Evaluating Cybersecurity Risks of Bulgaria’s Energy Sector: Focus on PV and HVAC-R
Abstract
1. Introduction
2. Literature Review
2.1. Real-World Cyber-Attack Examples
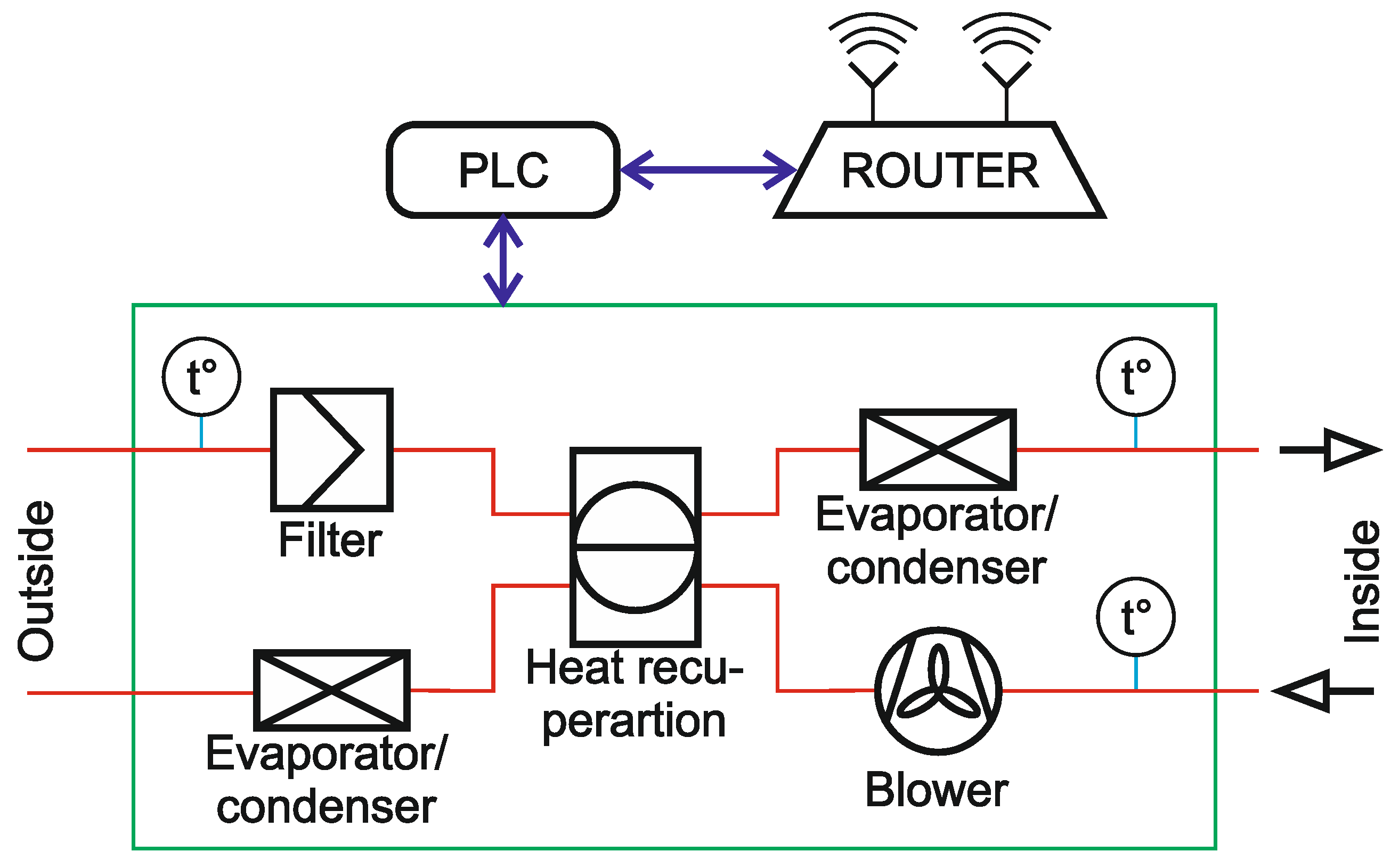
2.2. Cybersecurity of Heating, Ventilation, Air Conditioning, and Refrigeration Systems
2.3. Cybersecurity Regulations Concerning Electric Power Systems
- IEC 61850 for intelligent electronic devices in electrical substations [57].
- Regulation 2024/2847 on horizontal cybersecurity requirements for products with digital elements known as the Cyber Resilience Act (CRA) [58].
- Directive 2022/2555 on measures for a high common level of cybersecurity across the EU known as the Network and Information Security Directive (NIS 2) [59].
- The IEC 62443 series of standards on cybersecurity for industrial and automation systems [60].
