1. Introduction
Sharing threat intelligence data is essential in a contemporary, interconnected digital landscape where cyber threats evolve rapidly and pose significant risks to organizations and individuals alike. By pooling together data on emerging threats, attack techniques, and vulnerabilities, organizations can gain a comprehensive understanding of the threat landscape and identify potential risks early on.
According to a Ponemon Institute report [
1], high-performing companies are often willing to share intelligence than other companies. The report highlights the collaborative benefits of shared threat intelligence in enhancing cybersecurity posture and reducing risk. Moreover, government agencies, such as the Cybersecurity and Infrastructure Security Agency (CISA) in the United States, actively promote threat intelligence sharing among public and private sector organizations. Through programs like the Automated Indicator Sharing (AIS) [
2], participating organizations can exchange actionable threat indicators in real time, enabling them to strengthen their cyber defenses and respond to emerging threats more effectively.
However, when the source of intelligence information is unclear, it may lead to problems with quality and content. Research by Omar Al-Ibrahim et al. [
3] also pointed out that the current intelligence information focuses on quantity rather than the quality of information. Furthermore, organizations may engage in the sharing community with opportunistic motives, such as minimal contribution or exploiting the intelligence provided by others, leading to free-riding behavior. Therefore, the tamper-proof information sharing process and contributing members are important issues for information sharing.
Blockchain as a tamper-proof and decentralized storage technology has gained lots of attention recently. Along with well-known cryptocurrencies, non-fungible tokens (NFTs) have also made frequent appearances in various reports and news. For instance, in December 2021, an NFT artwork created by the artist Pak was sold for a staggering
$91.8 million [
4]. This event brought blockchain applications into the global spotlight, with widespread adoption in not only the financial sector but also in enterprises [
5], healthcare [
6], and the legal system [
7]. Additionally, countries worldwide are actively seeking international patents related to blockchain [
8], with China and the United States leading the way, having filed nearly 55,000 patents as of June 2021. This highlights the international significance of blockchain as an indispensable, decentralized data storage technology.
Nevertheless, the emergence of quantum computing poses a threat to most public key algorithms used today, as established by major international companies such as Microsoft and Google. These research have demonstrated the potential impact of quantum computing on current cryptographic techniques [
9,
10]. Therefore, it has become imperative to replace national critical infrastructure with post-quantum algorithms, prompting the National Institute of Standards and Technology (NIST) to initiate a competition for post-quantum cryptography standards. Recognizing the escalating risks posed by advancements in quantum computing, the National Institute of Standards and Technology (NIST) has undertaken a comprehensive initiative to standardize post-quantum cryptographic (PQC) algorithms. As of August 2024, NIST has finalized its initial set of encryption standards designed to withstand quantum computer-based cyberattacks. The primary standard for general encryption is based on the CRYSTALS-KYBER algorithm, now referred to as ML-KEM (Module-Lattice-Based Key-Encapsulation Mechanism). For digital signatures, NIST has standardized two algorithms: ML-DSA (Module-Lattice-Based Digital Signature Algorithm), derived from the CRYSTALS–Dilithium algorithm, and SLH-DSA (Stateless Hash-Based Digital Signature Algorithm), based on the SPHINCS+ algorithm. In March 2025, NIST selected the HQC (Hamming Quasi-Cyclic) algorithm as an additional post-quantum encryption standard, serving as a backup to ML-KEM due to its reliance on different mathematical foundations. As quantum computing technology continues to progress, migrating blockchain systems to these standardized post-quantum cryptographic mechanisms is essential to ensure long-term security.
Aside from quantum threats, there exist other concerns related to blockchain technology, such as efficiency and the substantial consumption of computational resources. Blockchain generates a new block approximately every ten minutes, resulting in delayed data storage efficiency. Moreover, the proof-of-work (PoW) consensus mechanism used to mine new blocks requires nodes to compete for mining rights. The node that successfully solves the cryptographic puzzle first receives the reward, with nodes possessing higher computational power having a greater likelihood of winning. However, other nodes still expend computational resources despite having a nonzero probability of finding a valid solution. This inefficiency and wastage of computational resources present significant challenges in blockchain research.
To address these issues, we aimed to design Asynchronous Quantum-Resistant Blockchain for Secure Intelligence Sharing (AQRB), adopting the concepts of the SPHINCS+, CRYSTALS-KYBER, and the dual blockchain to tackle quantum computing, blockchain efficiency, and computational power problems. Based on the PQCRYPTO project endorsed by the European Union [
11] and NIST, AQRB picks the SPHINCS
+ algorithm as the post-quantum digital signature algorithm and CRYSTALS-KYBER for constructing AQRB. In conjunction with the implementation of a dual blockchain to tackle efficiency challenges, the new research utilizes the Libra [
12] blockchain framework to achieve the following objectives:
- ■
Quantum-resistant computation: All data stored on the blockchain remains secure and immune to quantum computing attacks or tampering.
- ■
Data storage efficiency: Reduces synchronization delays by enabling an asynchronous transaction validation mechanism.
- ■
Blockchain network balance: Encourages fair participation of nodes in the consensus process to prevent computational power centralization.
The rest of this research is organized as follows:
Section 2 presents the literature review covering prior work.
Section 3 provides a review and discussion of the relevant literature.
Section 4 outlines the methodology of this research, detailing the system design, cryptographic integration, and threat model assumptions.
Section 5 presents the results of the experiments, including performance benchmarks and implementation metrics.
Section 6 provides security analyses, addressing confidentiality, integrity, and quantum resilience. Finally,
Section 7 concludes the contributions of AQRB and outlines future research directions.
