Differentiated GNSS Baseband Jamming Suppression Method Based on Classification Decision Information
Abstract
Featured Application
Abstract
1. Introduction
- (1)
- Different interference types require specific configurations of window length, mother wavelet type, or energy thresholds for optimal suppression. When cross-domain changes occur—such as variations in interference power levels or channel fading—preset parameters struggle to adapt synchronously, leading to either insufficient suppression bandwidth (resulting in residual leakage) or excessive bandwidth that inadvertently degrades the desired signal [16,17].
- (2)
- Transform-domain separation typically assumes significant energy differences between the signal and interference along at least one feature dimension. When the legitimate signal and interference exhibit similar energy levels in localized time–frequency regions, overly high thresholds may cause signal loss, while low thresholds allow interference sidelobes to persist, making it difficult to maintain consistent separation using fixed thresholds or projection dimensions.
- (3)
- Conventional transform-domain methods primarily target energy-based interference and lack capabilities for spoofing feature recognition or alerting. Spoofed components may remain latent in the observed data after transform processing, rendering subsequent filters unaware of degraded signal integrity, thereby continuously injecting false position information into the navigation solution and accumulating systemic bias [18,19].
2. Jamming Classification and Mathematical Modeling
- Environmental interference, which arises from non-line-of-sight (NLOS) propagation and signal blockage or interruption caused by dense urban structures or complex terrain.
- Man-made interference, which includes:
2.1. Suppressive Jamming
- (1)
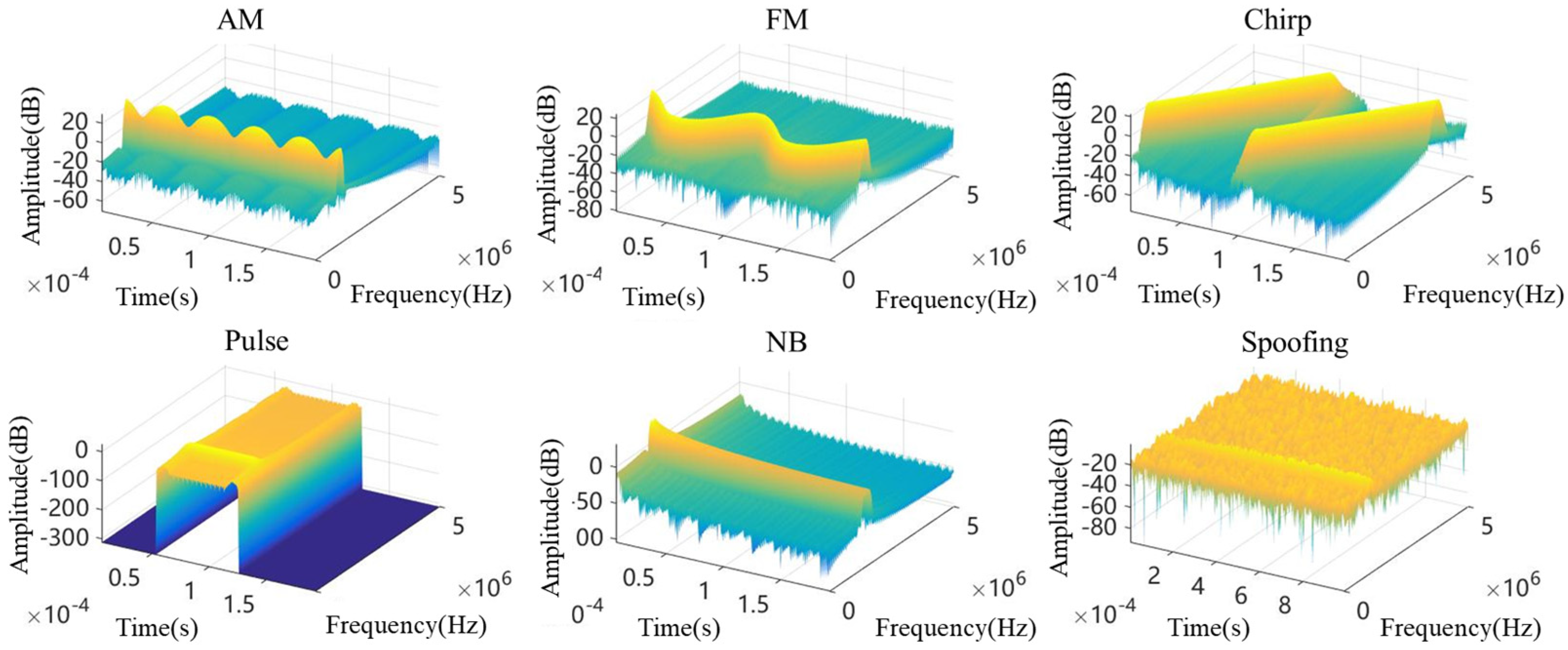
- Amplitude modulation (AM) jamming: As a subclass of continuous wave (CW) interference, AM jamming can be categorized into single-tone and multi-tone modulation types. Its defining characteristic lies in the carrier amplitude being modulated by a low-frequency signal. The interference at the -th sampling point can be expressed as [20]In this expression, denotes the number of amplitude-modulated tones. is the interference gain factor derived from the jamming signal ratio (JSR), representing the power ratio between the interference and the GNSS signal. denotes the channel coefficient vector of the suppressive interference link, and represents the convolution operator, accounting for multipath fading effects within the interference channel. , , and represent the amplitude, frequency, and phase of the -th AM interference component, respectively.
- (2)
- Frequency modulation (FM) jamming: This type of interference features a time-varying carrier frequency, characterized by a large instantaneous bandwidth and low power spectral density. Such properties enable it to effectively evade adaptive filtering and frequency-domain notch filtering strategies at the receiver. It is defined as [20]denotes the number of multi-tone carriers, is the frequency of the -th jamming component, and is the modulation index of the -th carrier.
