Abstract
Cybersecurity is increasingly recognized as a key enabler of Sustainable Development Goals (SDGs) and especially SDG 3 (Good Health and Well-being) as healthcare systems become more digitized. This study prioritizes cybersecurity control families from the NIST 800-53r5 framework using a structured framework combining the Analytic Hierarchy Process (AHP) and the Impact–Feasibility Matrix. From the impact–feasibility perspective, expert judgment reveals that while impact is the primary driver in selecting controls, feasibility—particularly budget and cost constraints—plays a decisive role in real-world implementation. A group of fifteen experts, including cybersecurity officers, health IT professionals, and public health advisors, has participated in structured surveys as per the methodological framework of this paper. Financial and budgetary limitations emerged as the top feasibility barrier, often determining whether high-impact controls are deployed or delayed. This underscores the need for strategic investments and phased implementation approaches, particularly in resource-constrained health systems. The results provide a practical roadmap for policymakers and healthcare administrators to allocate cybersecurity resources effectively, balancing technical necessity with economic feasibility to support resilient digital health infrastructures.
1. Introduction
In an increasingly digital world, the security and resilience of health systems have become integral to achieving global sustainable development objectives. As healthcare delivery models increasingly rely on interconnected technologies—such as electronic health records, telemedicine, and Internet of Medical Things (IoMT)—cybersecurity emerges as a critical enabler of Sustainable Development Goal 3 (SDG 3): ensuring healthy lives and promoting well-being for all at all ages [1]. While cybersecurity is traditionally treated as a technical or compliance-driven discipline, its role in sustaining vital health infrastructure and protecting sensitive health data positions it as a foundational component of public health strategy.
Moreover, healthcare institutions often function as complex production ecosystems akin to manufacturing systems, involving intricate supply chains for medical devices, pharmaceuticals, and other critical materials. Cybersecurity in this context safeguards not only digital information but also the integrity and reliability of supply chains, ensuring uninterrupted delivery of essential healthcare goods and services. Explicitly recognizing this manufacturing–management analogy enriches the understanding of cybersecurity’s role across the entire healthcare delivery process.
Despite growing recognition of this intersection, few studies have systematically investigated the specific contributions of cybersecurity controls to the realization of SDG 3. Addressing this gap, the present study evaluates the relevance and prioritization of cybersecurity domains from the NIST Special Publication 800-53 Revision 5 (NIST 800-53r5) [2] in supporting SDG 3 targets. Through a structured mapping and prioritization process, this paper aims to identify which cybersecurity measures hold the greatest potential to enhance the safety, reliability, and accessibility of digital health systems.
To this end, an integrated framework combining the Analytic Hierarchy Process (AHP) with the Impact–Feasibility Matrix is proposed to objectively evaluate the influence and practicality of NIST 800-53r5 control families in healthcare contexts. The literature review for this study rigorously included only those works that (a) deploy defined cybersecurity frameworks such as NIST 800-53r5 [2] and (b) directly address public health or SDG 3 outcomes, noting that health-sector-specific sources (e.g., [3,4,5]) consistently identify a gap in concrete, actionable mappings between cybersecurity controls and health system resilience. The AHP has been widely applied in numerous sectors—including healthcare [6], IoT [7], and cloud computing [8]—due to its structured approach to complex decision making and its ability to incorporate expert judgment. Its popularity stems from its transparency, adaptability, and effectiveness in handling multi-criteria problems, making it a suitable method for prioritizing cybersecurity measures that support public health outcomes. The outcome of this study is a data-driven prioritization matrix that offers actionable guidance for policymakers, health administrators, and IT professionals aiming to integrate cybersecurity strategies into broader health development agendas. By bridging the domains of cybersecurity and sustainable development, this research contributes to a more comprehensive understanding of digital health resilience within the framework of the 2030 Agenda.
The remainder of the paper is organized as follows: Section 2 reviews related work, while Section 3 provides background on cybersecurity and its relevance to the Sustainable Development Goals. Section 4 outlines the methodology adopted in this study. Section 5 explores the role of cybersecurity as an enabler of SDG 3. Section 6 presents the mapping of NIST control domains to SDG 3 targets, and Section 7 details the evaluation process using the proposed framework. Section 8 discusses the key findings, and finally, Section 9 concludes the paper.
2. Related Work
A review of the existing literature reveals that only a limited number of studies have explored the contribution of cybersecurity to the achievement of the Sustainable Development Goals (SDGs) [9].
Specifically, in [10], the authors explored the role of cybersecurity in supporting economic growth, social inclusion, and environmental sustainability across the 17 SDGs. However, their work offers only a broad overview and does not delve into the application of specific cybersecurity frameworks. In [11], the achievement of SDGs in cybersecurity is discussed through the use of the Artificial Intelligence of Things (AIoT) in healthcare applications. However, the study is limited to a specific domain and is not grounded in the analysis of concrete cybersecurity measures defined by established frameworks.
Moreover, in [12], the scholars examined the connection between cybersecurity and the sustainability and resilience capabilities of smart cities in the broader framework of SDG 11, in which the notion of a city’s resilience and sustainability is stressed.
In [13], a fuzzy set qualitative comparative analysis technique was proposed to identify combinations of security attacks that contribute to achieving cybersecurity in connected and automated vehicles, and its implications for the SDGs were examined.
Furthermore, in [14], the authors explored the vital intersection between cybersecurity and sustainable development, with a particular focus on SDG8 (Decent Work and Economic Growth) and SDG9 (Industry, Innovation, and Infrastructure). Drawing on cybersecurity framework, the authors systematically mapped and analyzed how cybersecurity controls enhance the resilience of IoT infrastructures and support economic development. In [15], the authors reviewed emerging cyber threats that could directly impede progress on the SDGs and classify the top five risks—such as ransomware, data breaches, and critical infrastructure attacks—highlighting their potential to disrupt areas ranging from health and education to environmental protection. Their work emphasizes the interconnected nature of cybersecurity within each goal and calls for targeted research and proactive security strategies tailored to the SDGs. This comprehensive mapping serves as a valuable reference for researchers, policymakers, and practitioners aiming to embed cybersecurity considerations into sustainable development planning. Finally, in [16], the scholars argue that securing digital infrastructures—such as electronic health records and telemedicine platforms—is fundamental to safeguarding public health, ensuring data integrity, and maintaining trust in digital services. The authors highlight that cyber-resilience in healthcare is not only about protecting information but also about preserving essential service delivery, connecting cybersecurity directly with sustainable health outcomes and SDG3 targets related to well-being. Although the discussion remains largely conceptual, it underscores the necessity of embedding cybersecurity within broader development agendas, aligning digital health initiatives with global sustainability objectives.
3. Background
3.1. Cybersecurity Domains of NIST 800-53r5
The NIST Special Publication 800-53 Revision 5 (NIST 800-53r5) serves as a comprehensive framework offering detailed guidance for securing information systems and managing cybersecurity risk, particularly within U.S. federal agencies and other organizations handling sensitive information. The framework is systematically structured into distinct control families, each encompassing a collection of controls that address specific areas of information security. These families are grouped under broader cybersecurity domains, which collectively form the foundation of a resilient and well-rounded cybersecurity strategy.
The cybersecurity domains and controls of NIST 800-53r5 are intended to support organizations in building a robust cybersecurity posture, effectively managing risks, as well as safeguarding the confidentiality, integrity, and availability of their information systems and data. The NIST 800-53r5 framework is not only a standard within U.S. federal agencies but is also globally adopted by private sector organizations aiming to strengthen their cybersecurity capabilities The primary cybersecurity domains defined by NIST 800-53r5 are outlined in Table 1.

Table 1.
NIST 800-53r5 family controls.
