On-Chain/Off-Chain Adaptive Low-Latency Network Communication Technology with High Security and Regulatory Compliance
Abstract
1. Introduction
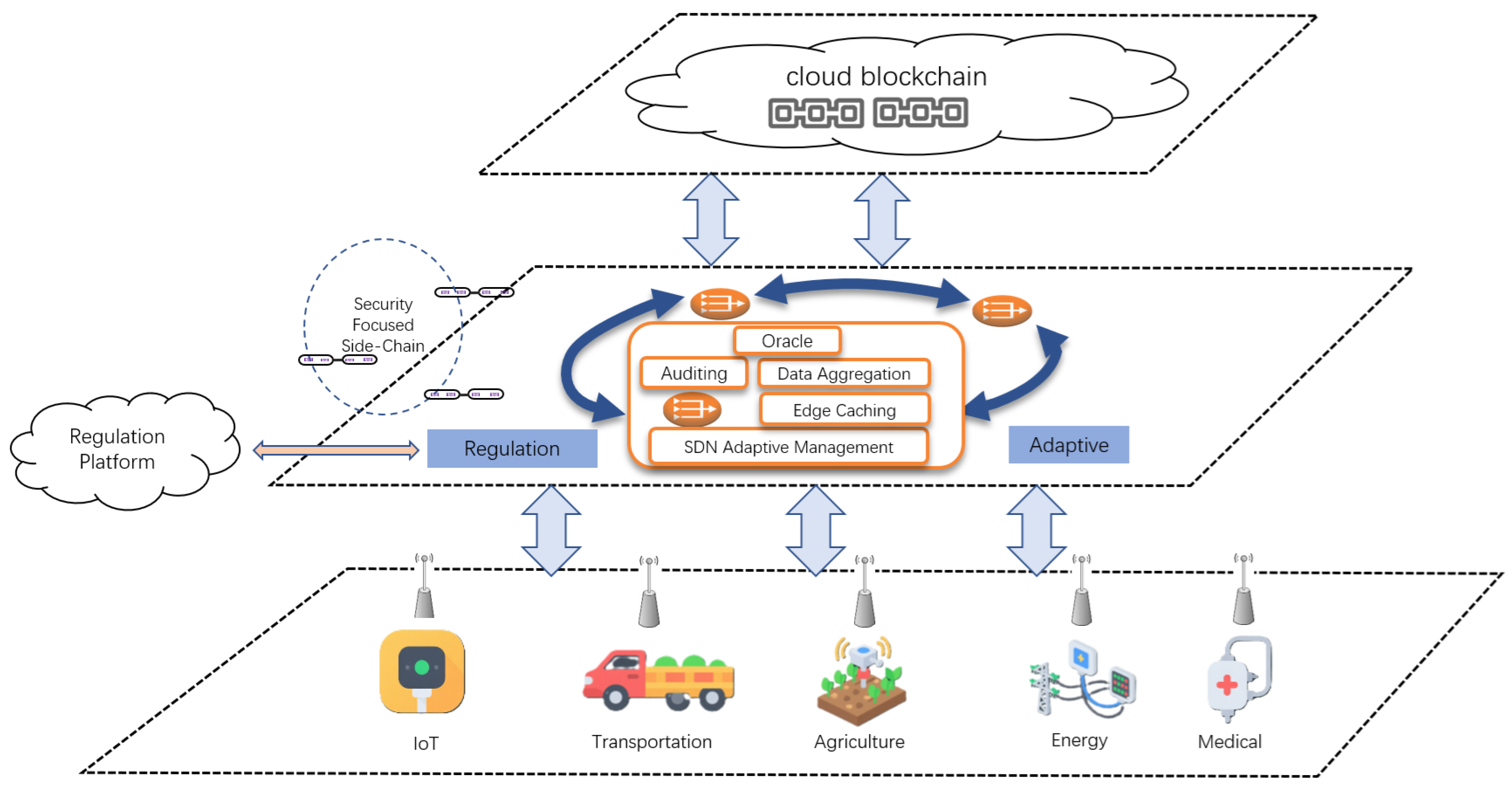
- A novel high-performance hierarchical communication architecture: We propose a hierarchical device–edge–chain architecture centered on software-defined edge gateways, specifically designed to bridge the efficiency and trust gap between massive off-chain devices and on-chain blockchain systems and achieve the critical performance target of processing tens of millions of data entries per second.
