A Blockchain Network Communication Architecture Based on Information-Centric Networking
Abstract
1. Introduction
- We propose BLOCK-ICN, an ICN-based blockchain network communication architecture compatible with IP networks that enables the deployment of blockchain applications on ICN nodes with computing and storage capabilities. While ensuring compatibility with existing P2P networks, BLOCK-ICN utilizes ICN multicast to provide relay acceleration services.
- We construct a hierarchical structured ICN relay network topology based on BLOCK-ICN. It utilizes delay information provided by the enhanced resolution system to partition network domains, and selects a domain gateway based on data flow forwarding dependencies, to optimize network topology alignment. Based on this topology, a parallel tree-based broadcast method leveraging ICN multicast is proposed, to reduce network broadcast latency and bandwidth consumption.
- We implemented a simulation of BLOCK-ICN using SimBlock. Experimental results demonstrated that, in a network with 16,000 nodes, compared to the Bitcoin network, when ICN nodes constituted of the total nodes, the broadcast latency for blocks to reach and of the network was reduced by and , respectively, while maintaining good network scalability.
2. Related Works
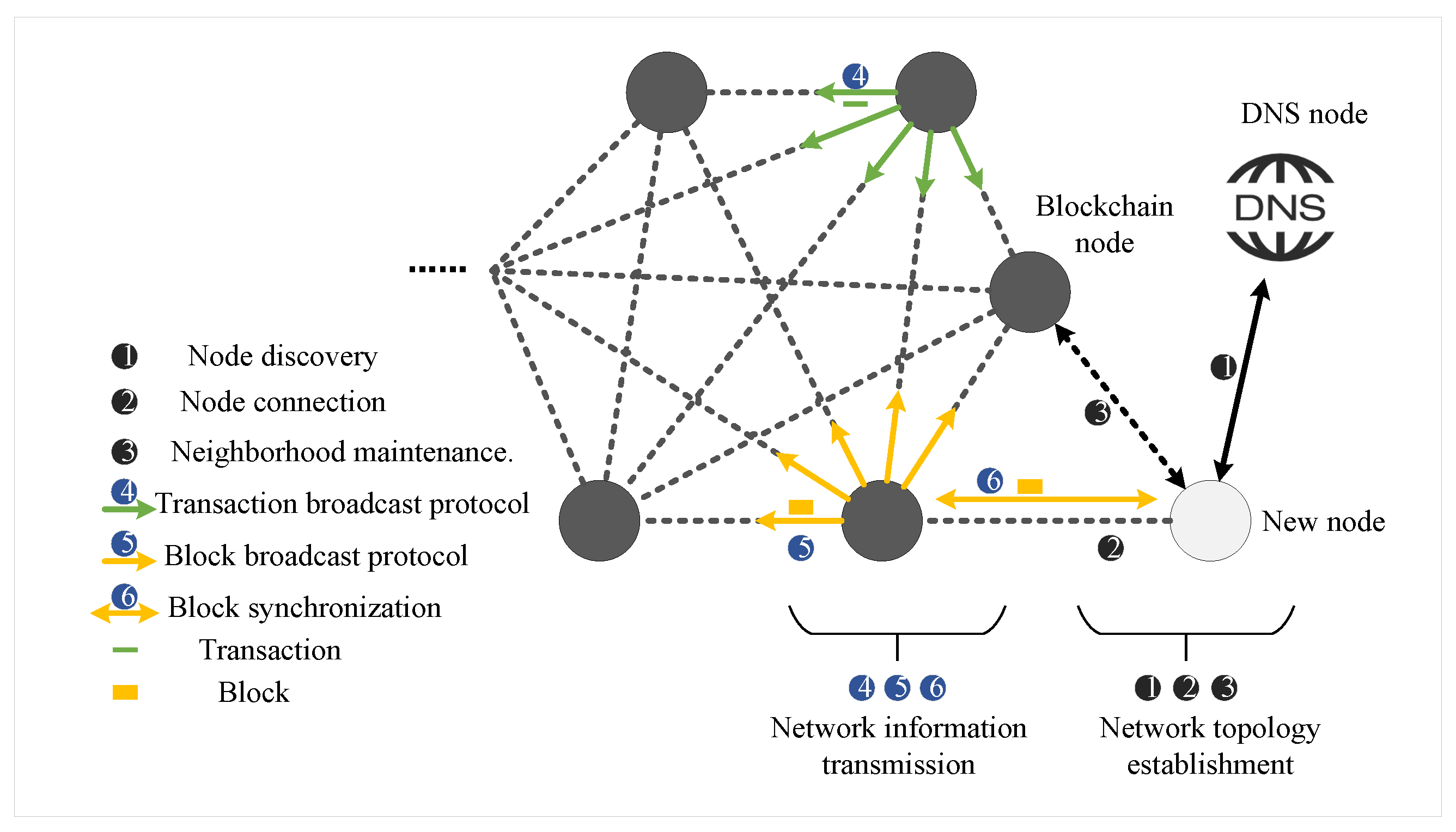
Blockchain Network Communication Process
3. Blockchain Based on ICN
3.1. Introduction to ICN Networks
Blockchain Research Based on ICN
4. Design
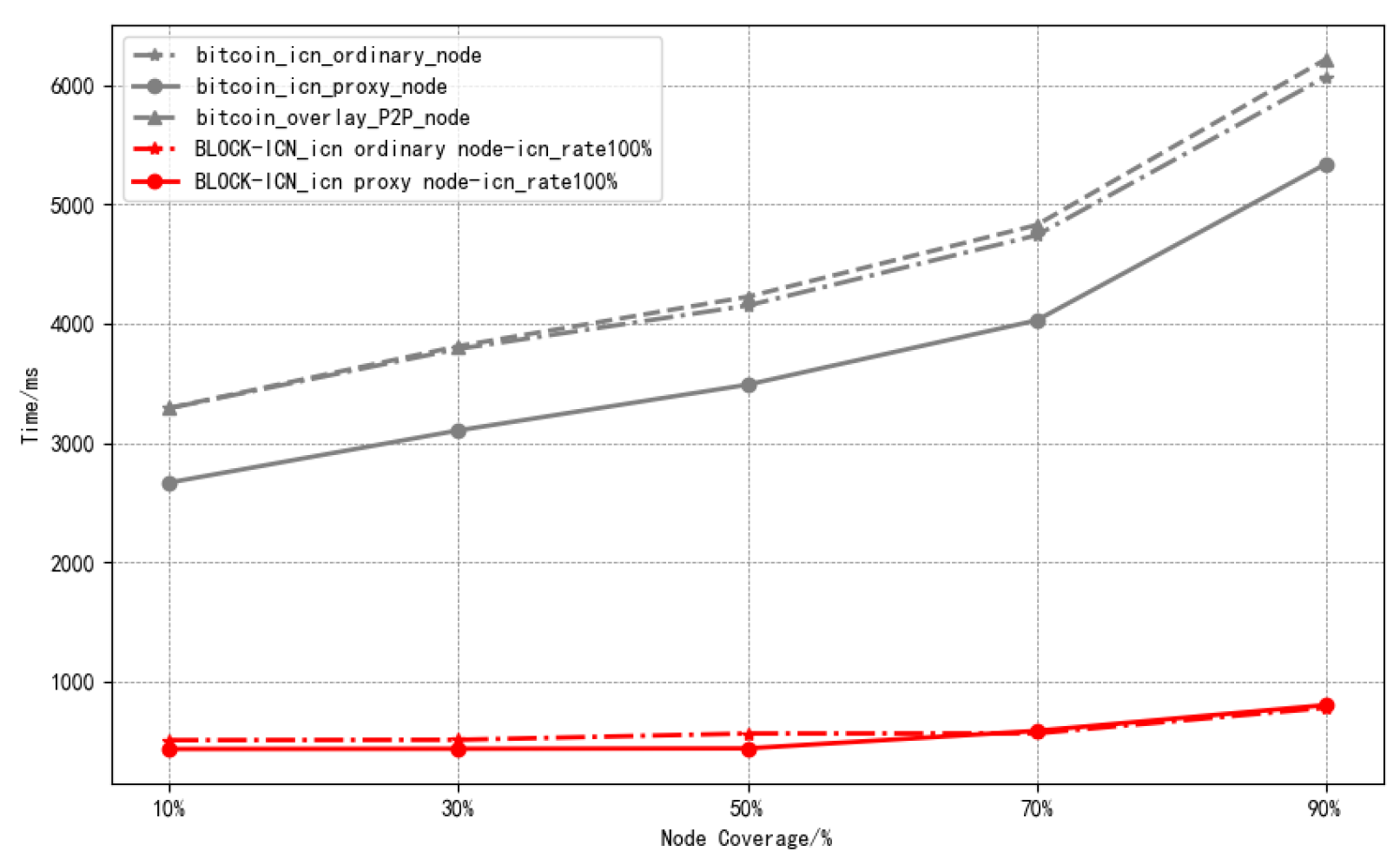
- P2P node: Consists of full nodes in the P2P network, establishes neighbor relationships with ICN nodes and other P2P nodes, and is responsible for receiving unicast messages from neighboring nodes and forwarding them to other P2P nodes.
