Advancing Data Privacy in Cloud Storage: A Novel Multi-Layer Encoding Framework
Abstract
1. Introduction
- (i)
- Development of a novel and adaptable framework that combines a multi-layer encoding storage arrangement and the one-time password (OTP) authorization approach for enhanced data protection in cloud environments.
- (ii)
- Ensuring a holistic novel approach to privacy preservation in cloud data storage through the examination and then categorization of several privacy attributes into distinct categories.
- (iii)
- Integration of a multi-cloud-based storage arrangement, enhancing data availability and redundancy for robust data privacy in cloud storage.
- (iv)
- Introduction of a novel multi-layer encryption approach as an additional layer of protection against privacy breaches in the ever-evolving cyber landscape.
- (v)
- Inspiring innovative research-driven solutions and aiding in the evaluation and enhancement of privacy approaches in cloud storage.
2. Background
2.1. Privacy Safeguarding
2.2. Related Work
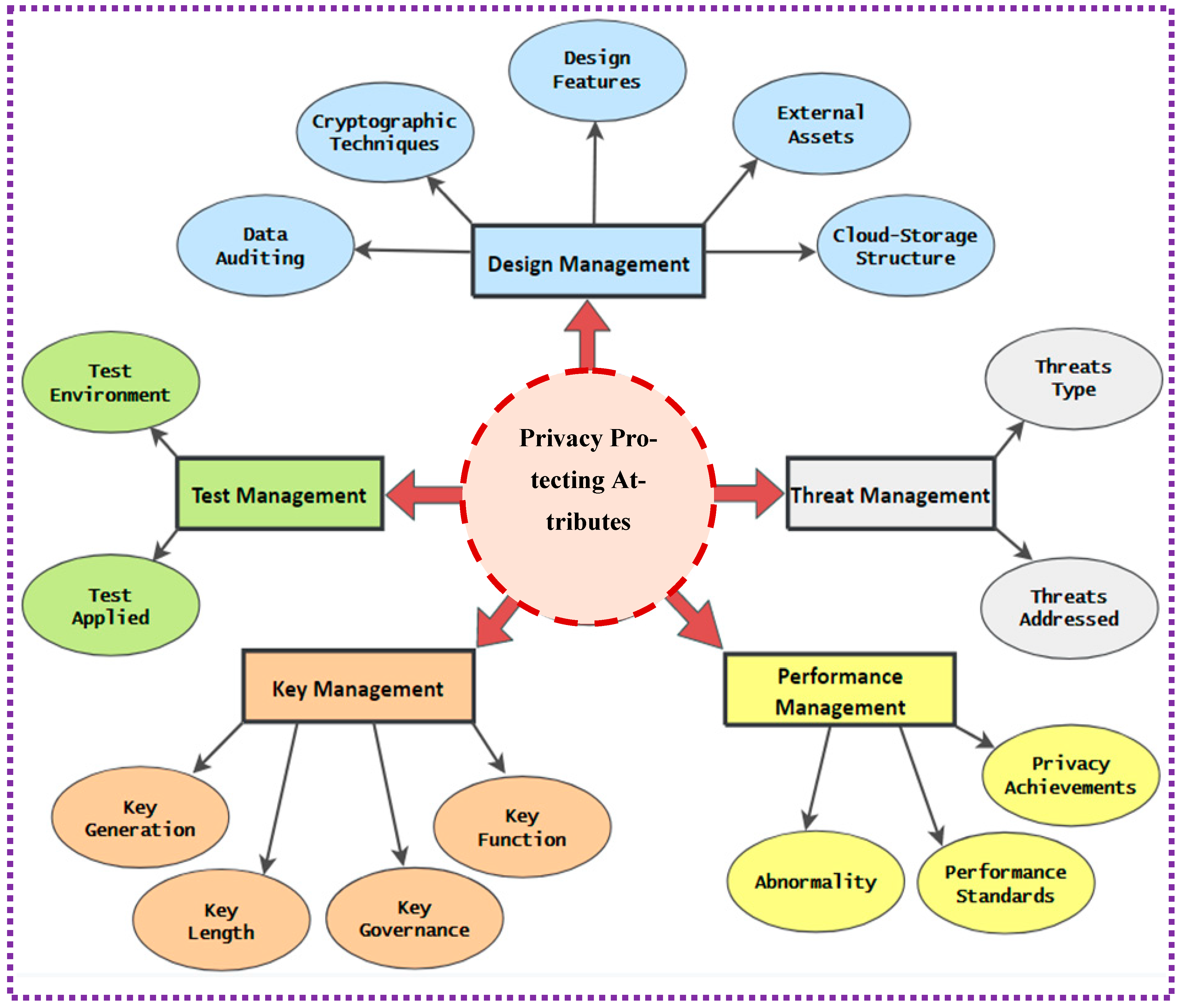
3. Privacy-Protecting Attributes Classification for the Storage of Cloud Data
3.1. Design Management
3.1.1. Design Features
3.1.2. Approaches to Data Auditing
- Concealment: Encoded data appears meaningless without the decoding logic.
- Multiple Barriers: Even if one encoding layer is breached, others remain intact.
- Built-in Verification: Integrity checks ensure that any unauthorized modifications are detected.
- Decoupled Storage: Metadata and decoding information can be stored separately, reducing the risk of full data exposure.
- —SQL for inserting new encoded data—
- INSERT INTO cloud_data (file_id, chunk_id, data_chunk, hash_code, uploaded_at)
- VALUES (‘F001’, ‘C01’, ‘U2FtcGxlRGF0YQ==’, ‘d3486ae9136e7856bc42212385ea797094475802’, NOW());
- —SQL for retrieving all chunks linked to a specific file—
- SELECT chunk_id, data_chunk FROM cloud_data WHERE file_id = ‘F001’ ORDER BY chunk_id;
- —SQL for validation of integrity—
- SELECT chunk_id FROM cloud_data WHERE file_id = ‘F001’ AND hash_code != SHA1(data_chunk);
3.1.3. Cryptographic Techniques
3.1.4. External Assets
3.1.5. Cloud Storage Structures
3.2. Key Management
3.2.1. Approaches for Generating Keys
3.2.2. Length of the Keys
3.2.3. Key Governance
3.2.4. Key Function
3.3. Test Management
3.3.1. Testing Environment
3.3.2. Test Applied
3.3.3. Empirical Validation of the Framework (Real-World Testing)
- (i)
- Performance Assessment and Scalability Testing: The authors evaluated the framework’s encryption and decryption speeds across diverse file sizes and formats to benchmark its performance. Further, its scalability was tested under varying data volumes and user loads to ensure consistent efficiency even as demand increases.
- (ii)
- Security Evaluation and Vulnerability Assessment: The authors conducted thorough security tests to uncover any potential weaknesses in the framework’s encryption methods and assessed its resilience against common cyber threats like brute force attacks and unauthorized access attempts to guarantee robust data protection.
- (iii)
- Usability Analysis and User Experience Testing: The authors assessed the framework’s user interface and overall user experience through usability tests. Feedback was solicited from users to gauge the framework’s ease of use and effectiveness in meeting their needs, thus ensuring high adoption rates and user satisfaction.
- (iv)
- Compliance Validation and Regulatory Conformance Testing: The framework’s compliance was verified with relevant data protection regulations such as GDPR, HIPAA, or PCI DSS. Audits were conducted to confirm adherence to legal requirements and the implementation of adequate safeguards for sensitive data stored in the cloud.
- (v)
- Real-World Scenario Simulation and Use-Case Testing: The authors simulated real-world scenarios like secure file sharing and collaborative data analysis to evaluate the framework’s performance in practical applications. This testing ensures that the framework effectively safeguards data privacy while supporting common tasks and workflows in real-world cloud storage environments.
3.3.4. Impact of the Framework on the End User Usability
3.4. Threat Management
3.4.1. Types of Threats
3.4.2. Threats Addressed
3.5. Management of Performance
3.5.1. Performance Standards
3.5.2. Abnormality
3.5.3. Privacy Achievements
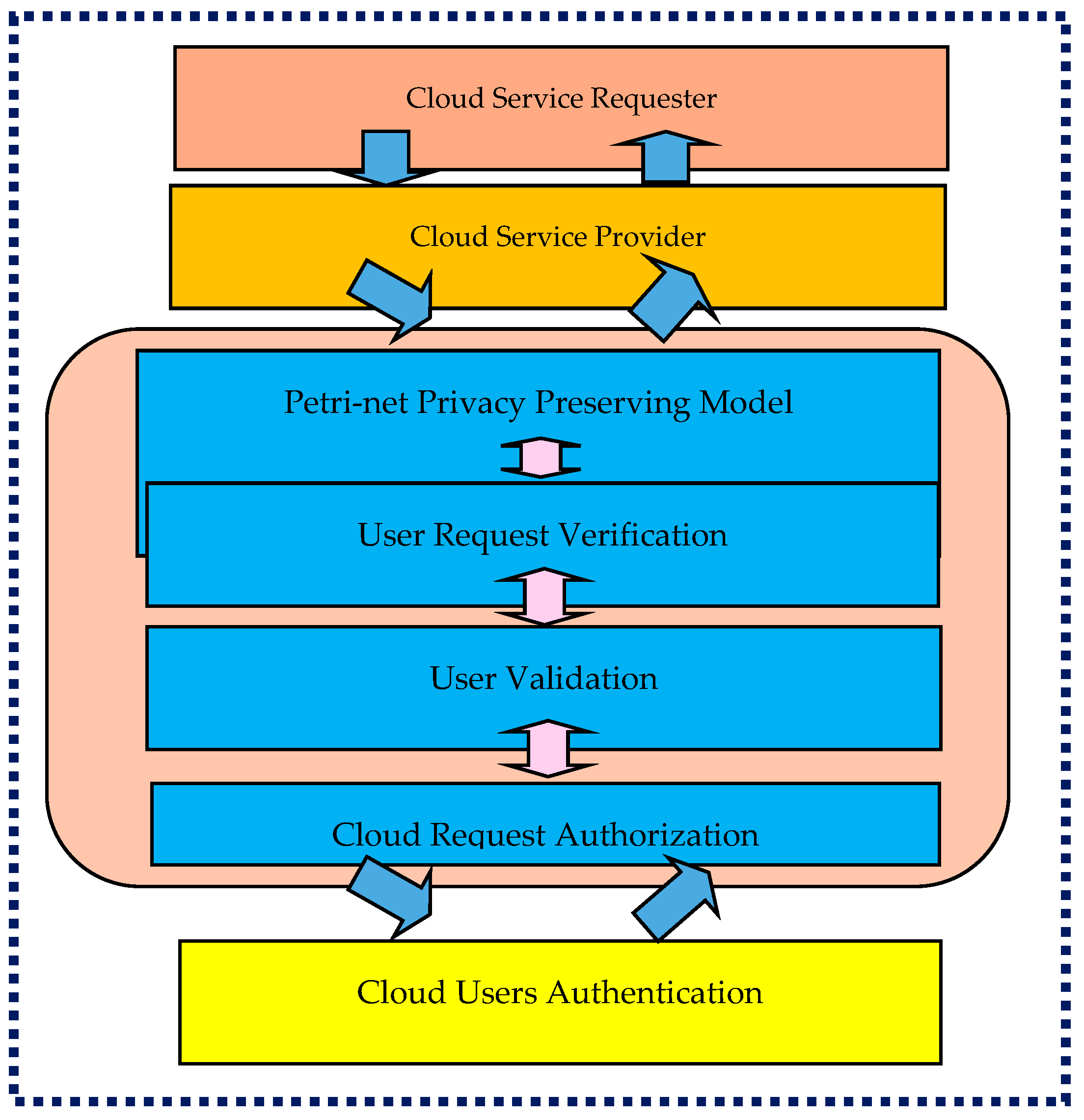
4. The Anticipated Cloud Storage Structure
4.1. Design Requirements
- (i)
- Technical expertise: The developer of the privacy-protecting approach should possess a comprehensive understanding of cloud-computing technologies. This ensures that designers can effectively address any design or security issues that may arise.