3.2. The United Nations’ SDGs
The 2030 Agenda for Sustainable Development, known as the United Nations’ SDGs, sets out an ambitious global vision to eradicate poverty, protect the environment, and promote inclusive prosperity. Established in September 2015 with the unanimous support of all 193 UN member countries, the SDGs outline a broad strategy to confront pressing global issues. Their ultimate objective is to unite international efforts in creating a more sustainable, just, and resilient world by 2030.
Each SDG is supported by a set of defined targets and measurable indicators, requiring unified action and strong partnerships both within and across nations. The SDGs embody a comprehensive and interlinked strategy for tackling worldwide issues, highlighting the importance of balancing social, economic, and environmental priorities to build a more sustainable and equitable future for current and coming generations [17]. The 17 SDGs are presented in Figure 1.

Figure 1.
Sustainable development goals [1].
4. Methodology Description
4.1. Approach
This study employs a systematic and comprehensive methodology to identify the relationship between the NIST 800-53r5 cybersecurity framework and the United Nations SDGs, consisting of the following key steps:
- 1
- Mapping of NIST 800-53r5 controls to the SDG3 targets: The process includes the systematic mapping of the specific security controls defined in the NIST 800-53r5 framework to relevant SDG3 targets. This involves identifying and aligning controls that directly address key global development challenges towards the achievement of the SDG3.
- 2
- Evaluation criteria: This step involves the establishment of a clear and structured criteria hierarchy using the AHP. The goal was to prioritize cybersecurity controls aligned with achieving SDG 3 targets. The approach is based on two main evaluation criteria, Impact (C1) and Feasibility (C2), that comprise sub-criteria whose priority weights are normalized such that the weights within each criterion sum to one. This ensures that the relative importance of sub-criteria within each criterion is fully distributed and directly comparable. Following the equation that defines them, the evaluation criteria are described in what follows:
- (a)
- : Impact of cybersecurity controls on SDG 3 targets: The evaluation of each control domain’s impact focused on its direct contribution to public health outcomes, its effectiveness in reducing cybersecurity risk exposure within healthcare environments, and its ability to enhance the continuity and resilience of health service delivery. The Impact criterion encompasses three specific sub-criteria:
- : Direct contribution of cybersecurity measures to health outcomes;
- : Reduction in cybersecurity risk exposure;
- : Enhancement of healthcare service continuity.
- (b)
- : Feasibility of implementation: The feasibility of implementing each control domain was assessed based on several key factors, including financial and budgetary constraints, the technical complexity of deployment, the availability of appropriately skilled personnel and necessary training, and the level of organizational support and institutional readiness. The Feasibility criterion includes four sub-criteria:
- : Financial and budgetary constraints;
- : Technical complexity;
- : Required workforce skills and training;
- : Organizational support and readiness.
Similarly, for each fixed sub-criterion, the priority scores assigned to the alternatives (the cybersecurity control families) are also normalized to sum to one as follows: - 3
- Pairwise comparison and weighting: In this step, the AHP is used to weigh the importance of the criteria and sub-criteria. A pairwise comparison approach was followed, involving structured consultations with a panel of 15 experts from cybersecurity and healthcare backgrounds as presented in Appendix A [18,19,20,21]. The 15-expert panel reflects strong sectoral and disciplinary diversity within a European context, including academia, public sector bodies, and private healthcare organizations. Both public hospitals and private providers were represented, capturing variations in priorities, resources, and regulatory obligations. The experts provided experience across both middle- and high-income healthcare settings in the EU, allowing the proposed tiers to account for differing levels of resources and infrastructure maturity. However, because the panel was limited to European contexts, the tiers are most applicable to comparable middle- and high-income systems. In low-income settings with fewer resources, limited workforce skills, or weaker regulatory frameworks, adaptation would be necessary to ensure feasibility. Through systematic comparisons, the experts assessed the relative importance of each criterion against the others, thus determining precise numerical weights. This approach allows for an objective, transparent identification of each criterion’s significance within the overall prioritization goal.
- 4
- Scoring cybersecurity controls: Following the definition and weighting of criteria and sub-criteria, the third step involves scoring each of the cybersecurity control families from the NIST framework. Experts rated each control family based on their judgment, expertise, and knowledge of the specific context using PWC for each sub-criterion, reflecting their contributions towards SDG 3 goals.
- 5
- Map total scores to the Impact–Feasibility Matrix: In this step, the aggregated scores derived from the AHP analysis were translated into two distinct dimensions: Impact and Feasibility. The Impact dimension was calculated by summing the weighted scores specifically related to health outcomes, cybersecurity risk reduction, and service continuity. In contrast, the Feasibility dimension was calculated by adding the weighted scores reflecting the financial and budgetary aspects, technical complexity, workforce skills and training, and organizational support. These two dimensions enabled clear visualization and comparison of the cybersecurity controls in terms of their overall importance and practical implementability.
- 6
- Determine priority tiers based on matrix quadrants: The final step involves the categorization of the cybersecurity control families into priority tiers based on their positions within the Impact–Feasibility Matrix. Controls characterized by both high impact and high feasibility were categorized as Tier 1 (Quick Wins), indicating they could provide immediate and substantial benefits and should be implemented urgently. Controls demonstrating high impact but moderate feasibility were classified as Tier 2 (Strategic Investment), suggesting a need for strategic planning and resource allocation. Controls with low-to-medium impact but which could still be feasible were assigned to Tier 3 (Opportunistic or Deferred), indicating lower immediate priority. Finally, controls with low impact or very low feasibility were placed into Tier 4 (Consider Later), meaning that they could be addressed as longer-term objectives or revisited as conditions change.
4.2. Analytic Hierarchy Process
The Analytic Hierarchy Process (AHP) was selected over alternative MCDM methods such as TOPSIS, PROMETHEE, BWM, or fuzzy extensions because it is particularly well suited to decision problems that require a hierarchical structuring of criteria and sub-criteria, as well as expert-driven pairwise comparisons [22,23,24,25,26,27,28].
Table 2 compares four widely used multi-criteria decision-making (MCDM) methods—AHP, TOPSIS, PROMETHEE, and BWM—against twelve decision characteristics relevant to SDG 3 prioritization. The results show that the AHP satisfies 10 out of the 12 requirements, the highest overall match, with a minimum gap of only two criteria. This highlights its strong suitability for our context, where hierarchical structuring of criteria, pairwise expert judgments, and transparency are crucial [29].

Table 2.
Comparison of MCDM methods for SDG 3 decision context.
The AHP framework enables the comparison of criteria, sub-criteria, and alternatives by allowing a group of M end-users to evaluate each pair of criteria () rather than assigning priorities directly [30]. This process reduces subjectivity and improves consistency in eliciting weights. Each user compares all possible criterion in pairs , and the results are captured in a square reciprocal matrix , which is called the PWC matrix for the end-user.
This study adopts the Analytic Hierarchy Process (AHP) following the guidelines outlined in `Uses and Limitations of the AHP Method’ [31], ensuring a robust methodological foundation. Our expert panel was composed of practitioners and researchers from cybersecurity and healthcare, who were selected to balance domain expertise and representativeness.
Each matrix element quantifies the relative importance of criterion over . By definition, , . The weights for each criterion (according to user m) are commonly computed by solving the following eigenvalue problem:
where defines the eigenvalues and defines the corresponding eigenvectors of the matrix . Assuming the eigenvalues are ordered so that is the largest, the weights are computed of the principal eigenvector of the pairwise comparison matrix by normalizing each component as follows:
where the principal eigenvector entries are strictly positive due to the properties of positive reciprocal matrices [32]. This normalization ensures that the weights sum to one and represent relative priorities.
To simplify pairwise judgments, a nine-level fundamental comparison scale was used, as shown in Table 3.

Table 3.
The nine-level fundamental comparison scale.