- ICN node: Consists of blockchain nodes deployed in the ICN network. In addition to storing the address information of overlay P2P neighbors, ICN nodes obtain and store the address information of intra-domain ICN nodes and the multicast service information of the intra-domain through the enhanced resolution system. As gateway nodes, they are responsible for forwarding multicast messages from domain gateway nodes to P2P nodes.
- ICN domain gateway node: Generated through the election of intra-domain ICN nodes, domain gateway nodes not only store the address information of overlay P2P neighbors, intra-domain ICN node address information, and intra-domain multicast information, but also update the multicast group service information and multicast group member information within the intra-domain and inter-domain through the enhanced resolution system. Acting as multicast sources, they broadcast messages to the multicast groups within the intra-domain and inter-domain.
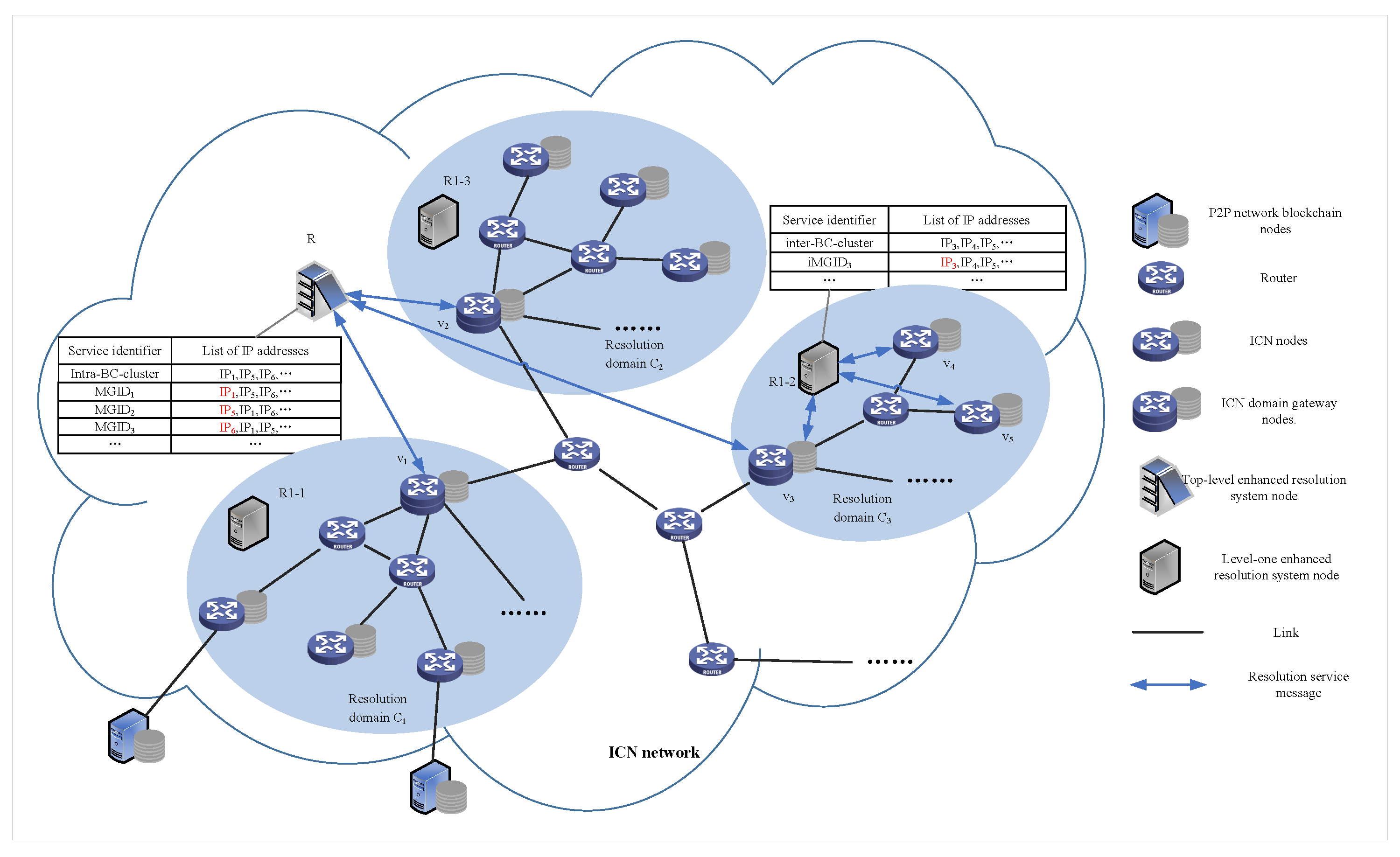
4.1. Network Topology Improvement
4.1.1. Domain Partition Based on Enhanced Resolution System Delay
- Step 1: The intra-domain ICN node sends a registration message to the intra-domain resolution node R1-i, including the node’s address information and the intra-domain service identifier information (inter-BC-cluster).
- Step 2: After receiving the registration message, the intra-domain resolution node R1-i adds the node’s address information to the registration list of the corresponding service identifier and sends a registration success message.
- Step 3: The elected domain gateway node in the domain sends a registration message to the highest-level resolution node R, including the domain gateway node’s address information and the inter-domain service identifier information (intra-BC-cluster).
- Step 4: After receiving the registration message, the highest-level resolution node R adds the domain gateway node’s address information to the registration list of the corresponding service identifier and sends a registration success message.
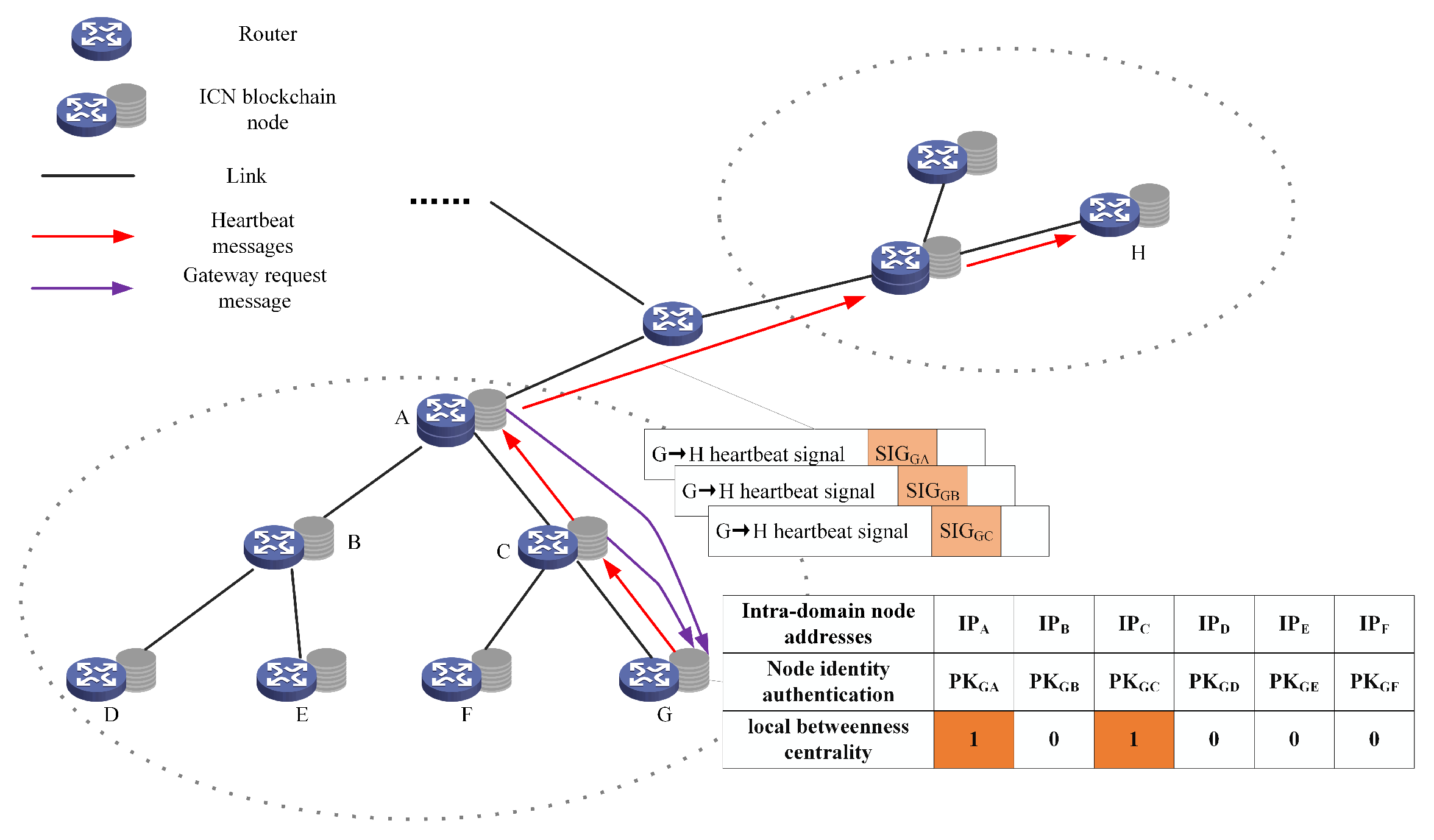
4.1.2. Domain Gateway Node Election
- intra-domain ICN node address information: ICN nodes acquire the address information of other intra-domain ICN nodes through the enhanced resolution system.