- (ii)
- Privacy policies and regulations: It is essential to establish a set of standards and regulations governing the usage of cloud services during the development of the privacy-preserving technique. Network participants must adhere to these requirements before establishing any connections within the cloud.
- (iii)
- Auditing mechanisms: Implementing monitoring mechanisms for network traffic is highly recommended. Auditing procedures serve as a vigilant checkpoint and a continuously observing system to identify any doubtful or abnormal activities.
- (iv)
- Data segmentation: Data partitioning into smaller segments has become a very basic-level approach for concealing sensitive information. Leveraging data segments and cloud technology can be outsourced to a multi-cloud-based storage approach for further enhancing privacy protection.
- (v)
- Access control and authentication: Robust approaches for controlling and managing access to cloud services must be employed. Implementing reliable access control measures is paramount in meeting privacy standards and ensuring authorized usage.
- (vi)
- Data encryption: Data transferred inside the cloud surroundings should be safeguarded against cryptographic threats. It is advisable to encrypt data using appropriate encryption protocols at all levels of the cloud network to ensure data privacy and integrity.
4.2. Components of the Framework
- (i)
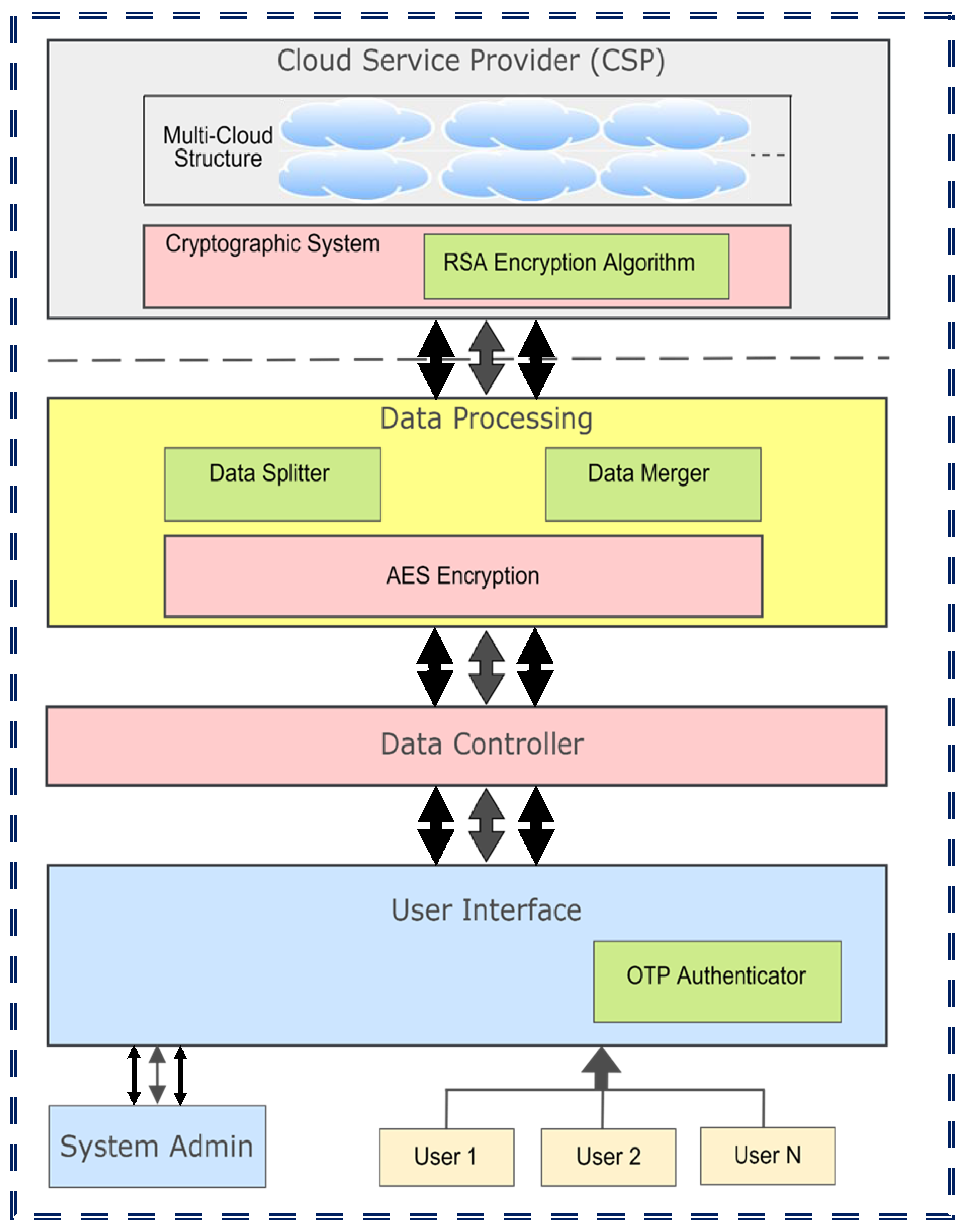
- Participants: In this section, we will integrate the privacy-protecting attributes and design elements to develop a new framework designed to protect cloud storage from privacy breaches. The subsequent components describe the framework’s structure, and the design elements incorporated within it are as follows: the proposed framework involves three key participants: the cloud service providers (CSPs), users, and the system administrator. The CSP offers a range of services, including network connectivity, computation time, etc. Users seek secure communication with the CSP, while the system administrator is responsible for crucial tasks such as data reception, initial AES encryption, and maintaining a list of authorized individuals.
- (ii)
- Registration: A registration process is implemented to allow users to fully utilize the features and cloud services.
- (iii)
- Data processing: To add an element of dispersion and enhance security, the framework allows for data segmentation and recombination. Users have the option to encode their data before outsourcing it to the cloud, utilizing AES encryption for the initial layer of protection.
- (iv)
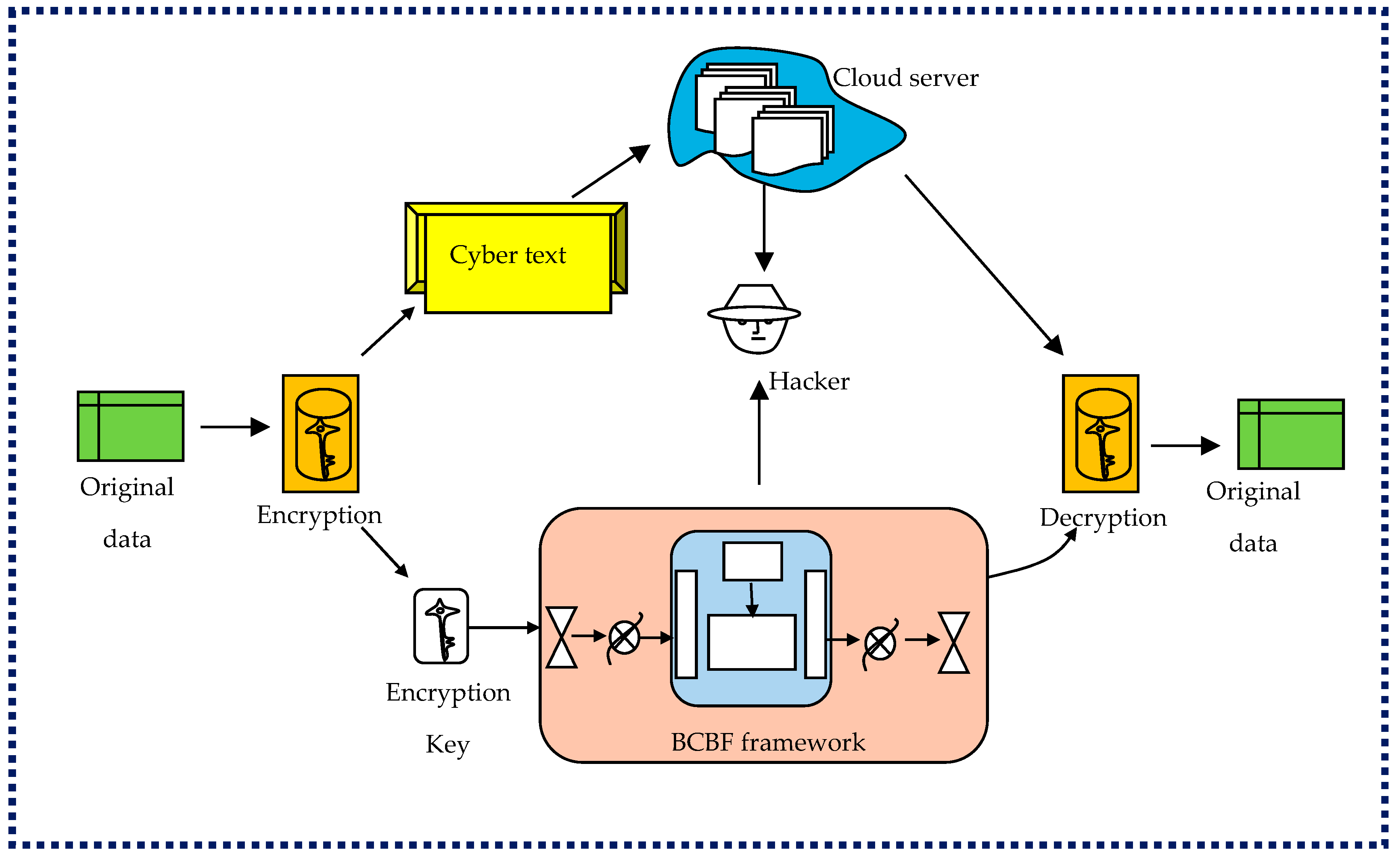
- Cryptographic techniques: The framework employs two encoding levels to safeguard susceptible data. The 1st layer of encoding is performed by authenticated participants using AES. The 2nd layer utilizes the RSA algorithm. This dual-layer encryption approach enhances the overall security of the system. AES and RSA algorithms generally work together to provide secure and efficient encryption. AES is fast and more suitable for encrypting large volumes of data, whereas RSA is used to securely transmit the AES key. In this combined approach, the data is first encrypted using AES for speed, and then the AES key is encrypted using the recipient’s RSA public key. After receiving the message, the recipient may decrypt the AES key using the private RSA key to access encrypted data. This combination will offer a balance between secure key exchange and speed. Example: While sending a highly confidential document, the sender will encrypt the file using AES, and then he/she will encrypt the AES key using RSA. The recipient will use his/her RSA private key to retrieve the AES key for decrypting the file. Further, the homomorphic encryption will allow data to remain encrypted during processing. Hence, it protects sensitive information while performing computations and data transmission. However, sometimes this method may involve high computational costs.
