A Trust Score-Based Access Control Model for Zero Trust Architecture: Design, Sensitivity Analysis, and Real-World Performance Evaluation
Abstract
1. Introduction
2. Background and Related Work
2.1. Traditional Access Control
2.1.1. Role-Based Access Control ()
2.1.2. Attribute-Based Access Control ()
2.1.3. Risk-Based Authentication ()
2.2. Zero Trust Security Models
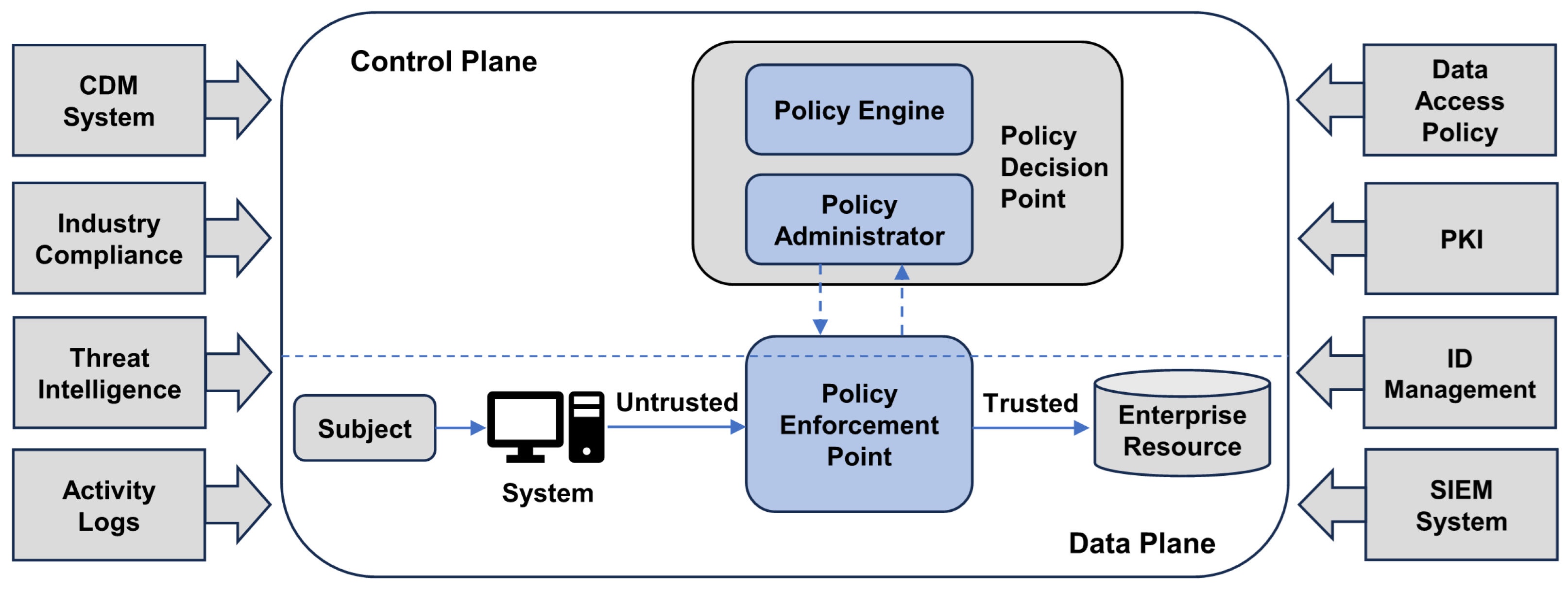
2.2.1. Zero Trust Architecture
2.2.2. Zero Trust Use Cases
2.3. Trust Score-Based Access Control
- Limitations of static policies: In an environment where a user’s environment or circumstances can change in real time, fixed access rights are insufficient to detect or respond to new threats.
- Lack of real-time threat assessment: Traditional access control performs authentication only at the point of access, so it cannot reflect changes in user behavior or environmental factors.
- Complex network environments: The adoption of cloud, mobile, and IoT devices has blurred network boundaries, making traditional access control models difficult to apply.
- Real-time data analysis: The Trust Score is updated in real time based on a comprehensive assessment of user behavior, network environment, device health, past threat history, and more.
- Dynamic access authorization: Access permissions are dynamically adjusted based on the Trust Score, requiring additional authentication or restricting access when trust levels are low.
- Flexible policy management: Because Trust Score is weighted, it can be flexibly adjusted to fit your organization’s environment.
3. Trust Score Modeling and Access Control Framework in Zero Trust Architecture
3.1. Trust Score Factors and Evaluation Criteria
- User Behavior (): Collect and evaluate data such as users’ login patterns, unusual access attempts, login time and location, etc. This factor, summarized in Table 2, is important for detecting insider threats and preventing account takeover.
- Network Environment (): Assesses the trustworthiness of the network by looking at the IP reputation of users, VPN usage, network traffic analysis, and more. The detailed items are shown in Table 3, which is essential for detecting external attacks and network-based threats.
- Device status (): Determine the security status of a device by assessing whether it is security patched, antivirus status, and whether the device is authenticated. The evaluation criteria are described in Table 4, which is especially important in BYOD environments or remote work environments.
- Threat History (): Analyzes a user’s history of previous security incidents, policy violations, etc., to assess their long-term trustworthiness. The detailed factors are presented in Table 5, and this is useful for proactively blocking repeat threat behavior.
3.2. Mathematical Modeling and Computation of Trust Score
3.2.1. Trust Score Calculation Formula
- : weight of factor i();
- : evaluation score of factor i (range: 0 to 100);
- n: total number of evaluation factors (in this study, ).
- : weights of each factor (their sum equals 1);
- : evaluation scores for user behavior, network environment, device status, and historical threat records, respectively.
3.2.2. Weight Assignment Rationale
3.2.3. Formula Calculation Examples
- Situation: A normal pattern of access in a secure environment (e.g., internal network).
- Scoring:
- –
- B = 90 points (Rationale: Overall good, with minor changes in some items);
- –
- N = 85 points (Rationale: Overall good);
- –
- D = 85 points (Rationale: Managed devices, good condition);
- –
- T = 80 points (Rationale: no history of severity).
- Calculation: = (0.4 × 90) + (0.3 × 85) + (0.2 × 85) + (0.1 × 80) = 86.5 points.
- Result: 86.5 points (above 80) → Decision to allow access.
- Situation: Behavior is good, but use of external public networks (N) and BYOD devices (D).
