaches and applications of blockchain in network security. In Proceedings of the 2020 3rd International Conference on Smart BlockChain (SmartBlock), Zhengzhou, China, 23–25 October 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 17–22. [Google Scholar]
- Li, T.; Ma, J.; Pei, Q.; Song, H.; Shen, Y.; Sun, C. DAPV: Diagnosing Anomalies in MANETs Routing With Provenance and Verification. IEEE Access 2019, 7, 35302–35316. [Google Scholar] [CrossRef]
- Zhou, J.; Chen, Z.; Du, M.; Chen, L.; Yu, S.; Li, F.; Chen, G.; Xuan, Q. Adversarial enhancement for community detection in complex networks. arXiv 2019, arXiv:1911.01670. [Google Scholar]
- Li, T.; Ma, J.; Sun, C. Dlog: Diagnosing router events with syslogs for anomaly detection. J. Supercomput. 2018, 74, 845–867. [Google Scholar] [CrossRef]
- Bagozi, A.; Bianchini, D.; De Antonellis, V.; Garda, M.; Melchiori, M. Services as Enterprise Smart Contracts in the Digital Factory. In Proceedings of the 2019 IEEE International Conference on Web Services (ICWS), Milan, Italy, 8–13 July 2019; pp. 224–228. [Google Scholar] [CrossRef]
- Bagozi, A.; Bianchini, D.; De Antonellis, V.; Garda, M.; Melchiori, M. Exploiting Blockchain and Smart Contracts for Data Exploration As a Service. In Proceedings of the 1st International Conference on Information Integration and Web-Based Applications & Services, New York, NY, USA, 2–4 December 2020; pp. 393–402. [Google Scholar] [CrossRef]
- Lopes, V.; Alexandre, L.A. Detecting Robotic Anomalies using RobotChain. In Proceedings of the 2019 IEEE International Conference on Autonomous Robot Systems and Competitions (ICARSC), Gondomar, Portugal, 24–26 April 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the Thirteenth EuroSys Conference, Porto, Portugal, 23–26 April 2018. [Google Scholar] [CrossRef]
- Casado-Vara, R.; Prieto, J.; la Prieta, F.D.; Corchado, J.M. How blockchain improves the supply chain: Case study alimentary supply chain. Procedia Comput. Sci. 2018, 134, 393–398. [Google Scholar] [CrossRef]
- Ndiaye, M.; Diallo, T.A.; Konate, K. ADEFGuard: Anomaly detection framework based on Ethereum smart contracts behaviours. Blockchain Res. Appl. 2023, 4, 100148. [Google Scholar] [CrossRef]
- Sammy, F.; Vigila, S.M.C. Anomaly Detection in Cloud Using Hexabullus Optimisation-Enabled Fuzzy Classifier with Smart Contract-Enabled Secure Communication. J. Inf. Knowl. Manag. 2024, 23, 2350058. [Google Scholar] [CrossRef]
- Chen, D.; Liao, Z.; Chen, R.; Wang, H.; Yu, C.; Zhang, K.; Zhang, N.; Shen, X. Privacy-Preserving Anomaly Detection of Encrypted Smart Contract for Blockchain-Based Data Trading. IEEE Trans. Dependable Secur. Comput. 2024, 21, 4510–4525. [Google Scholar] [CrossRef]
- Vaezi, M.; Azari, A.; Khosravirad, S.R.; Shirvanimoghaddam, M.; Azari, M.M.; Chasaki, D.; Popovski, P. Cellular, Wide-Area, and Non-Terrestrial IoT: A Survey on 5G Advances and the Road Toward 6G. IEEE Commun. Surv. Tutor. 2022, 24, 1117–1174. [Google Scholar] [CrossRef]
- Wang, J.; Jin, H.; Chen, J.; Tan, J.; Zhong, K. Anomaly detection in Internet of medical Things with Blockchain from the perspective of deep neural network. Inf. Sci. 2022, 617, 133–149. [Google Scholar] [CrossRef]