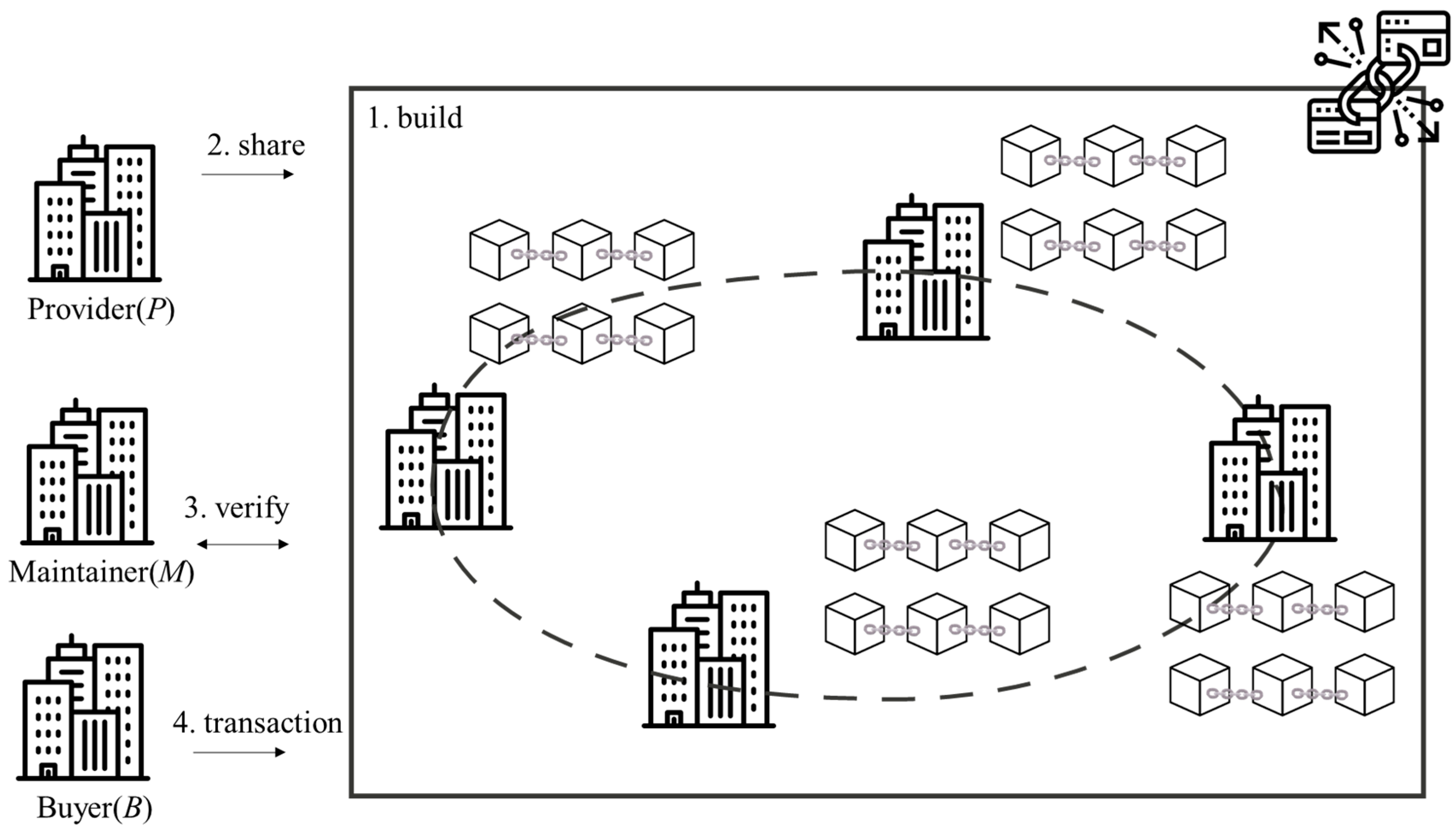
4. The Proposed Method
The flowchart of the AQRB is shown in
Figure 3, including three phases: building, sharing, and transactions. In the building phase, the post-quantum algorithm SPHINCS
+ and CRYSTALS-KYBER are introduced to generate the keys and addresses in blockchain. In the sharing phase, it explains the process of sharing and storing. The verifying phase illustrates how to verify the data and reputation in blockchain. After that, the data in the blockchain is uploaded by users. Finally, the transaction process is set when users propose the requirement. Notations used in the article are defined in
Table 2.
4.1. Building Phase
In the building phase, it delineates two key components;
Section 4.1.1 introduces the block content within the dual blockchain framework, while
Section 4.1.2 predominantly describes the key and address generation.
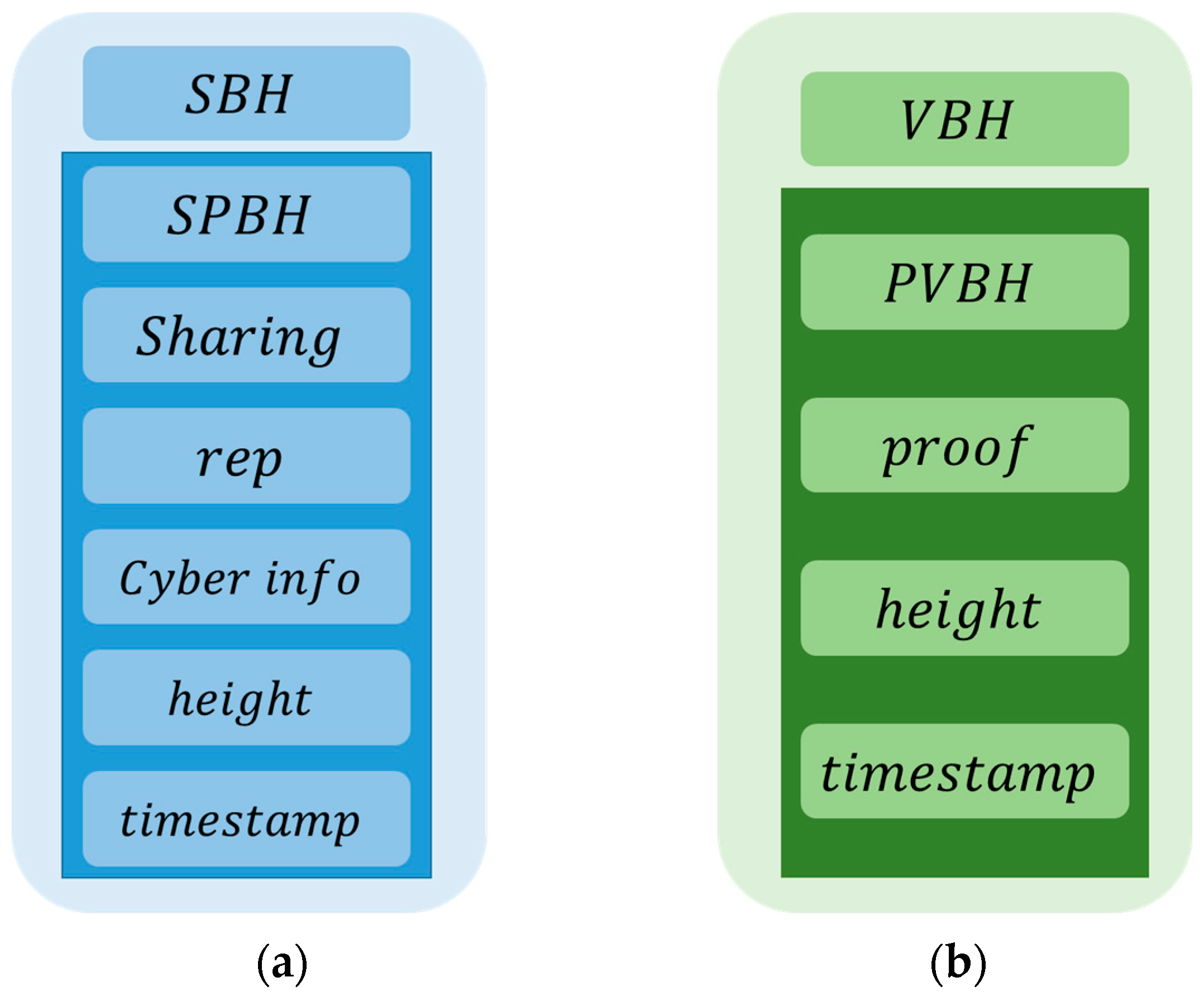
4.1.1. Block Content
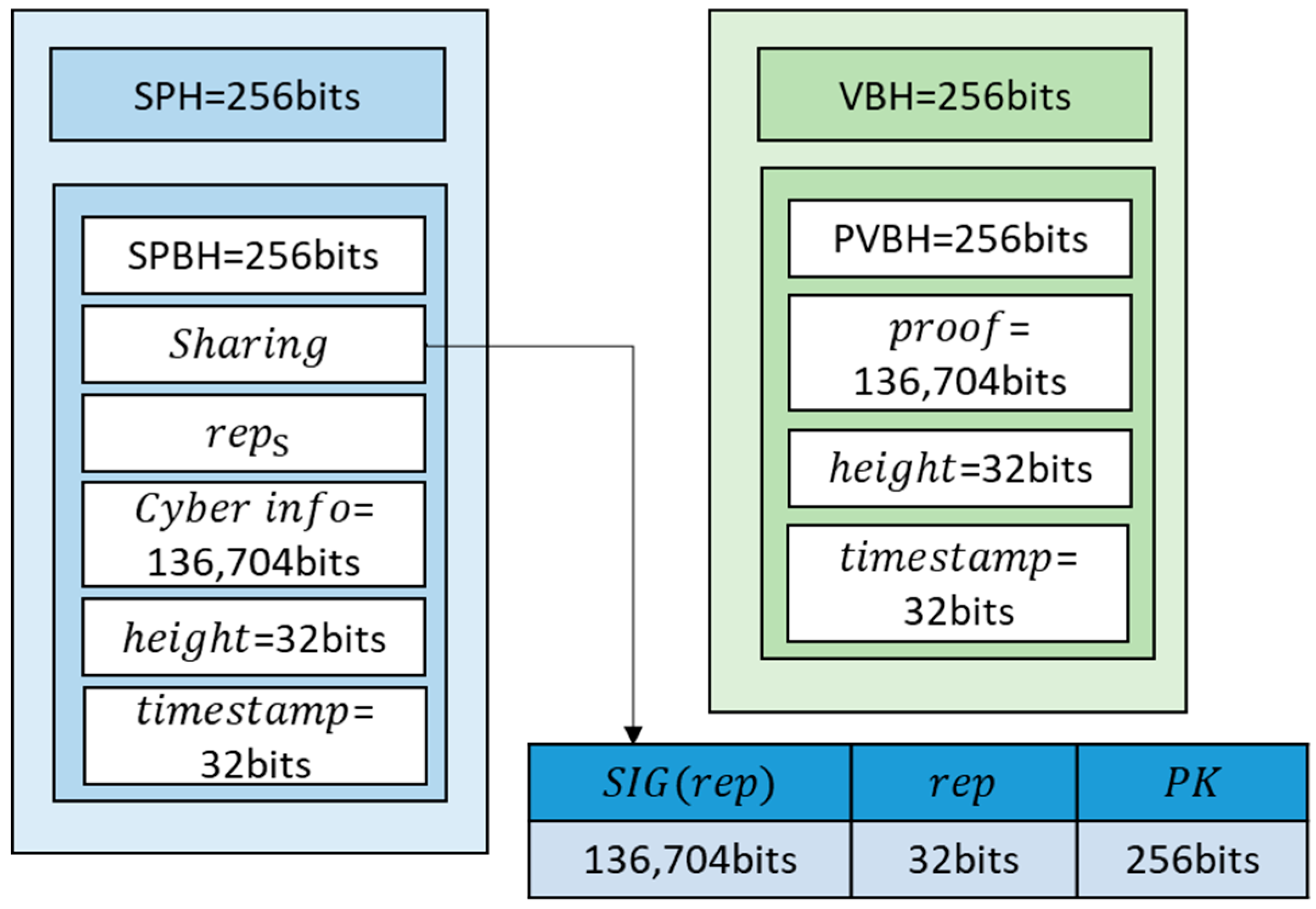
This segment is depicted in
Figure 4, showcasing the dual blockchain with contents, comprising two distinct chains: information chains and verification chains. The pertinent description is outlined below:
- ■
Information chain: the content of the information chain is shown in
