Abstract
The malicious contamination of food has been recognized by the World Health Organization (WHO) as a real and current threat that must be integrated into food safety systems to ensure preparedness for deliberate attacks. Traditional approaches, such as HACCP, effectively address unintentional hazards but remain insufficient against intentional contamination and sabotage. Food defense frameworks such as HACCP (Hazard Analysis and Critical Control Points), VACCP (Vulnerability Assessment and Critical Control Points), and TACCP (Threat Assessment and Critical Control Points) represent complementary methodologies, addressing unintentional, economically motivated, and deliberate threats, respectively. This review critically examines food defense frameworks across the European Union, the United States, and the United Kingdom, as well as standards benchmarked by the Global Food Safety Initiative (GFSI), drawing on peer-reviewed and grey literature sources. In the United States, the Food Safety Modernization Act (FSMA) mandates the development and periodic reassessment of food defense plans, while the European Union primarily relies on general food law and voluntary certification schemes. The United Kingdom’s PAS 96:2017 standard provides TACCP-based guidance that also acknowledges cybercrime as a deliberate threat. Building on these regulatory and operational gaps, this paper proposes the Cyber-FSMS model, an integrated framework that combines traditional food defense pillars with cyber risk management to address cyber–physical vulnerabilities in increasingly digitalized supply chains. The model introduces six interconnected components (governance, vulnerability assessment, mitigation, monitoring, verification, and recovery) designed to embed cyber-resilience into Food Safety Management Systems (FSMS). Priority actions include regulatory harmonization, practical support for small and medium-sized enterprises (SMEs), and the alignment of cyber-resilience principles with upcoming GFSI benchmarking developments, thereby strengthening the integrity, robustness, and adaptability of global food supply chains.
1. Introduction
Food defense has emerged as a critical pillar of global food security, encompassing strategies to protect the food supply chain from intentional adulteration, sabotage, and agroterrorism. Unlike conventional food safety systems that primarily address accidental hazards, food defense requires proactive and anticipatory mechanisms to mitigate deliberate threats [1,2,3]. The urgency of this issue is amplified by increasing geopolitical instability, the globalization of supply chains, and the rise of digital vulnerabilities across agri-food systems [4,5,6,7]. Accelerating digitalization spanning smart farming, IoT-enabled cold chains, blockchain traceability, and automated processing further expands the attack surface for cyber-enabled disruptions. By integrating IT and OT environments, digitalization increases system vulnerabilities and creates potential entry points for cyberattacks targeting production and logistics operations. This underscores the need to integrate cyber-risk management into food defense frameworks beyond classical HACCP-centric paradigms. [8].
Several sentinel incidents illustrate the multidimensional nature of food defense challenges. The 2008 melamine contamination of milk powder in China affected hundreds of thousands of infants and highlighted the severe health and economic consequences of economically motivated adulteration [9]. The 2011 STEC O104:H4 outbreak in Germany, likely traced to contaminated fenugreek seeds imported from Egypt, used to grow sprouts, demonstrated how early-stage contamination can escalate into a multinational crisis with enduring impacts on consumer confidence [10]. More recently, the 2021 ransomware attack on JBS Foods forced plant closures in the United States and Australia, revealing that cyberattacks can compromise food production as effectively as physical adulteration [11]. Collectively, these cases show that both physical and digital vectors of attack must be systematically addressed. In response, international organizations such as the World Health Organization (WHO) and the One Health High-Level Expert Panel have emphasized that deliberate food contamination, agroterrorism, and cyber-enabled threats represent credible risks requiring systemic preparedness [2,12,13]. Regulatory responses, however, remain fragmented. In the United States, the Food Safety Modernization Act (FSMA) established binding requirements for intentional adulteration [14,15], while the European Union relies on general food law [16] and voluntary Global Food Safety Initiative (GFSI)–benchmarked standards [17]. The United Kingdom’s PAS 96:2017 provides practical guidance through Threat Assessment and Critical Control Points (TACCP), yet its implementation is voluntary [18]. This regulatory heterogeneity highlights the lack of harmonized approaches that fully integrate both physical and digital threats [19]. At the same time, development agency reports reveal inconsistent conceptualizations of resilience within food security agendas [20].
Such work reinforces the argument that future food defense must bridge chemical, biological, physical, and cyber domains. Scholars also stress that the agri-food sector remains one of the least cyber-mature infrastructures, with relatively low awareness and preparedness compared to other critical industries [21,22]. Against this backdrop, the objective of this review is to systematically examine existing food defense frameworks, identify regulatory and operational gaps, and introduce the Cyber-FSMS model, which integrates cyber-resilience into traditional food safety and defense systems [23].
The Food Safety Management System (FSMS) is structured around several interrelated pillars that collectively address risks across the food supply chain. While traditional food safety emphasizes unintentional hazards, contemporary frameworks increasingly incorporate intentional contamination, economically motivated fraud, terrorism, agroterrorism, and broader resilience. Six pillars are consistently recognized in the international literature [1,12,24,25]:
- Food Safety: Ensures that food, feed, and related packaging do not harm consumers when prepared and consumed as intended. It primarily targets unintentional contamination (microbial, chemical, and physical hazards), using tools such as Hazard Analysis and Critical Control Points (HACCP), Good Manufacturing Practices (GMP), and systematic testing [1,26].
- Food Fraud: Defined as intentional misrepresentation or adulteration of food for economic gain, food fraud undermines both public health and consumer trust. Vulnerability Assessment and Critical Control Points (VACCP) is a preventive tool that systematically identifies points in the supply chain most vulnerable to fraud and establishes controls to mitigate such risks and authenticity testing represent key preventive tools [1,25,27].
- Food Defense: Focuses on adversarial, ideologically motivated, or criminal contamination. Core measures include Threat Assessment and Critical Control Points (TACCP), surveillance, controlled access, and supply chain monitoring [1,12,28].
- Food Terrorism: Involves deliberate contamination with chemical, biological, or radiological agents intended to destabilize societies. Effective mitigation requires inter-agency coordination, intelligence-sharing, and crisis management protocols [29,30].
- Agroterrorism: Targets agricultural resources such as crops and livestock, often through the introduction of harmful pathogens. Preventive strategies include strict biosecurity, animal health surveillance, and early warning system [29,31].
- Food Security: Defined by the FAO as continuous physical and economic access to sufficient, safe, and nutritious food. It connects closely with food safety and defense, emphasizing system resilience under geopolitical, economic, and environmental stress [32,33,34].
2. Materials and Methods
This review followed a structured methodology in line with the PRISMA 2020 guidelines [35] and best practices for evidence synthesis [36,37]. The protocol was designed to ensure comprehensive coverage of both scientific literature and regulatory sources relevant to food defense and cyber-resilience in agri-food supply chains.
- Literature search strategy
Systematic searches were conducted in Scopus, Web of Science Core Collection, PubMed, and Google Scholar, covering the period from January 2000 to December 2024. Given that Google Scholar is not a curated database and may produce duplicate or low-quality records, its outputs were screened manually for relevance, source credibility, and duplication prior to inclusion. Search strings combined controlled vocabulary (MeSH terms in PubMed) and free-text keywords related to intentional food contamination and cyber risks. Full Boolean search strings (including operators and combinations) are provided in Supplementary File S2 to support transparency and reproducibility. Examples of the search terms included:
- food defense, intentional adulteration, agroterrorism, food supply chain,
- TACCP, VACCP, FSMA, PAS 96, GFSI [18,26,38]
- cyber risk, cybersecurity, blockchain, artificial intelligence, digital food safety.
In addition, grey literature was retrieved from official websites of the European Commission, U.S. Food and Drug Administration (FDA), Food and Agriculture Organization (FAO), World Health Organization (WHO), and the Global Food Safety Initiative (GFSI), as well as industry white papers and technical standards.
- Eligibility criteria
Studies were included if they met the following criteria:
- peer-reviewed articles addressing intentional food contamination, food defense frameworks, or agroterrorism;
In this context, “international adulteration” refers to deliberate contamination or fraud occurring across national borders, often targeting export-oriented food supply chains.
- 2.
- regulatory or policy documents describing national or international requirements;
- 3.
- studies proposing digital or cyber-integrated food defense approaches.
Exclusion criteria were:
- publications not written in English;
- studies focused exclusively on unintentional food safety hazards.
- Screening and selection
The initial search identified 324 records. After removing duplicates, two independent reviewers screened titles, abstracts, and full texts. Disagreements were resolved through consensus. Inter-rater reliability was measured with Cohen’s κ = 0.81, indicating substantial agreement [39,40]. Reference lists of the included papers were hand-searched to identify additional sources. In total, 87 studies were included for analysis.
- Quality appraisal
For grey literature (policy papers, regulatory guidelines, and technical standards), quality appraisal was based on three criteria: (i) transparency of the issuing body (e.g., governmental, intergovernmental, or industry association), (ii) explicitness of methodology or scope, and (iii) practical applicability for food defense and cyber-risk management. Practical applicability was assessed through a qualitative consensus approach between two reviewers using a predefined rubric to minimize subjectivity. Documents not meeting at least two of these criteria were excluded.
The methodological quality of included studies was assessed according to study type:
- AMSTAR 2 for systematic reviews [41].
- MMAT for mixed-method designs [42,43].
- Transparency and applicability criteria for regulatory or policy documents.
- Data extraction and synthesis.