- (3)
- Chirp jamming: Its instantaneous frequency periodically sweeps over a predefined frequency band within a short time interval and resets at the end of each cycle. Common forms include linear chirp jamming and sinusoidally modulated chirp jamming, defined as follows [20]:is the initial sweep frequency, and define the lower and upper bounds of the sweep bandwidth, respectively, is the time taken to sweep from to , is a random variable used to determine the sweep direction, and is the initial phase of the chirp jamming signal.
- (4)
- Narrowband jamming: This refers to the injection of narrowband interference components with power significantly higher than the useful GNSS signal within the main frequency band. Its bandwidth is typically narrower than the main lobe bandwidth of the GNSS signal. The spectral expression is given by [20]Here, , , and represent the amplitude, center frequency, and bandwidth of the narrowband jamming signal, respectively. By passing a stationary random process through a band-pass filter, the time-domain expression of the interference, , is obtained. Its convolution with the pseudocode sequence of the navigation signal, , is given by .
- (5)
- Pulse jamming: This type of interference periodically generates multiple pulses within a fixed repetition interval, each with a certain duty cycle. It is characterized by short duration, significant spectral spreading, and high peak power. It is typically modeled as a series of Gaussian-shaped pulse pairs, expressed as [20]In this expression, represents the waveform of a single pulse, is the number of pulses per unit time, and , , and denote the amplitude, carrier frequency, and time delay parameter of the -th pulse, respectively.
2.2. Spoofing
- (1)
- Simple spoofing adopts a two-step strategy of “jamming first, then spoofing”. When a navigation terminal is already locked onto authentic satellite signals, it will maintain tracking as long as the code delay and Doppler shift of the spoofed signal fall outside the pull-in range of the tracking loop. Therefore, the attacker must first transmit high-power jamming signals to cause the receiver to lose lock. After maintaining the jamming for a certain period, the transmitter switches to broadcasting the spoofed signal. Once the terminal loses lock, it attempts reacquisition based on historical parameters and due to the power advantage of the spoofed signal, it locks onto it and includes it in the PVT solution. Thus, in single-interference-source scenarios, it can be assumed that suppression and spoofing interference, as well as different categories of suppression jamming signals, do not occur simultaneously.
- (2)
- Moderate-level spoofing achieves takeover without loss of lock by aligning the spoofed signal’s code phase and Doppler frequency with those of the authentic signal. The spoofing device first receives genuine satellite signals and estimates the relative position and velocity of the target receiver. It then generates spoofed signals with identical parameters and transmits them in an overlapping manner. As the spoofed signal gradually increases in power and introduces a slow code phase shift, the receiver’s tracking loop becomes dominated by the stronger spoofed signal, ultimately leading to takeover of the positioning solution. During this process, the receiver remains locked, making detection difficult and the spoofing highly covert.
- (3)
- Advanced-level spoofing extends moderate spoofing by introducing multiple transmitters. Each antenna independently simulates the signal of a specific satellite, collectively forming a spatial signal field that closely mimics real satellite geometry, thereby enhancing the resistance to multi-antenna spoofing detection techniques. However, due to the complexity of transmission synchronization, phase control, and environmental dynamics, practical implementation remains highly challenging, and engineering feasibility is currently low. As a result, this form of spoofing does not yet pose a significant real-world threat.
3. Proposed Jamming Suppression Method
3.1. Analysis of Performance Degradation Under a Unified Suppression Strategy
- (1)
- FDPB
- (2)
- TDPB
- (3)
- AFF
3.2. Directed Suppression Strategies with Known Interference Types
- (1)
- Upgrade condition: if , the suppression state escalates to the next level (Primary → Backup, or Backup → Conservative).
- (2)
- Downgrade condition: if already in a higher-level state and , the Backup state immediately downgrades to Primary, while the Conservative state downgrades after persisting for 60 ms.
- (3)
- All other cases: the current suppression state is maintained.
3.3. A Framework for Unknown Interference Open Set Detection and Conservative Suppression
- (1)
- Offline phase: class center and tail distribution modeling.
- (2)
- Online detection phase:
- (1)
- For the sample data block within the -th window, the covariance matrix is updated as
- (2)
- Decompose the updated covariance matrix as
- (3)
- The interference subspace dimension is estimated using the minimum description length (MDL) criterion:where .
- (4)
- Let the eigenvectors corresponding to the interference subspace be , and its orthogonal complement be . The projection matrix is constructed as
- (1)
- Let and the average power spectrum be . A frequency bin k is selected if it satisfiesRecord the spectral peak as , where is the threshold for peak detection in the spectrum.