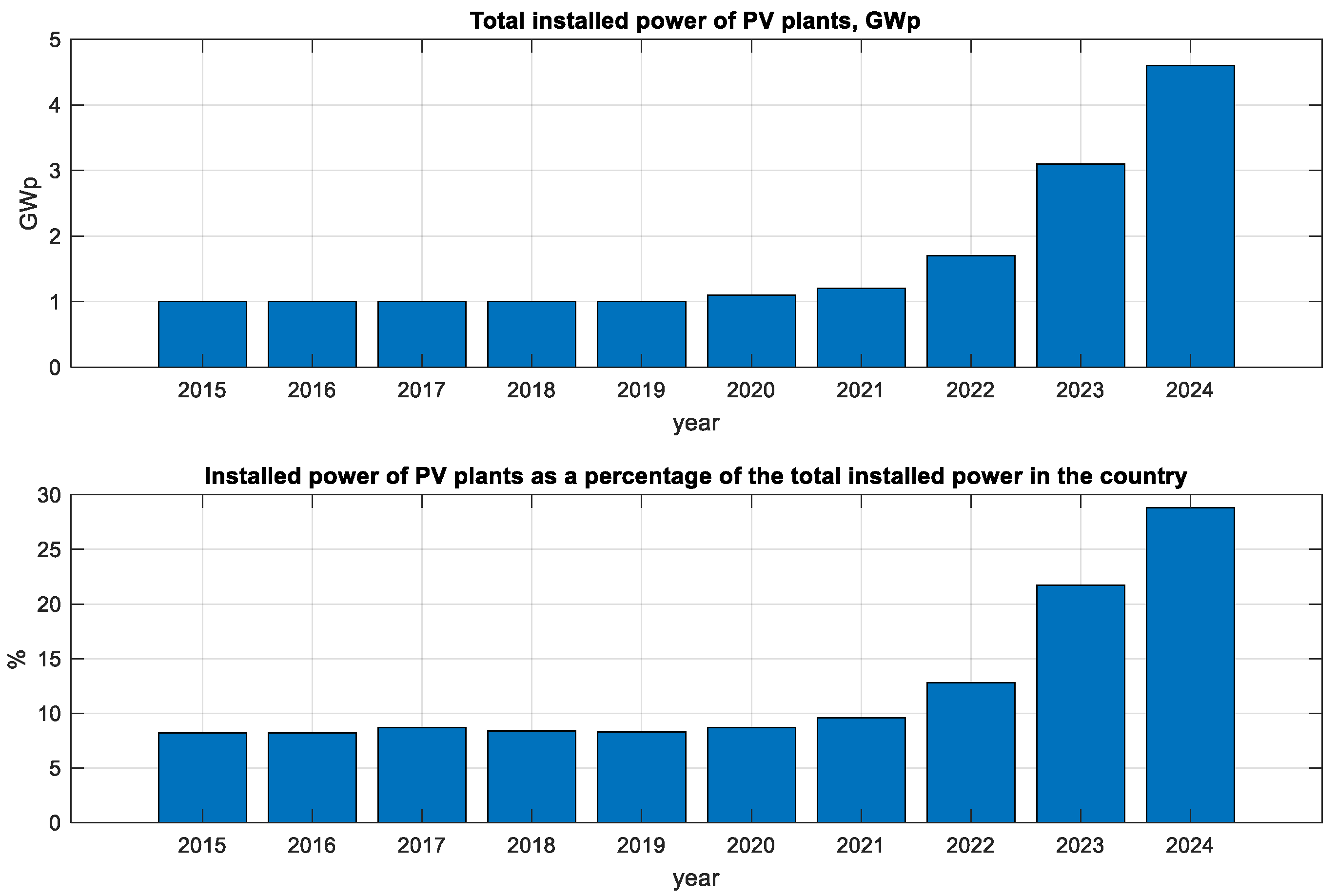
3. The Bulgarian Energy System—Current State, Issues, Trends, and Prospects
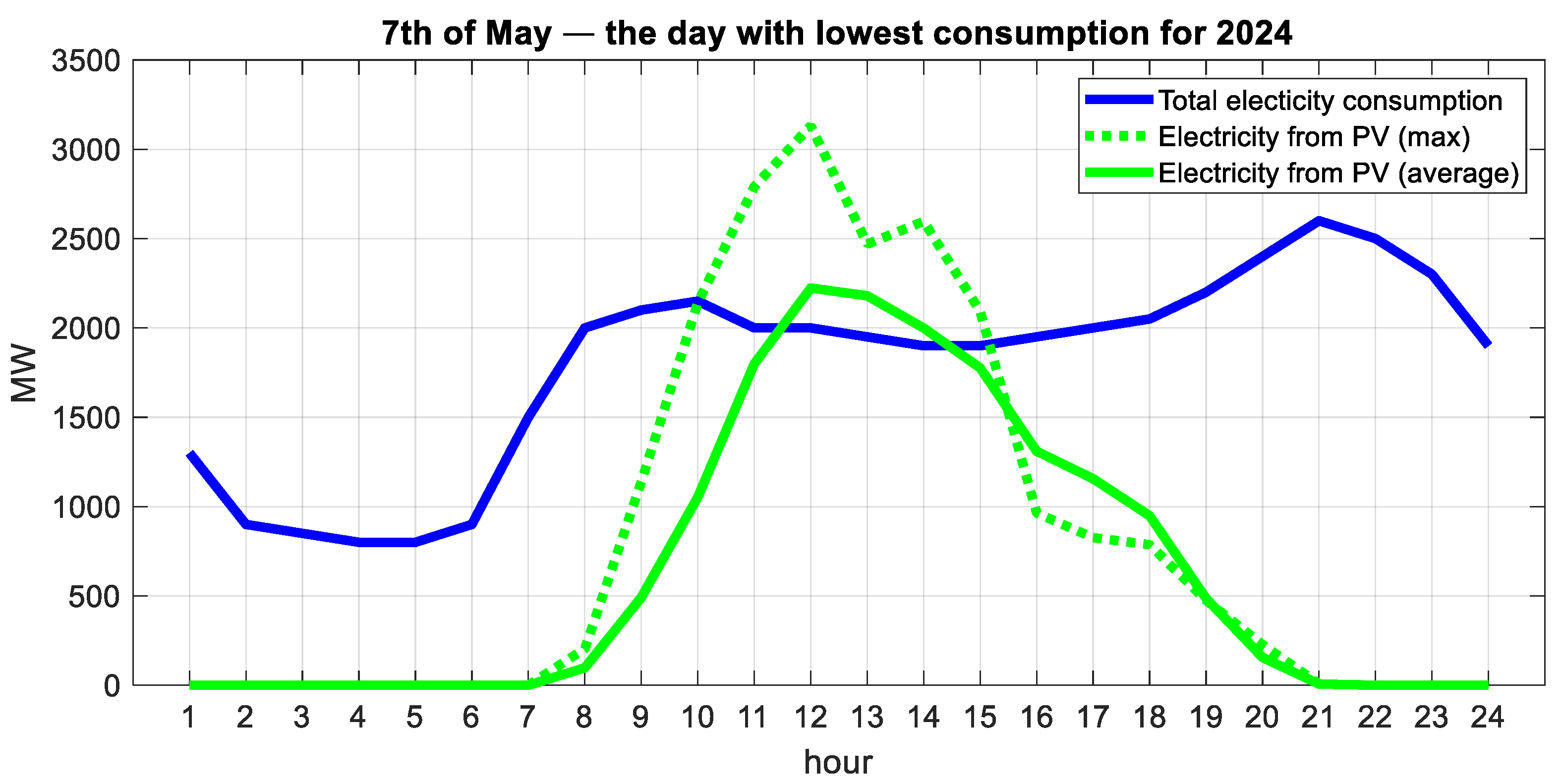
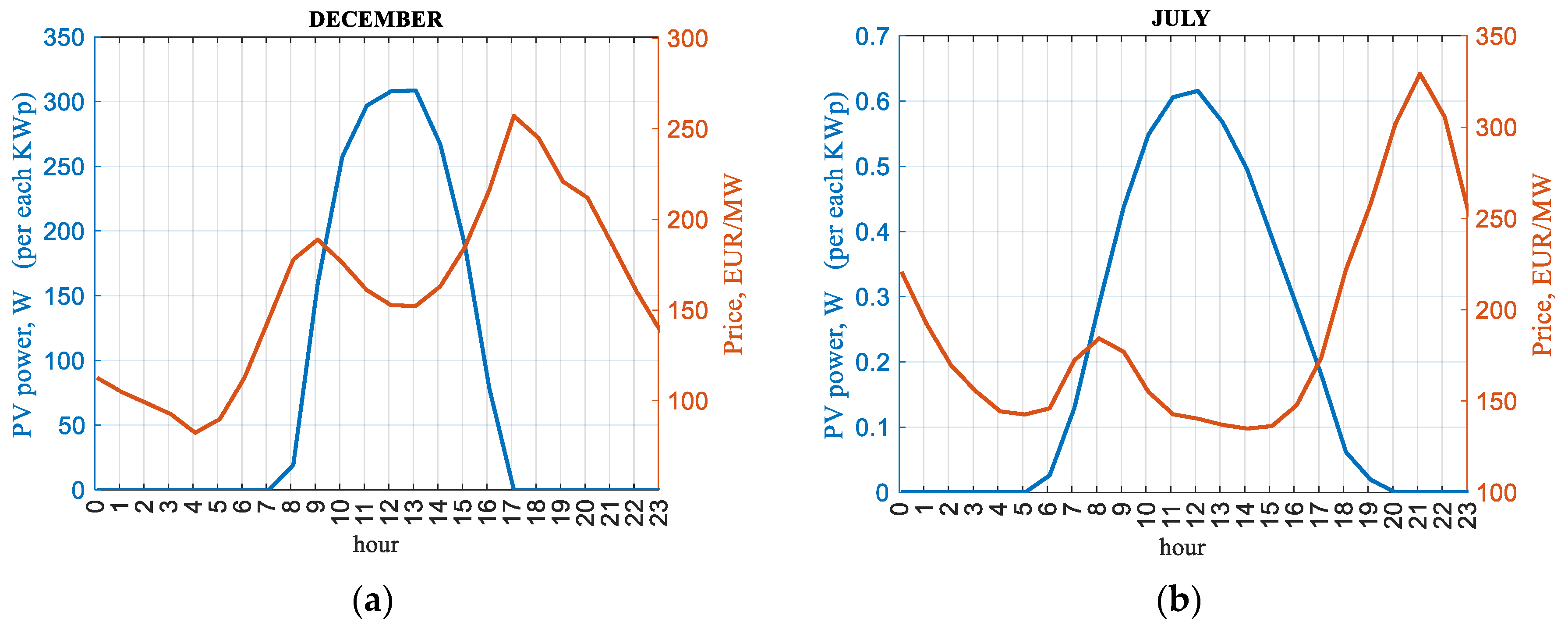
3.1. Energy Balance
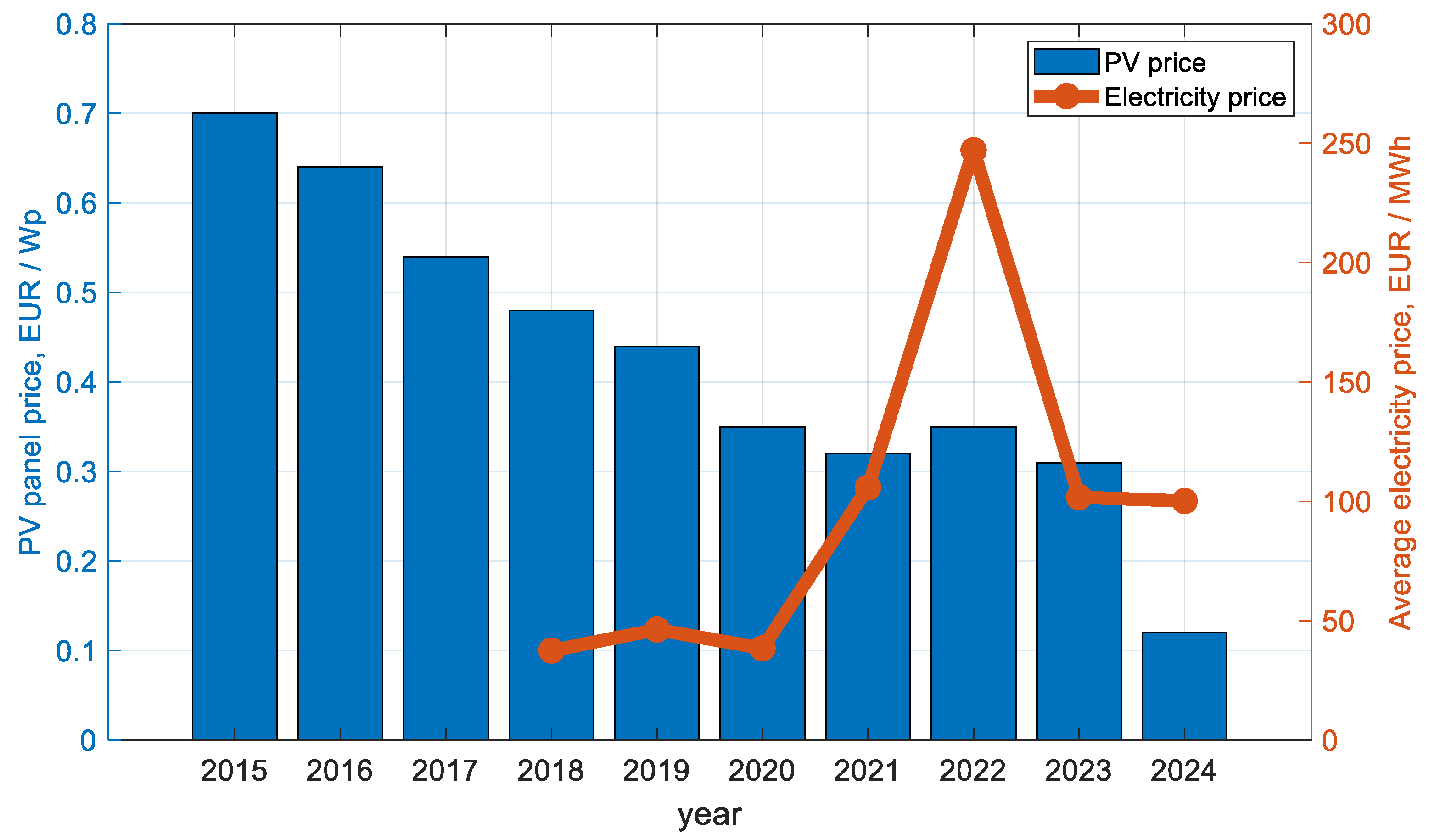
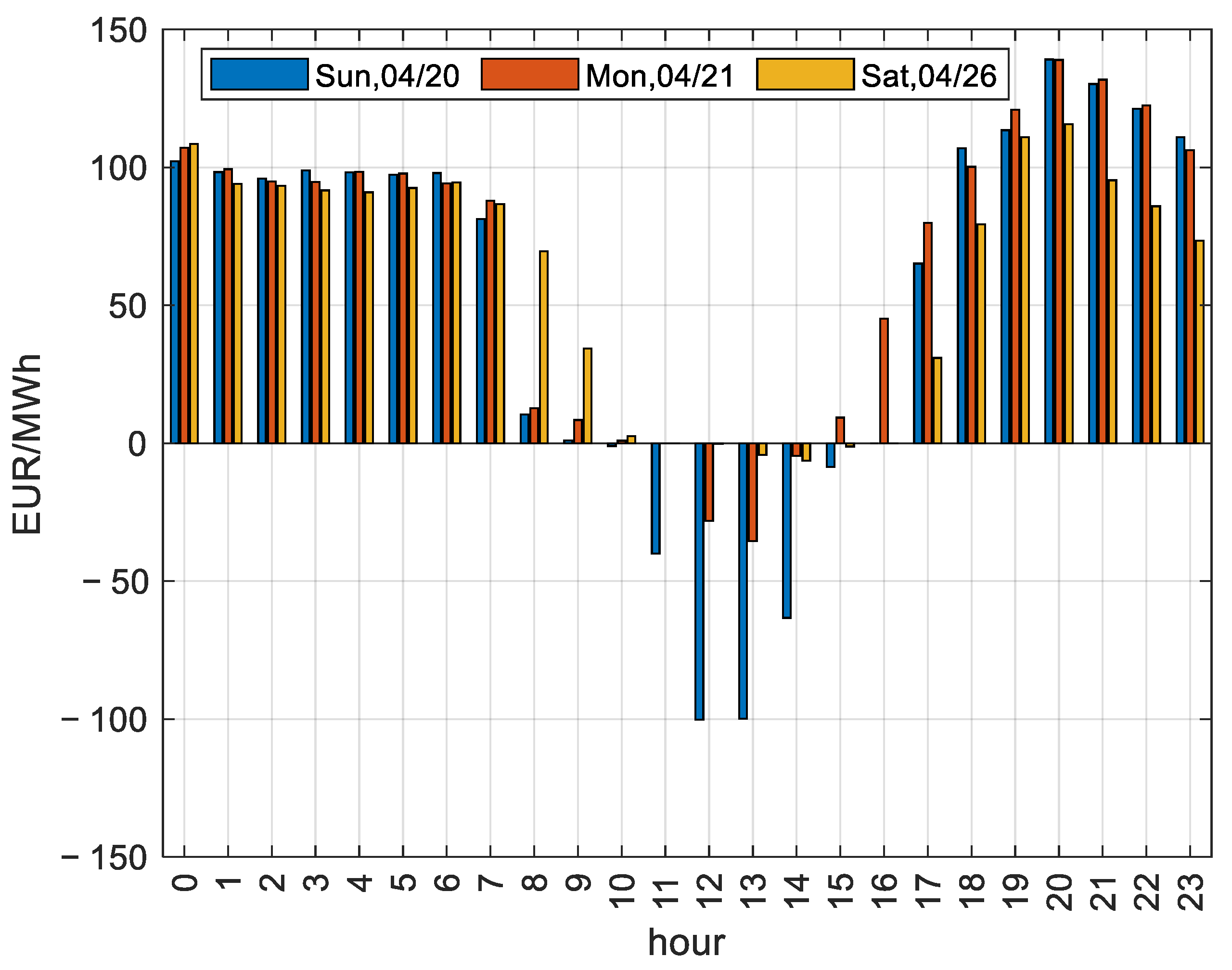
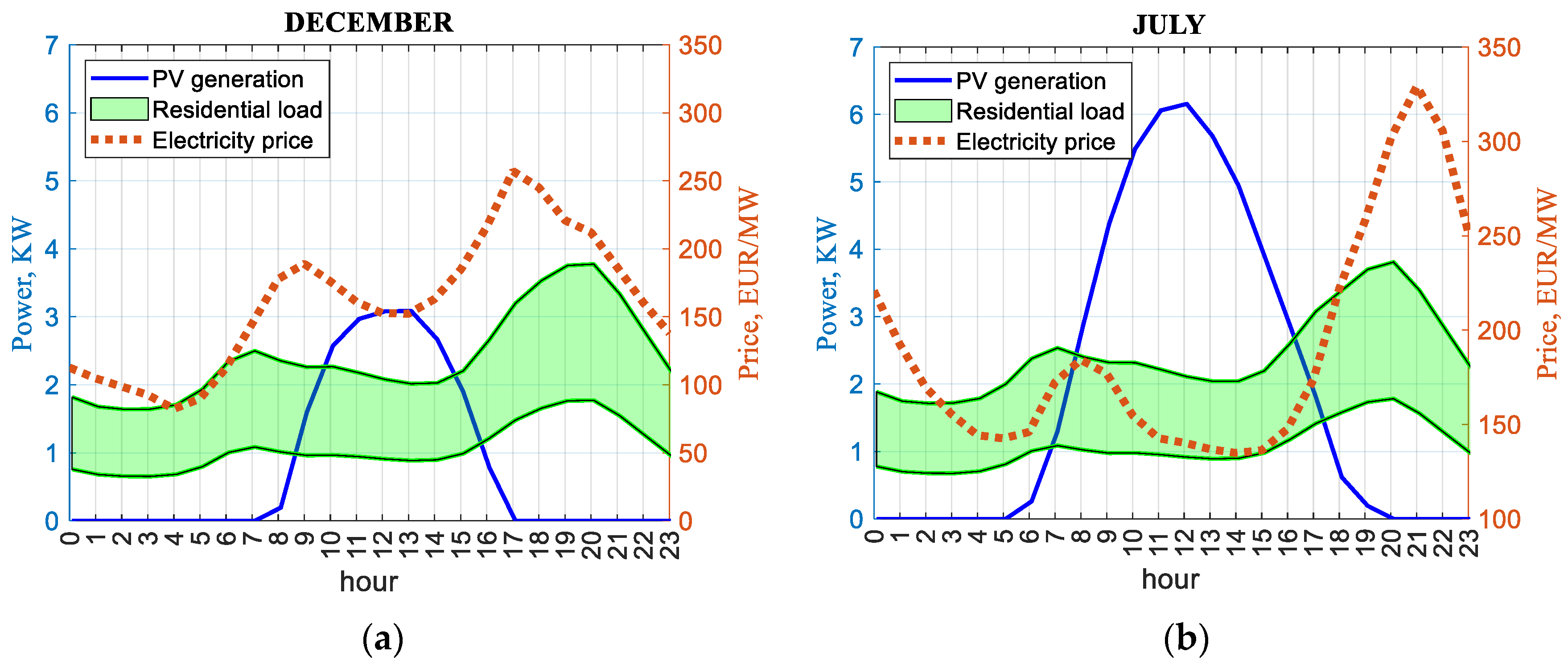
3.2. Price Effect
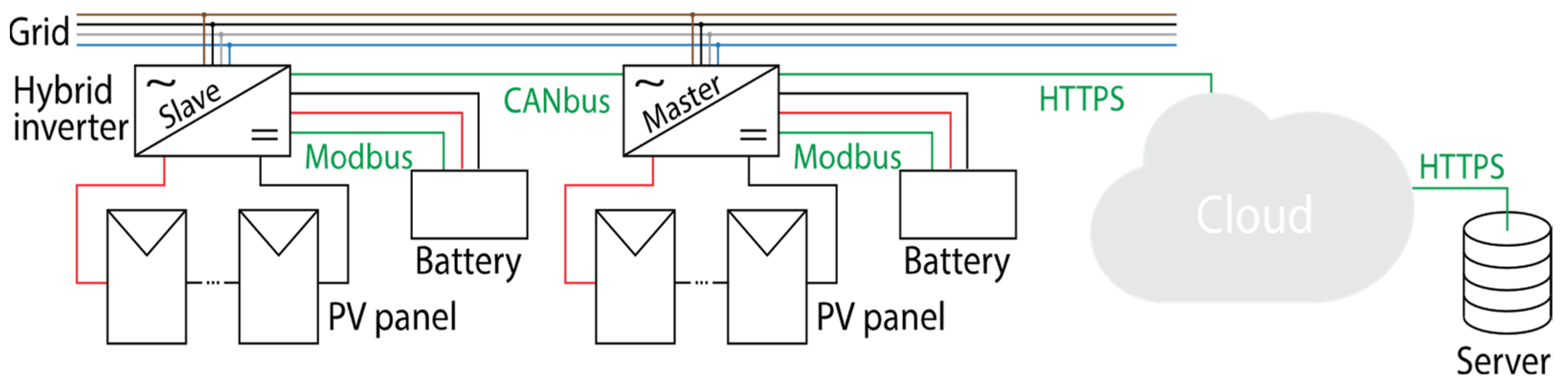
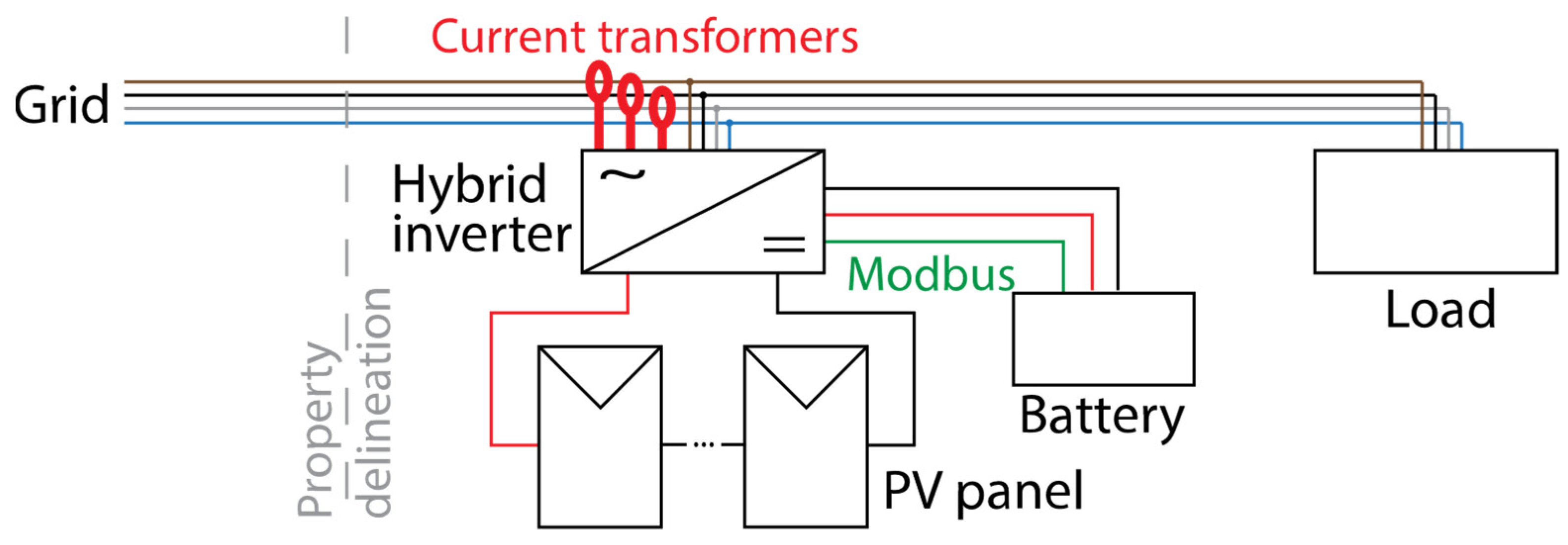
4. PV Plants with Energy Storage Capability
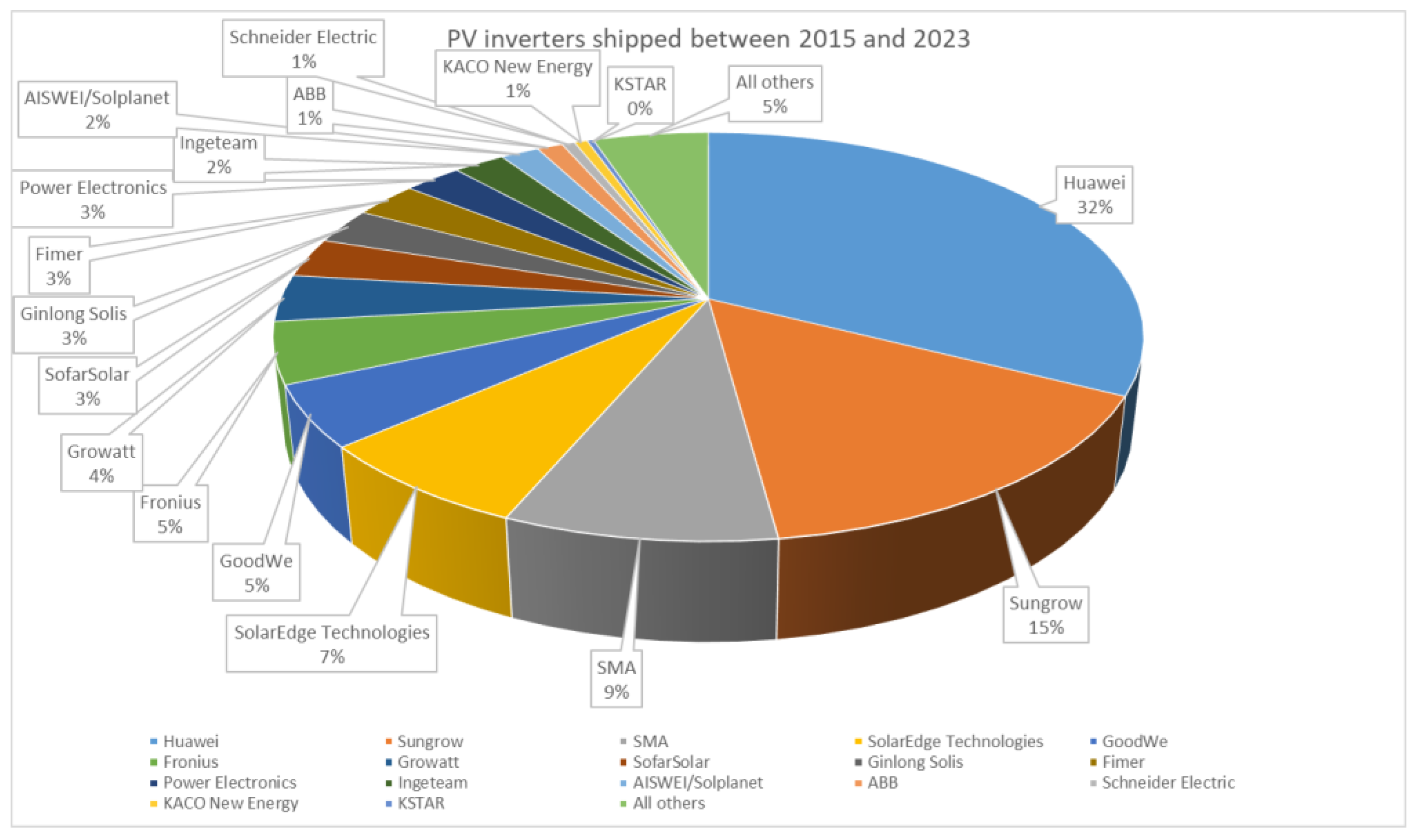
Hybrid Inverters and Security Concerns
- Huawei;
- Deye;
- GoodWe;
- Solis;
- Solax;
- Growatt;
- Sungrow;
- Afore;
- EASun;
- TBB Power.
- Attempts to destabilize the entire energy system with subsequent blackout. In the event of a simultaneous loss of large generating capacity, dangerous regimes