To evaluate the consistency of a user’s judgments, the Consistency Ratio () is calculated as , where the Consistency Index (CI) is defined as
and RI is the average random index, which is estimated from simulated reciprocal matrices [32] and presented in Appendix B. If , the pairwise matrix is considered to be consistent. To ensure consistency and reliability in expert judgments, the Consistency Ratio () was calculated for all pairwise comparison matrices using the eigenvalue method. A threshold of () was adopted for matrix acceptance, as is recommended in the AHP literature. All matrices used in the final aggregation satisfied this criterion. Instances exceeding these thresholds were re-examined from the experts to ensure consistency. This approach ensures the transparency and replicability of this prioritization framework, aligning with best practices for multi-criteria decision analysis.
Once all end-users have completed their comparisons, the final average weight for each criterion is computed as
These final weights represent the collective priorities of the attributes and serve as the outcome of the PWC process. The same process is followed in order to estimate the weights of sub-criteria (j), , and the relative scores of each alternative (i), , which is the cybersecurity control family in this paper, under each sub-criterion. Expert judgments were aggregated using the Averaging of Individual Priorities (AIP) method, where individual priority vectors were computed separately for each expert and then averaged arithmetically to generate the final composite weights. This method was chosen due to the heterogeneity of the expert group. The AIP method maintains visibility into individual expert assessments while supporting transparent aggregation. As a robustness check, the Aggregation of Individual Judgments (AIJ) method—based on geometric means at the matrix level—was also applied. The findings reveal that the Tier 1 rankings were stable across methods. The full comparison is provided in Appendix C.
4.3. Impact Feasibility Matrix
With the relative scores computed with the AHP for each cybersecurity control and each sub-criterion, the next step is the calculation of the overall weighted Impact and Feasibility scores for each cybersecurity control. This is achieved by multiplying each cybersecurity control’s priority vector value for each sub-criterion by the sub-criterion’s weights and summing these products.
Then, the total weighted Impact score for each cybersecurity control family calculated by summing the products of each Impact sub-criterion score multiplied by its respective weight is estimated. Similarly, the total weighted Feasibility score for each control family, summing across all Feasibility sub-criteria, is calculated.
The Impact score for each cybersecurity control i is calculated as follows:
Similarly, the Feasibility score for each cybersecurity control i is calculated by
where
- is the priority value for cybersecurity control i under Impact sub-criterion j.
- is the priority vector value for cybersecurity control i under Feasibility sub-criterion j.
- and are the weights for each respective sub-criterion.
To ensure a common interpretive scale, all Impact and Feasibility scores derived from the AHP calculations were normalized to the interval using the min–max linear transformation defined as follows [18]
where x is the unscaled score, and are the minimum and maximum values of all scores across control families. This transformation ensures that the lowest score maps to 1 and the highest to 5, providing a consistent scale for assigning prioritization tiers. For example, regarding the Access Control (AC), the composite scores obtained from the AHP process were 0.148 (Impact score) and 0.142 (Feasibility score). Given a global minimum value of 0.112 and a maximum of 0.157 across all control families, the normalized scores were computed as 4.20 and 3.43 for Impact and Feasibility, respectively. These normalized values were then used for tier assignment based on predefined thresholds. More, specifically, based on the normalized scores, we assigned tiers using the following rules:
- Tier 1 (Quick Wins): Impact and Feasibility .
- Tier 2 (Strategic Investment): Impact and Feasibility .
- Tier 3 (Opportunistic): Impact and Feasibility .
- Tier 4 (Consider Later): Impact and Feasibility .
These thresholds were selected to reflect both strategic importance and implementation readiness in a balanced way. After that, a two-dimensional matrix was developed, with the horizontal axis (X-axis) representing the Impact scores (ranging from low to high) and the vertical axis (Y-axis) representing the Feasibility scores (also ranging from low to high). Each cybersecurity control family was plotted within this matrix according to their calculated Impact and Feasibility scores.
Then, the matrix was divided into four strategic tiers based on their positions. Controls in the upper-right quadrant, demonstrating high impact and high feasibility, constitute Tier 1 (Quick Wins). Controls categorized as Tier 2 (Strategic Investment) are those with high impact and medium feasibility. Tier 3 (Opportunistic or Deferred) includes controls with low-to-medium impact but remaining practically feasible. Lastly, controls with low impact or very low feasibility are assigned to Tier 4 (Consider Later).
This approach provides a systematic, objective, and replicable approach to prioritizing cybersecurity controls in support of SDG 3 targets, effectively combining analytical rigor from the AHP and strategic clarity from the Impact–Feasibility Matrix approach.
5. Cybersecurity as an Enabler of the SDG3
This section seeks to examine how cybersecurity can contribute to ensuring healthy lives and promoting well-being for all, in alignment with SDG 3. The focus is on identifying cybersecurity measures and controls that support the delivery of safe, reliable, and resilient healthcare services, particularly in systems that rely on connected technologies such as IoT in medical infrastructure. The sub-targets of SDG 3 can be organized into the following categories:
- T3.1: Reduce the global maternal mortality ratio to less than 70 per 100,000 live births.
- T3.2: End preventable deaths of newborns and children under 5 years of age, aiming to reduce neonatal mortality to at least as low as 12 per 1000 live births and under-5 mortality to at least as low as 25 per 1000 live births.
- T3.3: End the epidemics of AIDS; tuberculosis; malaria; and neglected tropical diseases and combat hepatitis, water-borne diseases, and other communicable diseases.
- T3.4: Reduce premature mortality from non-communicable diseases by one-third through prevention and treatment and promote mental health and well-being.
- T3.5: Strengthen the prevention and treatment of substance abuse, including narcotic drug abuse and harmful use of alcohol.
- T3.6: Halve the number of global deaths and injuries from road traffic accidents.
- T3.7: Ensure universal access to sexual and reproductive healthcare services, including family planning, information and education, and the integration of reproductive health into national strategies and programs.
- T3.8: Achieve universal health coverage, including financial risk protection; access to quality essential healthcare services; and access to safe, effective, quality, and affordable essential medicines and vaccines for all.
- T3.9: Substantially reduce the number of deaths and illnesses from hazardous chemicals and air, water, and soil pollution and contamination.
- T3.a: Strengthen the implementation of the WHO Framework Convention on Tobacco Control in all countries, as appropriate.
- T3.b: Support research and development of vaccines and medicines for communicable and non-communicable diseases affecting developing countries and provide access to affordable essential medicines and vaccines in line with the TRIPS Agreement and the Doha Declaration on Public Health.
- T3.c: Substantially increase health financing and the recruitment, development, training, and retention of the health workforce in developing countries, especially in least-developed countries and small-island developing states.
- T3.d: Strengthen the capacity of all countries, especially developing countries, for early warning, risk reduction, and management of national and global health risks.
6. Mapping of NIST Domains to SDG3
The mapping of NIST 800-53r5 control families to SDG-3 sub-targets was conducted using a structured, reproducible coding protocol. Two experts with backgrounds in healthcare cybersecurity independently coded the relevance of each control family to SDG-3 sub-targets, primarily relying on official NIST control descriptions [33] and recent systematic reviews on cyber-health intersections. [3,4]. Disagreements were resolved through an adjudication session with additional subject matter experts, following established practices for health-sector mapping studies [5,34]. For non-obvious links (e.g., Media Protection’s relevance to telemedicine device security), we referenced illustrative examples from both the literature and recent policy guidance [35]. This multi-step procedure increases mapping rigor, minimizes bias, and aligns with accepted methodologies in both cybersecurity and public health research.
Table 4 presents a structured mapping between cybersecurity control families from the NIST 800-53r5 framework and the sub-targets of Sustainable Development Goal 3 (SDG 3), which focuses on ensuring healthy lives and promoting well-being for all at all ages.

Table 4.
Mapping of NIST 800-53r5 control families to SDG 3 sub-targets.
