Challenge–Response Pair Mechanisms and Multi-Factor Authentication Schemes to Protect Private Keys
Abstract
Featured Application
Abstract
1. Introduction
- In Section 2, the paper describes secure MFA schemes that are easy to use, combined with methods to generate private keys that truly protect users’ privacy. We describe a challenge–response pair (CRP) mechanism that is zero-knowledge, with N authentication factors such as tokens, biometry, and blockchain-based virtual tokens. During normal operations, the terminal device uses all factors of authentication to retrieve the private keys Sk and sign a document or a financial transaction.
- In Section 3, we suggest protocols based on a scheme in which the private keys are generated and kept secret by the user, while a service entity, a Keystore corporation, can authenticate the user, and transmit the public keys to the cloud, or a certificate authority (CA). The standardized LWE post-quantum cryptographic CRYSTALS Dilithium is suggested in the implementation of this last feature.
- In Section 4, we present the experimental work, the generation of reference tables from three important factors of authentication: PUF-based physical tokens, template-less biometry, and blockchain-based virtual tokens.
2. Description of the Protocol Protecting Private Keys with MFA
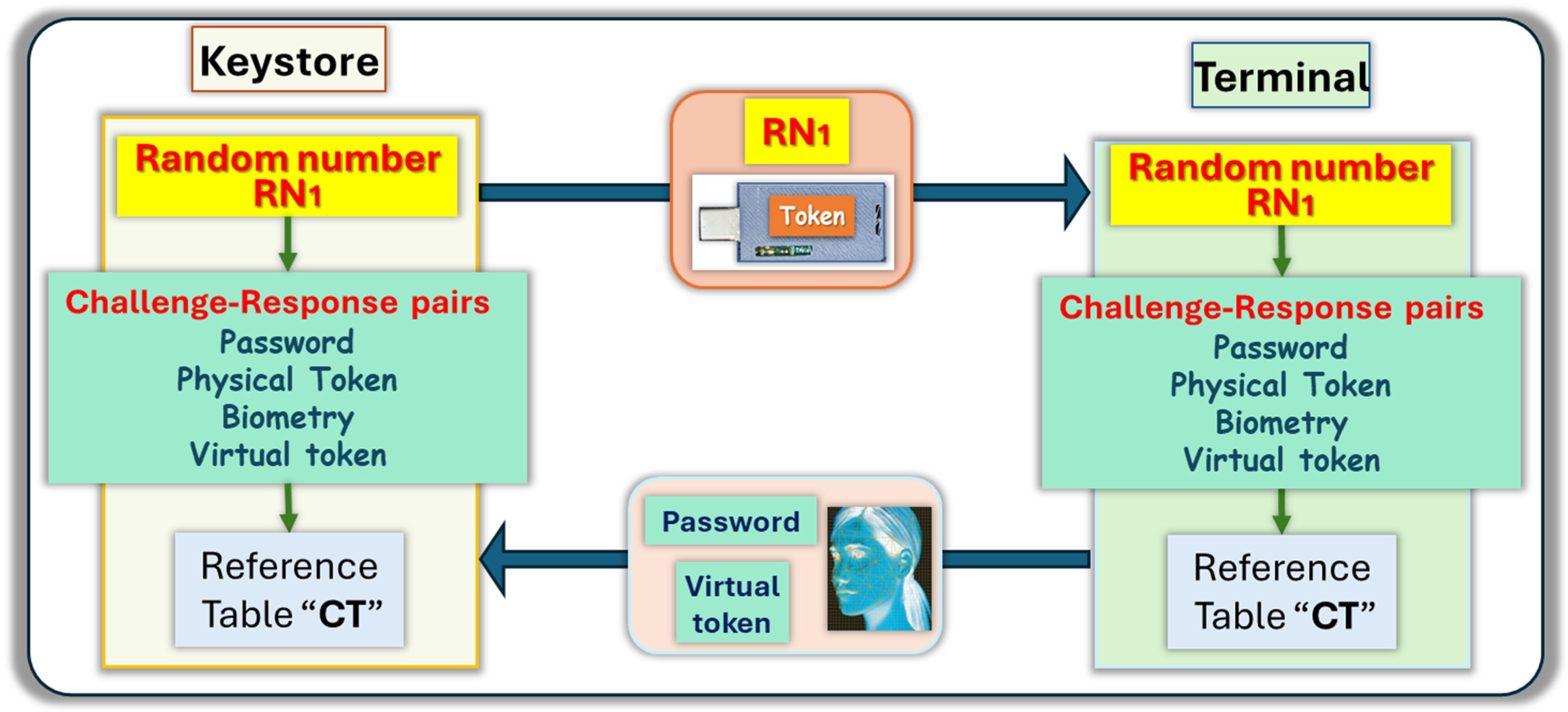
2.1. Factors of Authentication for the MFA
2.2. Description of the Enrollment Cycle
- Let be the state contained at each position (, ) of the table CT-T generated from the physical token.
- Let be the state contained at each position (, ) of the table CT-bio generated from the biometric scheme.
