Smart Grid Protection, Automation and Control: Challenges and Opportunities
Abstract
1. Introduction
2. Methodology
- What are the current and possible substation architectures for protection, automation and control?
- What are the general demands during migration from CPAC to VPAC systems?
- Describe the role of time synchronization, redundancy and cyber security in this migration.
3. Evolution of Substation Architectures and Digital Modernizations for Smart Substations
3.1. Comparasion of a Conventional P&C Systems vs. CPAC Approach
3.2. Migration from Conventional to Digital Substations
3.3. Virtualization of Protection, Automation and Control (VPAC)
4. Time Management and Synchronization
| Aspect | Description |
|---|---|
| Atomic Clocks vs. Grandmaster Clocks (GMC) [60] | Atomic Clocks: The vibration of atoms, such as those of cesium or rubidium, can be harnessed to provide an exceptionally precise measure of time. These atoms are a standard component in a multitude of scientific and telecommunications applications. GMC: Can use atomic technologies, high-quality crystal oscillators, or GPS to maintain network time accuracy. They act as the primary synchronization source in a network. |
| Time Synchronization in Networks [65] | Standards: Synchronization must comply with IEEE 1588 v2 (Precision Time Protocol, PTP) for station bus and process bus environments, and with the data models specified in IEC 61850. Requirements: Support for SNMP MIB from Annex E of UNE-EN IEC 62439-3:2022, and automatic adjustments for daylight saving time changes. |
| Implementation of PTP in Virtualized Environments | PTP Hardware Support on Host: Specialized hardware that supports PTP and synchronizes with an external server. PTP Passthrough: Uses direct I/O to minimize latency and improve accuracy. PTP Software Solutions: Specific software implementations for PTP. Network Time Protocol (NTP): Alternative for non-critical environments. Synchronization with External PTP Grandmaster: Synchronizes hosts and virtual machines with an external master clock. Virtualization Tools for Time Synchronization: Virtualization tools that synchronize with the host but do not meet PTP accuracy. |
| Additional Considerations | Network Infrastructure: Switches and routers must support and be configured for PTP. Latency in Virtualization: Consider latency and jitter in virtualized environments. Consistency in Synchronization: In order to prevent drift, it is essential that all components are synchronized with the same time source. Configuration Validation: Check and validate PTP configuration before deployment in production environments. |
| Synchronization Method [66] | Typical Accuracy | Description | Application |
|---|---|---|---|
| GPS | 10 ns | Synchronization based on the Global Navigation Satellite System (GNSS) with Coordinated Universal Time (UTC). Requires a hardware receiver and antenna. Generally used as a master time source. | High-precision synchronization for critical applications such as power utilities and telecommunications. |
| PTP | 100 ns | High-precision time distribution protocol with error correction through boundary or transparent clocks. Supports multiple sources with Best Master Clock Algorithm (BMCA) and LAN or WAN switching. | Critical and time-sensitive applications such as sample values (SV) and synchrophasors. |
| IRIG-B [67,68] | 1 µs | Precise time distribution requiring local cabling. Generally sourced from GPS clocks. For Intelligent Electronic Devices (IEDs), the typical accuracy of IRIG-B time synchronization is as follows:
Most modern IEDs adopt unmodulated IRIG-B to meet the stringent timing requirements of standards like IEC 61850, ensuring reliable event sequencing (SOE) and precise fault location through synchronized measurements. | Less critical applications such as GOOSE, MMS, and supervisory data in utility substations. |
| NTP | 200 µs (over LAN) | Lower precision time distribution protocol, including its stateless derivative Simple Network Time Protocol (SNTP). Achieves better precision when distributed from a local source. | Non-critical network devices and computing platforms. |
| Aspect | Descriptions |
|---|---|
| Network Configuration | Ensure the network infrastructure, including switches and routers, supports PTP and is appropriately configured. |
| Latency and Jitter | Solutions that minimize latency and jitter are preferable. Enabling “latency-sensitive” features in the hypervisor can help reduce these issues. |
| Consistency in the Environment | Ensure that all components in the virtualized environment are synchronized with the same time source to avoid time drift issues. |
| Testing and Validation | Before deploying PTP in a production environment, it is crucial to test and validate the configuration to ensure the required level of precision. |
| Round Trip Time (RTT) Testing | Conduct RTT tests using GOOSE messages between synchronized applications to verify the accuracy of synchronization. |
5. Redundancy
6. Comprehensive Cybersecurity Framework for VPAC Systems in Electrical Substations
7. Interoperability
8. Future of Electrical Substations, Challenges, and Advancing Towards Autonomous Network Management
9. Conclusions
- System reliability and real-time performance—VPAC solutions must match or exceed the performance of CPAC systems, ensuring low-latency operation for protection and control functions;
- Interoperability and legacy integration—The migration should allow for coexistence between legacy hardware and new digital systems, ensuring a smooth transition without full infrastructure replacement. Compatibility with IEC 61850 standards is critical;
- Robust communication infrastructure—A high-speed, deterministic network is essential to handle the increased data exchange between virtualized applications and field devices;
- Seamless deployment and minimal downtime—Planning the transition carefully is necessary to avoid service disruptions and operational risks. VPAC must be deployed in phases, allowing gradual adoption while maintaining system integrity.
- Scalability and maintainability—VPAC must support future expansions and software updates without requiring major system overhauls, reducing long-term operational costs.
- Network redundancy, using PRP (Parallel Redundancy Protocol) or HSR (High-availability Seamless Redundancy);
- Hardware redundancy, deploying multiple physical processing units;
- Software redundancy, ensuring VPAC applications run on geographically dispersed virtual machines for fault tolerance.
- Encryption and authentication protocols to prevent unauthorized access;
- Network segmentation and firewall protections to isolate critical assets;
- AI-driven anomaly detection to identify and mitigate cyber threats in real time.
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| AD | Active Directory |
| AI | Artificial Intelligence |
| BESS | Battery Energy Storage Systems |
| CIP | Critical Infrastructure Protection |
| CMS | Centralized Monitoring System |
| CPAC | Centralized Protection Automation and Control |
| CPU | Central Processing Unit |
| CS | Cyber Security |
| CT | Current Transformer |
| DAN | Dually Attached Node |
| DER | Distributed Energy Resources |
| DNP | Distributed Network Protocol |
| EMC | Electromagnetic Compatibility |
| EMS | Energy Management System |
| EV | Electrical Vehicle |
| FO | Fiber Optic |
| GMC | GrandMaster Clock |
| GNSS | Global Navigation Satellite System |
| GOOSE | Generic Object-Oriented Substation Event |
| GPS | Global Positioning System |
| HSR | High-Availability Seamless Redundancy |
| HW | Hardware |
| IED | Intelligent Electronic Device |
| IT | Information Technology |
| KVM | Kernel-based Virtual Machine |
| LDAP | Light-Weight Directory Access |
| LD | Logical Device |
| MAC | Media Access Control |
| MIB | Management Information Base |
| MU | Merge Unit |
| MFA | Multi Factor Authentication |
| NERC CIP | North American Electric Reliability Corporation Critical Infrastructure Protection |
| NIC | Network Interface Card |
| NPR | Numerical Protection Relay |
| OS | Operating System |
| OT | Operational Technology |
| P&C | Protection and Control |
| PACS | Protection, Automation, and Control System. |
| PCI | Peripheral Component Interconnect |
| PCIe | Peripheral Component Interconnect express |
| PDP | Programmable Data Planes |
| PRP | Parallel Redundancy Protocol |
| PTP | Precision Time Protocol |
| RBAC | Role Based Access Controls |
| RCT | Redundancy Control Trailer |
| SAN | Singly Attached Nodes |
| SAS | Substation Automation Systems |
| SCADA | Substation Automation and Data Acquisition |
| SDLC | Software Development Lifecycle |
| SoE | Sequence of Events |
| SMV | Sampled Measured Values |
| SNMP | Network Management Protocol |
| SNTP | Simple Network Time Protocol |
| SOC | Separation of Concern |
| SDN | Software-Defined Networks |
| SV | Sample Values |
| SW | Software |
| UFLS | Underfrequency-based Load-shedding Scheme |
| VM | Virtual Machines |
| vNIC | Virtual Network Interface Card |
| VLAN | Virtual Local Area Network |
| VPAC | Virtualization of Protection, Automation and Control |
References
- Lundqvist, B. 100 Years of Relay Protection, the Swedish ABB Relay History; ABB Automation Products, Substation Automation Division: Västerås, Sweden, 2001. [Google Scholar]
- Working Group on Centralized Substation Protection and Control, IEEE Power System Relaying Committee. Advancements in Centralized Protection and Control Within a Substation. IEEE Trans. Power Deliv. 2016, 31, 1945–1952. [Google Scholar] [CrossRef]
- Valtari, J. Centralized Architecture of the Electricity Distribution Substation Automation—Benefits and Possibilities; Tampere University of Technology: Tampere, Finland, 2013; ISBN 978-952-15-3061-6. [Google Scholar]
- EN 61850-5; Communication Networks and Systems for Power Utility Automation—Part 5: Communication Requirements for Functions and Device Models. CENELEC: Brussels, Belgium, 2013.
- Kulmala, A.; Raipala, O.; Hovila, P.; Yazadzhijan, B.-E.; Dantas, R.; Scoble, C. Virtualised Centralised Protection and Control—Constellation Project Case Study. In Proceedings of the 27th International Conference on Electricity Distribution (CIRED 2023), Rome, Italy, 12–15 June 2023; Institution of Engineering and Technology: Rome, Italy, 2023; pp. 1670–1674. [Google Scholar]
- About vPAC Ready Infrastructure. Available online: https://docs.vmware.com/en/VMware-Edge-Compute-Stack/services/utility-substation-vpac-ready-infrastructure/GUID-C9BAB086-57A7-4E74-838E-D530867AC21D.html (accessed on 15 May 2024).
- Hamanah, W.M.; Hossain, M.I.; Shafiullah, M.; Abido, M.A. AC Microgrid Protection Schemes: A Comprehensive Review. IEEE Access 2023, 11, 76842–76868. [Google Scholar] [CrossRef]
- ADMS and DERMS. Available online: https://search.abb.com/library/Download.aspx?DocumentID=9AKK107046A1569&DocumentPartId= (accessed on 22 April 2024).
- Home | SpringerLink. Available online: https://link.springer.com/ (accessed on 2 July 2024).
- IEEE Xplore. Available online: https://ieeexplore.ieee.org/Xplore/home.jsp (accessed on 18 June 2024).
- Web of Science. Available online: https://www.webofscience.com/wos/alldb/basic-search (accessed on 18 June 2024).
- Scopus. Available online: https://www.scopus.com (accessed on 18 June 2024).
- ScienceDirect.Com | Science, Health and Medical Journals, Full Text Articles and Books. Available online: https://www.sciencedirect.com/ (accessed on 2 July 2024).
- Thompson, M.; Lukach, D. Centralized Substation Protection and Control_IEEE PES PSRC WG K15. 2015. Available online: https://www.pes-psrc.org/kb/report/020.pdf (accessed on 22 May 2024).
- McKinsey Technology Trends Outlook 2023 | McKinsey. Available online: https://www.mckinsey.com/capabilities/mckinsey-digital/our-insights/the-top-trends-in-tech#new-and-notable (accessed on 18 June 2024).
- Can We Use IEC 61850 for Safety Related Functions? Available online: https://www.researchgate.net/publication/306244440_Can_we_use_IEC_61850_for_safety_related_functions (accessed on 18 June 2024).
- Santos, G.R.; Zancul, E.; Manassero, G.; Spinola, M. From Conventional to Smart Substations: A Classification Model. Electr. Power Syst. Res. 2024, 226, 109887. [Google Scholar] [CrossRef]
- Flores, E.P.; Niveri, H. Centralized Protection and Control—Enhancing Reliability, Availability, Flexibility and Improving Operating Cost Efficiency of Distribution Substations; ABB: Zurich, Switzerland, 2022. [Google Scholar]
- Beresh, B. I22: End-of-Useful Life Assessment of P&C Devices Report to Main Committee. 2015. Available online: https://www.pes-psrc.org/kb/report/048.pdf (accessed on 1 January 2024).
- De Oliveira e Sousa, B.; Starck, J.; Valtari, J. Viability Assessment for Centralised Protection and Control System Architectures in Medium Voltage (MV) Substations. CIRED—Open Access Proc. J. 2017, 2017, 1531–1534. [Google Scholar] [CrossRef]
- Rentschler, M.; Heine, H. The Parallel Redundancy Protocol for Industrial IP Networks. In Proceedings of the 2013 IEEE International Conference on Industrial Technology (ICIT), Cape Town, South Africa, 25–28 February 2013; pp. 1404–1409. [Google Scholar]
- Nsaif, S.A.; Rhee, J.M. Improvement of High-Availability Seamless Redundancy (HSR) Traffic Performance for Smart Grid Communications. J. Commun. Netw. 2012, 14, 653–661. [Google Scholar] [CrossRef]
- UNE-EN_IEC_62439-3:2022; Redes de Comunicación Industrial. Redes de Automatización de Alta Disponibilidad. Parte 3: Protocolo de Redundancia Paralela (PRP) y Anillo Homogéneo de Alta Disponibilidad (HSR). (Ratificada Por La Asociación Española de Normalización En Marzo de 2022). UNE: Madrid, Spain, 2022.
- IEEE Std 1686-2022 (Revision of IEEE Std 1686-2013); IEEE Standard for Intelligent Electronic Devices Cybersecurity Capabilities. IEEE: New York, NY, USA, 2023; pp. 1–36. [CrossRef]
- Strobel, M.; Wiedermann, N.; Eckert, C. Novel Weaknesses in IEC 62351 Protected Smart Grid Control Systems. In Proceedings of the 2016 IEEE International Conference on Smart Grid Communications (SmartGridComm), Sydney, NSW, Australia, 6–9 November 2016; pp. 266–270. [Google Scholar]
- Christensen, D.; Martin, M.; Gantumur, E.; Mendrick, B. Risk Assessment at the Edge: Applying NERC CIP to Aggregated Grid-Edge Resources. Electr. J. 2019, 32, 50–57. [Google Scholar] [CrossRef]
- IEEE Std 1588; IEEE Standard for a Precision Clock Synchronization Protocol for Networked Measurement and Control Systems. IEEE: New York, NY, USA, 2008.
- MiCOM Agile P747 Bus Protection: GE Grid Solutions. Available online: https://www.gevernova.com/grid-solutions/multilin/catalog/p747.htm (accessed on 9 August 2024).
- Multilin B90 Low Impedance Bus Protection System :: GE Grid Solutions. Available online: https://www.gevernova.com/grid-solutions/multilin/catalog/b90.htm (accessed on 9 August 2024).
- Easergy MiCOM P40. Available online: https://www.se.com/sg/en/product-range/60794-process-bus-and-iec-618509-2-le-for-protection-relays/ (accessed on 9 August 2024).
- Substation Automation, Protection and Control—Products | Ingeteam. Available online: https://www.ingeteam.com/en-us/power-grid-protection-and-control/substation-automation-protection-and-control/c32_19_p/products.aspx (accessed on 9 August 2024).
- Centralized Protection Featuring SIPROTEC 7SX85. Available online: https://www.siemens.com/global/en/products/energy/energy-automation-and-smart-grid/webinars/24-en/2407-protection-cpc-siprotec-7sx85.html (accessed on 9 August 2024).