- (v)
- Auditing: The framework emphasizes internal auditing conducted by the system admin rather than relying on external auditors. Internal auditing provides a higher level of security and confidentiality, as there is no risk of exposing sensitive data to external entities.
- (vi)
- Data controller: The framework includes a data controller mechanism that enables efficient retrieval and storage of data from cloud storage through the CSP. This ensures proper data management and facilitates seamless access to stored information.
- (vii)
- External assets: One notable technology integrated into the framework is the one-time password (OTP) for additional verification. OTP technology provides an extra layer of security by generating unique, time-limited passwords that users must provide for authentication purposes. By employing OTP, the framework enhances the verification process and strengthens user authentication.
- (viii)
- Combining data and segmentation: The framework employs combining data and segmentation mechanisms to enhance privacy. Prior to encryption, data is segmented into smaller chunks. Upon decryption, the combined result of these segments is supposed to be the original data.
- (ix)
- Multi-cloud storage: The framework recommends adopting a multi-cloud storage approach to ensure the availability of data and anonymization in the event of storage failures. This may help in enhancing data availability and maintaining anonymity.
4.3. Proposed Framework Functions
4.4. The Data Workflow
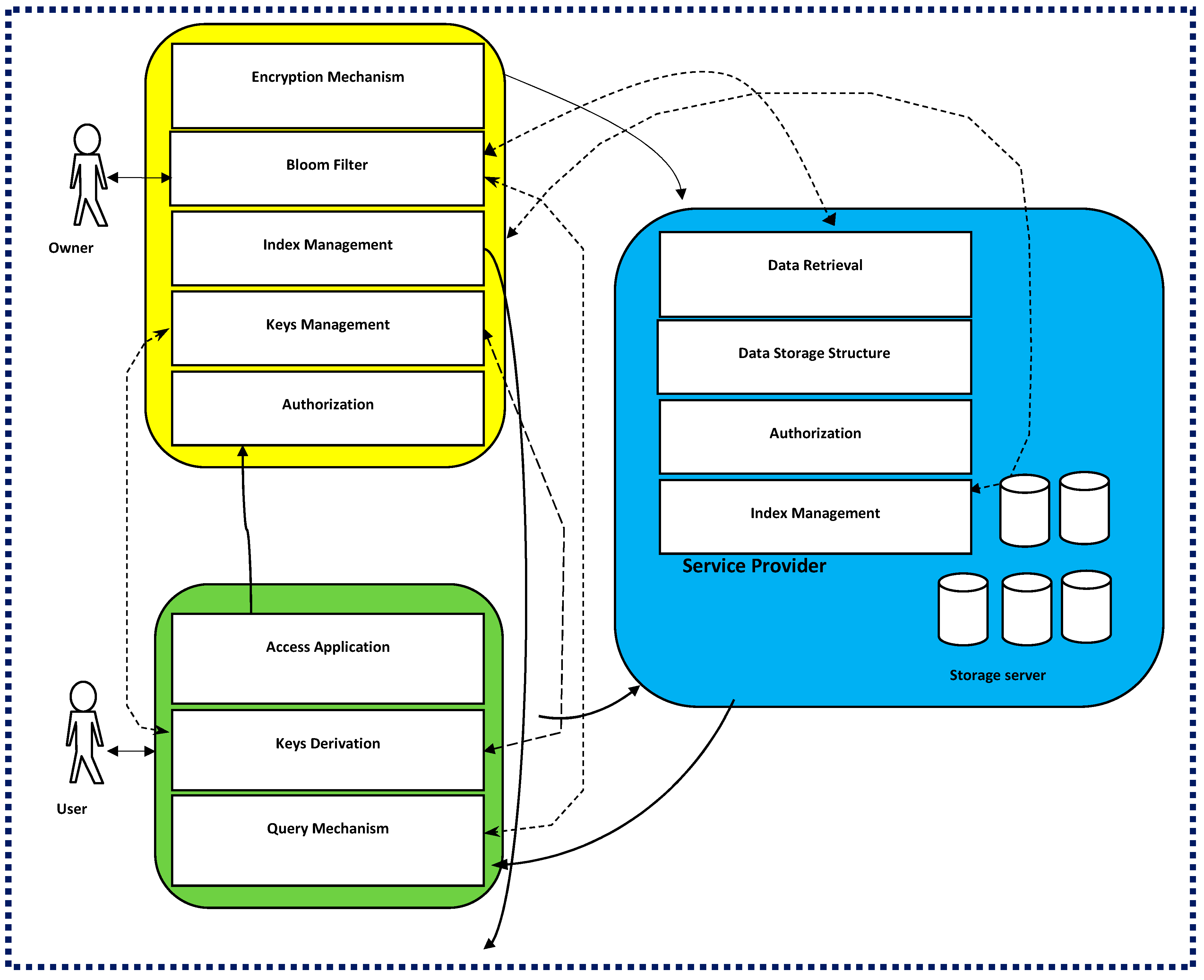
4.4.1. Registration Process
4.4.2. Data Storage Process
4.4.3. Data Retrieval Process
4.5. Implementation Steps of Proposed Framework
- Step 1:
- Requirement Assessment and Architecture Planning (Identify the nature of stored data, privacy requisites, and compliance needs; formulate the cloud storage architecture accordingly).
- Step 2:
- Infrastructure Setup and Data Encryption (Establish the cloud infrastructure and implement encryption protocols for data at rest, in transit, and during processing).
- Step 3:
- Access Control and Privacy Policy (Implement stringent access controls, employ identity management, and articulate explicit privacy policies governing data access).
- Step 4:
- Data Segregation and Redundancy (Categorize data based on sensitivity, introduce redundancy measures for data availability, and ensure systematic backup procedures).
- Step 5:
- Monitoring, Audit, and Incident Response (Deploy monitoring systems, conduct routine audits, and create an incident response plan to address security events effectively).
- Step 6:
- Security Assessments and User Training (Execute regular security audits encompassing vulnerability assessments and offer continuous user training on evolving security practices).
- Step 7:
- Updates and Patch Management (Keep all software components current with the latest security patches for the operating system, applications, and services).
- Step 8:
- Continuous Improvement and Emerging Technologies (Continually enhance the security framework based on evolving threats and integrate emerging technologies to fortify defenses).
- Step 9:
- Regular Audits and Compliance Checks (Conduct regular audits to ensure conformity with data protection regulations and perform checks to uphold security standards).
- Step 10:
- Trust and Customer Assurance (Foster trust through transparent communication, adherence to privacy commitments, and assuring customers about the robustness of data protection measures).
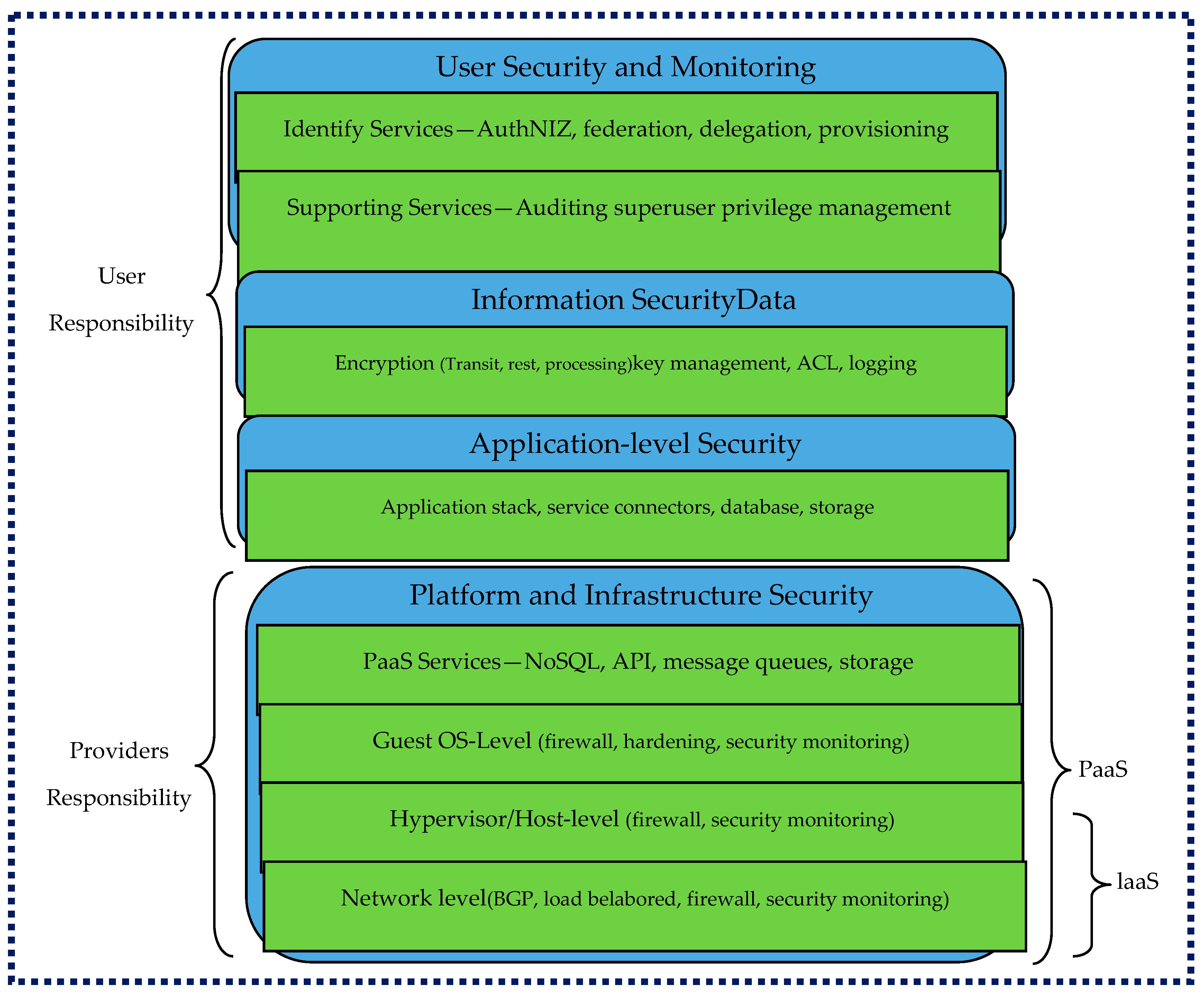
4.6. Cloud Storage, Privacy-Preserving Components, and the Experimental Environment
- Step 1:
- Receive input data containing potentially sensitive attributes, such as personally identifiable information (PII) or financial records.