may occur. It is obvious that after the events in Spain [79] and North Macedonia [80], where the energy system collapsed, system sustainability must be further studied. This is the most serious potential threat.
- Attempts to damage batteries. Batteries can be deactivated, which is associated with very large economic losses, but potentially there are also regimes in which they can be ignited or deflagrated. The mandatory use of BMSs does indeed greatly reduce the risk but does not eliminate it completely. A real event that damaged the batteries is described later.
- Attempts to cause economic losses. Here, the scenarios include an attack against a specific prosumer and also against a large number of inverters. In both cases, it is possible not only to turn off the inverters but to simulate frequent failures, which would completely compromise the reliability of the plant and at the same time make it difficult to detect the attack.
5. Risk Assessment of PV Plants with Hybrid Inverters
Threat Scenarios
6. Enhancing the Cybersecurity of Hybrid Inverters
- Easy to implement and familiar to engineers in practice;
- Provides both operational control and isolation from the manufacturer’s cloud;
- Easy modification of the control and direct entry into the emerging need for centralized dispatching control even of low-power generators.
- Increased costs;
- Complicated system.
7. Small-Scale Survey Among Installers and PV Owners
7.1. Survey Goal
- Level of cyberthreat awareness;
- The frequency of encountered problems that are related to updates or remote control;
- Willingness to adopt the proposed measures;
- Attitude towards future regulations.