- Ladd, S.B.; Raffield, T.I.; Haithcox, E.; Fultz, J.; Shrestha, A.; Chatterjee, A.; Nadkar, P. Case Study: Designing Centralized Protection and Control Systems for a Distribution Substation at Duke Energy. Available online: https://selinc.com/api/download/138747/ (accessed on 1 January 2024).
- Byerly, J.; Thakur, M.; Hostetler, J.; Burger, C.; Wenke, S. Distribution Digital Substation—Consolidated Protection and Digital Secondary Systems. Available online: https://selinc.com/api/download/138749/ (accessed on 1 January 2024).
- Protect a Range of Substation Assets Using One Relay. Available online: https://selinc.com/mktg/protect-a-range-of-substation-assets-using-one-relay/?utm_source=pardot&utm_medium=cpc&utm_content=display&utm_campaign=487E-CPC (accessed on 9 August 2024).
- Ganoo, P.; Joshi, S.; Valtari, J.; Niveri, H. Centralized Protection and Control System: Are We Ready for Deployment in the Chemical, Oil, and Gas Industry? IEEE Ind. Appl. Mag. 2022, 28, 48–61. [Google Scholar] [CrossRef]
- Centralized and Virtualized Protection and Control. Available online: https://new.abb.com/medium-voltage/digital-substations/campaigns/smart-substation-control-and-protection-ssc600 (accessed on 7 August 2024).
- SSC600 Toolkit. Available online: https://go.insideplus.abb.com/business-areas-and-divisions/electrification/divisions/distribution-solutions/product-groups/distribution-automation/da-sales-support/ssc600-toolkit (accessed on 9 August 2024).
- EN 60870-5-104; Telecontrol Equipment and Systems Part 5-104: Transmission Protocols—Network Access for IEC 60870-5-101 Using Standard Transport Profiles. CENELEC: Brussels, Belgium, 2006.
- Gutiérrez, S.A.; Botero, J.F.; Gómez, N.G.; Fletscher, L.A.; Leal, A. Next-Generation Power Substation Communication Networks: IEC 61850 Meets Programmable Networks. IEEE Power Energy Mag. 2023, 21, 58–67. [Google Scholar] [CrossRef]
- Shah, V. Protection—Evolution, Technologies and Trends. Power Res.—J. CPRI 2021, 17, 89–95. [Google Scholar] [CrossRef]
- Virtualization in Digital Substations. Available online: https://www.welotec.com/whitepaper/virtualization-in-digital-substations/ (accessed on 7 August 2024).
- EN 50160; Voltage Characteristics of Electricity Supplied by Public Electricity Networks. CENELEC: Brussels, Belgium, 2010.
- Implementing IP/MPLS Network-Based Synchronization for Line Differential Protection and Control. Available online: https://cse.cigre.org/cse-n031/implementing-ip/mpls-network-based-synchronization-for-line-differential-protection-and-control.html (accessed on 12 October 2024).
- Aichhorn, A.; Mayrhofer, R.; Krammer, H.; Kern, T. Realization of Line Current Differential Protection over IP-Based Networks Using IEEE 1588 for Synchronous Sampling. In Proceedings of the 13th International Conference on Development in Power System Protection 2016 (DPSP), Edinburgh, UK, 7–10 March 2016; pp. 1–6. [Google Scholar]
- Arc Fault Detection System REA. Available online: https://new.abb.com/medium-voltage/apparatus/arc-fault-protection/arc-fault-protection-system-rea (accessed on 16 November 2024).
- The Virtues of Virtualization. Available online: https://library.e.abb.com/public/259eadcfe59d40bba743c7764bd24713/118-123%20m2395_EN.pdf?x-sign=OmgCr+eHINwrBuyGu6OHutrOctLuI20OPGCQAc5AFbwwb1okK936gpB17DrayyvV (accessed on 18 June 2024).
- Smart Substation Control and Protection SSC600 SW. Available online: https://new.abb.com/medium-voltage/digital-substations/protection-relays/multiapplication/smart-substation-control-and-protection-ssc600-sw (accessed on 12 August 2024).
- Dayabhai, S.; Prestwich, J. A substation automation solution that uses virtualization to reduce cost while ensuring redundancy and security compliance. In Proceedings of the Power and Energy Automation Conference, Washington, DC, USA, 5–7 March 2018. [Google Scholar]
- vPACalliance. Available online: https://vpacalliance.com/ (accessed on 18 June 2024).
- E4SAlliance. Available online: https://www.e4salliance.com/ (accessed on 18 June 2024).
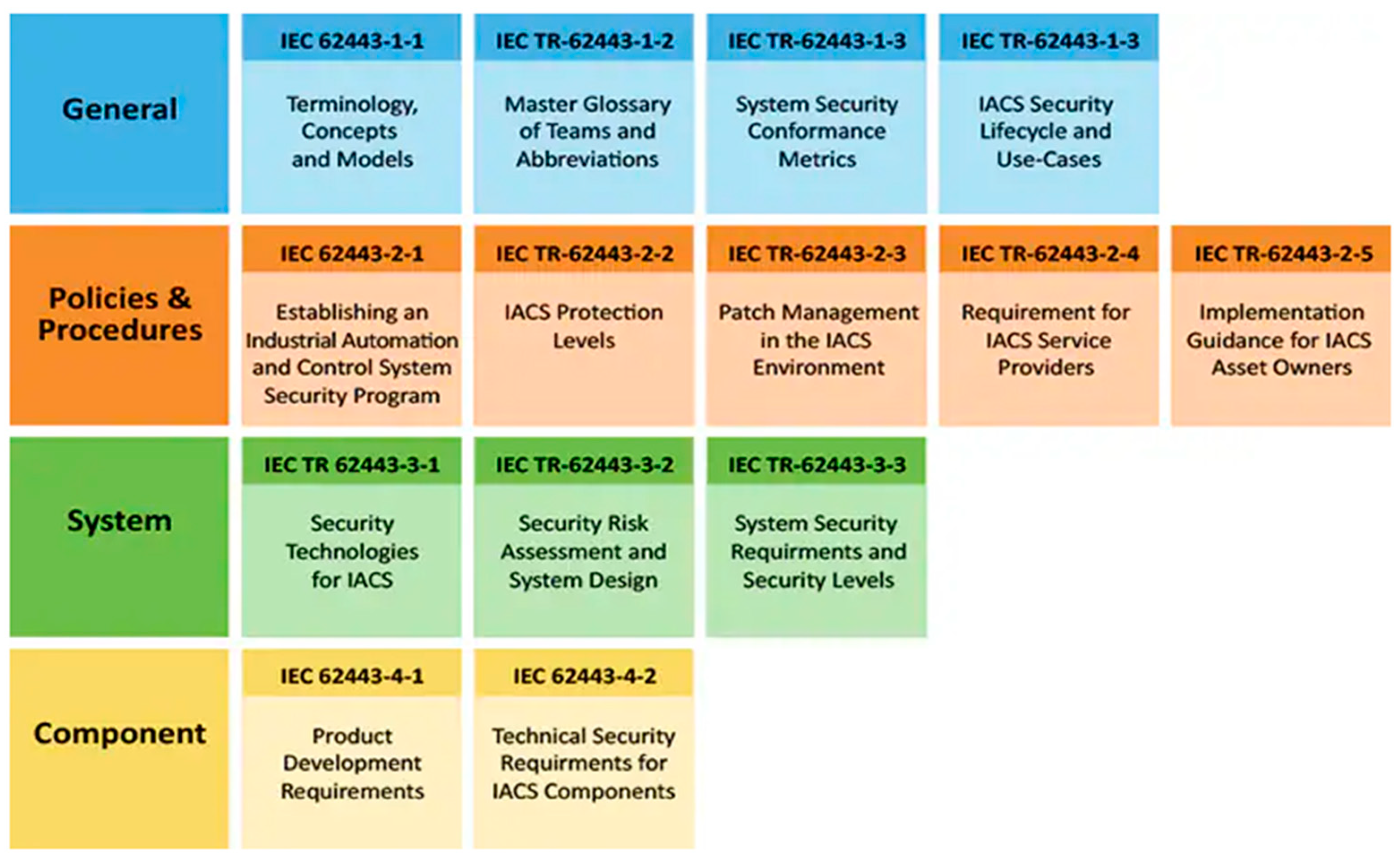
- EN IEC 62443; Security for Industrial Automation and Control Systems. CENELEC: Brussels, Belgium, 2024.
- Utility Substation Virtual Protection, Automation, and Control (vPAC) Ready Infrastructure; VMware, Inc.: Palo Alto, CA, USA, 2023.
- Virtualization of Protection and Control—Evaluation and Deployment Considerations. Available online: https://library.e.abb.com/public/3f5ff4e1c22b49a28987ffcac74eae96/White%20paper%202NGA001642_RevA_EN_finalb.pdf (accessed on 2 January 2024).
- Chen, R.; Zhang, Y.; Cao, C.; Zhao, Y.; Li, B.; Zhang, J.; Gu, W. Clock Synchronization in T-MPLS Network via PTP (IEEE 1588 V2). In Proceedings of the 2009 Asia Communications and Photonics Conference and Exhibition (ACP), Shanghai, China, 2–6 November 2009; Volume 2009-Supplement, pp. 1–8. [Google Scholar]
- Ingram, D.M.E.; Schaub, P.; Campbell, D.A.; Taylor, R.R. Evaluation of Precision Time Synchronisation Methods for Substation Applications. In Proceedings of the 2012 IEEE International Symposium on Precision Clock Synchronization for Measurement, Control and Communication Proceedings, San Francisco, CA, USA, 24–28 September 2012; pp. 37–42. [Google Scholar]
- Habib, H.F.; Lashway, C.R.; Mohammed, O.A. On the Adaptive Protection of Microgrids: A Review on How to Mitigate Cyber Attacks and Communication Failures. In Proceedings of the 2017 IEEE Industry Applications Society Annual Meeting, Cincinnati, OH, USA, 1–5 October 2017; pp. 1–8. [Google Scholar]
- Apostolov, A. Efficient Maintenance Testing in Digital Substations Based on IEC 61850 Edition 2. Prot. Control. Mod. Power Syst. 2017, 2, 37. [Google Scholar] [CrossRef]
- IEC/IEEE 61850-9-3; Communication Networks and Systems for Power Utility Automation—Part 9-3: Precision Time Protocol Profile for Power Utility Automation. IEC: Geneva, Switzerland, 2016.
- Grand Master Clock and GPS/GNSS Timing Solutions | Case Studies | GPS Receiver Chips & Modules | FURUNO. Available online: https://www.furuno.com/en/gnss/case/grandmasterclock#Disconnect (accessed on 10 May 2024).
- Volgyesi, P.; Dubey, A.; Krentz, T.; Madari, I.; Metelko, M.; Karsai, G. Time Synchronization Services for Low-Cost Fog Computing Applications. In Proceedings of the 2017 International Symposium on Rapid System Prototyping (RSP), Seoul, Republic of Korea, 19–20 October 2017; pp. 57–63. [Google Scholar]
- Ferrari, P.; Flammini, A.; Rinaldi, S.; Prytz, G. Evaluation of Time Gateways for Synchronization of Substation Automation Systems. IEEE Trans. Instrum. Meas. 2012, 61, 2612–2621. [Google Scholar] [CrossRef]
- Wang, H.; Zhu, G.; Hou, M.; Wang, S. Time Synchronization Based on Multiplexing RPR Channel and IRIG-B Time Code. In Proceedings of the 2015 5th International Conference on Electric Utility Deregulation and Restructuring and Power Technologies (DRPT), Changsha, China, 26–29 November 2015; pp. 869–872. [Google Scholar]
- Network Timing Technology: NTP vs. PTP | Masterclock Industry Knowledge. Available online: https://www.masterclock.com/network-timing-technology-ntp-vs-ptp.html (accessed on 12 October 2024).
- Antonova, G.S.; Apostolov, A.; Arnold, D.; Bedrosian, P.S.; Brunner, C.; Bui, D.P.; Dickerson, W.; Dood, M.; Gerstung, H.; Giarratano, D.; et al. Standard Profile for Use of IEEE Std 1588-2008 Precision Time Protocol (PTP) in Power System Applications: IEEE PES PSRC Working Group H7/Sub C7 Members and Guests. In Proceedings of the 2012 IEEE International Symposium on Precision Clock Synchronization for Measurement, Control and Communication Proceedings, San Francisco, CA, USA, 24–28 September 2012; pp. 31–36. [Google Scholar]
- Sagen, E.; Workman, K. Methods of Time Synchronization. Available online: https://cdn.selinc.com/assets/Literature/Publications/Technical%20Papers/6370_MethodsTime_KW_20090302_Web.pdf (accessed on 22 May 2024).
- Zeng, Y.; Chen, G. Research on Methods to Improve Precise Time Synchronization for IRIG-B Code Encoder. In Proceedings of the 2012 Asia-Pacific Power and Energy Engineering Conference, Shanghai, China, 27–29 March 2012; pp. 1–4. [Google Scholar]
- IRIG-B Time Code Accuracy and Connection Requirements with Comments on IED and System Design Considerations. Available online: https://www.arbiter.com/files/product-attachments/irig_accuracy_and_connection_requirements.pdf (accessed on 16 June 2024).
- Bian, B.; Tang, X.; Huang, X. Risk Analysis and Research Based on IEEE 1588 in Smart High Voltage Substation. In Proceedings of the IEEE PES Innovative Smart Grid Technologies, Tianjin, China, 21–24 May 2012. [Google Scholar]
- IEC 61588; Precision Clock Synchronization Protocol for Networked Measurement and Control Systems. IEC: Geneva, Switzerland, 2021.
- NIST SP 800-82; Guide to Industrial Control Systems (ICS) Security. NIST: Gaithersburg, MD, USA, 2015.
- IEEE Std C37.238; IEEE Standard Profile for Use of IEEE 1588 Precision Time Protocol in Power System Applications. IEEE: New York, NY, USA, 2017.
- Cherdantseva, Y.; Burnap, P.; Blyth, A.; Eden, P.; Jones, K.; Soulsby, H.; Stoddart, K. A Review of Cyber Security Risk Assessment Methods for SCADA Systems. Comput. Secur. 2016, 56, 1–27. [Google Scholar] [CrossRef]
- Antonova, G.; Frisk, L.; Tournier, J.-C. Communication Redundancy for Substation Automation. In Proceedings of the 2011 64th Annual Conference for Protective Relay Engineers, College Station, TX, USA, 11–14 April 2011; pp. 344–355. [Google Scholar]
- Kumar, S.; Das, N.; Islam, S. High Performance Communication Redundancy in a Digital Substation Based on IEC 62439-3 with a Station Bus Configuration. In Proceedings of the 2015 Australasian Universities Power Engineering Conference (AUPEC), Wollongong, Australia, 27–30 September 2015; pp. 1–5. [Google Scholar]
- Taikina-aho, M. Redundant IEC 61850 Communication Protocols in Substation Automation. Master’s Thesis, University of Vaasa, Vaasa, Finland, 2011. [Google Scholar]
- IEC/TR 61850-1; Communication Networks and Systems for Power Utility Automation—Part 1: Introduction and Overview. IEC: Geneva, Switzerland, 2013.