Several control families demonstrate high relevance across a wide range of SDG 3 targets. Specifically, Awareness and Training is applicable to every sub-target (T3.1–T3.d). This underscores the foundational role of human awareness in ensuring secure, resilient, and reliable digital health systems—from maternal care to pandemic preparedness. Additionally, Risk Assessment and Incident Response also show wide applicability. These families support early detection and response to security threats in healthcare environments, directly contributing to sub-targets like T3.3 (ending epidemics) and T3.d (health risk preparedness). Planning and Identification and Authentication are also highly relevant, providing strategic and technical controls that enable secure access and policy-driven management of healthcare systems.
Control families such as Contingency Planning; Assessment, Authorization, and Continuous Monitoring; System and Communications Protection; and System and Information Integrity are directly aligned with sub-targets that require system reliability and resilience, such as T3.8 (universal health coverage) and T3.9 (reducing deaths from environmental hazards). These controls strengthen the digital infrastructure that increasingly underpins healthcare delivery, especially in emergency contexts.
While certain control families exhibit narrower applicability, their relevance to specific SDG 3 objectives remains substantial. Specifically, Media Protection and Maintenance contribute to the secure use and upkeep of mobile and IoT-enabled medical devices (e.g., for telemedicine), which are particularly relevant to T3.4 (mental health) and T3.8 (health access). Moreover, Program Management and SA (System and Services Acquisition) contribute to organizational-level planning and procurement strategies for secure health technologies, which are vital in developing country contexts (T3.c). Lastly, Supply-Chain Risk Management has targeted impact on health system integrity and preparedness (T3.b, T3.c, T3.d), ensuring that critical medicines and digital tools are sourced from trustworthy suppliers.
7. Evaluation Results
7.1. Evaluation of Criteria and Sub-Criteria
The results indicate that Impact was considered significantly more important than Feasibility, with a weight of 62% compared to 38% for Feasibility. This suggests that experts placed greater emphasis on the effectiveness of cybersecurity controls in supporting public health outcomes, rather than on the ease or practicality of their implementation (Figure 2).
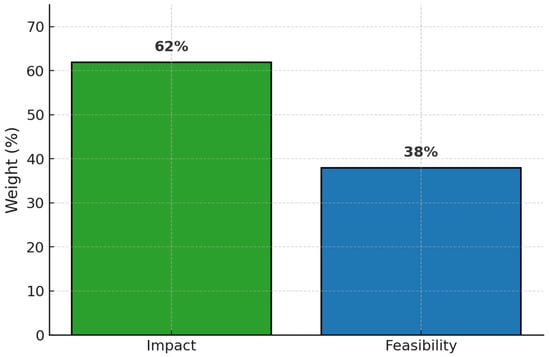
Figure 2.
Weighting of evaluation criteria: Impact vs. Feasibility .
Impact on SDG3 () was evaluated using three key sub-criteria (Table 5), each reflecting a distinct aspect of how cybersecurity controls support public health objectives. Among these, the most heavily weighted was the direct contribution to achieving SDG 3 targets, receiving of the total Impact weight. This highlights the expert panel’s prioritization of cybersecurity controls that have a clear and measurable influence on health outcomes, such as protecting patient data. Controls such as Incident Response (IR), Access Control (AC), and Risk Assessment (RA) are prioritized because they protect electronic health records, secure medical devices, and preserve system availability, which are all foundational to quality care.

Table 5.
Sub-criterion labels and descriptions with weights.
The second most important sub-criterion, with a weight of , was the reduction in cybersecurity risk exposure, reflecting the importance of controls that prevent or mitigate attacks on healthcare systems—particularly as such incidents can disrupt service delivery and erode patient trust. Cybersecurity breaches can lead to severe service disruptions in healthcare environments, with ransomware attacks often delaying critical medical procedures such as surgeries, diagnostics, and emergency interventions. These incidents not only compromise patient safety but also erode trust in digital health systems. Consequently, the reduction in cybersecurity risk exposure is viewed as a vital enabler for achieving SDG 3, which emphasizes health and well-being. This perspective aligns with international health IT policy guidance, which highlights that cyberattacks on healthcare institutions can produce non-linear and cascading effects on health outcomes. As the digitalization of health services accelerates, the ability to prevent, detect, and respond to cyber threats becomes increasingly central to sustaining safe and continuous care delivery.
Although service continuity received the lowest weight among the Impact sub-criteria (), its significance should not be overlooked. Experts recognized it as a foundational element—crucial for maintaining operational stability in healthcare systems—but considered it secondary to more direct factors such as public health impact and cybersecurity risk reduction. This prioritization reflects the view that while continuity supports long-term resilience, it cannot substitute for measures that actively prevent threats or enhance health outcomes. Nevertheless, real-world cases underscore its critical role; for example, the ransomware attack on Ireland’s Health Service Executive (HSE) caused widespread IT outages, resulting in delayed treatments, canceled appointments, and compromised patient care. Such incidents demonstrate that loss of service continuity can have immediate and measurable effects on health delivery, reinforcing the need to include resilience planning as a core aspect of any cybersecurity strategy aimed at advancing SDG 3. Figure 3 illustrates the aforementioned weights.
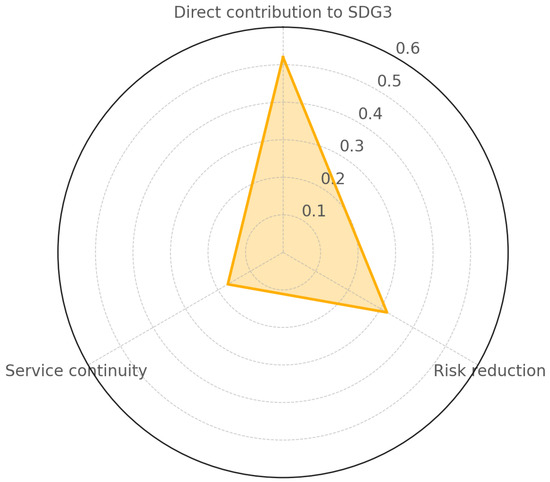
Figure 3.
Impact sub-criteria weights.
Feasibility of implementation () was assessed using four sub-criteria that reflect common barriers and enablers to the adoption of cybersecurity measures (Table 5), particularly in healthcare systems. Figure 3 underscores the practical constraints that influence the implementation of cybersecurity controls, particularly within healthcare settings where resource limitations and legacy infrastructure are prevalent. Financial constraints emerged as the most significant barrier, accounting for of the feasibility weight. This reflects the reality that even highly effective controls may not be implemented if their cost exceeds available budgets—a situation commonly observed in healthcare organizations, especially in low- and middle-income countries, where cybersecurity spending often lags behind actual risk exposure. Technical complexity and workforce training, each weighted at , jointly highlight the dual challenge of deploying sophisticated controls and ensuring that qualified personnel are available to manage them. For instance, controls like System and Communications Protection (SC) may require both advanced infrastructure and specialized cybersecurity expertise. These findings emphasize the importance of integrating capacity-building and workforce development into digital health initiatives. Finally, organizational and political support, while weighted lowest at , remains a relevant factor. It suggests that although leadership buy-in may be expected once a compelling case is made, in practice, the absence of strong governance or political commitment can still hinder implementation, regardless of technical or financial readiness. The aforentioned results are presented in Figure 4. In addition, feasibility considerations extend beyond direct financial and technical aspects to include integration with legacy systems, operational disruptions during deployment, and indirect costs such as licensing or consultancy. Long-term sustainability also depends on ongoing maintenance activities, including updates, patching, and compliance audits, which create recurring demands. Equally important is workforce training and continuous capacity building, as healthcare staff must adapt to evolving threats through both initial and ongoing education. Furthermore, feasibility is influenced by the production processes and life cycles of medical devices, since procurement, certification, and integration into clinical workflows often impose regulatory and organizational dependencies that delay or complicate implementation. Taken together, these factors underscore the need for a total cost of ownership perspective, where implementation, maintenance, training, and production life-cycle considerations are jointly addressed to ensure resilient and sustainable adoption of cybersecurity controls in healthcare environments.