- Let be the state contained at each position (, ) of the table CT-VT generated from the biometric scheme.
- Let be the state contained at each position (, ) of the resulting table CT computed from CT-T, CT-Bio, and CT-VT. They are computed as follows:
- ○
- If all , , and consist only of “0” or “1” states then:
- ○
- Otherwise:
- ○
- If all regardless of k are states “0” or “1”, then:
- ○
- Otherwise:
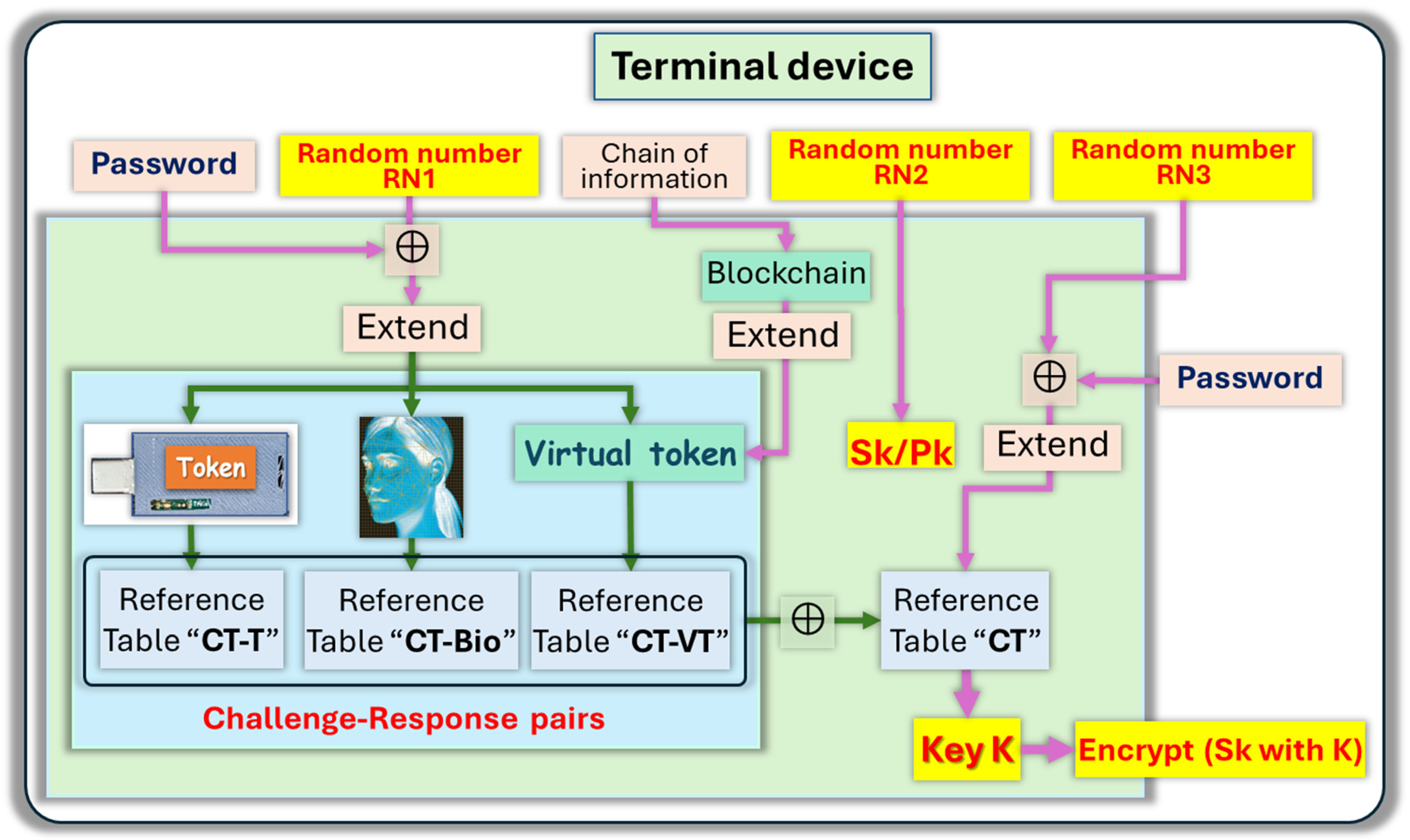
2.3. Generation of Ephemeral Keys
2.4. Role of the Keystore
3. Description of a Protocol for PKI Enhancing Privacy with MFA
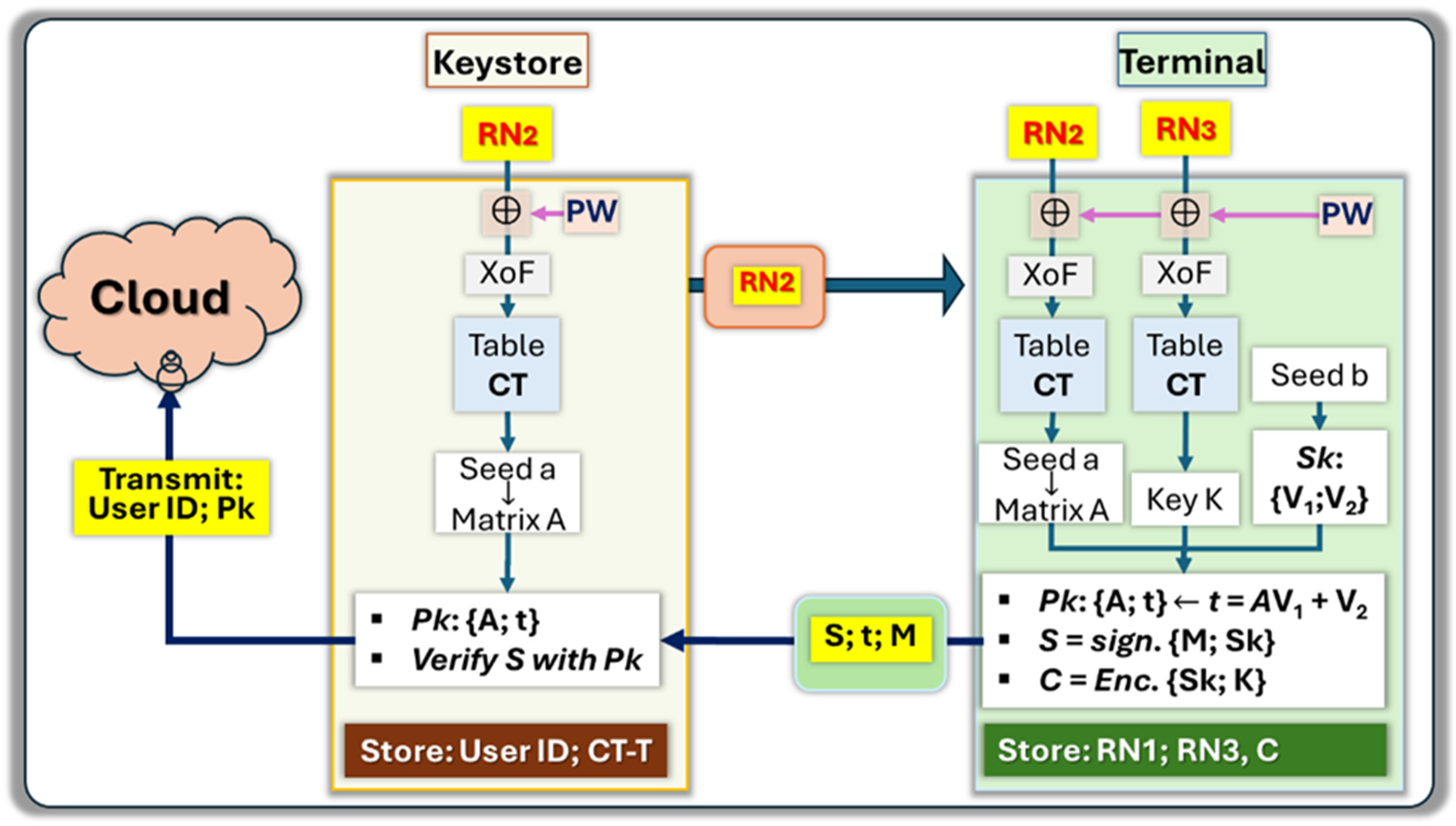
3.1. Enrollment Cycle with Private Key Generation
- Initial operations driven by the Keystore corporation KSC:
- ○
- Generation of the reference table CT:
- ❖
- RN1’ RN1⊕PW: with random number RN1, and password PW
- ❖
- challenges RN1’: with XoF function.
- ❖
- With CRP mechanisms, they generate 4 reference tables
- (1)
- CT-bio challenges: CRP from the facial image
- (2)
- CT-T challenges: CRP from a token
- (3)
- CT-VT challenges: CRP from a virtual token
- (4)
- CT(CT-bio)⊕(CT-T)⊕(CT-VT): concatenation
- ○
- Generation of Seed-a:
- ❖
- RN2’ RN2⊕PW: with random number RN2, and password PW
- ❖
- challenges RN2’: with XoF function.
- ❖
- Seed-a challenges: CRP mechanism with table CT
- ○
- KSC transmit RN1 and RN2 by email to the client’s smartphone
- Operations driven by the “Crypto Wallet” apps in the client’s phone:
- ○
- Generation of Seed-a following the same steps as above:
- ❖
- Seed-a RN1, RN2, PW, image, token, and virtual token.