- Step 2:
- Analyze the data schema to identify attributes that require protection to uphold privacy.
- Step 3:
- Initialize encryption processes by establishing cryptographic frameworks and generating encryption keys.
- Step 4:
- Employ a multi-layer encoding approach, utilizing various encryption techniques like symmetric or asymmetric encryption, to enhance data security.
- Step 5:
- Selectively apply encryption to sensitive attributes based on their level of sensitivity and privacy requirements.
- Step 6:
- Transform the data into an encoded format while ensuring integrity during the encoding process.
- Step 7:
- Manage encoding layers effectively, including tracking encryption keys and maintaining access controls to uphold data integrity.
- Step 8:
- Implement robust access control mechanisms to restrict unauthorized access to the encoded data.
- Step 9:
- Utilize secure storage and transmission methods to prevent unauthorized access and data breaches.
- Step 10:
- Decrypt the data selectively, allowing for the retrieval of original attributes when necessary.
- Step 11:
- Validate privacy preservation measures through regular assessments and audits to ensure compliance with privacy standards.
- Step 12:
- Continuously monitor and update encryption algorithms, access controls, and privacy policies to adapt to emerging threats and maintain effective data privacy protection.
4.7. Cloud Storage and Privacy-Preserving Software Testing Tools
4.8. Contributions and Improvements in Existing Ideas
- Improvement 1: Dynamic Policy Adjustment (Development of adaptive frameworks that will adjust the privacy policies depending on user behavior and data sensitivity levels).
- Improvement 2: User-Centric Encryption Models (Empowers the users with customizable encryption options adaptable to specific data sensitivity requirements).
- Improvement 3: Decentralized Key Management(Encourages the use of distributed key management technologies for enhancing transparency and security).
- Improvement 4: Enhanced Data Visualization(Encourages and provides instinctive tools to the users for understanding and managing their data privacy and utility trade-offs efficiently).
- Improvement 5: Optimized Resource Allocation (Introduces resource-awareness approaches to minimize latency time and computation costs during security management).
- Improvement 6: Cross-Domain Privacy Standards (Establishes universal privacy-preserving standards to perform interoperability across various sectors using cloud storage).
4.9. Comparison with Existing Techniques
5. Discussions
5.1. Implications
5.2. Impact of Coupling on the Proposed Model
5.3. Broader Impacts of the Multi-Layer Encoding Framework on Privacy-Sensitive Domains
5.4. Various Examples of the Described Cloud Storage Privacy-Protecting Model
- (i)
- Data Encryption: Privacy-preserving models in cloud storage commonly utilize encryption techniques to safeguard data. Encryption ensures that data remains confidential, even if unauthorized access occurs.
- (ii)
- Access Control: Privacy-preserving models integrate access control mechanisms to regulate and restrict data access and modification in cloud storage. This prevents unauthorized users from viewing or altering sensitive information.
- (iii)
- Anonymization: Some privacy-preserving models in cloud storage employ anonymization techniques to remove personally identifiable information from data. This makes it challenging to link specific individuals to their stored information.
- (iv)
- Differential Privacy: Differential privacy techniques add noise or randomness to data before storing it in the cloud. This ensures that individual data points cannot be accurately identified, preserving individuals’ privacy while allowing meaningful data analysis.
- (v)
- Secure Multi-Party Computation (MPC): MPC enables various parties to collectively perform computations on their data without revealing sensitive information to each other or the cloud storage provider. This protects data privacy during collaborative analysis.
- (vi)
- Homomorphic Encryption: Homomorphic encryption is a groundbreaking advancement in the field of data security and privacy. It introduces a transformative capability to perform computations on encrypted data without the need for decryption, paving the way for a multitude of opportunities in secure and privacy-preserving data processing. It maintains data privacy throughout the computation process.
- (vii)
- Attribute-Based Encryption (ABE): ABE is an advanced cryptographic technique designed to offer precise control over access to data stored in cloud environments. It enables data encryption with specific attributes, allowing only users with matching attributes to decrypt and access the data.
- (viii)
- Privacy-Preserving Auditing: Privacy-preserving models may include auditing mechanisms that enable users to verify the integrity and authenticity of their cloud-stored data without revealing the actual content. This ensures data integrity while maintaining privacy.
- (ix)
- Data Residency and Jurisdiction Controls: Privacy-preserving models can incorporate features that allow users to specify the geographic location where their data should be stored.
- (x)
- Secure Data Deletion: Privacy-preserving models address the secure deletion of data from cloud storage. This ensures that deleted data is permanently removed and cannot be recovered, protecting the privacy of individuals whose data was stored in the cloud.
5.5. Importance of a Password Verification System in Performance Measurement of the Proposed Approach
5.6. Integration of Multi-Factor Authentication and K-Anonymity with the Proposed Framework
6. Conclusions
- (i)
- During the handling of large datasets or numerous users, the described system may bring computational delays due to multi-level cloud arrangement and multi-layer encryption.
- (ii)
- The advanced multi-layer architecture of cloud-storage security requires significant expertise, and hence, it may have limited accessibility for smaller organizations.
- (iii)
- Interruption in service may affect the data availability in a multi-layer and multi-cloud environment.
- (iv)
- End users may face the problem of inconvenience due to the frequent requirements of authentication and encryption processes.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
- # Multi-Layer Encoding Framework with Privacy-Preserving Attributes
- import numpy as np
- from sklearn.preprocessing import OneHotEncoder
- from diffprivlib.models import LogisticRegression
- from sklearn.model_selection import train_test_split
- # Sample dataset with sensitive categorical attribute
- # Format: [ID, Gender] -- Assuming ‘Gender’ is sensitive
- data = np.array([[1, ‘Male’],
- [2, ‘Female’],
- [3, ‘Male’],
- [4, ‘Female’]])
- # Extract features (e.g., Gender)
- features = data[:, 1].reshape(−1, 1)
- # First Layer: One-Hot Encoding
- encoder = OneHotEncoder(sparse = False)
- encoded_features = encoder.fit_transform(features)
- # Dummy labels for model fitting (required by diffprivlib models)
- # In a real case, this could be replaced with actual prediction labels
- labels = np.array([0, 1, 0, 1]) # Example labels for supervised model
- # Split data (required by sklearn/diffprivlib)
- X_train, X_test, y_train, y_test = train_test_split(encoded_features, labels, test_size = 0.5, random_state = 42)
- # Second Layer: Apply Differential Privacy using diffprivlib Logistic Regression
- epsilon = 1.0 # Privacy budget
- model = LogisticRegression (epsilon = epsilon)
- model.fit (X_train, y_train)
- # Use model to transform input with privacy guarantee
- encoded_data_privacy = model.predict_proba (encoded_features)
- # Third Layer: Optional additional encoding (e.g., encryption)
- # Placeholder for additional security mechanisms
- # Output the final encoded data
- print (“Encoded data with privacy-preserving attributes:”)
- print (encoded_data_privacy)
References
- Akremi, A.; Rouached, M. A comprehensive and holistic knowledge model for cloud privacy protection. J. Supercomput. 2021, 77, 7956–7988. [Google Scholar] [CrossRef]
- Salek, M.S.; Khan, S.M.; Rahman, M.; Deng, H.-W.; Islam, M.; Khan, Z.; Chowdhury, M.; Shue, M. A Review on cyber security of cloud computing for supporting connected vehicle applications. IEEE Internet Things J. 2022, 9, 8250–8268. [Google Scholar] [CrossRef]
- Rashid, Z.; Noor, U.; Altmann, J. Economic model for evaluating the value creation through information sharing within the cyber security information sharing ecosystem. Future Gener. Comput. Syst. 2021, 124, 436–466. [Google Scholar] [CrossRef]
- Mishra, A.; Alzoubi, Y.I.; Gill, A.Q.; Anwar, M.J. Cyber security enterprises policies: A comparative study. Sensors 2022, 22, 538. [Google Scholar] [CrossRef] [PubMed]
- Gill, S.S.; Kumar, A.; Singh, H.; Singh, M.; Kaur, K.; Usman, M.; Buyya, R. Quantum computing: A taxonomy, systematic review and future directions. Softw. Pract. Exp. 2022, 52, 66–114. [Google Scholar] [CrossRef]
- Kumar; Goyal, R. On cloud security requirements, threats, vulnerabilities, and counter measures: A survey. Comput. Sci. Rev. 2019, 33, 1–48. [Google Scholar] [CrossRef]
- Gupta, B.B.; Agrawal, D.P.; Wang, H. Computer, and Cyber Security: Principles, Algorithm, Applications, and Perspectives; Taylor & Francis Group: Oxford shire, UK; CRC Press: Boca Raton, FL, USA, 2019. [Google Scholar]
- Alzahrani, A.; Alyas, T.; Alissa, K.; Abbas, Q.; Alsaawy, Y.; Tabassum, N. Hybrid approach for improving the performance of data reliability in cloud storage management. Sensors 2022, 22, 5966. [Google Scholar] [CrossRef]
- Pathak, M.; Mishra, K.N.; Singh, S.P. Securing data and preserving privacy in cloud IoT-based technologies an analysis of assessing threats and developing effective safeguard. Artif. Intell. Rev. 2024, 57, 269. [Google Scholar] [CrossRef]
- El-Booz, S.A.; Attiya, G.; El-Fishawy, N. A secure cloud storage system combining time-base done-time password and automatic blocker protocol. EURASIP J. Inf. Secur. 2015, 188–194. [Google Scholar]
- Yuan, D.; Song, X.; Xu, Q.; Zhao, M.; Wei, X.; Wang, H.; Jiang, H. An ORAM-based privacy preserving data sharing scheme for cloud storage. J. Inf. Secur. Appl. 2018, 39, 1–9. [Google Scholar] [CrossRef]
- Jin, Y.; Wang, Y. An improved scheme of privacy-preserving based on Lagrange interpolation in cloud storage. In Proceedings of the 2nd International Conference on Artificial Intelligence and Industrial Engineering (AIIE2016), Beijing, China, 20–21 November 2016; pp. 424–428. [Google Scholar]
- Subha, T.; Jayashri, S. Efficient privacy-preserving integrity checking model for cloud at a storage security. In Proceedings of the 8th International Conference on Advanced Computing (ICoAC), Chennai, India, 19–21 January 2017; pp. 55–60. [Google Scholar]
- Kavin, P.; Ganapathy, S. A secured storage and privacy-preserving model using CRT for providing security on cloud and IoT-based applications. Comput. Netw. 2019, 151, 181–190. [Google Scholar] [CrossRef]
- Fritze, M.; Schiller-Wurster, K. Time to Get Serious About Hardware Cyber Security. Available online: https://www.defenseone.com/ideas/2018/01/time-get-serious-about-hardware-cybersecurity/145210/ (accessed on 2 March 2022).