- Scoring:
- –
- B = 80 points (Rationale: Relatively good);
- –
- N = 50 points (Rationale: Public network use reduces trust);
- –
- D = 65 points (Rationale: Moderate security with BYOD devices);
- –
- T = 80 points (Rationale: Good historical record).
- Calculation: = (0.4 × 80) + (0.3 × 50) + (0.2 × 65) + (0.1 × 80) = 68.0 points.
- Result: 68.0 points (60–79 points) → Decide it requires additional authentication (MFA).
- Multiple risk events including abnormal times/login attempts (B), suspicious IPs (N), and vulnerable devices (D).
- Scoring:
- –
- B = 35 points (Rationale: Highly suspicious behavior);
- –
- N = 25 points (Rationale: Network environment is highly risky);
- –
- D = 40 points (Rationale: Device security is very weak);
- –
- T = 30 points (Rationale: Poor past history).
- Calculation: = (0.4 × 35) + (0.3 × 25) + (0.2 × 40) + (0.1 × 30) = 32.5 points.
- Result: 32.5 points (less than 60 points) → Decision to block access.
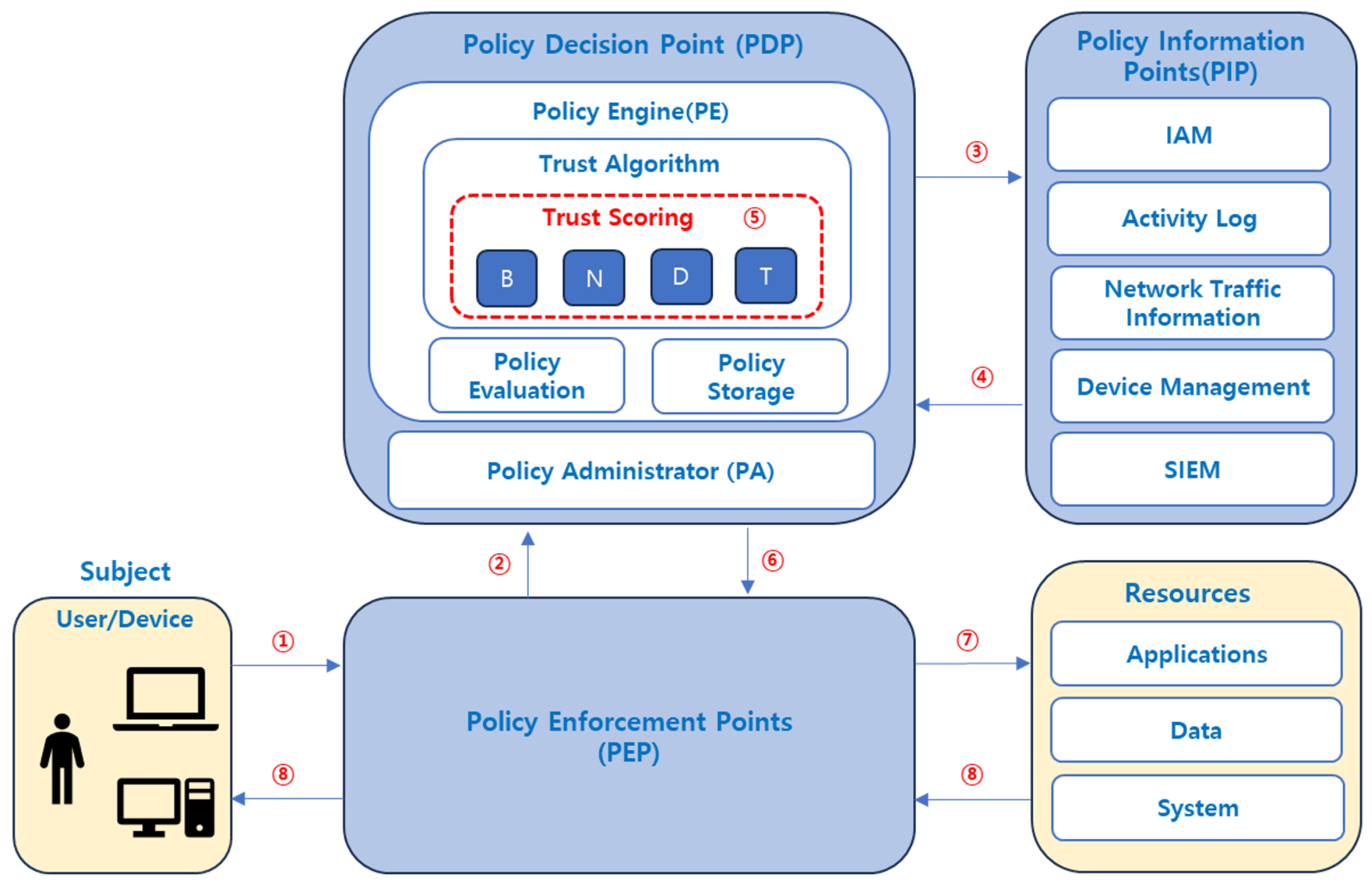
3.3. Access Control Process Using Trust Score in
- Access request: A user attempts to access a system or application.
- Request Intercept: The PEP intercepts an access request and forwards it to the PDP.
- Data collection requests: The PDP requests information from PIP-related systems to collect key element information (user behavior, network environment, device status, past threat history, etc.).
- Real-time information response: Each PIP system responds to the PDP in real time with the status of each key element related to the user.
- Calculate Trust Score: The PDP calculates a weighted Trust Score based on the collected data.
- Security decision: The PDP makes a decision to allow access, require additional authentication, or block access based on the calculated Trust Score.
- Execute the decision: The PEP executes the PDP’s decision, and the PEP connects a session to grant access to the resource as requested by the Subject.
- Send resource information: The resource responds to the user’s request and terminates the session if there is no response for a period of time.
3.4. Benefits of Trust Score-Based Access Control
- Enhanced real-time threat detection and response: Trust Score continuously assesses the health of users and devices based on real-time data. This enables immediate detection of new threats and dynamic adjustment of access permissions as they arise.
- Enhanced dynamic authentication: Trust Score automatically adjusts authentication strength based on the user’s trust level. Legitimate users get seamless access without unnecessary additional authentication, while suspicious users are asked for additional authentication (e.g., two-factor authentication, biometrics, etc.).
- Flexible security policy management: Trust Score-based systems can set customized security policies by adjusting the weights to meet enterprise needs. This ensures the flexibility of security policies for different industries (finance, healthcare, cloud, etc.).