Figure 4a, including sharing block header
, previous sharing block header (
,
,
,
,
, and
.
- ■
Verification chain: the content of the verification chain is shown in
Figure 4a, including verification block header
previous verification block header
,
, and
.
Figure 4.
Dual block content: (a) information block, (b) verification block.
Figure 4.
Dual block content: (a) information block, (b) verification block.
4.1.2. Key Generation
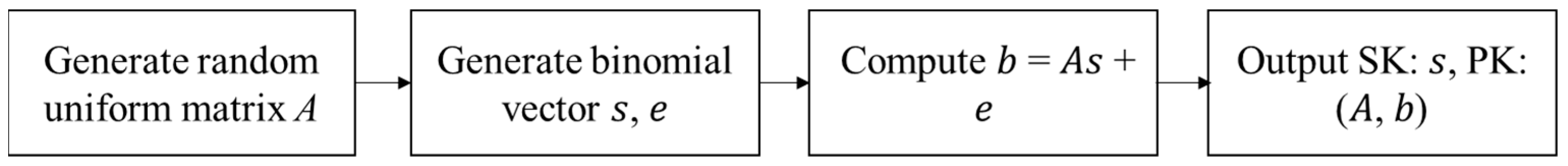
Step 1: The key used for encrypting shared intelligence is created by CRYSTALS-KYBER. The process is shown in
Figure 5. Initially, a random uniform matrix
is generated. Subsequently, the binomial vector
is derived from
, with the vector
representing error coding. Following this,
is computed, thus leading to the generation of the private key
and the public key
.
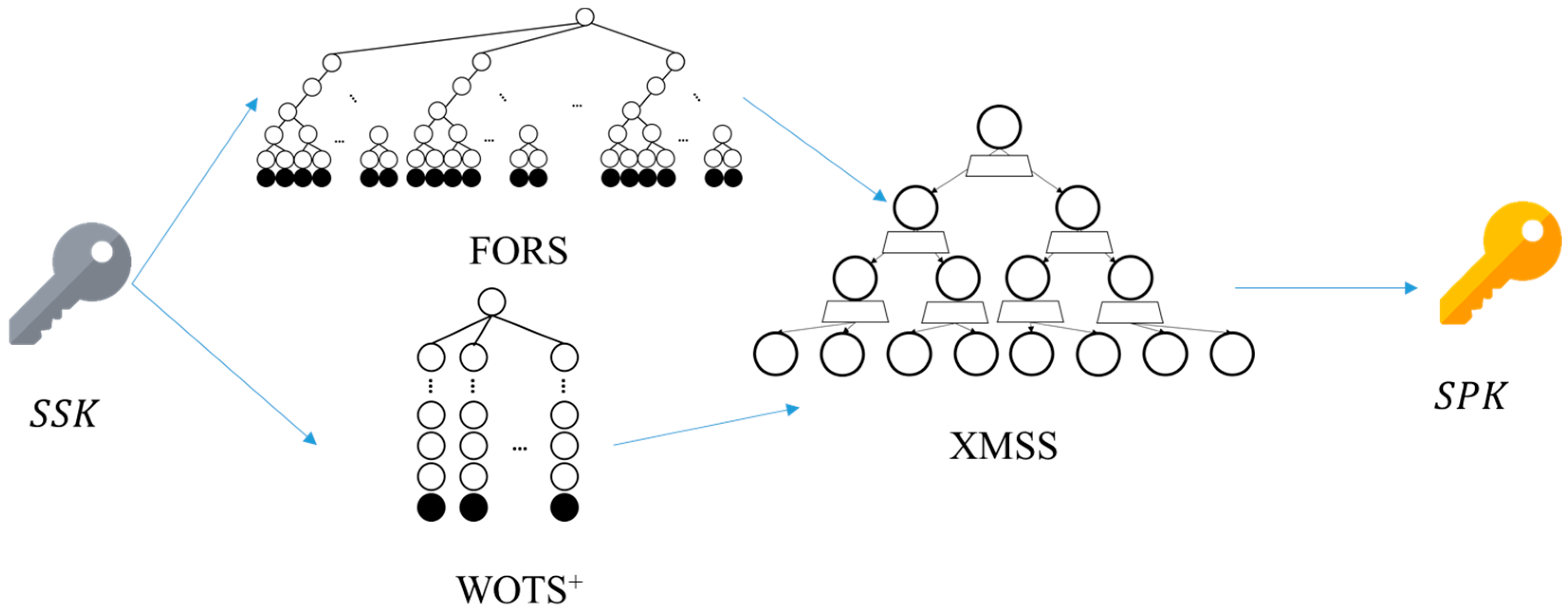
Step 2: The blockchain key is constructed by SPHINCS
+, as shown in
Figure 6. First, user
chooses a random number to create the private key seed
, sets it to the WOTS
+ and FORS bottom layer of SPHINCS
+, which goes through the hash function to build the WOTS
+ and FORS trees, and then XMSS connects FORS and WOTS
+ to generate a
and
.