- Robust fault tolerance and scalability: We incorporate dynamic path switching and capacity-aware load redistribution mechanisms mediated by software-defined networking (SDN), ensuring high availability and scalability to handle link failures and fluctuating workloads effectively.
- End-to-end regulatory compliance: We develop a sidechain-based auditing system integrated within the architecture, providing transparent, tamper-proof logs for data provenance and workflow execution, ensuring adherence to regulatory requirements across the entire communication path.
2. Background and Related Work
2.1. Blockchain Fundamentals
2.2. Blockchain Scalability
3. Materials and Methods
3.1. System Design Analysis
3.2. Architecture Design
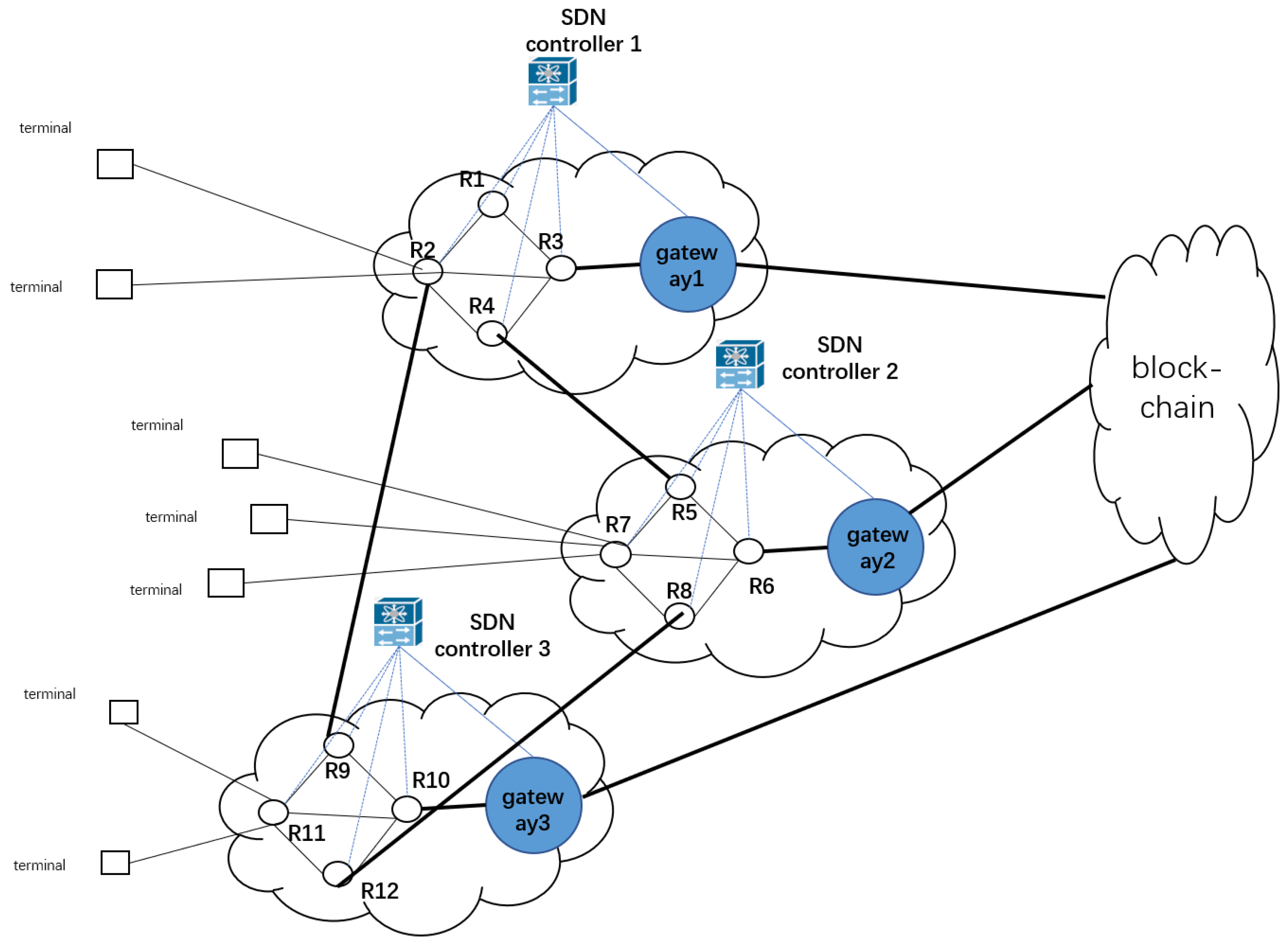
3.2.1. SDN Architecture
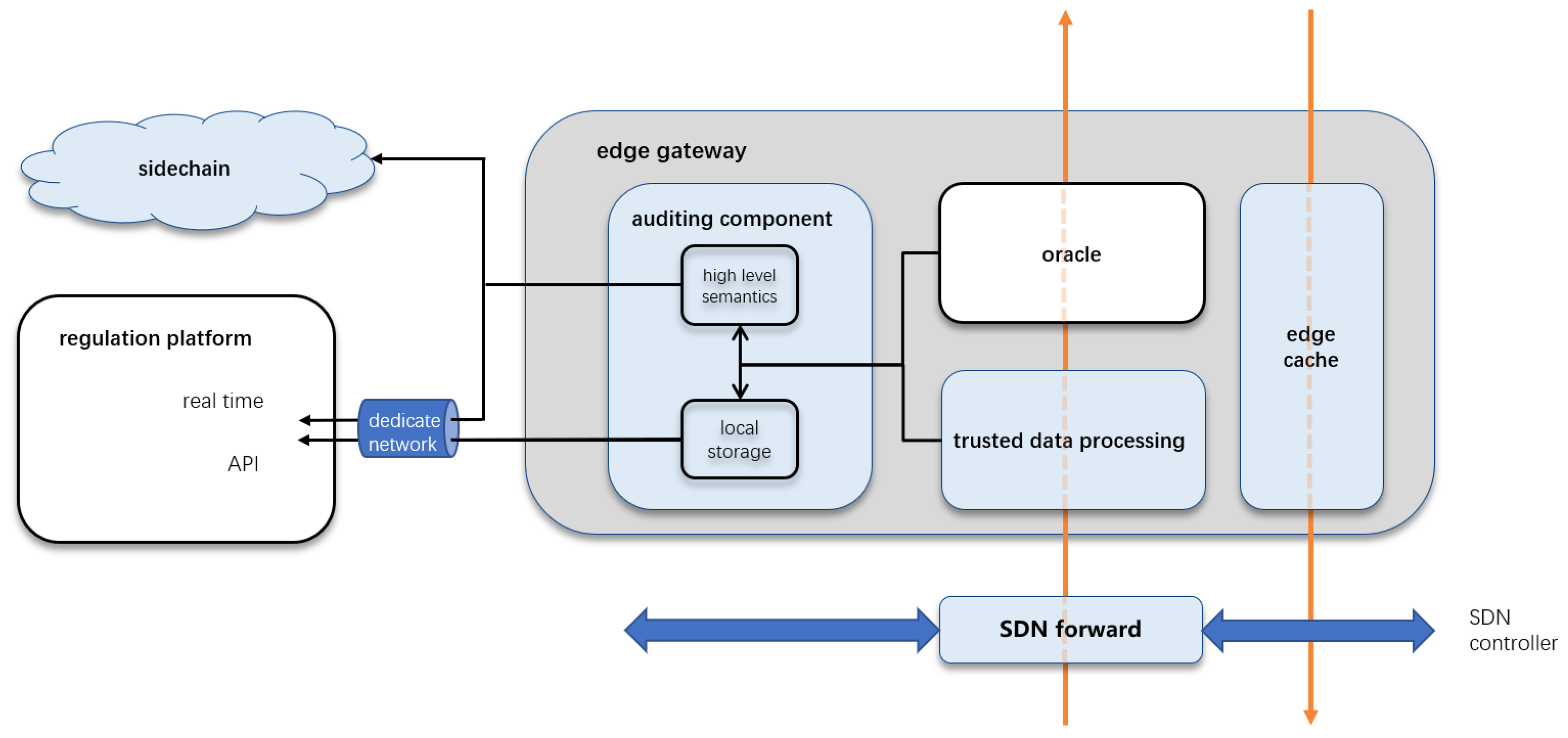
