1. Introduction
In the context of the widespread use of distributed computing and cloud infrastructures for storing and protecting confidential information, secret sharing schemes play a crucial role in ensuring reliable and fault-tolerant access to data [
1,
2]. The most common solutions are classical threshold schemes (e.g., Shamir’s scheme), which allow the secret to be reconstructed from any subset of
out of
participants. These schemes enable the distribution of confidential information among multiple parties without storing it in full at a single location, significantly enhancing data security [
3,
4].
Secret sharing schemes make it possible to divide confidential information
Q into
parts and distribute them among
participants. To reconstruct the original secret, it is sufficient to have any k of them. A scheme of this type is also referred to as an (
)—threshold secret sharing scheme [
5,
6].
Currently, the most widely used methods include Shamir’s scheme as well as the schemes of Mignotte, Asmuth–Bloom, and others. A distinctive feature of the Mignotte and Asmuth–Bloom schemes is the use of the Chinese Remainder Theorem (CRT) in the secret sharing process [
7]. The CRT allows the reconstruction of a numerical value from its representation in a system of residues with pairwise coprime moduli. This provides the mathematical and algorithmic foundation for secret reconstruction schemes. However, the Asmuth–Bloom and Mignotte schemes impose significant constraints on the secret—value
. In the first case, it is limited to the set
, while in the second case, the range of possible values is substantially reduced due to the exclusion of a sufficiently large interval of numbers.
Shamir’s secret sharing scheme was first introduced by Adi Shamir in 1979 in his paper How to Share a Secret [
8]. This work described an
) threshold scheme that allows reconstruction of the secret from any
out of
parts. The scheme relies on the Lagrange interpolation polynomial, which makes it possible to reconstruct the original secret when k valid shares are available [
9,
10].
Advantages of Shamir’s Scheme:
Good scalability. The number of participants can be increased to a value comparable to the size of the finite field , while the minimum number of shares required to reconstruct the secret remains unchanged.
Perfect distribution. Each share (also referred to as a “shadow”) has the same size as the original secret, making the scheme efficient in terms of data volume.
Flexibility and renewability. New shares can be generated for the same secret using a different polynomial. This reduces the risk of compromise, as leaked old shares cannot be used unless they originate from the same polynomial.
Cryptographic strength. If an adversary possesses fewer than k shares, they cannot reconstruct even a single bit of the secret. This level of security is mathematically proven.
Disadvantages of Shamir’s Scheme:
Dependence on a trusted dealer. The basic implementation assumes that the central trusted party (the dealer) correctly generates and distributes the shares. If the dealer is untrustworthy, they may provide incorrect values, making it impossible to reconstruct the secret.
Risk of sabotage by the dealer. A malicious or unreliable dealer can intentionally distort the data, disrupt the scheme’s integrity, and even cause complete failure.
In [
11], the secret sharing problem is considered from an information-theoretic perspective. The authors propose a method in which only specific participants can reconstruct the secret. They also explore information security techniques in the presence of noise in communication channels used to transmit the shares.
In [
12], a time-based secret sharing scheme is introduced. The authors examine approaches for ensuring information-theoretic security by applying temporal constraints.
In [
13], a threshold secret sharing scheme based on the Chinese Remainder Theorem is proposed. It is shown to efficiently detect errors and even reveal intentional tampering.
The authors of [
14] developed an efficient and reliable threshold scheme for sharing multiple secrets using modern cryptographic tools based on elliptic curves and bilinear pairings.
In [
15], the Asmuth–Bloom scheme and its modification are examined. The modified version uses fractal geometry as the encoding function. A numerical method for computing shares is also proposed, enabling simultaneous splitting and encoding of images without the need for additional algorithms, thus avoiding increased computational complexity.
A new threshold scheme based on lattices is described in [
16], with its distinguishing feature being the ability for participants to verify the correctness of their received shares. The security of the scheme relies on the computational hardness of lattice problems.
In [
17], an encryption algorithm for color images based on the two-dimensional Logistic–Rulkov Neural Map (2D-LRNM) is presented. It is designed to ensure efficient and secure image transmission, particularly in the context of social networks. The algorithm provides separate processing of the three-color channels, incorporates inter-channel interaction, and employs a block-based parallel encryption scheme. The key stream is generated using the 2D-LRNM, which exhibits strong chaotic properties. Experimental results demonstrate a high level of cryptographic security of the proposed approach, as well as a significant reduction in computation time.
The proposed approach has found application in the generation of personal cryptographic keys used in biometric authentication systems and public key infrastructures, where the scheme supports multi-user authorization with the help of cryptographic hardware modules.