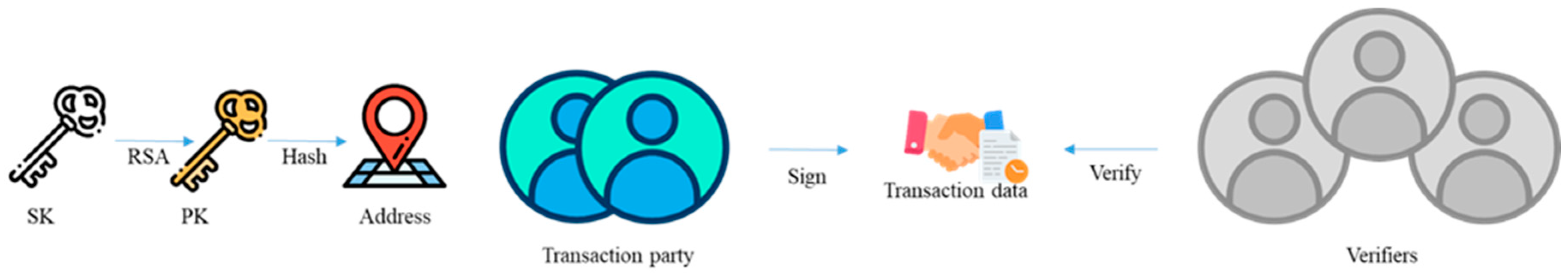
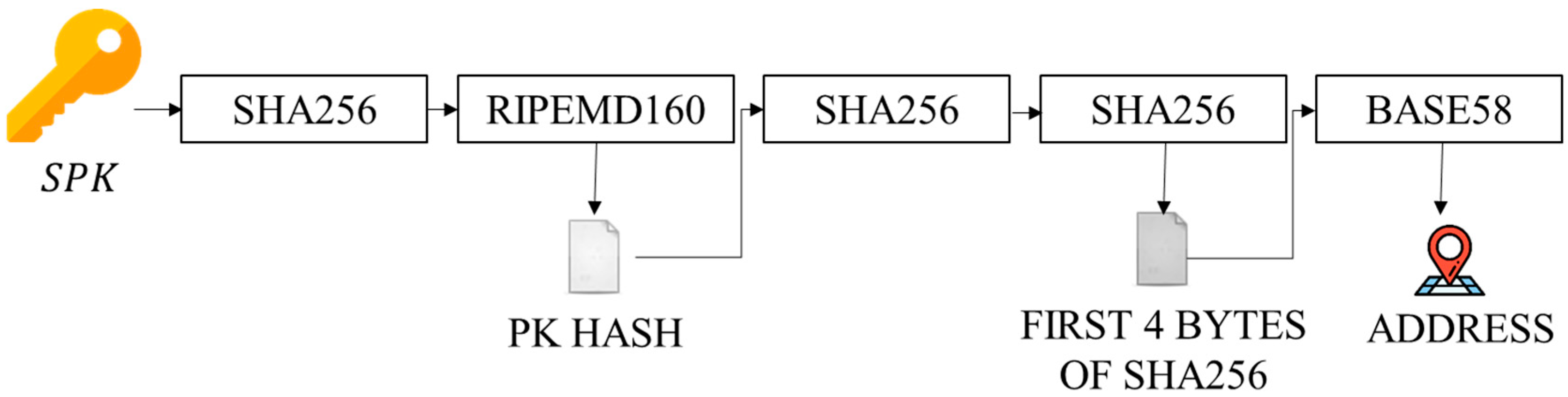
Step 3: The public key
is input into SHA256 and RIPEMD160 to obtain
PK hash. The outcome is further input into SHA256 twice. The first 4 bytes of consequence are combined with
PK hash, while the concatenation result is passed to BASE58 to generate an
, as shown in
Figure 7. Finally,
and (
,
) are broadcasted on the blockchain work.
4.2. Sharing Phase
This phase illustrates the process of information sharing, as shown in
Figure 8.
Step 1: calculates and broadcasts and signature to AQRB.
Step 2: Once obtains and from AQRB, it utilizes to verify . If it is positive, can be considered to become one of in this transaction; otherwise, the transaction is not established.
Step 3: When
wants to become
, it calculates
and
through Equations (1) and (2).
where
and
are the lengths of the information chain and verification chain. Next,
generates
and computes the signature
. Finally,
transmits
to
.
Step 4: After
receives request, it verifies
identity. Then,
requests the content of the block from the relevant user recorded in
and
. Subsequently,
verifies the correctness of these two blocks. If they are correct,
ensures that the
and
are promised by
. Then,
continues to wait for willing participants until the total competitiveness satisfies Equation (3).
Step 5: When receives a reply from , it means that has recognized as . Subsequently, uses to verify the correctness of the signature. At the same time, checks whether and are correct. If they are valid, uses to extract the tx||timestamp. Next, calculates and compares the result with the of Step 1. If they are the same, it means that successfully obtains the information shared this time. can create the latest block of .
4.3. Transactions Phase
This phase illustrates the intelligence sharing process, as shown in
Figure 9. Numbers 1 to 3 in the figure correspond to Step 1 to Step 3 described below.
Step 1: When obtains the information from , initiates a transaction with to obtain the and , and then sends the purchase request to P.
Step 2: After receiving the request, signs the message using its own private key , obtaining the signature . Subsequently, encrypts both the original message and the signature using , resulting in , which is then sent to .
Step 3: Once receives the data from , it applies to decrypt and verify the identity of by . If it is correct, broadcasts the to the blockchain; otherwise, the transaction is not established.
Step 4: The miners compete to become through Equation (1), and determine the number n of when it reaches the condition as Equations (4) and (5).
Step 5: obtains through performing hash function H(H(, and derives ().
Step 6:
packs
(
) into broadcast information
and broadcasts it to the AQRB,
Data = (
(
),
,
,
), including signature of
, transaction information, timestamp, and public key of
.
5. Experiments Result
The experiments are conducted with Windows 10 64-bit operating system and Intel Core i7-10510U CPU 2.6 GHz processor.
Section 4.1 offers the discussion on storage, while
Section 4.2 focuses on the analysis of computational resource usage.
5.1. Storage Space Cost
AQRB leverages SPHINCS
+ as the algorithm to construct the blockchain and selects SPHINCS+-128f as the parameter with the same robustness as ECDSA (P-256). According to the information block and verification block content in
Figure 10, the data size of Cyber information is 136,704 bits,
and
are 256 bits,
and
are both 32 bits,
is 137,312 bits, and the total number of
and verification blocks depends on the number of information maintenance companies
. Therefore, the storage space is estimated based on the three conditions: supply and demand balance, oversupply, and undersupply. With the block establishment condition being twice that of the
reputation value, it requires 2–4, 5–7, and 1 company maintenance for each condition discussed.
In the context of supply and demand balance, when two to four companies take charge of maintaining data, includes the , , and . If the data are maintained by two enterprises, size is 273,984 bits and the two verification blocks are 274,624 bits. In the case that three enterprises are involved in the provision, size is 410,976 bits and the verification block is 411,936 bits. When four companies are involved in the maintenance, size is 547,968 bits and the verification block is 549,248 bits. Therefore, while two to four companies join the data play, it takes 685,632 to 1,234,240 bits for the information block. In comparison, in cases of oversupply and undersupply, the data sizes are 1,508,552 to 2,057,152 and 411,328, respectively.