7.2. Survey’s Results
7.3. Discussion
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
List of Abbreviations
| Abbreviation | Description |
| BMS | Battery management system |
| CPS | Cyber-physical system |
| CRA | Cyber Resilience Act |
| DDoS | Distributed denial of service |
| DG | Distributed generation |
| DIA | Data integrity attack |
| DoS | Denial of service |
| FDIA | False data injection attack |
| HVAC-R | Heating, ventilation, air conditioning, and refrigeration |
| IBEX | Independent Bulgarian Energy Exchange |
| LFP | Lithium-ion iron phosphate |
| MITM | Man-in-the-middle |
| NCCS | Network Code on Cybersecurity |
| NIS | Network and Information Security |
| PLC | Programmable logic controller |
| PV | Photovoltaic |
| PVGIS | Photovoltaic Geographical Information System |
| RESs | Renewable energy sources |
| SCADA | Supervisory control and data acquisition |
References
- Su, Q.; Wang, H.; Sun, C.; Li, B.; Li, J. Cyber-attacks against cyber-physical power systems security: State estimation, attacks reconstruction and defense strategy. Appl. Math. Comput. 2022, 413, 126639. [Google Scholar] [CrossRef]
- Harrou, F.; Taghezouit, B.; Bouyeddou, B.; Sun, Y. Cybersecurity of photovoltaic systems: Challenges, threats, and mitigation strategies: A short survey. Front. Energy Res. 2023, 11, 1274451. [Google Scholar] [CrossRef]
- E&ENEWS; Sobczak, B. ‘Cyber Event’ Disrupted U.S. Grid Networks—DOE. 2019. Available online: https://www.eenews.net/articles/cyber-event-disrupted-u-s-grid-networks-doe/ (accessed on 1 April 2025).
- Ye, J.; Giani, A.; Elasser, A.; Mazumder, S.K.; Farnell, C.; Mantooth, H.A. A Review of Cyber–Physical Security for Photovoltaic Systems. IEEE J. Emerg. Sel. Top. Power Electron. 2022, 10, 4879–4901. [Google Scholar] [CrossRef]
- Ahmed, C.M.; Palleti, V.R.; Mishra, V.K. A practical physical watermarking approach to detect replay attacks in a CPS. J. Process Control 2022, 116, 136–146. [Google Scholar] [CrossRef]
- Zhao, A.P.; Li, S.; Gu, C.; Yan, X.; Hu, P.J.-H.; Wang, Z.; Xie, D.; Cao, Z.; Chen, X.; Wu, C.; et al. Cyber Vulnerabilities of Energy Systems. IEEE J. Emerg. Sel. Top. Ind. Electron. 2024, 5, 1455–1469. [Google Scholar] [CrossRef]
- Yang, K.; Wang, H.; Wang, H.; Sun, L. An effective intrusion-resilient mechanism for programmable logic controllers against data tampering attacks. Comput. Ind. 2022, 138, 103613. [Google Scholar] [CrossRef]
- Kang, B.; Maynard, P.; McLaughlin, K.; Sezer, S.; Andrén, F.; Seitl, C.; Kupzog, F.; Strasser, T. Investigating Cyber-Physical Attacks against IEC 61850 Photovoltaic Inverter Installations. In Proceedings of the IEEE 20th Conference on Emerging Technologies & Factory Automation (ETFA), Luxembourg, 8–11 September 2015; pp. 1–8. [Google Scholar] [CrossRef]
- Ghiasi, M.; Niknam, T.; Wang, Z.; Mehrandezh, M.; Dehghani, M.; Ghadimi, N. A comprehensive review of cyber-attacks and defense mechanisms for improving security in smart grid energy systems: Past, present and future. Electr. Power Syst. Res. 2023, 215 Pt A, 108975. [Google Scholar] [CrossRef]
- Benkraouda, H.; Chakkantakath, M.A.; Keliris, A.; Maniatakos, M. SNIFU: Secure Network Interception for Firmware Updates in legacy PLCs. In Proceedings of the IEEE 38th VLSI Test Symposium (VTS), San Diego, CA, USA, 5–8 April 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Sahoo, S.; Dragičević, T.; Blaabjerg, F. Cyber Security in Control of Grid-Tied Power Electronic Converters—Challenges and Vulnerabilities. IEEE J. Emerg. Sel. Top. Power Electron. 2021, 9, 5326–5340. [Google Scholar] [CrossRef]
- Riurean, S.; Fîță, N.-D.; Păsculescu, D.; Slușariuc, R. Securing Photovoltaic Systems as Critical Infrastructure. A Multi-Layered Assessment of Risk, Safety, and Cybersecurity. Sustainability 2025, 17, 4397. [Google Scholar] [CrossRef]
- Dedrick, J.; Perrin, K.A.; Sabaghian, E.; Wilcoxen, P.J. Assessing cyber attacks on local electricity markets using simulation analysis: Impacts and possible mitigations. Sustain. Energy Grids Netw. 2023, 34, 100993. [Google Scholar] [CrossRef]
- Li, F.; Xie, R.; Yang, B.; Guo, L.; Ma, P.; Shi, J. Detection and Identification of Cyber and Physical Attacks on Distribution Power Grids with PVs: An Online High-Dimensional Data-Driven Approach. IEEE J. Emerg. Sel. Top. Power Electron. 2022, 10, 1282–1291. [Google Scholar] [CrossRef] [PubMed]
- SMA Solar Technology AG. Public Cyber Security: Guidelines for a Secure System Communication; Technical Information; CyberSecurity-TI-en-20; SMA Solar Technology AG: Niestetal, Germany, 2025; Available online: https://files.sma.de/downloads/CyberSecurity-TI-en-20.pdf (accessed on 4 April 2025).
- Terneva, Z.; Nenova, M.; Terneva, V.; Vladimirov, I.; Nikolova, D. Cyberattack types—Methods and technics for protection of communication resources. In Proceedings of the 57th International Scientific Conference on Information, Communication and Energy Systems and Technologies (ICEST), Ohrid, North Macedonia, 16–18 June 2022; pp. 1–4. [Google Scholar] [CrossRef]
- Khan, R.; Maynard, P.; McLaughlin, K.; Laverty, D.; Sezer, S. Threat Analysis of BlackEnergy Malware for Synchrophasor based Real-time Control and Monitoring in Smart Grid. In Proceedings of the 4th International Symposium for ICS & SCADA Cyber Security Research (ICS-CSR), Belfast, UK, 23–25 August 2016. [Google Scholar] [CrossRef]
- Priyadarshini, I.; Kumar, R.; Sharma, R.; Singh, P.K.; Satapathy, S.C. Identifying cyber insecurities in trustworthy space and energy sector for smart grids. Comput. Electr. Eng. 2021, 93, 107204. [Google Scholar] [CrossRef]
- Sharabov, M.; Tsochev, G.; Gancheva, V.; Tasheva, A. Filtering and Detection of Real-Time Spam Mail Based on a Bayesian Approach in University Networks. Electronics 2024, 13, 374. [Google Scholar] [CrossRef]
- Symantec. Dragonfly: Cyberespionage Attacks Against Energy Suppliers, Security Response. 2014. Available online: https://docs.broadcom.com/doc/dragonfly_threat_against_western_energy_suppliers (accessed on 10 April 2025).
- Carter, C.; Onunkwo, I.; Cordeiro, P.; Johnson, J. Cyber Security Assessment of Distributed Energy Resources. In Proceedings of the IEEE 44th Photovoltaic Specialist Conference (PVSC), Washington, DC, USA, 25–30 June 2017; pp. 2135–2140. [Google Scholar] [CrossRef]
- Teymouri, A.; Mehrizi-Sani, A.; Liu, C.-C. Cyber Security Risk Assessment of Solar PV Units with Reactive Power Capability. In Proceedings of the IECON 2018—44th Annual Conference of the IEEE Industrial Electronics Society, Washington, DC, USA, 21–23 October 2018; pp. 2872–2877. [Google Scholar] [CrossRef]
- Tuyen, N.D.; Quan, N.S.; Linh, V.B.; Tuyen, V.V.; Fujita, G. A Comprehensive Review of Cybersecurity in Inverter-Based Smart Power System Amid the Boom of Renewable Energy. IEEE Access 2022, 10, 35846–35875. [Google Scholar] [CrossRef]
- Gao, R.; Yang, G.-H. Sampled-data distributed state estimation with multiple transmission channels under denial-of-service attacks. Appl. Math. Comput. 2022, 429, 127229. [Google Scholar] [CrossRef]
- Kulbacki, M.; Chaczko, Z.; Barton, S.; Wajs-Chaczko, P.; Nikodem, J.; Rozenblit, J.W.; Klempous, R.; Ito, A.; Kulbacki, M. A Review of the Weaponization of IoT: Security Threats and Countermeasures. In Proceedings of the IEEE 18th International Symposium on Applied Computational Intelligence and Informatics (SACI), Timisoara, Romania, 23–25 May 2024; pp. 000279–000284. [Google Scholar] [CrossRef]
- Nenova, M.; Atanasov, D.; Kassev, K.; Nenov, A. Intrusion Detection System Model Implementation against DDOS attacks. In Proceedings of the IEEE International Conference on Microwaves, Antennas, Communications and Electronic Systems (COMCAS), Tel-Aviv, Israel, 4–6 November 2019; pp. 1–4. [Google Scholar] [CrossRef]
- Hristov, M.; Nenova, M.; Iliev, G.; Avresky, D. Integration of Splunk Enterprise SIEM for DDoS Attack Detection in IoT. In Proceedings of the IEEE 20th International Symposium on Network Computing and Applications (NCA), Boston, MA, USA, 23–26 November 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Tatipatri, N.; Arun, S.L. A Comprehensive Review on Cyber-Attacks in Power Systems: Impact Analysis, Detection, and Cyber Security. IEEE Access 2024, 12, 18147–18167. [Google Scholar] [CrossRef]
- Aoufi, S.; Derhab, A.; Guerroumi, M. Survey of false data injection in smart power grid: Attacks, countermeasures and challenges. J. Inf. Secur. Appl. 2020, 54, 102518. [Google Scholar] [CrossRef]
- Musleh, A.S.; Chen, G.; Dong, Z.Y.; Wang, C.; Chen, S. Vulnerabilities, Threats, and Impacts of False Data Injection Attacks in Smart Grids: An Overview. In Proceedings of the International Conference on Smart Grids and Energy Systems (SGES), Perth, Australia, 23–26 November 2020; pp. 77–82. [Google Scholar] [CrossRef]
- Mohammadpourfard, M.; Khalili, A.; Genc, I.; Konstantinou, C. Cyber-Resilient Smart Cities: Detection of Malicious Attacks in Smart Grids. Sustain. Cities Soc. 2021, 75, 103116. [Google Scholar] [CrossRef]
- Huang, Y.; He, H. Advance learning technique for the electricity market attack detection. Comput. Electr. Eng. 2022, 100, 107865. [Google Scholar] [CrossRef]
- Patel, H.R. Replay Attack Detection in Smart Grids Using Switching Multi-Sine Watermarking. Master’s Thesis, Concordia University, Montreal, QC, Canada, 2023. [Google Scholar]
- Khazaei, J.; Asrari, A. Second-Order Cone Programming Relaxation of Stealthy Cyberattacks Resulting in Overvoltages in Cyber-Physical Power Systems. IEEE Syst. J. 2022, 16, 4267–4278. [Google Scholar] [CrossRef]
- Peng, S.; Liu, M.; Zuo, K.; Tan, W.; Deng, R. Stealthy Data Integrity Attacks Against Grid-tied Photovoltaic Systems. In Proceedings of the IEEE 6th International Conference on Industrial Cyber-Physical Systems (ICPS), Wuhan, China, 8–11 May 2023; pp. 1–7. [Google Scholar] [CrossRef]
- Karnouskos, S. Stuxnet worm impact on industrial cyber-physical system security. In Proceedings of the IECON 2011—37th Annual Conference of the IEEE Industrial Electronics Society, Melbourne, VIC, Australia, 7–10 November 2011; pp. 4490–4494. [Google Scholar] [CrossRef]
- Kushner, D. The real story of stuxnet. IEEE Spectr. 2013, 50, 48–53. [Google Scholar] [CrossRef]
- Matrosov, A.; Rodionov, E.; Harley, D.; Malcho, J. Stuxnet Under the Microscope. 2010. Available online: https://www.esetnod32.ru/company/viruslab/analytics/doc/Stuxnet_Under_the_Microscope.pdf (accessed on 15 April 2025).