However, such schemes assume the homogeneity of participants and do not account for their functional or organizational affiliation. This makes classical schemes vulnerable in situations where
All participants belong to the same subgroup (e.g., the same department or one side of a conflict of interest);
Collusion is possible within a single group;
Strict adherence to principles of role-based access control or regulatory compliance is required (e.g., dual control, the four-eyes principle, or zero trust policies).
Thus, a contradiction arises: on the one hand, joint access to a resource is required, but on the other hand, it must be ensured that access is granted only with the participation of representatives from different groups with distinct roles and trust levels.
To address these limitations, we propose a secret sharing scheme with mandatory participation of representatives from each subgroup. In this scheme, participants are pre-assigned to logical groups based on roles or trust boundaries, and the secret can only be reconstructed if at least one representative from each subgroup is involved.
In this study, the main mathematical quantities and their notations were used. They are summarized in
Table 1.
2. Materials and Methods
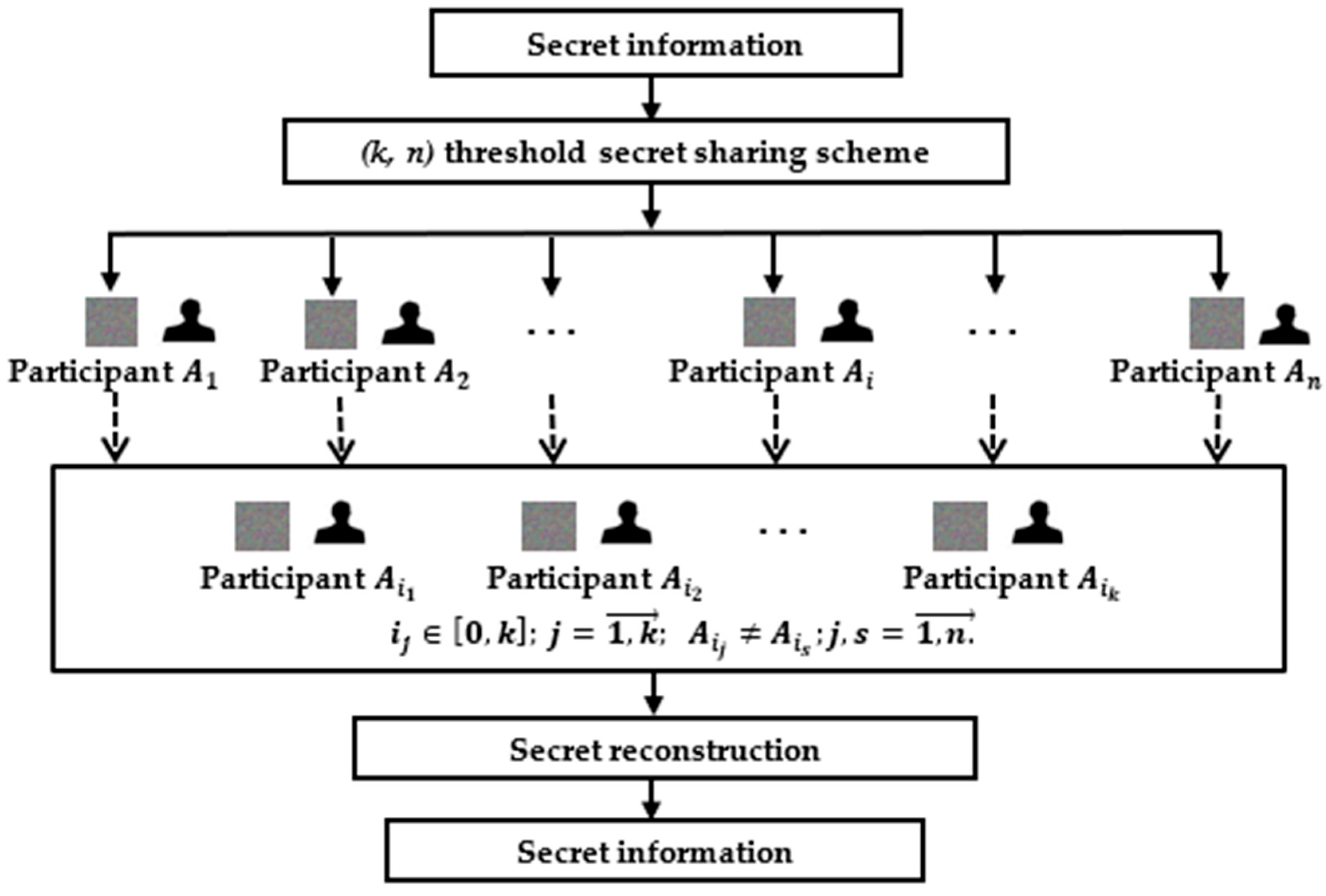
To enable secure distributed storage, a cryptographic secret sharing approach is employed. Confidential data is divided into several shares, which are stored in independent cloud repositories. The original information can be reconstructed only by combining a sufficient number of shares, ensuring both fault tolerance and protection against unauthorized access (see
Figure 1).