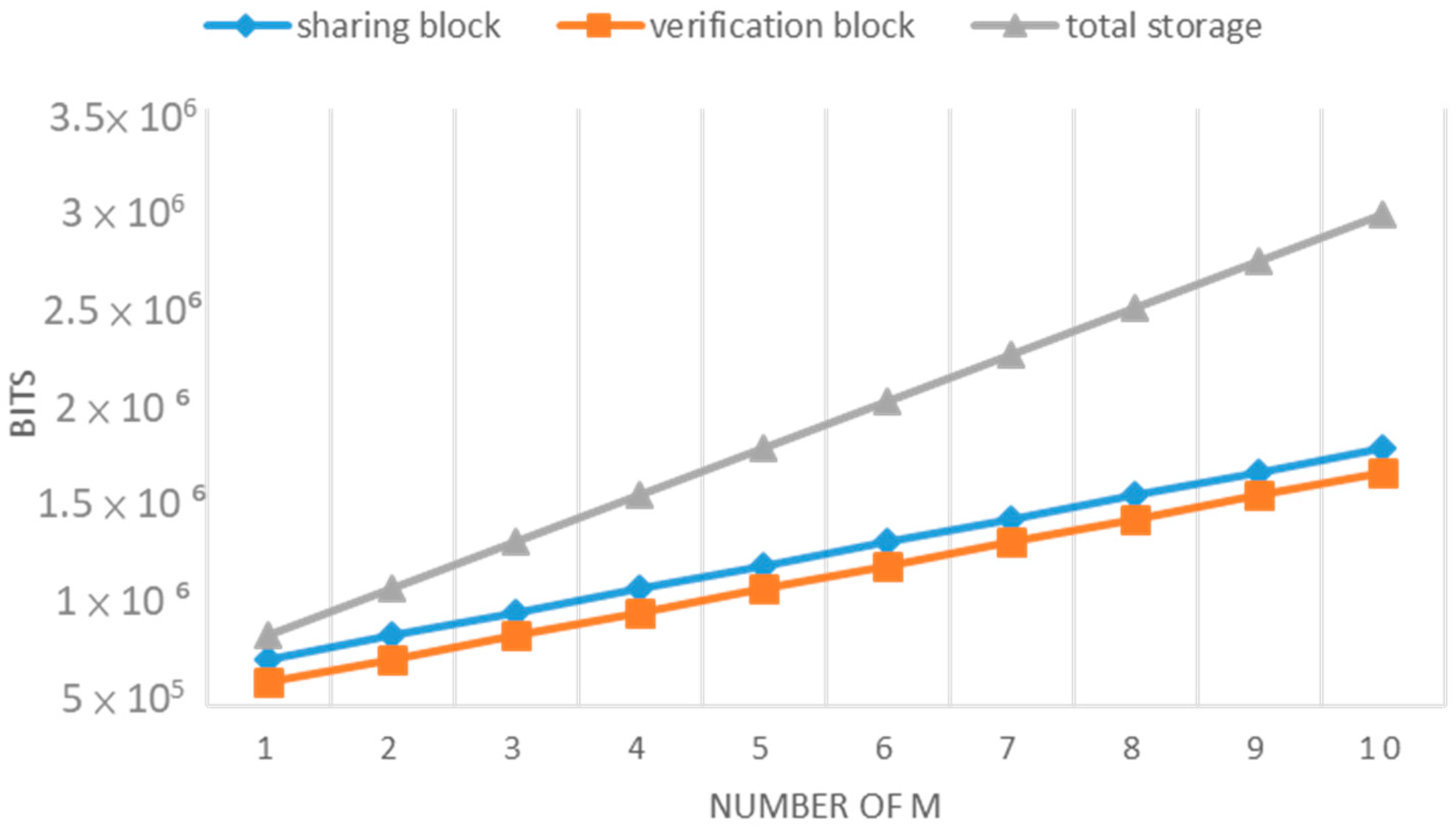
Figure 11 illustrates the storage costs of sharing block and verification block under different numbers of companies participating in the data maintenance. As the number of companies increases, the storage space required for both sharing block and verification block increases, impacting the total storage space consumption.
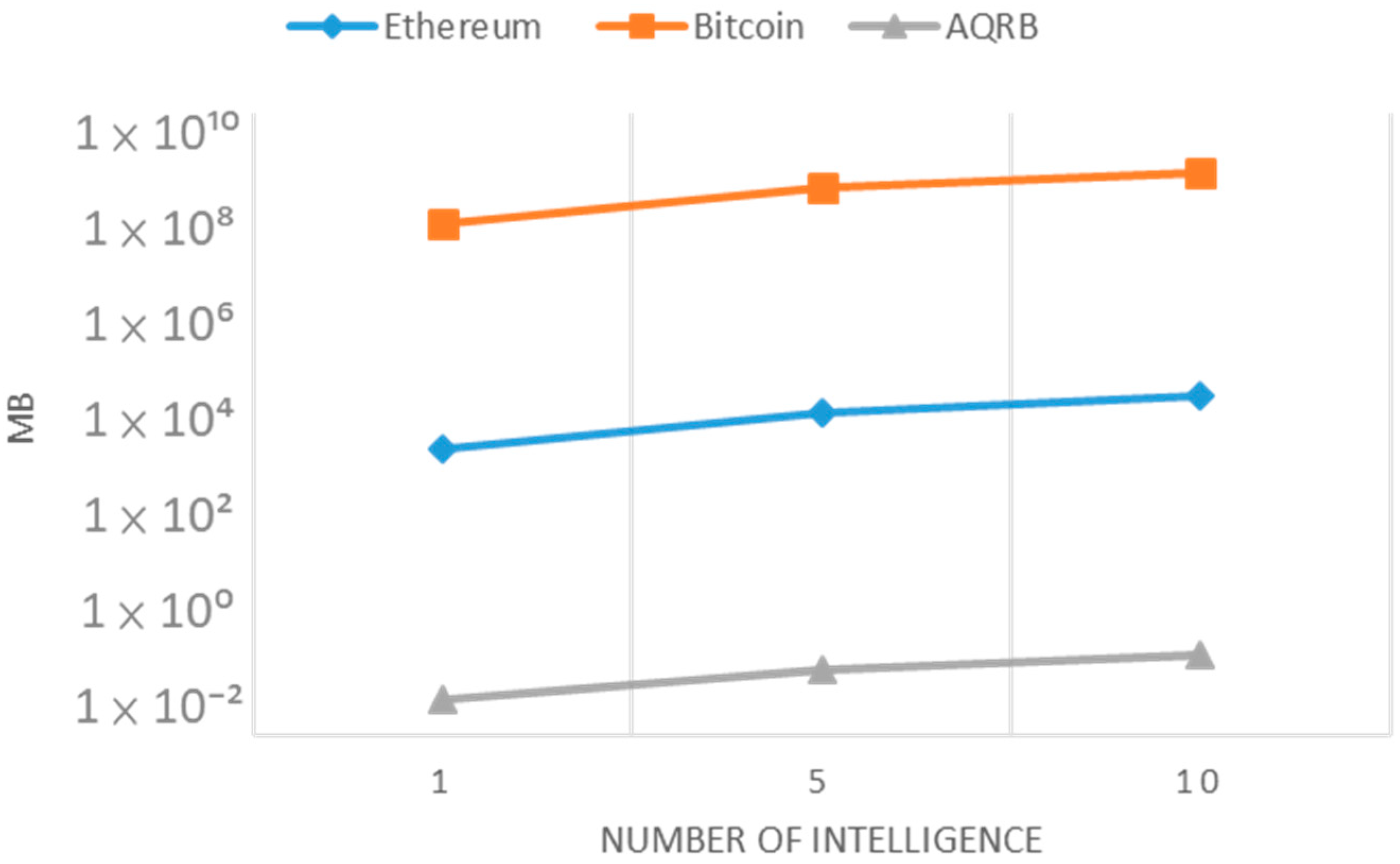
Figure 12 illustrates the advantage of AQRB in terms of storage cost compared to popular blockchain like Bitcoin and Ethereum. As of now, the record shows 46 million users, with an average block size of 1.5 MB for Bitcoin. Ethereum has 378,000 users with an average block size of 72,000 bits. In contrast, AQRB requires the storage of only those nodes that are pertinent to its operation, thereby achieving significant data storage efficiency.