- ○
- Generate a public/private key pair with Dilithium and sign M:
- ❖
- Matrix-A Seed-a: with XoF function
- ❖
- Vectors V1 and V2 Seed-b; Private key Sk: {V1; V2}
- ❖
- Vector V1 + V2; Public key Pk: {Seed-a;}
- ❖
- : Sign message M with Sk
- ○
- Protect the private key Sk:
- ❖
- RN3’ RN3⊕PW’: with random number RN3, and PW’
- ❖
- challenges RN3’: with XoF function
- ❖
- Key K challenges: with a CRP mechanism and table CT
- ❖
- : Encrypt Sk with AES and K
- ○
- Transmit by email the message M, the signature S and vector to KSC
- ○
- Store RN2; RN3; and
- Final verification, and posting of the public keys
- ○
- Between seed-a that was generated from the table CT, and from the user, KSC is in possession of the full public key Pk: {Seed-a; t}
- ○
- KSC can verify the signature S of message M with Pk
- ○
- KSC transmits to a Certificate Authority, or the cloud, client’s ID and Pk
- ○
- KSC only keeps record of the crypto-table of the token CT-T
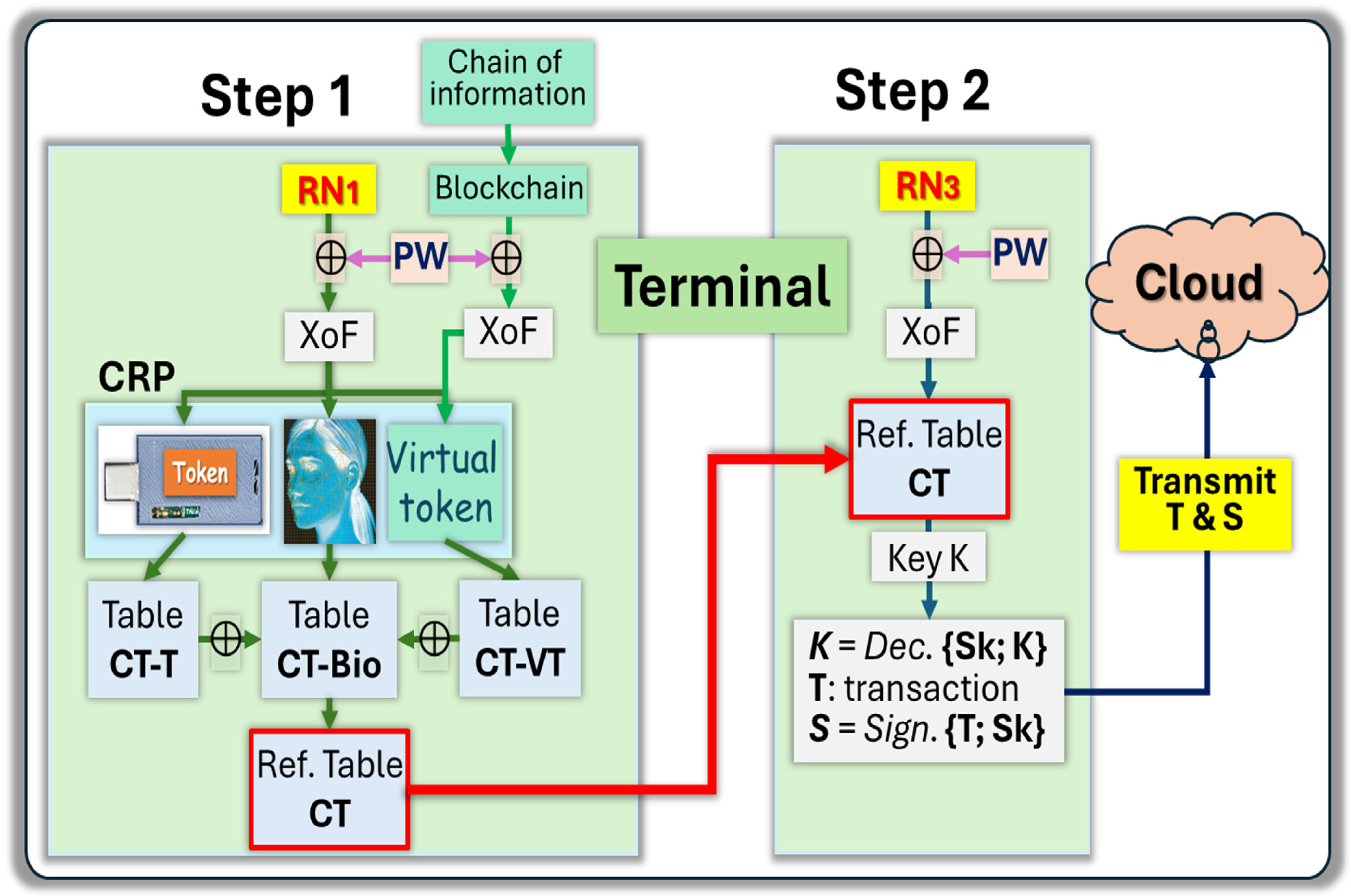
3.2. Signing a Transaction in a PKI Environment
- The user can recover the reference table CT with RN1 by plugging in the physical token, presenting their visual image, and computing the virtual token. Liveness tests can be inserted into the protocol to avoid third parties passing the visual test with an image of the user. The use of biometric images is “template-less”, which protects the privacy of the user.
- The user can recover the ephemeral key K from the reference table CT and RN3 with a CRP mechanism.
- The ephemeral key allows the decryption of Sk the private key.
- Sk is used to compute S, the signature of transaction T.
- The user transmits signature S, transaction T, and the public key Pk online.
- The signature can be openly verified by third parties with access to S, N, and Pk.
4. Experimental Section and Analysis
4.1. Generation of Reference Tables from PUF-Based Physical Tokens
4.2. Generation of Reference Tables from Biometric Images
4.3. Generation of Reference Tables from Blockchain-Based Virtual Tokens
4.4. Combination of Multiple Factors
5. Discussion: Recovery Protocols in Real-Life Implementation
5.1. Secure Key Recovery When the Token Is Defective or Lost
- One possible vector of attack could start with an insider or a side-channel analysis able to intercept the table CT-T, and the password needed during challenge generation. The first line of defense against such an attack is the one-way-ness of the CRP mechanism generating CT-T from the token. The 256 × 256 positions are randomly located in the SRAM, which contains one million cells, so the number of possible combinations to generate the table is staggering: . It is highly unlikely that knowledge of the table could result in disclosure of RN1. Without RN1, the opponent cannot find the reference table CT-Bio from the biometric image, or CT-VT from the virtual token, making the uncovering of the combined reference table CT extremely hard. In addition, knowledge of RN2 is also needed in the multi-layered MFA process.
- Another vector of attack could be taking physical control of the terminal device, and asking the Keystore to transmit CT-T. This could be a formidable attack, if the opponent also had access to all other factors of authentication. It is therefore recommended to incorporate additional protocols between the Keystore and the terminal device to protect the transmission of CT-T, such as the transmission of a code to a separate route such as email or SMS. In this second case, the token does not protect the terminal device; however, all other layers of protection remain in place. The MFA protocols were designed to keep an acceptable protection when only one factor of authentication is compromised; knowledge of CT-T is not enough to disclose CT, or therefore the ephemeral key.
5.2. Secure Recovery When the Biometric Image Is Defective or Lost
- The service could be provided by the Keystore; however, storing both CT-T and CT-Bio in the same location is not recommended.
- The user could ask the financial advisor managing their family trust to store CT-Bio, with written instructions to give back the reference table.
- Other examples of methods include the encryption of CT-Bio and its storage in the cloud, as well as the involvement of a family member.
5.3. Enhancing the One-Way-Ness of the Generation of CT-Bio
5.4. Secure Recovery When the Terminal Device Is Defective or Lost
5.5. Extreme Case: A Physical Threat
- The password could incorporate the warning signal.
- A change in facial expression can be detected by the CRP mechanism generating the CT-Bio that is presented in Section 2. The user could, for example, smile during the enrollment cycle in such a way that a recovery process without a smile could trigger an abnormal rate of errors in the CT-bio, and a warning signal.
- The retrieval of the virtual token could incorporate the warning signal.
- The MFA factors could be entered out of a pre-arranged sequence, thereby sending the warning signal.