Data were extracted using a standardized template shown in Figure 1, focusing on:
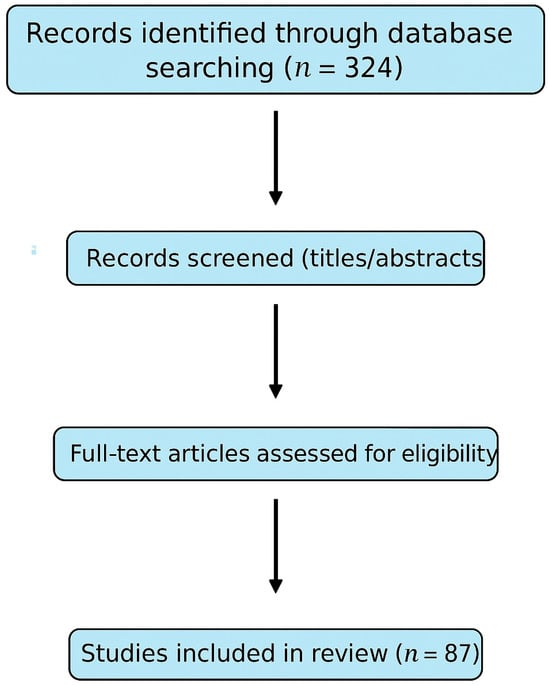
Figure 1.
PRISMA flow diagram illustrating the literature selection process (324 identified → 87 included) [1,4].
- Jurisdiction and legal framework.
- Type of threat (intentional adulteration, cyber risk, agroterrorism).
- Methodological framework (e.g., TACCP, VACCP, CARVER+Shock) [24,44].
- Outcomes, implementation challenges, and innovations relevant to cyber-food defense.
A narrative thematic synthesis was performed, grouping results into three domains:
- international food defense frameworks,
- cyber incidents in the agri-food sector,
- enabling standards and technologies for Cyber-FSMS integration.
Themes were identified through iterative coding and clustering of extracted data, allowing emergent categories to reflect key conceptual and methodological trends.
The complete dataset of 87 included records is provided in Supplementary File S1, alongside the PRISMA 2020 checklist [35].
3. Results
3.1. Agricultural Supply Chains and Food Defense: An Expanded Overview
The agricultural supply chain is a complex, multi-stage system spanning upstream inputs (seeds, fertilizers, veterinary medicines, equipment) to downstream stages such as cultivation, harvesting, processing, distribution, retail, and consumer access [42,43,45]. Each stage is exposed to specific vulnerabilities that can be exploited for intentional contamination or disruption [41,44]:
Inputs: Susceptible to adulteration of seeds, feed, or veterinary products, with direct effects on animal and crop health [7,44].
Primary production: Vulnerable to biological or chemical sabotage, as well as environmental stressors [1].
Post-harvest handling: Storage, sorting, and cleaning are sensitive points for both spoilage and deliberate contamination [24].
Processing and manufacturing: Increasingly automated systems introduce not only classical hazards but also cyber–physical vulnerabilities (e.g., SCADA/PLC attacks, IoT manipulation) [46,47].
Distribution and logistics: Multi-actor involvement and fragmented traceability create opportunities for tampering, diversion, or fraud [36,48,49].
Retail and consumer interface: As the frontline of consumer trust, this stage is vulnerable to product tampering and requires transparent labeling, tamper-evident packaging, and surveillance [37].
Table 1 summarizes vulnerabilities, threats, and mitigation measures across these stages. Such a structured overview provides the foundation for the thematic synthesis presented later in this review.

Table 1.
Vulnerabilities, threats, and defense measures in the agri-food supply chain.
The multi-stakeholder nature of agri-food supply chains—from producers and suppliers to processors, distributors, retailers, regulators, and consumers—necessitates a systems-based and collaborative approach [29,49]. Policy support, advisory services, and knowledge-sharing platforms are critical for building resilience [36]. Furthermore, recent crises, including the Russia–Ukraine conflict and COVID-19 pandemic, have illustrated how food systems can be strategically weaponized or disrupted at scale [28,29,50,51,52].
3.2. Descriptive Synthesis of Included Studies
Among the 87 studies included in this review, 42% addressed regulatory frameworks, 35% focused on technological or operational countermeasures, and 23% analyzed cyber-related risks. Percentages were calculated based on thematic coding of all included studies:
Geographically, publications were concentrated in the United States (38%), the European Union (31%), and the United Kingdom (12%), with fewer than 5% of studies originating from low- and middle-income countries (LMICs), primarily Brazil and India. This imbalance underscores the need for more global perspectives. Already in 2020, Okupa emphasized that the U.S. agri-food sector, as one of 16 critical infrastructures, faces specific cybersecurity risks with systemic implications [53]. More recent national-level analyses, such as Ingemundsen’s study of Norwegian agriculture, confirm that cyber risks directly affect food security and national preparedness [54].
Overall, the literature revealed three dominant approaches:
- Prescriptive frameworks (e.g., FSMA in the US);
- Voluntary guidance (e.g., PAS 96 in the UK);
- Certification-driven schemes (e.g., BRCGS, IFS, FSSC under GFSI benchmarking) [55,56,57].
These categories provide the analytical structure for the synthesis presented below. The results are presented in three parts:
- Table 2: Comparison of regulatory and certification frameworks.
 Table 2. Comparison of global food defense frameworks.
Table 2. Comparison of global food defense frameworks. - Table 3: Case studies of major cyber incidents affecting food and agriculture supply chains.
 Table 3. Selected cyber incidents in agri-food sector.
Table 3. Selected cyber incidents in agri-food sector. - Table 4: Enabling standards and technologies for operationalizing the Cyber-FSMS model.
 Table 4. Standards & technologies enabling Cyber-FSMS.
Table 4. Standards & technologies enabling Cyber-FSMS.
As summarized in Table 2, FSMA mandates periodic vulnerability reanalysis, PAS 96 provides voluntary TACCP guidance, and GFSI-benchmarked schemes require documented food defense plans but provide limited explicit coverage of cyber risks. [27].
Table 3 highlights incidents such as the ransomware attack on JBS Foods (2021) and the Whole Foods supplier cyberattack (2025), both of which triggered cascading disruptions across supply chains [30]. These events demonstrate that digital risks can destabilize food systems as severely as physical adulteration, underscoring the urgency of integrated defense frameworks such as the proposed Cyber-FSMS model.
Table 3 highlights major cyber incidents in the agri-food sector. The 2021 ransomware attack on JBS Foods forced temporary shutdowns of slaughterhouses in the United States and Australia, disrupting meat supply chains globally and resulting in a ransom payment of USD 11 million [58]. In June 2025, a cyberattack on United Natural Foods Inc. (UNFI), the primary supplier for Whole Foods, disrupted retail distribution and demonstrated how vulnerabilities at third-party vendors can cascade into consumer-facing shortages, as UNFI was forced to disable ordering systems and switch to manual processing, which led to delivery delays and empty shelves in Whole Foods stores [59,60,61] Additional incidents include the Dole Foods ransomware attack (2023), which halted fresh produce packaging lines, and the Maple Leaf Foods cyber intrusion (2022), which disrupted IT and logistics operations. Collectively, these cases illustrate that ransomware and supply-chain cyber intrusions create cascading failures—plant closures, distribution bottlenecks, financial losses, and reputational harm—that extend well beyond the scope of traditional food safety systems.
Table 4 presents complementary standards and technologies that can support the operationalization of the proposed Cyber-FSMS model. These include GS1 EPCIS 2.0, enabling interoperable digital traceability across global supply chains; NIST Cybersecurity Framework (CSF) 2.0, providing governance and risk management structures; and IEC 62443, addressing operational technology (OT) and industrial control system (ICS) security [62,63,64,65]. Together, these standards provide a foundation for integrating cyber-resilience into existing food safety and defense practices.
- Cyber-FSMS: An Integrated Food Safety and Cyber-Risk Framework
The digitalization of agri-food supply chains introduces both unprecedented opportunities and novel vulnerabilities [62,64]. Blockchain-enabled traceability, IoT-based cold-chain monitoring, and automated process control systems improve transparency, efficiency, and consumer trust. At the same time, these technologies expand the attack surface for malicious actors, exposing food systems to ransomware, supply-chain intrusions, and IoT manipulations that can trigger cascading disruptions [46,56,65]. Such events demonstrate that cyberattacks can destabilize food safety and integrity as severely as deliberate physical contamination.
Traditional Food Safety Management Systems (FSMS), such as HACCP and ISO 22000, were designed to address accidental hazards and intentional contamination of physical origin. However, they provide little explicit coverage of cyber–physical risks [1,4,12]. To address this gap, we propose the Cyber-FSMS model, a modular framework designed as an extension to HACCP/ISO 22000 and GFSI-benchmarked schemes. As summarized in Table 5, Cyber-FSMS integrates governance, digital vulnerability assessment, mitigation, monitoring, verification, and recovery, thereby embedding cyber-risk management into all pillars of food defense [46,57,66].

Table 5.
Core components of the Cyber-FSMS framework.
3.3. Cyber-FSMS Components
- (i)
- Cyber-Context Scoping (Governance).
Systematic mapping of IT and operational technology (OT) assets—including SCADA/PLC, ERP platforms, and third-party data flows—must be conducted at the outset. Governance structures should assign clear roles and responsibilities for cyber defense, with executive-level oversight to align cyber measures with food safety objectives [67].