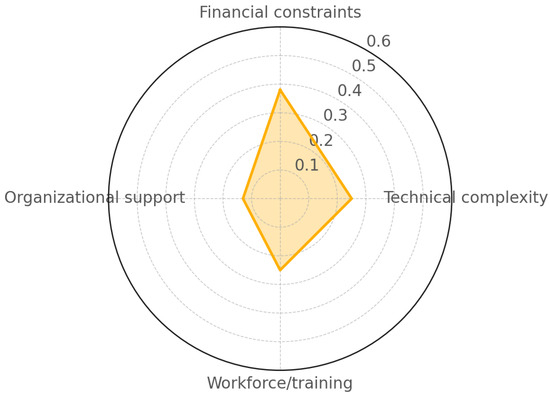
Figure 4.
Feasibility sub-criteria weights.
7.2. Prioritization of NIST 800-53r5 Control Families
Table 6 presents the prioritization of NIST 800-53r5 control families based on expert evaluations of their average impact on SDG 3 and their implementation feasibility. Each control family score has been normalized with a score from 1 to 5 for both dimensions, for simplicity reasons, and then categorized into one of four priority tiers according to its combined performance on the Impact–Feasibility Matrix.

Table 6.
Prioritization of NIST 800-53r5 control families based on impact and feasibility.
Tier 1: Critical Priority includes control families that scored highly on both Impact (≥4.4) and Feasibility (≥4.0). These include Incident Response (IR), Access Control (AC), Risk Assessment (RA), Identification and Authentication (IA), and Planning (PL). These controls are regarded as essential to digital health infrastructure because they directly support clinical continuity, data protection, and organizational preparedness. Incident Response (IR) (highest average scores—Impact: 4.9; Feasibility: 4.2) reflects the urgency of having operational protocols to detect, respond to, and recover from cyber incidents, in alignment with NIST guidance on healthcare cybersecurity. Access Control (AC) and Identification and Authentication are indispensable technical safeguards, being foundational for protecting the confidentiality, integrity, and availability of electronic health information. They also align with regulatory frameworks such as HIPAA [34] and GDPR, which require appropriate access restrictions and identity verification to safeguard personal health data. Risk Assessment (RA) enables proactive vulnerability identification and mitigation, while Planning ensures cybersecurity is embedded within organizational governance, fostering sustainability and resilience.
Also within Tier 1 is Awareness and Training (AT), which is classified as a “Quick Win.” It combines moderate-to-high Impact (4.0) with very high Feasibility (4.4), reflecting that healthcare organizations can rapidly implement staff training programs at low cost. Given that human error remains a leading cause of breaches, this control offers substantial return on minimal investment and is especially relevant in resource-constrained environments.
Tier 2 includes families such as System and Communications Protection (SC), System Integrity (SI), Contingency Planning (CP), Personnel Security (PS), and Audit and Accountability (AU). These controls provide significant Impact (ranging from 3.8 to 4.4) but are somewhat less feasible (typically around 3.6–3.9), often due to infrastructure limitations, technical complexity, or the need for interdepartmental coordination. For example, SC may require advanced configurations like firewalls, encrypted communication, and network segmentation—resources that may not be readily available in all healthcare environments, particularly in LMICs. CP and PS are crucial during system failures or workforce changes, but their effectiveness often hinges on institutional maturity and prior investments.
Tier 3 (Opportunistic or Consider Later) includes controls such as Assessment and Continuous Monitoring (CA), Maintenance (MA), System and Services Acquisition (SA), and PII Processing and Transparency (PT). These controls either scored lower in Impact (e.g., PT: 3.1) or Feasibility (e.g., CA: 3.2), reflecting that while they may not deliver immediate or direct public health gains, they play important roles in system compliance, auditability, and ethical governance. For example, CA supports long-term assurance through ongoing security evaluation, while SA addresses security-by-design concerns in new systems.
Tier 4: Long-term/Low Priority is solely represented by Supply-Chain Risk Management (SR), which received the lowest average scores in both dimensions (Impact: 3.0; Feasibility: 2.8). Despite its current limitations, SR is increasingly relevant given the growing threat of software supply chain attacks, as seen in incidents like SolarWinds. However, due to resource intensity and dependency on external partners, SR is better suited for future inclusion once foundational cybersecurity practices are in place.
This tiered prioritization provides a practical roadmap for decision makers in the health sector, allowing them to sequence cybersecurity investments in a way that maximizes impact on health outcomes while realistically navigating technical, financial, and institutional constraints.
7.3. Sensitivity Analysis
In this section, we discuss the reliability of the results, given the level of uncertainties involved, by carrying out a sensitivity analysis. In order to further validate the reliability of the final ranking of the alternatives, Monte Carlo simulations were performed by simultaneously changing more than one parameter. The weights of all criteria were perturbed from to (1 + ), where the perturbations were assumed to be zero mean, identically distributed, independent random variables uniformly distributed inside [−]. Such random perturbation may be due to inconsistencies of the PWC matrices [18]. Table 7 presents the results before and after the sensitivity analysis, assuming (corresponding to a maximum of relative variation). The weights have been normalized so that their sum is equal to 1. The priorities of the NIST control families were calculated using Monte Carlo iterations.

Table 7.
Comparison of rankings and Tier assignments for NIST control families before and after sensitivity analysis.
As shown in the table, the Tier 1 control families—namely, IR, AT, AC, RA, CP, SI, SC, and IA—demonstrated complete stability in their tier assignments. Although minor fluctuations were observed in the rankings of AC and RA, such shifts were marginal and did not result in any reclassification across tiers. This is an important indication that the top priority controls (Tier 1) are robustly prioritized regardless of changes in the weight inputs, reinforcing their criticality to supporting SDG 3 outcomes.
Similarly, Tier 2 controls such as PL, CM, PM, and PS remained stable in their tier classification despite some intra-tier rank variability (e.g., CM dropped from rank 10 to 12, while PM improved from 11 to 10). These changes suggest that while relative positioning among Tier 2 controls is moderately sensitive, their overall strategic importance remains consistent. Similar observations are also stable for the controls that fall into the Tiers 3 and 4.
8. Discussion
The results highlight that impact was considered significantly more important than feasibility. This finding is consistent with the literature, since studies have shown that, in sectors such as healthcare and emergency services, the consequences of cyber failures can be severe and far-reaching, directly affecting human safety and well-being [35].
For example, the World Health Organization’s Global Strategy on Digital Health (2020–2025) highlights the necessity of securing digital health systems as a matter of public safety, noting that cybersecurity is an essential element of resilient health systems (WHO 2020) [36]. Similarly, the European Union Agency for Cybersecurity emphasizes that cybersecurity measures in the health sector must be outcome-driven, endorsing prioritization based on potential harm reduction rather than implementation ease [5]. These sources support the idea that when cyber risks affect patient safety or public health, the benefits of a control’s impact are often more important than how hard or costly it is to implement. For this reason, the result of 62% weight for Impact compared to 38% for Feasibility shows a practical and risk-aware approach that is in line with global guidance on protecting digital health systems.
Among the Impact-related sub-criteria, the direct contribution to SDG 3 objectives received the highest weight (52%), highlighting the expert panel’s strong emphasis on cybersecurity controls that demonstrably enhance public health outcomes. This finding is consistent with the existing literature, which underscores the importance of securing patient data, telemedicine platforms, and digital health records as critical components for ensuring healthcare quality and trust [3,4]. The second most important factor was the reduction in cybersecurity risk exposure, reflecting the urgent need to protect healthcare systems from cyber threats that could compromise sensitive information or disrupt clinical operations. As noted by Choi and Johnson [37], cyber incidents such as data breaches and ransomware attacks have measurable impacts on both patient safety and system-level performance. The third sub-criterion, healthcare service continuity and resilience, received a weight of 17%, indicating its role as a supportive, though not primary, concern within the overall prioritization process. Nonetheless, its importance is clearly evidenced in recent studies. For example, a 2023 qualitative investigation revealed that ransomware attacks have led to postponed medical procedures, ambulance rerouting, and blocked access to critical patient records—directly compromising both emergency and routine care [38]. Additionally, feasibility assessments must account for the production processes and life cycles of medical devices, since their procurement, certification, maintenance, and eventual integration into healthcare workflows directly influence the practicality and timing of cybersecurity control adoption.