- Identity authentication information of intra-domain ICN nodes: Public key information , exchanged between intra-domain ICN nodes, is used for identity authentication.
- data flow forwarding dependencies table: This table records data flow forwarding dependencies among intra-domain ICN nodes. If a node serves as an upstream node, it is marked as1; otherwise, it is marked as 0. This information is essential for evaluating the node local betweenness centrality within the domain. The score life cycle is defined as T ms. If an upstream node fails to transmit the next round of proxy request information packets within T ms, its data flow forwarding dependency status is reset to 0. The dependency relationship is formally expressed aswhere C denotes the set of intra-domain ICN nodes, and represents the data flow forwarding dependency list of node G.
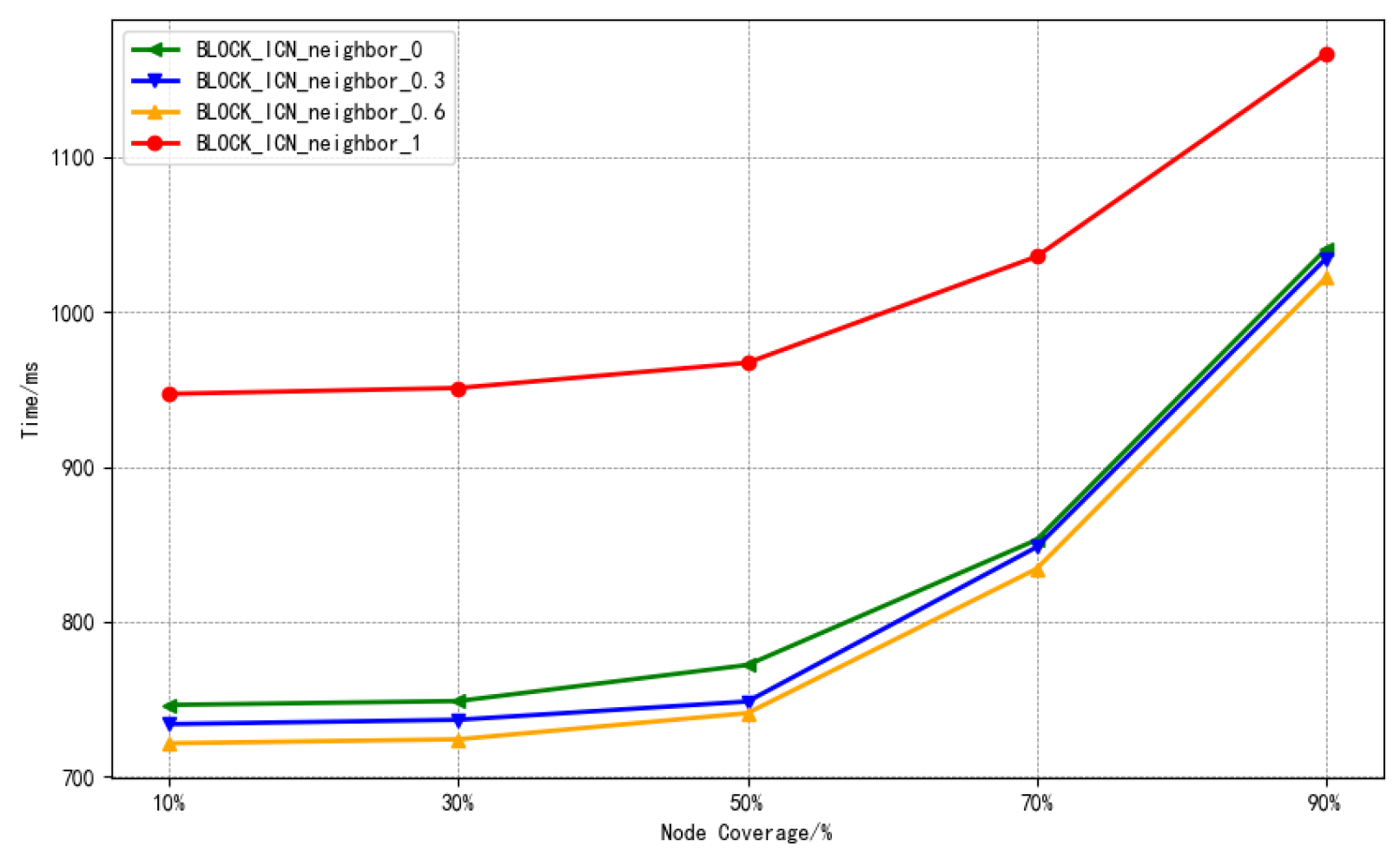
- Step 1: The intra-domain ICN node G transmits blockchain heartbeat messages to inter-domain ICN nodes. These heartbeat messages randomly incorporate various co-signed information (e.g., , , ), with each signature being included with a probability (), as negotiated with other nodes.
- Step 2: An upstream ICN node (e.g., node A) verifies whether the signature information corresponds to that of internal nodes by matching the predefined fields in the forwarded data packets. If a match is found and the associated IP address remains consistent, this confirms that the upstream node has received the heartbeat packet originating from the downstream node. The upstream node then sends a gateway request message to the downstream node and confirms its upstream status by signing the request with its private key.
- Step 3: Upon receiving the gateway request message, the downstream node verifies its legitimacy. If the request is deemed valid, the data flow forwarding dependency table is updated, and the relationship between the upstream node and downstream node is recorded.
- Proposal phase: The candidate node p broadcasts a proposal message along with its local betweenness centrality evaluation table to other intra-domain ICN nodes.
- Voting phase: Upon receiving the proposal, each node verifies the proposal and multicasts the vote message and its own local betweenness centrality evaluation table to other nodes.
- Proposal confirmation phase: After receiving at least messages, each node constructs the local betweenness centrality evaluation table based on the local betweenness centrality evaluation matrices of other nodes. The candidate node with the highest local betweenness centrality score is then selected and a new voting message , along with the updated local betweenness centrality evaluation table, is multicast to other nodes.
- Election submission phase: After receiving at least messages, the candidate node in the proposal is confirmed as the domain gateway node. The new domain gateway node information is then multicast to all nodes.