- Improve operational efficiency: Automated Trust Score assessment and access control minimizes administrator intervention, reducing operational costs and reducing the complexity of security management.
- Improve user experience: Minimize unnecessary authentication processes for legitimate users to maintain business efficiency and increase user satisfaction.
4. Trust Score Sensitivity Analysis and Policy Simulation
4.1. Simulation Environment Setup
- Virtual Environment Configuration
- Data collection
- Weight and Threshold Configuration
- −
- Allow access if ≥ 80.
- −
- Require multi-factor authentication (MFA) if is between 60 and 79.
- −
- Block access if < 60.
- Simulation Method:
- Setting Variables by Factor:
- We set the input values for , and T to 30, 50, 70, and 90, respectively.
- We assigned weight values for the four factors using the default configuration of 0.4 (B), 0.3 (N), 0.2 (D), and 0.1 (T).
- To assess factor impact, we varied the value of one factor at a time while keeping the others fixed and observed the resulting changes.
- Simulation Tools:
- We ran large-scale simulations using data analysis tools such as Python.
- We evaluated the responsiveness and sensitivity of Trust Score based on data from various scenarios.
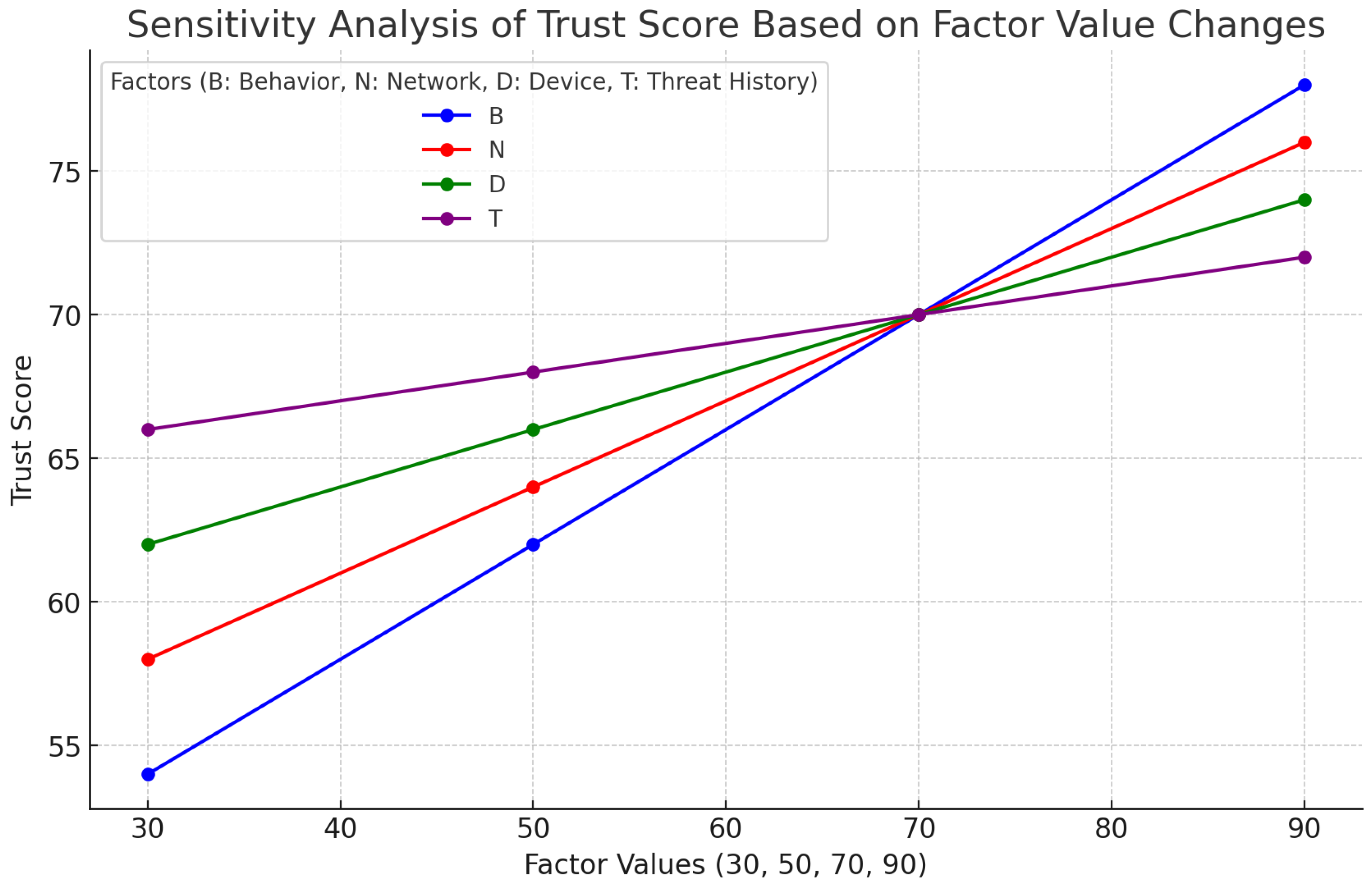
4.2. Sensitivity Analysis of Trust Score by Factor Value Changes
- Prioritization of User Behavior ()
- –
- User Behavior, set to a weight of 0.4, shows the largest change in Trust Score value (24 points) and is found to have the largest impact and the most sensitivity to changes in factor values. The higher the B value, the greater the increase in , which provides important insights in insider threat or account takeover scenarios.
- –
- Detailed analysis: A increase of 20 in the User Behavior score is associated with an average 8-point increase in . User behavior is a key factor for anomaly detection, as unusual access patterns or changes in usage behavior sensitively change the Trust Score.
- Importance of Network Environment ()
- –
- With a weight of 0.3, the network environment has a large variation in Trust Score value (18 points) and has the second-largest impact on Trust Score after user behavior. decreases rapidly in untrusted network environments, which suggests increased security in remote work environments
- –
- Detailed analysis: increased by an average of 6 points when the network environment score increased by 20. This is a useful indicator for detecting external attacks or evaluating the stability of remote access environments, and shows that network environments are volatile and subject to change, which has a constant impact on Trust Score.
- The impact of device health () and past threat history ()
- –
- With weights of 0.2 and 0.1, respectively, device state ( variance of 12 points) and past threat history ( variance of 6 points) have a relatively small impact on Trust Score. However, when utilized in conjunction, these two factors contribute to balancing security policies.