- EN 61850-3; Communication Networks and Systems for Power Utility Automation—Part 3: General Requirements. CENELEC: Brussels, Belgium, 2013.
- EN 61850-9-2; Communication Networks and Systems for Power Utility Automation—Part 9-2: Specific Communication Service Mapping (SCSM)—Sampled Values over ISO/IEC 8802-3. CENELEC: Brussels, Belgium, 2011.
- IEC/TR 61850-90-4; Communication Networks and Systems for Power Utility Automation—Part 90-4: Network Engineering Guidelines. IEC: Geneva, Switzerland, 2020.
- IEC TR 61850-90-2; Communication Networks and Systems for Power Utility Automation—Part 90-2: Using IEC 61850 for Communication Between Substations and Control Centres. IEC: Geneva, Switzerland, 2016.
- EN 61508-1; Functional Safety of Electrical/Electronic/Programmable Electronic Safety-Related Systems—Part 1: General Requirements. CENELEC: Brussels, Belgium, 2010.
- EN 62439-1; Industrial Communication Networks—High Availability Automation Networks—Part 1: General Concepts and Calculation Methods. CENELEC: Brussels, Belgium, 2012.
- EN IEC 62439-3; Industrial Communication Networks—High Availability Automation Networks—Part 3: Parallel Redundancy Protocol (PRP) and High-Availability Seamless Redundancy (HSR). CENELEC: Brussels, Belgium, 2022.
- IEC TS 62351-1; Power Systems Management and Associated Information Exchange—Data and Communications Security—Part 1: Communication Network and System Security—Introduction to Security Issues. IEC: Geneva, Switzerland, 2007.
- IEC TS 60870-5-7; Telecontrol Equipment and Systems—Part 5-7: Transmission Protocols—Security Extensions to IEC 60870-5-101 and IEC 60870-5-104 Protocols (Applying IEC 62351). IEC: Geneva, Switzerland, 2013.
- CIP-002-3(i); Cyber Security—Critical Cyber Asset Identification. NERC: Washington, DC, USA, 2006.
- IEEE Std 1815; IEEE Standard for Electric Power Systems Communications—Distributed Network Protocol (DNP3). IEEE: New York, NY, USA, 2012.
- ISO/IEC 27001; Information Security, Cybersecurity and Privacy Protection—Information Security Management Systems—Requirements. IEC: Geneva, Switzerland, 2022.
- ANSI-TIA-942; Telecommunications Infrastructure Standard for Data Centers. TIA: Arlington, TX, USA, 2005.
- Antonova, G.S.; Sastry, S.; Vasudevan, B. Review of Digital Substation Communication Technologies. In Proceedings of the 2022 75th Annual Conference for Protective Relay Engineers (CPRE), College Station, TX, USA, 28–31 March 2022; pp. 1–26. [Google Scholar]
- IEEE Std C37.240-2014; IEEE Standard Cybersecurity Requirements for Substation Automation, Protection, and Control Systems. IEEE: New York, NY, USA, 2015; pp. 1–38. [CrossRef]
- IEEE Std 1547.3-2023 (Revision of IEEE Std 1547.3-2007); IEEE Guide for Cybersecurity of Distributed Energy Resources Interconnected with Electric Power Systems. IEEE: New York, NY, USA, 2023; pp. 1–183. [CrossRef]
- Dolezilek, D.; Gammel, D.; Fernandes, W. Cybersecurity Based on IEC 62351 and IEC 62443 for IEC 61850 Systems. In Proceedings of the 15th International Conference on Developments in Power System Protection (DPSP 2020), Liverpool, UK, 9–12 March 2020. 6p. [Google Scholar] [CrossRef]
- Ahn, G.-J.; Sandhu, R.; Kang, M.; Park, J. Injecting RBAC to Secure a Web-Based Workflow System. In Proceedings of the ACM Workshop on Role-Based Access Control, Berlin, Germany, 26–28 July 2000; pp. 1–10. [Google Scholar] [CrossRef]
- Koutsonikola, V.; Vakali, A. LDAP: Framework, Practices, and Trends. IEEE Internet Comput. 2004, 8, 66–72. [Google Scholar] [CrossRef]
- Leszczyna, R. Cybersecurity and Privacy in Standards for Smart Grids—A Comprehensive Survey. Comput. Stand. Interfaces 2018, 56, 62–73. [Google Scholar] [CrossRef]
- Zero Trust Maturity Model | CISA. Available online: https://www.cisa.gov/zero-trust-maturity-model (accessed on 28 May 2024).
- The Role of Vmtheft and Hyperjacking in Virtualization—ProQuest. Available online: https://www.proquest.com/openview/53dc5734a3fe20a0f7db99549209a8ac/1?pq-origsite=gscholar&cbl=18750&diss=y (accessed on 10 December 2024).
- Lathika, K. Recent Trends in IT—Virtualization. Available online: https://ssrn.com/abstract=2845483 (accessed on 22 May 2024).
- Cosman, E. Structuring the ISA/IEC 62443 Standards. Available online: https://gca.isa.org/blog/structuring-the-isa-iec-62443-standards (accessed on 9 September 2024).
- Dolezilek, D.; Hussey, L. Requirements or Recommendations? Sorting out NERC CIP, NIST, and DOE Cybersecurity. In Proceedings of the 2011 64th Annual Conference for Protective Relay Engineers, College Station, TX, USA, 11–14 April 2011; pp. 328–333. [Google Scholar]
- NERC. Available online: https://www.nerc.com/pa/Stand/Pages/default.aspx (accessed on 17 May 2024).
- Apostolov, A.; Dood, M.; Tengdin, J. Developing IEEE 1613 Standards for Communications Network in Substations. IEEE Power Energy Mag. 2004, 2, 73–75. [Google Scholar] [CrossRef]
- Hussain, S.M.S.; Ustun, T.S.; Kalam, A. A Review of IEC 62351 Security Mechanisms for IEC 61850 Message Exchanges. IEEE Trans. Ind. Inform. 2020, 16, 5643–5654. [Google Scholar] [CrossRef]
- IEEE Std 1547.4-2011; IEEE Guide for Design, Operation, and Integration of Distributed Resource Island Systems with Electric Power Systems. IEEE: New York, NY, USA, 2011; pp. 1–54. [CrossRef]
- Nist, G.M. The NIST Cybersecurity Framework 2.0; NIST CSWP 29; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2023.
- NIST SP 800-63 Digital Identity Guidelines. Available online: https://pages.nist.gov/ (accessed on 22 May 2024).
- Stouffer, K.; Pease, M.; Tang, C.; Zimmerman, T.; Pillitteri, V.; Lightman, S.; Hahn, A.; Saravia, S.; Sherule, A.; Thompson, M. Guide to Operational Technology (OT) Security; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2023.
- TPM 2.0 A Brief Introduction. Available online: https://trustedcomputinggroup.org/wp-content/uploads/TPM-2.0-A-Brief-Introduction.pdf (accessed on 22 May 2024).
- ISAGCQuick Start Guide: An Overview of ISA/IEC 62443 Standards Security of Industrial Automation and Control SystemsA Quick Start Guide FINAL. Available online: https://gca.isa.org/hubfs/ISAGCA%20Quick%20Start%20Guide%20FINAL.pdf (accessed on 22 May 2024).
- Blair, S.M.; Roscoe, A.J.; Irvine, J. Real-Time Compression of IEC 61869-9 Sampled Value Data. In Proceedings of the 2016 IEEE International Workshop on Applied Measurements for Power Systems (AMPS), Aachen, Germany, 28–30 September 2016; pp. 1–6. [Google Scholar]
- IEC 61869-2:2012; Instrument Transformers—Part 2: Additional Requirements for Current Transformers. IEC: London, UK, 2012. Available online: https://www.une.org/encuentra-tu-norma/busca-tu-norma/iec/?c=6050 (accessed on 10 January 2025).
- Home—UCAIug. Available online: https://www.ucaiug.org/default.aspx (accessed on 14 August 2024).
- Hong, Q.; Blair, S.M.; Catterson, V.M.; Dyśko, A.; Booth, C.D.; Rahman, T. Standardization of Power System Protection Settings Using IEC 61850 for Improved Interoperability. In Proceedings of the 2013 IEEE Power & Energy Society General Meeting, Vancouver, BC, Canada, 21–25 July 2013; pp. 1–5. [Google Scholar]
- Ustun, T.S. Interoperability and Interchangeability for Microgrid Protection Systems Using IEC 61850 Standard. In Proceedings of the 2016 IEEE International Conference on Power and Energy (PECon), Melaka, Malaysia, 28–29 November 2016; pp. 7–12. [Google Scholar]
- Ridwan, M.I.; Miswan, N.S.; Shokri, M.S.M.; Noran, M.N.; Lajim, R.M.; Awang, H.N. Interoperability in Smart Grid Using IEC 61850 Standard: A Power Utility Prospect. In Proceedings of the 2014 IEEE Innovative Smart Grid Technologies—Asia (ISGT ASIA), Kuala Lumpur, Malaysia, 20–23 May 2014; pp. 261–266. [Google Scholar]
- Kim, H.J.; Jeong, C.M.; Sohn, J.-M.; Joo, J.-Y.; Donde, V.; Ko, Y.; Yoon, Y.T. A Comprehensive Review of Practical Issues for Interoperability Using the Common Information Model in Smart Grids. Energies 2020, 13, 1435. [Google Scholar] [CrossRef]
- Stojanović, Z.; Vlaisavljević, M.; Simić, S.; Nunes, M.; Bardi, S. Testing of centralized protection in digital substations using a real-time simulator under the auspices of the IEC61850 standard. In Proceedings of the 14th PAC World Conference, Athens, Greece, 17–19 June 2024. [Google Scholar]
- Kabbara, N.; Nait Belaid, M.O.; Gibescu, M.; Camargo, L.R.; Cantenot, J.; Coste, T.; Audebert, V.; Morais, H. Towards Software-Defined Protection, Automation, and Control in Power Systems: Concepts, State of the Art, and Future Challenges. Energies 2022, 15, 9362. [Google Scholar] [CrossRef]
- Balouji, E.; Bäckström, K.; Olsson, V.; Hovila, P.; Niveri, H.; Kulmala, A.; Salo, A. Distribution network fault prediction utilising protection relay disturbance recordings and machine learning. In Proceedings of the 27th International Conference on Electricity Distribution (CIRED 2023), Rome, Italy, 12–15 June 2023; pp. 2273–2277. [Google Scholar]
- ADAM Fleet Management. Available online: https://new.abb.com/medium-voltage/digital-substations/software-products/adam-fleet-management (accessed on 12 October 2024).
- Adams, H.S. ABB Survey Reveals Staggering Downtime Costs for Manufacturers: The Urgent Need for Reliable Maintenance Strategies. Available online: https://manufacturingdigital.com/procurement-and-supply-chain/unscheduled-downtime-costs-us-125-000-per-hour-abb-survey (accessed on 12 October 2024).
- Aleem, S.A.; Shahid, N.; Naqvi, I.H. Methodologies in Power Systems Fault Detection and Diagnosis. Energy Syst. 2014, 6, 85–108. [Google Scholar] [CrossRef]
- Hunt, R.; Flynn, B.; Smith, T. The Substation of the Future: Moving Toward a Digital Solution. IEEE Power Energy Mag. 2019, 17, 47–55. [Google Scholar] [CrossRef]
- Pashaei, M.; Kauhaniemi, K.; Laaksonen, H. Implementation of Adaptive Centralized Protection Scheme in Active Networks with a HIL Setup. In Proceedings of the 2024 International Conference on Smart Energy Systems and Technologies (SEST), Torino, Italy, 10–12 September 2024; pp. 1–6. [Google Scholar]
- Santo, D. Testing Digital Substations: Advancements with HIL. Available online: https://www.typhoon-hil.com/blog/testing-digital-substations-advancements-with-hardware-in-the-loop-technology/ (accessed on 9 September 2024).