| Algorithm 1 Domain gateway node election algorithm |
|
4.1.3. Optimization of the Liveness Protocol Between Domain Gateway Nodes and Intra-Domain ICN Nodes
4.1.4. Fault Tolerance Strategy
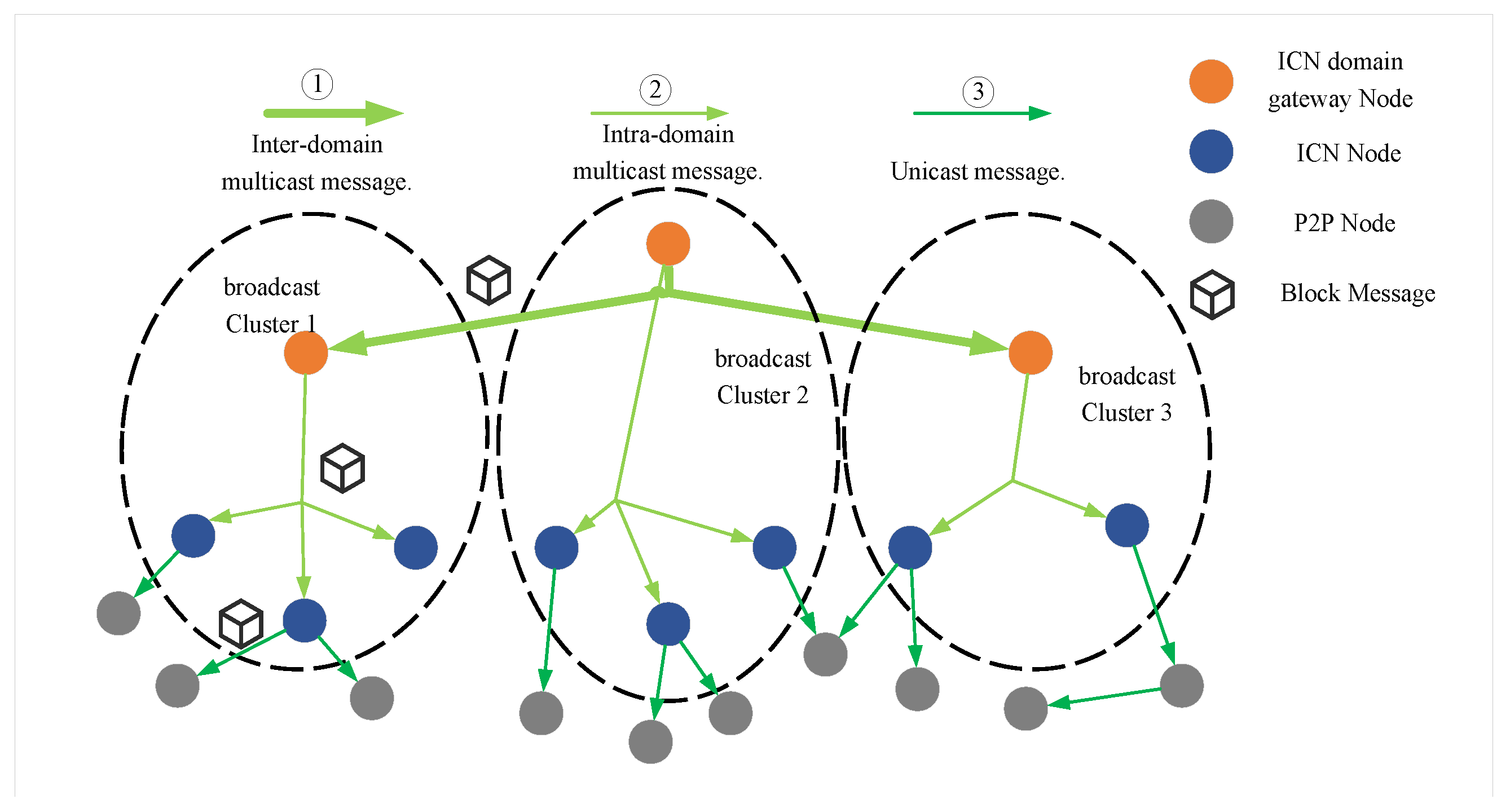
4.2. Optimization of the Broadcast Protocol
Message Broadcast Protocol Based on ICN Multicast
- If the message originates from an intra-domain ICN node or a P2P node, the gateway node multicasts the message to both intra-domain and inter-domain multicast groups.
- If the message originates from an inter-domain gateway node via multicast, this indicates that the message has already been propagated across domains. In this case, the gateway node only needs to multicast the message to the intra-domain multicast group.
- If the received message originates from a domain gateway node, the ICN node broadcasts the message to P2P nodes.
- If the message originates from an intra-domain regular ICN node or a P2P node, the ICN node first sends the message to the domain gateway node and then propagates it to the P2P nodes.
5. Method Analysis
5.1. Blockchain Partitioning Method Based on Enhanced Resolution System
- Time Complexity: By using the latency information of the existing infrastructure enhanced resolution system as prior conditions, the additional probing and calculation of value latency between nodes is reduced. Nodes only need to query the enhanced resolution system to obtain the addresses of other intra-domain ICN nodes, resulting in a time complexity of , thus reducing time complexity and bandwidth consumption.