- (ii)
- Cyber-Vulnerability Assessment (C-VACCP).
Extending VACCP/TACCP to digital assets is essential. Cyber-FSMS adapts the Common Vulnerability Scoring System (CVSS v4.0) to rank threats according to exposure, criticality, and business impact [67,68,69,70,71]. Combining qualitative TACCP-style workshops with quantitative scoring enables balanced, risk-informed decision-making.
- (iii)
- Integrated Mitigation Controls.
Physical and digital safeguards must be harmonized. Measures include multi-factor authentication (MFA), network segmentation, secure remote access, anomaly detection in IoT data, and resilient backup systems. Digital control systems that are critical for food integrity should be classified as Operational Critical Control Points (OCCPs) [65,71].
- (iv)
- Monitoring and Detection.
Continuous surveillance requires Security Information and Event Management (SIEM) and Intrusion Detection Systems (IDS). Digital traceability standards such as GS1 EPCIS 2.0 enhance anomaly detection by linking event-based data to blockchain registries, thereby strengthening forensic traceability in recalls [72,73].
- (v)
- Verification and Reanalysis.
Cyber controls should be validated through penetration testing, red-team exercises, and scenario-based simulations. Plans must be reanalyzed periodically or after significant operational changes (e.g., supplier onboarding, software upgrades, mergers), consistent with FSMA’s intentional adulteration rule [74].
- (vi)
- Incident Response and Recovery.
Cyber-specific scenarios must be integrated into food recall and crisis management procedures. This includes regulatory reporting, partner communication, and fallback mechanisms such as cloud redundancy and secondary data centers. Defined playbooks for ransomware and supply-chain intrusions reduce downtime and ensure business continuity [12,56,75].
Figure 2 depicts the Cyber-FSMS cycle, which embeds cyber-specific measures into the six conventional FSMS pillars (Food Safety, Food Fraud, Food Defense, Food Terrorism, Agroterrorism, Food Security). By combining governance, prevention, detection, and recovery, Cyber-FSMS provides a holistic defense system that strengthens resilience against ransomware, blockchain tampering, and IoT-based manipulation [20,76].
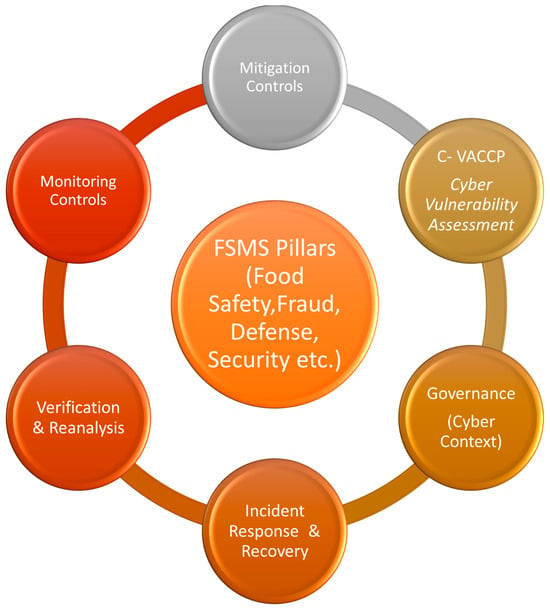
Figure 2.
Cyber-FSMS cycle: integration of cyber-specific measures into conventional FSMS pillars.
3.4. Emerging Challenges and Integration
While traditional FSMS frameworks have historically emphasized accidental contamination, modern food systems are increasingly shaped by complex and systemic shocks. Recent geopolitical crises, such as the Russia–Ukraine conflict, have demonstrated the strategic weaponization of food supplies, disrupting global grain exports and exacerbating price volatility and food insecurity [28,46,77]. Similarly, the COVID-19 pandemic exposed vulnerabilities of globalized supply chains, including labor shortages, logistics bottlenecks, and disrupted cross-border regulatory coordination [27,78]. These events confirm that food safety and defense cannot be considered in isolation from broader resilience strategies. As Fanzo and colleagues argue, achieving food security requires integrated, multi-scalar actions across food systems [79].
At the same time, the rapid digitalization of agri-food systems has created a new layer of vulnerabilities. Cyberattacks on SCADA/PLC systems, blockchain-based traceability platforms, and IoT-enabled cold-chain monitoring can simultaneously disrupt production, logistics, and consumer access [57,65]. Integrating cyber-risk management into FSMS—aligned with frameworks such as the NIST Cybersecurity Framework 2.0 and digital traceability standards like GS1 EPCIS 2.0, is essential to ensure both operational continuity and food integrity [62,63,72,79].
Addressing these challenges requires multi-sectoral collaboration among food safety experts, ICT specialists, policymakers, and international organizations. Only an interdisciplinary integration of expertise in food science, cybersecurity, and crisis management can ensure viable food systems under conditions of geopolitical instability, pandemics, and cyber-enabled disruptions. In parallel, rights-based frameworks such as food sovereignty highlight complementary pathways for strengthening local resilience and ecological stewardship [80]. Operationalizing these approaches depends on effective capacity building and knowledge transfer.
3.5. Capacity Building and Visual Tools
Effective implementation of FSMS—including the proposed Cyber-FSMS model—depends not only on regulatory alignment but also on capacity building and knowledge transfer across all supply chain actors. Regional studies (e.g., Indonesia and the South Pacific) illustrate how training and technical assistance can operationalize resilience within food system frameworks [63,81]. This is particularly critical for small and medium-sized enterprises (SMEs) and in developing regions, where institutional and technical capacities remain limited [52,82].
Key strategies for building resilience include:
- Targeted training programs covering both traditional TACCP/VACCP approaches and basic cyber hygiene practices, supported by certification bodies and industry associations.
- Low-cost digital toolkits for SMEs, offering vulnerability assessment templates, risk dashboards, and simplified monitoring solutions [64].
- Public–private partnerships and international coordination (e.g., EFSA crisis preparedness programs, WHO One Health initiatives) to organize joint preparedness exercises and scenario simulations [83].
- Visual tools, such as risk mapping dashboards, flow diagrams of supply chain f, and scenario-based visualization—can enhance comprehension of complex FSMS and Cyber-FSMS concepts, making them more accessible for operators with limited resources. Embedding cybersecurity literacy into food safety training is especially important, as many food operators lack awareness of digital vulnerabilities. Attention must also be paid to social dimensions, including gendered aspects of resilience in food systems, which shape household- and community-level food security outcomes [84,85,86].
By combining classical food defense education with ICT-focused modules, capacity building initiatives can strengthen preparedness and ensure that stakeholders across the chain are able to recognize, prevent, and respond to both physical and digital threats.
Food fraud is a complex and evolving challenge that affects not only economic stability but also consumer health, regulatory systems, and trust in the global food supply chain. Traditional food safety management approaches such as HACCP are designed to prevent unintentional hazards, whereas food fraud involves deliberate actions and therefore requires different preventive strategies such as TACCP and VACCP [1,87] Although awareness of food fraud has increased significantly in recent years, there remain critical gaps in surveillance and laboratory detection, particularly when fraudulent practices involve compounds not usually tested in specific foods.
A major difficulty lies in the laboratory detection of substances not routinely included in analytical protocols. Conventional testing panels often exclude unexpected contaminants, as was tragically illustrated during the 2008 melamine scandal in China, which caused widespread illness in infants before the adulterant was identified [9]. Recent studies highlight analytical advancements for detecting adulteration in specific food matrices, including dairy products such as kajmak [88], olive oil [89], and extra virgin olive oil [90]. Comparable challenges occur with unauthorized preservatives, such as sulfites, which are permitted in certain products like wine but banned in others such as meat [91]. Several studies and national inspections have confirmed cases of illicit sulfite use in minced meat and meat preparations, posing a risk to vulnerable consumers [92]. Because it is neither feasible nor cost-effective to screen every sample for thousands of potential compounds, detection strategies must shift towards risk-based and targeted approaches, supported by international data sharing and the identification of atypical patterns in food composition. In this context, advances in untargeted metabolomics, foodomics, and chemometric profiling provide promising tools to identify anomalies that may indicate fraud, even in the absence of predefined target compounds [93,94].
An additional layer of complexity involves compounds that naturally occur in food, where the line between natural presence and fraudulent addition is often blurred. For example, nitrates in spinach and other leafy vegetables vary significantly according to season, agricultural practices, and storage conditions, and levels sometimes exceed regulatory thresholds [95,96,97]. Similarly, phosphorus is naturally present in meat, but its levels can also be increased illegally through the addition of phosphates to improve water-holding capacity. Health risk assessments in different countries have highlighted the need to distinguish between natural phosphorus levels and those indicating illicit addition [98]. Differentiating such cases requires robust baseline data, validated threshold values, and advanced analytical techniques such as isotopic ratio analysis, which can provide additional evidence of origin and authenticity [99].
Given these challenges, effective fraud prevention must extend beyond analytical testing. Experts recommend that inspectors adopt intelligence-led and risk-prioritized strategies, focusing resources on high-risk commodities, trade anomalies, and products with a known history of fraud [12,87]. Early warning systems, enhanced international collaboration, and digital traceability tools are essential to detect fraudulent practices more efficiently. Practical approaches include the integration of VACCP-based vulnerability assessments, targeted screening for high-risk chemicals such as melamine and sulfites, and the use of rapid, non-destructive screening technologies (e.g., spectroscopy, portable biosensors) for preliminary checks, followed by confirmatory laboratory analyses [100,101].