- Nguyen, T.D.; Marchal, S.; Miettinen, M.; Fereidooni, H.; Asokan, N.; Sadeghi, A.R. DÏoT: A Federated Self-learning Anomaly Detection System for IoT. In Proceedings of the 2019 IEEE 39th International Conference on Distributed Computing Systems (ICDCS), Dallas, TX, USA, 7–9 July 2019; pp. 756–767. [Google Scholar] [CrossRef]
- Liu, Y.; Garg, S.; Nie, J.; Zhang, Y.; Xiong, Z.; Kang, J.; Hossain, M.S. Deep Anomaly Detection for Time-Series Data in Industrial IoT: A Communication-Efficient On-Device Federated Learning Approach. IEEE Internet Things J. 2021, 8, 6348–6358. [Google Scholar] [CrossRef]
- Fernandez Maimo, L.; Perales Gómez, Á.L.; García Clemente, F.J.; Gil Pérez, M.; Martínez Pérez, G. A Self-Adaptive Deep Learning-Based System for Anomaly Detection in 5G Networks. IEEE Access 2018, 6, 7700–7712. [Google Scholar] [CrossRef]
- Nguyen, H.L.; Eisenbarth, J.P.; Ignat, C.L.; Perrin, O. Blockchain-Based Auditing of Transparent Log Servers. In Proceedings of the Data and Applications Security and Privacy XXXII (DBSec 2018), Bergamo, Italy, 16–18 July 2018; Lecture Notes in Computer Science. Kerschbaum, F., Paraboschi, S., Eds.; Springer: Cham, Switzerland, 2018; Volume 10980, pp. 19–34. [Google Scholar] [CrossRef]
- Careem, M.A.A.; Dutta, A. SenseChain: Blockchain based Reputation System for Distributed Spectrum Enforcement. In Proceedings of the 2019 IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN), Newark, NJ, USA, 11–14 November 2019; pp. 1–10. [Google Scholar] [CrossRef]
- Tange, K.; De Donno, M.; Fafoutis, X.; Dragoni, N. A Systematic Survey of Industrial Internet of Things Security: Requirements and Fog Computing Opportunities. IEEE Commun. Surv. Tutor. 2020, 22, 2489–2520. [Google Scholar] [CrossRef]
- Huang, J.; Kong, L.; Chen, G.; Wu, M.Y.; Liu, X.; Zeng, P. Towards Secure Industrial IoT: Blockchain System With Credit-Based Consensus Mechanism. IEEE Trans. Ind. Inform. 2019, 15, 3680–3689. [Google Scholar] [CrossRef]
- Kuo, C.C.; Shyu, J.Z. A cross-national comparative policy analysis of the blockchain technology between the USA and China. Sustainability 2021, 13, 6893. [Google Scholar] [CrossRef]
- Kukrety, N.; Kaushik, P.; Pande, S.S. Blockchain Technology and Legal Framework in India: A Systematic Review. Empir. Econ. Lett. 2023, 22, 1–18. [Google Scholar]
- Conlon, T.; Corbet, S.; Oxley, L. The influence of European MiCa regulation on cryptocurrencies. Glob. Financ. J. 2024, 63, 101040. [Google Scholar] [CrossRef]
- Ponce-Bobadilla, A.V.; Schmitt, V.; Maier, C.S.; Mensing, S.; Stodtmann, S. Practical guide to SHAP analysis: Explaining supervised machine learning model predictions in drug development. Clin. Transl. Sci. 2024, 17, e70056. [Google Scholar] [CrossRef]
- Dieber, J.; Kirrane, S. Why model why? Assessing the strengths and limitations of LIME. arXiv 2020, arXiv:2012.00093. [Google Scholar] [CrossRef]
- Patel, V.; Pan, L.; Rajasegarar, S. Graph deep learning based anomaly detection in ethereum blockchain network. In Proceedings of the International Conference on Network and System Security, Melbourne, Australia, 25–27 November 2020; Springer: Berlin/Heidelberg, Germany, 2020; pp. 132–148. [Google Scholar]
- Yang, X.; Yue, C.; Zhang, W.; Liu, Y.; Ooi, B.C.; Chen, J. SecuDB: An in-enclave privacy-preserving and tamper-resistant relational database. Proc. VLDB Endow. 2024, 17, 3906–3919. [Google Scholar] [CrossRef]