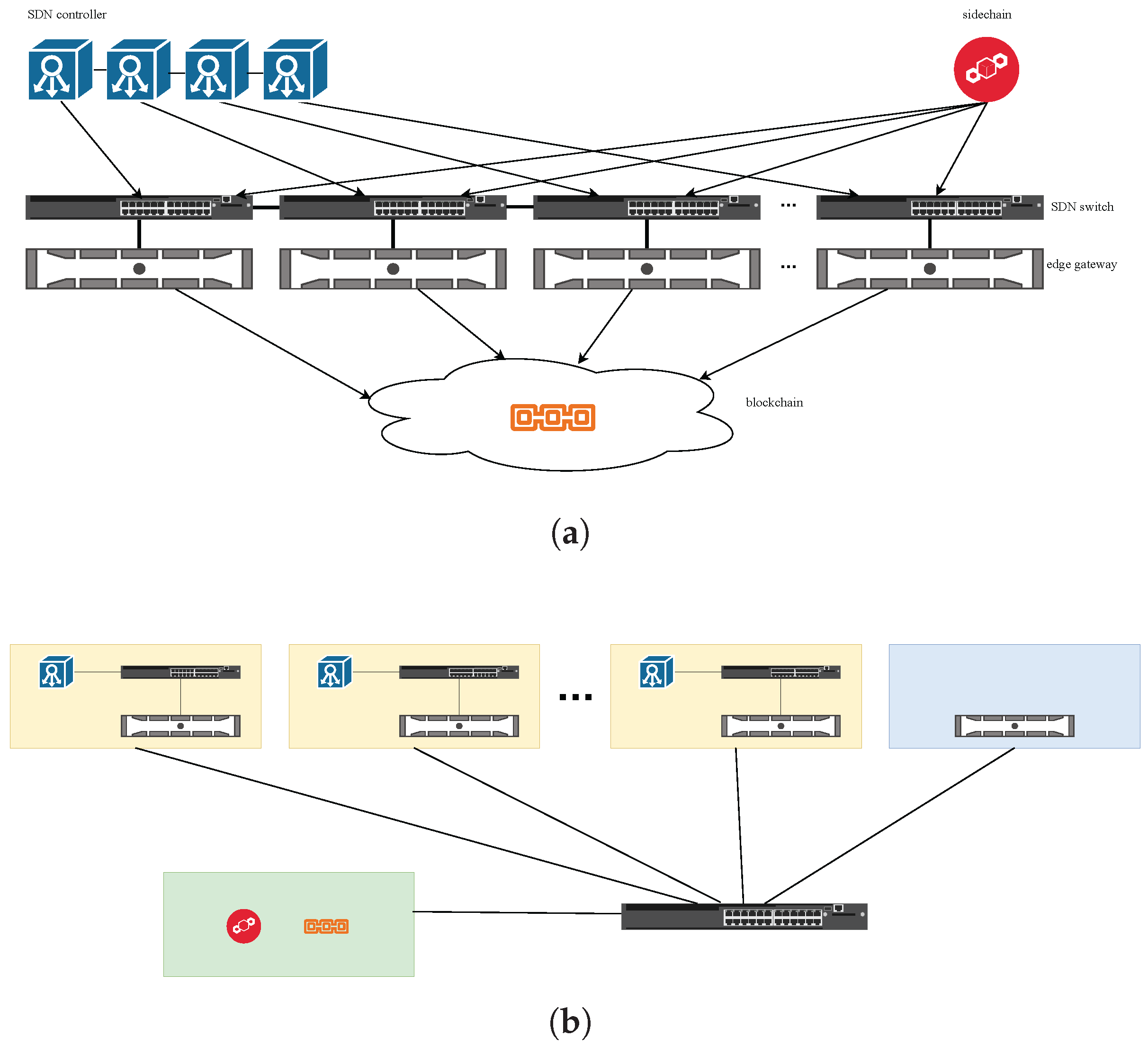
3.2.2. Edge Gateway Architecture
| Algorithm 1 Hash tree aggregate algorithm. |
|
3.2.3. Data On-Chaining Process
3.2.4. Data Off-Chaining Process
4. Experimental Evaluation
4.1. Experimental Configuration
4.1.1. Network Topology
4.1.2. Parameter Settings
4.1.3. Traffic Generation
4.1.4. Test Limitations
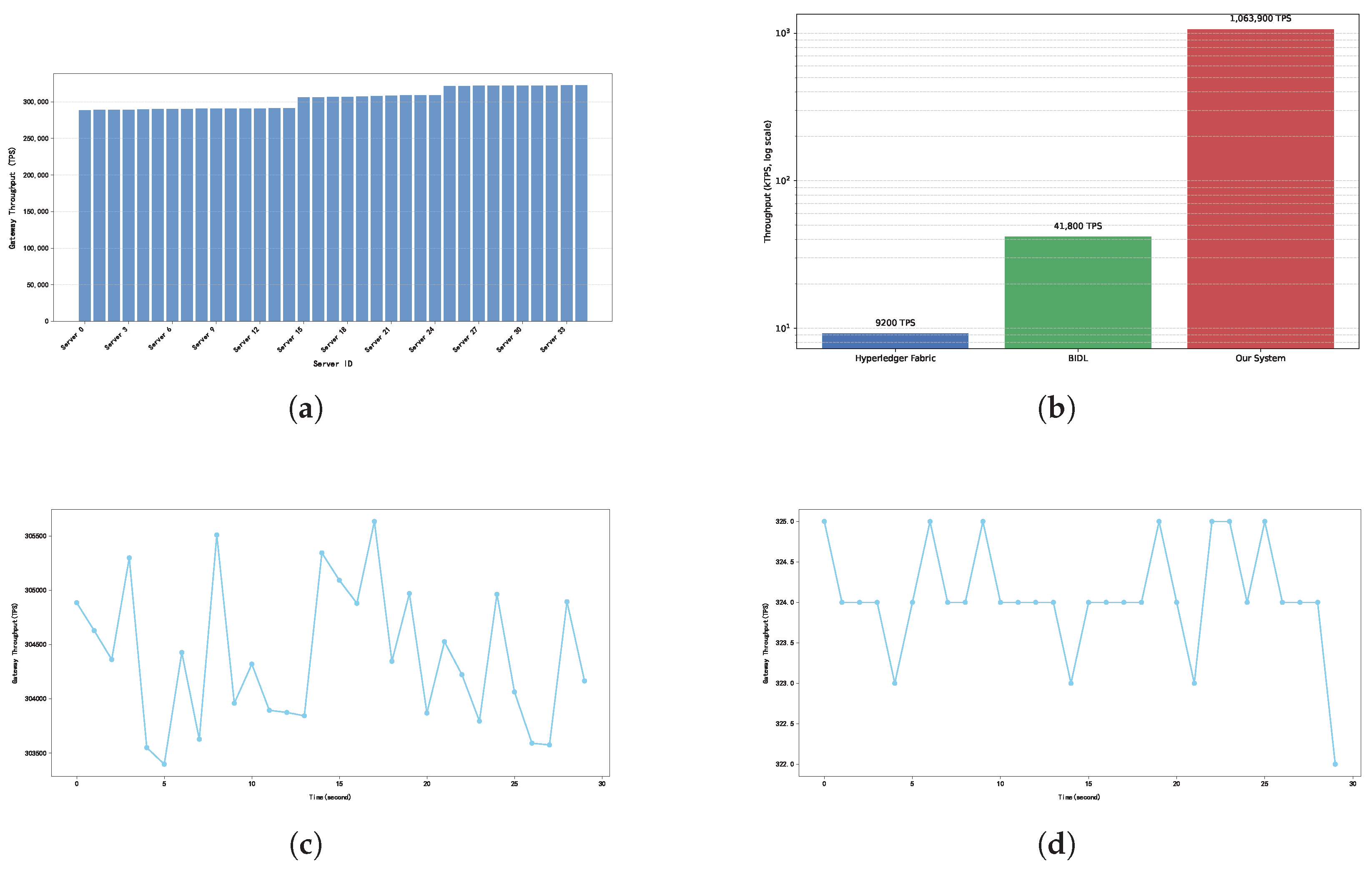