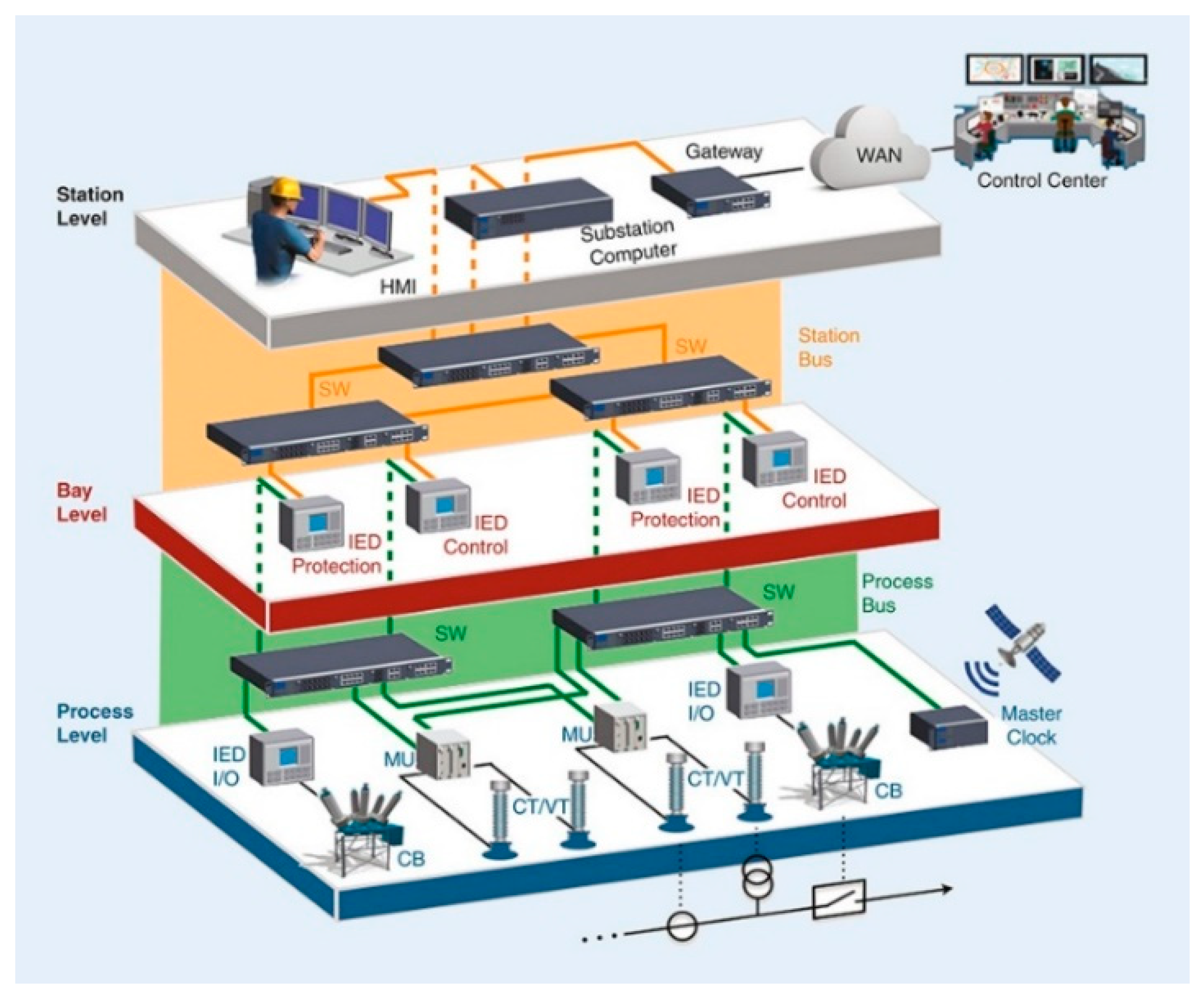
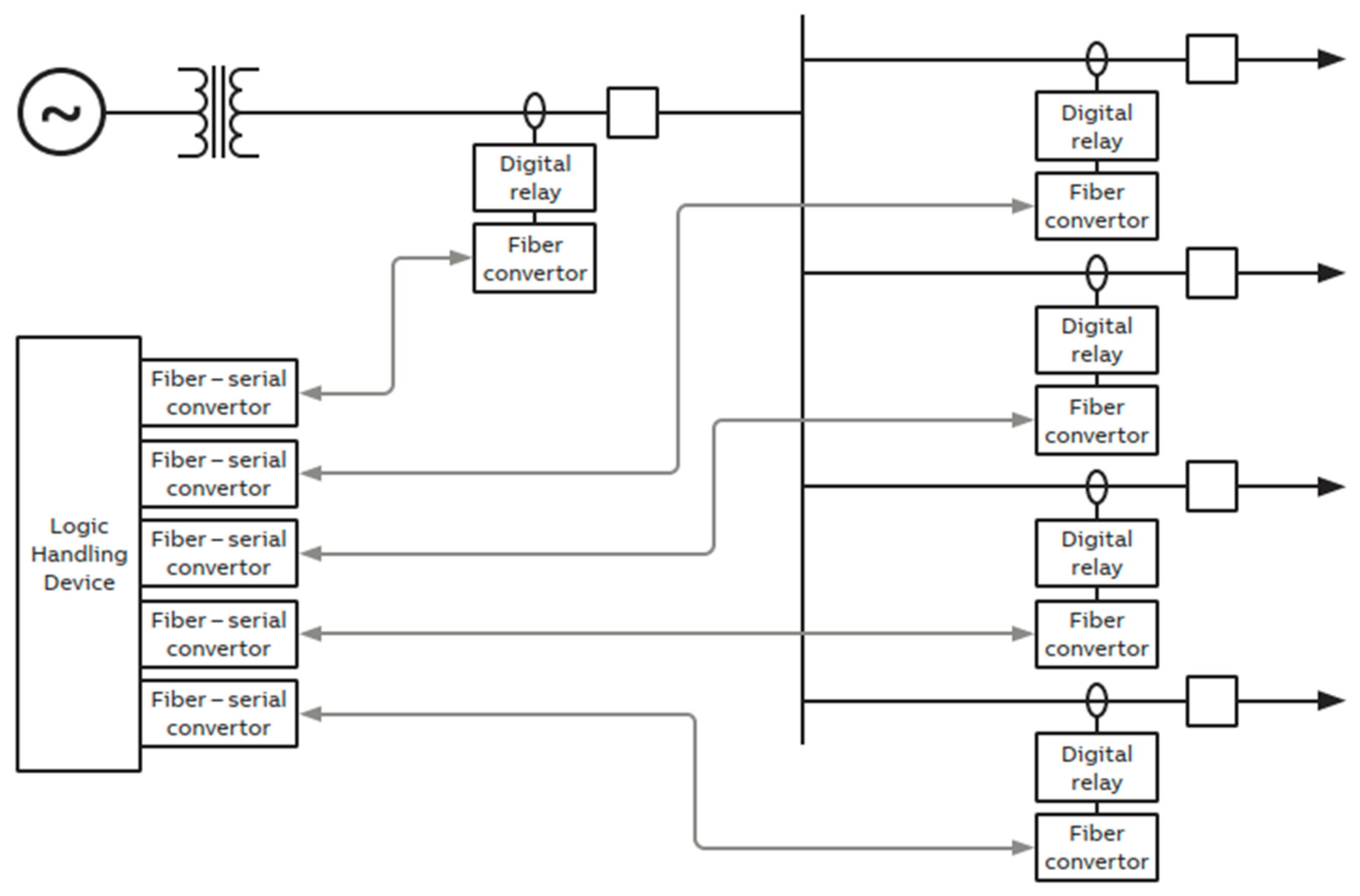
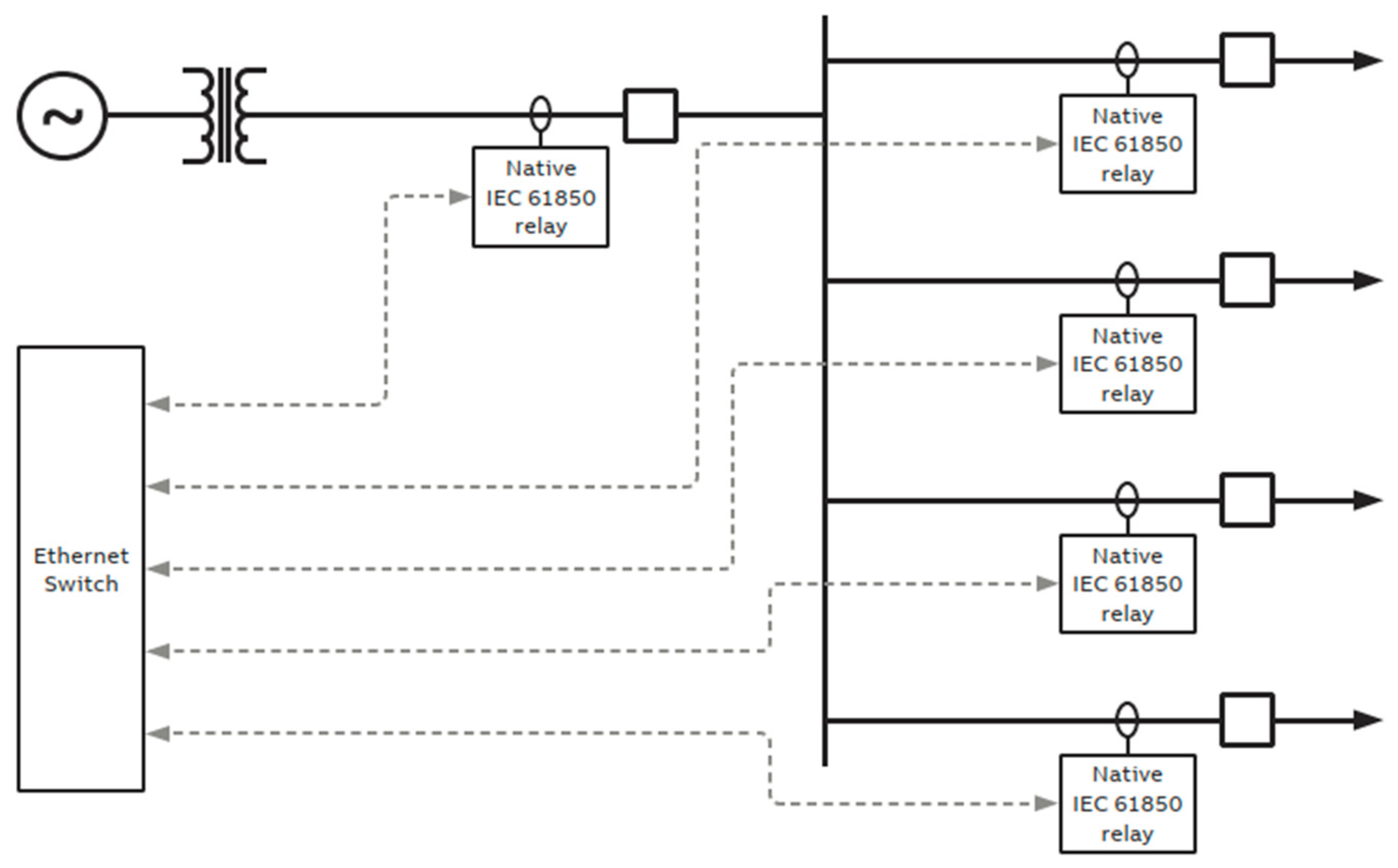
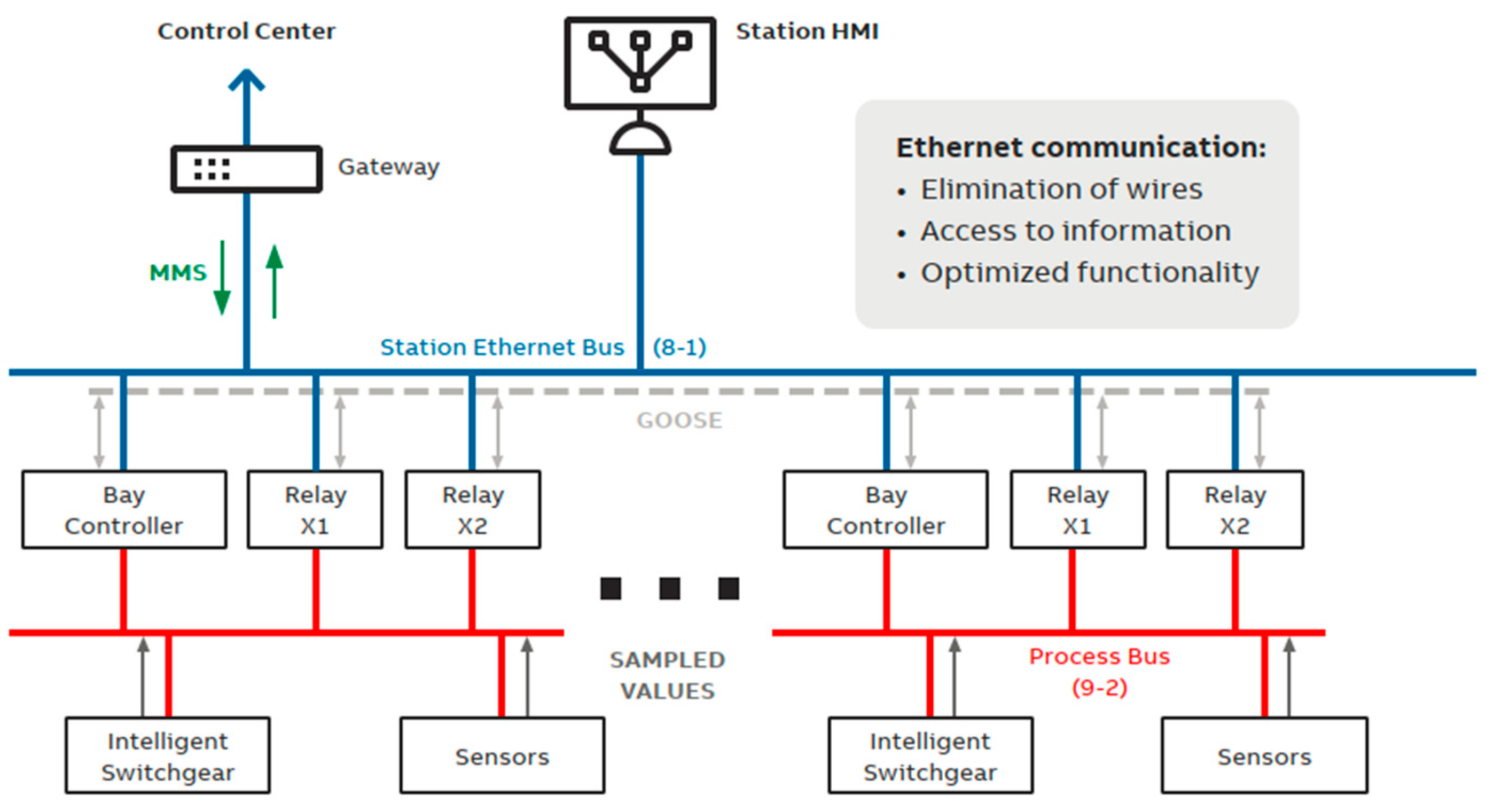
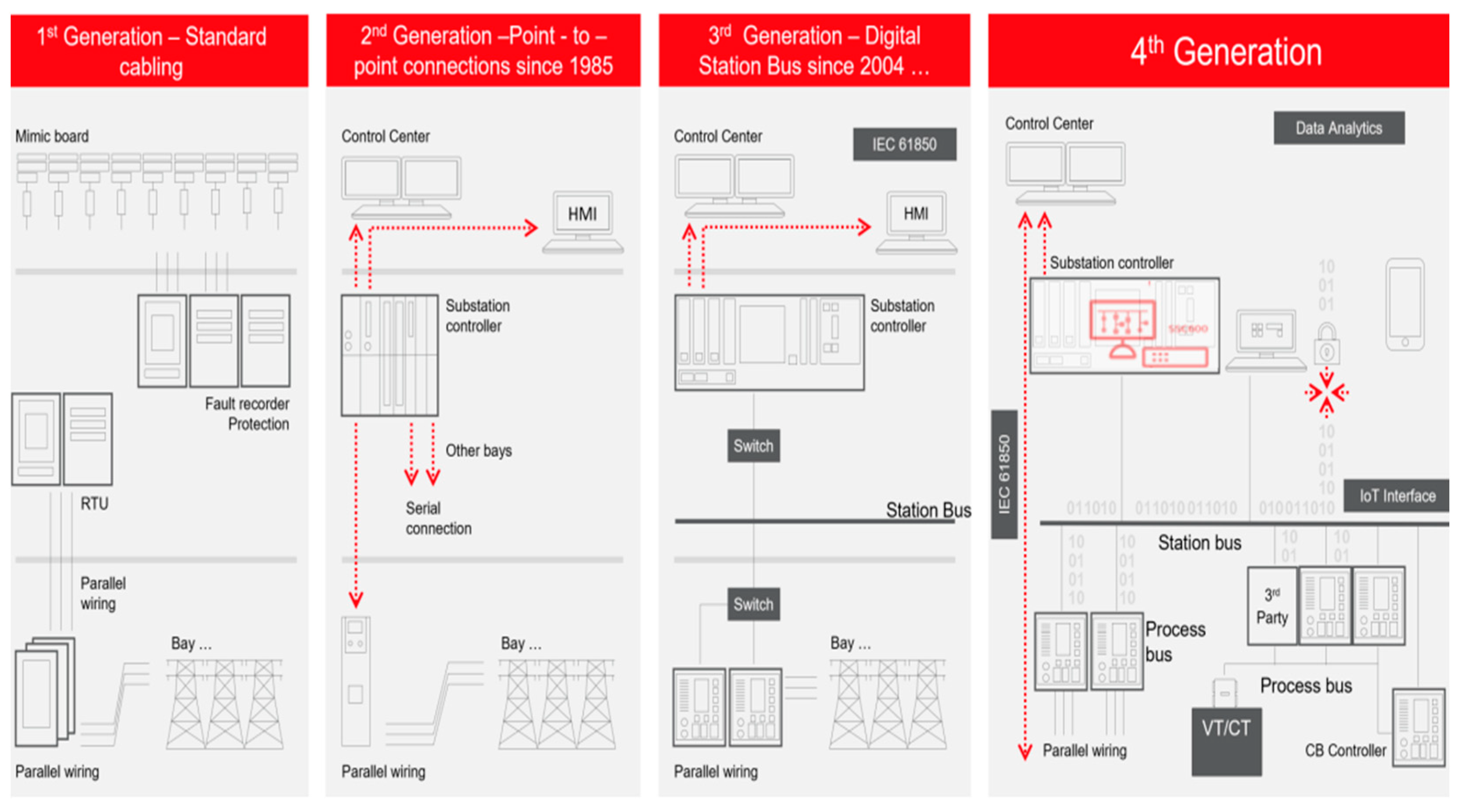
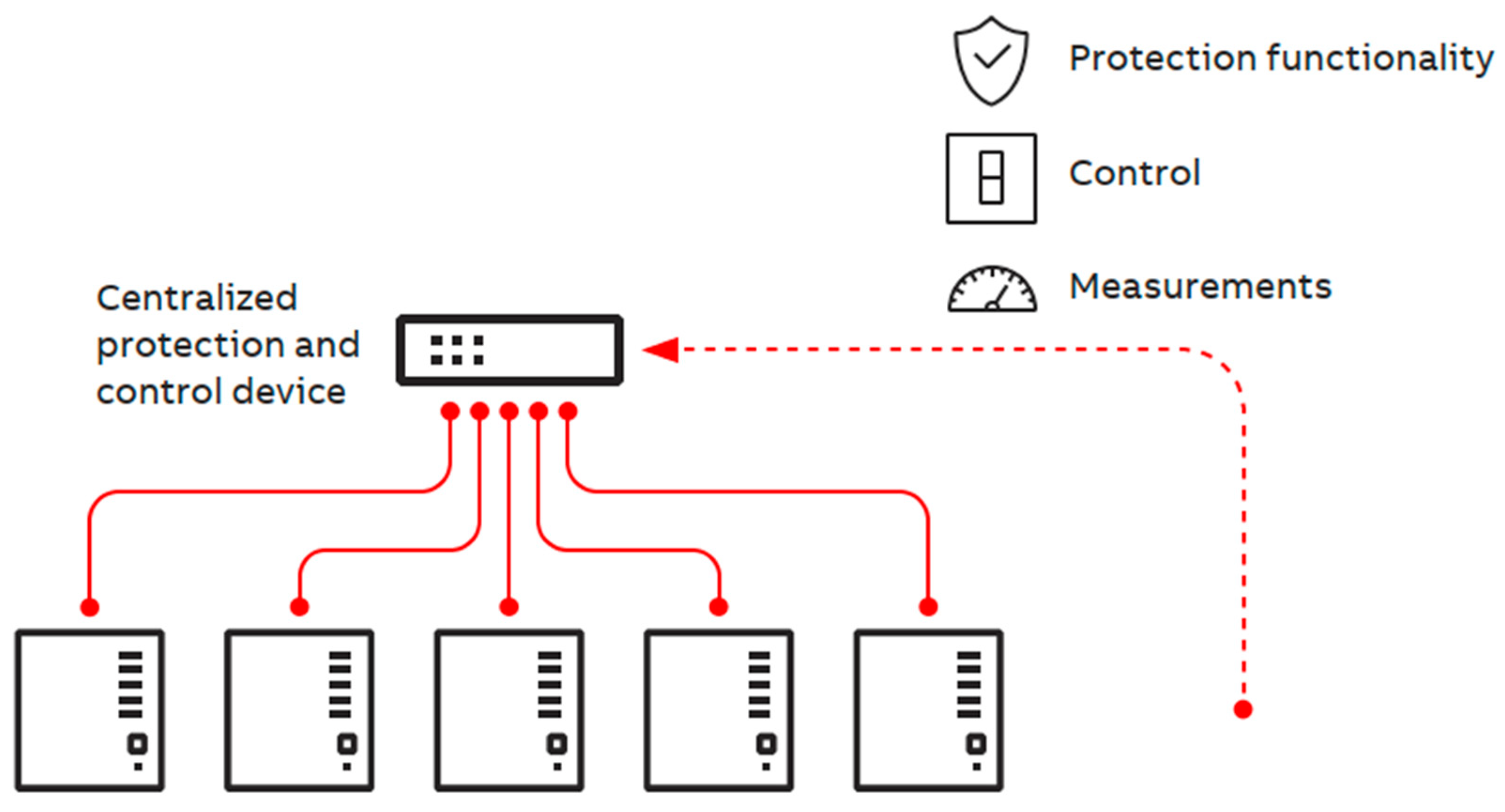


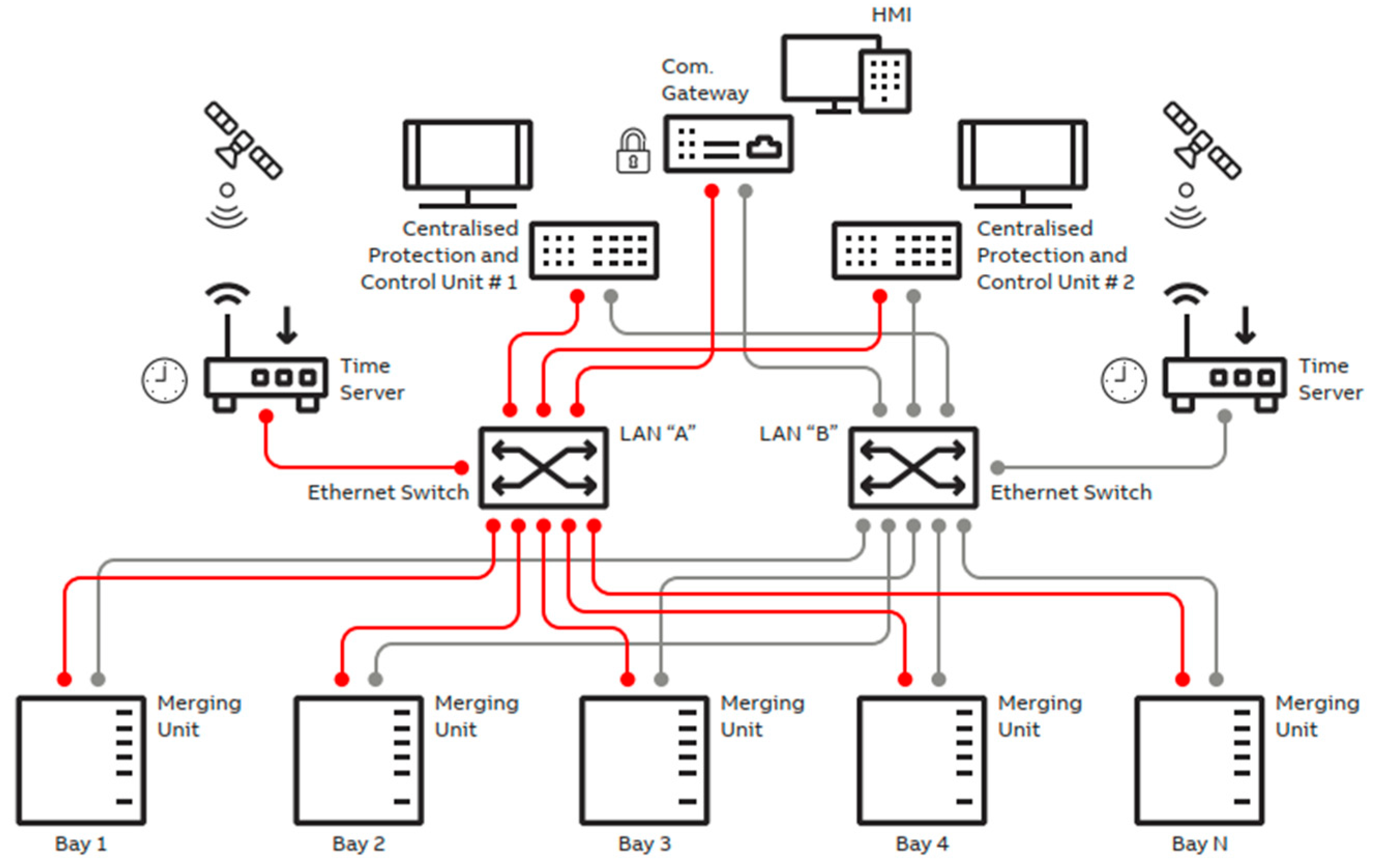
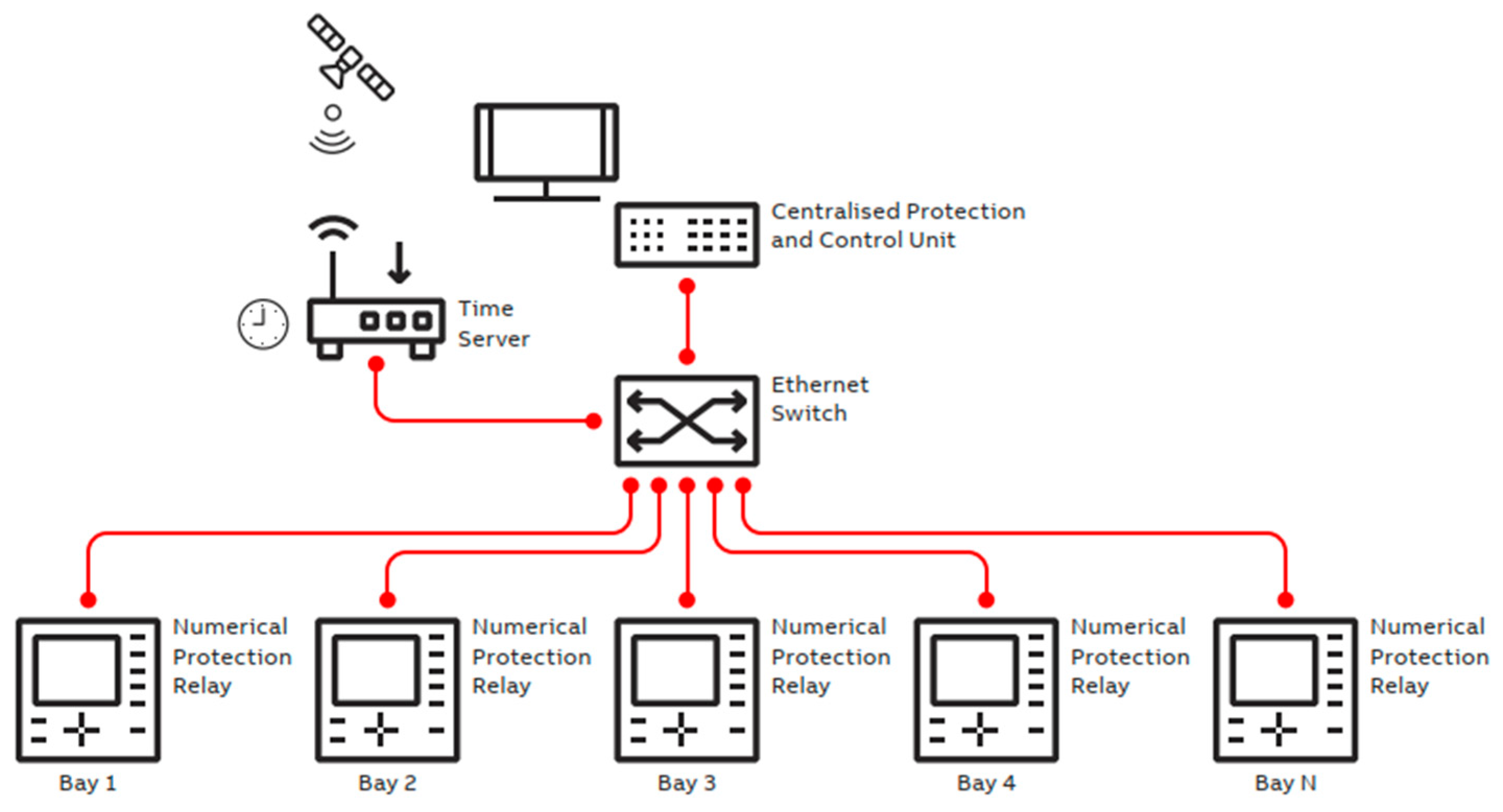

| Criteria/Test Feature | Conventional P&C System | CPAC Approach |
|---|---|---|
| Flexible Configuration | Flexibility is limited by the need to configure each device individually. | High flexibility with rapid, centralized reconfiguration capabilities. |
| Commissioning and Maintenance | Requires time and effort for each individual device. | Centralized configuration and maintenance streamline the process, enhancing efficiency. |
| Startup Costs | Lower initial costs due to reliance on existing devices and mature technology. | Requires an initial investment in new technology and staff training. |
| Life-Cycle Cost | High maintenance and upgrade costs due to the distributed nature of the system. | Centralization leads to cost reduction and life-cycle simplification. |
| Reconfiguration | Time-consuming and costly; each device needs individual reconfiguration. | Quick and easy reconfiguration from a central point. |
| Communication Infrastructure | Leverages existing infrastructures but may face capacity and speed limitations. | May require upgrades to support centralization and increased data traffic. |
| Resistance to Change | Less resistance due to reliance on established technologies. | Potential resistance due to the need for adopting new technologies and modifying established processes. |
| Protection and Control | Relies on discrete, distributed devices, each responsible for specific protection and control tasks. | Centralizes protection and control, consolidating multiple functions into a single management point for enhanced coordination. |
| System Complexity | Simpler initial configuration, but maintenance and upgrades are challenging due to dispersed devices. | More complex initial configuration, but significantly easier maintenance and upgrades due to system centralization. |
| Scalability | Limited scalability: expansions require significant hardware and software modifications at multiple points. | Facilitates the addition of new functions and system expansion with upgrades at strategic points. |
| Security and Cybersecurity | Inconsistent security, relying on individual device security. | Enhanced cybersecurity through centralized authentication, authorization, auditing, and system hardening measures. |
| Factory Pre-Shipment Tests | Individual testing of each relay. | Tests are comparable to those conducted on conventional systems. |
| Commissioning Tests | Individual on-site testing of each relay with secondary injection of currents and applied voltages. | Secondary injection is performed on the merging units (MUs), similar to conventional system testing. |
| Periodic Maintenance Tests | Each relay is regularly tested throughout its operational lifespan. | Sampled value (SV) simulations and GOOSE messages enable maintenance testing without altering wiring or communication setups. |
| Test Configuration | Test equipment is configured at each stage of the relay’s lifecycle. | Test equipment configuration remains unchanged, saving time in wiring and connecting equipment. |
| Test Automation | Limited applicability in test automation. | Test process can be automated using GOOSE and SV simulation capabilities per IEC 61850 standards. |
| Secondary Injection | Conducted directly on the protection relays. | Conducted on the MUs, allowing the CPAC to disregard actual MU values during testing in simulation mode. |
| Time Synchronization | Information is distributed without facilitating synchronization. | Fault detection and analysis information is consolidated in a single location with built-in time synchronization. |
| Alarm Notification | Alarm information is dispersed across multiple devices. | Trigger information from multiple feeders is consolidated on a single alarm notification page. |
| Waveform Capture | Waveform capture is completed individually for each relay. | The same disturbance recorder function is used across all feeders, enabling waveform comparison from multiple feeders. |
| Sequence of Events | Events are listed individually for each relay. | Events from multiple feeders are presented chronologically within the CPAC system for a clear and comprehensive view. |
| SCADA System Cost | Additional investment required for SCADA system. | SCADA system advantages are provided at no additional financial cost. |
| Criteria | Centralized Architecture with Communication Redundancy | Hybrid Architecture with Numerical Protection Relays | Hybrid Architecture with Numerical Protection Relays Using Simplified Local Protection |
|---|---|---|---|
| Main feature | Fully centralized protection system with PRP-based communications redundancy using Merging Units (MU) and CPAC systems to send and receive data over independent LAN networks. | Protection system that integrates numerical protection relays capable of handling the Sampled Analogue Values (SAV) communication profile of IEC 61850-9-2, enabling them to function as merging units and provide information to the CPAC unit. | Protection system with numerical protection relays in the individual bays that communicate with the centralized CPAC unit via an Ethernet switch. This setup allows simplified local protection within the bays and advanced substation-level protection within the CPAC unit. |
| Advantages | This solution ensures the availability of functional protection in cases of device failure. It enhances engineering and maintenance efficiency through identical configurations in redundant units. It also enables a redundant unit to take over during upgrades or testing. | This solution facilitates the implementation of both local and advanced protection schemes, leveraging the advantages of both decentralized and centralized protection. It provides flexibility by integrating relays and merging units, allowing it to address diverse protection requirements. | This solution integrates the flexibility of centralized protection with the capability to add new functionalities to the substation via the centralized CPAC unit. It also enables the efficient distribution of protection across different levels. |
| Disadvantages | This solution requires a higher initial investment in redundant communication infrastructure. Additionally, the increased configuration complexity can elevate implementation and maintenance costs. | The configuration and coordination of relays and fusion units will become more complex, which may result in higher implementation and maintenance costs. | Greater coordination between the relays in the bays and the centralized CPAC unit is necessary to ensure optimal performance. A robust communication infrastructure is essential to support the increased configuration complexity. |
| Characteristic | SIPROTEC 7SX85 | MULTILIN B90 | MICOM Agile P747 | Easergy MiCOM P40 | SEL-487E | ABB SSC600 |
|---|---|---|---|---|---|---|
| Brand | SIEMENS | GE | GE | SCHEINDER ELECTRIC | SEL | ABB |
| Protection | Feeders, lines, transformers, motors, generators, capacitor banks | Low-impedance busbars | Busbars | Lines, transformers, generators, busbars | Transformers, buses, lines, feeders | Lines, transformers, busbars, generators |
| Control and Automation | Yes | Yes | Yes | Yes | Yes | Yes |
| Monitoring and Diagnostics | Advanced | Advanced | Advanced | Advanced | Advanced | Advanced |
| Communication Protocols | IEC 61850, GOOSE, Ethernet | IEC 61850, DNP3, Modbus | IEC 61850, DNP3, Modbus | IEC 61850, DNP3, Modbus | IEC 61850, DNP3, Modbus | IEC 61850, GOOSE, IEC 60870-5-104 [39], Ethernet |
| User Interface | Graphical display, specialized software | Graphical display, specialized software | Graphical display, specialized software | Graphical display, specialized software | Graphical display, specialized software | Web HMI, Graphical display, specialized software |
| Flexibility and Scalability | Modular, configurable | Modular, configurable | Modular, configurable | Modular, configurable | Modular, configurable | Modular, configurable, controls up to 30 devices |
| Firmware Updates | Yes | Yes | Yes | Yes | Yes | Yes |
| Customizable Functions | Yes | No | No | No | Yes | Yes |
| Reduction of Devices | No | No | No | No | Yes | Yes |
| AI Capabilities | No | No | No | No | No | Yes |
| Aspect | Drawbacks |
|---|---|
| Hardwiring | Copper wiring not supervised High costs of hardwiring CT/VTs Long installation and manual testing |
| Control Panels | Conventional protection relays Different relays for different functions The low-impedance busbar 87B requires additional secondary windings on CTs Lower flexibility: new function requires a new relay High costs for construction of the panels |
| Substation | High costs for the protection and control room inside the substation Separate panels for gateways and local SCADA |
| Step | Description | Tasks | Benefits |
|---|---|---|---|
| 1 | Conventional Substations—Protection and Control | Existing state with copper wiring and conventional relays. | Existing challenges with high costs, long installation, and low flexibility. |
| 2 | Digital Substation “Light” Hardwiring Replaced by Process Bus FOProtection and Control | Replace copper hardwiring with fiber optic (FO)-based IEC 61850 Process Bus (61850-9-2LE). Implement IEC 61850 GOOSE messaging for communication. | Faster deployment: Quicker installation process due to reduced physical wiring. Monitored communication: Real-time monitoring of communication channels. Cost reduction: Lower costs associated with reduced copper wiring. Interoperability: Enhanced compatibility with various devices and manufacturers. Faster deployment. Monitored communication. Cost reduction. Improved interoperability. |
| 3 | Digital Substation “FULL” Process Bus FO + Centralized PACS Protection and Control | Implement a full process bus FO infrastructure. Deploy a centralized Protection, Automation, and Control System (PACS). | Simplification: Reduced complexity with centralized control. Space savings: Less physical space required for equipment. Enhanced flexibility: Easier to add new functions through software updates. |