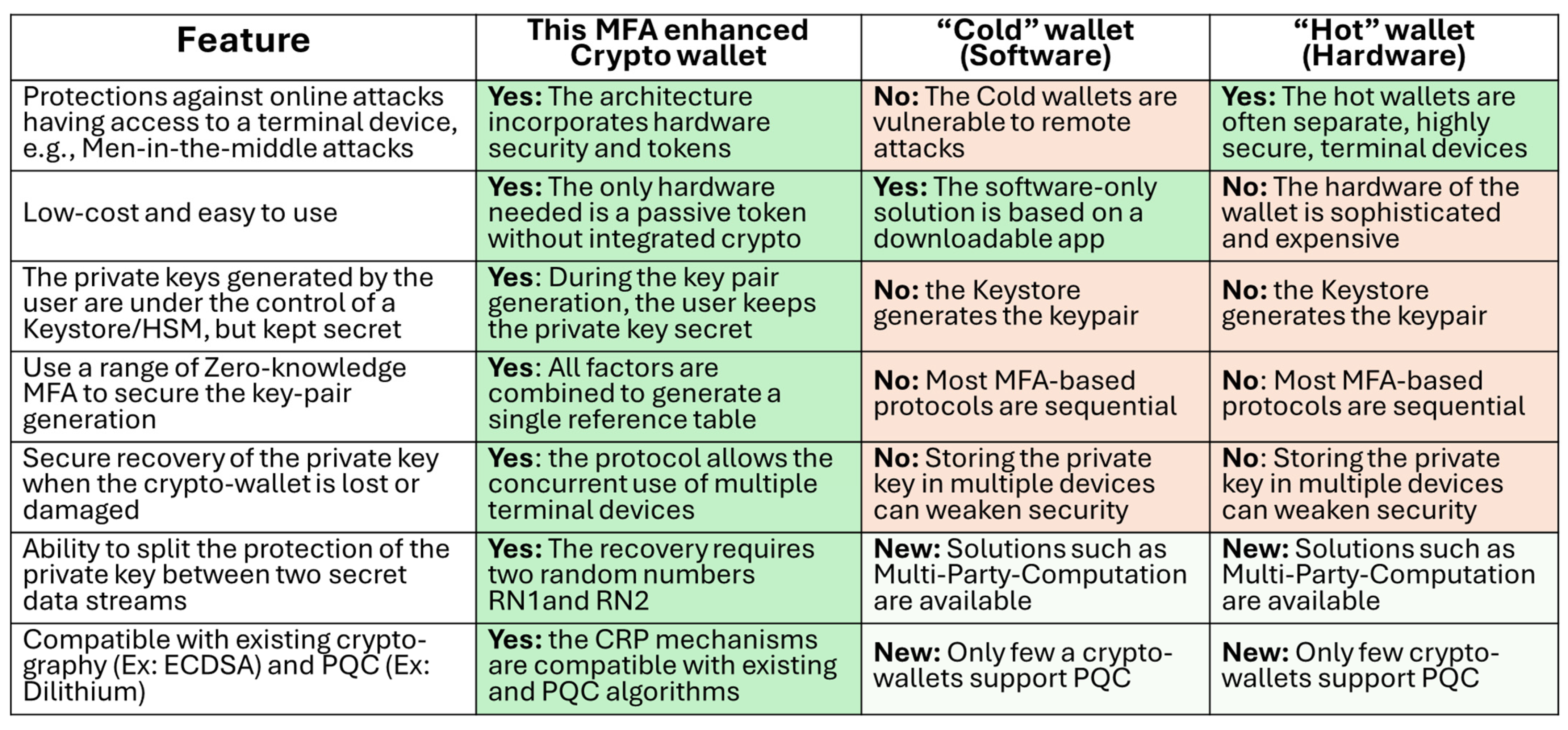
5.6. Comparative Analysis—Crypto Wallets
6. Conclusions and Future Work
- ○
- The enrollment process, token distribution, and recovery cycles can be managed by an independent Keystore corporation, which only has access to the first random number RN1. Both the user and the Keystore independently generate from RN1 (concatenated with a password) a combined reference table from multiple CRP mechanisms based on multiple factors of authentication.
- ○
- The novel key pair generating scheme preserves the privacy of users. As the shared RN1 enables verification of the validity of the public key Pk by the Keystore, the private keys are solely generated by the user with RN2, which is never shared and erased after key generation. The method is compatible with current PKI infrastructures, and crypto wallets with NIST’s standardized PQC.
- ○
- During normal operation, the MFA is directly under the control of each user, and easy to operate. To obtain their private key and sign a crypto-transaction, the user enters the password, RN1, and RN3; inserts the token into one of the terminals pre-loaded with the app; obtains an image from the camera; and retrieves the virtual token.
- ○
- On demand, the Keystore corporation can transmit to the user the reference table of the token CT-T. This allows the user to retrieve the private key when the token is lost. A new virtual enrollment using a new token is recommended.
- ○
- The user can use multiple devices, thereby being protected against HW failure or loss of a single crypto wallet. With current technologies, the loss of a crypto wallet is catastrophic, and private keys are lost. The flexibility does not compromise the security, as the public keys are not stored in a single crypto wallet that can be stolen and hacked.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AI | Artificial Intelligence |
| CA | Certificate Authority |
| CRP | Challenge–Response Pair |
| CT-T | Crypto Table Token |
| CT-Bio | Crypto Table Bio |
| CT-VT | Crypto Table Virtual Token |
| CT-Mask | Crypto Table Mask |
| ECC | Elliptic Curve Cryptography |
| FRR | False Reject Rate |
| FAR | False Acceptance Rate |
| HW | Hardware |
| HSM | Hardware Secure Module |
| K | Ephemeral Key |
| KDE | Kernel Density Estimation |
| LWE | Learning With Errors |
| MFA | Multi-Factor Authentication |
| MSB | Most Significant Bit |
| PKI | Public Key Infrastructure |
| PUF | Physical Unclonable Functions |
| Pk | Public Key |
| PQC | Post-Quantum Cryptography |
| PW | Password |
| RBC | Response-Based Cryptography |
| ReRAM | Resistive Random Access Memory |
| RSA | Rivest, Shamir, Adleman |
| SRAM | Static Random Access Memory |
| Sk | Secret Key/Private Key |
| SMS | Short Message Service |
References
- Buchmann, J.A.; Karatsiolis, E.; Wiesmaier, A. Introduction to Public Key Infrastructures; Springer: Berlin/Heidelberg, Germany, 2013. [Google Scholar]
- Lozupone, V. Analyze encryption and public key infrastructure (PKI). Int. J. Inf. Manag. 2018, 38, 42–44. [Google Scholar] [CrossRef]
- Smailes, J.; Köhler, S.; Birnbach, S.; Strohmeier, M.; Martinovic, I. KeySpace: Public Key Infrastructure Considerations in Interplanetary Networks. arXiv 2024, arXiv:2408.10963v3. [Google Scholar] [CrossRef]
- El-Hajj, M.; Beune, P. Lightweight public key infrastructure for the Internet of Things: A systematic literature review. J. Ind. Inf. Integr. 2024, 41, 100670. [Google Scholar] [CrossRef]
- Gentry, C.B. Certificate-Based Encryption and Public Key Infrastructure. 2002. Available online: https://patents.google.com/patent/US8074073B2/en?q=(Gentry+certificate)&oq=Gentry+certificate (accessed on 5 January 2025).
- Alam, M.; Hoffstein, J.; Cambou, B. Privately Generated Key Pairs for Post Quantum Cryptography in a Distributed Network. Appl. Sci. 2024, 19, 8863. [Google Scholar] [CrossRef]
- NIST Status Report of Phase 3 of PQC Program, NISTIR.8309. Available online: https://www.nist.gov/publications/status-report-second-round-nist-post-quantum-cryptography-standardization-process (accessed on 22 July 2020).
- Ducas, L.; Kiltz, E.; Lepoint, T.; Lyubashevsky, V.; Schwabe, P.; Seiler, G.; Stehlé, D. CRYSTALS-Dilithium Algorithm Specifications and Supporting Documentation; Part of the Round 3 Submission Package to NIST. Available online: https://pq-crystals.org/dilithium (accessed on 19 February 2021).