Overall, food fraud detection cannot rely solely on routine laboratory analysis. Instead, it requires a multi-layered system that combines advanced science, targeted risk assessment, regulatory enforcement, and international collaboration. Such integrated strategies are essential to safeguard public health, maintain consumer confidence, and ensure resilience in the increasingly complex global food system.
4. Discussion
The findings of this review highlight both the progress and persistent gaps in global food defense approaches. A comparative analysis of mandatory and voluntary frameworks underscores a fundamental trade-off: prescriptive regulation ensures rigor but may overburden SMEs, while voluntary guidance is more accessible but unevenly adopted [1,85]. Integration of cyber threats into conventional food defense models remains inconsistent, leaving systemic vulnerabilities despite notable regulatory evolution. Synthesis of key patterns. Across the included studies and cases, three patterns are salient: (i) ransomware and supplier-side intrusions dominate cyber incidents affecting the agri-food sector; (ii) dependencies on third-party vendors amplify operational disruptions; and (iii) evidence is geographically skewed toward the US/EU/UK, with limited perspectives from low- and middle-income countries (LMICs). These patterns indicate that conventional food defense controls alone are insufficient to ensure continuity and integrity in increasingly digitalized supply chains and that targeted capacity building—especially beyond high-income contexts—remains a critical gap. Implications for capacity building. The limited LMIC representation is not merely a coverage artifact; it constrains generalizability and obscures context-specific needs (e.g., connectivity limitations, fragmented cold chains, and scarce OT security expertise). Strengthening capacity therefore requires low-cost toolkits, shared training resources, and public–private partnerships that can be scaled through sector associations and donor-supported programs.
4.1. Cyber Threats as Emerging Food Defense Challenges
Digitalization has transformed agri-food supply chains, but it has also introduced new classes of vulnerabilities. Ransomware and cyberattacks targeting IT/OT systems, cold-chain logistics, and blockchain platforms can halt production, paralyze distribution, and erode consumer trust [101,102,103,104,105,106,107]. Although PAS 96 [18] acknowledges cybercrime as a deliberate threat, most global frameworks remain reactive rather than preventive. Measures such as multifactor authentication, intrusion detection systems, and secure backups are technologically feasible, yet adoption is uneven and often constrained by cost and technical expertise, particularly among SMEs [1,107].
Emerging technologies including blockchain for traceability, IoT-based monitoring, and AI-driven risk detection offer promising opportunities [33,68,74,107,108,109]. However, implementation is skewed: large multinational enterprises have invested heavily in these tools, whereas smaller operators frequently lack the financial and technical resources to deploy them effectively [8,110,111].
As illustrated in Figure 3, ransomware and other cyber–physical threats can trigger cascading effects across production, logistics, and retail systems, ultimately compromising both food availability and consumer safety [56,72,81,111]. The diagram underscores the interdependencies between digital infrastructures and food system integrity, emphasizing why cyber resilience must become a core pillar of food defense [4,33].These systemic vulnerabilities underscore the urgency of embedding cyber resilience into food defense [8,23,30].
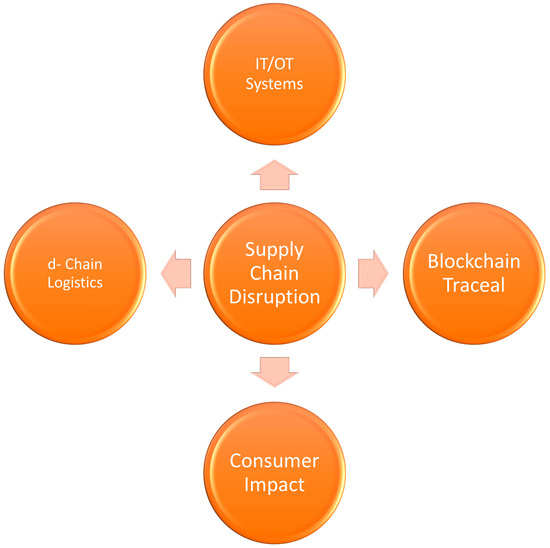
Figure 3.
Conceptual diagram of cyber–physical threats in agri-food systems.
At the same time, modern food defense frameworks are increasingly embracing digital technologies—including blockchain for enhanced traceability, sensor networks for real-time monitoring, and AI-driven risk assessments—to proactively detect vulnerabilities and respond swiftly across geographically dispersed supply chains [8,23,73,74,98]. When effectively deployed, these tools can counteract the very disruptions illustrated in Figure 3 by strengthening detection, transparency, and response capacities [1,63].
Integrating such technological innovations with existing regulatory standards and industry best practices offers a path toward resilient and adaptive food defense systems capable of addressing both traditional and emerging threats [1,105] This layered integration is conceptualized in Figure 4, which depicts food defense as an overlay to FSMS pillars (PRPs, HACCP, VACCP, TACCP), bridging physical and digital domains within a unified framework [15].
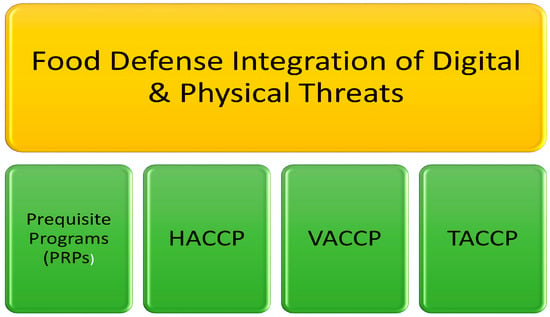
Figure 4.
Conceptual framework of food defense as an overlay to FSMS pillars (PRPs, HACCP, VACCP, TACCP), integrating both physical and digital threats.
4.2. Policy and Global Approaches (Consolidated)
The uneven integration of cyber-risk management into food safety systems highlights major gaps in both policy frameworks and industry practice [22,112,113]. In the United States, the Food Safety Modernization Act (FSMA) provides binding requirements for intentional adulteration, including vulnerability assessments and periodic reanalysis [13,14,78]. In contrast, the European Union’s General Food Law (EC 178/2002) sets broad principles for food safety but does not explicitly mandate food defense or cyber resilience [18,102]. The UK offers practical guidance through the Threat Assessment and Critical Control Points (TACCP) approach and acknowledges cybercrime as a deliberate threat, yet its adoption remains voluntary [18].
As summarized in Table 2, regulatory regimes differ in prescriptiveness and scope. Rather than re-stating framework details, we focus here on actionable levers to close the implementation gap—particularly for SMEs. Practical instruments include
- (i)
- Tax incentives or matching grants to offset the costs of essential OT/IT controls (e.g., MFA, network segmentation, secure backup);
- (ii)
- Regulatory sandboxes for piloting cyber-FSMS elements without immediate full compliance burdens;
- (iii)
- Tiered compliance models that align control maturity with facility risk profiles;
- (iv)
- Shared services (e.g., sectoral SOCs, incident-response playbooks) delivered via industry associations; and
- (v)
- Template-based documentation (threat mapping, C-VACCP scoring sheets, OCCP registers) to reduce administrative load.
Illustrative LMIC cases. For example, donor-supported food safety programs in export-oriented horticulture have combined TACCP training with basic cyber hygiene (e.g., credential management and backup routines) to sustain certification and market access. Similarly, cooperative-led cold-chain projects have adopted simple anomaly-logging checklists and incident-reporting trees to accelerate response without heavy tooling. Such cases suggest that modular, low-cost measures can materially improve resilience where advanced solutions are not yet feasible.
Globally, low- and middle-income countries (LMICs) face even greater barriers. Limited institutional capacity, scarce financial resources, and gaps in digital infrastructure constrain their ability to detect and mitigate intentional threats [27,96,110]. This asymmetry reinforces inequalities in food system resilience, widening the gap between high-income countries and LMICs.
For SMEs, full compliance with resource-intensive frameworks such as FSMA is often unattainable. Instead, practical steps for gradual Cyber-FSMS adoption include:
- Incremental integration of cyber hygiene into HACCP/TACCP programs (e.g., MFA, staff awareness, secure backups).
- Adoption of low-cost digital traceability tools (e.g., GS1 EPCIS 2.0, cloud-based inventory systems) [60].
- Participation in industry-led training and public–private knowledge-sharing platforms that lower costs and build expertise collectively [3,63].
- Leveraging voluntary guidelines such as PAS 96 as a stepping-stone toward more comprehensive compliance [18].
These measures are feasible for SMEs and create a pathway toward broader Cyber-FSMS adoption without disproportionate burdens.
Certification-driven schemes under the Global Food Safety Initiative (GFSI) [68], including BRCGS, IFS, and FSSC 22000, require food defense documentation but provide little explicit coverage of cyber–physical threats [17,53,73]. This regulatory diversity creates uncertainty for multinational operators and leads to uneven adoption, especially among small and medium-sized enterprises (SMEs) [8,51]. Implementation is further limited by financial and technical barriers. SMEs often lack the resources to adopt advanced cyber controls such as IEC 62443-based industrial security standards or the NIST Cybersecurity Framework (CSF 2.0) [63,64,104]. Without targeted incentives, technical assistance, and public–private partnerships, the digital divide between large corporations and SMEs will deepen, leaving critical parts of the food system vulnerable [22,81,106,107,108,113].