- Yang, X.; Zhang, Y.; Wang, S.; Yu, B.; Li, F.; Li, Y.; Yan, W. LedgerDB: A centralized ledger database for universal audit and verification. Proc. VLDB Endow. 2020, 13, 3138–3151. [Google Scholar] [CrossRef]
- Yang, X.; Zhang, R.; Yue, C.; Liu, Y.; Ooi, B.C.; Gao, Q.; Zhang, Y.; Yang, H. VeDB: A software and hardware enabled trusted relational database. Proc. ACM Manag. Data 2023, 1, 1–27. [Google Scholar] [CrossRef]
- Chen, Z.; Duan, J.; Kang, L.; Qiu, G. Supervised anomaly detection via conditional generative adversarial network and ensemble active learning. IEEE Trans. Pattern Anal. Mach. Intell. 2022, 45, 7781–7798. [Google Scholar] [CrossRef] [PubMed]
- Raza, A.; Hardy, L.; Roehrer, E.; Yeom, S.; Kang, B.H. GPSPiChain-blockchain and AI based self-contained anomaly detection family security system in smart home. J. Syst. Sci. Syst. Eng. 2021, 30, 433–449. [Google Scholar] [CrossRef]
- Regev, Y.A.; Vassdal, H.; Halden, U.; Catak, F.O.; Cali, U. Hybrid ai-based anomaly detection model using phasor measurement unit data. In Proceedings of the 2022 IEEE 1st Global Emerging Technology Blockchain Forum: Blockchain & Beyond (iGETblockchain), Irvine, CA, USA, 7–11 November 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–6. [Google Scholar]
- Olawale, O.P.; Ebadinezhad, S. Cybersecurity anomaly detection: Ai and ethereum blockchain for a secure and tamperproof ioht data management. IEEE Access 2024, 12, 131605–131620. [Google Scholar] [CrossRef]
- Kuznetsov, O.; Frontoni, E.; Kuznetsova, K.; Shevchuk, R.; Karpinski, M. NFT Technology for Enhanced Global Digital Registers: A Novel Approach to Tokenization. Future Internet 2024, 16, 252. [Google Scholar] [CrossRef]

| # | Research Institution | Country | Count |
|---|---|---|---|
| 1 | Beijing University of Posts and Telecommunications | China | 10 |
| 2 | University of Electronic Science and Technology of China | China | 10 |
| 3 | Brandon University | Canada | 8 |
| 4 | China Medical University Taiwan | Taiwan | 8 |
| 5 | King Saud University | Saudi Arabia | 8 |
| 6 | Chinese Academy of Sciences | China | 7 |
| 7 | Egyptian Knowledge Bank | Egypt | 6 |
| 8 | Guangzhou University | China | 6 |
| 9 | National Institute of Technology System | India | 6 |
| 10 | Nirma University | India | 6 |
| 11 | Northern Border University | Saudi Arabia | 6 |
| 12 | Texas A&M University System | USA | 6 |
| 13 | University System of Georgia | USA | 6 |
| 14 | Vellore Institute of Technology | India | 6 |
| 15 | Xidian University | China | 6 |
| # | Author | Research Institution | Count | Year |
|---|---|---|---|---|
| 1 | Srivastava Gautam | Brandon University, Canada | 8 | 2021 |
| 2 | Tanwar Sudeep | Nirma University, India | 6 | 2022 |
| 3 | Kumar Prabhat | National Institute of Technology, India | 5 | 2021 |
| 4 | Li Tao | Guizhou University, China | 5 | 2019 |
| 5 | Zhang Kaiwen | Ecole de Technologie Supérieure, Canada | 5 | 2022 |
| 6 | Chang Sang-Yoon | University of Colorado, USA | 4 | 2021 |
| 7 | Fan Wenjun | University of Colorado, USA | 4 | 2021 |
| 8 | Kim Jinoh | Texas A&M University, USA | 4 | 2021 |
| 9 | Kumar Randhir | National Institute of Technology, India | 4 | 2021 |
| 10 | Li Ji | SKL-MEAC, China | 4 | 2020 |
| # | Author | Research Institution | Centr. | Count | Year |
|---|---|---|---|---|---|
| 1 | Satoshi Nakamoto | — | 0.17 | 206 | 2018 |
| 2 | Mohamed Amine Ferrag | Guelma University, Algeria | 0.07 | 58 | 2020 |