The core idea of this approach is that no single share contains enough information to reconstruct the original biometric data (templates). Full recovery of the secret is only possible by combining a predefined number of shares, referred to as the threshold value. This provides a high level of security, particularly in distributed data storage and processing infrastructures.
A wide range of secret sharing schemes has been developed to implement these mechanisms, each with its own characteristics, advantages, and limitations. When choosing the optimal solution, special attention should be paid to efficiency: the scheme must ensure a high level of confidentiality while minimizing computational and memory costs.
The key criteria influencing these parameters are as follows:
Perfection—ensures that if fewer than the threshold number of participants (less than ) collaborate, no information about the secret can be obtained. This guarantees the highest level of confidentiality.
Ideality—means that the size of each share is equal to the size of the original secret. Such a scheme avoids additional memory overhead and is efficient in terms of storage.
Resource intensity—refers to the amount of memory required for storing and processing the data, including the shares and any auxiliary information. The lower the required memory, the more efficient the scheme.
Algorithmic complexity—reflects the computational load on the system when generating shares and reconstructing the secret. Efficient schemes minimize the number of operations, which is particularly important for systems with limited computational capacity.
2.1. Lagrange Interpolation Polynomial
Experimental data often consist of a set of points describing the behavior of a measured signal over time or with respect to another variable. For theoretical analysis of such data, it is necessary to construct an approximating function that connects discrete values with a continuous representation—an interpolation polynomial of degree . One of the most widely used methods is Lagrange interpolation. The Lagrange interpolation polynomial (LIP) is a polynomial of degree that passes through all the given data points. These points may be obtained either experimentally or through random sampling at different time moments. The time intervals between the points may be uneven.
The general form of the Lagrange interpolation polynomial of degree
is given by the formula:
where
is the degree of the polynomial
,
is the value of the interpolated function
at the interpolation node
,
are the Lagrange basis polynomials, defined as follows:
Each basis polynomial equals zero at all interpolation nodes except
, where it is equal to one. The main advantage of the Lagrange form is that it explicitly expresses the values of the interpolated function at the specified points, which is especially convenient when function values change while the nodes remain fixed. Moreover, the number of arithmetic operations required to construct the Lagrange polynomial is on the order of
, making it one of the most efficient among known analytical representations of interpolation polynomials [
9,
18].
2.2. Chinese Remainder Theorem
The Chinese Remainder Theorem (CRT) is a fundamental result in number theory that makes it possible to solve systems of congruences with pairwise coprime moduli. It is widely used in cryptography, computational algorithms, coding theory, secret sharing schemes, and other fields [
19,
20].
Let
be pairwise coprime natural numbers, and
be some integers. Then there exists a unique (within a fixed modulus) integer
that satisfies the following system of congruences:
Furthermore, any two solutions A and B of this system are congruent to each other modulo the product of all moduli:
in other words, the solution to the system of congruences is unique modulo
.
Let us introduce the following notation:
; is the quotient of the total modulus divided by the corresponding modulus ;
denotes the multiplicative inverse of
modulo
, which means:
Then the general solution
can be explicitly represented by:
This formula makes it possible to efficiently compute the solution of the system of congruences and is frequently used in practice in cryptographic algorithms.
3. Results
3.1. Proposed Secret Sharing Scheme with Mandatory Subgroup Participation
This study proposes a secret sharing scheme based on a combination of traditional methods and enhanced to increase the level of information—theoretic security. At the same time, the scheme is designed to perform its main function—reliably partitioning confidential information into multiple shares and allowing its reconstruction only by a specified group of participants.
The main feature of the proposed scheme lies in combining two methods—the Lagrange interpolation form and the Chinese remainder theorem. Next, we will describe the algorithm in more detail.