Overall, the diversity of regulatory regimes and resource asymmetries underscores the urgency of integrating cyber-risk into food defense [22,111]. Practical incentives, scalable tools, and international alignment through the proposed Cyber-FSMS can support more equitable and resilient global food supply chains
4.3. Future Research and Implementation Pathways
Operationalizing Cyber-FSMS. Translating these findings into practice requires embedding six concise steps into existing FSMS: governance and scoping (asset maps, roles), C-VACCP (digital vulnerability analysis), integrated mitigation (MFA, segmentation, OCCPs), monitoring and detection (logs, IDS/SIEM, event-based traceability), verification and re-analysis (tests, drills, change-triggered reviews), and incident response and recovery (playbooks, backup and restore). This provides a proportional pathway for SMEs while aligning with more advanced implementations in larger organizations [22,105,111].
Future Research Directions:
- Operational evidence. Implement and evaluate Cyber-FSMS in diverse facility types (including SMEs) with before-and-after metrics (e.g., MTTR, downtime at OCCPs, recall traceability times) [22,46,56,67,111].
- Economic evaluation. Compare costs of preparedness bundles (e.g., MFA + segmentation + backups) against the economic impact of realistic cyber incidents to inform policy and resource allocation [14,22,102].
- One Health integration. Examine governance models that link biological, chemical, zoonotic, and cyber risks to support holistic resilience [20,77,113].
- Equity and social dimensions. Investigate how gender, equity, and local sovereignty interact with digital vulnerabilities to design inclusive adoption pathways [34,63,82].
4.4. Applications and Implications
The proposed Cyber-FSMS can be operationalized through a structured six-step blueprint:
- (i)
- Governance: mapping of IT/OT assets and clear alignment of cyber defense responsibilities within food safety governance structures
- (ii)
- C-VACCP workshops that integrate qualitative TACCP analysis with quantitative CVSS scoring;
- (iii)
- Identification of Operational Critical Control Points (OCCPs) for digital assets such as SCADA systems, ERP platforms, and blockchain traceability nodes;
- (iv)
- Deployment of technical controls including multi-factor authentication, network segmentation, and patch management;
- (v)
- continuous monitoring using SIEM/IDS tools combined with EPCIS 2.0 traceability events; and
- (vi)
- Regular incident response exercises that include cyberattack and contamination simulations.
For small and medium-sized enterprises (SMEs), scaled-down versions of this model can be developed, focusing on essential controls and low-cost solutions, supported by industry associations and certification bodies. As shown in Table 6, Cyber-FSMS integrates classical food defense measures with digital safeguards, bridging governance, vulnerability assessment, and incident recovery [46,57,73,104,113].

Table 6.
Cyber-FSMS components and their role.
This structured summary highlights how each component contributes to a resilient and adaptive food defense system. Similarly, Uršulin-Trstenjak et al. [99] showed that applying foodomics approaches in elderly homes can detect simultaneous exposure to mycotoxins, antinutrients, and chemical hazards. Such findings suggest that OCCPs within a Cyber-FSMS should not only cover SCADA or ERP systems but also sensor-based monitoring of environmental and chemical risks [101,112,113].
Another relevant dimension of food fraud involves undetected chemical adulterants, such as melamine or unauthorized preservatives. Routine analytical programs often exclude rare or unexpected compounds, increasing the risk of undetected fraud. For example, sulfites—allowed in wine are prohibited in meat, yet misuse still occurs. Fusarium-derived mycotoxins such as zearalenone further illustrate the complexity of chemical hazards, as they can enter the food chain through contaminated crops and require targeted screening strategies [105]. Because full-spectrum chemical analysis is cost-prohibitive, targeted screening based on risk profiling and intelligence-led sampling is essential [88,100,114]. In addition to these targeted measures, Euratom legislation provides complementary safeguards for radiological protection in food and feed. These regulations define maximum permitted levels of radioactive contamination and establish emergency preparedness measures applicable in the event of nuclear accidents or radiological emergencies [115,116].
Moreover, the Rapid Alert System for Food and Feed (RASFF) operates as a key EU-wide mechanism for early detection, information sharing, and coordinated management of food safety incidents, enhancing resilience and transparency across the agri-food supply chain [117].
Inspectors should apply vulnerability mapping and intelligence-sharing to prioritize high-risk commodities and ingredients.
5. Future Research Directions and Limitations
This review has several limitations. First, it relied primarily on English-language sources, which may bias the representation of global practices. Second, much of the available literature is with limited empirical data on real-world implementation. Third, the review is weighted toward the U.S., EU, and UK, with relatively scarce evidence from LMICs. These gaps underscore the need for future empirical research, particularly case studies of SMEs and developing regions, to validate the practical applicability of Cyber-FSMS.
Future research should focus on:
- (i)
- Standardizing C-VACCP methodologies, combining TACCP-style qualitative workshops with quantitative CVSS scoring for cyber assets [113].
- (ii)
- Validating OCCPs across different food sectors (dairy, meat, fresh produce) to determine critical digital control points [73].
- (iii)
- Assessing the interoperability of food defense frameworks with international cybersecurity standards [63,80].
- (iv)
- Evaluating the effectiveness of GS1 EPCIS 2.0 for forensic traceability in recall scenarios. In addition, chemical hazard case studies such as hop mycotoxin monitoring in Central Europe provide valuable models for testing how digital traceability tools could accelerate recall and root-cause analysis [102,105,108,109,114].
- (v)
- Developing cost-effective SME toolkits to lower entry barriers for integrated food-cyber defense [22,105].
- (vi)
- Designing and testing cross-sector preparedness exercises, coordinated by regulatory bodies such as EFSA and WHO, to simulate combined physical and cyber food defense incidents.
These directions will support the operationalization of Cyber-FSMS and contribute to harmonized, resilient food defense systems worldwide [27,46,102,111].
6. Conclusions
A comprehensive and proactive approach to food defense is essential for safeguarding the integrity and resilience of modern food supply chains. Awareness of intentional contamination risks must extend across the entire chain—from primary production and processing, through distribution and retail, to the final consumer. This also includes the protection of authenticity schemes such as Geographical Indications, which, when embedded into Cyber-FSMS, provide dual protection against both contamination and fraud.
Food defense must address both intentional adulteration and naturally occurring contaminants. Embedding multidimensional hazard monitoring into Cyber-FSMS therefore strengthens resilience against both inadvertent and deliberate threat.
Integrating food defense into national and international legal frameworks, supported by science-based standards, is crucial for reducing vulnerabilities to intentional contamination and protecting public health, economic stability, and consumer trust. However, regulatory gaps remain, particularly in the EU, where binding food defense legislation lags behind evolving threats, exposing cross-border supply chains to risks.
The proposed Cyber-FSMS framework contributes to closing these gaps by embedding cyber-risk management within existing FSMS pillars. This integration positions cyber-resilience as an indispensable element of food defense in increasingly digitalized supply chains, addressing vulnerabilities such as ransomware, IoT manipulation, and blockchain tampering.
Ultimately, sustaining safe, resilient, and trustworthy food systems requires a collective commitment of all stakeholders. Embedding food defense—augmented by digital and cyber- resilience—into harmonized regulatory frameworks and scientific best practices is essential for effectively countering both traditional and emerging threats.
Supplementary Materials
The following supporting information can be downloaded at: https://www.mdpi.com/article/10.3390/app152011020/s1. File S1: PRISMA 2020 Checklist; Supplementary File S2.
Author Contributions
Conceptualization, N.P.B., N.U.-T., B.Š. and I.D.Š.; methodology, N.P.B. and I.D.Š.; software, B.Š. and I.D.Š.; investigation, N.P.B., N.U.-T., B.Š. and I.D.Š.; resources, B.Š.; data curation, N.P.B. and I.D.Š.; writing—original draft preparation, N.P.B. and I.D.Š.; writing—review and editing, N.U.-T. and I.D.Š.; visualization, I.D.Š.; supervision, B.Š. and N.U.-T.; funding acquisition, B.Š. and N.U.-T. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
No new data were created or analyzed in this study. Data sharing is not applicable to this article.