- Kalaivani, A.; Ananthi, B.; Sangeetha, S. Enhanced hierarchical attribute-based encryption with modular padding for improved public auditing in cloud computing using a semantic ontology. Clust. Comput. 2019, 22, 3783–3790. [Google Scholar] [CrossRef]
- Alzoubi, Y.I.; Al-Ahmad, A.; Kahtan, H. Block chain technology as a Fog computing security and privacy solution: An overview. Comput. Commun. 2022, 182, 129–152. [Google Scholar] [CrossRef]
- Razaque, A.; Rizvi, S.S. Privacy-preserving model: A new scheme for auditing cloud stakeholders. J. Cloud Comput. 2017, 6, 7. [Google Scholar] [CrossRef]
- Kuang, L.; Tu, S.; Zhang, Y.; Yang, X. Providing privacy preserving in next POI recommendation for mobile edge computing. J. Cloud Comput. 2020, 9, 10. [Google Scholar] [CrossRef]
- Chamikara, M.A.P.; Bertók, P.; Liu, D.; Camtepe, S.; Khalil, I. Efficient data perturbation for privacy-preserving and accurate at a stream mining. Pervasive Mob. Comput. 2018, 48, 1–19. [Google Scholar] [CrossRef]
- Nagaraj, J.; Kumar, P. Review on privacy-preserving in cloud computing. Int. J. Comput. Appl. 2014, 975, 23–26. [Google Scholar]
- Tissir, N.; ElKafhali, S.; Aboutabit, N. Cyber security management in cloud computing: Semantic literature review and conceptual frame work proposal. J. Reliab. Intell. Environ. 2021, 7, 69–84. [Google Scholar] [CrossRef]
- Ghantous, G.B.; Gill, A.Q. Dev Ops reference architecture for multi-cloud IoT applications. In Proceedings of the 20th Conference on Business Informatics (CBI), Vienna, Austria, 11–13 July 2018; pp. 158–167. [Google Scholar]
- Singh, N.; Singh, A.K. Data privacy protection mechanisms in the cloud. Data Sci. Eng. 2018, 3, 24–39. [Google Scholar] [CrossRef]
- Joseph, N.M.; Daniel, E.; Vasanthi, N. Survey on privacy-preserving methods for storage in cloud computing. In Proceedings of the Amrita International Conference of Women in Computing, Amrita Vishwa Vidyapeetham, India, 9–11 January 2013; pp. 1–4. [Google Scholar]
- Bhagyashri, S.; Gurave, Y. A survey on privacy-preserving techniques for secure cloud storage. Int. J. Comput. Sci. Mob. Comput. (IJCSMC) 2014, 3, 675–680. [Google Scholar]
- Liu, Y.; Sun, Y.L.; Ryoo, J.; Rizvi, S.; Vasilakos, A.V. A survey of security and privacy challenges in cloud computing: Solutions and future directions. J. Comput. Sci. Eng. 2015, 9, 119–133. [Google Scholar] [CrossRef]
- Li, J.; Yan, H.; Zhang, Y. Identity-based privacy-preserving remote data integrity checking for cloud storage. IEEE Syst. J. 2020, 15, 577–585. [Google Scholar] [CrossRef]
- Waqar, A.; Raza, A.; Abbas, H.; Khan, M.K. A frame work for the preservation of cloud users’ data privacy using dynamic reconstruction of metadata. J. Netw. Comput. Appl. 2013, 36, 235–248. [Google Scholar] [CrossRef]
- Gundert, L.; Shen, M.-Y.; Lee, M. Understanding Security Through Probability. Available online: https://blogs.cisco.com/security/understanding-security-through-probability (accessed on 1 March 2022).
- Yang, X.; Yue, C.; Zhang, W.; Liu, Y.; Ooi, B.C.; Chen, J. Secu DB: An In-Enclave Privacy-Preserving and Tamper-Resistant Relational Database. Proc. VLDB Endow. 2024, 17, 3906–3919. [Google Scholar] [CrossRef]
- Wang, X.; Garg, S.; Lin, H.; Hu, J.; Kaddoum, G.; Piran, M.J.; Hossain, M.S. Toward Accurate Anomaly Detection in Industrial Internet of Things Using Hierarchical Federated Learning. IEEE Internet Things J. 2022, 9, 7110–7119. [Google Scholar] [CrossRef]
- Wang, X.; Garg, S.; Lin, H.; Kaddoum, G.; Hu, J.; Hossain, M.S. A Secure Data Aggregation Strategy in Edge Computing and Blockchain-Empowered Internet of Things. IEEE Internet Things J. 2020, 7, 14237–14246. [Google Scholar] [CrossRef]
- Wang, X.; Garg, S.; Lin, H.; Kaddoum, G.; Hu, J.; Hassan, M.M. Heterogeneous Block chain and AI-Driven Hierarchical Trust Evaluation for 5G-Enabled Intelligent Transportation Systems. IEEE Trans. Intell. Transp. Syst. 2021; 22, in press. [Google Scholar] [CrossRef]
- Wang, X.; Hu, J.; Lin, H.; Garg, S.; Kaddoum, G.; Piran, M.J.; Hossain, M.S. QoS and Privacy- Aware Routing for 5G-Enabled Industrial Internet of Things: A Federated Reinforcement Learning Approach. IEEE Trans. Ind. Informat. 2022, 18, 4189–4197. [Google Scholar] [CrossRef]
- Torkura, K.A.; Sukmana, M.I.; Cheng, F.; Meinel, C. Continuous auditing and threat detection in multi-cloud infrastructure. Comput. Secur. 2021, 102, 102–124. [Google Scholar] [CrossRef]
- Rizvi, S.; Karpinski, K.; Kelly, B.; Walker, T. Utilizing third party auditing to managing trust in the cloud. Procedia Comput. Sci. 2015, 61, 191–197. [Google Scholar] [CrossRef]
- Gupta, L.; Salman, T.; Ghubaish, A.; Unal, D.; Al-Ali, A.K.; Jain, R. Cyber security of multi-cloud health care systems: A hierarchical deep learning approach. Appl. Soft Comput. 2022, 118, 108439. [Google Scholar] [CrossRef]
- Hamilton, T. Test Environment for Software Testing. Available online: https://www.guru99.com/test-environment-software-testing.html (accessed on 1 March 2022).
- Dong, B.; Chen, Z.; Wang, H.; Tang, L.-A.; Zhang, K.; Lin, Y.; Li, Z.; Chen, H. Efficient discovery of abnormal event sequences in enterprise security systems. In Proceedings of the 2017 ACMon Conference on Information and Knowledge Management, Singapore, 6–10 November 2017; pp. 707–715. [Google Scholar]
- Zhang, Z.; Zhang, W.; Qin, Z. A partially hidden policy CP-ABE scheme against at tribute values guessing attacks with online privacy-protective decryption testing in IoT assisted cloud computing. Future Gener. Comput. Syst. 2021, 123, 181–195. [Google Scholar] [CrossRef]
- Tan, J.; Liao, X.; Liu, J.; Cao, Y.; Jiang, H. Channel Attention Image Stega nography with Generative Adversarial Networks. IEEE Trans. Netw. Sci. Eng. 2022, 9, 888–903. [Google Scholar] [CrossRef]
- Hu, J.; Liao, X.; Wang, W.; Qin, Z. Detecting Compressed Deep fake Videos in Social Networks Using Frame-Temporality Two-Stream Convolution Network. IEEE Trans. Circuits Syst. Video Technol. 2022, 32, 1089–1102. [Google Scholar] [CrossRef]
- Chen, J.; Liao, X.; Wang, W.; Qian, Z.; Qin, Z.; Wang, Y. SNIS: A Signal Noise Separation-Based Network forPost-Processed Image Forgery Detection. IEEE Trans. Circuits Syst. Video Technol. 2023, 33, 935–951. [Google Scholar] [CrossRef]
- Kilinc, N.; Sezer, L.; Mishra, A. Cloud-based test tools: A brief comparative view. Cybern. Inf. Technol. 2018, 18, 3–14. [Google Scholar]
- Mishra, A.; Alzoubi, Y.I.; Anwar, M.J.; Gill, A.Q. Attributes impacting cyber security policy development: An evidence from seven nations. Comput. Secur. 2022, 120, 102820. [Google Scholar] [CrossRef]
- Mishra, D.; Aydin, S.; Mishra, A.; Ostrovska, S. Knowledge management in requirement elicitation: Situational methods view. Comput. Stand. Interfaces 2018, 56, 49–61. [Google Scholar] [CrossRef]
- D Shukla, K.; Dwivedi, V.K.; Trivedi, M.C. Encryption algorithm in cloud computing. Mater. Today Proc. 2021, 37, 1869–1875. [Google Scholar] [CrossRef]
- Thabit, F.; Al homdy, S.; Jagtap, S. Security analysis and performance evaluation of a new light weight cryptographic algorithm for cloud computing. Glob. Transit. Proc. 2021, 2, 100–110. [Google Scholar] [CrossRef]
- Thompson, M. CISOs should work closely with their IT AM colleagues. Netw. Secur. 2021, 2021, 9–12. [Google Scholar] [CrossRef]
- Ramalingam, C.; Mohan, P. Addressing semantics standards for cloud portability and interoperability in amulti-cloud environment. Symmetry 2021, 13, 317. [Google Scholar] [CrossRef]
- Alzoubi, Y.I.; Osmanaj, V.H.; Jaradat, A.; Al-Ahmad, A. Fog computing security and privacy for the Internet of Thing applications: State-of-the-art. Secur. Priv. 2021, 4, e145. [Google Scholar] [CrossRef]
- Lightedge. com. Why Multi-Cloud Strategy Beats Single Cloud Almost Every Time. Available online: https://lightedge.com/resources/why-multi-cloud-strategy-beats-single-cloud-almost-every-time/ (accessed on 30 June 2025).
- Stubbs, R. Classification of Cryptographic Keys. Available online: https://www.cryptomathic.com/news-events/blog/classification-of-cryptographic-keys-functions-and-properties (accessed on 1 March 2022).