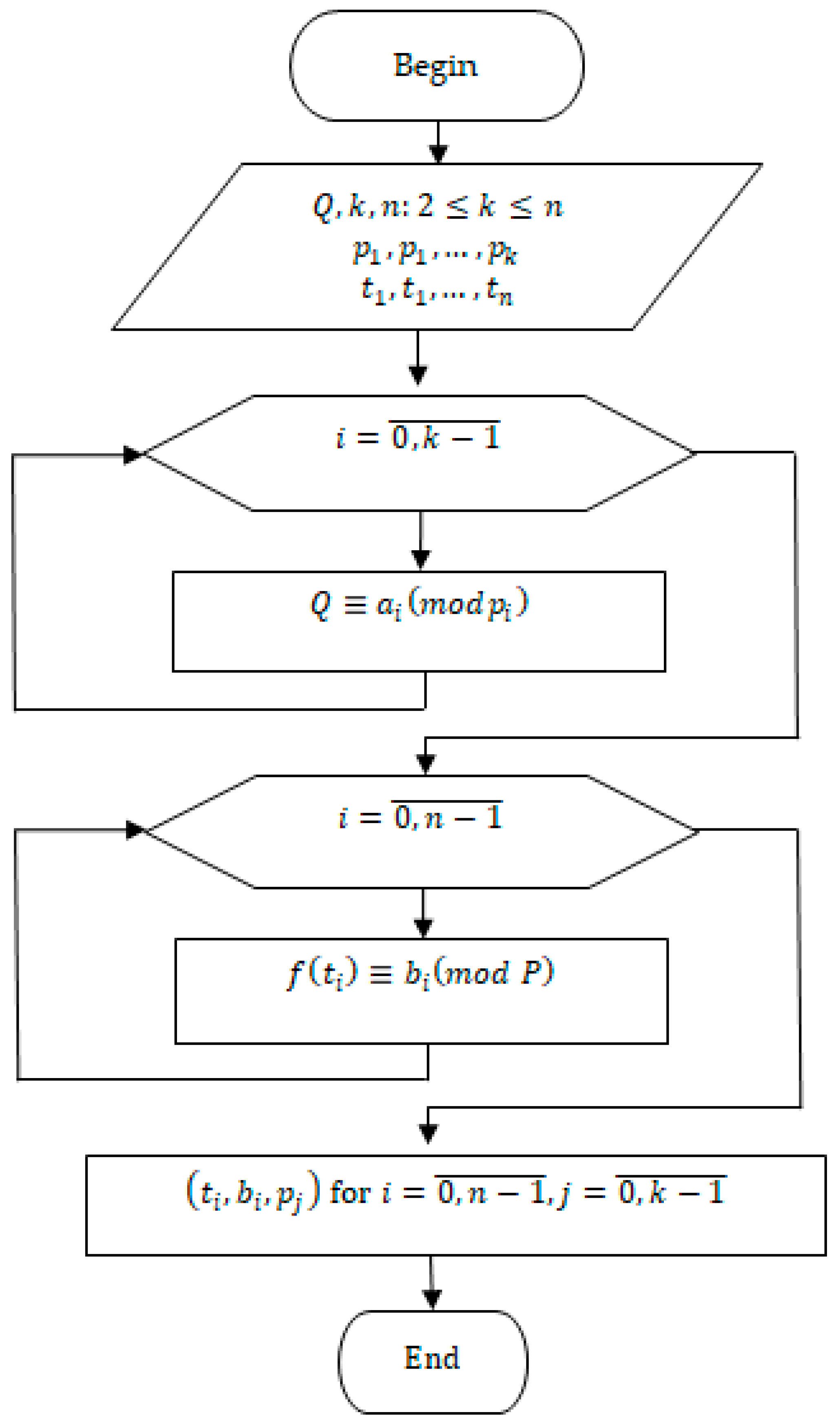
3.1.1. Secret Distribution
We consider to be the total number of participants and to be the number of participants required to reconstruct the secret. As in other similar algorithms, any participants can successfully reconstruct the secret, while a group with fewer participants cannot do so. The condition must be satisfied, as it is essential for the correctness of the scheme. The inequality guarantees the requirement of collective participation and excludes the possibility of unilateral secret reconstruction. The condition reflects a natural constraint, according to which the number of required shares cannot exceed the total number of participants, thereby ensuring the feasibility of the reconstruction procedure.
In accordance with the number of participants who can reconstruct the secret, primes are selected.
We denote the secret (in this case, biometric data or a template) by
. Then the coefficients
of the polynomial
for
are computed according to the following relationships (6):
Therefore, polynomial
is defined as follows:
For each participant, a number
is randomly selected in such a way that
, where
. Subsequently, components of the shares for all
participants are computed by Formula (8):
Here . As a result, each participant receives their share in the following form: for .
The block diagram of secret sharing is shown in
Figure 2.