- –
- Detailed analysis: A 20-point increase in Device Health Score increased by 4 points, and a 20-point increase in Past Threat History Score increased by 2 points. Device Health Score measures device integrity and security health, and plays an important role in maintaining a trusted environment, while Past Threat History has little impact on the current Trust Score, because in a Zero Trust Architecture environment, the focus is on current health rather than past history.
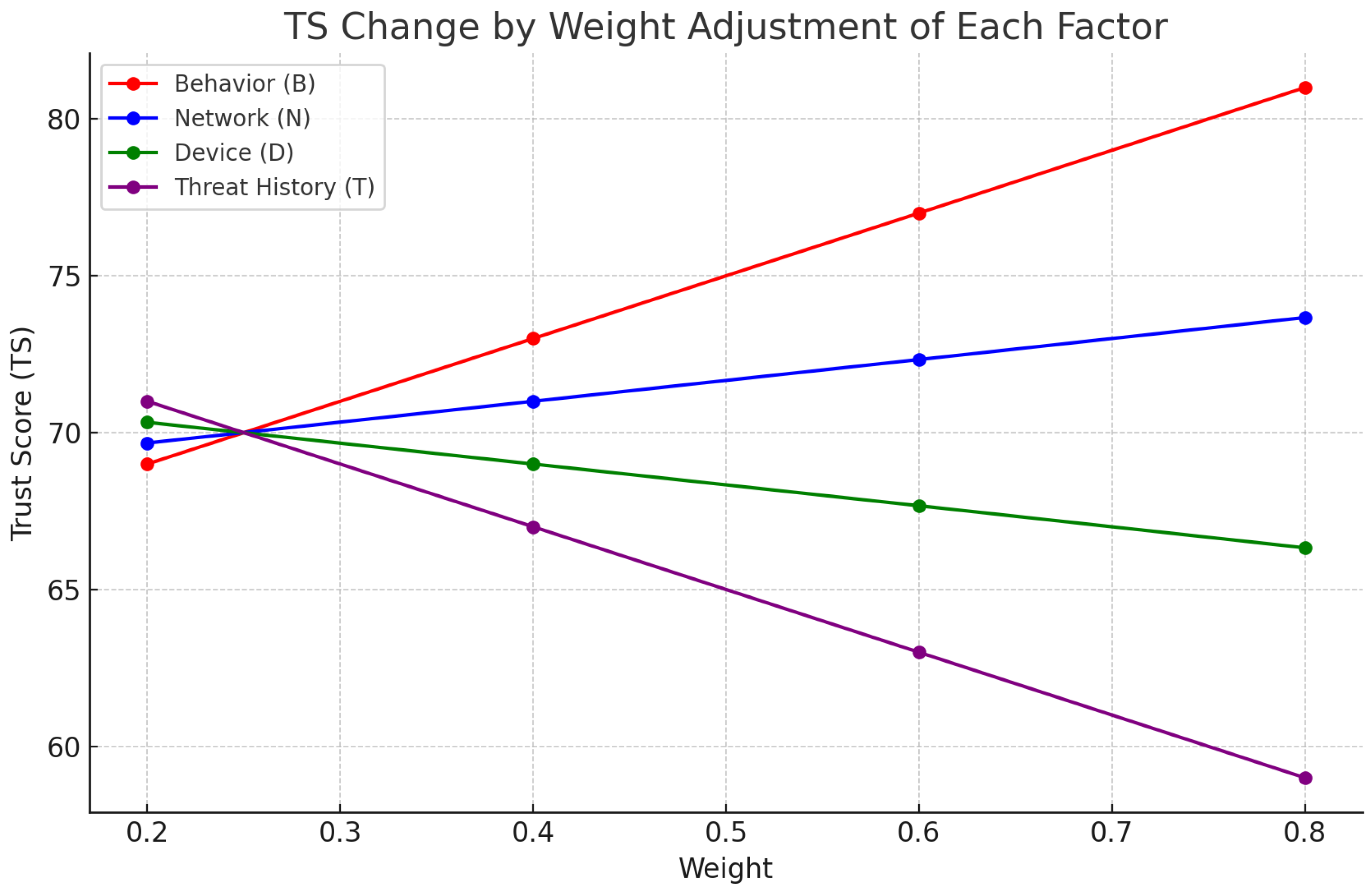
4.3. Sensitivity Analysis of Trust Score by Factor Weight Changes
- Setting fixed factor values:
- –
- B (Behavior) = 85: Login time/location/behavior falls into the normal category.
- –
- N (Network) = 75: Access to corporate internal network, no VPN bypass.
- –
- D (Device) = 65: Frequently used device, but some security warnings present.
- –
- T (Threat History) = 55: Some minor threat history exists.
- Conditions for changing weights:
- –
- For each factor (), we vary the weights to 0.2, 0.4, 0.6, and 0.8.
- –
- For the other three factors, the remaining weights are distributed equally 1:1:1, so that the total sums to 1.
- The B factor has a sharp increase in as its weight increases, contributing to the rapid induction of a permissive policy for legitimate users.
- The T factor is a threat history-based factor, with a sharp decrease in as its weight increases, enabling policy to quickly block or require additional authentication.
4.4. Summary of Simulation Results
5. Empirical Evaluation of Performance and Scalability
5.1. Experimental Setup
- CPU: Intel(R) Core(TM) Ultra 7 155H 3.80 GHz.
- Memory: 32 GB DDR4 RAM (3200 MHz).
- Storage: 1 TB NVMe SSD (PCIe 4.0).
- Operating System: Windows 11 (64-bit).
- Python Environment: Python 3.13.
- Libraries: pandas, numpy, psutil, memory_profiler, concurrent.futures.
5.2. Cross-Dataset Performance Evaluation (UNSW-NB15 vs. CICIDS2017)
5.3. Performance Analysis Under Fixed Data Volume
5.4. Scalability Testing Under Varying Dataset
- The average computation time per row remains nearly constant across all dataset sizes, indicating that the model’s processing time increases proportionally with input volume rather than exponentially.
- Memory usage also increases gradually in proportion to the data size, showing no abrupt resource spikes even at one million records.
- Most importantly, the model achieves a throughput of over 70,000 Trust Score computations per second () in all scenarios, including the largest-scale test, which suggests that the model maintains performance even under high load.
5.5. Comparative Benchmark with Legacy Access Control Models
- : Static role mapping and predefined permissions.
- : Attribute-rule matching using multiple features (e.g., protocol, flags).
- : Dynamic risk assessment based on context and event frequency.
- (Ours): Weighted arithmetic computation based on four normalized features ().