- (2)
- For each peak frequency, construct a pair of fixed-bandwidth poles as . All notch filters are cascaded to form the overall transfer function
- (3)
- The time-domain filtered output is given by
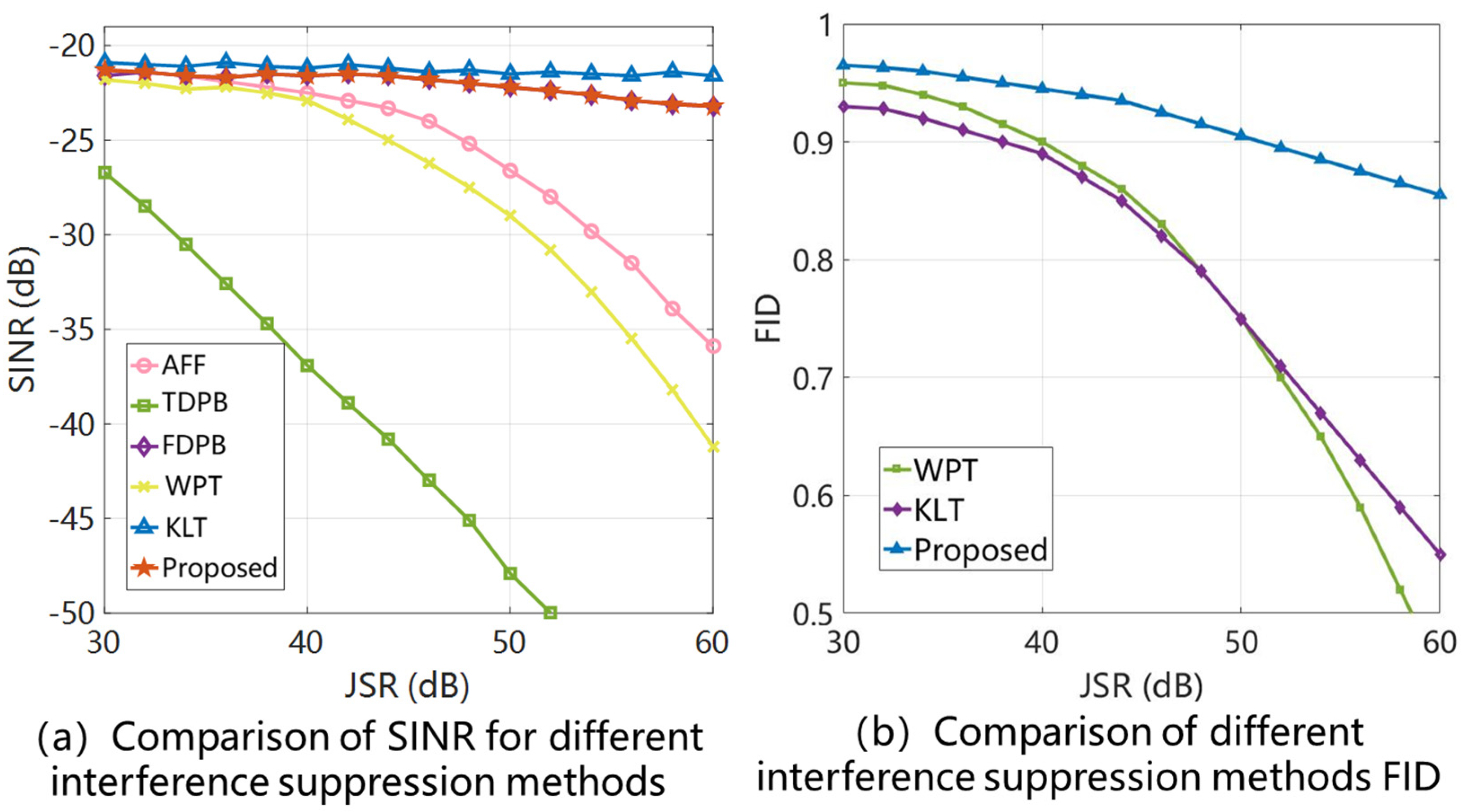
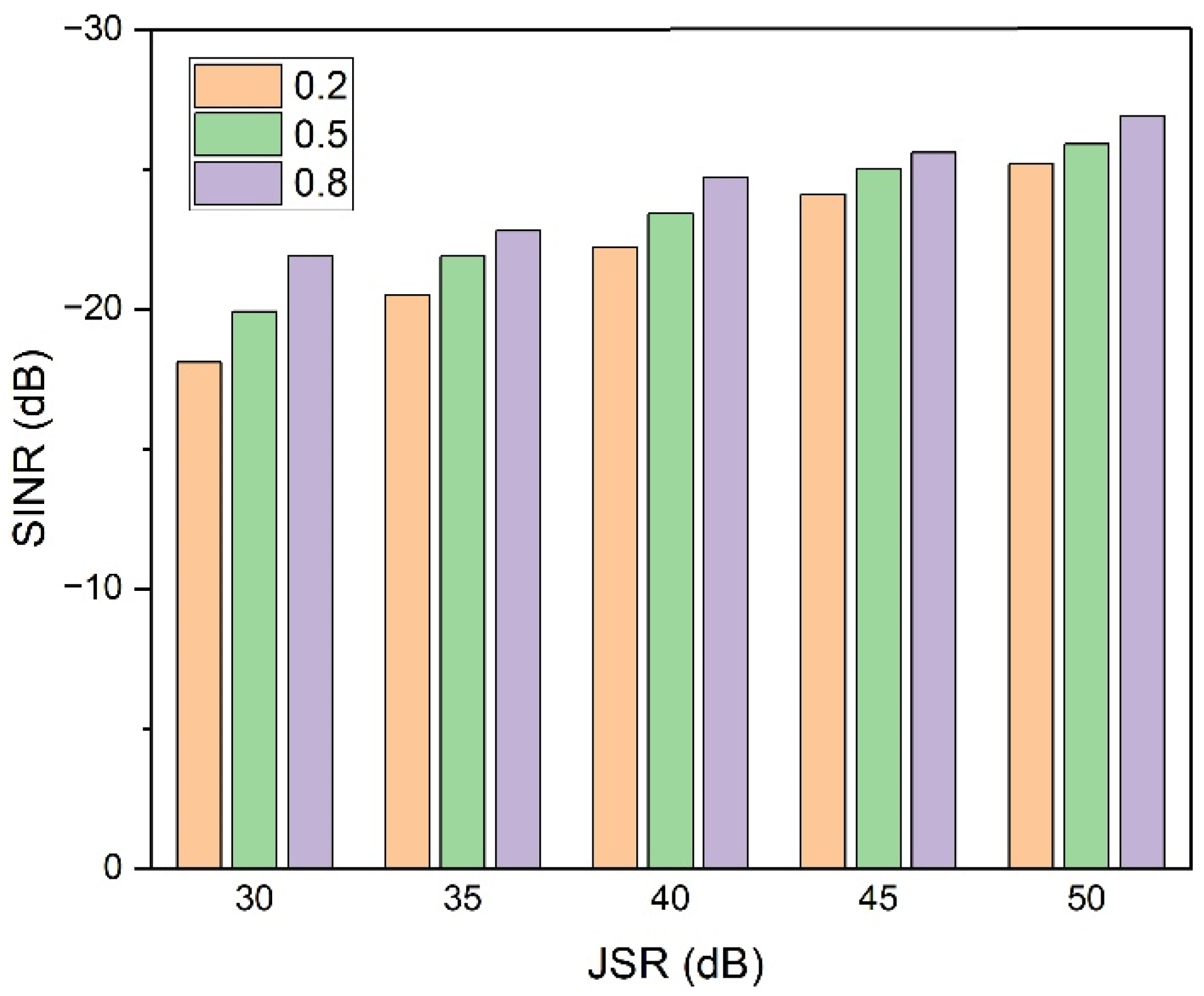
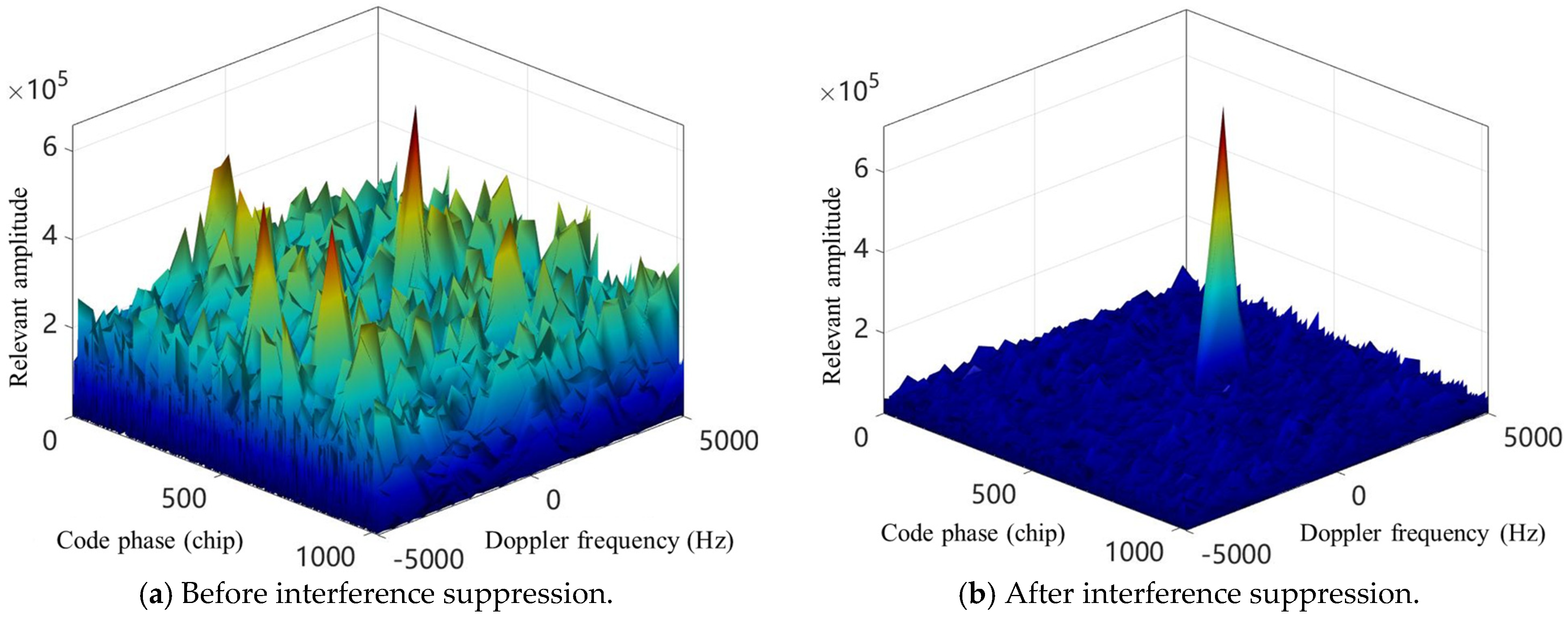
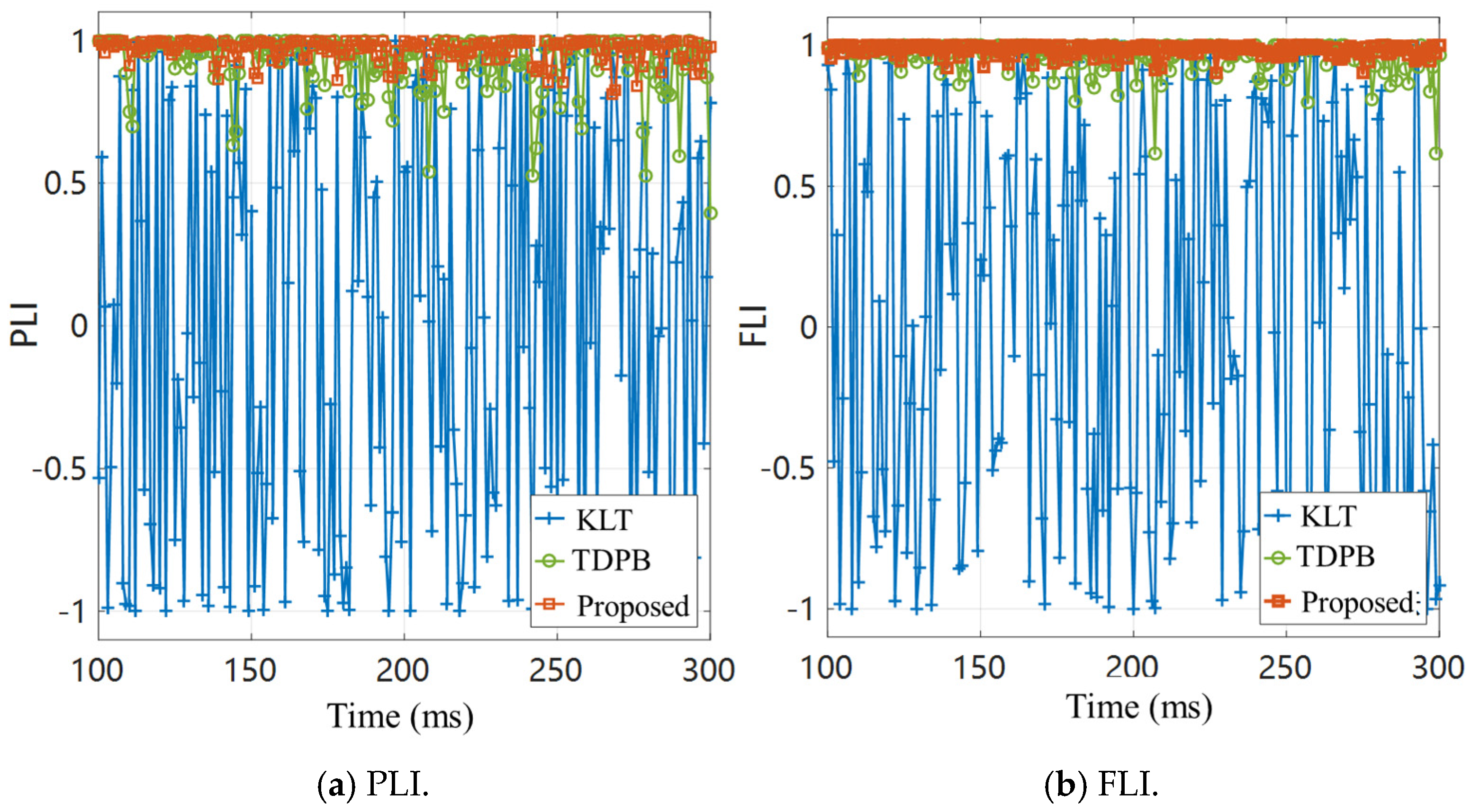
4. Results