4.2. System Performance Evaluation
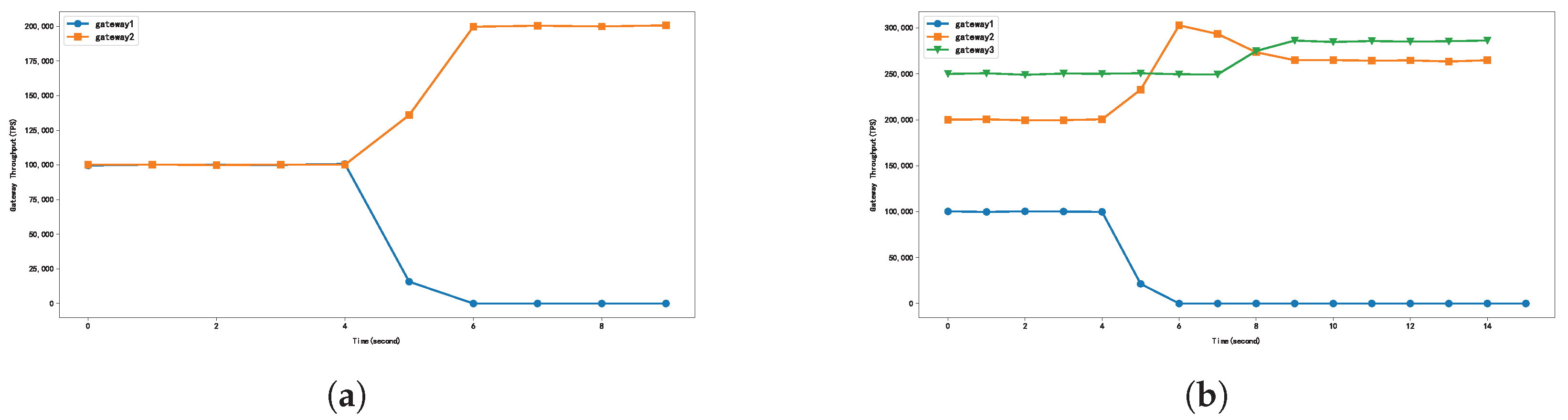
4.3. Fault Tolerance Evaluation
5. Discussion
Deployment Considerations in Cost-Sensitive Environments
6. Conclusions and Future Work
- An edge-centric semantic compression and aggregation pipeline achieving up to 1000:1 effective data reduction, bridging the gap between device data generation and blockchain processing capacity;
- A TEE-protected processing environment at the edge, ensuring confidentiality and integrity even under untrusted infrastructure;
- An SDN-controlled network layer that enables sub-second failover, capacity-aware routing, and global network visibility;
- A regulatory-compliant auditing subsystem based on a dedicated sidechain and multi-layer storage model.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 1 July 2025).