6. Conclusions and Future Research Directions
6.1. Contribution
6.2. Future Research Directions
6.3. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Ghasemshirazi, S.; Shirvani, G.; Alipour, M.A. Zero Trust: Applications, Challenges, and Opportunities. arXiv 2023, arXiv:2309.03582. [Google Scholar] [CrossRef]
- Tsai, M.; Lee, S.; Shieh, S.W. Strategy for Implementing of Zero Trust Architecture. IEEE Trans. Reliab. 2023, 72, 1234–1250. [Google Scholar] [CrossRef]
- Kindervag, J. No More Chewy Centers: Introducing the Zero Trust Model of Information Security; Forrester Research: Cambridge, MA, USA, 2010; Available online: https://www.forrester.com/report/No-More-Chewy-Centers-The-Zero-Trust-Model-Of-Information-Security/RES56682 (accessed on 6 August 2025).
- Kim, H.; Kim, Y.; Kim, S. A Study on the Security Requirements Analysis to Build a Zero Trust-based Remote Work Environment. arXiv 2024, arXiv:2401.03675. [Google Scholar] [CrossRef]
- Al-Kahtani, M.; Sandhu, R. A Hybrid Access Control Model With Dynamic COI for Secure Localization of Satellite and IoT-Based Vehicles. IEEE Access 2020, 8, 24196–24208. [Google Scholar] [CrossRef]
- Angiulli, M.; Furfaro, F.; Lax, G.; Sacca, D. Toward an Ideal Access Control Strategy for Industry 4.0 Manufacturing Systems. IEEE Access 2021, 9, 114037–114050. [Google Scholar] [CrossRef]
- Wang, J.; Wang, Z.; Song, J.; Cheng, H. Attribute and User Trust Score-Based Zero Trust Access Control Model in IoV. Electronics 2023, 12, 4825. [Google Scholar] [CrossRef]
- Bradatsch, L.; Miroshkin, O.; Trkulja, N.; Kargl, F. Zero Trust Score-Based Network-Level Access Control in Enterprise Networks. In Proceedings of the 2023 IEEE 22nd International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Changsha, China, 20–22 November 2023; IEEE: Piscataway, NJ, USA, 2024; pp. 1–8. [Google Scholar] [CrossRef]
- Kuhn, D.R.; Coyne, E.J.; Weil, T.R. Adding Attributes to Role-Based Access Control. Computer 2010, 43, 79–81. [Google Scholar] [CrossRef]
- Singh, J.; Rani, S.; Kumar, V. Role-Based Access Control (RBAC) Enabled Secure and Efficient Data Processing Framework for IoT Networks. Int. J. Commun. Netw. Inf. Secur. 2024, 16, 91–103. [Google Scholar] [CrossRef]
- Butt, A.U.R.; Mahmood, T.; Saba, T.; Bahaj, S.O.; Alamri, F.S.; Iqbal, M.W. An Optimized Role-Based Access Control Using Trust Mechanism in E-Health Cloud Environment. IEEE Access 2023, 11, 138813–138826. [Google Scholar] [CrossRef]
- Marquis, Y.A. From Theory to Practice: Implementing Effective Role-Based Access Control Strategies to Mitigate Insider Risks in Diverse Organizational Contexts. J. Eng. Res. Rep. 2024, 26, 138–154. [Google Scholar] [CrossRef]
- Mpamugo, E.; Ansa, G. Enhancing Network Security in Mobile Applications with Role-Based Access Control. J. Inf. Secur. Innov. 2024, 6, 863. [Google Scholar] [CrossRef]
- de Carvalho Junior, M.A.; Bandiera-Paiva, P. Health Information System Role-Based Access Control: Current Trends and Issues. J. Healthc. Eng. 2018, 2018, 6510249. [Google Scholar] [CrossRef]
- Hu, V.C.; Ferraiolo, D.; Kuhn, D.R.; Schnitzer, A.; Sandlin, K.; Miller, R.; Scarfone, K. Guide to Attribute-Based Access Control (ABAC) Definition and Considerations; NIST Special Publication 800-162; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2017. [Google Scholar] [CrossRef]
- Servos, D.; Osborn, S.L. Current Research and Open Problems in Attribute-Based Access Control. In Proceedings of the 2016 ACM International Workshop on Attribute-Based Access Control, New Orleans, LA, USA, 11 March 2016; Bertino, E., Ed.; ACM: New York, NY, USA, 2016; pp. 1–7. [Google Scholar] [CrossRef]
- Singh, D.; Thada, V.; Sabri, M.S. Review of Attribute-Based Access Control (ABAC) Models for Cloud Computing. In Proceedings of the IEEE International Conference on Computing, Power and Communication Technologies (ComPE), Katra, India, 4–6 September 2021; IEEE: Piscataway, NJ, USA, 2021; p. 9752139. [Google Scholar] [CrossRef]
- Fernández, M.; Thuraisingham, B. A Category-Based Model for ABAC. In Proceedings of the Third ACM Workshop on Attribute-Based Access Control (ABAC’18), Incheon, Republic of Korea, 4 June 2018; ACM: New York, NY, USA, 2018; pp. 32–34. [Google Scholar] [CrossRef]
- Panende, M.F.; Riadi, I.; Prayudi, Y. Comparison of Attribute-Based Access Control (ABAC) Model and Rule-Based Access (RBAC) to Digital Evidence Storage (DES). Int. J. Adv. Comput. Sci. Appl. 2018, 9, 136–143. [Google Scholar] [CrossRef]
- Xu, Y.; Zeng, Q.; Wang, G.; Zhang, C.; Ren, J.; Zhang, Y. An Efficient Privacy-Enhanced Attribute-Based Access Control Mechanism. Concurr. Comput. Pract. Exp. 2019, 31, e5556. [Google Scholar] [CrossRef]
- Wiefling, S.; Dürmuth, M.; Lo Iacono, L. Verify It’s You: How Users Perceive Risk-Based Authentication. IEEE Secur. Priv. 2021, 19, 32–42. [Google Scholar] [CrossRef]
- Makowski, J.-P.; Pöhn, D. Evaluation of Real-World Risk-Based Authentication at Online Services Revisited: Complexity Wins. In Proceedings of the 2023 ACM SIGSAC Conference on Computer and Communications Security, Copenhagen, Denmark, 26–30 November 2023; ACM: New York, NY, USA, 2023; pp. 3125–3137. [Google Scholar] [CrossRef]
- Büttner, A.; Pedersen, A.T.; Wiefling, S.; Gruschka, N.; Lo Iacono, L. Is It Really You Who Forgot the Password? When Account Recovery Meets Risk-Based Authentication. In Proceedings of the 2024 International Conference on Information Security and Cryptology, Seoul, Republic of Korea, 13–15 December 2024; Springer: Cham, Switzerland, 2024; pp. 345–359. [Google Scholar] [CrossRef]
- Unsel, V.; Wiefling, S.; Gruschka, N.; Lo Iacono, L. Risk-Based Authentication for OpenStack: A Fully Functional Implementation and Guiding Example. In Proceedings of the 2023 ACM Conference on Cloud Computing Security Workshop, Copenhagen, Denmark, 26 November 2023; ACM: New York, NY, USA, 2023; pp. 115–125. [Google Scholar] [CrossRef]
- Wiefling, S.; Jørgensen, P.R.; Thunem, S.; Lo Iacono, L. Pump Up Password Security! Evaluating and Enhancing Risk-Based Authentication on a Real-World Large-Scale Online Service. ACM Trans. Priv. Secur. 2022, 25, 21. [Google Scholar] [CrossRef]
- Wiefling, S.; Dürmuth, M.; Lo Iacono, L. More Than Just Good Passwords? A Study on Usability and Security of Risk-Based Authentication. In Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, Orlando, FL, USA, 9–13 November 2020; ACM: New York, NY, USA, 2020; pp. 1837–1851. [Google Scholar] [CrossRef]
- Rose, S.; Borchert, O.; Mitchell, S.; Connelly, S. Zero Trust Architecture; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2020; NIST Special Publication 800-207. [Google Scholar] [CrossRef]
- Ward, R.; Beyer, B. BeyondCorp: A New Approach to Enterprise Security. Login 2014, 39, 6–11. Available online: https://research.google/pubs/beyondcorp-a-new-approach-to-enterprise-security/ (accessed on 23 August 2025).