| 4 | Digital Substation “FULL” Process Bus FO + Centralized PACS Backups/Faults + Anomalies Recordings | Integrate backup systems and fault/anomalies recording capabilities within the centralized PACS. | Improved reliability: Enhanced fault detection and recording for better analysis. Data management: Centralized storage and management of fault and anomaly data. |
| 5 | Digital Substation “FULL” Process Bus FO + Centralized PACS AI Fault Analysis | Implement AI-based fault analysis within the centralized PACS. | Advanced diagnostics: AI algorithms provide detailed fault analysis, improving maintenance and response times. Predictive maintenance: Early detection of potential issues before they cause significant problems. |
| 6 | Digital Substation “FULL” Process Bus FO + Centralized PACS AI Fault Analysis + AI Fault Prediction | Enhance AI to include fault prediction. | Proactive maintenance: AI predicts faults before they occur, allowing for proactive maintenance. Operational efficiency: Reduced downtime and maintenance costs through predictive insights. |
| Aspect | Description |
|---|---|
| Advantages | |
| Network Management | Automatic topology detection Efficient management of multicast traffic (GOOSE, SV) Logical partitioning (slicing) to improve QoS and prioritize critical traffic fast fault recovery |
| Security and Cybersecurity | Global visibility and control Putting in place security measures that include the blocking of traffic or network segregation Integration of lightweight machine learning within programmable switches for intrusion detection Future-proofed platform for patching and cybersecurity upgrades |
| Automation and Error Reduction | Reduction in manual configuration Decrease in human errors In-band telemetry for real-time data collection and proactive maintenance |
| Unresolved Risks and Challenges | |
| Implementation Complexity | The effective coordination and management of SDN and PDP present significant challenges, requiring substantial investment in infrastructure and training |
| Critical Time Requirements | For some critical messages inside the substation, such as Type 1A GOOSE messages, the driving requirements are very strict in terms of time (3–10 ms); any such PDP integration should make sure these requirements are met without adding unacceptable latency Real-time performance in an SDN-based substation depends upon appropriate hardware: inappropriate switches or bad servers degrade operations. The loss of a GPS clock or weak time synchronization as a result of poor engineering will also make the protection systems disturbed, reducing stability and reliability |
| Security and Resilience | Although SDNs and PDPs improve security, both also introduce new attack surfaces. Consistency with rapid response without overloading the processing of traffic remains an open issue |
| Lack of Datasets | Only a few datasets that can be used to train machine learning-based security models are public, and thus, constructing generalized and effective security solutions is limited |
| Future Research Lines | |
| Standardized Frameworks | Standardized frameworks that take into account the integration of security requirements in IEC 61850 with the demand for cybersecurity in programmable networks must be developed |
| Telemetry and Data Analysis | Farther research in in-band telemetry techniques and real-time data analysis to forestall failures and attacks should be considered |
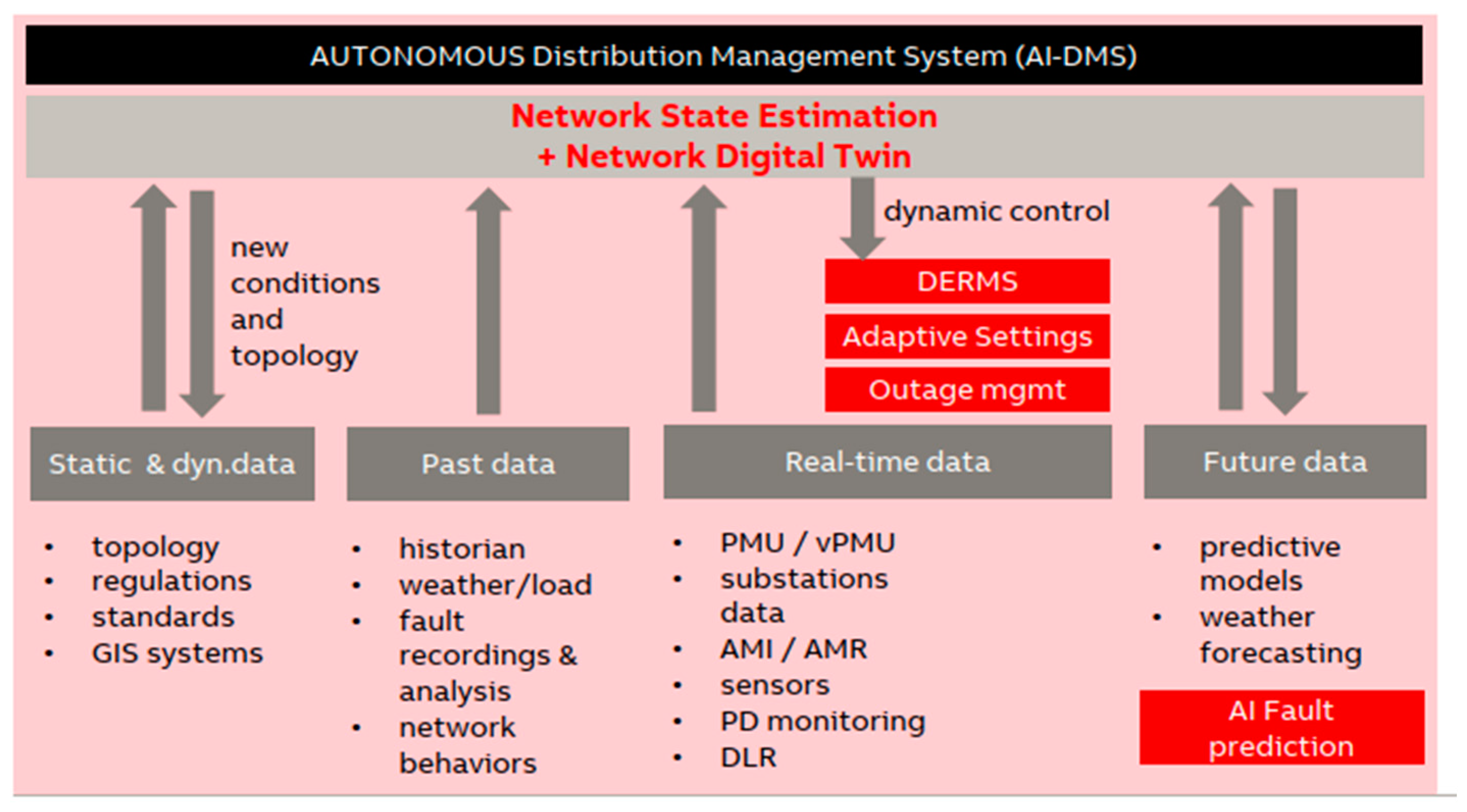
| Automated Network Management | Further investigate the aspects of the combination in the use of SDN and PDPs that will enable the complete automation of network management, including firmware updates, security patching, and incident response, autonomously |
| Advanced Cybersecurity | It should be carried out in the context of improved intrusion detection and response techniques, specifically binarized neural networks, and other forms of Machine Learning that efficiently operate on programmable devices |
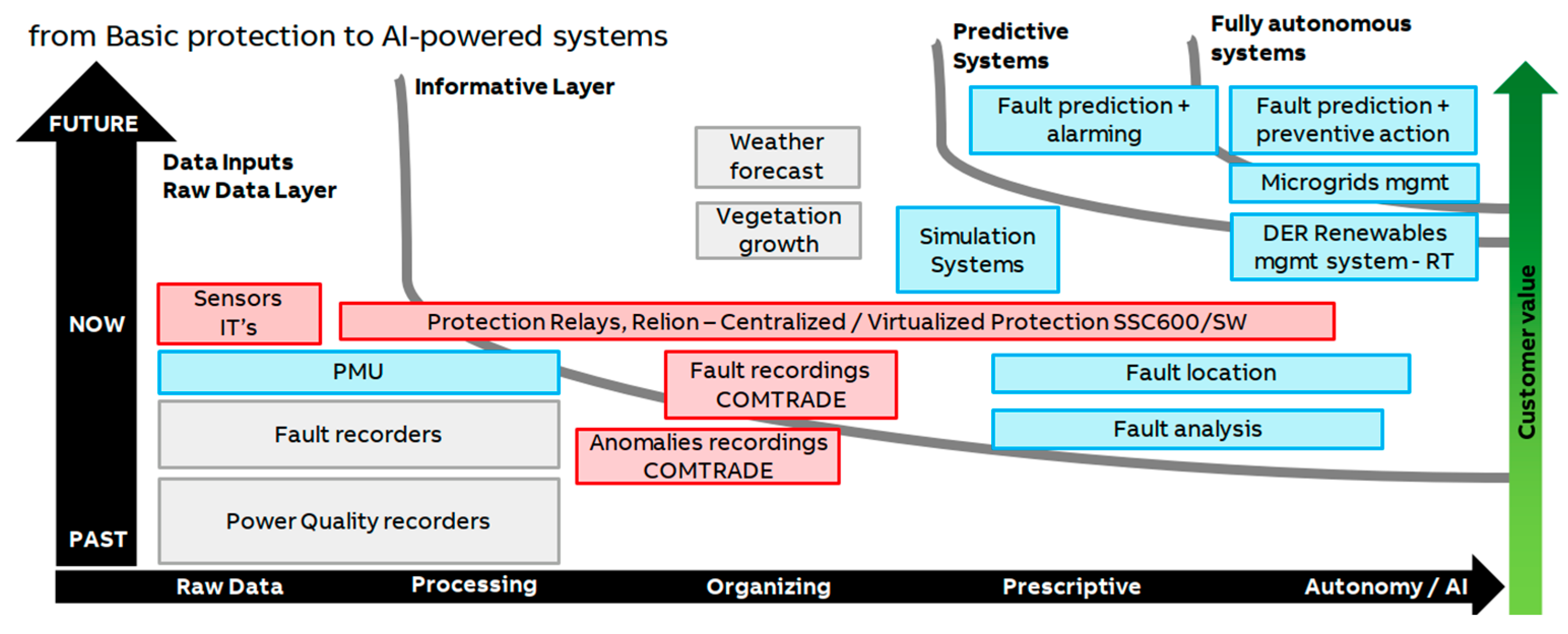
| Power Quality, Line Differential Protection Over IP and Interoperability | One major future direction of research will be connected with the increase in the sampling rate up to 14.4 kHz in order to meet EN50160 [43] in the case of power quality monitoring and to reach Official Metering Class 0.2 S accuracy. Another technical challenge is given by the deployment of line differential protection over IP-based networks [44,45]. Plug-and-play merging units are foreseen to ease interoperability and expand system flexibility while reducing the engineering efforts and commissioning time. |
| Aspect | Characteristics | Benefits |
|---|---|---|
| Remote Operation | Remote monitoring and control Integration with automation systems | Reduces risk by minimizing personnel exposure to electrical hazards Increases efficiency through quick response without physical intervention |
| Non-Traditional Instrument Transformers | Rogowski current sensors and voltage sensors | Prevents hazards such as high voltages in open CTs and ferro-resonance Easier, safer installation and maintenance |
| Arc Flash Sensors [46] | Rapid detection of arcs via light and heat | Protects personnel and equipment by quickly extinguishing arcs Enhances system reliability and availability through reduced damage |
| Infrastructure | Description |
|---|---|
| Data and Communication Model | IEC 61850: It is an international standard that defines data models and communication services for substation automation, ensuring seamless interoperability among devices from different manufacturers. |
| Software Virtualization | Software and hardware decoupling: It allows applications to run in virtual environments independent of physical hardware. Virtual Machines (VMs) and containers: Applications can run in VMs or containers, virtualizing different operating system layers. |
| Resource Allocation and Management | CPU and memory: Exclusive CPU core and memory bandwidth allocation policies for critical applications. Cache and memory partitioning: Minimizes interference between applications through cache partitioning and the exclusive reservation of memory bandwidth. |
| System Interoperability and Efficiency | Avoiding the duplication of inherited relay logic: Simplify control logic and efficiently distribute functionality. Adaptability and scalability: Facilitates integration of new technologies and adaptation to changes in the electrical grid. |
| Safety and Reliability | Real-time protection: Meet stringent real-time data processing requirements. High availability: Ensures continuous availability of critical applications, even during hardware or software failures. |
| Communication Network | Virtual and physical networks: The deployment of network virtualization technologies facilitates the interconnection of virtualized applications with the underlying physical network infrastructure. IEC 61850 standard: It defines communication via Ethernet, thereby facilitating data exchange and control between substation devices. |
| Deployment And Maintenance | Flexible and rapid deployment: The implementation of new applications and updates is conducted flexibly, thereby reducing the time and costs associated with maintenance. Testing and validation: Comprehensive laboratory testing and field validation are conducted to guarantee compliance with operational requirements before deployment. |
| Aspect | Traditional Protection Systems | CPAC Systems (e.g., SSC600) | VPAC Systems |
|---|---|---|---|
| Hardware Failures | High risk due to numerous individual relays and aging infrastructure. | Centralized hardware reduces the number of components, but central failure risk exists. | Virtualization reduces hardware dependency but introduces potential performance overhead. |
| Complexity and Misconfiguration | Complex systems with many devices lead to a higher risk of misconfiguration. | A centralized system simplifies configuration, but a misconfiguration can impact the entire system. | Complexity in managing virtual environments; misconfigurations can affect multiple virtual instances. |
| Redundancy | Often lacks sufficient redundancy; single failures can compromise protection. | Dual redundancy with hot–hot modes is recommended to ensure continuous operation. | Redundancy can be implemented through virtual machines but relies on robust network infrastructure. |
| Response Time | Slower response times, especially in detecting and isolating faults. | Faster response due to centralized control and real-time processing. | Performance depends on the virtualization layer; careful management is needed to avoid delays. |
| Interoperability | Limited interoperability between different vendors’ devices. | Designed for interoperability, especially with compliance with standards like IEC 61850. | High interoperability due to the use of open standards and vendor-independent hardware. |
| Security | Basic security; often reliant on physical security and legacy protocols. | Advanced security with encryption, authentication, and compliance with IEC 62443 [52]. | Comprehensive security measures are needed, including virtual environment protection. |
| Network Dependencies | Less reliant on complex networks; simpler communication protocols. | Highly dependent on robust network infrastructure; requires redundancy in communication paths. | Strong dependency on network reliability; latency and bandwidth can impact performance. |
| Software Vulnerabilities | Limited software components reduce the risk, but a lack of updates can expose vulnerabilities. | Regular software updates and rigorous testing are essential to prevent failures. | Increased risk due to the complexity of the virtual environment; robust management of the software lifecycle is critical. |
| Maintenance and Testing | Maintenance-intensive; testing can be cumbersome due to multiple devices. | Simplified maintenance with fewer devices; regular testing in simulated environments is crucial. | Virtualized testing environments allow for extensive testing but require careful management. |
| Scalability and Flexibility | Limited scalability; difficult to adapt to new requirements. | Highly scalable and flexible; easy to reconfigure and expand. | Maximum scalability means it can quickly adapt to new demands and integrate new applications. |