- Dragos Inc. CRASHOVERRIDE Analysis of the Threat to Electric Grid Operations. 2017. Available online: https://www.dragos.com/wp-content/uploads/CrashOverride-01.pdf?utm_referrer (accessed on 10 April 2025).
- Slowik, J.; Dragos Inc. CRASHOVERRIDE: Reassessing the 2016 Ukraine Electric Power Event as a Protection-Focused Attack. 2019. Available online: https://www.dragos.com/wp-content/uploads/2021/03/CRASHOVERRIDE.pdf?hs (accessed on 10 April 2025).
- Rector, S. A Case Study of the CRASHOVERRIDE Malware, Its Effects and Possible Countermeasures; Cybersecurity Undergraduate Research Showcase. 5.; Old Dominion University: Norfolk, VA, USA, 2024. [Google Scholar] [CrossRef]
- Khan, S.; Madnick, S. Protecting Chiller Systems from Cyberattack Using a Systems Thinking Approach. Network 2022, 2, 606–627. [Google Scholar] [CrossRef]
- Elnour, M.; Meskin, N.; Khan, K.; Jain, R. HVAC system attack detection dataset. Data Brief 2021, 37, 107166. [Google Scholar] [CrossRef]
- Chen, D.; Sun, Q.Z.; Qiao, Y. Defending against cyber-attacks in building HVAC systems through energy performance evaluation using a physics-informed dynamic Bayesian network (PIDBN). Energy 2025, 322, 135369. [Google Scholar] [CrossRef]
- Elnour, M.; Meskin, N.; Khan, K.; Jain, R. Application of data-driven attack detection framework for secure operation in smart buildings. Sustain. Cities Soc. 2021, 69, 102816. [Google Scholar] [CrossRef]
- Li, G.; Ren, L.; Fu, Y.; Yang, Z.; Adetola, V.; Wen, J.; Zhu, Q.; Wu, T.; Candan, K.S.; O’Neill, Z. A critical review of cyber-physical security for building automation systems. Annu. Rev. Control 2023, 55, 237–254. [Google Scholar] [CrossRef]
- Ding, S.; Gu, W.; Lu, S.; Yu, R.; Sheng, L. Cyber-attack against heating system in integrated energy systems: Model and propagation mechanism. Appl. Energy 2022, 311, 118650. [Google Scholar] [CrossRef]
- Morales-Gonzalez, C.; Harper, M.; Cash, M.; Luo, L.; Ling, Z.; Sun, Q.Z.; Fu, X. On building automation system security. High-Confid. Comput. 2024, 4, 100236. [Google Scholar] [CrossRef]
- Li, G.; Ren, L.; Pradhan, O.; O’Neill, Z.; Wen, J.; Yang, Z.; Fu, Y.; Chu, M.; Huang, J.; Wu, T.; et al. Emulation and detection of physical faults and cyber-attacks on building energy systems through real-time hardware-in-the-loop experiments. Energy Build. 2024, 320, 114596. [Google Scholar] [CrossRef]
- Moudgil, V.; Hewage, K.; Hussain, S.A.; Sadiq, R. Integration of IoT in building energy infrastructure: A critical review on challenges and solutions. Renew. Sustain. Energy Rev. 2023, 174, 113121. [Google Scholar] [CrossRef]
- Fan, C.; Lei, Y.; Sun, Y.; Mo, L. Novel transformer-based self-supervised learning methods for improved HVAC fault diagnosis performance with limited labeled data. Energy 2023, 278 Pt B, 127972. [Google Scholar] [CrossRef]
- Karbasi, A.; Farhadi, A. A cyber-physical system for building automation and control based on a distributed MPC with an efficient method for communication. Eur. J. Control 2021, 61, 151–170. [Google Scholar] [CrossRef]
- Moosavi, S.A.; Asgari, M.; Kamel, S.R. Developing a comprehensive BACnet attack dataset: A step towards improved cybersecurity in building automation systems. Data Brief 2024, 57, 111192. [Google Scholar] [CrossRef] [PubMed]
- Galler, M. Basic Recommendations For HVAC Cybersecurity. ASHRAE J. 2021, 63, 1–2. Available online: https://tsapps.nist.gov/publication/get_pdf.cfm?pub_id=932229 (accessed on 25 April 2025).
- Association of European Refrigeration Component Manufacturers (ASERCOM). ASERCOM Cyber-Security Guideline for Connected HVAC/R Equipment. 2018. Available online: https://asercom.org/wp-content/uploads/2021/01/English_CyberSecurity-Guideline.pdf (accessed on 20 March 2025).
- Vijayshankar, S.; Chang, C.-Y.; Utkarsh, K.; Wald, D.; Ding, F.; Balamurugan, S.P.; King, J.; Macwan, R. Assessing the impact of cybersecurity attacks on energy systems. Appl. Energy 2023, 345, 121297. [Google Scholar] [CrossRef]
- IEC 61850-7-420:2021; Communication Networks and Systems for Power Utility Automation—Part 7-420: Basic Communication Structure—Distributed Energy Resources and Distribution Automation Logical Nodes. International Electrotechnical Commission: Geneva, Switzerland, 2021.
- European Commission. Regulation (EU) 2024/2847 of the European Parliament and of the Council of 23 October 2024 on Horizontal Cybersecurity Requirements for Products with Digital Elements and Amending Regulations (EU) No 168/2013 and (EU) 2019/1020 and Directive (EU) 2020/1828 (Cyber Resilience Act) (Text with EEA Relevance), OJ L, 2024/2847, 20.11.2024, Document 32024R2847. Available online: https://eur-lex.europa.eu/eli/reg/2024/2847/oj/eng (accessed on 28 May 2025).
- European Commission. Directive (EU) 2022/2555 of the European Parliament and of the Council of 14 December 2022 on Measures for a High Common Level of Cybersecurity Across the Union, Amending Regulation (EU) No 910/2014 and Directive (EU) 2018/1972, and Repealing Directive (EU) 2016/1148 (NIS 2 Directive) (Text with EEA Relevance), OJ L 333, 27.12.2022, Document 32022L2555. Available online: https://eur-lex.europa.eu/eli/dir/2022/2555/oj/eng (accessed on 28 May 2025).
- International Electrotechnical Commission. International Society of Automation, ISA/IEC 62443 Series of Standards. Available online: https://www.isa.org/standards-and-publications/isa-standards/isa-iec-62443-series-of-standards (accessed on 28 May 2025).
- European Union Agency for Cybersecurity, ENISA. Guideline on Security Measures Under the EECC, Fourth edition, July 2021. Available online: https://www.enisa.europa.eu/publications/guideline-on-security-measures-under-the-eecc (accessed on 28 May 2025).