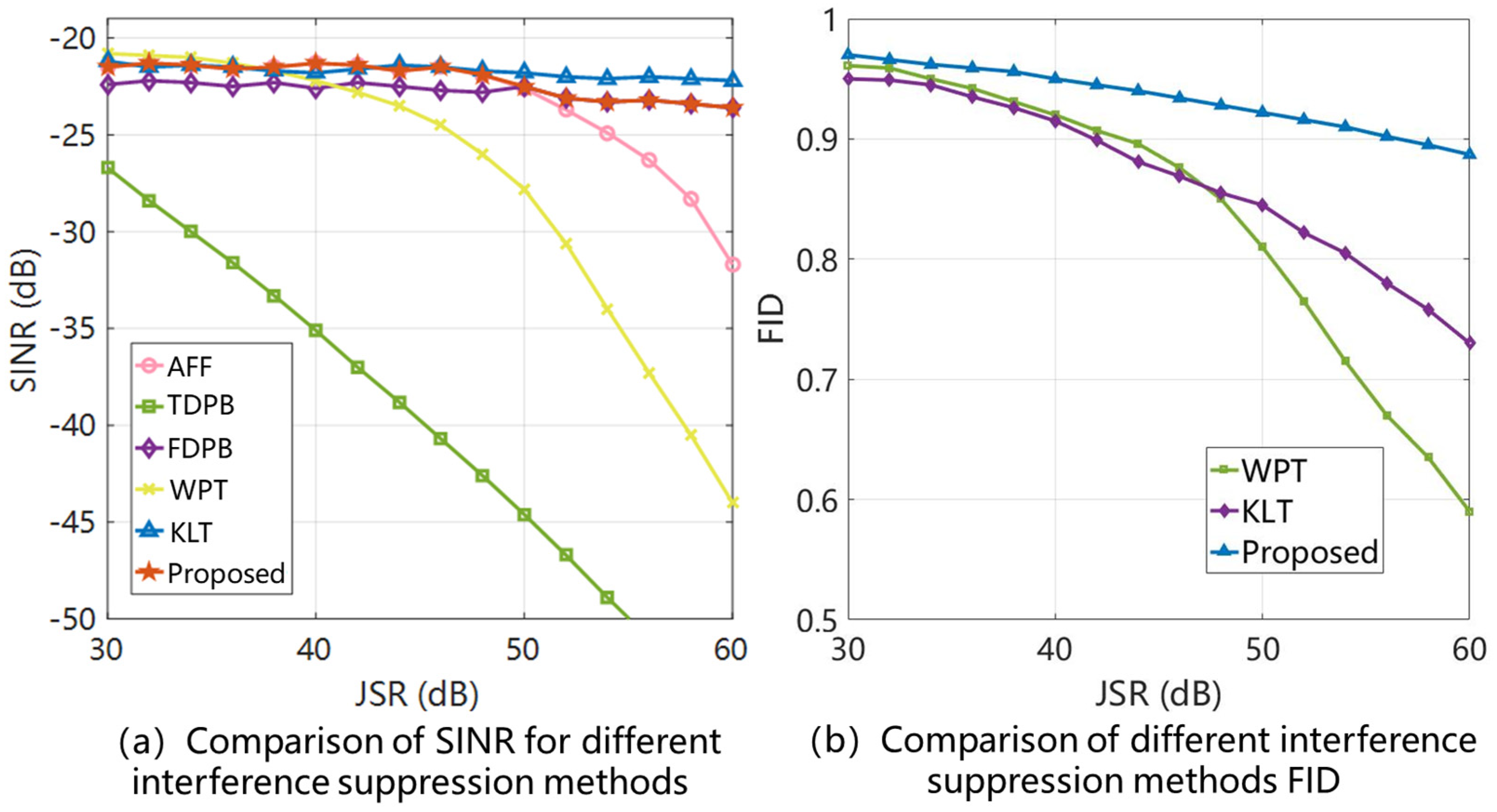
- (1)
- SINR: used to assess the steady-state performance after interference suppression;
- (2)
- FID: measures the degree to which the model preserves GNSS signal integrity.