- Fouque, P.-A.; Hoffstein, J.; Kirchner, P.; Lyubashevsky, V.; Pornin, T.; Prest, T.; Ricosset, T.; Seiler, G.; Whyte, W.; Zhang, Z. Falcon: Fast-Fourier Lattice-Based Compact Signatures over NTRU; NIST PQC Project Round 2, Documentation. Available online: https://falcon-sign.info/falcon.pdf (accessed on 1 October 2020).
- Casanova, A.; Faugere, J.-C.; Macario-Rat, G.; Patarin, J.; Perret, L.; Ryckeghem, J. GeMSS: A Great Multivariate Short Signature; NIST PQC Project Round 2, Documentation. Available online: https://csrc.nist.gov/CSRC/media/Presentations/gemss-round-2-presentation/images-media/gemss-perret.pdf (accessed on 3 January 2017).
- Peikert, C.; Pepin, Z. Algebraically Structured LWE Revisited. J. Cryptol. 2024, 37, 28. [Google Scholar] [CrossRef]
- Regev, O. New Lattice-Based Cryptographic Constructions. J. ACM 2004, 51, 899–942. [Google Scholar] [CrossRef]
- McEliece, R.J. A Public-Key Cryptosystem Based on Algebraic Coding Theory; California Institute of Technology: Pasadena, CA, USA, 1978; pp. 114–116. [Google Scholar]
- Biswas, B.; Sendrier, N. McEliece Cryptosystem Implementation: Theory and Practice. In Post-Quantum Cryptography; Buchmann, J., Ding, J., Eds.; PQCrypto, Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2008; Volume 5299. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: www.biticoin.org (accessed on 5 January 2025).
- Aggarwal, S.; Kumar, N. Chapter Twelve–Cryptocurrencies; Aggarwal, S., Kumar, N., Raj, P., Eds.; Advances in Computers; Elsevier: Amsterdam, The Netherlands, 2021; Volume 121, pp. 227–266. [Google Scholar] [CrossRef]
- Shahzad, M.; Xu, S.; Lim, W.; Hasnain, M.; Nusrat, S. Cryptocurrency awareness, acceptance, and adoption: The role of trust as a cornerstone. Humanit. Soc. Sci. Commun. 2024, 11, 4. [Google Scholar] [CrossRef]
- García-Monleón, F.; Erdmann, A.; Arilla, R. A value-based approach to the adoption of cryptocurrencies. J. Innov. Knowl. 2023, 8, 100342. [Google Scholar] [CrossRef]
- Eyal, I.; Gencer, A.E.; Sirer, E.G.; Renesse, R.V. Bitcoin-NG: A Scalable Blockchain Protocol. In Proceedings of the 13th USENIX Symposium on Networked Systems Design and Implementation (NSDI ’16), Santa Clara, CA, USA, 16–18 March 2016. [Google Scholar]
- Juels, A.; Rahman, F. Systems and Methods for Securing Cryptocurrency Purchases. U.S. Patent 10,846,663 B2, 24 November 2020. [Google Scholar]
- Fan, C.-H.; Shih, M.-C. Cryptocurrency Securing Method and Device Thereof. U.S. Patent 11,386,429 B2, 12 July 2022. [Google Scholar]
- Fan, C.-H.; Hsu, C.-Y.; Shih, M.-C. Cryptocurrency securing system and method. U.S. Patent 11,941,610 B2, 26 March 2024. [Google Scholar]
- Tripathi, G.; Ahad, M.; Casalino, G. A comprehensive review of blockchain technology: Underlying principles and historical background with future challenges. Decis. Anal. J. 2023, 9, 100344. [Google Scholar] [CrossRef]
- Justinia, T. Blockchain Technologies: Opportunities for Solving Real-World Problems in Healthcare and Biomedical Sciences. Acta Inform. Med. 2019, 27, 284–291. [Google Scholar] [CrossRef]
- Croman, K.; Decker, C.; Eyal, I.; Gencer, A.E.; Juels, A.; Kosba, A.; Miller, A. On scaling decentralized blockchains. In Financial Cryptography and Data Security; Springer: Berlin/Heidelberg, Germany, 2016. [Google Scholar]
- Luu, L.; Narayanan, V.; Zheng, C.; Baweja, K.; Gilbert, S.; Saxena, P. A secure sharing protocol for open blockchains. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016. [Google Scholar]
- Dorri, A.; Kanhere, S.S.; Jurdak, R. Blockchain in internet of things: Challenges and solutions. arXiv 2016, arXiv:1608.05187. [Google Scholar]
- Gervais, A.; Karame, G.O.; Wüst, K.; Glykantzis, V.; Ritzdorf, H.; Capkun, S. On the security and performance of proof of work blockchains. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016. [Google Scholar]
- Zheng, Z.; Xie, S.; Dai, H.-N.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2016, 14, 352. [Google Scholar] [CrossRef]
- Yu, Y.; Sharma, T.; Das, S.; Wang, Y. Don’t put all your eggs in one basket: How Cryptocurrency Users Choose and Secure Their Wallets. In Proceedings of the 2024 CHI Conference on Human Factors in Computing Systems, Honolulu, HI, USA, 11–16 May 2024. [Google Scholar] [CrossRef]
- Barbereau, T.; Bodó, B. Beyond financial regulation of crypto-asset wallet software: In search of secondary liability. Comput. Law Secur. Rev. 2023, 49, 105829. [Google Scholar] [CrossRef]
- Houy, S.; Schmid, P.; Bartel, A. Security Aspects of Cryptocurrency Wallets—A Systematic Literature Review. ACM Comput. Surv. 2024, 56, 1–31. [Google Scholar] [CrossRef]
- Pospieszalski, M.; Odom, C. Crypto Currency Hardware Wallet. U.S. Patent 2022/0335422 A1, 20 October 2022. [Google Scholar]
- Wright, C.; Savanah, S. Secure Multiparty Loss Resistant Storage and Transfer of Cryptographic Keys for Blockchain Based Systems in Conjunction with a Wallet Management System. European Patent EP3259724B1, 24 March 2021. [Google Scholar]
- Nolan, M.; Carboni, D.; Smith, N. Contextual Authentication of an Electronic Wallet. Methods and Systems Are Provided for a Contextual Authentication of an Electronic Wallet (e-Wallet). U.S. Patent 11,386,420 B2, 12 July 2022. [Google Scholar]
- Abramova, S.; Böhme, R. Anatomy of a High-Profile Data Breach: Dissecting the Aftermath of a Crypto-Wallet Case. In Proceedings of the 32nd USENIX Security Symposium (USENIX Security 23), Anaheim, CA, USA, 9–11 August 2023; USENIX Association: Berkeley, CA, USA, 2023; pp. 715–732. [Google Scholar]
- Almadani, M.; Alotaibi, S.; Alsobhi, H.; Hussain, O.; Hussain, F. Blockchain-based multi-factor authentication: A systematic literature review. Internet Things 2023, 23, 100844. [Google Scholar] [CrossRef]
- Kebande, V.; Awaysheh, F.; Ikuesan, R.; Alawadi, S.; Alshehri, M. A Blockchain-Based Multi-Factor Authentication Model for a Cloud-Enabled Internet of Vehicles. Sensors 2021, 21, 6018. [Google Scholar] [CrossRef] [PubMed]
- Jose Diaz Rivera, J.; Muhammad, A.; Song, W.-C. Securing Digital Identity in the Zero Trust Architecture: A Blockchain Approach to Privacy-Focused Multi-Factor Authentication. IEEE Open J. Commun. Soc. 2024, 5, 2792–2814. [Google Scholar] [CrossRef]
- Islamov, I. Secret Material Exchange and Authentication Cryptography Operations. U.S. Patent 11,637,694 B2, 25 April 2023. [Google Scholar]
- Be’ery, T.; Ohayon, O.; Shlomovits, O.; Benattar, G.; Manuskin, A.; Leiba, O. System and Method of Multi-Party Computation Based Multi-Factor Authentication. U.S. Patent 2023/0299942 A1, 21 September 2023. [Google Scholar]
- Popp, N. Token Provisioning. 2024. Available online: https://patents.google.com/patent/US8015599B2/en?q=(Token+Provisioning)&inventor=popp&oq=Token+Provisioning++popp (accessed on 5 January 2025).