Each participant’s share is divided into
groups. Each group uses one modulus. To reconstruct the secret, it is necessary to involve at least one representative from each group. Otherwise, the secret cannot be recovered. The following is a pseudocode example of a scheme with a threshold of (5, 10) (Algorithm 1):
| Algorithm 1. Example of a scheme with a threshold of (5, 10): |
//Step 1: Initialize input values
1://Shares of participants
2:,,,,//Modules
//Step 2: Randomly distributepairs among groups
3: Group 1 =
4: Group 2 =
5: Group 3 =
6: Group 4 =
7: Group 5 =
//Step 3: Assign moduli to the groups ModulAssignments:
8: → Group 1
9: → Group 2
10: → Group 3
11: → Group 4
12: → Group 5
//Step 4: Select at least one representative from each group
SelectedParticipants = {
13: Group 1: ,
14: Group 2: ,
15: Group 3: ,
16: Group 4: ,
17: Group 5: ,
} |
It should be emphasized that in the proposed scheme, the term “selection of a representative of each group” does not refer to generators of the multiplicative or additive group of integers modulo a prime . A subgroup representative is a participant in the scheme who is assigned a specific share of the secret associated with the modulus . Thus, the term “representative” pertains exclusively to the organizational role within the scheme, rather than to the mathematical concept of a “group generator”.
The proposed scheme differs from classical approaches such as Shamir’s scheme (based on Lagrange interpolation), Blakley’s scheme (using vector spaces), and the Karnin-Greene-Hellman scheme (based on solving systems of linear equations), by providing higher resilience to participant compromise attacks. Dividing participants into groups adds an extra layer of protection: even if an adversary gains access to shares from the permitted number of participants, the secret cannot be reconstructed without the mandatory presence of at least one member from each group. This significantly reduces the risk of attacks involving an external entity impersonating a valid participant (e.g., acting as the th party) for cryptographic analysis or brute-force guessing. While many existing schemes counter such threats by introducing authentication mechanisms, the proposed approach enhances security through the structure of the scheme itself.
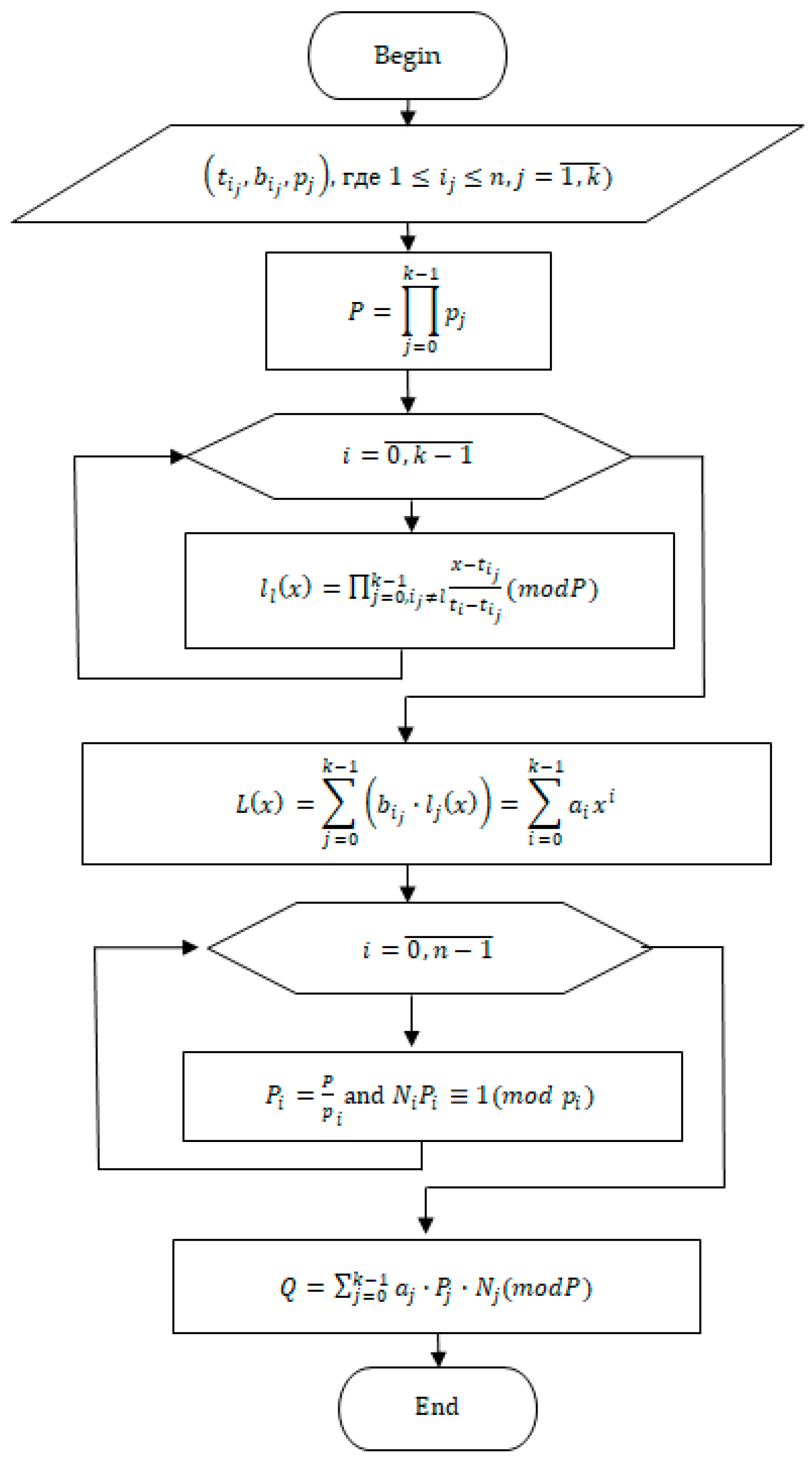
3.1.2. Secret Reconstruction
At least participants must combine their shares to recover the secret. To do this, participants use their shares where . Reconstruction can be performed in two ways:
Using Lagrange Interpolation Polynomial. The coefficients of the polynomial (7) are computed by the formula . The coefficients then define the system of congruences (6). Subse-quently, the secret is reconstructed based on the Chinese Remainder Theorem and Formula (5).
The block diagram of secret reconstruction is shown in
Figure 3.
System (9) comprises linear equations with variables. Solving this system makes it possible to determine the coefficients of polynomial in expression (7). The coefficients then define the set of congruences (6), which, together with the Chinese Remainder Theorem and Formula (5), allow for complete reconstruction of the secret.
The Lagrange interpolation method is recommended in cases where computational efficiency is a priority and all required subgroup representatives have provided valid shares. The system of linear equations method is more appropriate in scenarios that demand higher fault tolerance and the ability to verify the correctness of shares, as it allows inconsistencies to be detected.