- Security: The enhanced resolution system in the network acts as an independent third-party trusted infrastructure, similarly to the service in the network. It only provides deterministic latency resolution services and does not participate in data transmission in the network. Therefore, a certain level of security in the network partitioning process can be ensured.
- Feasibility: When a new node joins or leaves the resolution domain, it only needs to send registration or deregistration message information to the enhanced resolution system nodes. The enhanced resolution system nodes update the registration information, without the need for a large-scale recalculation of the entire network. This reduces the computational complexity and improves scalability.
5.2. Domain Gateway Node Selection Algorithm
5.2.1. Time Complexity Analysis
5.2.2. Security Analysis
5.2.3. Feasibility Analysis
6. Evaluation
6.1. Experimental Settings
6.1.1. Implementation
- The simulation parameters of the Bitcoin network are usually obtained from real-world blockchain network data, using tools like xblock or blocksci. These tools can provide node information in the blockchain network but cannot provide the topological information of routers in the blockchain network. Therefore, it is not possible to construct the underlying network topology of a real blockchain network. It is unreasonable to conduct simulation experiments on other networks or self-designed underlying network topologies, because it is not possible to acquire the node distribution in the blockchain network on other networks and this cannot ensure the authenticity of the simulation experiments.
- To implement simulations that are compatible with both the blockchain network and the ICN network layer, extensive code modifications to NS3 would be required. In simulation experiments, for a blockchain network with a blockchain node quantity in the order of 10,000, a larger-scale underlying network topology would need to be implemented in the underlay ICN network layer, which greatly increases the complexity of the experiments.
6.1.2. Platform Configuration
6.1.3. Simulation Experiment Parameters
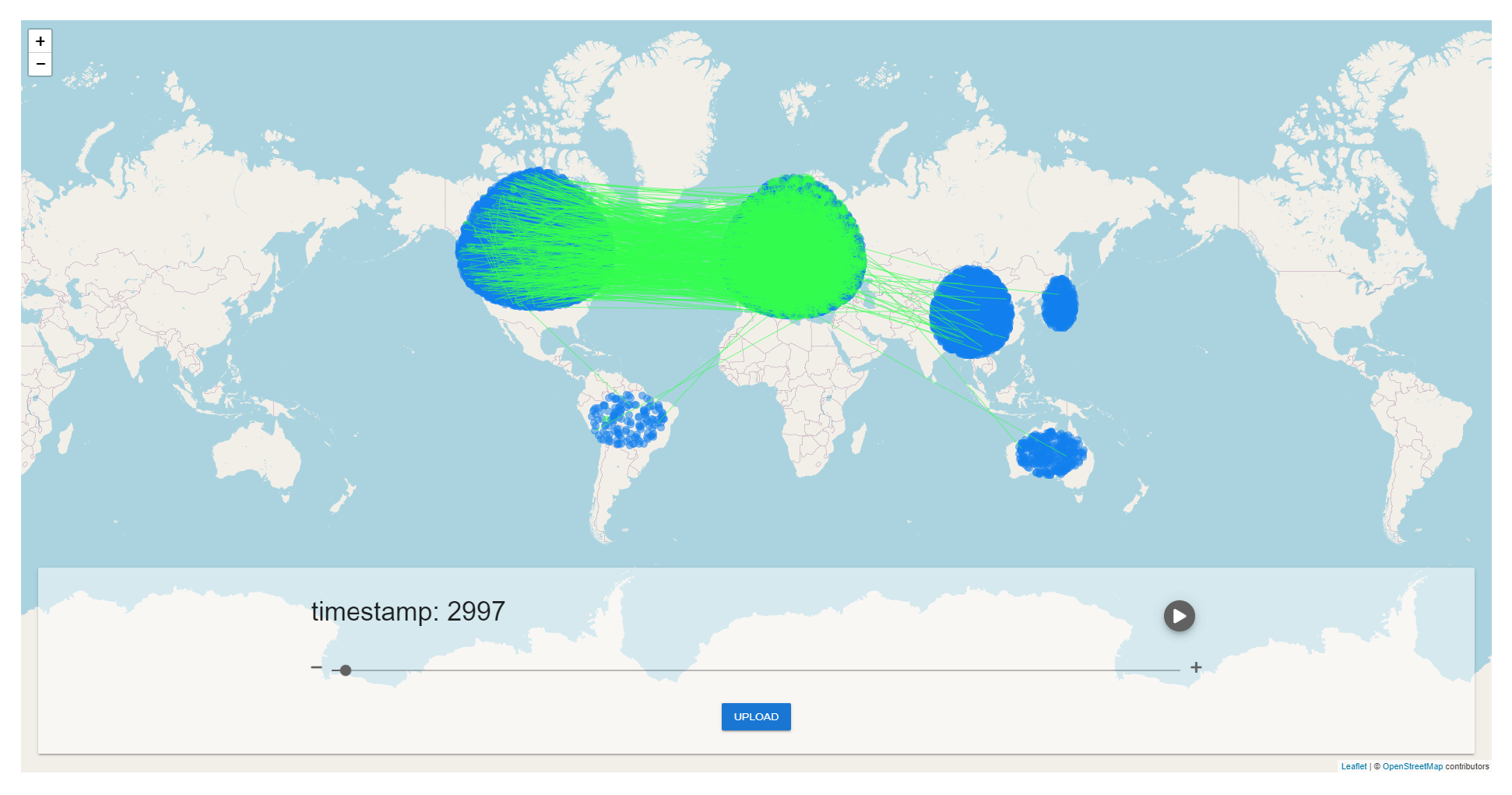
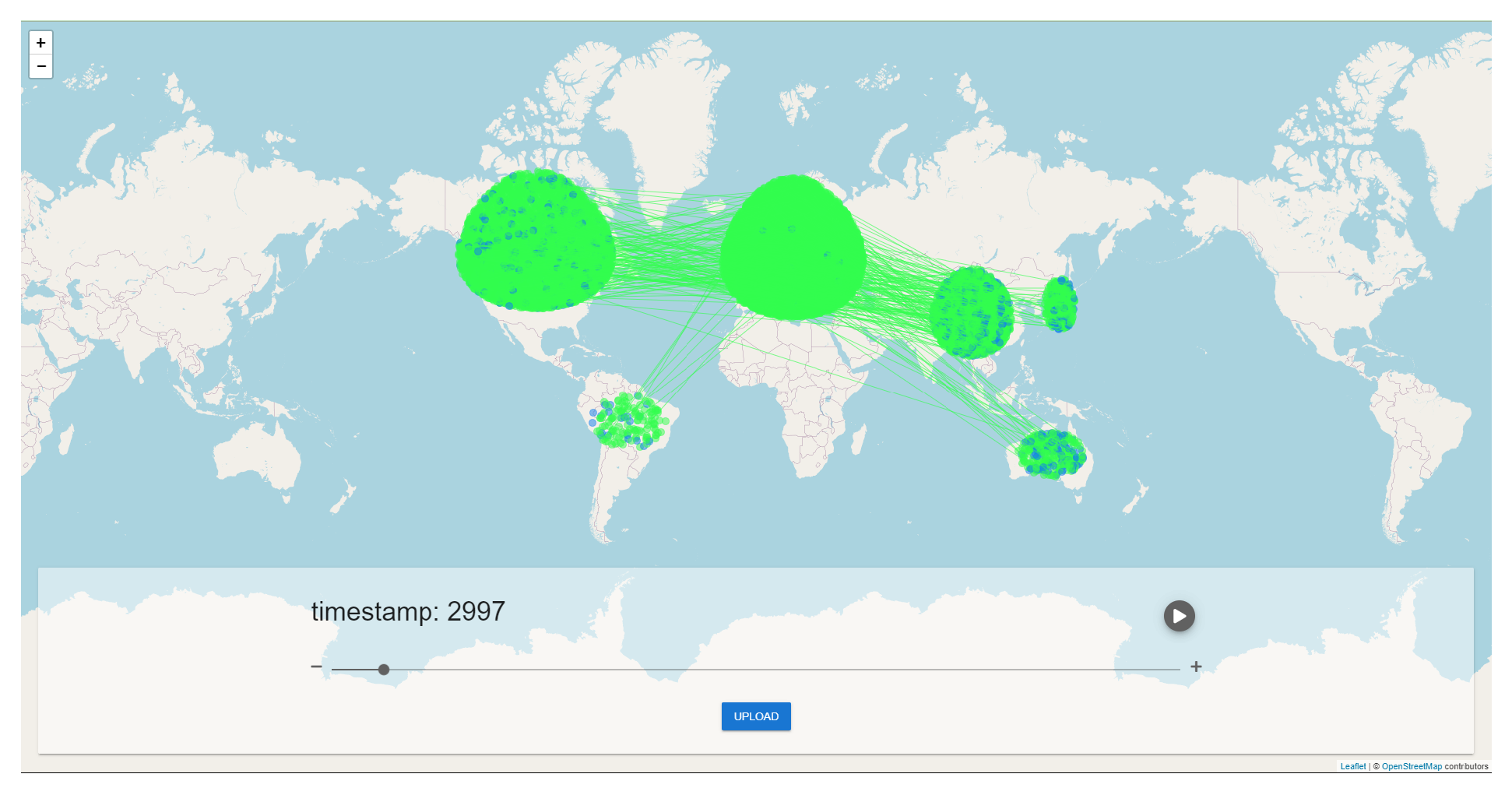
Node Distribution
Network Latency
Bandwidth
| Parameter | Bitcoin |
|---|---|
| Node Quantity | 6000, 9000, 10,000, 13,000, 16,000 [41] |
| Block Generation Time | 10 min [44] |
| Block Size | 0.5 MB [44] |
| Node Neighbor Quantity | Distributed according to Miller et al. [18] |
| Node distribution | Bitnodes [41] |
| Network latency | WonderNetwork [42] |
| Network bandwidth | testmy.net [43] |
6.1.4. Simulation Evaluation Metrics
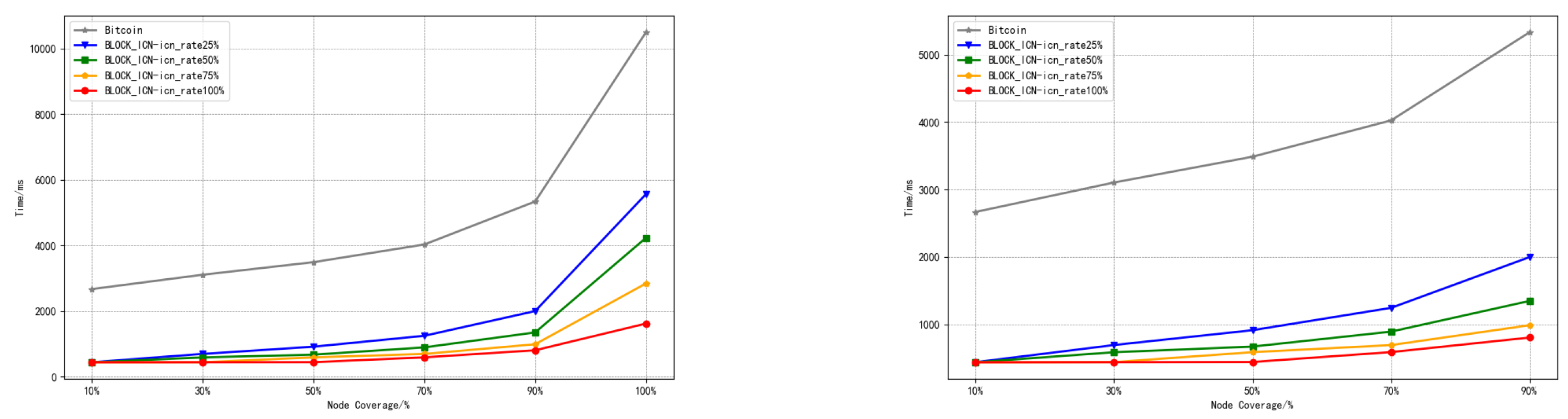
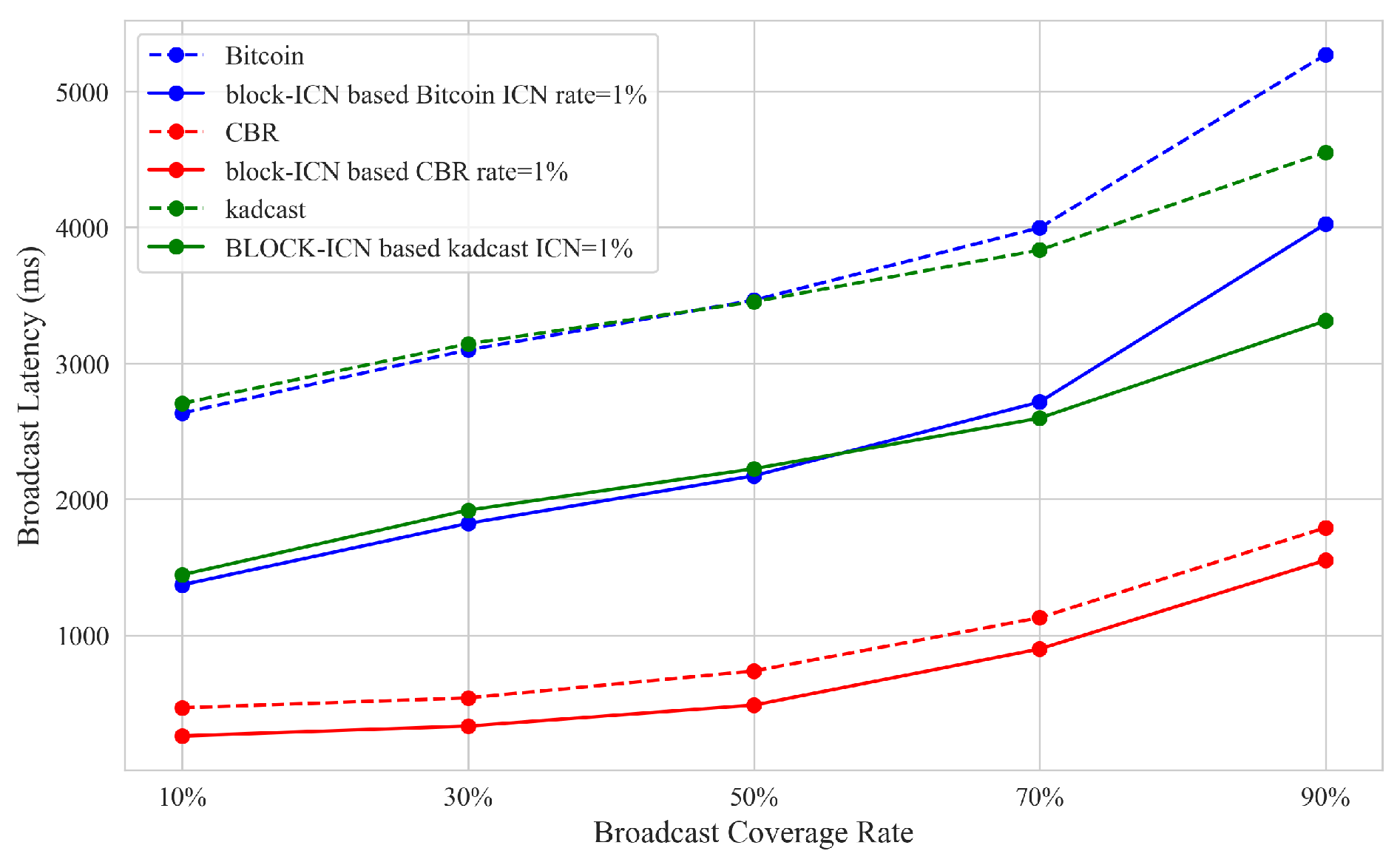
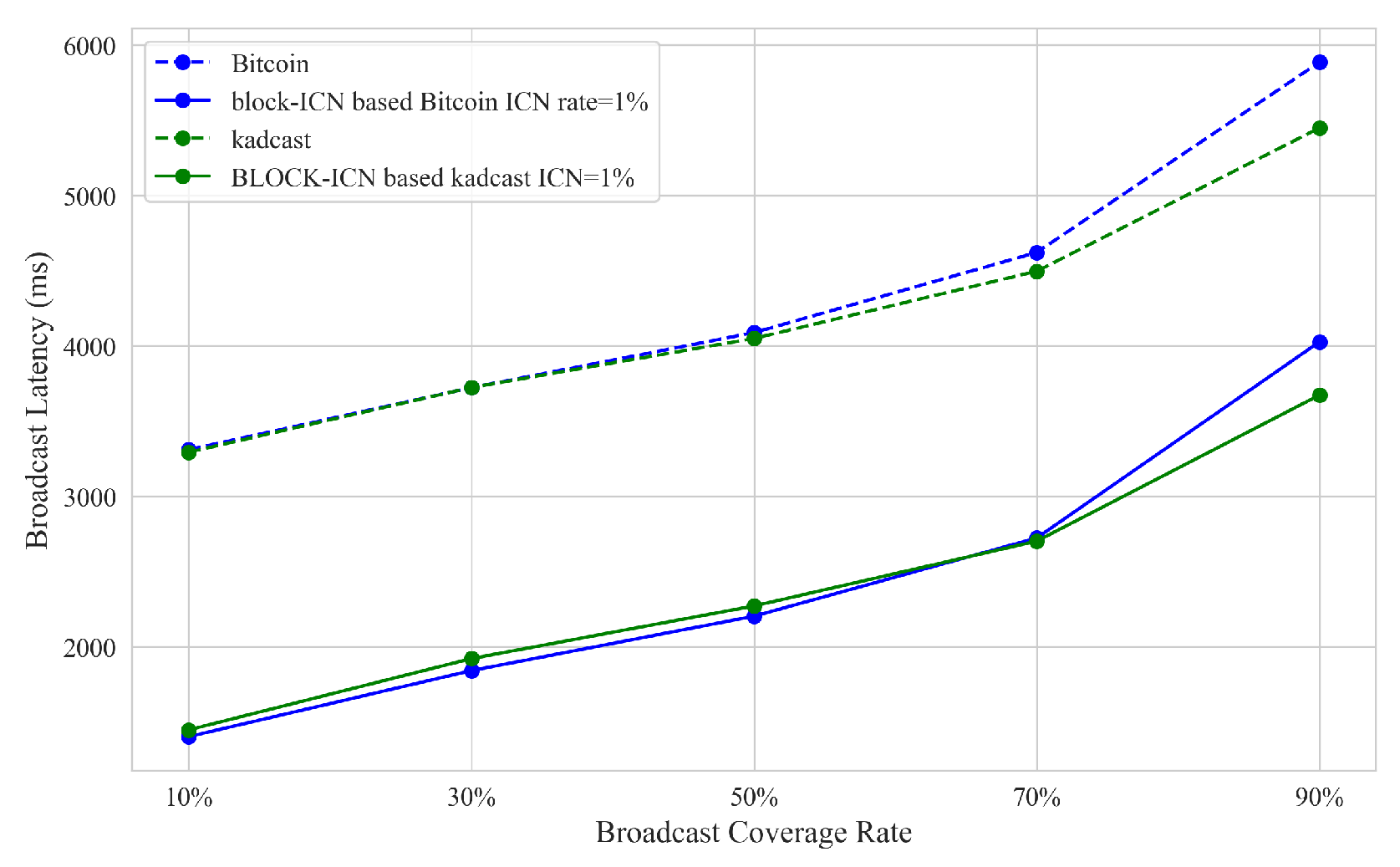
- Broadcast delay: The broadcast delay of the blockchain network refers to the time required for transactions and blocks to be broadcast in the network. In the experiment, we selected the broadcast delay of blocks in the network as the main reference, and we fixed the number of blockchain network nodes to 16,000, which is the current scale of the actual Bitcoin network. We compared the changes in block broadcast time under different broadcast coverage rates between BLOCK-ICN and the Bitcoin network.