Conflicts of Interest
Nina Puhač Bogadi was employed by the company Podravka Inc. The remaining authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
References
- Manning, L.; Soon, J.M. Food Safety, Food Fraud, and Food Defense: A Fast Evolving Literature. J. Food Sci. 2016, 81, 823–834. [Google Scholar] [CrossRef] [PubMed]
- Mettenleiter, T.C.; Markotter, W.; Charron, D.F.; Adisasmito, W.B.; Almuhairi, S.; Behravesh, C.B.; Bilivogui, P.; Bukachi, S.A.; Casas, N.; Becerra, N.C.; et al. The One Health High-Level Expert Panel (OHHLEP). One Health Outlook 2023, 5, 18. [Google Scholar] [CrossRef] [PubMed]
- FAO; UNEP; WHO; WOAH. One Health Joint Plan of Action, 2022–2026: Working Together for the Health of Humans, Animals, Plants and the Environment; WHO: Geneva, Switzerland, 2022. [Google Scholar]
- Ivanov, D. Supply Chain Viability and the COVID-19 Pandemic: A Conceptual and Formal Generalisation of Four Major Adaptation Strategies. Int. J. Prod. Res. 2021, 59, 3535–3552. [Google Scholar] [CrossRef]
- Mirabelli, G.; Solina, V. Blockchain and Agricultural Supply Chains Traceability: Research Trends and Future Challenges. Procedia Manuf. 2020, 42, 414–421. [Google Scholar] [CrossRef]
- FAO. The Future of Food and Agriculture: Trends and Challenges; Food and Agriculture Organization of the United Nations: Rome, Italy, 2017. [Google Scholar]
- Calicioglu, O.; Flammini, A.; Bracco, S.; Bellù, L.; Sims, R. The Future Challenges of Food and Agriculture: An Integrated Analysis of Trends and Solutions. Sustainability 2019, 11, 222. [Google Scholar] [CrossRef]
- Roosevelt, M.; Raile, E.D.; Anderson, J.R. Resilience in Food Systems: Concepts and Measurement Options in an Expanding Research Agenda. Agronomy 2023, 13, 444. [Google Scholar] [CrossRef]
- Gossner, C.M.E.; Schlundt, J.; Ben Embarek, P.; Hird, S.; Lo-Fo-Wong, D.; Beltran, J.J.O.; Teoh, K.N.; Tritscher, A. The Melamine Incident: Implications for International Food and Feed Safety. Environ. Health Perspect. 2009, 117, 1803–1808. [Google Scholar] [CrossRef]
- EFSA. Shiga Toxin-Producing E. coli (STEC) O104:H4 2011 Outbreaks in Europe: Taking Stock. EFSA J. 2011, 9, 2390. [Google Scholar] [CrossRef]
- The Guardian. US Meatpacking Plants Get Back on Stream after Crippling Cyber-Attack. 2 June 2021. Available online: https://www.theguardian.com/food/2021/jun/02/cyber-attack-targets-worlds-largest-meat-processing-company (accessed on 29 August 2025).
- WHO. Terrorist Threats to Food: Guidance for Establishing and Strengthening Prevention and Response Systems; WHO: Geneva, Switzerland, 2002; Available online: https://apps.who.int/iris/handle/10665/42619 (accessed on 22 November 2022).
- U.S. Code of Federal Regulations. Mitigation Strategies to Protect Food Against Intentional Adulteration (21 CFR Part 121). 2025. Available online: https://www.ecfr.gov/current/title-21/chapter-I/subchapter-B/part-121 (accessed on 18 August 2025).
- U.S. FDA. Background on the FDA Food Safety Modernization Act (FSMA). 2022. Available online: https://www.fda.gov/food/food-safety-modernization-act-fsma/background-fda-food-safety-modernization-act-fsma (accessed on 28 November 2022).
- European Commission. Health and Food Safety 2023—Annual Report on Monitoring the Application of EU Law. 2023. Available online: https://commission.europa.eu/law/application-eu-law/implementing-eu-law/infringement-procedure/2023-annual-report-monitoring-application-eu-law/health-and-food-safety-2023_en (accessed on 29 August 2025).
- European Parliament and Council. Regulation (EC) No 178/2002 (General Food Law). 2002. Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/PDF/?uri=CELEX:32002R0178 (accessed on 15 October 2022).
- GFSI. Benchmarking Requirements Part I: The GFSI Benchmarking Process; GFSI: Levallois-Perret, France, 2020. [Google Scholar]
- BSI. PAS 96: Guide to Protecting and Defending Food and Drink from Deliberate Attack; BSI: Yokohama, Japan, 2017; Available online: https://www.bsigroup.com/en-ID/pas-96-food-defence/ (accessed on 27 December 2022).
- Smart Food Safe. Exploring the Concepts of HACCP, TACCP & VACCP. 2025. Available online: https://smartfoodsafe.com/haccp-taccp-vaccp/ (accessed on 15 September 2025).
- Béné, C. Resilience of Local Food Systems and Links to Food Security—A Review of Some Important Concepts in the Context of COVID-19 and Other Shocks. Food Secur. 2020, 12, 805–822. [Google Scholar] [CrossRef]
- Botschner, J.; Corley, C.; Fraser, E.D.G.; Kotak, R.; McMahon, D.; Newman, L. Cybersecurity in Digital Agriculture: A National Security Risk? In Advances in Science, Technology & Security Applications; Springer: Berlin/Heidelberg, Germany, 2024; pp. 281–315. [Google Scholar] [CrossRef]
- ENISA. Report on the State of the Cybersecurity in the Union. 2024. Available online: https://www.enisa.europa.eu/publications/2024-report-on-the-state-of-the-cybersecurity-in-the-union (accessed on 29 August 2025).
- TQCSI. Food Defence & Food Fraud: VACCP Food Fraud Plan & TACCP Food Defence. 2025. Available online: https://www.tqcsi.com/resources/food-defence-food-fraud (accessed on 15 September 2025).
- Bogadi, N.P.; Banović, M.; Babić, I. Food Defence System in Food Industry: Perspective of the EU Countries. J. Consum. Prot. Food Saf. 2016, 11, 217–226. [Google Scholar] [CrossRef]
- U.S. Food and Drug Administration. Food Safety Modernization Act (FSMA). 2025. Available online: https://www.fda.gov/food/guidance-regulation-food-and-dietary-supplements/food-safety-modernization-act-fsma (accessed on 29 September 2025).
- GFSI. Position Paper on Mitigating the Public Health Risk of Food Fraud; GFSI: Levallois-Perret, France, 2014. [Google Scholar]
- Adewusi, A.O.; Chiekezie, N.R.; Eyo-Udo, N.L. Cybersecurity Threats in Agriculture Supply Chains: A Comprehensive Review. World J. Adv. Res. Rev. 2022, 15, 490–500. [Google Scholar] [CrossRef]
- FAO. Note on the Impact of the War on Food Security in Ukraine; FAO: Rome, Italy, 2022. [Google Scholar]
- Kimball, A.M. Risky Trade; Routledge: London, UK, 2016. [Google Scholar]
- Ivanov, D.; Dolgui, A. Viability of Intertwined Supply Networks: Extending the Supply Chain Resilience Angles towards Survivability—A Position Paper Motivated by COVID-19 Outbreak. Int. J. Prod. Res. 2020, 58, 2904–2915. [Google Scholar] [CrossRef]
- Seebeck, L. Responding to Systemic Crisis: The Case of Agroterrorism. Stud. Confl. Terror. 2007, 30, 691–721. [Google Scholar] [CrossRef]
- FAO. The State of Food Security and Nutrition in the World; FAO: Rome, Italy, 2020; ISBN 9789251329016. [Google Scholar]
- Engler-Stringer, R. Food Security. In Encyclopedia of Quality of Life and Well-Being Research; Springer: Berlin/Heidelberg, Germany, 2014. [Google Scholar]
- Hassen, T.B.; Bilali, H.E. Food Security in the Gulf Cooperation Council Countries: Challenges and Prospects. J. Food Secur. 2019, 7, 159–169. [Google Scholar] [CrossRef]
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. The PRISMA 2020 Statement: An Updated Guideline for Reporting Systematic Reviews. BMJ 2021, 372, n71. [Google Scholar] [CrossRef]
- Khan, M.; Ahmed, S.; Bhattacharjee, R. AI and Blockchain in Critical Food Supply Infrastructure: Cybersecurity Threats and Solutions. Comput. Fraud Secur. 2024, 2024, 95–105. [Google Scholar] [CrossRef]
- OECD Publishing. OECD-FAO Agricultural Outlook 2021–2030; OECD: Paris, France, 2025; Available online: https://www.oecd.org/en/publications/oecd-fao-agricultural-outlook-2021-2030_19428846-en.html (accessed on 29 August 2025).
- U.S. FDA. Mitigation Strategies to Protect Food Against Intentional Adulteration (Final Rule); U.S. FDA: Silver Spring, MD, USA, 2024.
- McHugh, M.L. Interrater Reliability: The Kappa Statistic. Biochem. Medica 2012, 22, 276–282. [Google Scholar] [CrossRef]
- Ouzzani, M.; Hammady, H.; Fedorowicz, Z.; Elmagarmid, A. Rayyan—A Web and Mobile App for Systematic Reviews. Syst. Rev. 2016, 5, 210. [Google Scholar] [CrossRef]
- Shea, B.J.; Reeves, B.C.; Wells, G.; Thuku, M.; Hamel, C.; Moran, J.; Moher, D.; Tugwell, P.; Welch, V.; Kristjansson, E.; et al. AMSTAR 2: A Critical Appraisal Tool for Systematic Reviews That Include Randomised or Non-Randomised Studies of Healthcare Interventions, or Both. BMJ 2017, 358, j4008. [Google Scholar] [CrossRef] [PubMed]
- Lindgren, K.-A.; Lang, T. Food Security and the Fractured Consensus on Food Resilience: An Analysis of Development Agency Narratives; Palgrave Macmillan: Cham, Switzerland, 2023. [Google Scholar] [CrossRef]
- Hong, Q.N.; Fàbregues, S.; Bartlett, G.; Boardman, F.; Cargo, M.; Dagenais, P.; Gagnon, M.P.; Griffiths, F.; Nicolau, B.; O’Cathain, A.; et al. The Mixed Methods Appraisal Tool (MMAT) Version 2018 for Information Professionals and Researchers. Educ. Inf. 2018, 34, 285–291. [Google Scholar] [CrossRef]
- U.S. Food and Drug Administration. An Overview of the CARVER + Shock Method for Food Sector Vulnerability Assessments. 2022. Available online: https://www.fda.gov/food/food-defense-initiatives/carver-shock-primer (accessed on 10 November 2022).