5.2. Computational Resource Usage
In this subsection, we evaluated the computational resources by assessing the algorithms used, the time spent at each stage, and the differences in the number of and , using a data size of 1 MB.
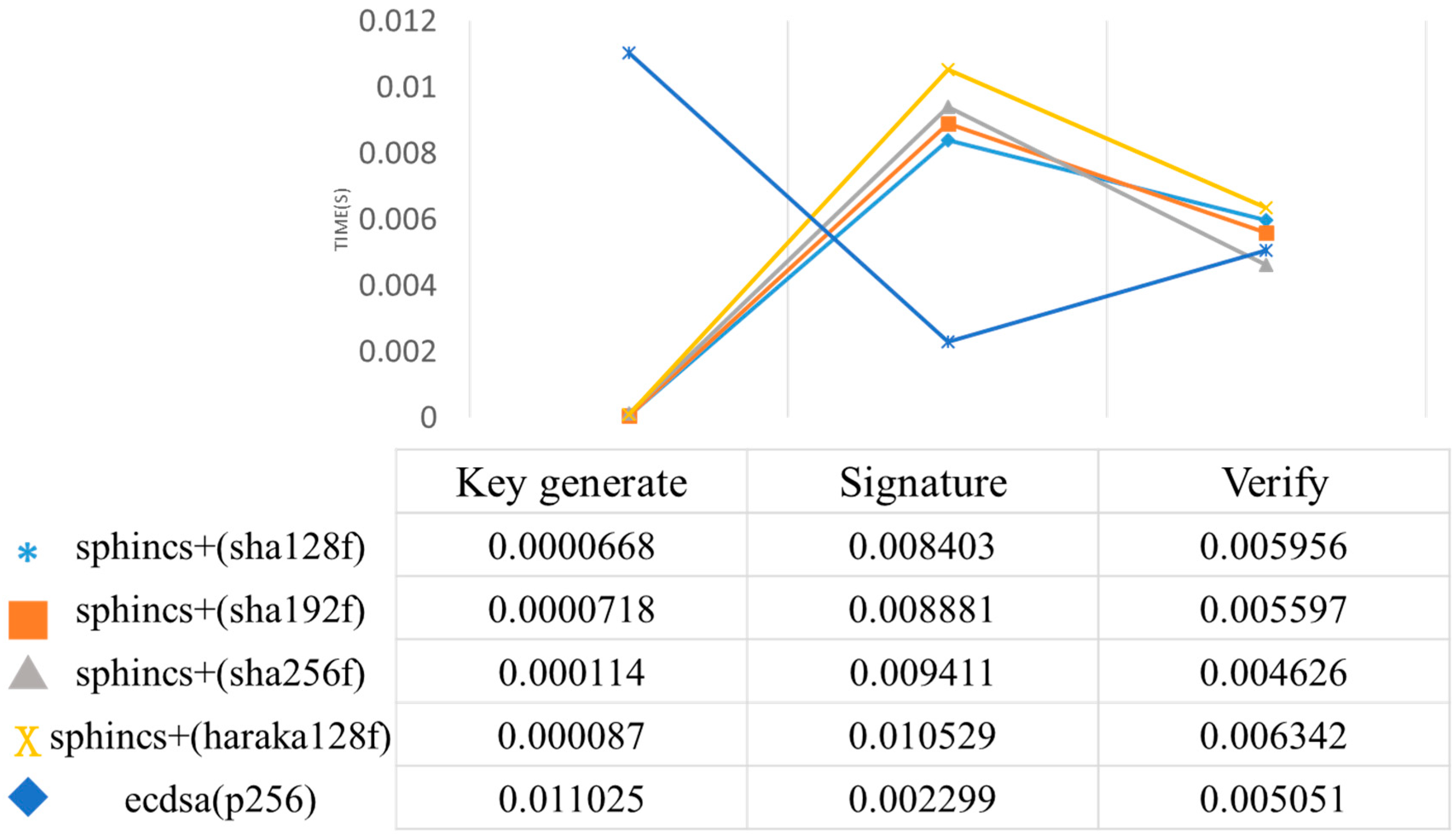
The computational performance comparisons between SPHINCS+ and ECDSA in terms of key generation, signature, and verification under the configurations of sha128f, sha192f, sha256f, and haraka128f against the P-256 curve of ECDSA are shown in
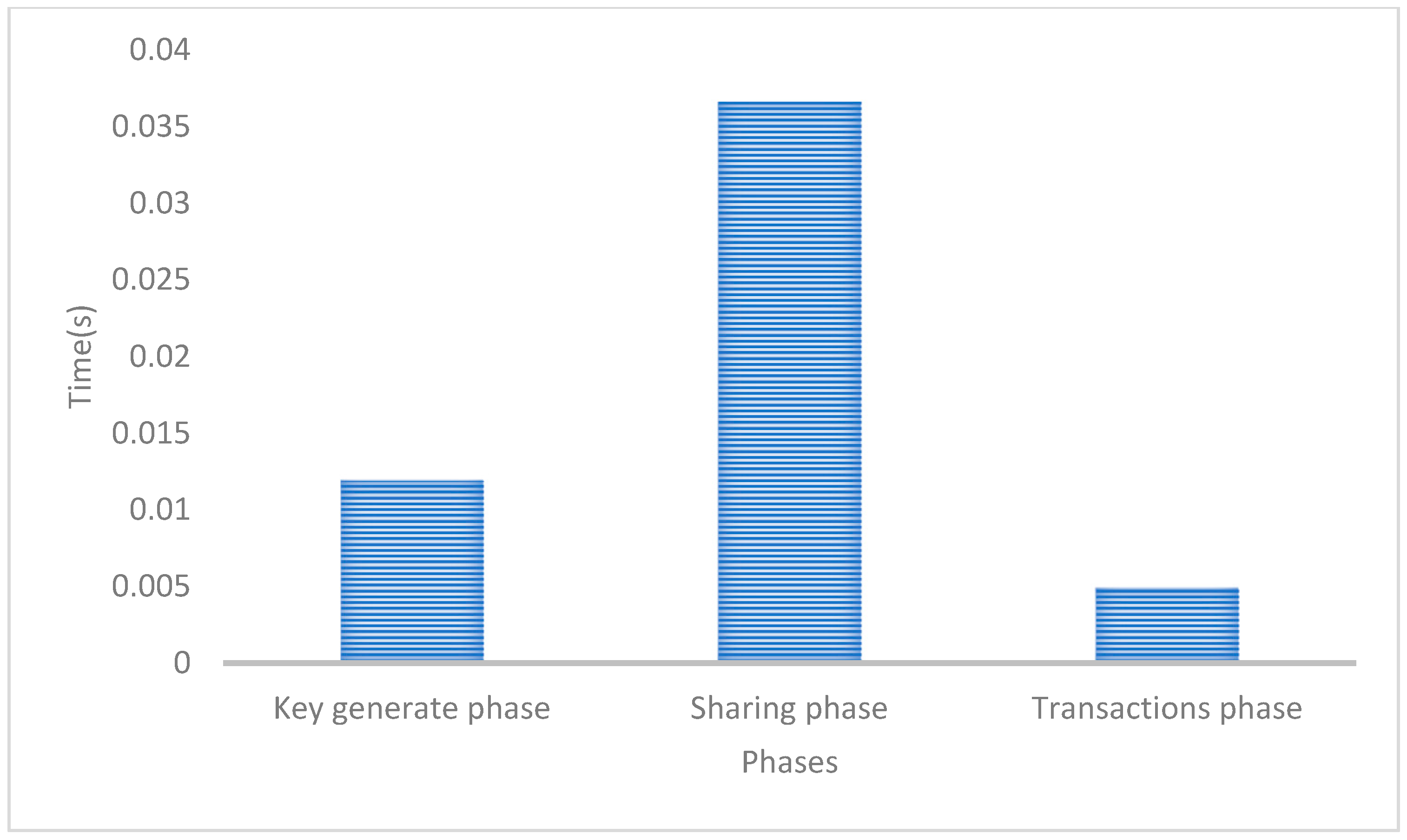
Figure 13. The table below the graph provides the specific times for each operation. Although SPHINCS+ exhibits slower performance in signing operations, its key generation and verification times are comparable to those of ECDSA. Moreover, SPHINCS+ offers the higher robustness against quantum attacks, ensuring a better level of protection. For a deep insight into the phase analysis, the time consumption at different stages is illustrated in
Figure 14.