- Osborn, B.; Allievi, A.; Beyer, B.; More, A.; Ward, R. BeyondCorp: Design to Deployment at Google. Login 2016, 41, 28–34. Available online: https://research.google/pubs/beyondcorp-design-to-deployment-at-google/ (accessed on 23 August 2025).
- Spear, B.; Beyer, B.; Cittadini, L.; Saltonstall, M. BeyondCorp: The Access Proxy. Login 2016, 41, 28–33. Available online: https://research.google/pubs/beyondcorp-the-access-proxy/ (accessed on 23 August 2025).
- Beraud, P.; Grasset, J.-Y.; Jumelet, A. Implementing a Zero Trust Approach with Azure Active Directory; Microsoft France: Paris, France, 2019; Available online: https://www.microsoft.com/en-us/download/details.aspx?id=58366 (accessed on 23 August 2025).
- Department of Defense. DoD Zero Trust Strategy; Department of Defense: Washington, DC, USA, 2022. Available online: https://dodcio.defense.gov/Portals/0/Documents/Library/DoD-ZTStrategy.pdf (accessed on 23 August 2025).
- George, A.T.; Neve, H.R.; Muraleedharan, N. A Trust Score Calculation Approach for Zero Trust Access System. In Proceedings of the 2023 IEEE 20th India Council International Conference (INDICON), Ahmedabad, India, 15–17 December 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 392–397. Available online: https://www.proceedings.com/content/073/073473webtoc.pdf (accessed on 23 August 2025).
- Park, U.H.; Hong, J.H.; Kim, A.; Son, K.H. Endpoint Device Risk-Scoring Algorithm Proposal for Zero Trust. Electronics 2023, 12, 1906. [Google Scholar] [CrossRef]
- Wang, R.; Li, C.; Zhang, K.; Tu, B. Zero-Trust Based Dynamic Access Control for Cloud Computing. Cybersecurity 2025, 8, 12. [Google Scholar] [CrossRef]
- Kasongo, S.M.; Sun, Y. Performance Analysis of Intrusion Detection Systems Using a Feature Selection Method on the UNSW-NB15 Dataset. J. Big Data 2020, 7, 105. [Google Scholar] [CrossRef]
- Verizon. 2023 Data Breach Investigations Report (DBIR); Verizon Enterprise: New York, NY, USA, 2023; Available online: https://www.verizon.com/business/resources/T87b/reports/2023-dbir-executive-summary.pdf (accessed on 23 August 2025).
- Jeong, E.; Yang, D. Trust Score-Based Modeling—Experimental Code Repository. Available online: https://github.com/Yang9un/Trust-Score-Based-Modeling (accessed on 23 August 2025).
| Access Control Methods Eatures | Pros | Cons | Application Examples | Real-Time Detection | Granting Access | Flexibility | |
|---|---|---|---|---|---|---|---|
| RBAC | Granting access based on roles | Management simplicity, policy consistency | Lack of dynamic change response | Managing user groups in the enterprise | × (Not supported) | Role-based presets | Low |
| ABAC | Grant access based on attributes when conditions are met | Flexible, fine-grained access control | Complicated to set up and manage policies | Cloud environments, multi-system | × (Not supported) | Attribute-based conditional granting | High |
| RBA | Determine access with real-time risk level assessment | Better user experience, security balance | Requires risk assessment accuracy | Online services, finance | △ (limited) | Real-time granting based on risk level | Medium |
| TS-based ZTA | Control access with a multi-factor-based Trust Score assessment | Dynamic access, high security | Computational complexity, high computational burden | Zero Trust Architecture, high-security enterprises, government organizations | ✓ (real-time) | Dynamic granting based on Trust Score | Very high |
| Detail Item | Description | Detail Item Score |
|---|---|---|
| ① Login Frequency | Establish normal login patterns, and consider deviations from those norms as security risks (login frequency per day) | 20 pts: Normal (1 to 5 times) 15 pts: Slightly abnormal (6 to 10 times) 10 pts: Suspicious (11 to 15 times) 5 pts: At risk (16+) 0 pts: Very high risk level (30+) |
| ② Failed Login Attempts | Utilize login failure counts to detect unusual login attempts | 20 pts: 0 to 2 failures (Normal range) 15 pts: 3–5 failed attempts (Some mistakes) 10 pts: 6–10 failed attempts (Abnormal patterns) 5 pts: 11–50 failed attempts (Brute force likely) 0 pts: 50+ failures (Automated attack attempts) |
| ③ Off-Hours Login | Assess security threats by detecting users accessing different time zones than they normally log in to | 20 pts: Normal business hours (9:00–18:00) 15 pts: Acceptable overtime (18:00–22:00 login) 10 pts: Unusual hours (22:00–02:00 login) 5 pts: Weekend and holiday logins (High risk) 0 pts: Very high risk time logins (02:00–05:00) |
| ④ New Location Login | Detect anomalous behavior where users sign in from places, they do not normally sign in from | 20 pts: Traditional login region (same as before) 15 pts: Different region within the same country 10 pts: New country login (low risk) 5 pts: New country login (medium risk) 0 pts: Impossible move detected |
| ⑤ Downloading large amounts of data | Evaluate for potential attacks like account takeover or data exfiltration when users download unusually large data volumes rapidly | 20 pts: Normal download (500 MB or less per day) 15 pts: Minor over download (2 GB–5 GB) 10 pts: Unusual downloads (5 GB–10 GB) 5 pts: High risk (10 GB–50 GB downloads per day) 0 pts: Data breach (50 GB or more downloads) |