We also clarified that both methods can be applied only if at least one representative from each subgroup participates. Otherwise, the system of equations or the interpolation polynomial remains underdetermined, and secret reconstruction becomes impossible.
4. Discussion
Let us consider the criteria for evaluating a secret sharing scheme that provide maximum confidentiality while minimizing memory and computational resources:
The solution of a system of linear equations with k variables forms the basis of the algorithm. If the number of equations is less than (in other words, if the number of participants holding shares is below the required threshold), the system has multiple solutions, preventing accurate reconstruction of the secret.
The choice of the number of subgroups and the ranges of moduli is determined by two factors: security requirements and the organizational structure of the system.
First, the number of subgroups reflects the level of role-based separation of authority. If the system involves independent organizations (for example, multiple cloud providers or legally distinct parties), each of them should constitute a separate subgroup. Thus, k is selected in accordance with the number of independent trust domains that must be controlled.
Second, the selection of modulus ranges directly affects the cryptographic strength of the scheme. According to the Chinese Remainder Theorem, the overall secret space is determined by the product of the moduli . The larger the value of , the higher the level of security, since an adversary would need to consider a significantly broader range of possible secrets. To prevent brute-force attacks, each modulus must be chosen sufficiently large and must be prime. In practice, it is recommended to use a modulus length of at least 1024 bits, which complies with modern security requirements.
Ideality of the scheme. A secret sharing scheme is considered perfect if no group of illegitimate participants can extract any information about the secret from their shares [
3]. Furthermore, the scheme is called ideal if the size of each share is equal to the size of the original secret. In the proposed algorithm, the secret is uniformly distributed across all disseminated shares.
Resource consumption. Let us estimate the algorithm’s resource consumption. If we reserve 8 bytes for each of polynomial coefficients and for each of shares (taking into account both the argument and the value of the share), the total memory usage will be bytes. For example, when the required memory is 768 bytes.
Scheme Complexity
Selecting random primes and polynomial interpolation according to Formulas (6) and (7) has complexity .
Distributing the secret involves computing and disseminating triplets for i, yielding a complexity of .
Thus, the overall computational complexity during the distribution phase is .
Reconstruction of the secret using Lagrange polynomial interpolation has complexity .
Reconstruction of the secret using the Chinese remainder theorem also has complexity .
Taken together, the total complexity of the algorithm is .
The results of evaluating these criteria for the proposed scheme are presented in
Table 2.
During the study, 6 threshold secret sharing schemes were considered. The evaluation criteria included algorithm complexity for sharing and reconstruction, resource consumption, and security properties—perfection and ideality of the schemes. The results, presented in
Table 3, allow for a comparative analysis of various methods. Here, the symbol “+” indicates that the considered scheme possesses the properties of ideality and perfection, while “−” denotes that these properties are not satisfied.