Figure 5 presents a scatter plot of the NIST 800-53r5 control families mapped according to their average impact on SDG 3 and their average feasibility of implementation.
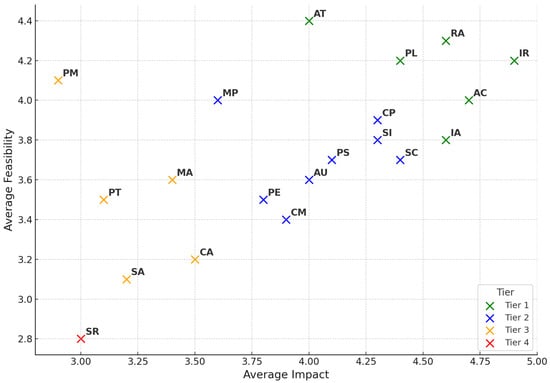
Figure 5.
Impact vs. Feasibility matrix with tier classifications for NIST 800-53r5 control families.
Tier 1 (Quick Wins) includes controls with both high impact and high feasibility. Notably, IR (Incident Response), RA (Risk Assessment), and AT (Awareness and Training) are positioned here. These controls are seen as highly effective and practical, making them ideal for immediate implementation in health-sector cybersecurity strategies aligned with SDG 3. IR (Incident Response) plays a critical role in ensuring continuity of care during cybersecurity incidents. Its high Feasibility score reflects the availability of mature practices and tools that can be adopted even by resource-constrained institutions. RA (Risk Assessment) supports informed decision making by identifying vulnerabilities and prioritizing mitigation efforts, thus helping health organizations proactively manage cyber threats before they impact public health services. Its strong placement in this quadrant reflects its foundational importance and the relative ease of integrating risk assessments into existing governance or compliance frameworks. AT (Awareness and Training) addresses the human factor—the most commonly exploited vulnerability in cybersecurity breaches. This control ensures that healthcare staff are educated about threats such as phishing, ransomware, and social engineering, thereby reducing the likelihood of human error. Its particularly high Feasibility score makes it an ideal early intervention, especially in environments where budget or technical infrastructure may be limited.
Tier 2 (Strategic Investments) consists of controls with high impact but moderate feasibility. They require longer-term planning, cross-functional coordination, and adequate resourcing, but their implementation is pivotal for achieving a robust and resilient digital health ecosystem aligned with SDG 3. Policymakers and administrators may need to allocate targeted funding or seek public–private partnerships to make these investments viable. Prominent examples in this quadrant include SC (System and Communications Protection) and CP (Contingency Planning). SC (System and Communications Protection) encompasses a wide range of technical safeguards such as firewalls, intrusion detection systems, encryption protocols, and secure network architectures. These controls are essential for protecting the confidentiality, integrity, and availability of health information and systems—particularly in connected environments like hospitals, telehealth platforms, or public health databases. CP (Contingency Planning) ensures that healthcare services can continue operating or recover quickly in the event of cyber disruptions, natural disasters, or system failures. This includes having data backup solutions, recovery procedures, and tested response plans in place.
Tier 3 (Opportunistic) includes cybersecurity controls that are relatively feasible to implement but are perceived to have lower direct impact on health-related outcomes. These controls may not be urgent or foundational for achieving SDG 3, but they can enhance overall system resilience when integrated into broader cybersecurity strategies. Representative controls in this tier include PM (Program Management) and MP (Media Protection). PM (Program Management) involves the establishment of governance, planning, budgeting, and oversight structures for cybersecurity activities. Its high Feasibility score reflects the fact that many health organizations already maintain administrative functions that can integrate cybersecurity oversight with relatively low technical complexity. However, the perceived indirect link to immediate health outcomes likely explains its lower Impact rating. MP (Mobile Device Management) is designed to secure smartphones, tablets, and other mobile endpoints that increasingly support clinical workflows, telemedicine, and remote patient monitoring. Its moderate Impact score may reflect variability in mobile device usage across health systems, but its high Feasibility score is attributable to the availability of mature commercial MDM solutions that are cost-effective and easy to deploy.
Finally, Tier 4 (Long-Term Consideration) includes controls like SR (Supply-Chain Risk Management), which scored low on both Impact and Feasibility. SR (Supply-Chain Risk Management) addresses vulnerabilities introduced through third-party vendors, service providers, and hardware or software suppliers. Its low Feasibility score may reflect the complexity of monitoring, vetting, and coordinating across multiple external actors, particularly in under-resourced healthcare environments where supply-chain governance is often fragmented.
We acknowledge several limitations inherent in this study. Firstly, the analysis is primarily based on expert judgment from a selected panel; thus, the findings may reflect regional or institutional biases, limiting generalizability across diverse healthcare contexts. Secondly, the current work lacks empirical validation through real-world case studies or pilot implementations within hospitals or healthcare institutions, which would strengthen the practical applicability of the prioritization framework.
9. Conclusions
This study explored the intersection between structured cybersecurity controls and sustainable development, focusing specifically on how the NIST 800-53r5 control families can support the achievement of Sustainable Development Goal 3 (SDG 3): Good Health and Well-being. Through a comprehensive methodology involving mapping, expert-driven evaluation, and AHP-based prioritization, the research identified which cybersecurity domains contribute most significantly—and feasibly—to enhancing digital health system resilience.
The findings reveal that control families such as Incident Response, Access Control, Risk Assessment, and Awareness and Training hold both high Impact and high Feasibility scores, making them strong candidates for immediate implementation in health-sector cybersecurity strategies. The study also confirms that experts assigned greater weight to impact on health outcomes (62%) compared to feasibility (38%), emphasizing a risk-informed, outcome-driven mindset aligned with global digital health priorities.
Importantly, this research demonstrates the value of embedding cybersecurity considerations into broader sustainable development agendas. By translating cybersecurity control frameworks into development-relevant evaluations, stakeholders are better equipped to plan strategic and resource-conscious interventions that strengthen health systems and protect vulnerable populations.
While the present study provides a foundational framework for aligning cybersecurity with SDG 3 (Good Health and Well-being), several directions for future research are evident. First, there is a need to broaden the scope by extending the analysis to other SDGs beyond SDG 3—such as SDG 4 on Quality Education or SDG 9 on Industry, Innovation, and Infrastructure—to explore how cybersecurity contributes to digital sustainability across diverse sectors. Specifically, SDG 4’s emphasis on equitable and inclusive education closely intersects with cybersecurity by safeguarding digital learning environments, promoting cyber literacy, and enabling secure access to educational technologies worldwide.
Beyond its theoretical contribution, this study provides a practical decision-support tool for healthcare organizations facing increasing cybersecurity pressures. By translating expert judgments into a transparent Impact–Feasibility framework, the results can guide hospitals, policymakers, and administrators in sequencing cybersecurity investments according to both their expected health impact and their feasibility under real-world constraints. For example, resource-limited hospitals can focus first on Tier 1 “Quick Wins” such as Incident Response, Access Control, and Awareness and Training, while larger medical centers may adopt a phased strategy that also incorporates Tier 2 strategic investments like System and Communications Protection. In this way, the proposed framework not only advances scholarly understanding but also offers actionable pathways for building resilient and sustainable digital health infrastructures.