- Gajdić, D. Definition and Characteristics of Short Agri-Food Supply Chains for Products. Econ. Thought Pract. 2019, 28, 381–408. [Google Scholar]
- Mottaleb, K.A.; Kruseman, G.; Snapp, S. Potential Impacts of Ukraine-Russia Armed Conflict on Global Wheat Food Security: A Quantitative Exploration. Glob. Food Sec. 2022, 35, 100659. [Google Scholar] [CrossRef]
- James. 8 Recent Cyber Attacks on Food Production and Agriculture. WISDIAM. 2025. Available online: https://wisdiam.com/publications/recent-cyber-attacks-food-agriculture-sector/ (accessed on 29 August 2025).
- Orton, E. Get Ready for Cyber-Attacks on Global Food Supplies. WIRED, 15 February 2022. [Google Scholar]
- Mentzer, J.T.; DeWitt, W.; Keebler, J.S.; Min, S.; Nix, N.W.; Smith, C.D.; Zacharia, Z.G. Defining Supply Chain Management. J. Bus. Logist. 2001, 22, 1–25. [Google Scholar] [CrossRef]
- EFSA. Food Incident Preparedness and Response. 2025. Available online: https://www.efsa.europa.eu/en/topics/topic/food-incident-preparedness-and-response (accessed on 29 August 2025).
- OECD; FAO. OECD-FAO Guidance for Responsible Agricultural Supply Chains; OECD Publishing: Paris, French, 2016. [Google Scholar] [CrossRef]
- Caprile, A. EPRS—European Parliamentary Research Service: PE 729.367; Members’ Research Service: Brussels, Belgium, 2022; Available online: https://www.europarl.europa.eu/ReData/etudes/ATAG/2022/729367/EPRS_ATA(2022)729367_EN.pdf (accessed on 16 September 2025).
- Okupa, H. Cybersecurity and the Future of Agri-Food Industries. Master’s Thesis, Kansas State University, Manhattan, KS, USA, 2020. Available online: https://krex.k-state.edu/items/b0df534a-11cf-48b2-94a3-41e94ab64515 (accessed on 16 September 2025).
- Ingemundsen, A.A. Cyber Security Risks in Norwegian Agriculture and the Influence on National Food Security. Master’s Thesis, UiT The Arctic University of Norway, Tromsø, Norway, 2025. Available online: https://hdl.handle.net/10037/37890 (accessed on 15 September 2025).
- BRCGS. Global Standard for Food Safety; BRCGS: London, UK, 2022. [Google Scholar]
- IFS. IFS Food Standard Version 8—Doctrine v4 (EN). 2025. Available online: https://www.ifs-certification.com/images/ifs_documents/IFS_Food_v8_doctrine_v4_EN.pdf (accessed on 29 August 2025).
- Food Safety Magazine Editorial Team. GFSI Releases Benchmarking Requirements Version 2024. Food Safety Magazine, 20 December 2024. Available online: https://www.food-safety.com/articles/10028-gfsi-releases-benchmarking-requirements-version-2024 (accessed on 15 September 2025).
- Sayegh, E. Cyberattack on Whole Foods Supplier Disrupts Supply Chain—Again. Forbes, 19 June 2025. Available online: https://www.forbes.com/sites/emilsayegh/2025/06/19/cyberattack-on-whole-foods-supplier-disrupts-food-supply-chain-again/ (accessed on 29 August 2025).
- Reuters. Whole Foods Supplier United Natural Foods Says Cyber Incident Disrupted Operations. 2025. Available online: https://www.reuters.com/business/whole-foods-supplier-united-natural-foods-says-cyber-incident-disrupted-2025-06-09/ (accessed on 9 June 2025).
- Cybersecurity Dive. UNFI Cyberattack Disrupted Grocery Distribution and Reduced Earnings. 2025. Available online: https://www.cybersecuritydive.com/news/unfi-cyberattack-reduce-quarterly-earnings/751849/ (accessed on 10 June 2025).
- FoodNavigator. Whole Foods Supplier UNFI Hit by Cyberattack Causing Distribution Delays. 2025. Available online: https://www.foodnavigator.com/Article/2025/06/11/wholefoods-supplier-unfi-hit-by-cyber-attack/ (accessed on 11 June 2025).
- International Society of Automation (ISA). ISA/IEC 62443 Series of Standards—The World’s Only Consensus-Based Automation and Control Systems Cybersecurity Standards. 2025. Available online: https://www.isa.org/standards-and-publications/isa-standards/isa-iec-62443-series-of-standards (accessed on 15 September 2025).
- NIST. The NIST Cybersecurity Framework (CSF) 2.0; National Institute of Standards and Technology, U.S. Department of Commerce: Gaithersburg, MD, USA, 2024. Available online: https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.29.pdf (accessed on 28 August 2025).
- GS1. EPCIS and CBV Implementation Guideline: Using EPCIS & CBV to Increase Supply Chain Visibility. 2022. Available online: https://www.gs1.org/docs/epc/EPCIS_Guideline.pdf (accessed on 15 September 2025).
- Wamba; Fosso, S.; Queiroz, M.M. Blockchain in Operations and Supply Chain Management: Benefits, Challenges and Future Research Opportunities. Int. J. Inf. Manag. 2020, 52, 102064. [Google Scholar] [CrossRef]
- Kamilaris, A.; Fonts, A.; Prenafeta-Boldú, F.-X. The Rise of Blockchain Technology in Agriculture and Food Supply Chains. Trends Food Sci. Technol. 2019, 91, 640–652. [Google Scholar] [CrossRef]
- Humayed, A.; Lin, J.; Li, F.; Luo, B. Cyber-Physical Systems Security—A Survey. IEEE Internet Things J. 2017, 4, 1802–1831. [Google Scholar] [CrossRef]
- GFSI. Benchmarking Requirements Part IV: Glossary of Terms; GFSI: Levallois-Perret, France, 2024. [Google Scholar]
- FIRST. Common Vulnerability Scoring System Version 4.0: Specification Document. 2023. Available online: https://www.first.org/cvss/v4-0/specification-document (accessed on 15 September 2025).
- Zahid, M.; Inayat, I.; Daneva, M.; Mehmood, Z.H. Security Risks in Cyber-Physical Systems—A Systematic Mapping Study. J. Softw. Evol. Process 2021, 33, e2346. [Google Scholar] [CrossRef]
- Zografopoulos, I.; Ospina, J.; Liu, X.; Konstantinou, C. Cyber-Physical Energy Systems Security: Threat Modeling, Risk Assessment, Resources, Metrics, and Case Studies. IEEE Access 2021, 9, 29775–29818. [Google Scholar] [CrossRef]
- Tantawy, A.; Abdelwahed, S.; Erradi, A.; Shaban, K. Model-Based Risk Assessment for Cyber-Physical Systems Security. Comput. Secur. 2020, 96, 101864. [Google Scholar] [CrossRef]
- Feng, H.; Wang, X.; Duan, Y.; Zhang, J.; Zhang, X. Applying Blockchain Technology to Improve Agri-Food Traceability: A Review of Development Methods, Benefits and Challenges. J. Clean. Prod. 2022, 355, 131750. [Google Scholar] [CrossRef]
- Zetter, K. Inside the Cunning, Unprecedented Hack of Ukraine’s Power Grid. WIRED. 2016. Available online: https://www.wired.com/2016/03/inside-cunning-unprecedented-hack-ukraines-power-grid/ (accessed on 15 September 2025).
- Tian, F. An Agri-Food Supply Chain Traceability System for China Based on RFID & Blockchain Technology. In Proceedings of the 2016 13th International Conference on Service Systems and Service Management (ICSSSM 2016), Kunming, China, 24–26 June 2016. [Google Scholar] [CrossRef]
- U.S. FDA. Mitigation Strategies to Protect Food Against Intentional Adulteration. Final Rule Fed. Regist. 2016, 81, 34165–34223. [Google Scholar]
- Linkov, I.; Trump, B.D. The Science and Practice of Resilience. In Springer Handbooks: Risk, Systems and Decisions; Springer: Cham, Switzerland, 2019. [Google Scholar]
- Welsh, C. The Russia-Ukraine War and Global Food Security: A Seven-Week Assessment, and the Way Forward for Policymakers; Center for Strategic and International Studies: Washington, DC, USA, 2022. [Google Scholar]
- Laborde, D.; Martin, W.; Swinnen, J.; Vos, R. COVID-19 Risks to Global Food Security. Science 2020, 369, 500–502. [Google Scholar] [CrossRef]
- Hobbs, J.E. Food Supply Chains during the COVID-19 Pandemic. Can. J. Agric. Econ. 2020, 68, 171–176. [Google Scholar] [CrossRef]
- Wittman, H. Food Sovereignty: A New Rights Framework for Food and Nature? Environ. Soc. 2011, 2, 87–105. [Google Scholar] [CrossRef]
- Bellotti, W.; Ingram, J. Enhancing Capacity of Scientists and Practitioners for Promoting More Sustainable and Resilient Food Systems in Indonesia and the South Pacific. APN Sci. Bull. 2022, 12, 161–171. [Google Scholar] [CrossRef]
- Upton, J.; Avîrvarei, A.C.; Bottex, B.; Georganas, A.; Georgiev, M.; Johnson, J.; Gkrintzali, G. 2023 Crisis Preparedness Training: Annual Report; EFSA Supporting Publications 20; European Food Safety Authority: Parma, Italy, 2023. [Google Scholar] [CrossRef]
- Caron, P.; Daguet, E.; Dury, S. The Global Food System Is Not Broken but Its Resilience Is Threatened. In Resilience and Food Security in a Food Systems Context; Palgrave Macmillan: Cham, Switzerland, 2023; pp. 53–79. ISBN 978-3-031-23535-1. [Google Scholar]
- Bryan, E.; Ringler, C.; Meinzen-Dick, R. Gender, Resilience, and Food Systems. In Resilience and Food Security in a Food Systems Context; Palgrave Macmillan: Cham, Switzerland, 2023; pp. 239–280. [Google Scholar] [CrossRef]
- TCI Systems. IFS Food Standard Version 7—Food Safety Systems (Blog). 2025. Available online: https://tcisys.com/blog/ifs-food-standard-version-7/ (accessed on 29 August 2025).