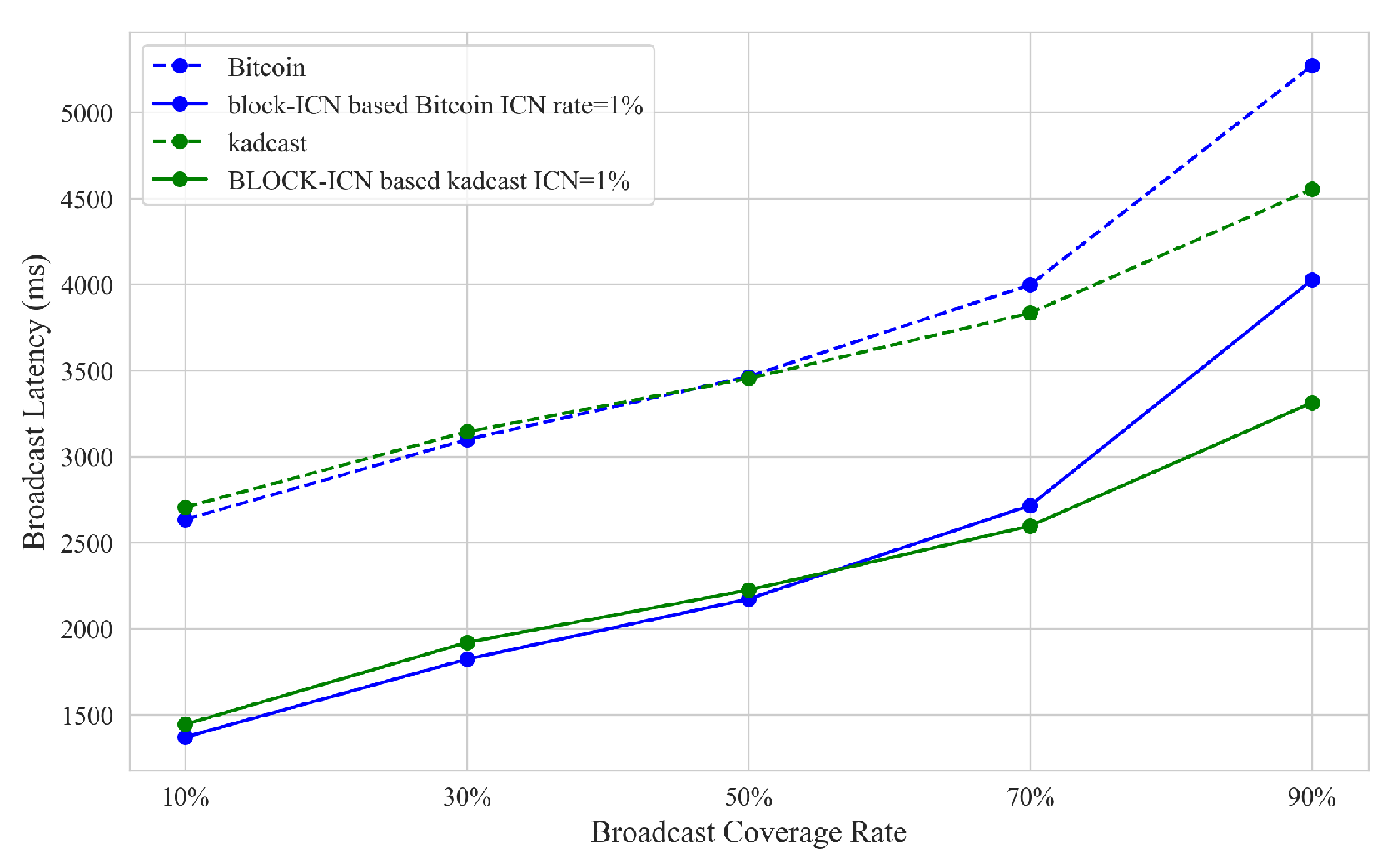
- Network scalability: Network scalability refers to the changes in network broadcast delay as the number of network nodes increases. According to data from bitnodes [41], the number of Bitcoin nodes was about 6000 in 2015, about 9000 in 2019, and was estimated to be about 16,000 in 2023. Therefore, in our experiment, network scalability refers to the changes in the time required to broadcast blocks to the entire network as the number of nodes increased from 2000 to 16,000.
- Network load: Since simulating ICN multicast in the P2P network is difficult, we based our analysis on the existing research on NDN multicast and IP unicast bandwidth utilization in blockchain networks [14], and we applied the bandwidth optimization parameters set in the simulation experiment. We compared the bandwidth consumption under different network scales.
6.2. Broadcast Delay Results
6.3. Network Scalability
6.4. Network Load
7. Discussion
- While BLOCK-ICN enhances broadcast efficiency, it may also reduce network decentralization, due to the introduction of structured routing and domain gateway nodes in ICN. Thus, more research and experimentation are required to evaluate the performance and scalability of ICN in practical deployments.
- In BLOCK-ICN, ICN nodes typically rely on certification authorities for authentication to mitigate Sybil and Eclipse attacks. As part of our future work, we aim to design a reputation-based evaluation mechanism that utilizes network information to assess node credibility, further reducing the risk of such attacks.
- Regarding the gateway node election algorithm, our current theoretical evaluation considered only simple network topologies. We acknowledge the need for further theoretical validation and experimental analysis in more complex network environments, to comprehensively demonstrate its advantages.
- When BLOCK-ICN is deployed in large-scale networks, the number of multicast groups and members may increase significantly, posing performance challenges for gateway nodes. Since this issue is difficult to fully simulate in a network emulation environment, real-world deployment and testing are necessary for further verification and optimization.
- Although SimBlock provides a controlled environment for evaluating block propagation and communication efficiency, real-world blockchain networks involve dynamic node churn, diverse network topologies, and varying degrees of congestion, which were not fully captured in our simulations. To further validate our approach, future work will incorporate more comprehensive network models or real-world experimental deployments.
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008. Available online: https://assets.pubpub.org/d8wct41f/31611263538139.pdf (accessed on 26 January 2025).
- Dai, H.N.; Zheng, Z.; Zhang, Y. Blockchain for Internet of Things: A survey. IEEE Internet Things J. 2019, 6, 8076–8094. [Google Scholar] [CrossRef]
- Mettler, M. Blockchain technology in healthcare: The revolution starts here. In Proceedings of the 2016 IEEE 18th International Conference on e-Health Networking, Applications and Services (Healthcom), Munich, Germany, 14–16 September 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–3. [Google Scholar]
- Croman, K.; Decker, C.; Eyal, I.; Gencer, A.E.; Juels, A.; Kosba, A.; Miller, A.; Saxena, P.; Shi, E.; Gün Sirer, E.; et al. On Scaling Decentralized Blockchains. In Proceedings of the Financial Cryptography and Data Security, Christ Church, Barbados, 26 February 2016; Clark, J., Meiklejohn, S., Ryan, P.Y., Wallach, D., Brenner, M., Rohloff, K., Eds.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2016; pp. 106–125. [Google Scholar] [CrossRef]
- Dotan, M.; Pignolet, Y.A.; Schmid, S.; Tochner, S.; Zohar, A. Survey on Blockchain Networking: Context, State-of-the-Art, Challenges. ACM Comput. Surv. 2021, 54, 107:1–107:34. [Google Scholar] [CrossRef]
- Decker, C.; Wattenhofer, R. Information Propagation in the Bitcoin Network. In Proceedings of the IEEE P2P 2013 Proceedings, Trento, Italy, 9–11 September 2013; pp. 1–10. [Google Scholar] [CrossRef]
- Papadis, N.; Borst, S.; Walid, A.; Grissa, M.; Tassiulas, L. Stochastic Models and Wide-Area Network Measurements for Blockchain Design and Analysis. In Proceedings of the IEEE INFOCOM 2018–IEEE Conference on Computer Communications, Honolulu, HI, USA, 16–19 April 2018; pp. 2546–2554. [Google Scholar] [CrossRef]
- Rohrer, E.; Tschorsch, F. Kadcast: A Structured Approach to Broadcast in Blockchain Networks. In Proceedings of the 1st ACM Conference on Advances in Financial Technologies, Zurich, Switzerland, 21–23 October 2019; Association for Computing Machinery: New York, NY, USA, 2019. AFT ’19. pp. 199–213. [Google Scholar] [CrossRef]
- Maymounkov, P.; Mazières, D. Kademlia: A Peer-to-Peer Information System Based on the XOR Metric. In Proceedings of the Peer-to-Peer Systems, Cambridge, MA, USA, 7–8 March 2002; Druschel, P., Kaashoek, F., Rowstron, A., Eds.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2002; pp. 53–65. [Google Scholar] [CrossRef]
- Falcon. A Fast Bitcoin Backbone. 2023. Available online: http://www.falcon-net.org (accessed on 26 January 2025).
- FIBRE Fast Internet Bitcoin Relay Engine. 2023. Available online: https://bitcoinfibre.org/ (accessed on 26 January 2025).
- Yakovenko, A. Solana: A New Architecture for a High Performance Blockchain v0. 8.13. 2018. Available online: https://solana.com/solana-whitepaper.pdf (accessed on 26 January 2025).