| Feature | SSC600 | SSC600 SW |
|---|---|---|
| Type of Protection | Centralized | Virtualized |
| Function Integration | Protection, control, monitoring, and communication | Virtualized protection and control |
| Interoperability | Compliance with IEC 61850 | Compliance with IEC 61850 |
| Cybersecurity | Advanced measures aligned with IEC 62443 and NERC CIP | Advanced measures aligned with IEC 62443 and NERC CIP |
| Flexibility | More rigid structure due to dedicated hardware | High flexibility and scalability |
| Hardware | Requires multiple physical devices | Reduces the need for physical hardware |
| Costs | Potentially higher due to additional hardware | Potentially lower due to reduced hardware |
| Implementation and Updates | Requires hardware installation and updates | Faster and more efficient implementation and updates |
| Consideration Area | Description | Additional Details | |
|---|---|---|---|
| Compliance | Ensure compliance with laws, regulations, and security standards; obtain necessary certifications and audits. | Compliance with standards like IEC 62443 and NERC CIP ensures cybersecurity and operational consistency across all substation systems. | |
| Availability and Reliability | Design with high robustness, including redundancy at all levels to ensure continuous operation. | Implement redundancy for station and process bus traffic; network recovery methods (IEC 61850, IEC 62439-3) like PRP and HSR with zero recovery time. | |
| Real-Time Performance | Challenge: Historically, virtualization technologies have struggled to deliver the real-time performance required for critical applications. Current Shift: New solutions are emerging that promise improved real-time performance. | Handling real-time operations is critical in VPAC applications, which require immediate responses. Current improvements in hardware and software are addressing these limitations. New hardware/software solutions address historical performance issues. Immediate responses are critical for handling SMV and GOOSE traffic. | |
| Software Development Lifecycle (SDLC) | Follow SDLC best practices, excluding unnecessary services and componentsm to minimize the attack surface and performance issues. | Integrating security into every stage of the software development lifecycle helps reduce vulnerabilities and ensure performance optimization. | |
| Integrated Security | Implement strong encryption, authentication protocols, and protection against internal and external threats. | Ensure security across the virtual infrastructure, including hypervisors, management platforms, and data in transit and at rest. | |
| Interoperability | Adhere to open standards and communication protocols to interact with diverse devices and systems. | VPAC systems should work seamlessly across different manufacturers, especially under IEC 61850-9-2 LE for SV communication. | |
| System Monitoring and Auditability | Implement continuous monitoring and auditing to detect and respond to anomalies, ensuring system integrity. | Monitoring is critical for maintaining stability, especially in real-time VPAC systems. Implement logs for real-time event detection and response. | |
| Data Integrity and Isolation | Protection: Ensure that data in a virtualized environment are properly isolated and protected against unauthorized access through network segmentation and data encryption in transit and at rest. | Network Segmentation: Divide the network into isolated segments to enhance security. Encryption: Protect data both in transit and at rest to prevent unauthorized access. | |
| Hypervisor Types and Solutions (Hardware-Based Virtualization) | Type-1 Hypervisors: Run directly on the hardware, providing more predictable performance. Type-2 Hypervisors: Run on a host operating system, which can introduce delays and security issues. Kernel-Based Virtualization (KVM): Enables live migration and resource scheduling, though it may not be ideal for critical traffic due to switching times. OS-Level Virtualization: Offers low resource overhead and additional services but provides less isolation. | Type-1: Lower overhead, higher performance. Ideal for production environments. Type-2: Easier to implement but less efficient for critical applications. KVM: Suitable for diverse workloads, but live migration requires caution. OS-Level: Highly efficient but less isolated, making it suitable for less critical applications. | |
| Hardware Acceleration | Usage: Hardware acceleration is preferred for PAC virtualization because it provides guaranteed service for SMV and GOOSE traffic. Type-1 Hypervisors: Utilize hardware acceleration through the host BIOS. Type-2 Hypervisors: Dependent on the host operating system for acceleration, potentially resorting to software emulation if native support is unavailable. | Advantages: Improves performance and efficiency for intensive tasks. Disadvantages: Requires compatible hardware and proper configurations. | |
| Network Virtualization | Real-time traffic handling: Crucial for VPAC applications that rely on SMV and GOOSE data. Technologies: NIC Virtualization—Utilizes features like guaranteed bandwidth for SMV traffic. SR-IOV—PCI Express extension for virtualizing NIC resources. Potential issues: Risk of broadcast storms and internal latencies. | NIC Virtualization: Allows reservation of specific bandwidth for critical traffic. SR-IOV: Enhances NIC resource efficiency but requires hardware support. Latencies: Minimizing latency and managing network load is essential for performance. | |
| Access Control Management | Establish robust access control to restrict system access to authorized personnel. | Utilize Role-Based Access Control (RBAC) with LDAP integration. Automation of access rights management can reduce unauthorized access risks. | |
| Backup and Disaster Recovery | Develop and maintain comprehensive backup and disaster recovery plans for rapid system recovery. | Ensures rapid system recovery during failures. The regular testing of backup systems is necessary to validate the reliability of disaster recovery protocols. | |
| Time Synchronization | Precision: Ethernet can achieve software-based synchronization with 1 ms precision. Advanced Protocols: IEEE 1588v2 and IEC 61850-9-3 allow for 1 μs precision, necessary for IEC 61850-9-2 process buses. Alternatives: In the absence of GPS, the Best Master Clock algorithm can be used for synchronization. | IEEE 1588v2: Provides high precision for critical applications requiring exact synchronization. GPS: Offers precise synchronization but depends on signal availability. SNTP: Less precise, suitable only for less demanding systems. | |
| Redundancy and High Availability | Importance: Ensuring high availability and reliability in the communication network is essential. Standards: IEC 61850 and IEC 62439-3 define network recovery methods with zero recovery time, such as PRP and HSR. Implementation: Redundancy is preferred for station and process bus traffic, while other applications may use virtual redundancy. | PRP and HSR: Guarantee recovery times without packet loss in case of network failures. Virtual Redundancy: Can be less costly but is less robust than physical redundancy. Monitoring: Crucial for maintaining network stability and preventing failures. | |
| Virtual Resource Optimization | Management: Efficiently managing virtual resources is crucial to avoid overload and ensure optimal system performance. Key Areas: Proper configuration of virtual machines, virtual networks, and storage. | Configuration: Adjust virtual resources to balance load and avoid bottlenecks. Monitoring: Track resource usage to make proactive adjustments | |
| Virtual Infrastructure Security | Approach: Ensure that the software and the underlying virtual infrastructure, including hypervisors and management platforms, have specific security measures for virtual environments. | Security Measures: Implement regular patches and updates and protect virtualization management platforms. Isolation: Ensure virtual resources are protected against unauthorized access. | |
| Scalability and Flexibility | Requirement: VPAC systems must be scalable and flexible, allowing for the easy addition of new nodes and virtual resources without interrupting system operation. | Scalability: Facilitate system expansion to support growth in demand. Flexibility: Adapt the system to changing needs and infrastructure. | |
| Hardware Material List | Maintain an inventory of all hardware components to ensure quality and compatibility. | Hardware selection must comply with IEC 61850 and IEEE 1613 standards for reliability in harsh substation environments. | |
| Hardware | Flexibility: Virtualization aims to provide flexibility in hardware selection. Environmental Requirements: Comply with environmental standards to ensure reliability in electrical substations. Standards: Requirements specified in IEC 61850 and IEEE 1613 for electromagnetic compatibility and hardware reliability. | Regulatory Compliance: Ensures hardware suitability for industrial environments. Robustness: Hardware must be resilient to operate in substation conditions. Flexibility: Allows adaptation to different configurations and needs. | |
| Software Behaviour List | Provide detailed software behavior and connection descriptions to manage system interactions effectively. | Mapping the interactions between virtual and physical devices helps avoid conflicts and ensures proper system operation. | |
| Standard/Recommendation | Description | Application |
|---|---|---|
| IEEE 1588 [27] | Standard for a precision clock synchronization protocol for networked measurement and control systems | Defines the Precision Time Protocol (PTP) for clock synchronization in networked measurement and control systems. |
| IEC 61850-9-3:2016 [59] | Communication networks and systems for power utility automation | Specifies time accuracy and synchronization requirements in substation automation networks. |
| IEC 61588 [70] | Precision clock synchronization protocol for networked measurement and control systems | Equivalent to IEEE 1588, applicable in industrial automation and control networks. |