- (3)
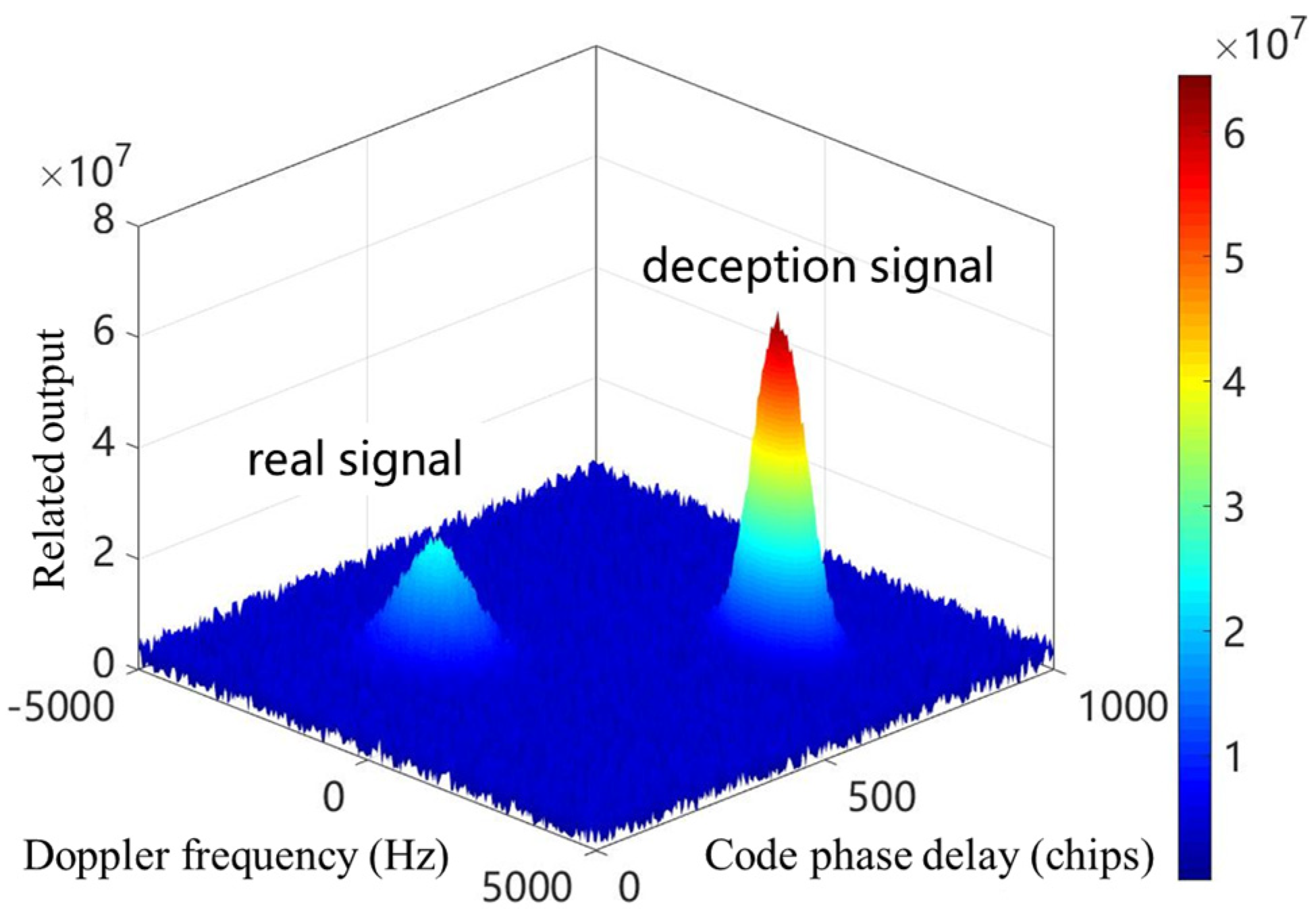
- CAF: employs the cross-ambiguity function to evaluate signal acquisition capability.
5. Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ren, B.; Chen, F.; Ni, S.; Han, C.; Lu, Z.; Han, S. Performance analysis of repeater spoofing suppression based on GNSS multi-beam receiver. Front. Phys. 2022, 10, 970132. [Google Scholar] [CrossRef]
- Yang, L.; Zhu, J.; Fu, Y.; Yu, Y. Integrity Monitoring for GNSS Precision Positioning. In Positioning and Navigation Using Machine Learning Methods; Springer: Berlin/Heidelberg, Germany, 2024; pp. 59–75. [Google Scholar]
- Chen, F. GNSS Antenna Array Receiver Interference Suppression and Measurement Deviation Compensation Technology; National University of Defense Technology: Changsha, China, 2017. [Google Scholar]
- Huang, S.; Guo, K.; Wang, Z.; Zhu, Y.; Tang, H.; Wang, Y. A dme interference signal identification and mitigation approach based on gaussian mixture model used for bds b2a receivers. In Proceedings of the 2023 IEEE/AIAA 42nd Digital Avionics Systems Conference (DASC), Barcelona, Spain, 1–5 October 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1–6. [Google Scholar]
- Ni, S.; Binbin, R.; Chen, F.; Lu, Z.; Wang, J.; Ma, P.; Sun, Y. GNSS spoofing suppression based on multi-satellite and multi-channel array processing. Front. Phys. 2022, 10, 905918. [Google Scholar] [CrossRef]
- Gioia, C. GNSS Navigation in Difficult Environments: Hybridization and Reliability. Ph.D. Thesis, University Parthenope of Naples, Naples, Italy, 2014. [Google Scholar]
- Ma, X.; Han, C.; Jin, R.; Wang, D.; Bai, P.; Zhen, W. Study on gnss spoofing interference detection method in urban multipath environment based on cnn and clustering model. In Proceedings of the 2023 Cross Strait Radio Science and Wireless Technology Conference (CSRSWTC), Guilin, China, 10–13 November 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1–3. [Google Scholar]
- Gioia, C.; Borio, D. A statistical characterization of the Galileo-to-GPS inter-system bias. J. Geod. 2016, 90, 1279–1291. [Google Scholar] [CrossRef]
- Borio, D.; Camoriano, L.; Lo Presti, L. Two-pole and multipole notch filters: A computationally effective solution for GNSS interference detection and mitigation. IEEE Syst. J. 2008, 2, 38–47. [Google Scholar] [CrossRef]
- Lineswala, P.L.; Shah, S.N. Performance analysis of different interference detection techniques for navigation with Indian constellation. IET Radar Sonar Navig. 2019, 13, 1207–1213. [Google Scholar] [CrossRef]
- Borio, D.; Gioia, C. Robust interference mitigation: A measurement and position domain assessment. In Proceedings of the 2020 International Technical Meeting of the Institute of Navigation, San Diego, CA, USA, 21–24 January 2020; pp. 274–288. [Google Scholar]
- Musumeci, L.; Dovis, F. Use of the wavelet transform for interference detection and mitigation in global navigation satellite systems. Int. J. Navig. Obs. 2014, 2014, 262186. [Google Scholar] [CrossRef]
- Park, K.; Lee, D.; Seo, J. Dual-polarized GPS antenna array algorithm to adaptively mitigate a large number of interference signals. Aerosp. Sci. Technol. 2018, 78, 387–396. [Google Scholar] [CrossRef]
- Kornblith, S.; Shlens, J.; Le, Q.V. Do better imagenet models transfer better? In Proceedings of the IEEE Computer Society Conference on Computer Vision and Pattern Recognition, Long Beach, CA, USA, 15–20 June 2019; pp. 2656–2666. [Google Scholar]
- Borio, D. Robust signal processing for GNSS. In Proceedings of the 2017 European Navigation Conference (ENC), Lousanne, Switzerland, 9–12 May 2017; pp. 150–158. [Google Scholar]