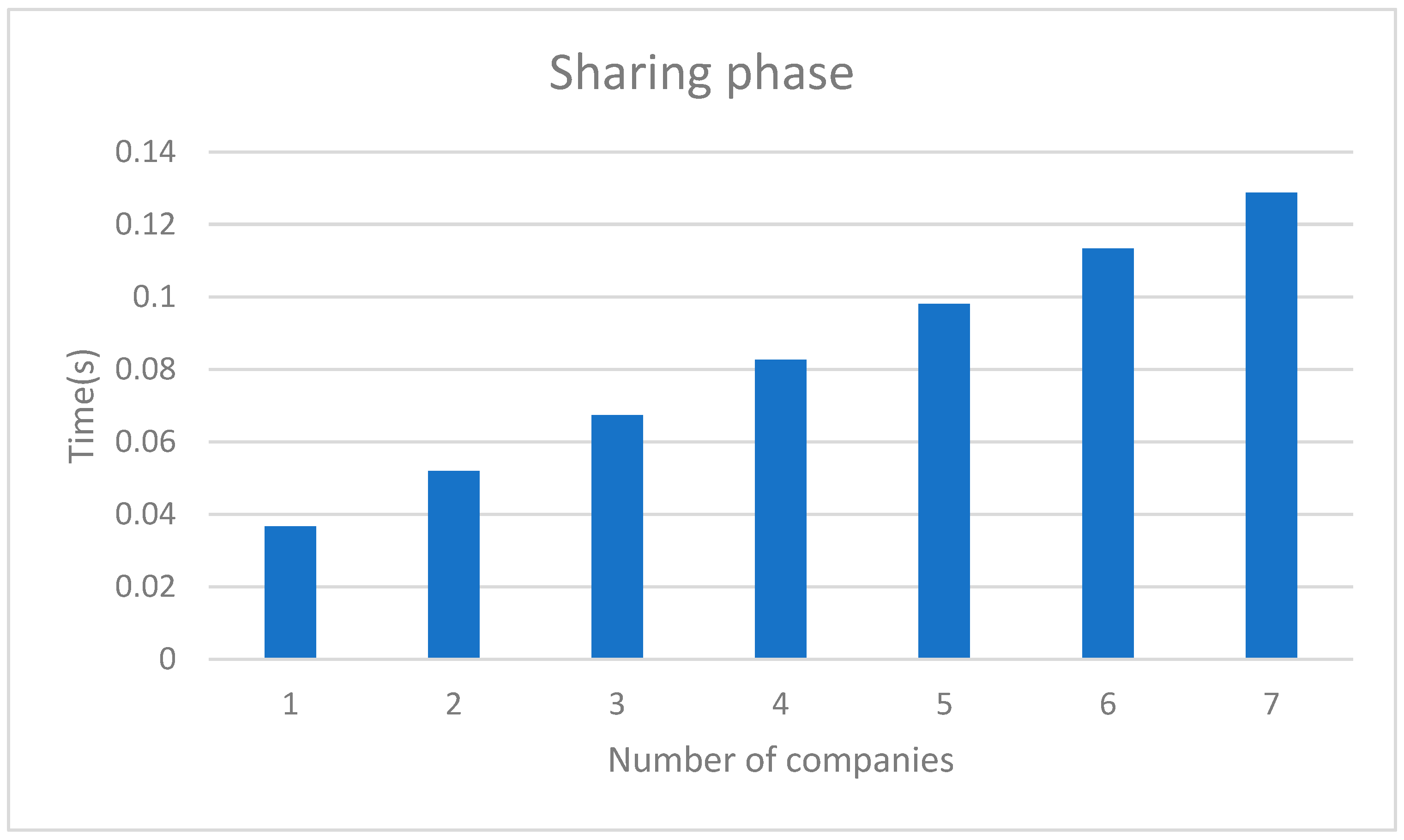
The further-detailed computational resource usage in the sharing phase by the number of companies maintaining the blockchain is displayed in
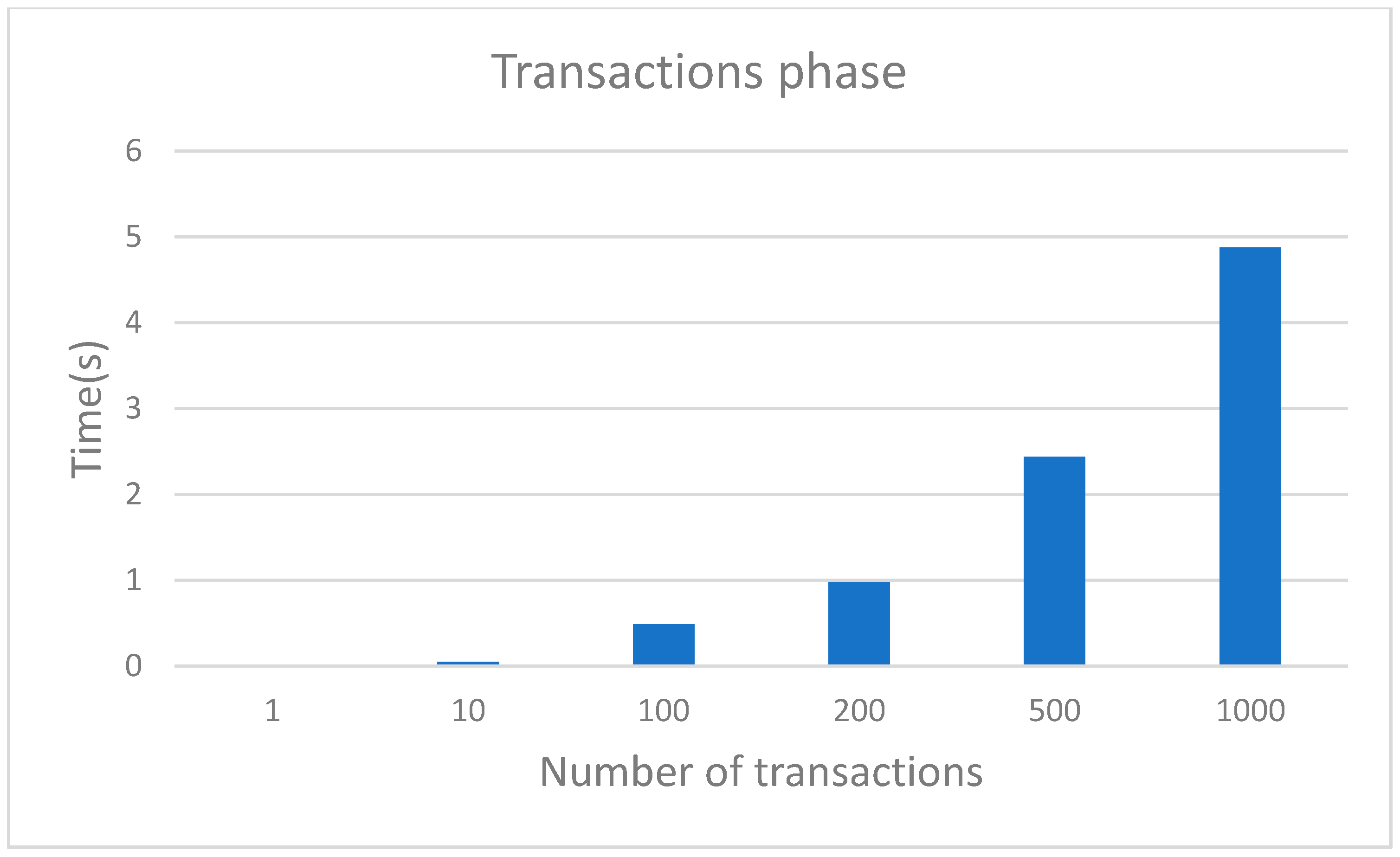
Figure 15. It is clear that the increasing number of companies has led to the linear increase of computational resources required for the sharing phase. The computational resource usage during the transactions phase relative to the number of transactions is depicted in
Figure 16. As the number of transactions increases, resource usage shows a significant rise, highlighting the computational cost associated with the higher transaction volumes.