| NIST SP 800-82 [71] | Guide to Industrial Control System (ICS) Security | Provides guidelines for the security of industrial control systems, including aspects of time synchronization. |
| IEEE C37.238 [72] | Standard Profile for Use of IEEE 1588 Precision Time in Power System Applications | Defines the profile for using IEEE 1588 in power system applications, ensuring precise synchronization in electrical environments. |
| Aspect | Descriptions |
|---|---|
| Required Precision | Network precision must be better than ±1 µs before commissioning. |
| GMC Precision | Each Grandmaster Clock (GMC) should have an inaccuracy of less than 250 ns and maintain this precision for at least 5 s after losing the reference signal. |
| Current Transducer Requirements | Transducers should have an accuracy error of less than 50 ns and a drift of less than 15 µs. Once synchronized, they must maintain 1 µs precision within a 5 s window. |
| MU/IED Precision [58]. | Measurement units (MU) and Intelligent Electronic Devices (IEDs) must have clocks synchronized to a minimum precision of 1 µs, in accordance with T5 class of IEC 61850-5. |
| Network Time Inaccuracy | Confirm that network time inaccuracy is less than ±1 µs. |
| GMC Testing | Verify the precision of the GMC and its ability to maintain accuracy after losing the reference signal. |
| Slave Clock Verification | Confirm the accuracy of slave clocks using a 1 PPS output and measure the PTP fields generated by each GMC. |
| Current Transducer Testing | Confirm the correctness of the PTP message correction field and verify the accuracy of current transducers under different traffic conditions. |
| Network Configuration and Topology | Verify that all network components are configured correctly and that all clocks are synchronized to the same time domain. |
| Synchronization Class | Precision (μs) | Sync. Error | Application |
|---|---|---|---|
| TL | >10,000 | Low precision | General synchronization for various low-precision applications. |
| T0 | 10,000 | 10 ms | Event stamping with 10 ms precision. |
| T1 | 1000 | 1 ms | Event stamping with 1 ms precision. |
| T2 | 100 | 100 μs | Zero-crossing tagging and data for distributed synchronization checks. Waveform-based switching tags. |
| T3 | 25 | 25 μs | Various applications. |
| T4 | 4 | 4 μs | Sample tagging or synchronized sampling. |
| T5 | 1 | 1 μs | High-precision sample tagging or highly synchronized sampling. |
| Type | Description | Performance Class | Requirement Description | Transfer Time (ms) | Typical Interface (IF) |
|---|---|---|---|---|---|
| 1A “Trip” | The trip message is the most critical fast message in the substation, with more stringent requirements than other fast messages. Also applicable to interlocking, intertrips, and logical discrimination between protection functions. | P1 | Total transmission time must be less than a quarter cycle (5 ms for 50 Hz, 4 ms for 60 Hz). | TT6: ≤3 ms | 3, 5, 8 |
| 4Raw Data (“Samples”) | Includes output data from digitizer transducers and digital instruments, consisting of continuous streams of synchronized samples from each IED, interleaved with data from other IEDs. | P7a | Acceptable delay for protection functions using these samples (Equivalent to P1). | TT6: ≤3 ms | 4, 8 |
| P8b | Acceptable delay for other functions using these samples (Equivalent to P2). | TT5: ≤10 ms | 2, 4, 8 |
| Category | Requirement | Description |
|---|---|---|
| Hardware | Duplication of Critical Components | Essential components like servers, power supplies, networks, and storage units must be duplicated to prevent a single point of failure. |
| Network Devices | Routers, switches, and cables should be configured redundantly to ensure continuous connectivity. | |
| Load Balancing | Workload distribution among active components to avoid overloading a single component. | |
| Automatic Failover | Automatic mechanisms to switch to a backup component in case of primary component failure. | |
| Physical Isolation | Redundant components should be in different physical locations to protect against local events affecting both systems. | |
| Software | Application Redundancy | Critical applications should run on redundant instances, on the same server (virtualization) or different servers. |
| State and Data Management | Synchronize data and maintain state consistency between active and backup systems. | |
| Failover Mechanisms | Enable seamless and automatic transition between the primary and backup systems in case of failure. | |
| Operational Procedures | Testing and Validation | Perform regular failover tests to ensure that the backup system operates correctly. |
| Seamless Updates | Allow updates and maintenance without interrupting service, using appropriate update strategies. | |
| Patching and Maintenance | Apply patches and conduct maintenance without affecting system availability. | |
| Monitoring and Alerts | Implement active monitoring with real-time alerts for failures and anomalous conditions. | |
| Management and Procedures | Documentation and Procedures | Maintain comprehensive documentation of the redundant system architecture, failover procedures, and recovery plans. |
| Personnel Training | Train personnel in the redundant system’s operation, maintenance, and recovery, and conduct emergency drills. |
| Standard/Regulation | Descriptions |
|---|---|
| IEC 61850 [77] | Standard for electrical network automation, including redundancy in communication and protection systems to ensure high availability. |
| IEC 61850-3 [78] | General hardware requirements for devices in electrical substations. |
| IEC 61850-5 [4] | Performance and functionality requirements for automation and control devices in substations. |
| IEC 61850-9-2 [79] | Standard for the transmission of sampled values and synchronization data over Ethernet. |
| IEC 61850-90-4 [80] | Part of IEC 61850 addresses redundancy in network and communication systems. |
| IEC 61850-90-2 [81] | Standard for integrating communication systems in substation automation, including redundancy in message communication. |
| IEC 61508 [82] | Standard for the functional safety of electrical, electronic, and programmable systems, including redundancy requirements to ensure safety systems. |
| IEC 62439 [83] | Standard covering protocols for redundancy in industrial networks, including PRP and HSR. |
| IEC 62439-3 [84] | Part of IEC 62439 specifies PRP and HSR to ensure network availability. |
| IEC 62351 [85] | Security standard for communications in industrial automation and control systems. |
| IEC 60870-5-7 [86] | Security extensions for IEC 60870-5-104. |
| IEC 60870-5-104 [39] | Standard for remote control of electrical power systems over a network protocol. |
| IEEE 1588 (PTP) [27] | Standard for time synchronization over Ethernet networks, may involve redundant mechanisms to ensure time precision and availability. |
| NERC CIP [87] | Critical Infrastructure Protection standards, including redundancy and security requirements for power grid control and protection systems. |
| DNP SA V5/6 [88] | Standard for security and authentication in distribution automation and control networks. |
| ISO 27001 [89] | Standard for information security management, may include measures for redundancy in handling critical data and systems. |
| TIA/EIA-942 [90] | Standard for data center design, covering redundancy in IT infrastructure to ensure high availability. |
| System | Description | Advantages | Disadvantages | Application |
|---|---|---|---|---|
| System 1 | Two CPAC units to eliminate loss of protection if one CPAC fails. Only one Merging Unit (MU) per protected circuit. | High availability of protection in case one CPAC unit fails. | If the MU fails, the specific circuit will be unprotected. | Users rely on a single multifunction relay per circuit in a conventional setup. |
| System 2 | One CPAC unit and a multifunction relay or Intelligent Merging Unit (IMU) per circuit can act as an MU. | The IMU provides protection if the CPAC unit fails. | If the IMU fails, the circuit where it was used will be unprotected. | Users with multifunction relays capable of acting as merging units are looking to add new functions or backup protection. |
| System 3 | Two MUs per protected circuit to eliminate a single point of failure. | No system failure will compromise protection. | The number of circuits protected by the CPAC unit is halved. | Clients aim to avoid a single point of failure and provide all protection and control functions at the CPAC level. |
| System 4 | Two CPAC units for the entire system, one MU and one IMU per protected circuit. | High reliability: the failure of both CPACs and an MU or IMU leaves no circuit unprotected. | The system’s complexity increases due to the integration of multiple components, necessitating rigorous management and expertise to ensure seamless operation and coordination. | Users seeking the highest levels of reliability. |
| System 5 | One CPAC unit for the entire system, one MU and one IMU per protected circuit. | Avoids a single point of failure by adding an IMU; the system is protected even if the CPAC, MU, or IMU fails. | The number of circuits protected by the CPAC unit is halved. | Users with microprocessor relays that can act as merging units and wish to add additional functions or backup protection without a single point of failure. |
| Method | Advantages | Disadvantages | Weaknesses | Strengths | Opportunities | Threats |
|---|---|---|---|---|---|---|
| N | Low initial cost. | No failure tolerance. | High probability of total service disruption. | Simplicity in implementation. | Ideal for non-critical systems. | High risk of significant downtime in case of failure. |
| N + 1 | Improves resilience against single failures. | Limited protection against multiple failures. | Does not ensure high availability. | Increases availability. | Suitable for critical systems with tolerance for one failure. | Risk if failures are multiple or simultaneous. |
| 2N | High availability. | Expensive and complex to implement and maintain. | High duplication cost. | High resilience. | Reduces downtime risk significantly in critical applications. | Complexity in management and high operational costs. |