- Shahbazi, Z.; Byun, Y. Analysis of the Security and Reliability of Cryptocurrency Systems Using Knowledge Discovery and Machine Learning Methods. Sensors 2022, 22, 9083. [Google Scholar] [CrossRef]
- Fiske, M. Securing Transactions with a Blockchain Network. U.S. Patent 11,824,991 B2, 21 November 2023. [Google Scholar]
- Weichbroth, P.; Wereszko, K.; Anacka, H.; Kowal, J. Security of Cryptocurrencies: A View on the State-of-the-Art Research and Current Developments. Sensors 2023, 23, 3155. [Google Scholar] [CrossRef]
- Barthelemy, S.; Thieblemont, J. Method for Two Step Digital Signature. U.S. Patent 8,589,693, 22 October 2008. [Google Scholar]
- Maximov, A.; Hell, M.; Smeets, B. Methods of Proving Validity and Determining Validity, Electronic Device, Server and Computer Programs. U.S. Patent 10,511,440, 20 February 2015. [Google Scholar]
- Herder, C.; Srivastava, T. System and Method for Securing Personal Information via Biometric Public Key. U.S. Patent 11,343,099 B2, 24 May 2022. [Google Scholar]
- Yaldin, D.; Riva, B.; Navon, A.; Pachmanov, L.; Katz, J. Techniques for Securing Digital Signatures Using Multi-Party Computation. U.S. Patent 11,689,371 B2, 27 June 2023. [Google Scholar]
- Pala, M.; Scriber, B.; Goeringer, S. Systems and Methods for Integrating Crypto-Currency Wallet Identifiers with Digital Certificates. U.S. Patent 2019/0295069 A1, 26 September 2019. [Google Scholar]
- Maletsky, K.D.; Seymour, M.J.; Garner, B.P. Generating Keys Using Secure Hardware. 2015. Available online: https://patents.google.com/patent/US9118467B2/en?inventor=Maletsky&oq=Maletsky+ (accessed on 3 September 2024).
- Herder, C.; Yu, M.-D.; Koushanfar, F.; Devadas, S. Physical Unclonable Functions and Applications: A Tutorial. Proc. IEEE 2014, 102, 1126–1141. [Google Scholar] [CrossRef]
- Schrijen, G.-J.; van der Leest, V. Comparative Analysis of SRAM Memories Used as PUF Primitives. In Proceedings of the 2012 Design, Automation & Test in Europe Conference & Exhibition (DATE), Dresden, Germany, 12–16 March 2012. [Google Scholar]
- Liu, R.; Wu, H.; Pang, Y.; Qian, H.; Yu, S. A Highly Reliable and Tamper-Resistant RRAM PUF: Design and Experimental Validation. In Proceedings of the 2016 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), McLean, VA, USA, 3–5 May 2016; Volume 100, pp. 13–18. [Google Scholar]
- Cambou, B.; Gowanlock, M.; Yildiz, B.; Ghanaimiandoab, D.; Lee, K.; Nelson, S.; Philabaum, C.; Stenberg, A.; Wright, J. Post Quantum Cryptographic Keys Generated with Physical Unclonable Functions. Appl. Sci. 2021, 11, 2801. [Google Scholar] [CrossRef]
- Aguilar Rios, M.; Alam, M.; Cambou, B. MRAM Devices to Design Ternary Addressable Physically Unclonable Functions. Electronics 2023, 12, 3308. [Google Scholar] [CrossRef]
- Cambou, B.; Mohammadi, M.; Philabaum, C.; Booher, D. Statistical Analysis to Optimize the Generation of Cryptographic Keys from Physical Unclonable Functions. In Advances in Intelligent Systems and Computing; Springer International Publishing: Cham, Switzerland, 2020; pp. 302–321. [Google Scholar]
- Nowroozi, E.; Seyedshoari, S.; Mekdad, Y.; Savas, E.; Conti, M. Cryptocurrency wallets: Assessment and security. arXiv 2023, arXiv:2303.12940. [Google Scholar]
- Hinkes, A. Throw away the key or the key holder? Northwestern J. Technol. Intellect. Prop. 2019, 16, 1. [Google Scholar]
- Maine, J.; Nguyen, X.-T. Crypto Losses; University of Maine School of Law Digital Commons, Faculty Publications: Partland, OR, USA, 2024. [Google Scholar]
- Mallik, A. Man-in-the-Middle-Attack: Understanding in Simple Words. Cyberspace J. Pendidik. Teknol. Inf. 2019, 2, 109. [Google Scholar] [CrossRef]
- Chimienti, M.; Kochanska, U.; Pinna, A. Understanding the Crypto-Asset Phenomenon, Its Risks and Measurement Issues; Published as Part of the ECB Economic Bulletin; European Central Bank: Frankfurt, Germany, 2019. [Google Scholar]
- Holmes, A.; Buchanan, J. A framework for live host-based Bitcoin wallet forensics and triage. Forensic Sci. Int. Digit. Investig. 2023, 44, 301486. [Google Scholar] [CrossRef]
- Cambou, B.; Telesca, D.; Jacinto, H.S. PUF-Protected Methods to Generate Session Keys. In Lecture Notes in Networks and Systems; Springer International Publishing: Cham, Switzerland, 2022; pp. 744–764. [Google Scholar]
- Rusia, M.K.; Singh, D.K. A Comprehensive Survey on Techniques to Handle Face Identity Threats: Challenges and Opportunities. Multimed. Tools Appl. 2022, 82, 1669–1748. [Google Scholar] [CrossRef]
- Generated Photos. Available online: https://generated.photos/ (accessed on 5 January 2025).