These results have demonstrated a detailed analysis of the computational efficiency and resource requirements for different post-quantum cryptographic algorithms, evidencing the balance between security and performance in a blockchain environment.
6. Security Analysis
This section analyzes the security of the post-quantum blockchain model designed in AQRB. The characteristics of data security, resistance to quantum computing attacks, lightweight storage burden, sustainable maintenance, and consensus efficiency between related works and AQRB.
- □
Data Security
Concerning the blockchain-based [
16] and post-quantum blockchain studies [
17,
18], users must store data from all nodes. To tamper with the information, an attacker needs to control at least 51% of the network computational power; thus, ensuring data security as demonstrated in [
16,
17,
18].
On the contrary, the data are stored by the responsible maintaining enterprise once the intelligence sharing is initiated in AQRB. After the sharing phase, other enterprises can request the intelligence through the acquisition phase. According to the concept of network externalities, the value of a product increases with the number of users. Thus, as more entities seek the shared intelligence, its value escalates. Consequently, the more enterprises acquire the intelligence, the more enterprises are involved in maintaining it, thereby enhancing data security in AQRB. This approach ensures that data security is proportional to the value of the information, thereby achieving a robust data security model.
- □
Resistance to Quantum Computing Attacks
Resistance to quantum computing attacks refers to the ability of cryptographic algorithms to withstand attempts at decryption using quantum computers. In [
16], blockchain technology relies on ECDSA for its signature algorithm. However, ECDSA has been proven insecure under quantum computing attacks, rendering current blockchain applications vulnerable to such attacks. Recent studies [
17,
18] have investigated various post-quantum algorithms, including Falcon, Dilithium, and Rainbow. In July 2022, NIST has selected Falcon and Dilithium as parts of the post-quantum digital signature standards, while the Rainbow signature scheme has suffered from key recovery attacks, leading to its exclusion from the final list of recommended algorithms.
As with AQRB, SPHINCS+ is adopted as the foundational digital signature algorithm for constructing the blockchain, which is recognized by NIST as a post-quantum digital signature standard. Therefore, it inherits the capability to withstand quantum computing attacks. This adoption ensures that the blockchain is secure against the computational threats posed by quantum computers, offering a significant security advantage over traditional cryptographic methods.
- □
Lightweight Storage Burden
The characteristic of lightweight storage burden refers to reducing the amount of data that needs to be stored and synchronized across a blockchain network. Traditional blockchain architectures, including most post-quantum blockchain studies [
17,
18], primarily apply Proof-of-Work (PoW), Proof-of-Stake (PoS), or Proof-of-Activity (PoA) as consensus mechanisms. These systems require all participating nodes to store and synchronize the entire transaction history, regardless of their relevance to specific data exchanges. As a result, the storage requirements scale with the chain’s growth, imposing a heavy burden on all nodes.
In contrast, the Meepo framework proposed by Zheng et al. [
16] introduced a sharded consortium blockchain with multiple execution environments, allowing organizations to process and store only relevant transactional data within their own domains. This localized data handling effectively reduces the synchronization and storage load on individual nodes. Similarly, AQRB adopts an asynchronous dual blockchain model [
22], where data are maintained only by the involved enterprises. There is no need to synchronize all blocks across the network, thereby significantly reducing overall storage demands and enhancing scalability.
- □
Sustainable Maintenance
Sustainable maintenance in a blockchain concerns the system’s ability in maintaining its long-term operations and security without degrading performance. The essential operations of blockchain-based [
16] and post-quantum blockchain studies [
17,
18] are influenced by factors such as mining rewards, total currency, and transaction demands. Nodes may opt to perform transactions or mining exclusively. Such imbalanced behaviors, like solely validating or solely initiating data storage, will negatively impact the blockchain network, leading to its decline and failing to meet the requirements for sustainable maintenance.
In AQRB, the sharing and maintenance are interdependent. Before acquiring information from others, users must first share their intelligence. Units seeking intelligence must spend their earned reputation values and assist in maintaining data security. This mechanism ensures a balanced operation of the intelligence platform, preventing any participant from gaining intelligence without contributing. Thus, AQRB can guarantee that users either provide shared intelligence or contribute to blockchain verification, achieving sustainable maintenance.
- □
Consensus Efficiency
Consensus efficiency refers to the speed and effectiveness, with which a blockchain network can reach agreement on the validity of transactions. Traditional systems based on PoW and PoA [
16] provide high reliability but require global validation by a majority of the network’s computational resources. This results in significant time delays, particularly as network size and transaction volume increase. Post-quantum blockchain approaches [
17,
18] face additional challenges due to slower signature generation and verification speeds when using quantum-resistant algorithms such as hash-based or lattice-based schemes, further lowering consensus throughput.
Zheng et al. [
16] addressed this issue by proposing localized consensus mechanisms in their sharded architecture, where only the relevant shards participate in transaction validation, thereby reducing consensus latency. Building upon this idea, AQRB employs an asynchronous, contribution-balanced consensus mechanism. In this design, only the relevant parties are involved in each data sharing or acquisition event. This targeted participation dramatically improves consensus speed and efficiency, allowing the system to process transactions more effectively within the same time frame compared to traditional global consensus methods.
7. Conclusions
AQRB integrates a post-quantum, dual blockchain architecture to enable quantum-resistant computation. This architecture adopts SPHINCS+ and CRYSTALS-KYBER as its core cryptographic algorithms, ensuring robust data security against potential quantum attacks. The dual-chain design effectively reduces the burden of full network synchronization, thereby significantly lowering the overall storage requirements across the system. Furthermore, storage costs are dynamically adjusted based on real-time supply and demand conditions. Experimental evaluations demonstrate that the proposed architecture achieves superior efficiency and reduced storage consumption compared to conventional blockchain systems, highlighting its scalability and resource optimization capabilities. In addition, AQRB employs an asynchronous balancing contribution mechanism, wherein only relevant parties participate in each data sharing or acquisition event. This selective involvement enhances consensus efficiency by minimizing unnecessary communication overhead. Users are also required to contribute information before accessing new data and must expend earned reputation points to obtain information. This reputation-based access model contributes to maintaining data security and supports the sustainable operation of the blockchain ecosystem.
Looking ahead, research will focus on further optimizing the consensus efficiency and scalability of dual blockchain architectures, particularly in high-throughput or real-time applications. In addition, investigating hybrid cryptographic systems that integrate multiple post-quantum algorithms will enhance the system’s resilience against diverse quantum attack vectors. To strengthen privacy and data sovereignty, the integration of advanced privacy-preserving technologies such as zero-knowledge proofs, homomorphic encryption, and biometric authentication will be explored. These technologies aim to provide strong security protections without compromising user anonymity, making it feasible to build blockchain systems that can handle both scalability and post-quantum threats in real-world applications.