- IEEE Std 1547.3-2023 (Revision of IEEE Std 1547.3-2007); IEEE Guide for Cybersecurity of Distributed Energy Resources Interconnected with Electric Power Systems. IEEE: New York, NY, USA, 2023; pp. 1–183. [CrossRef]
- Sarker, P.P.; Das, U.; Varshney, N.; Shi, S.; Kulkarni, A.; Farahmandi, F.; Tehranipoor, M. When Everyday Devices Become Weapons: A Closer Look at the Pager and Walkie-talkie Attacks. arXiv 2025. [Google Scholar] [CrossRef]
- Rogers, M.; Ruppersberger, C.A.D. Investigative Report on the U.S. National Security Issues Posed by Chinese Telecommunications Companies Huawei and ZTE; U.S. House of Representatives Permanent Select Committee on Intelligence: Washington, DC, USA, 2012. [Google Scholar]
- Euronews. Eleven EU Countries Took 5G Security Measures to ban Huawei, ZTE. Available online: https://www.euronews.com/next/2024/08/12/eleven-eu-countries-took-5g-security-measures-to-ban-huawei-zte (accessed on 30 May 2025).
- PV-Magazine. Una Empresa Danesa Descubre «Componentes Sospechosos» en Tecnología Energética Importada (Danish Company Discovers ‘Suspicious Components’ in Imported Energy Technology). Available online: https://www.pv-magazine.es/2025/05/27/una-empresa-danesa-descubre-componentes-sospechosos-en-tecnologia-fotovoltaica-importada/ (accessed on 29 May 2025).
- European Commission. Commission Delegated Regulation (EU) 2024/1366 of 11 March 2024 Supplementing Regulation (EU) 2019/943 of the European Parliament and of the Council by Establishing a Network Code on Sector-Specific Rules for Cybersecurity Aspects of Cross-Border Electricity Flows, OJ L, 2024/1366, 24.5.2024, Document 32024R1366. Available online: https://eur-lex.europa.eu/eli/reg_del/2024/1366/oj/eng (accessed on 28 May 2025).
- SolarPower Europe. Solutions for PV Cyber Risks to Grid Stability. 2025. Available online: https://api.solarpowereurope.org/uploads/SPE_2025_Solutions_for_PV_Cyber_Risks_to_Grid_Stability_032dc2ae5a.pdf (accessed on 28 May 2025).
- Market Data Forecast. Global Solar Hybrid Inverter Market Research Report—Segmentation By Product (Single-Phase Hybrid Solar Inverter and Three-Phase Hybrid Solar Inverter), by End User (Commercial, Residential, and Others), and Region—Industry Forecast 2024 to 2032. Available online: https://www.marketdataforecast.com/market-reports/solar-hybrid-inverter-market (accessed on 31 May 2025).
- Independent Bulgarian Energy Exchange (IBEX). Available online: https://ibex.bg (accessed on 4 April 2025).
- Electricity System Operator (ESO). Available online: https://eso.bg (accessed on 4 April 2025).
- Photovoltaic Geographical Information System (PVGIS). Available online: https://joint-research-centre.ec.europa.eu/photovoltaic-geographical-information-system-pvgis_en (accessed on 4 April 2025).
- International Renewable Energy Agency (IRENA). Electricity Storage Valuation Framework: Assessing System Value and Ensuring Project Viability; International Renewable Energy Agency: Abu Dhabi, United Arab Emirates, 2020; ISBN 978-92-9260-161-4. [Google Scholar]
- Schmalensee, R. Competitive Energy Storage and the Duck Curve; MIT CEEPR Working Paper Series, CEEPR WP 2020-012; MIT Center for Energy and Environmental Policy Research: Cambridge, MA, USA, 2020; Available online: https://ceepr.mit.edu (accessed on 28 May 2025).
- eRisk Group. The Californian Duck is Coming to Europe, with a Smile; eRisk Group: Baarn, The Netherlands, 2014; Available online: https://eriskgroup.com/ (accessed on 28 May 2025).
- Hartner, M.; Permoser, A. Through the valley: The impact of PV penetration levels on price volatility and resulting revenues for storage plants. Renew. Energy 2018, 115, 1184–1195. [Google Scholar] [CrossRef]
- Pavlík, M. Ever More, Frequent Negative, Electricity Prices: A New Reality and Challenges for Photovoltaics and Wind Power in a Changing Energy Market—Threat or Opportunity, and Where Are the Limits of Sustainability? Energies 2025, 18, 2498. [Google Scholar] [CrossRef]
- Understanding Ultralow and Negative Power Prices: Causes, Impacts and Improvements, Eurelectric Position Paper. 2024. Available online: https://www.eurelectric.org/ (accessed on 30 May 2025).
- ENTSO-E. ENTSO-E Expert Panel Initiates the Investigation into the Causes of Iberian Blackout. Available online: https://www.entsoe.eu/news/2025/05/09/entso-e-expert-panel-initiates-the-investigation-into-the-causes-of-iberian-blackout/ (accessed on 30 May 2025).
- ENTSO-E. Incident in the Power System of North Macedonia on May 18th. Available online: https://www.entsoe.eu/news/2025/05/30/incident-in-the-power-system-of-north-macedonia-on-may-18th/ (accessed on 30 May 2025).
- PV-Magazine. El Tema de la Ciberseguridad es un Problema Real, Pero la Información de Reuters hay que Cogerla con Pinzas. (Cybersecurity Is a Real Problem, but Reuters’ Reporting Should Be Taken with a Grain of Salt.). Available online: https://www.pv-magazine.es/2025/05/15/el-tema-de-la-ciberseguridad-es-un-problema-real-pero-la-informacion-de-reuters-hay-que-cogerla-con-pinzas/ (accessed on 29 May 2025).
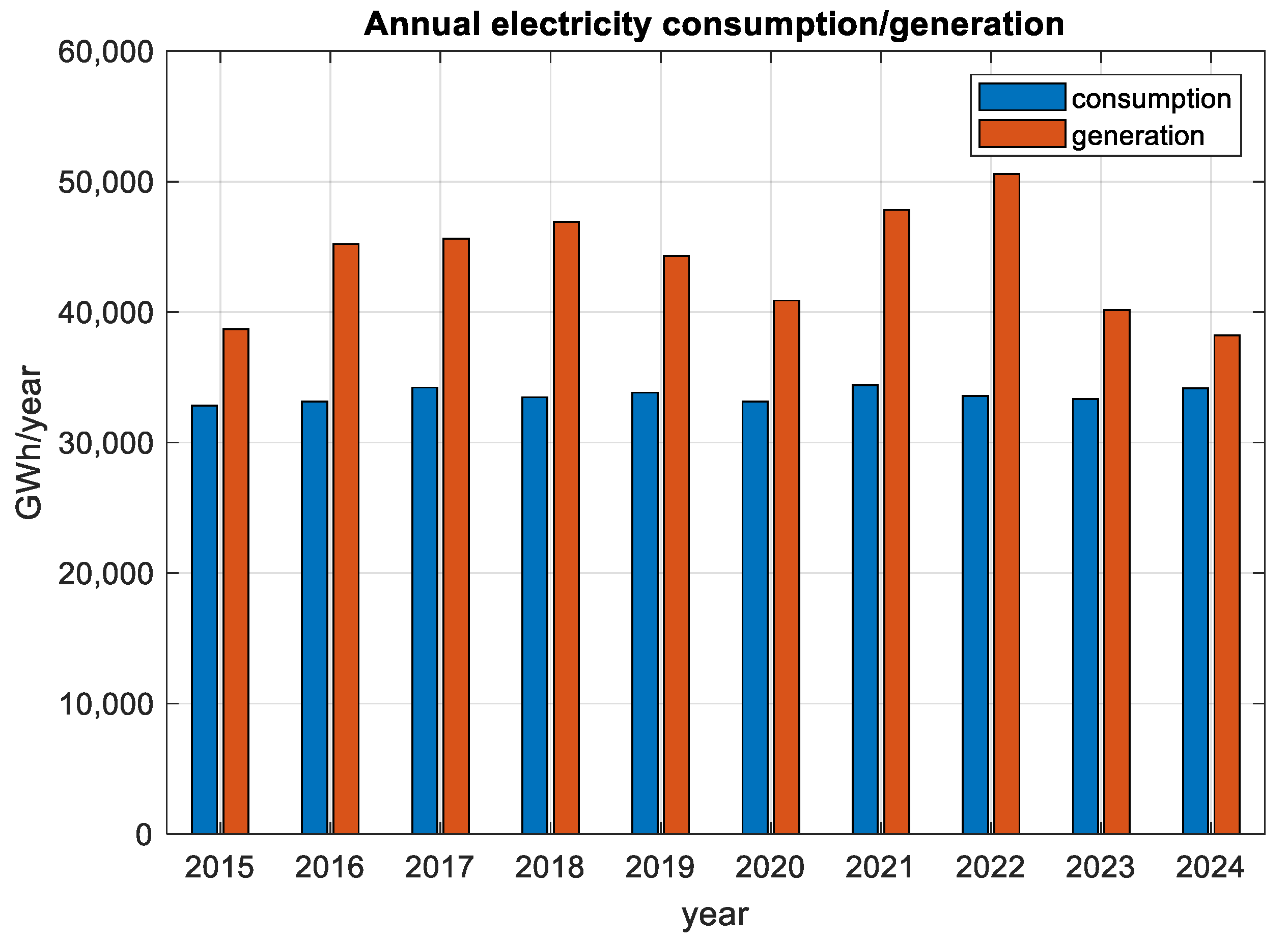