Moreover, this study’s expert panel was composed of European practitioners and researchers, and the resulting criteria weights and prioritization tiers reflect predominantly middle- and high-income health system contexts; accordingly, generalizability beyond similar settings is limited, and caution is warranted when extrapolating to regions with different regulatory environments, resource constraints, and threat landscapes.
Additionally, future research should consider dynamic and longitudinal evaluation approaches to examine how the prioritization of cybersecurity controls may evolve over time, particularly in response to emerging cyber threats, technological advancements, and updated global development targets.
Finally, involving a broader, more internationally diverse panel of experts would enhance the representativeness and robustness of findings, mitigating regional or sectoral biases inherent in smaller, localized panels. Including empirical validations via case studies and conducting sensitivity analyses to assess result stability under varying assumptions would further strengthen the framework’s practical applicability and scholarly rigor.
Author Contributions
Conceptualization, G.D.; Methodology, G.D., E.F., G.F., and S.E.; Validation, T.S.; Investigation, data curation, S.E., T.K., and G.D.; Writing—original draft, G.D.; Writing—review and editing, G.D., S.E., E.F., and G.F.; Visualization, G.D.; Supervision, T.K.; Project administration, T.S. and T.K. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the European Union’s Horizon Europe Research and Innovation Program through the AppTake Project under Grant 101128082.
Data Availability Statement
Data available on request due to restrictions.
Conflicts of Interest
Authors Georgia Dede and Spyridon Evangelatos were employed by the company Netcompany S.A. The funders had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript; or in the decision to publish the results. The remaining authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Appendix A. Experts’ Profiles
In the following table the experts’ profiles are presented in terms of sector, area of expertise, and years of experience.

Table A1.
Experts’ profiles by sector, area of expertise, and years of experience.
Table A1.
Experts’ profiles by sector, area of expertise, and years of experience.
| ID | Sector Type (EU) | Area of Expertise | Years |
|---|---|---|---|
| E1 | Academia | Cybersecurity Research in Health | 10 |
| E2 | Public Sector | Digital Health Policy | 7 |
| E3 | Private Sector | IT Risk and Governance | 11 |
| E4 | Academia | Health Informatics | 10 |
| E5 | Private Sector | eHealth | 11 |
| E6 | Private Sector | Medical Device Security | 9 |
| E7 | Academia | Health Informatics and Cybersecurity | 11 |
| E8 | Public Sector | Telemedicine Infrastructure | 13 |
| E9 | Private Sector | Cybersecurity Compliance | 12 |
| E10 | Academia | Cybersecurity in Health Systems | 9 |
| E11 | Private Sector | Health Data Privacy | 10 |
| E12 | Academia | Cybersecurity Compliance | 8 |
| E13 | Private Sector | Healthcare IT | 7 |
| E14 | Public Sector | Cybersecurity | 16 |
| E15 | Academia | Cybersecurity | 8 |
Appendix B. Random Index
The Random Index (RI), introduced by Saaty [20] for the Analytic Hierarchy Process (AHP), is the average the Consistency Index (CI) from randomly generated reciprocal matrices of size n. It is used to compute the Consistency Ratio (CR) (see Section 4.2).

Table A2.
Random Index (RI) values for matrix sizes to 15.
Table A2.
Random Index (RI) values for matrix sizes to 15.
| Matrix Size (n) | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Random Index (RI) | 0.00 | 0.00 | 0.58 | 0.90 | 1.12 | 1.24 | 1.32 | 1.41 | 1.45 | 1.49 | 1.51 | 1.48 | 1.56 | 1.57 | 1.59 |
Appendix C. AIP vs. AIJ Comparison
To ensure transparency and robustness in the prioritization of cybersecurity control families, the results of two aggregation approaches used in the Analytic Hierarchy Process were compared: Averaging of Individual Priorities (AIP) and Aggregation of Individual Judgments (AIJ). The table below presents the ranks assigned to each NIST SP 800-53 Rev. 5 control family under both methods, as well as the corresponding tier classification derived from the Impact–Feasibility Matrix. The comparison demonstrates that Tier 1 control families remain stable across both aggregation approaches, while only minor differences appear in the relative order of lower-tier controls, confirming the robustness of the overall prioritization framework.

Table A3.
Comparison of AIP and AIJ ranks with tier classifications for NIST SP 800-53 Rev. 5 control families.
Table A3.
Comparison of AIP and AIJ ranks with tier classifications for NIST SP 800-53 Rev. 5 control families.
| Control Family | AIP Rank | AIJ Rank | Tier (AIP) | Tier (AIJ) |
|---|---|---|---|---|
| IR | 1 | 1 | Tier 1 | Tier 1 |
| AT | 2 | 2 | Tier 1 | Tier 1 |
| AC | 3 | 4 | Tier 1 | Tier 1 |
| RA | 4 | 3 | Tier 1 | Tier 1 |
| CP | 5 | 5 | Tier 1 | Tier 1 |
| SI | 6 | 6 | Tier 1 | Tier 1 |
| SC | 7 | 7 | Tier 1 | Tier 1 |
| IA | 8 | 8 | Tier 1 | Tier 1 |
| PL | 9 | 9 | Tier 2 | Tier 2 |
| CM | 10 | 11 | Tier 2 | Tier 2 |
| PM | 11 | 12 | Tier 2 | Tier 2 |
| PS | 12 | 10 | Tier 2 | Tier 2 |
| CA | 13 | 13 | Tier 3 | Tier 3 |
| SA | 14 | 15 | Tier 3 | Tier 3 |
| AU | 15 | 14 | Tier 3 | Tier 3 |
| MA | 16 | 18 | Tier 3 | Tier 3 |
| PE | 17 | 16 | Tier 3 | Tier 3 |
| SR | 18 | 17 | Tier 3 | Tier 3 |
| MP | 19 | 20 | Tier 4 | Tier 4 |
| PT | 20 | 19 | Tier 4 | Tier 4 |
References
- SDG. Sustainable Development Goals. 2025. Available online: https://sdgs.un.org/goals (accessed on 15 August 2025).
- National Institute of Standards and Technology (NIST). NIST Special Publication 800-53 Revision 5. 2020. Available online: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-53r5.pdf (accessed on 15 August 2025).