- Amiruddin, A.; Ratna, A.A.P.; Sari, R.F. Construction and analysis of key generation algorithms based on modified Fibonacci and scrambling factors for privacy preservation. Int. J. Netw. Secur. 2019, 21, 250–258. [Google Scholar]
- Amirany, A.; Jafari, K.; Moaiyeri, M.H. True random number generator for reliable hardware security modules based on an euromorphic variation-tolerant spintronic structure. IEEE Trans. Nanotechnol. 2020, 19, 784–791. [Google Scholar] [CrossRef]
- Yamato, Y. Automatic verification technology of software patches for user virtual environments on IaaS cloud. J. Cloud Comput. 2015, 4, 1–14. [Google Scholar] [CrossRef]
- Potter, B.; McGraw, G. Software security testing. IEEE Secur. Priv. 2004, 2, 81–85. [Google Scholar] [CrossRef]
- Yang, X.; Wang, S.; Li, F.; Zhang, Y.; Yan, W.; Gai, F.; Yu, B.; Feng, L.; Gao, Q.; Li, Y. UbiquitousVerification in CentralizedLedger Database. In Proceedings of the 2022 IEEE 38th International Conference on Data Engineering (ICDE), Kuala Lumpur, Malaysia, 9–12 May 2022; pp. 1808–1821. [Google Scholar] [CrossRef]
- Cayirci, E.; De Oliveira, A.S. Modelling trust and risk for cloud services. J. Cloud Comput. 2018, 7, 14. [Google Scholar] [CrossRef]
- Öztayşi, B.; Kutlu, A.C. Determining the importance of performance measurement criteria based on total quality management using fuzzy analytical network process. In Practical Applications of Intelligent Systems. Advances in Intelligent and Soft Computing; Wang, Y., Li, T., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 391–400. [Google Scholar]
- Bergh, D.D.; Ketchen, D.J., Jr.; Orlandi, I.; Heugens, P.P.; Boyd, B.K. Information asymmetry in management research: Past accomplishments and future opportunities. J. Manag. 2019, 45, 122–158. [Google Scholar] [CrossRef]
- Yang, E.; Joshi, G.P.; Seo, C. Improving the detection rate of rarely appearing intrusions in network-based intrusion detectionsystems. Comput. Mater. Contin. 2021, 66, 1647–1663. [Google Scholar]
- ŽTurk; de Soto, B.G.; Mantha, B.R.; Maciel, A.; Georgescu, A. A systemic frame work for addressing cyber security in construction. Autom. Constr. 2022, 133, 103988. [Google Scholar]
- Hu, F.; Qiu, M.; Li, J.; Grant, T.; Taylor, D.; McCaleb, S.; Butler, L.; Hamner, R. A review on cloud computing: Design chall enges in architecture and security. J. Comput. Inf. Technol. 2011, 19, 25–55. [Google Scholar] [CrossRef]
- Educative. Security on the Cloud—Design Principles. Available online: https://www.educative.io/courses/cloud-architecture-a-guide-to-design-and-architect-your-cloud/7nnxwPxALZj (accessed on 6 March 2022).
- Nexor. The 14 Cloud Security Principles—What Do They Mean for You? Available online: https://www.nexor.com/cloud-security-principles/ (accessed on 6 March 2022).
- Ahuja, R.; Mohanty, S.K.; Sakurai, K. A scalable attribute-set-based access control with both sharing andfull-fledged delegation of access privileges in cloud computing. Comput. Electr. Eng. 2017, 57, 241–256. [Google Scholar] [CrossRef]
- Ismail, U.M.; Islam, S. A unified frame work for cloud security transparency and audit. J. Inf. Secur. Appl. 2020, 54, 102594. [Google Scholar]
- Ru Wei, H.; Xiao Lin, G.; Si, Y.; Wei, Z. Study of Privacy-preserving Framework for Cloud Storage. ComSIS 2011, 8, 801–819. [Google Scholar] [CrossRef]
- Chandramohan, A.D.; Vengattaraman, T.; Rajaguru, D.; Dhavachelvan, P. A new privacy preserving technique for cloud service user end or segment using multi-agents. J. King Saud Univ.—Comput. Inf. Sci. 2016, 28, 37–54. [Google Scholar] [CrossRef]
- Li, Y.; Gai, K.; Qiu, L.; Qiu, M.; Zhao, H. Intelligent cryptography approach for secure distributed big data storage in cloud computing. Inf. Sci. 2017, 387, 103–115. [Google Scholar] [CrossRef]
- Liu, X.; Lin, Y.; Liu, Q.; Yao, X. A Privacy-Preserving Principal Component Analysis Outsourcing Framework. In Proceedings of the 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/ 12th IEEE International Conference on Big Data Science and Engineering, NewYork, NY, USA, 1–3 August 2018. [Google Scholar]
- Fern, M.; Jaimunk, J.; Thuraisingham, B. Privacy-Preserving Architecture for Cloud-IoT Platforms. In Proceedings of the 2019 IEEE International Conference on Web Services (ICWS), Milan, Italy, 8–13 July 2019. [Google Scholar] [CrossRef]
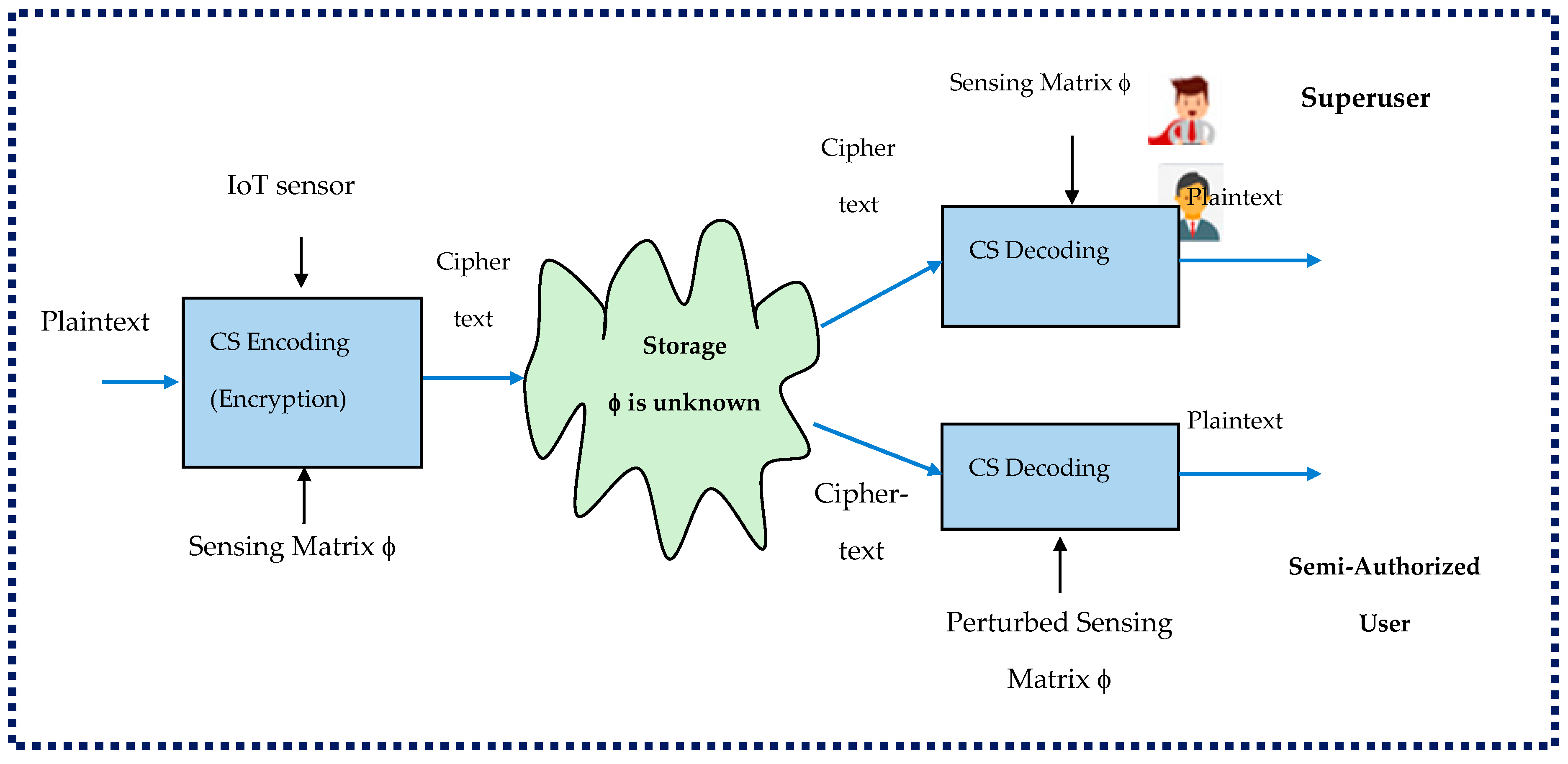
- Kuldeep, G.; Zhang, Q. Multi-class privacy-preserving cloud computing based on compressive sensing forIoT. J. Inf. Secur. Appl. 2022, 66, 103139. [Google Scholar]
- Kumar, A.; Aljrees, T.; Hsieh, S.-Y.; Singh, K.U.; Singh, T.; Raja, L.; Samriya, J.K.; Mundotiya, R.K. A Hybrid Solution for Secure Privacy-Preserving Cloud Storage & Information Retrieval. Res. Open Access Hum.-Centric Comput. Inf. Sci. 2023, 13, 11. [Google Scholar] [CrossRef]
- Gopinath, N. Enhancing the Cloud Security using Secured Quantum Key Distribution. Res. Sq. 2023. preprint. [Google Scholar]
- Safe Li Share. Available online: https://www.cybersecurityintelligence.com/safelishare-10782.html (accessed on 26 June 2025).
- Skyflow. Securing the Modern AI Data Stack. Data Privacy Vault for PII, PCI, and PHI. Available online: https://www.skyflow.com (accessed on 26 June 2025).