- Honig, M.L.; Poor, H.V. Adaptive interference suppression. In Wireless Communications: Signal Processing Perspectives; Prentice-Hall: Upper Saddle River, NJ, USA, 1998; pp. 64–128. [Google Scholar]
- Zhang, L.; Zhao, H.; Sun, C.; Bai, L.; Feng, W. Enhanced GNSS spoofing detector via multiple-epoch inertial navigation sensor prediction in a tightly-coupled system. IEEE Sens. J. 2022, 22, 8633–8647. [Google Scholar] [CrossRef]
- Hu, Y.; Bian, S.; Li, B.; Zhou, L. A novel array-based spoofing and jamming suppression method for GNSS receiver. IEEE Sens. J. 2018, 18, 2952–2958. [Google Scholar] [CrossRef]
- Park, K.; Seo, J. Single-Antenna-Based GPS Antijamming Method Exploiting Polarization Diversity. IEEE Trans. Aerosp. Electron. Syst. 2021, 57, 919–934. [Google Scholar] [CrossRef]
- Zhang, Z.; Deng, Z.; Liu, J.; Ding, Z.; Liu, B. LJCD-Net: Cross-Domain Jamming Generalization Diagnostic Network Based on Deep Adversarial Transfer. Sensors 2024, 24, 3266. [Google Scholar] [CrossRef] [PubMed]
- Borio, D.; Gioia, C. GNSS interference mitigation: A measurement and position domain assessment. Navig. J. Inst. Navig. 2021, 68, 93–114. [Google Scholar] [CrossRef]
- Song, J.; Lu, Z.; Xiao, Z.; Li, B.; Sun, G. Optimal order of time domain adaptive filter for anti jamming navigation receiver. Remote Sens. 2021, 14, 48. [Google Scholar] [CrossRef]

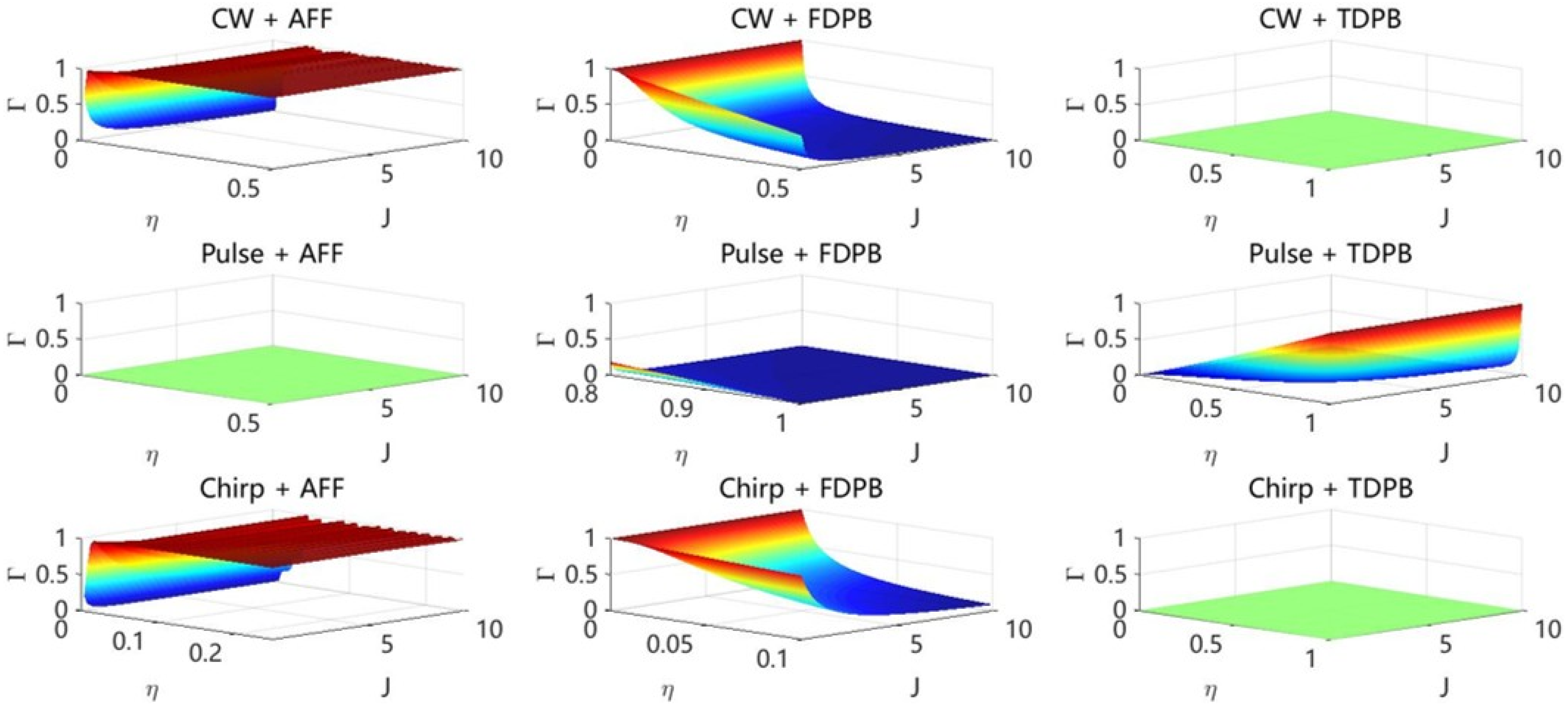




| Jamming | Algorithm | ||
|---|---|---|---|
| NB | AFF | ||
| FDPB | |||
| TDPB | |||
| Pulse | AFF | ||
| FDPB | |||
| TDPB | |||
| Chirp | AFF | ||
| FDPB | |||
| TDPB | |||
| Jamming | Preferred | Alternative | Estimated Parameters | Estimation Method |
|---|---|---|---|---|
| AM | AFF | FDPB | FFT + Hilbert | |
| FM | FDPB | FDPB | FFT + PLL | |
| Chirp | FDPB | AFF | STFT + Hough | |
| NB | AFF | FDPB | FFT single-peak | |
| Pulse | TDPB | FDPB | Time-domain CFAR |
| Jamming | Parameter Setting |
|---|---|
| AM | MHz, |
| FM | MHz, |
| Chirp | MHz, MHz, ms, |
| NB | MHz, kHz |
| Pulse | , |
| No. | Parameter | Value | No. | Parameter | Value |
|---|---|---|---|---|---|
| 1 | Signal Type | GPS L1 C/A | 7 | Frequency Search Step Size | 300 Hz |
| 2 | SNR | −20 dB | 8 | Tracking Duration | 1 s |
| 3 | JNR | 30 dB | 9 | DLL Loop Bandwidth | 1 Hz |
| 4 | Doppler Frequency | 1500 Hz | 10 | PLL Loop Bandwidth | 10 Hz |
| 5 | Code Phase Offset | 479 chips | 11 | FLL Loop Bandwidth | 20 Hz |
| 6 | Code Phase Search Step Size | 0.5 chip | 12 | Relevant Interval | 1 s |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Deng, Z.; Zhang, Z.; Gao, X.; Liu, P. Differentiated GNSS Baseband Jamming Suppression Method Based on Classification Decision Information. Appl. Sci. 2025, 15, 7131. https://doi.org/10.3390/app15137131
Deng Z, Zhang Z, Gao X, Liu P. Differentiated GNSS Baseband Jamming Suppression Method Based on Classification Decision Information. Applied Sciences. 2025; 15(13):7131. https://doi.org/10.3390/app15137131
Chicago/Turabian StyleDeng, Zhongliang, Zhichao Zhang, Xiangchuan Gao, and Peijia Liu. 2025. "Differentiated GNSS Baseband Jamming Suppression Method Based on Classification Decision Information" Applied Sciences 15, no. 13: 7131. https://doi.org/10.3390/app15137131
APA StyleDeng, Z., Zhang, Z., Gao, X., & Liu, P. (2025). Differentiated GNSS Baseband Jamming Suppression Method Based on Classification Decision Information. Applied Sciences, 15(13), 7131. https://doi.org/10.3390/app15137131