- Poon, J.; Dryja, T. The Bitcoin Lightning Network. 2016. Available online: https://lightning.network/lightning-network-paper.pdf (accessed on 1 July 2025).
- Wang, J.; Wang, H. Monoxide: Scale out blockchains with asynchronous consensus zones. In Proceedings of the 16th USENIX Symposium on Networked Systems Design and Implementation (NSDI 19), Boston, MA, USA, 26–28 February 2019; USENIX Association: Berkeley, CA, USA, 2019; pp. 95–112. [Google Scholar]
- Hong, Z.; Guo, S.; Li, P.; Chen, W. Pyramid: A layered sharding blockchain system. In Proceedings of the IEEE INFOCOM 2021—IEEE Conference on Computer Communications, Virtual, 10–13 May 2021; pp. 1–10. [Google Scholar]
- Kokoris-Kogias, E.; Jovanovic, P.; Gasser, L.; Gailly, N.; Syta, E.; Ford, B. Omniledger: A secure, scale-out, decentralized ledger via sharding. In Proceedings of the 2018 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 20–24 May 2018; pp. 583–598. [Google Scholar]
- Zamani, M.; Movahedi, M.; Raykova, M. Rapidchain: Scaling blockchain via full sharding. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, CCS ’18, Toronto, ON, Canada, 15–19 October 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 931–948. [Google Scholar]
- Qi, J.; Chen, X.; Jiang, Y.; Jiang, J.; Shen, T.; Zhao, S.; Wang, S.; Zhang, G.; Chen, L.; Au, M.; et al. Bidl: A High-Throughput, Low-Latency Permissioned Blockchain Framework for Datacenter Networks. In Proceedings of the ACM SIGOPS 28th Symposium on Operating Systems Principles, Virtual, 26–29 October 2021; pp. 18–34. [Google Scholar] [CrossRef]
- Sun, G.; Jiang, M.; Khooi, X.; Li, Y.; Li, J. NeoBFT: Accelerating Byzantine Fault Tolerance Using Authenticated In-Network Ordering. In Proceedings of the ACM SIGCOMM 2023 Conference, New York, NY, USA, 10 September 2023; pp. 239–254. [Google Scholar] [CrossRef]
- Wei, X.; Cheng, R.; Yang, Y.; Chen, R.; Chen, H. Characterizing Off-path SmartNIC for Accelerating Distributed Systems. In Proceedings of the 17th USENIX Symposium on Operating Systems Design and Implementation (OSDI 23), Boston, MA, USA, 10–12 July 2023; pp. 987–1004. Available online: https://www.usenix.org/conference/osdi23/presentation/wei-smartnic (accessed on 27 March 2025).
- Zhou, Y.; Wang, Z.; Dharanipragada, S.; Yu, M. Electrode: Accelerating Distributed Protocols with eBPF. In Proceedings of the 20th USENIX Symposium on Networked Systems Design and Implementation (NSDI 23), Boston, MA, USA, 17–19 April 2023; pp. 1391–1407. Available online: https://www.usenix.org/conference/nsdi23/presentation/zhou (accessed on 27 March 2025).
- Castro, M.; Liskov, B. Practical Byzantine fault tolerance. In Proceedings of the Third Symposium on Operating Systems Design and Implementation (OSDI), New Orleans, LA, USA, 22–25 February 1999; pp. 173–186. [Google Scholar]
- Larimer, D. Delegated Proof-of-Stake (DPoS). 2014. Available online: https://bitshares.org/technology/delegated-proof-of-stake-consensus/ (accessed on 22 July 2025).