- Johnson, W.B.; Lindenstrauss, J. Extensions of Lipschitz Mappings into a Hilbert Space. Contemp. Math. 1984, 6, 189–206. [Google Scholar]
- Hinrichs, A.; Vybíral, J. Johnson-Lindenstrauss Lemma for Circulant Matrices. Random Struct. Algorithms 2011, 39, 391–398. [Google Scholar]
- Cambou, B. Multi-Factor Authentication Using a Combined Secure Pattern; Part I. U.S. Patent 9,514,292, 6 December 2016. [Google Scholar]



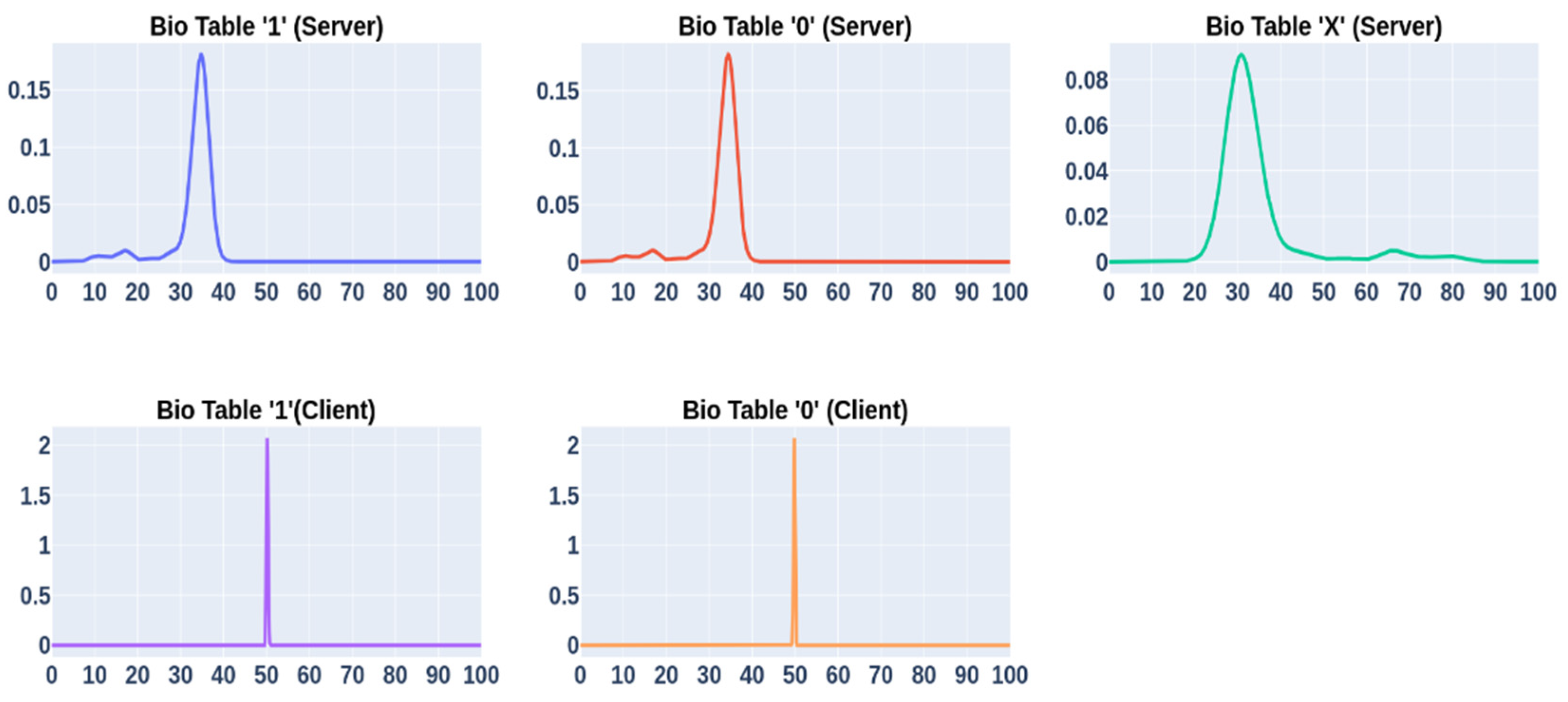
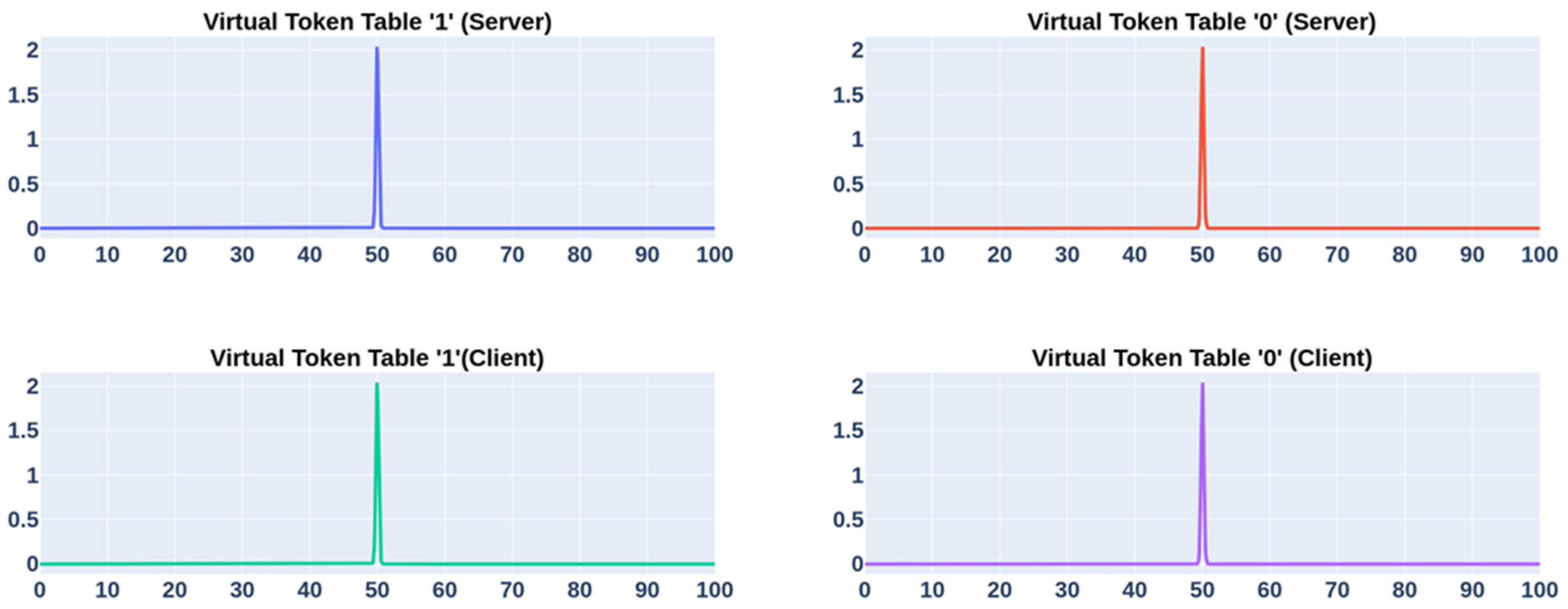


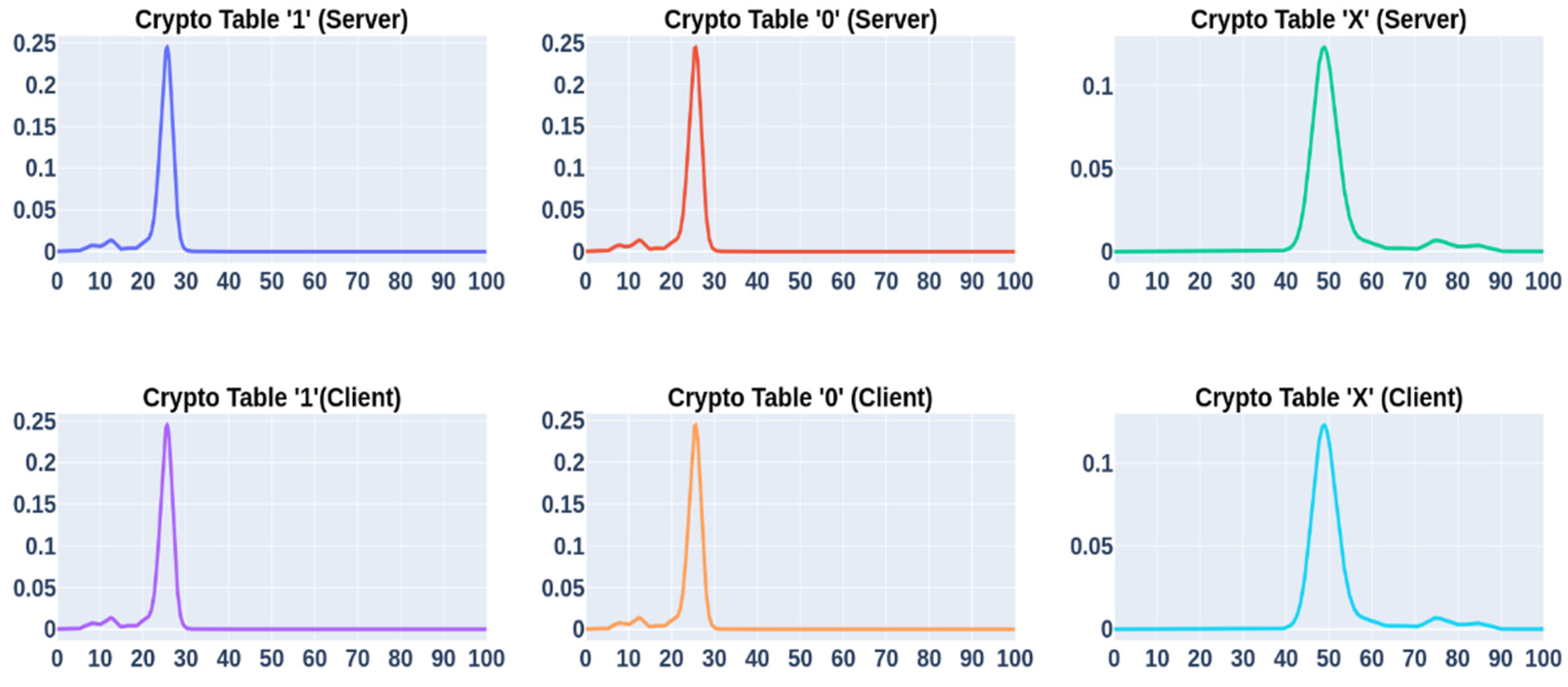
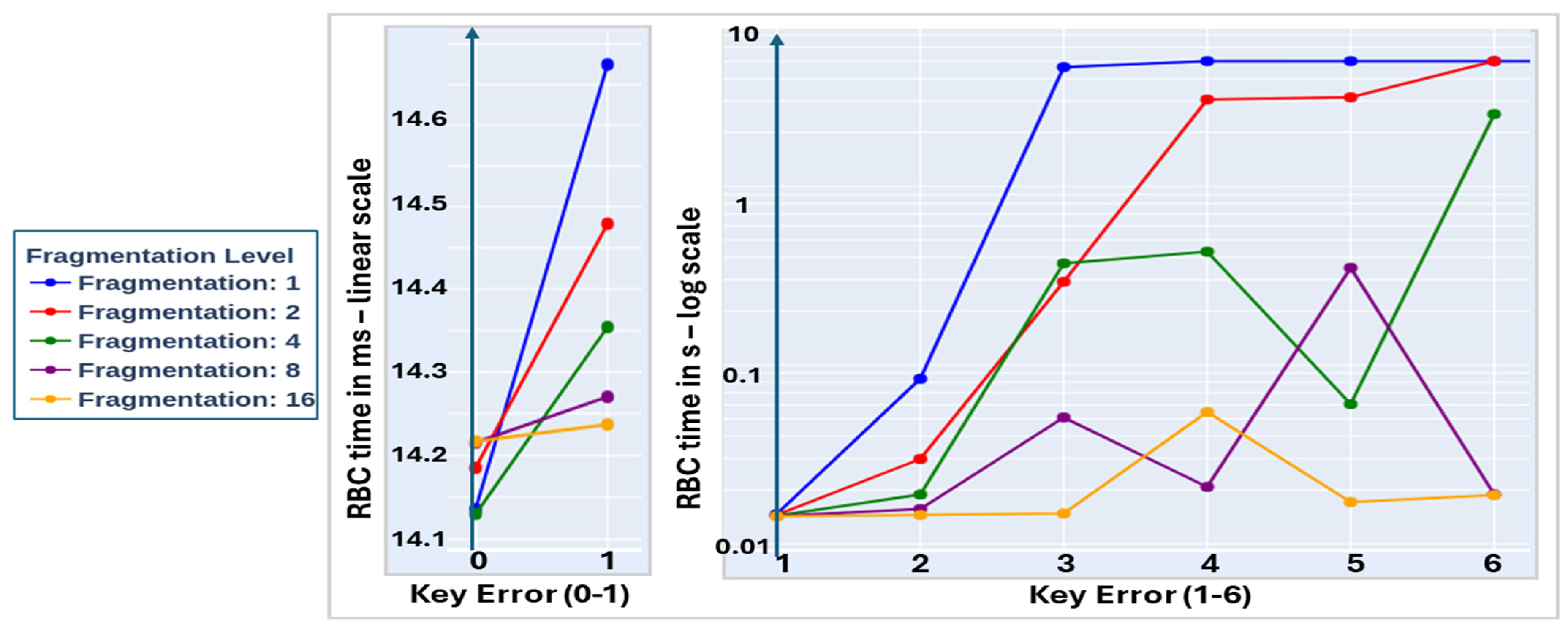

| Test Type | Fragmentation | True (%) | False (%) |
|---|---|---|---|
| FRR (False Reject Rate) | 1 | 77.67 | 22.33 |
| 2 | 96.70 | 3.30 | |
| 4 | 99.24 | 0.76 | |
| 8 | 100 | 0 | |
| 16 | 100 | 0 | |
| FAR (False Acceptance Rate) | 1 | 0 | 100 |
| 2 | 0.25 | 99.75 | |
| 4 | 1.01 | 98.98 | |
| 8 | 7.89 | 92.13 | |
| 16 | 21.88 | 78.12 |
| Gender | Age Range | Skin Tone | True (%) | False (%) |
|---|---|---|---|---|
| Female | 20–34 |
| 94.28 | 5.72 |
| 98.33 | 1.67 | ||
| 93.33 | 6.67 | ||
| 94 | 6 | ||
| 95.38 | 4.62 | ||
| 35–50 |
| 100 | 0 | |
| 91.67 | 8.33 | ||
| 95 | 5 | ||
| 95.71 | 4.29 | ||
| 94.55 | 5.45 | ||
| 51–65 |
| 95 | 5 | |
| 92.22 | 7.78 | ||