At the theoretical research stage, to optimize the software implementation of the secret sharing algorithm based on threshold schemes, algorithm complexity and resource consumption were analyzed. The algorithm’s execution time under different parameters was also measured. The results are presented below (see
Table 4).
Consider the following approach. Let the moduli
be known, and
participants of the scheme possess their respective shares of the secret. Let us analyze the possibility of reconstructing the secret. Since there is a group of
participants with the sets
, we can form the following system of linear congruences:
In this system, the values
(
) and
(for
) are considered known. Thus, we have a system of
linear equations with
unknowns. According to linear algebra, such a system has infinitely many solutions and can be satisfied for arbitrary values of the
th variable.
Here for are known (determined) values.
Adding the condition to this system (11) does not reduce its set of solutions, because these sets are equivalent.
Let the secret
be uniquely determined by the system of congruences
where
are pairwise coprime moduli corresponding to the subgroups, and
. Assume that each subgroup provides at least one valid share containing the residue
.
If at least one modulus
is missing, the system of congruences becomes incomplete. In this case, the set of solutions takes the form
where
. Since
, the secret is no longer uniquely defined but corresponds to a set of
different values. This means that adversaries, even if colluding and combining
shares, cannot uniquely reconstruct the secret without the participation of at least one representative from each subgroup.
Thus, the requirement of mandatory subgroup participation is an inherent mathematical constraint of the scheme and ensures its resilience against internal collusion.
If a participant of the scheme provides erroneous (false) information from their share, there is a probability that this share will not be involved in solving the system of congruences.
There are
possible ways to choose
participants out of
. The number of ways to select
participants such that a specific fixed participant is not included equals
. Therefore, the probability that, in a random selection of
participants, the fixed participant is not chosen is
Here, p denotes the probability that a particular participant will not be included in a randomly selected subset of participants. The selection of participants is assumed to be uniformly random over all subsets. This formula thus provides a statistical estimate and does not account for strategic participant behavior (such as targeted sabotage or other adversarial actions), which should be analyzed separately within the threat model.
5. Conclusions
Secret sharing schemes are among the key areas in the field of information security. This paper presents a new secret sharing scheme with mandatory subgroup participation and analyzes its properties.
The study addresses the issues of secure distribution of confidential information and its reliable reconstruction. Unlike most existing secret sharing schemes, the proposed solution is initially designed with enhanced resistance to internal threats and cryptographic attacks. While other approaches rely on additional authentication mechanisms to prevent such attacks, the proposed scheme is inherently resilient: even if an adversary gains access to the shares of k legitimate participants, they will not be able to reconstruct the secret Q without satisfying the structural requirement of having representatives from all subgroups.
A theoretical and computational complexity analysis of the algorithm was carried out, along with an assessment of potential threats posed by both external adversaries and untrustworthy internal participants. The results showed that the proposed scheme possesses the property of ideality (in the sense of exact reconstruction under the defined conditions) and demonstrates high resource efficiency, making it a promising option for practical applications.
Reliability, ease of implementation, and resistance to adversarial actions make the proposed scheme a suitable solution for modern challenges in secure authentication and the distributed storage of sensitive information.
The algorithm has been implemented in C# and tested on practical use cases. Future work will focus on further improving the algorithm’s robustness and exploring its applicability in various scenarios, with the results to be presented in subsequent publications.
Author Contributions
Conceptualization, D.D. and A.K.; methodology, N.K.; software, D.D.; validation, N.K., A.K. and K.A.; formal analysis, D.D.; investigation, A.K.; resources, N.K.; data curation, A.K.; writing—original draft preparation, N.K.; writing—review and editing, K.A.; visualization, K.A.; supervision, D.D.; project administration, N.K.; funding acquisition, A.K. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Ministry of Science and Higher Education of the Republic of Kazakhstan and carried out within the framework of project AP23487787 “Development of an algorithm for reliable storage of biometric data of authentication systems in spatially distributed repositories” at the Institute of Information and Computational Technologies.
Data Availability Statement
Data are contained within the article.