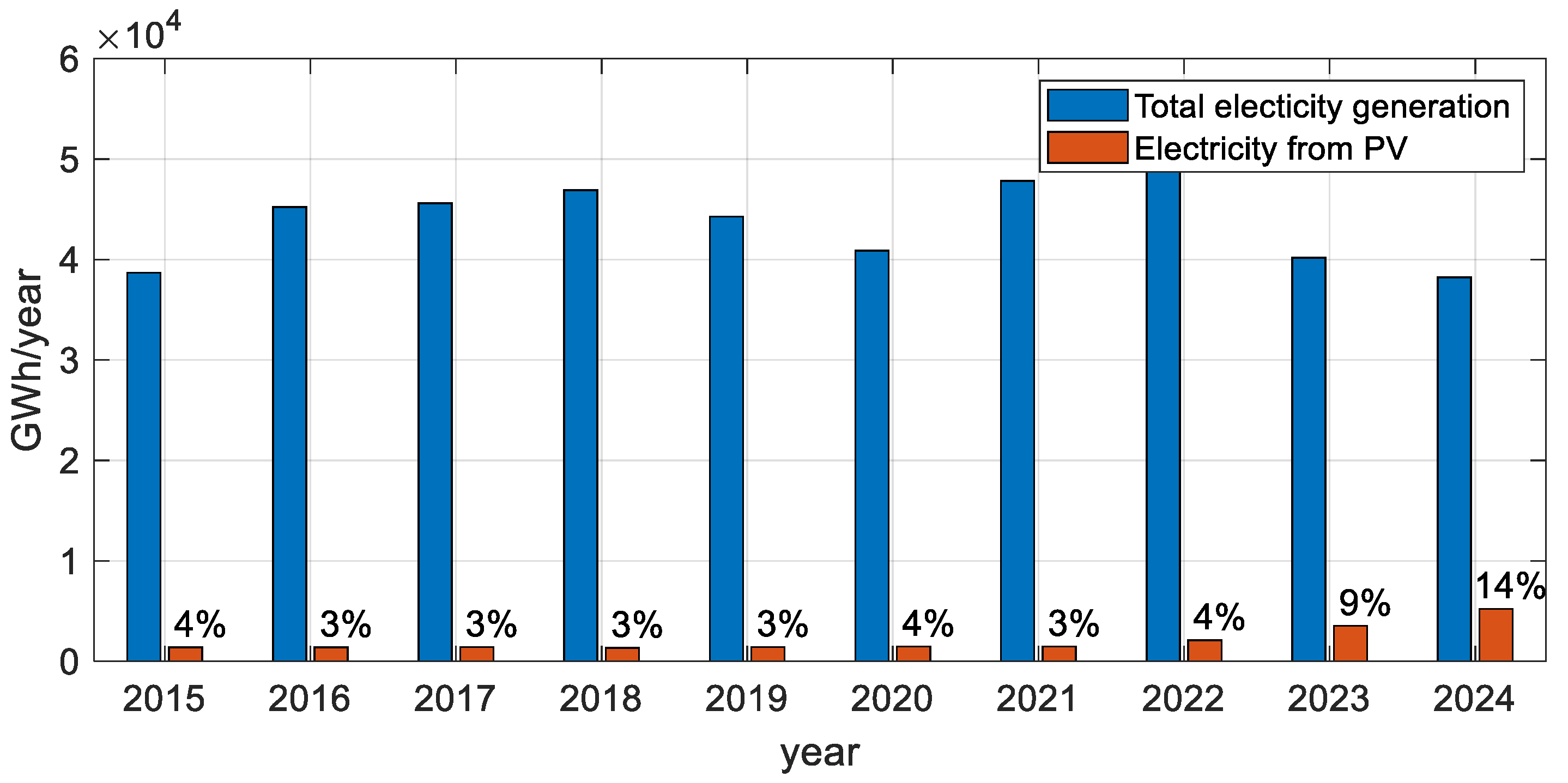
| Cyber-Attack Events | Year | Reference |
|---|---|---|
| Cyber-attack on Ohio’s Davis–Besse nuclear power plant. | 2003 | [25] |
| Use of a Stuxnet worm on the Iranian nuclear program—the first ever malware targeting PLCs and SCADA systems. | 2010 | [25,36,37,38] |
| Duqu and Flame malwares purposed to spy on an Iranian oil company. | 2011 and 2012 | [37] |
| HAVEX (Backdoor.Oldrea) malware, purposed for cyber espionage, targeting numerous industrial systems in energy, aviation, pharmaceutical, defense, and petrochemical companies, primarily in the USA and Europe. | 2013 | [8,20,39] |
| BlackEnergy malware—the BlackEnergy 1 attack on Georgia; the BlackEnergy 2 attack on critical infrastructures in the US; and the BlackEnergy 3 attack on three of Kyiv’s power distribution companies. | 2008 2014 2015 | [2,17,25,27,28,39] |
| CRASHOVERRIDE (Industroyer) malware—used in the second attack on Ukraine’s grid. | 2016 | [39,40,41] |
| TRITON (TRISIS) malware—an attack on the equipment of a petrochemical plant in Saudi Arabia. | 2017 | [40] |
| Cyber-attack on water treatment plant in Florida, USA. | 2021 | [42] |
| Score | Value |
|---|---|
| 1 | Single device (or small number of devices) |
| 2 | Device group—for example, all devices of a given installer |
| 3 | Large number of devices—all devices of a given vendor |
| Score | Value |
|---|---|
| 1 | Very difficult—requires large resources, such as physical access, firmware access (0-day exploit), etc. |
| 2 | Moderate—hacker group level |
| 3 | Easy—basic skills and minimum resources |
| Score | Value |
|---|---|
| 1 | Low—happens very rarely or there are no records of such a scenario. |
| 2 | Moderate—there is a history of such scenarios, but they are not common. |
| 3 | High—frequently occurring scenarios that are well known and described. |
| Score | Value |
|---|---|
| 10+ | Critical |
| 6–10 | High |
| 3–6 | Medium |
| 1–3 | Low |
| Threat | Impact | Difficulty | Likelihood | Risk Score | Risk Level |
|---|---|---|---|---|---|
| 2 | 2 | 2 | 8 | High |
| 2 | 2 | 2 | 8 | High |
| 3 | 1 | 2 | 6 | High |
| 2 | 1 | 1 | 2 | Low |
| 2 | 2 | 1 | 4 | Medium |
| 3 | 1 | 1 | 3 | Medium |
| 3 | 3 | 1 | 9 | High |
| Threat | Vulnerability | IEC 27005 Impact | IEC 27005 Likelihood | IEC 27005 Detection | Measure |
|---|---|---|---|---|---|
| Insufficient identity check | Medium | Medium | Moderate | Multi-factor authentication, log control, access isolation |
| Insufficient identity check | Medium | Medium | Moderate | Multi-factor authentication, log control, access isolation |
| Insufficient identity check | High | Medium | Good | Multi-factor authentication, log control, access isolation |
| Lack of network segmentation or encryption | Medium | Low | Good | Interface isolation, encryption, communication monitoring |
| Unknown or unauthorized devices with access | Medium | Low | Moderate | Limiting unauthorized access by MAC filtering and whitelisting trusted devices |
| Untrusted suppliers or lack of software control | High | Low | Good | Outsourcer control, vendor security policies |
| Untrusted suppliers or lack of software control | High | Low | Poor | Outsourcer control, vendor security policies |
| Threat | NIST CSF Category | Recommended Control |
|---|---|---|
| PR.AC—Access Control | Implement strong authentication and access restrictions |
| PR.AC—Access Control | Implement strong authentication and access restrictions |
| PR.AC—Access Control | Implement strong authentication and access restrictions |
| PR.PT—Protective Technology/DE.CM—Monitoring | Isolate interfaces; monitor communications |
| PR.IP—Information Protection/DE.DP—Detection Processes | Block unauthorized devices; maintain asset inventory |
| ID.AM—Asset Management/PR.AT—Awareness Training | Control third-party access; enforce supplier security policies |
| ID.AM—Asset Management/PR.AT—Awareness Training | Control third-party access; enforce supplier security policies |
| Questionnaire | Response |
|---|---|
| Yes—36%; No—64%. |
| Yes—12%; No—88%. |
| Yes—18%; Partially—31%; No—51%. |
| Yes—73%; No—19%; Abstained—8 %. |
| Yes—91%; No—5%; Abstained—4%. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gueorgiev, V.; Totev, V.; Tsankov, P.; Stoyanov, S. Evaluating Cybersecurity Risks of Bulgaria’s Energy Sector: Focus on PV and HVAC-R. Appl. Sci. 2025, 15, 6672. https://doi.org/10.3390/app15126672
Gueorgiev V, Totev V, Tsankov P, Stoyanov S. Evaluating Cybersecurity Risks of Bulgaria’s Energy Sector: Focus on PV and HVAC-R. Applied Sciences. 2025; 15(12):6672. https://doi.org/10.3390/app15126672
Chicago/Turabian StyleGueorgiev, Vultchan, Valentin Totev, Plamen Tsankov, and Stoyan Stoyanov. 2025. "Evaluating Cybersecurity Risks of Bulgaria’s Energy Sector: Focus on PV and HVAC-R" Applied Sciences 15, no. 12: 6672. https://doi.org/10.3390/app15126672
APA StyleGueorgiev, V., Totev, V., Tsankov, P., & Stoyanov, S. (2025). Evaluating Cybersecurity Risks of Bulgaria’s Energy Sector: Focus on PV and HVAC-R. Applied Sciences, 15(12), 6672. https://doi.org/10.3390/app15126672