| 2N + 1 | Maximum availability and resilience. | Very high cost and extreme complexity in design and maintenance. | Complex operation and high maintenance costs. | Protects against multiple failures. | Ideal for mission-critical environments. | Management complexity and high operational costs. |
| Challenge | Proposed Strategy |
|---|---|
| Proprietary Operating Systems | Implement a multi-layered security framework to enhance protection. |
| Heterogeneous Network Technologies | Integrate cybersecurity measures with legacy systems while upgrading them. |
| VM Isolation | Employ advanced isolation techniques and conduct regular security audits. |
| Vulnerabilities in Automation Systems | Ensure systems are modular, scalable, and compliant with established cybersecurity standards. |
| Threats in Virtualized Environments | Utilize cutting-edge security measures to prevent and detect hyperjacking and similar threats. |
| Standard | Description | Application |
|---|---|---|
| IEC 61850 [94] | Communication in electric substation automation systems. | Facilitates information exchange between devices in substations. |
| IEEE 1613 [104] | Environmental and testing requirements for communication network devices in electric power substations. | Ensures the reliability of communication devices under adverse environmental conditions. |
| IEC 62439-3 [23] | Highly available and redundant network protocols, such as PRP and HSR, ensure continuous communication. | Ensures continuous and redundant communication in substation networks. |
| IEC 62443 [94] | Cybersecurity standards for Industrial Automation and Control Systems (IACS). | Comprehensive protection of industrial automation and control systems against cyber threats. |
| NERC CIP [102] | Critical Infrastructure Protection standards in North America. | Protects energy control systems and critical data in electric infrastructure. |
| IEC 62351 [25,105] | Cybersecurity for energy management systems and information exchange. | Protects data and communications in energy management systems. |
| IEEE 1686 [24] | Cybersecurity standard for Intelligent Electronic Devices (IEDs). | Defines cybersecurity requirements for IEDs in automation systems. |
| IEEE 1547.3 [93,106] | Cybersecurity for distributed energy resources (DERs) interconnected with electric power systems. | Ensures secure integration of DERs with electric power systems. |
| IEEE C37.240-2014 [92] | Cybersecurity requirements for automation, protection, and control systems. | Implements security measures in automation and protection systems. |
| NIST Cybersecurity Framework [107] | Framework for improving cybersecurity in organizations (Versions 1.1 and 2.0). | Provides guidelines for enhancing organizational cybersecurity. |
| NIST SP 800-53 Rev.5 [108] | Security and privacy controls for organizations and information systems. | Establishes security and privacy controls for information systems. |
| NIST SP 800-82 Rev. 3 [109] | Guide to Industrial Control System (ICS) security. | Enhances security in industrial control systems. |
| NIST SP 800-63 [108] | Guidelines on digital identity and authentication. | Defines policies and procedures for digital identity and authentication. |
| TPM 2.0 [110] | Trusted Platform Module specification for cybersecurity evaluation. | Ensures hardware integrity based on TPM standards. |
| CISA Zero Trust [98] | The maturity model for cybersecurity is based on the Zero Trust principle. | Implements a cybersecurity model that assumes no actor is inherently trusted. |
| IEC 61850-3 [40] | Mandatory compliance for systems in substations, covering environmental and security criteria. | Ensures environmental resilience and security in substation equipment. |
| PWI TR 61850-90-20 [25] | Guidelines for redundancy systems in network and communication for utility automation. | Implements redundancy systems in utility network automation. |
| IEC 62351:2023 SER [105] | Security for data and communications in energy management systems. | Protects the integrity and confidentiality of data in energy management systems. |
| Component | Security Specification | Implementation Strategy |
|---|---|---|
| Server Hardware | Ensure the physical and logical integrity and security of servers. | Subject servers to additional cybersecurity certifications and compliance with safety standards. |
| Networks | Implement network segmentation and access controls. | Use firewalls, VLANs, and access control lists to enforce segmentation and limit unauthorized access. |
| Configuration and Testing Tools | Utilize secure tools that do not introduce vulnerabilities. | Deploy secure configuration and testing tools that are validated and regularly updated. |
| Support Systems | Comply with best practices in monitoring and management systems. | Implement continuous monitoring and automated alerts to maintain system integrity. |
| Substation Software | Protect through regular patching and updates. | Establish a rigorous patch management process to ensure timely updates and vulnerability mitigation. |
| Solution Management | Implement security measures throughout the solution lifecycle. | Integrate security protocols from the design phase through to decommissioning, ensuring consistent security. |
| Risk Assessment and Management | Identify and mitigate cyber risks. | Conduct regular risk assessments and implement risk mitigation strategies tailored to the specific threats. |
| Security Requirements for System Components | Ensure all components are protected against threats. | Harden all components, including hardware, software, and networks, against known vulnerabilities. |
| Operational Security Measures | Protect the continuous and secure operation of the system. | Implement real-time monitoring, incident response plans, and failover mechanisms to ensure resilience. |
| Hardware Protection | Compliance with additional cybersecurity certifications and safety standards. | Enforce strict compliance with IEC 62443 and related physical and logical security standards. |
| Communication Protection | Implement network segmentation and access controls. | Use secure communication protocols (e.g., TLS, VPNs) and robust authentication mechanisms to protect data in transit. |
| Software Integrity | Ensure software integrity through regular patches and updates. | Automate software updates and patching while validating changes against cybersecurity standards. |
| Access Management | Define roles and authentication systems for software access. | Implement Role-Based Access Control (RBAC) integrated with enterprise LDAP for streamlined access management. |
| Protocol/Tool | Description |
|---|---|
| GOOSE | Facilitates communication between protection and control devices in substations. |
| SV (sampled values) | Transmits voltage and current readings within substations. |
| PRP (Parallel Redundancy Protocol) | Ensures uninterrupted communication by providing network redundancy. |
| TPM (Trusted Platform Module) | Secures the integrity of devices through hardware-based security. |
| Aspect | Strengths | Weaknesses | Opportunities | Threats |
|---|---|---|---|---|
| Efficiency and Cost | CPAC systems streamline operations and reduce costs. | Transition involves managing significant technical and operational changes. | Exploring SaaS and IaaS models can drive innovation and flexibility. | Technological advancements may outpace current systems. |
| Safety and Flexibility | Improved safety through non-traditional sensors. | Virtualized systems may experience performance issues and increased latency. | Leveraging big data and AI/ML for predictive analytics can enhance fault prediction and maintenance. | Increased reliance in cloud-based solutions may create single points of failure. |
| Redundancy | Advanced redundancy techniques like PRP enhance resilience and availability. | Ensuring full interoperability between different manufacturers’ IEDs remains challenging. | Developing integrated systems that combine physical and digital elements can enhance reliability. | Cybersecurity threats such as malware and ransomware pose risks to virtualized systems. |
| Technology Integration | Adoption of modern technologies like AI and ML improves predictive capabilities. | Dependency on cloud and network infrastructure requires robust management. | Partnerships and pilot programs can help identify optimal solutions and best practices. | System integration with legacy technologies may lead to compatibility issues. |
| Data Management | AI/ML tools like ABB’s ADAM offer high-precision predictive analytics for better maintenance. | Complexity of managing large amounts of data and ensuring data integrity. | Utilizing analytics and big data can improve operational efficiency and reduce downtime. | Regulatory and compliance challenges may arise with evolving standards and requirements. |
| Action | Goal |
|---|---|
| Strengthening Cybersecurity Measures | Implement advanced protocols and conduct regular assessments to protect against cyber threats. |
| Improving Interoperability | Adopt open standards for seamless integration between systems and manufacturers. |
| Enhancing Real-Time Performance | Invest in hardware acceleration and optimize virtualization techniques to reduce latency. |
| Expanding Predictive Analytics | Utilize AI/ML tools and big data for predictive maintenance and enhanced fault detection. |
| Ensuring Physical and Digital Integration | Develop strategies for coordinating physical IEDs with digital systems and establish robust backups. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rubio, S.; Bogarra, S.; Nunes, M.; Gomez, X. Smart Grid Protection, Automation and Control: Challenges and Opportunities. Appl. Sci. 2025, 15, 3186. https://doi.org/10.3390/app15063186
Rubio S, Bogarra S, Nunes M, Gomez X. Smart Grid Protection, Automation and Control: Challenges and Opportunities. Applied Sciences. 2025; 15(6):3186. https://doi.org/10.3390/app15063186
Chicago/Turabian StyleRubio, Sergio, Santiago Bogarra, Marco Nunes, and Xavier Gomez. 2025. "Smart Grid Protection, Automation and Control: Challenges and Opportunities" Applied Sciences 15, no. 6: 3186. https://doi.org/10.3390/app15063186
APA StyleRubio, S., Bogarra, S., Nunes, M., & Gomez, X. (2025). Smart Grid Protection, Automation and Control: Challenges and Opportunities. Applied Sciences, 15(6), 3186. https://doi.org/10.3390/app15063186