| Detail Item | Description | Detail Item Score |
|---|---|---|
| ① IP Reputation | Evaluate your user’s IP address to see if it’s on a malicious IP list | 20 pts: Highly trusted IP 15 pts: Typical IP 10 pts: IP with warnings 5 pts: Blacklisted IP 0 pts: Need immediate access blocked |
| ② VPN Usage | Detect VPN usage to assess external IP hiding and anonymous access | 20 pts: Enterprise-approved VPN 15 pts: Trusted VPN 10 pts: Known General VPN 5 pts: Use an anonymous VPN service 0 pts: Using a known malicious VPN service |
| ③ Anomalous Network Traffic | Detect anomalies in user traffic, analyze anomalous data transfer volumes and access frequency | 20 pts: Normal traffic pattern 15 pts: Minor anomalies (slightly increase) 10 pts: Increased abnormal traffic 5 pts: Lots of abnormal traffic 0 pts: Malicious traffic |
| ④ Access Location Reliability | Evaluate access in non-traditional countries or high-risk areas | 20 pts: Registered trusted location 15 pts: Previously frequented location 10 pts: New location (low risk) 5 pts: New location (medium risk) 0 pts: Accessing high-risk countries/regions |
| ⑤ Network Stability | Evaluate the reliability of network connectivity, frequency and duration of connection session interruptions | 20 pts: Very stable (no outages) 15 pts: Slightly unstable (intermittent reconnection) 10 pts: Intermittent disconnections 5 pts: Frequent disconnections 0 pts: Very unstable or suspected DDoS |
| Detail Item | Description | Detail Item Score |
|---|---|---|
| ① Security Patch Status | Assess whether you have the latest security patches | 20 pts: All security patches applied 15 pts: Some critical patches missing 10 pts: Many patches missing 5 pts: Major patches not applied 0 pts: Very poorly patched |
| ② Antivirus Status | Evaluate whether your antivirus program is active and up-to-date | 20 pts: Up-to-date and active 15 pts: Active but delayed updates 10 pts: Inactive 5 pts: Long out of date 0 pts: No antivirus installed |
| ③ Device Authentication | Assess whether a device is pre-authenticated | 20 pts: Authorized corporate-managed device 15 pts: Personally authorized device 10 pts: Unenrolled but identifiable device 5 pts: Unauthorized device 0 pts: Unidentified or illegal devices |
| ④ Device Integrity | Assess device integrity status, such as whether it is rooted or jailbroken | 20 pts: Full integrity 15 pts: Minor anomalies 10 pts: Questionable integrity 5 pts: Evidence of jailbreak or rooting attempts 0 pts: Obvious integrity compromise |
| ⑤ Device Encryption | Evaluate whether your device applies encryption when storing and transmitting data | 20 pts: Fully encrypted 15 pts: Only sensitive data is encrypted 10 pts: Partial or limited encryption 5 pts: No encryption applied 0 pts: High risk of sensitive data leakage |
| Detail Item | Description | Detail Item Score |
|---|---|---|
| ① Threat History | Evaluate a user’s involvement in past security incidents | 20 pts: No incident history 15 pts: Minor accident history (1 incident) 10 pts: Moderate accident history (2–3) 5 pts: Severe incident history (4 or more) 0 pts: Repeated and persistent incidents |
| ② Security Policy Violation History | Evaluate a user’s history of security policy violations | 20 pts: No violation history 15 pts: Minor policy violation (1 incident) 10 pts: Repeated minor violations (2–3 times) 5 pts: Major policy violations (1 or more) 0 pts: Serious violations requiring immediate action |
| ③ Account Compromise History | Assess whether your account has been compromised or breached in the past | 20 pts: No history of violations 15 pts: Suspected minor breach (unconfirmed) 10 pts: 1 account breach (low risk) 5 pts: Multiple breaches (medium risk) 0 pts: Serious breach history |
| ④ Frequency of Policy Violation | Assess how often users violate security policies | 20 pts: No policy violations 15 pts: Infrequent (once a year or less) 10 pts: Intermittent (2–3 times per year) 5 pts: Frequent (4 or more times per year) 0 pts: Very frequent (1 or more per month) |
| ⑤ Response to Past Threats | Responding to past threats and evaluating possible improvements | 20 pts: Immediate response and recurrence fully prevented 15 pts: Rapid response and partial prevention of recurrence 10 pts: Responded but did not prevent recurrence 5 pts: Delayed response and risk of recurrence 0 pts: No response and immediate action required |
| Baseline: 90 | Baseline: 70 | Baseline: 50 | Baseline: 30 | ||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| B | N | D | T | T.S | B | N | D | T | T.S | B | N | D | T | T.S | B | N | D | T | T.S |
| 90 | 90 | 90 | 90 | 90 | 70 | 70 | 70 | 70 | 70 | 50 | 50 | 50 | 50 | 50 | 30 | 30 | 30 | 30 | 30 |
| Varying B: | |||||||||||||||||||
| 70 | 90 | 90 | 90 | 82 | 90 | 70 | 70 | 70 | 78 | 90 | 50 | 50 | 50 | 66 | 90 | 30 | 30 | 30 | 54 |
| 50 | 90 | 90 | 90 | 74 | 50 | 70 | 70 | 70 | 62 | 70 | 50 | 50 | 50 | 58 | 70 | 30 | 30 | 30 | 46 |