Acknowledgments
The authors are grateful to all lab members of the Information Security Laboratory (Institute of Information and Computational Technologies) for their useful suggestions and support.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| SSS | Secret Sharing Scheme |
| CRT | Chinese Remainder Theorem |
| LIP | Lagrange Interpolation Polynomial |
References
- Čuřík, P.; Ploszek, R.; Zajac, P. Practical Use of Secret Sharing for Enhancing Privacy in Clouds. Electronics 2022, 11, 2758. [Google Scholar] [CrossRef]
- Huang, C.-W.; Juan, J.S.-T. New (t, n)-Threshold P-VSS Schemes Using Fewer Types of Polarizers. Eng. Proc. 2025, 92, 49. [Google Scholar] [CrossRef]
- Liu, Y.; Sun, Q.; Yang, Z.; Zhou, Y.; Zhao, W.; Shi, D. Progressive Reconstruction on Region-Based Secret Image Sharing. Electronics 2024, 13, 1529. [Google Scholar] [CrossRef]
- Liu, Y.X.; Yang, C.N.; Wu, S.Y.; Chou, Y.S.; Sun, Q.D. Progressive (k,n) secret image sharing scheme with meaningful shadow images by GEMD and RGEMD. J. Vis. Commun. Image Represent. 2018, 55, 766–777. [Google Scholar] [CrossRef]
- Mogilevskaya, N.S.; Kulbikayan, R.V.; Zhuravlev, L.A. Threshold File Sharing Based on Bit Masks: Ideas and Possible Applications. Bull. Don State Tech. Univ. 2011, 11, 1749–1754. (In Russian) [Google Scholar]
- Gao, S.; Ding, S.; Ho-Ching Iu, H.; Erkan, U.; Toktas, A.; Simsek, C.; Wu, R.; Xu, X.; Cao, Y.; Mou, J. A three-dimensional memristor-based hyperchaotic map for pseudorandom number generation and multi-image encryption. Chaos 2025, 35, 073105. [Google Scholar] [CrossRef] [PubMed]
- Chervyakov, N.I.; Deryabin, M.A. A new method of threshold secret sharing based on residue class systems. Inf. Technol. 2016, 22, 211–219. (In Russian) [Google Scholar]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Buchanan, W.J. Shamir Secret Sharing (SSS). Asecuritysite.com. 2024. Available online: https://asecuritysite.com/shares (accessed on 30 April 2024).
- Alam, I.; Alali, A.S.; Ali, S.; Asri, M.S.M. A Verifiable Multi-Secret Sharing Scheme for Hierarchical Access Structure. Axioms 2024, 13, 515. [Google Scholar] [CrossRef]
- Zou, S.; Liang, Y.; Lai, L.; Shamai, S. An information theoretic approach to secret sharing. IEEE Trans. Inf. Theory 2015, 61, 3121–3136. [Google Scholar] [CrossRef]
- Watanabe, Y.; Shikata, J. Timed-release secret sharing scheme with information theoretic security. arXiv 2014, arXiv:1401.5895. [Google Scholar] [CrossRef]
- Xu, R.; Wang, X.; Morozov, K.; Cheng, C.; Ding, J. Revisiting Group Oriented Secret Sharing Schemes. Inf. Sci. 2022, 589, 751–769. [Google Scholar] [CrossRef]
- Binu, V.P.; Sreekumar, A. Threshold multi-secret sharing using elliptic curve and pairing. arXiv 2016, arXiv:1603.09524. [Google Scholar] [CrossRef]
- Chervyakov, N.I.; Kocherov, Y.N. Modification of Asmuth-Bloom data sharing scheme using the fractal geometry method. Infocommun. Technol. 2017, 15, 7–14. (In Russian) [Google Scholar] [CrossRef]
- Bahman, R.; Ziba, E. A verifiable threshold secret sharing scheme based on lattices. Inf. Sci. 2019, 501, 655–661. [Google Scholar] [CrossRef]
- Gao, S.; Zhang, Z.; Iu, H.H.-C.; Ding, S.; Mou, J.; Erkan, U.; Toktas, A.; Li, Q.; Wang, C.; Cao, Y.; et al. A Parallel Color Image Encryption Algorithm Based on a 2-D Logistic-Rulkov Neuron Map. IEEE Internet Things J. 2025, 12, 18115–18124. [Google Scholar] [CrossRef]
- Prashanti, G.; Bhat, M.N. Cheating identifiable polynomial based secret sharing scheme for audio and image. Multimed. Tools Appl. 2024, 83, 403–423. [Google Scholar] [CrossRef]
- Tsai, Y.-Y.; Jhou, J.-Y.; You, T.-Y.; Lu, C.-T. Advancing Secret Sharing in 3D Models Through Vertex Index Sharing. Electronics 2025, 14, 1675. [Google Scholar] [CrossRef]
- Du, J.; Dai, C.; Mao, P.; Dong, W.; Wang, X.; Li, Z. An Efficient Lightweight Authentication Scheme for Smart Meter. Mathematics 2024, 12, 1264. [Google Scholar] [CrossRef]
| Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).