- Yin, M.; Malkhi, D.; Reiter, M.; Gueta, G.; Abraham, I. HotStuff: BFT Consensus in the Lens of Blockchain. In Proceedings of the 2019 ACM Symposium on Principles of Distributed Computing (PODC), Toronto, ON, Canada, 29 July–2 August 2019; pp. 347–356. [Google Scholar]
- IOTA Stiftung. About IOTA. 2025. Available online: https://docs.iota.org/about-iota (accessed on 27 March 2025).
- Nano Foundation. Nano Documentation. 2025. Available online: https://docs.nano.org/protocol-design/introduction/ (accessed on 27 March 2025).
- Vite Labs Limited. ZERO GAS LAYER-1. 2018. Available online: https://vite.org/ (accessed on 27 March 2025).
- Bentov, I.; Hubáček, P.; Moran, T.; Nadler, A. Tortoise and hares consensus: The meshcash framework for incentive-compatible, scalable cryptocurrencies. In Cyber Security Cryptography and Machine Learning; Dolev, S., Margalit, O., Pinkas, B., Schwarzmann, A., Eds.; Springer International Publishing: Cham, Switzerland, 2021; pp. 114–127. [Google Scholar]
- Xiao, J.; Zhang, S.; Zhang, Z.; Li, B.; Dai, X.; Jin, H. Nezha: Exploiting concurrency for transaction processing in dag-based blockchains. In Proceedings of the 2022 IEEE 42nd International Conference on Distributed Computing Systems (ICDCS), Bologna, Italy, 10–13 July 2022; pp. 269–279. [Google Scholar]
- Zhang, F.; Cecchetti, E.; Croman, K.; Juels, A.; Shi, E. Town crier: An authenticated data feed for smart contracts. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, CCS ’16, Vienna, Austria, 24–28 October 2016; Association for Computing Machinery: New York, NY, USA, 2016; pp. 270–282. [Google Scholar]
- Atwal, K.S.; Bassiouni, M. Softaccess: Cloud-based software defined virtualized wireless mobile access networks. In Proceedings of the 2017 5th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud), San Francisco, CA, USA, 6–8 April 2017; pp. 96–101. [Google Scholar]
- Kim, H.; Schlansker, M.; Santos, J.R.; Tourrilhes, J.; Turner, Y.; Feamster, N. Coronet: Fault tolerance for software defined networks. In Proceedings of the 2012 20th IEEE International Conference on Network Protocols (ICNP), Austin, TX, USA, 30 October–2 November 2012; pp. 1–2. [Google Scholar]
- Li, H.; Li, Q.; Jiang, Y.; Zhang, T.; Wang, L. A declarative failure recovery system in software defined networks. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–6. [Google Scholar]
- Wu, D.; Arkhipov, D.I.; Asmare, E.; Qin, Z.; McCann, J.A. Ubiflow: Mobility management in urban-scale software defined iot. In Proceedings of the 2015 IEEE Conference on Computer Communications (INFOCOM), Hong Kong, China, 26 April–1 May 2015; pp. 208–216. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jin, Y.; Huang, D.; Tian, C. On-Chain/Off-Chain Adaptive Low-Latency Network Communication Technology with High Security and Regulatory Compliance. Appl. Sci. 2025, 15, 8880. https://doi.org/10.3390/app15168880
Jin Y, Huang D, Tian C. On-Chain/Off-Chain Adaptive Low-Latency Network Communication Technology with High Security and Regulatory Compliance. Applied Sciences. 2025; 15(16):8880. https://doi.org/10.3390/app15168880
Chicago/Turabian StyleJin, Yu, Daming Huang, and Chen Tian. 2025. "On-Chain/Off-Chain Adaptive Low-Latency Network Communication Technology with High Security and Regulatory Compliance" Applied Sciences 15, no. 16: 8880. https://doi.org/10.3390/app15168880
APA StyleJin, Y., Huang, D., & Tian, C. (2025). On-Chain/Off-Chain Adaptive Low-Latency Network Communication Technology with High Security and Regulatory Compliance. Applied Sciences, 15(16), 8880. https://doi.org/10.3390/app15168880