- Singh, A.; Satapathy, S.C.; Roy, A.; Gutub, A. Ai-based mobile edge computing for IoT: Applications, challenges, and futurescope. Arab. J. Sci. Eng. 2022, 47, 9801–9831. [Google Scholar] [CrossRef]
- Mishra, A.; Alzoubi, Y.I.; Gill, A.Q.; Mishra, K.N. EnhancingPrivacy-Preserving Mechanisms in Cloud Storage: A Novel Conceptual Frame work. Concurr. Comput. Pract. Exp. 2023, 35, e7831. [Google Scholar] [CrossRef]


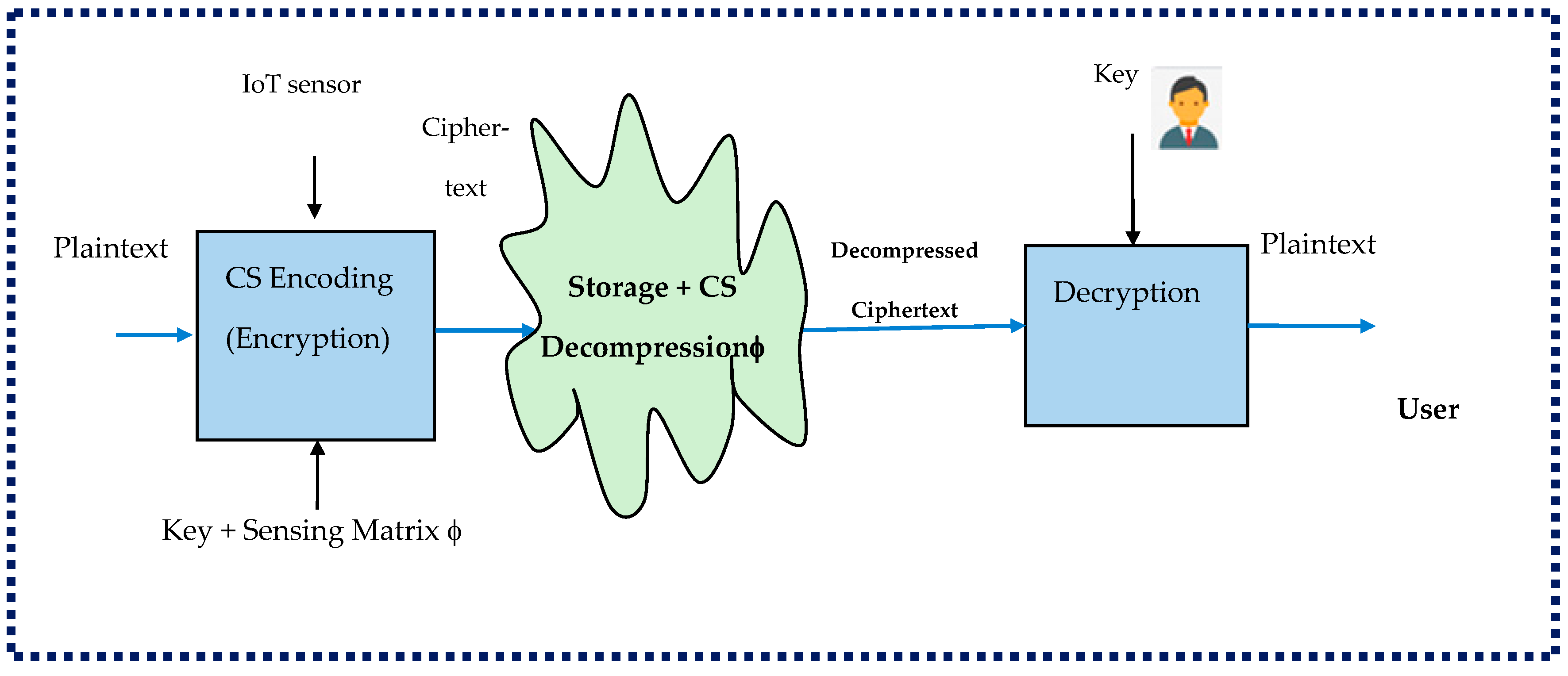
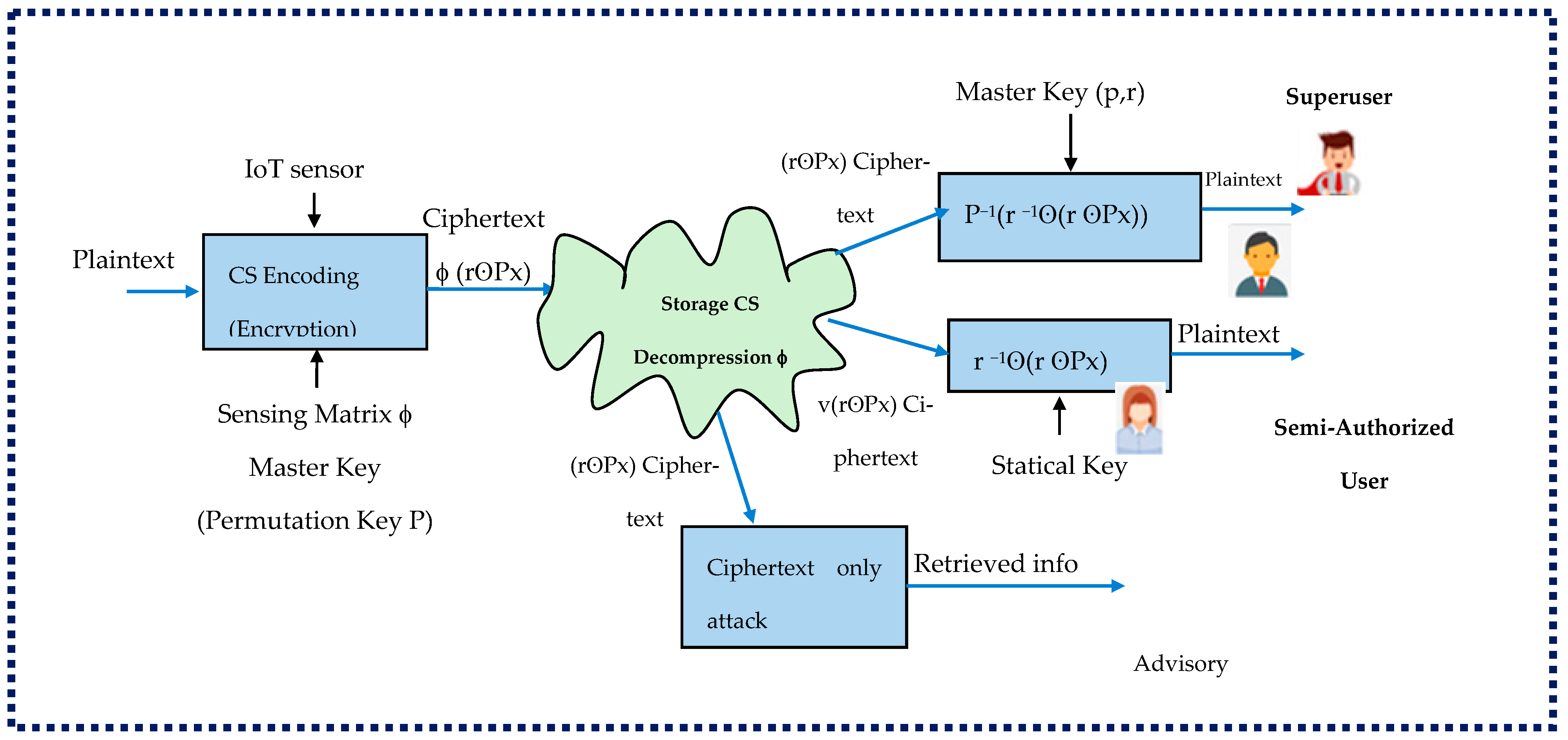
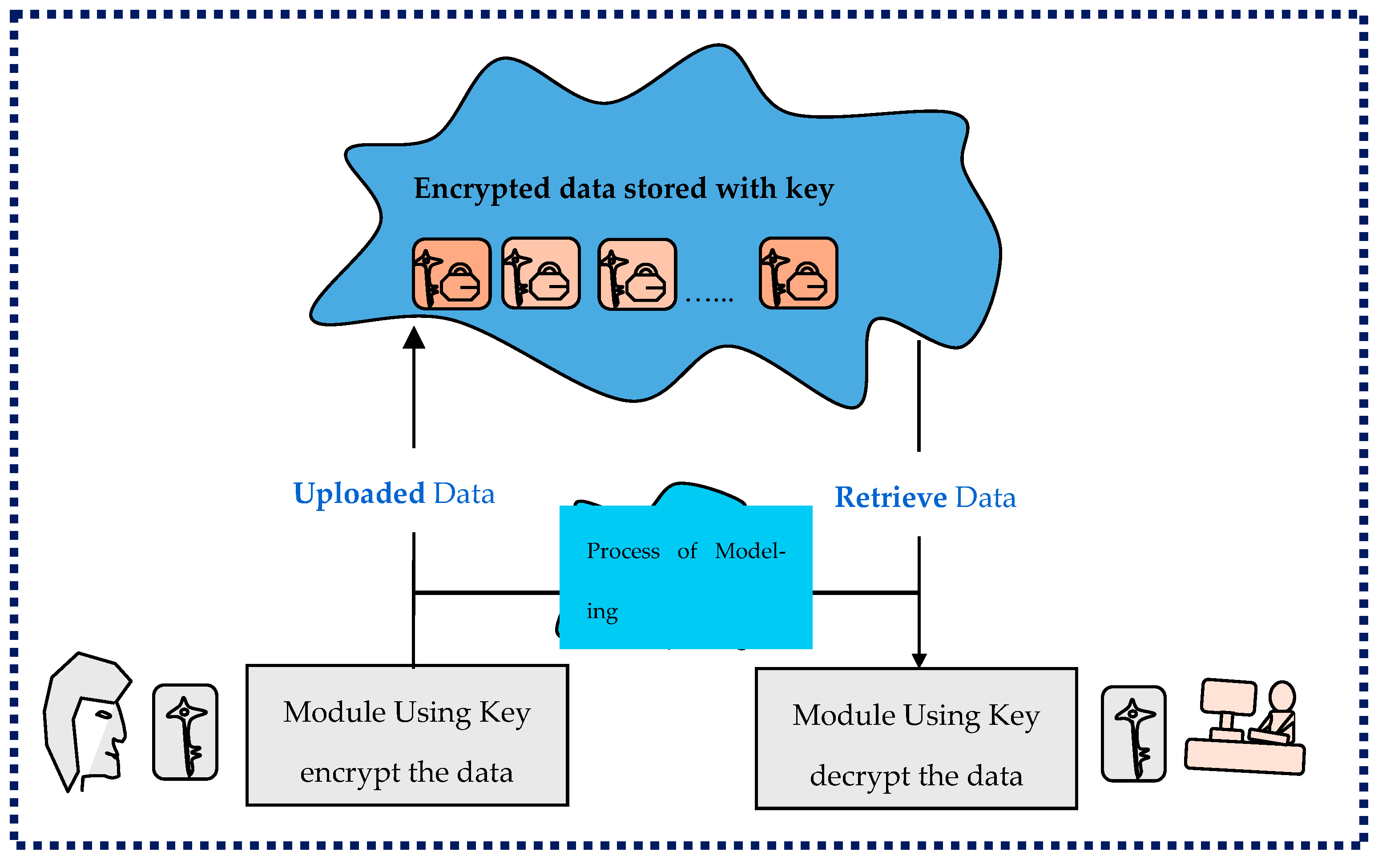
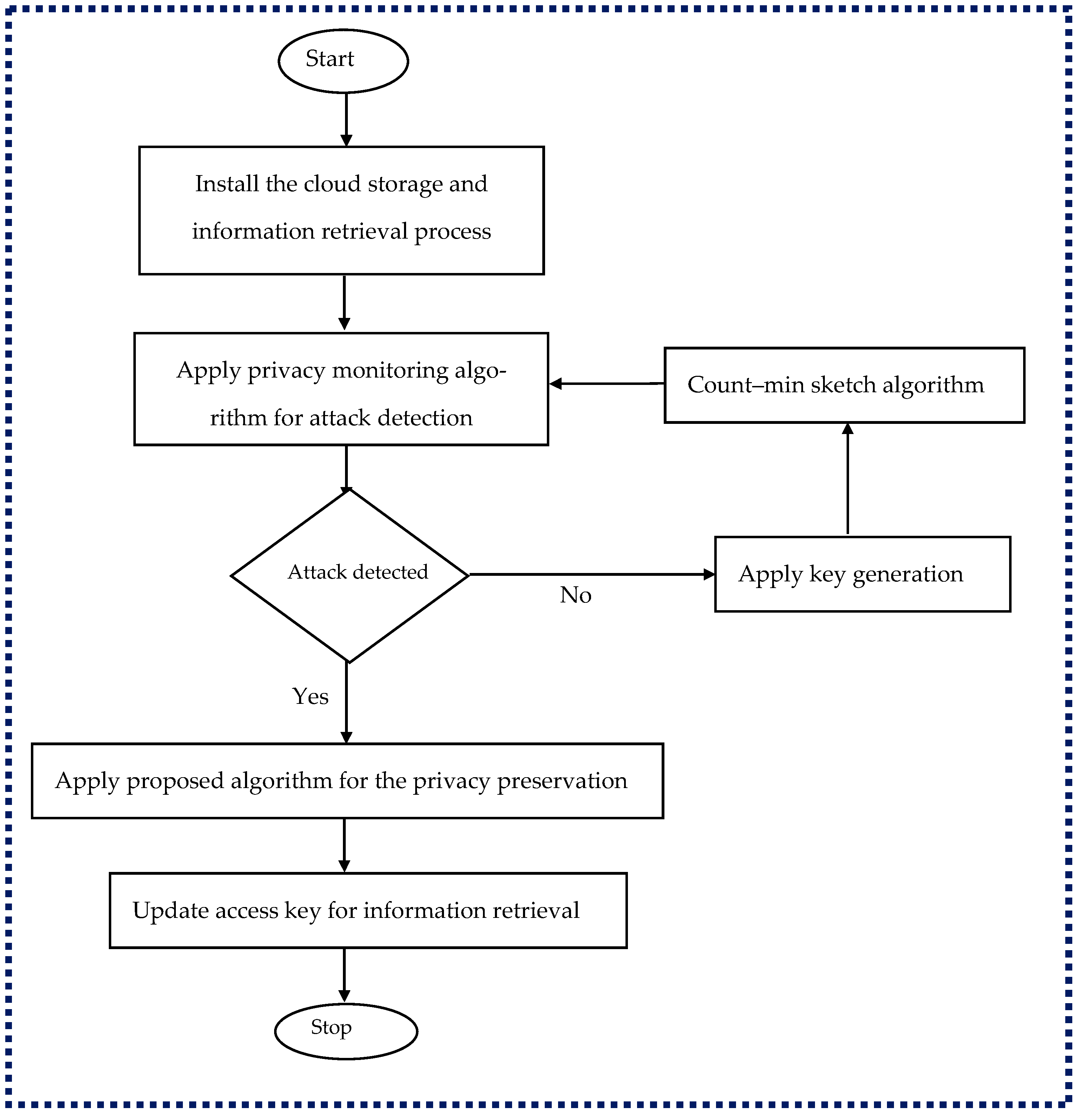
| Privacy-Preserving Attribute | Study | Characteristics |
|---|---|---|
| Design features | [11,14] |
|
| Data auditing | [43,46] |
|
| Cryptographic technique | [10,11,12,13,14,16,44,45,48,49] |
|
| External assets | [12,14,45,50] |
|
| Structure of the cloud storage | [36,51] |
|
| Privacy-Protecting Attribute | Study | Characteristics |
|---|---|---|
| Key generation technique | [11,48] |
|
| Key length | [14,54] |
|
| Key governance | [14,45] |
|
| Key function | [49,54] |
|
| Privacy-Protecting Attribute | Reference | Characteristics |
|---|---|---|
| Test environment | [15,39] |
|
| Test applied | [10,12,13,14,45] |
|
| Privacy-Protecting Attribute | Study | Characteristics |
|---|---|---|
| Threat type | [10,59,60] |
|
| Threat addressed | [22,60] |
|
| Privacy-Preserving Attribute | Study | Properties |
|---|---|---|
| Performance standards | [11,12,14,61] |
|
| Abnormality | [10,11,13,44] |
|
| Privacy achievements | [62,63,64] |
|
| Paper ID | Encryption | Access Control | Anonymization | Data Integrity | Auditability | Scalability | Threat Detection | |
|---|---|---|---|---|---|---|---|---|
| 1. | [2] Salek et al. (2022) | Uses advanced cryptographic protocols for connected vehicles. | Role-Based Access Control (RBAC). | Limited focus. | Blockchain-based for secure communication. | Highlights monitoring mechanisms. | Moderate (connected vehicle constraints). | Strong focus on vehicular cybersecurity. |
| 2. | [5] Gill et al. (2022) | Quantum-resistant cryptographic methods. | Enhanced quantum-computing-aware methods. | No focus. | Discusses impact of quantum computing on integrity. | Highlights future quantum audit tools. | High (quantum approaches adapt well). | Discusses potential quantum-enabled threats. |
| 3. | [6] Kumar and Goyal (2019) | Broad coverage of standard encryption. | Discusses fine-grained control (ABAC). | Mentions pseudonymization. | Comprehensive focus on hashing and blockchain. | Limited, suggests general measures. | High (modular approaches). | Surveys cloud threat detection methods. |
| 4. | [22] Tissir et al. (2021) | Semantic-based cryptographic solutions. | Conceptual models for access control. | Emphasizes k-anonymity. | Moderate (framework proposal only). | Proposes auditing framework. | High (semantic adaptability). | Limited focus on practical threat detection. |
| 5. | [36] Torkura et al. (2021) | Encryption for multi-cloud environments. | Highlights advanced access models. | Limited focus. | Strong, continuous validation with Merkle trees. | Extensive focus on real-time auditing. | Moderate (multi-cloud setup overhead). | Detailed techniques for multi-cloud threats. |
| 6. | [38] Gupta et al. (2022) | Encryption using hierarchical deep learning. | Focus on healthcare-specific RBAC. | Data obfuscation techniques discussed. | Strong emphasis on healthcare data pipelines. | Limited, proposes basic mechanisms. | High (hierarchical model adaptability). | Healthcare-specific threat detection. |
| 7. | [41] Z. Zhang et al. (2019) | Advanced CP-ABE scheme to prevent guessing attacks. | Fine-grained, attribute-based control. | Policy hiding addresses partial anonymization. | Ensures integrity via privacy-protective decryption. | Limited to policy verification. | Scalable for IoT-cloud integrations. | Targets attribute guessing attacks. |