- Shojaei, P.; Vlahu-Gjorgievska, E.; Chow, Y.W. Security and privacy of technologies in health information systems: A systematic literature review. Computers 2024, 13, 41. [Google Scholar] [CrossRef]
- Sunil, V.; Mathew, S.P. A Systematic Review on Cybersecurity Threats and Challenges in Hospitals. Acta Medica Int. 2024, 11, 1–6. [Google Scholar] [CrossRef]
- Zurawski, S.; Chodyka, M.; Nowicka, J.; Marek, G.T.; Dawidziuk, R.; Gralak, K. The Impact of Cyberthreats on the Security of Important Sectors of the Economy on the Example of the Healthcare Sector. Eur. Res. Stud. J. 2025, 28, 150–162. [Google Scholar] [CrossRef]
- Georgia, D.; Evangelia, F.; Georgios, C.; Christos, M.; Thomas, K. Evaluation of end user requirements for smart home applications and services based on a decision support system. Internet Things 2021, 16, 100431. [Google Scholar] [CrossRef]
- Dede, G.; Filiopoulou, E.; Paroni, D.V.; Michalakelis, C.; Kamalakis, T. Analysis and evaluation of major COVID-19 features: A pairwise comparison approach. Oper. Res. Forum 2023, 4, 15. [Google Scholar] [CrossRef]
- Filiopoulou, E.; Dede, G.; Michalakelis, C.; Kamalakis, T. End-user and provider requirements for pricing policies of infrastructure as a service. IEEE Internet Comput. 2019, 23, 36–48. [Google Scholar] [CrossRef]
- Dede, G.; Petsa, A.M.; Kavalaris, S.; Serrelis, E.; Evangelatos, S.; Oikonomidis, I. Cybersecurity as a contributor to United Nations SDGs towards enhancing the ESG Reporting. In Proceedings of the 2024 5th International Conference in Electronic Engineering, Information Technology & Education (EEITE), Chania, Greece, 29–31 May 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 1–6. [Google Scholar]
- Odumesi, J.O.; Sanusi, B.S. Achieving Sustainable Development Goals from a Cybersecurity Perspective. Adv. Multidiscip. Sci. Res. J. Publ. 2023, 2, 1–10. [Google Scholar] [CrossRef]
- Vijarania, M.; Gupta, S.; Agrawal, A.; Misra, S. Achieving Sustainable Development Goals in Cyber Security Using AIoT for Healthcare Application. In Artificial Intelligence of Things for Achieving Sustainable Development Goals; Springer: Berlin/Heidelberg, Germany, 2024; pp. 207–231. [Google Scholar]
- Andrade, R.O.; Yoo, S.G.; Tello-Oquendo, L.; Ortiz-Garcés, I. Cybersecurity, sustainability, and resilience capabilities of a smart city. In Smart Cities and the un SDGs; Elsevier: Amsterdam, The Netherlands, 2021; pp. 181–193. [Google Scholar]
- Karuppiah, K.; Sankaranarayanan, B.; Ali, S.M.; Priyanka, R. A fsQCA-based framework for cybersecurity of connected and automated vehicles: Implications for sustainable development goals. Vehicles 2024, 6, 484–508. [Google Scholar] [CrossRef]
- Dede, G.; Petsa, A.M.; Kavalaris, S.; Serrelis, E.; Evangelatos, S.; Oikonomidis, I.; Kamalakis, T. Cybersecurity as a Contributor Toward Resilient Internet of Things (IoT) Infrastructure and Sustainable Economic Growth. Information 2024, 15, 798. [Google Scholar] [CrossRef]
- Mohamed, N.N.; Abuobied, B.H.H. Cybersecurity challenges across sustainable development goals: A comprehensive review. Sustain. Eng. Innov. 2024, 6, 57–86. [Google Scholar] [CrossRef]
- Kuday, A.D. Sustainable Development in the Digital World: The Importance of Cybersecurity. Disaster Med. Public Health Prep. 2024, 18, e279. [Google Scholar] [CrossRef] [PubMed]
- Dede, G.; Lalas, G.; Filiopoulou, E.; Kamalakis, T. Assessment of Cybersecurity Measures towards the Achievement of the UN SDG8: An AHP and MoSCoW Approach. In Proceedings of the 2025 6th International Conference in Electronic Engineering & Information Technology (EEITE), Chania, Crete, 4–6 June 2025; IEEE: New York, NY, USA, 2025; pp. 1–6. [Google Scholar]
- Dede, G.; Kamalakis, T.; Sphicopoulos, T. Convergence properties and practical estimation of the probability of rank reversal in pairwise comparisons for multi-criteria decision making problems. Eur. J. Oper. Res. 2015, 241, 458–468. [Google Scholar] [CrossRef]
- Dede, G.; Kamalakis, T.; Sphicopoulos, T. Theoretical estimation of the probability of weight rank reversal in pairwise comparisons. Eur. J. Oper. Res. 2016, 252, 587–600. [Google Scholar] [CrossRef]
- Wind, Y.; Saaty, T.L. Marketing applications of the analytic hierarchy process. Manag. Sci. 1980, 26, 641–658. [Google Scholar] [CrossRef]
- Forman, E.; Peniwati, K. Aggregating individual judgments and priorities with the analytic hierarchy process. Eur. J. Oper. Res. 1998, 108, 165–169. [Google Scholar] [CrossRef]
- Talero-Sarmiento, L.; Gonzalez-Capdevila, M.; Granollers, A.; Lamos-Diaz, H.; Pistili-Rodrigues, K. Towards a Refined Heuristic Evaluation: Incorporating Hierarchical Analysis for Weighted Usability Assessment. Big Data Cogn. Comput. 2024, 8, 69. [Google Scholar] [CrossRef]
- Urruchi Villegas, D.G.; Pacheco Oropeza, F.A. Improvement of sales distribution process in a dairy sector company using the impact-feasibility matrix. In Proceedings of the 4th Indian International Conference on Industrial Engineering and Operations Management Hyderabad, Telangana, India, 7–9 November 2024. [Google Scholar]
- Petriki, O.; Bobori, D.C. Ecological Assessment and SWOT–AHP Integration for Sustainable Management of a Mediterranean Freshwater Lake. Sustainability 2025, 17, 4950. [Google Scholar] [CrossRef]
- Boonsothonsatit, G.; Vongbunyong, S.; Chonsawat, N.; Chanpuypetch, W. Development of a hybrid AHP-TOPSIS decision-making framework for technology selection in hospital medication dispensing processes. IEEE Access 2024, 12, 2500–2516. [Google Scholar] [CrossRef]
- Wątróbski, J.; Bączkiewicz, A.; Rudawska, I. A Strong Sustainability Paradigm based Analytical Hierarchy Process (SSP-AHP) method to evaluate sustainable healthcare systems. Ecol. Indic. 2023, 154, 110493. [Google Scholar] [CrossRef]
- Weng, F.; Tian, J.; Fang, X.; Cheng, S.; Pan, Z.; Liu, Y. Research on establishment decision of medical equipment measurement standard based on GDM-AHP. Sci. Rep. 2025, 15, 9309. [Google Scholar] [CrossRef]
- Maulana, M.M.; Suroso, A.I.; Nurhadryani, Y.; Seminar, K.B. The Smart Governance Framework and Enterprise System’s Capability for Improving Bio-Business Licensing Services. Informatics 2023, 10, 53. [Google Scholar] [CrossRef]
- Ishizaka, A.; Labib, A. Review of the main developments in the analytic hierarchy process. Expert Syst. Appl. 2011, 38, 14336–14345. [Google Scholar] [CrossRef]
- Saaty, T.L.; Vargas, L.G. Models, Methods, Concepts & Applications of the Analytic Hierarchy Process; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2012; Volume 175. [Google Scholar]
- Munier, N.; Hontoria, E. Uses and Limitations of the AHP Method; Springer: Berlin/Heidelberg, Germany, 2021. [Google Scholar]
- Saaty, T.L. Decision-making with the AHP: Why is the principal eigenvector necessary. Eur. J. Oper. Res. 2003, 145, 85–91. [Google Scholar] [CrossRef]
- U.S. Department of Commerce. Commerce Open Government Plan, Version 4.0. 2016. Available online: https://www.nist.gov/system/files/documents/2017/12/20/formatted_nist_open_government_plan_2016_final.pdf (accessed on 29 September 2025).
- Moore, W.; Frye, S. Review of HIPAA, part 1: History, protected health information, and privacy and security rules. J. Nucl. Med. Technol. 2019, 47, 269–272. [Google Scholar] [CrossRef] [PubMed]
- Garcia-Perez, A.; Cegarra-Navarro, J.G.; Sallos, M.P.; Martinez-Caro, E.; Chinnaswamy, A. Resilience in healthcare systems: Cyber security and digital transformation. Technovation 2023, 121, 102583. [Google Scholar] [CrossRef]
- WHO. WHO Director-General’s Opening Remarks at the Media Briefing on COVID-19-11 March 2020; WHO: Geneva, Switzerland, 2020; pp. 3–5. [Google Scholar]
- Choi, S.J.; Johnson, M.E. Do hospital data breaches reduce patient care quality? arXiv 2019, arXiv:1904.02058. [Google Scholar] [CrossRef]
- Dotson, M.; Gorli, K.; Coustasse, A. Cyber Threats in Healthcare: The Ransomware Epidemic. Ph.D. Thesis, Marshall University, Huntington, WV, USA, 2025. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).