| 91.78 | 8.22 | ||
| 90 | 10 | ||
| 98.57 | 1.43 | ||
| Male | 20–34 |
| 93.33 | 6.67 |
| 95.38 | 4.62 | ||
| 98.61 | 1.39 | ||
| 96.67 | 3.33 | ||
| 96 | 4 | ||
| 35–50 |
| 95 | 5 | |
| 89.23 | 10.77 | ||
| 96.37 | 3.64 | ||
| 96.67 | 3.33 | ||
| 92 | 8 | ||
| 51–65 |
| 97 | 3 | |
| 98.18 | 1.82 | ||
| 100 | 0 | ||
| 89.33 | 10.67 | ||
| 94.55 | 5.45 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cambou, B.F.; Alam, M. Challenge–Response Pair Mechanisms and Multi-Factor Authentication Schemes to Protect Private Keys. Appl. Sci. 2025, 15, 3089. https://doi.org/10.3390/app15063089
Cambou BF, Alam M. Challenge–Response Pair Mechanisms and Multi-Factor Authentication Schemes to Protect Private Keys. Applied Sciences. 2025; 15(6):3089. https://doi.org/10.3390/app15063089
Chicago/Turabian StyleCambou, Bertrand Francis, and Mahafujul Alam. 2025. "Challenge–Response Pair Mechanisms and Multi-Factor Authentication Schemes to Protect Private Keys" Applied Sciences 15, no. 6: 3089. https://doi.org/10.3390/app15063089
APA StyleCambou, B. F., & Alam, M. (2025). Challenge–Response Pair Mechanisms and Multi-Factor Authentication Schemes to Protect Private Keys. Applied Sciences, 15(6), 3089. https://doi.org/10.3390/app15063089