| 3 | Zibin Zheng | Sun Yat-Sen University, China | 0.04 | 32 | 2019 |
| 4 | Gavin Wood | Ethereum Foundation, UK | 0.06 | 29 | 2018 |
| 5 | Varun Chandola | University of Minnesota, USA | 0.09 | 28 | 2018 |
| 6 | Thai T. Pham | Stanford University, USA | 0.05 | 27 | 2020 |
| 7 | Nour Moustafa | University of New South Wales at ADFA, Australia | 0.02 | 27 | 2020 |
| 8 | Ayoub Khan | University of Bisha, Saudi Arabia | 0.06 | 24 | 2019 |
| 9 | Pradeep Kumar | Indian Institute of Management Ranchi, India | 0.05 | 23 | 2021 |
| 10 | Weili Chen | Sun Yat-Sen University, China | 0.04 | 23 | 2021 |
| ID | Size | Silhouette | Label (LLR) | Year | Major Publications |
|---|---|---|---|---|---|
| 0 | 56 | 0.904 | using unsupervised learning | 2020 | [28,29,33,55,61,62,63,64,65,66,67,68,69,70] |
| 1 | 45 | 0.924 | bitcoin concepts threat | 2017 | [37,57,71,72,73,74,75,76,77] |
| 2 | 43 | 0.884 | lightweight federated learning | 2021 | [27,78,79,80,81,82,83,84,85,86,87,88,89,90] |
| 3 | 33 | 0.920 | knowledge-defined networking | 2020 | [34,91,92,93,94,95,96,97,98,99] |
| 4 | 31 | 0.890 | intrusion detection system | 2018 | [100,101,102,103,104,105,106] |
| 5 | 28 | 0.928 | sustainable smart cities | 2019 | [107,108,109,110,111,112] |
| 6 | 16 | 0.987 | industrial network | 2017 | [58,113,114,115,116,117] |
| 7 | 15 | 0.951 | smart contract | 2017 | [98,118,119,120,121,122,123,124,125] |
| 8 | 14 | 1.000 | 5G advance | 2019 | [80,85,126,127,128,129,130] |
| 9 | 9 | 0.866 | server | 2015 | [53,131,132] |
| 10 | 7 | 1.000 | things security | 2018 | [98,133,134] |
| Ref. | Type | Methodology | Period | Trend Analysis | Bibliometric Analysis | Future Directions | Blockchain Platforms |
|---|---|---|---|---|---|---|---|
| [31] | Review | Narrative | N/S | – | – | + | General |
| [32] | Review | Narrative | 2012–2024 | + | – | + | General |
| [33] | Review | Narrative | 2014–2023 | + | – | + | General |
| [34] | Article | Narrative | 2018–2023 | – | – | + | Infrastructure |
| [35] | Brief Review | Narrative | N/S | – | – | – | Financial |
| [36] | Conf. Paper | Narrative | N/S | – | – | + | General |
| [37] | Article | Narrative | N/S | – | – | + | General |
| [38] | Conf. Paper | Narrative | N/S | – | – | + | Financial |
| Our | Systematic | PRISMA | 2017–2024 | + | + | + | General |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shevchuk, R.; Martsenyuk, V.; Adamyk, B.; Benson, V.; Melnyk, A. Anomaly Detection in Blockchain: A Systematic Review of Trends, Challenges, and Future Directions. Appl. Sci. 2025, 15, 8330. https://doi.org/10.3390/app15158330
Shevchuk R, Martsenyuk V, Adamyk B, Benson V, Melnyk A. Anomaly Detection in Blockchain: A Systematic Review of Trends, Challenges, and Future Directions. Applied Sciences. 2025; 15(15):8330. https://doi.org/10.3390/app15158330
Chicago/Turabian StyleShevchuk, Ruslan, Vasyl Martsenyuk, Bogdan Adamyk, Vladlena Benson, and Andriy Melnyk. 2025. "Anomaly Detection in Blockchain: A Systematic Review of Trends, Challenges, and Future Directions" Applied Sciences 15, no. 15: 8330. https://doi.org/10.3390/app15158330
APA StyleShevchuk, R., Martsenyuk, V., Adamyk, B., Benson, V., & Melnyk, A. (2025). Anomaly Detection in Blockchain: A Systematic Review of Trends, Challenges, and Future Directions. Applied Sciences, 15(15), 8330. https://doi.org/10.3390/app15158330