- van Ruth, S.M.; Huisman, W.; Luning, P.A. Food Fraud Vulnerability and Its Key Factors. Trends Food Sci. Technol. 2017, 67, 70–75. [Google Scholar] [CrossRef]
- Radovanovic, M.; Hovjecki, M.; Simunovic, S.; Miocinovic, J. Detection of milk fat adulteration with margarine and palm oil in kajmak. Mljekarstvo 2025, 75, 91–101. [Google Scholar] [CrossRef]
- Aparicio, R.; Morales, M.T. Detection of Olive Oil Adulteration. Trends Food Sci. Technol. 2019, 91, 262–272. [Google Scholar] [CrossRef]
- Meenu, M.; Cai, Q.; Xu, B. A Critical Review on Analytical Techniques to Detect Adulteration of Extra Virgin Olive Oil. Trends Food Sci. Technol. 2019, 91, 391–408. [Google Scholar] [CrossRef]
- Knežević, N.; Palfi, M.; Vrandečić, K.; Šarkanj, I.D.; Ćosić, J. Quality Labels on Agricultural and Food Products. Meso 2021, 23, 420. [Google Scholar] [CrossRef]
- Mičović, E.; Mantovani, A.; Jevšnik, M. Risk Management and Risk Communication of an Illegal Use of Sulphites in Meat Preparations. Sanit. Inženirstvo Int. J. Sanit. Eng. Res. 2023, 16, 23–39. [Google Scholar] [CrossRef]
- Medić, A.; Medana, C. Advances in Food Metabolomics. Appl. Sci. 2025, 15, 8283. [Google Scholar] [CrossRef]
- Zhang, S.; Chen, J.; Gao, F.; Su, W.; Li, T.; Wang, Y. Foodomics as a Tool for Evaluating Food Authenticity and Safety from Field to Table: A Review. Foods 2025, 14, 15. [Google Scholar] [CrossRef]
- Iammarino, M.; Di Taranto, A.; Cristino, M. Monitoring of Nitrites and Nitrates Levels in Leafy Vegetables (Spinach and Lettuce): A Contribution to Risk Assessment. J. Sci. Food Agric. 2014, 94, 773–778. [Google Scholar] [CrossRef]
- Martín León, V.; Luzardo, O.P. Evaluation of Nitrate Contents in Regulated and Non-Regulated Leafy Vegetables of High Consumption in the Canary Islands, Spain: Risk Assessment. Food Chem. Toxicol. 2020, 146, 111812. [Google Scholar] [CrossRef] [PubMed]
- Stagnari, F.; Polilli, W.; Campanelli, G.; Platani, C.; Trasmundi, F.; Scortichini, G.; Galieni, A. Nitrate Content Assessment in Spinach: Exploring the Potential of Spectral Reflectance in Open Field Experiments. Agronomy 2023, 13, 193. [Google Scholar] [CrossRef]
- Milešević, J.; Vranić, D.; Gurinović, M.; Korićanac, V.; Borović, B.; Zeković, M.; Šarac, I.; Milićević, D.R.; Glibetić, M. The Intake of Phosphorus and Nitrites through Meat Products: A Health Risk Assessment of Children Aged 1 to 9 Years Old in Serbia. Nutrients 2022, 14, 242. [Google Scholar] [CrossRef]
- Uršulin-Trstenjak, N.; Šarkanj, I.D.; Sajko, M.; Vitez, D.; Živoder, I. Determination of the Personal Nutritional Status of Elderly Populations Based on Basic Foodomics Elements. Foods 2021, 10, 2391. [Google Scholar] [CrossRef]
- WHO; FAO; OIE/WOAH. Taking a Multisectoral, One Health Approach: A Tripartite Guide to Addressing Zoonotic Diseases in Countries; WHO: Geneva, Switzerland, 2019. [Google Scholar]
- Šarkanj, B.; Šarkanj, I.D.; Shamtsyan, M. Mycotoxins in Food—How to Prevent and What to Do When Things Go Bad. E3S Web Conf. 2020, 215, 01004. [Google Scholar] [CrossRef]
- Pourmadadkar, M.; Lezzi, M.; Corallo, A. Cyber Security for Cyber-Physical Systems in Critical Infrastructures: Bibliometrics Analysis and Future Directions. IEEE Trans. Eng. Manag. 2024, 71, 15405–15421. [Google Scholar] [CrossRef]
- Bowcut, S. Shielding the Supply: Cybersecurity in Food and Agriculture. Cybersecurity Guide. 2025. Available online: https://cybersecurityguide.org/industries/food-and-agriculture/ (accessed on 15 September 2025).
- Kulkarni, A.; Wang, Y.; Gopinath, M.; Sobien, D.; Rahman, A.; Batarseh, F.A. A Review of Cybersecurity Incidents in the Food and Agriculture Sector. J. Agric. Food Res. 2025, 14, 102245. [Google Scholar] [CrossRef]
- Rai, A.; Das, M.; Tripathi, A. Occurrence and Toxicity of a Fusarium Mycotoxin, Zearalenone. Crit. Rev. Food Sci. Nutr. 2020, 60, 2710–2729. [Google Scholar] [CrossRef]
- Boyes, H.; Isbell, R.; Watson, T. Critical Infrastructure in the Future City: Developing Secure and Resilient Cyber-Physical Systems. Lect. Notes Comput. Sci. 2016, 8985, 13–23. [Google Scholar] [CrossRef]
- Grady, C.; Rajtmajer, S.; Dennis, L. When Smart Systems Fail: The Ethics of Cyber-Physical Critical Infrastructure Risk. IEEE Trans. Technol. Soc. 2021, 2, 6–14. [Google Scholar] [CrossRef]
- Rose, D.C.; Wheeler, R.; Lobley, M.; Chivers, C.A. Agriculture 4.0: Making It Work for People, Production, and the Planet. Land Use Policy 2021, 100, 104933. [Google Scholar] [CrossRef]
- Dutta, P.; Choi, T.-M.; Somani, S.; Butala, R. Blockchain Technology in Supply Chain Operations: Applications, Challenges and Research Opportunities. Transp. Res. Part E Logist. Transp. Rev. 2020, 142, 102067. [Google Scholar] [CrossRef]
- Sharma, R.; Shishodia, A.; Gunasekaran, A.; Min, H.C.; Munim, Z.H. The Role of Artificial Intelligence in Supply Chain Management: Mapping the Territory. Int. J. Prod. Res. 2022, 60, 7527–7550. [Google Scholar] [CrossRef]
- Tendall, D.M.; Joerin, J.; Kopainsky, B.; Edwards, P.; Shreck, A.; Le, Q.B.; Kruetli, P.; Grant, M.; Six, J. Food System Resilience: Defining the Concept. Glob. Food Secur. 2015, 6, 17–23. [Google Scholar] [CrossRef]
- Ecker, O.; Breisinger, C. The Food Security System: A New Conceptual Framework; IFPRI Discussion Paper 01166; International Food Policy Research Institute: Washington, DC, USA, 2012; Available online: https://cgspace.cgiar.org/server/api/core/bitstreams/93d64eb8-b18e-4fe0-ba80-e4c96587a97b/content (accessed on 28 September 2025).
- Ntafloukas, K.; McCrum, D.P.; Pasquale, L. A Cyber-Physical Risk Assessment Approach for Internet of Things Enabled Transportation Infrastructure. Appl. Sci. 2022, 12, 9241. [Google Scholar] [CrossRef]
- Dodlek, Š.; Ivana; Vahčić, N.; Markov, K.; Haramija, J.; Uršulin-Trstenjak, N.; Hajdek, K.; Sulyok, M.; Krska, R.; Šarkanj, B. First Report on Mycotoxin Contamination of Hops (Humulus lupulus L.). Toxins, 2024; 16, 293. [Google Scholar] [CrossRef] [PubMed]
- European Council. Council Regulation (Euratom) 2016/52 of 15 January 2016 Laying Down Maximum Permitted Levels of Radioactive Contamination of Food and Feed Following a Nuclear Accident or Any Other Radiological Emergency. Official Journal of the European Union L 13/2, 20 January 2016. Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX%3A32016R0052 (accessed on 28 September 2025).
- European Commission. Council Directive 2013/59/Euratom: Basic Safety Standards for Protection against Ionising Radiation. Official Journal of the European Union L 13, 17 January 2014. Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX%3A32013L0059 (accessed on 28 September 2025).
- European Commission. RASFF Annual Report 2023—Rapid Alert System for Food and Feed. Brussels: Publications Office of the European Union. Available online: https://food.ec.europa.eu/safety/rasff_en (accessed on 28 September 2025).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).