| 30 | 90 | 90 | 90 | 66 | 30 | 70 | 70 | 70 | 54 | 30 | 50 | 50 | 50 | 42 | 50 | 30 | 30 | 30 | 38 |
| Varying N: | |||||||||||||||||||
| 90 | 70 | 90 | 90 | 84 | 70 | 90 | 70 | 70 | 76 | 50 | 90 | 50 | 50 | 62 | 30 | 90 | 30 | 30 | 48 |
| 90 | 50 | 90 | 90 | 78 | 70 | 50 | 70 | 70 | 64 | 50 | 70 | 50 | 50 | 56 | 30 | 70 | 30 | 30 | 42 |
| 90 | 30 | 90 | 90 | 72 | 70 | 30 | 70 | 70 | 58 | 50 | 30 | 50 | 50 | 44 | 30 | 50 | 30 | 30 | 36 |
| Varying D: | |||||||||||||||||||
| 90 | 90 | 70 | 90 | 86 | 70 | 70 | 90 | 70 | 74 | 50 | 50 | 90 | 50 | 58 | 30 | 30 | 90 | 30 | 42 |
| 90 | 90 | 50 | 90 | 82 | 70 | 70 | 50 | 70 | 66 | 50 | 50 | 70 | 50 | 54 | 30 | 30 | 70 | 30 | 38 |
| 90 | 90 | 30 | 90 | 78 | 70 | 70 | 30 | 70 | 62 | 50 | 50 | 30 | 50 | 46 | 30 | 30 | 50 | 30 | 34 |
| Varying T: | |||||||||||||||||||
| 90 | 90 | 90 | 70 | 88 | 70 | 70 | 70 | 90 | 72 | 50 | 50 | 50 | 90 | 54 | 30 | 30 | 30 | 90 | 36 |
| 90 | 90 | 90 | 50 | 86 | 70 | 70 | 70 | 50 | 68 | 50 | 50 | 50 | 70 | 52 | 30 | 30 | 30 | 70 | 34 |
| 90 | 90 | 90 | 30 | 84 | 70 | 70 | 70 | 30 | 66 | 50 | 50 | 50 | 30 | 48 | 30 | 30 | 30 | 50 | 32 |
| Weight | Behavior (B) | Network (N) | Device (D) | Threat History (T) |
|---|---|---|---|---|
| 0.2 | 69 | 69.67 | 70.33 | 71 |
| 0.4 | 73 | 71 | 69 | 67 |
| 0.6 | 77 | 72.33 | 67.67 | 63 |
| 0.8 | 81 | 73.67 | 66.33 | 59 |
| Element | TS Variation | Sensitivity Direction | Policy Effect |
|---|---|---|---|
| Behavior (B) | +12.00 | Positive | Promotes allowance for normal users |
| Threat History (T) | −12.00 | Negative | Promotes blocking for threat users |
| Network (N) | +4.00 | Positive | Supplements policy with environmental context |
| Device (D) | −4.00 | Negative | Filters based on device trustworthiness |
| Perspective | Key Elements | Role | Policy Utilization |
|---|---|---|---|
| Zero Trust Operation Strategy | B, N | Real-time status evaluation and access control | User context-based policy setting, MFA inducement |
| Policy Design Based on Sensitivity Analysis | B, T | High sensitivity → Induces policy switching | Automatic trigger criteria for allow/block policies |
| Integrated Strategy | B (common) + N or T | Flexible weight optimization according to objectives | Adaptive policy tuning based on convenience or security enhancement |
| Dataset | Accuracy | Precision | Recall | F1-Score | ROC-AUC |
|---|---|---|---|---|---|
| UNSW-NB15 | 0.9588 | 0.9631 | 0.9770 | 0.9700 | 0.9935 |
| CICIDS2017 | 0.9999 | 0.9999 | 1.0000 | 1.0000 | 1.0000 |
| Factor | Meaning | Mapped Features (UNSW-NB15) | Description |
|---|---|---|---|
| B (User Behavior) | Behavioral patterns and connection characteristics of the user | ct_state_ttl, ct_dst_sport_ltm, is_sm_ips_ports | Reflects behavioral traits such as connection state, frequent port reuse, and multi-port/multi-IP activities |
| N (Network Environment) | Characteristics of the network protocol and connection context | proto, service, state | Represents the protocol type, service category, and session status to evaluate the trustworthiness of the network environment |
| D (Device Status) | Activity and response traits of the device | sttl, dpkts, dbytes | Indicates device behavior using TTL, the number of packets sent, and total bytes exchanged |
| T (Threat History) | Historical record of attacks or anomalies | attack_cat, label | Uses known attack categories and anomaly labels to reflect historical exposure to threats |
| Data Size (Rows) | Total Time (s) | Avg Time (ms/Row) | Memory Usage (MB) | TPS (Trust Scores/s) |
|---|---|---|---|---|
| 175,000 | 2.41 | 0.0138 | 7.72 | 72,656 |
| Data Size (Rows) | Total Time (s) | Avg Time (ms/Row) | Memory Usage (MB) | TPS (Trust Scores/s) |
|---|---|---|---|---|
| 10,000 | 0.14 | 0.0140 | 6.25 | 71,429 |
| 50,000 | 0.68 | 0.0136 | 6.78 | 73,529 |
| 100,000 | 1.36 | 0.0136 | 7.29 | 73,529 |
| 1,000,000 | 13.74 | 0.0137 | 9.14 | 72,766 |
| Model | Avg Latency (ms/Record) | Throughput (TPS) |
|---|---|---|
| RBAC | 0.0490 | 20,416 |
| ABAC | 0.0466 | 21,452 |
| RBA | 0.0523 | 19,110 |
| T.S. (Ours) | 0.0137 | 70,200 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jeong, E.; Yang, D. A Trust Score-Based Access Control Model for Zero Trust Architecture: Design, Sensitivity Analysis, and Real-World Performance Evaluation. Appl. Sci. 2025, 15, 9551. https://doi.org/10.3390/app15179551
Jeong E, Yang D. A Trust Score-Based Access Control Model for Zero Trust Architecture: Design, Sensitivity Analysis, and Real-World Performance Evaluation. Applied Sciences. 2025; 15(17):9551. https://doi.org/10.3390/app15179551
Chicago/Turabian StyleJeong, Eunsu, and Daeheon Yang. 2025. "A Trust Score-Based Access Control Model for Zero Trust Architecture: Design, Sensitivity Analysis, and Real-World Performance Evaluation" Applied Sciences 15, no. 17: 9551. https://doi.org/10.3390/app15179551
APA StyleJeong, E., & Yang, D. (2025). A Trust Score-Based Access Control Model for Zero Trust Architecture: Design, Sensitivity Analysis, and Real-World Performance Evaluation. Applied Sciences, 15(17), 9551. https://doi.org/10.3390/app15179551