- Jin, T.; Zhang, X.; Liu, Y.; Lei, K. BlockNDN: A Bitcoin Blockchain Decentralized System over Named Data Networking. In Proceedings of the 2017 Ninth International Conference on Ubiquitous and Future Networks (ICUFN), Milan, Italy, 4–7 July 2017; pp. 75–80. [Google Scholar] [CrossRef]
- Thai, Q.T.; Ko, N.; Byun, S.H.; Kim, S.M. Design and Implementation of NDN-Based Ethereum Blockchain. J. Netw. Comput. Appl. 2022, 200, 103329. [Google Scholar] [CrossRef]
- Ahlgren, B.; Dannewitz, C.; Imbrenda, C.; Kutscher, D.; Ohlman, B. A Survey of Information-Centric Networking. IEEE Commun. Mag. 2012, 50, 26–36. [Google Scholar] [CrossRef]
- Guo, J.; Wang, M.; Chen, B.; Yu, S.; Zhang, H.; Zhang, Y. Enabling Blockchain Applications Over Named Data Networking. In Proceedings of the ICC 2019–2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Stoica, I.; Morris, R.; Karger, D.; Kaashoek, M.F.; Balakrishnan, H. Chord: A Scalable Peer-to-Peer Lookup Service for Internet Applications. ACM SIGCOMM Comput. Commun. Rev. 2001, 31, 149–160. [Google Scholar] [CrossRef]
- Miller, A.; Litton, J.; Pachulski, A.; Gupta, N.; Levin, D.; Spring, N.; Bhattacharjee, B. Discovering Bitcoin’s Public Topology and Influential Nodes; University of Maryland: College Park, MD, USA, 2015. [Google Scholar]
- Wang, X.; Jiang, X.; Liu, Y.; Wang, J.; Sun, Y. Data Propagation for Low Latency Blockchain Systems. IEEE J. Sel. Areas Commun. 2022, 40, 3631–3644. [Google Scholar] [CrossRef]
- Bhabak, P.; Harutyunyan, H.; Kropf, P. Efficient Broadcasting Algorithm in Harary-like Networks. In Proceedings of the 2017 46th International Conference on Parallel Processing Workshops (ICPPW), Bristol, UK, 14–17 August 2017; pp. 162–170. [Google Scholar] [CrossRef]
- Kim, S.K.; Ma, Z.; Murali, S.; Mason, J.; Miller, A.; Bailey, M. Measuring Ethereum Network Peers. In Proceedings of the Internet Measurement Conference 2018, Boston, MA, USA, 31 October–2 November 2018; IMC ’18. Association for Computing Machinery: New York, NY, USA, 2018; pp. 91–104. [Google Scholar] [CrossRef]
- Karp, R.; Schindelhauer, C.; Shenker, S.; Vocking, B. Randomized Rumor Spreading. In Proceedings of the 41st Annual Symposium on Foundations of Computer Science, Redondo Beach, CA, USA, 12–14 November 2000; pp. 565–574. [Google Scholar] [CrossRef]
- Sundhar Ram, S.; Nedić, A.; Veeravalli, V.V. Asynchronous Gossip Algorithms for Stochastic Optimization. In Proceedings of the 48h IEEE Conference on Decision and Control (CDC) Held Jointly with 2009 28th Chinese Control Conference, Shanghai, China, 15–18 December 2009; pp. 3581–3586. [Google Scholar] [CrossRef]
- Donet Donet, J.A.; Pérez-Solà, C.; Herrera-Joancomartí, J. The Bitcoin P2P Network. In Proceedings of the Financial Cryptography and Data Security, Christ Church, Barbados, 7 March 2014; Böhme, R., Brenner, M., Moore, T., Smith, M., Eds.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2014; pp. 87–102. [Google Scholar] [CrossRef]
- Sourav, S.; Robinson, P.; Gilbert, S. Slow Links, Fast Links, and the Cost of Gossip. IEEE Trans. Parallel Distrib. Syst. 2019, 30, 2130–2147. [Google Scholar] [CrossRef]
- Zhang, L.; Afanasyev, A.; Burke, J.; Jacobson, V.; Claffy, K.; Crowley, P.; Papadopoulos, C.; Wang, L.; Zhang, B. Named data networking. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 66–73. [Google Scholar] [CrossRef]
- Liao, Y.; Sheng, Y.; Wang, J. A brief survey on information centric networking proof of concepts for IMT-2020 and emerging networks. J. Netw. New Media 2018, 7, 54–63. [Google Scholar]
- Jacobson, V.; Smetters, D.K.; Thornton, J.D.; Plass, M.F.; Briggs, N.H.; Braynard, R.L. Networking named content. In Proceedings of the 5th International Conference on Emerging Networking Experiments and Technologies, Rome, Italy, 1–4 December 2009; pp. 1–12. [Google Scholar]
- Venkataramani, A.; Kurose, J.F.; Raychaudhuri, D.; Nagaraja, K.; Mao, M.; Banerjee, S. Mobilityfirst: A mobility-centric and trustworthy internet architecture. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 74–80. [Google Scholar] [CrossRef]
- Fotiou, N.; Nikander, P.; Trossen, D.; Polyzos, G.C. Developing information networking further: From PSIRP to PURSUIT. In Proceedings of the Broadband Communications, Networks, and Systems: 7th International ICST Conference, BROADNETS 2010, Athens, Greece, 25–27 October 2010; Revised Selected Papers 7. Springer: Berlin/Heidelberg, Germany, 2012; pp. 1–13. [Google Scholar]
- Wang, J.; Chen, G.; You, J.; Sun, P. Seanet: Architecture and technologies of an on-site, elastic, autonomous network. J. Netw. New Media 2020, 6, 1–8. [Google Scholar]
- Information-Centric Networking in Networks Beyond IMT-2020: Framework of Locally Enhanced Name Mapping and Resolution. 2020. Available online: https://store.accuristech.com/standards/itu-t-y-3079?product_id=2881802 (accessed on 26 January 2025).
- Li, R.; Asaeda, H. DIBN: A Decentralized Information-Centric Blockchain Network. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Luu, L.; Narayanan, V.; Zheng, C.; Baweja, K.; Gilbert, S.; Saxena, P. A Secure Sharding Protocol For Open Blockchains. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, CCS ’16, Vienna, Austria, 24–28 October 2016; ACM: New York, NY, USA, 2016; pp. 17–30. [Google Scholar] [CrossRef]
- Datta, S.; Giannella, C.; Kargupta, H. K-Means Clustering Over a Large, Dynamic Network. In Proceedings of the 2006 SIAM International Conference on Data Mining (SDM), Bethesda, MD, USA, 20–22 April 2006; Proceedings, Society for Industrial and Applied Mathematics. SIAM: Philadelphia, PA, USA, 2006; pp. 153–164. [Google Scholar] [CrossRef]
- Hao, W.; Zeng, J.; Dai, X.; Xiao, J.; Hua, Q.S.; Chen, H.; Li, K.C.; Jin, H. Towards a Trust-Enhanced Blockchain P2P Topology for Enabling Fast and Reliable Broadcast. IEEE Trans. Netw. Serv. Manag. 2020, 17, 904–917. [Google Scholar] [CrossRef]
- sallal, M.F.; Owenson, G.; Adda, M. Proximity Awareness Approach to Enhance Propagation Delay on the Bitcoin Peer-to-Peer Network. In Proceedings of the 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS), Atlanta, GA, USA, 5–8 June 2017; pp. 2411–2416. [Google Scholar] [CrossRef]
- Aoki, Y.; Otsuki, K.; Kaneko, T.; Banno, R.; Shudo, K. SimBlock: A Blockchain Network Simulator. In Proceedings of the IEEE INFOCOM 2019—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Paris, France, 29 April–2 May 2019; pp. 325–329. [Google Scholar] [CrossRef]
- Banno, R.; Shudo, K. Simulating a Blockchain Network with SimBlock. In Proceedings of the 2019 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Seoul, Republic of Korea, 14–17 May 2019; pp. 3–4. [Google Scholar] [CrossRef]
- Nagayama, R.; Banno, R.; Shudo, K. Identifying Impacts of Protocol and Internet Development on the Bitcoin Network. In Proceedings of the 2020 IEEE Symposium on Computers and Communications (ISCC), Rennes, France, 7–10 July 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Bitnodes: Global Bitcoin Nodes Distribution. 2023. Available online: https://bitnodes.earn.com/ (accessed on 9 August 2024).
- Global Ping Statistics—WonderNetwork. 2023. Available online: https://wondernetwork.com/pings (accessed on 9 August 2024).
- Top Countries for Bandwidth. 2023. Available online: https://testmy.net/country (accessed on 9 August 2024).
- BitInfoCharts. Bitcoin Block Size Chart. 2025. Available online: https://bitinfocharts.com/comparison/bitcoin-size.html (accessed on 5 March 2025).












| Software and Hardware | Versions/Models |
|---|---|
| Operating System | 64-bit Windows 10 |
| Processor | Intel Core i5-10505 |
| CPU | 3.20 GHz |
| RAM | 32 GB DDR4 |
| Hard Drive | 1 TB SSD |
| Platform | SimBlock |
| IDE | PyCharm and IntelliJ |
| Programming Language | Python 3.10 and Java |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhou, Y.; Han, R.; Li, Y. A Blockchain Network Communication Architecture Based on Information-Centric Networking. Appl. Sci. 2025, 15, 3340. https://doi.org/10.3390/app15063340
Zhou Y, Han R, Li Y. A Blockchain Network Communication Architecture Based on Information-Centric Networking. Applied Sciences. 2025; 15(6):3340. https://doi.org/10.3390/app15063340
Chicago/Turabian StyleZhou, Yufei, Rui Han, and Yang Li. 2025. "A Blockchain Network Communication Architecture Based on Information-Centric Networking" Applied Sciences 15, no. 6: 3340. https://doi.org/10.3390/app15063340
APA StyleZhou, Y., Han, R., & Li, Y. (2025). A Blockchain Network Communication Architecture Based on Information-Centric Networking. Applied Sciences, 15(6), 3340. https://doi.org/10.3390/app15063340