| 8. | [55] Amiruddin et al. (2019) | Advanced cryptographic techniques for storage. | Highlights encryption-integrated control. | Limited focus. | Emphasizes cryptographic proof mechanisms. | Detailed coverage of cryptographic auditing. | Moderate (storage-specific solutions). | Limited focus on general cloud threats. |
| 9. | Proposed Approach | Advanced cryptographic approaches for storage. | Highlights advanced accessed model and encryption-integrated control. | Emphasized k-anonymity with limited focus on pseudo-anonymity. | Advanced framework with emphasis on cryptography. | Descriptive coverage of cryptography-based real-time auditing | Advanced modular approach. | Detailed focus on practical threat detection and multi-cloud threats. |
| Paper ID | Advantages | Limitations | |
|---|---|---|---|
| 1. | [2] Salek et al. (2022) | It provides a comprehensive review of cloud cybersecurity for connected vehicles; scalable to IoT-cloud integration. | Limited focus on anonymization and auditability details; it lacks practical implementation insights. |
| 2. | [5] Gill et al. (2022) | It envisions robust post-quantum cryptographic solutions; it explores scalability and future threats. | Theoretical insights without immediate practical applicability; it has a limited focus on anonymization. |
| 3. | [6] Kumar and Goyal (2019) | It provides a detailed survey of cloud security challenges and countermeasures. It provides further extensive coverage of access control. | It has limited focus on scalability and practical applications; it lacks detailed anonymization strategies. |
| 4. | [22] Tissir et al. (2021) | It provides a conceptual framework adaptable to various cloud environments and addresses management challenges. | It does not focus explicitly on anonymization or encryption details; it lacks practical validation. |
| 5. | [36] Torkura et al. (2021) | It provides practical and scalable solutions for multi-cloud auditing and threat detection. | It has limited focus on encryption and anonymization; it is primarily targeted at auditing use cases. |
| 6. | [38] Gupta et al. (2022) | It includes advanced use of hierarchical deep learning for scalable and effective threat detection. Further, it ensures healthcare data integrity. | It focuses mainly on healthcare use cases; it has limited discussion on anonymization and cryptographic details. |
| 7. | [41] Z. Zhang et al. (2019) | It provides an innovative CP-ABE scheme that ensures robust access control and partial anonymization. It is scalable with IoT-cloud integration. | It has limited focus on auditability and broad threat landscapes; it mainly addresses attribute-guessing attacks. |
| 8. | [55] Amiruddin et al. (2019) | It provides a comprehensive review of cryptographic challenges and solutions. It emphasizes data integrity. | It focuses primarily on cryptographic methods; it has scalability challenges in multi-cloud contexts. |
| 9. | The proposed multi-layer encoding framework | Incorporates various privacy-protecting attributes traced in the survey. Further, it incorporates well-designed elements to ensure data privacy and security. | To ensure cloud scalability within the framework, it is imperative to establish a viable mechanism. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mishra, K.N.; Lal, R.K.; Barwal, P.N.; Mishra, A. Advancing Data Privacy in Cloud Storage: A Novel Multi-Layer Encoding Framework. Appl. Sci. 2025, 15, 7485. https://doi.org/10.3390/app15137485
Mishra KN, Lal RK, Barwal PN, Mishra A. Advancing Data Privacy in Cloud Storage: A Novel Multi-Layer Encoding Framework. Applied Sciences. 2025; 15(13):7485. https://doi.org/10.3390/app15137485
Chicago/Turabian StyleMishra, Kamta Nath, Rajesh Kumar Lal, Paras Nath Barwal, and Alok Mishra. 2025. "Advancing Data Privacy in Cloud Storage: A Novel Multi-Layer Encoding Framework" Applied Sciences 15, no. 13: 7485. https://doi.org/10.3390/app15137485
APA StyleMishra, K. N., Lal, R. K., Barwal, P. N., & Mishra, A. (2025). Advancing Data Privacy in Cloud Storage: A Novel Multi-Layer Encoding Framework. Applied Sciences, 15(13), 7485. https://doi.org/10.3390/app15137485







