An ECC-Based Anonymous and Fast Handover Authentication Protocol for Internet of Vehicles
Abstract
1. Introduction
- A secure and efficient handover authentication protocol for the Internet of Vehicles is proposed, which can achieve mutual authentication and key negotiation between vehicles and Roadside Units (RSUs), and provide secure and reliable real-time communication. The proposed protocol is lightweight, with few message exchanges between entities, which effectively reduces communication and computational overhead and the risk of privacy leakage.
- The proposed protocol uses the time tree technology in trusted computing [5] to share some private data of vehicles, ensuring the security of vehicle authentication while improving the efficiency of authentication. When a vehicle moves across domains, it does not need to re-register and authenticate, reducing the cost of the vehicle in the authentication process.
- The proposed protocol implements “non-full key escrow”. The private key of the vehicle is generated by the TA and the vehicle separately. The TA only knows part of the vehicle’s private key. Even if the TA is malicious, the security of the vehicle’s private key can be guaranteed.
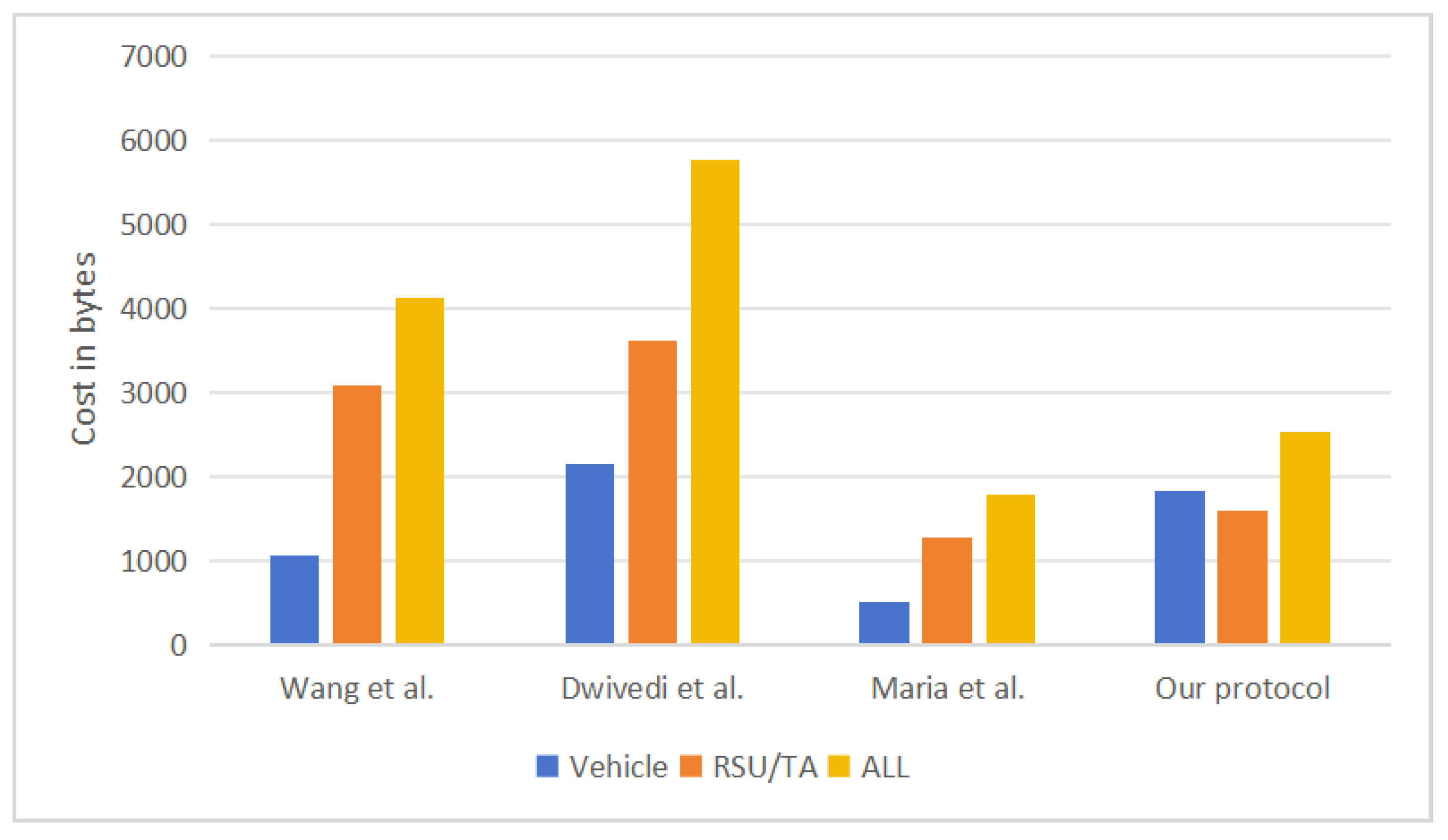
- Performance analysis shows that compared with existing protocols, the proposed protocol greatly reduces the communication overhead in the authentication process and the computational overhead when switching the authentication process.
2. Related Works
2.1. Cryptography-Based Identity Authentication Protocol
2.2. Challenge–Response-Based Authentication Protocol
2.3. Blockchain-Based Identity Authentication Protocol
| Protocol | Advantages | Limitations |
|---|---|---|
| Zhang et al. [6] | Low computation and communication overheads. | Vulnerable to impersonation attacks. |
| Xiong et al. [7] | Guaranteeing forward and backward secrecy. | Vulnerable to desynchronization attacks and privileged insider attacks. |
| Wang et al. [8] | Low computation and communication overheads. | Vulnerable to desynchronization attacks and RSU capture attacks. |
| Wang and Liu [9] | Low computation and communication overheads. | Vulnerable to privileged insider attacks and RSU capture attacks. |
| He et al. [10] | Low computation and communication overheads. | Not handover authentication. |
| Li et al. [11] | Low computation and communication overheads. | Not handover authentication. |
| Cao et al. [12] | Low computation and communication overheads. | Presence of key escrow problem. |
| Zhang et al. [14] | Resist physical capture attacks. | Complexity and high deployment overhead. |
| Ren et al. [15] | Not requiring key storage. | Complexity and high computation overhead. |
| Choi et al. [16] | Resist physical capture attacks. | Not handover authentication. |
| Mo et al. [17] | Resist physical emulation attacks and sensor node capture attacks. | Complexity and high computation overhead. |
| Yazdinejad et al. [18] | Cross-domain authentication. | Complexity and high computation overhead. |
| Zhang et al. [19] | Hide users’ sensitive information on the blockchain. | Complexity and high deployment overhead. |
| Shen et al. [20] | Hide users’ sensitive information on the blockchain. | Not handover authentication. |
| Son et al. [21] | Low computation and communication overheads. | Vulnerable to RSU capture attacks. |
| Yu et al. [22] | Low computation and communication overheads. | Vulnerable to vehicle capture attacks. |
| Gu et al. [23] | Low deployment overheads. | Complexity and high deployment overhead. |
| Kanjanapruthipong et al. [24] | Resist SPoF attacks. | Complexity and high deployment overhead. |
| Wang et al. [25] | Resist vehicle impersonation attacks and tracking attacks. | Complexity and high deployment overhead. |
3. Preliminaries
3.1. Elliptic Curve Cryptosystem
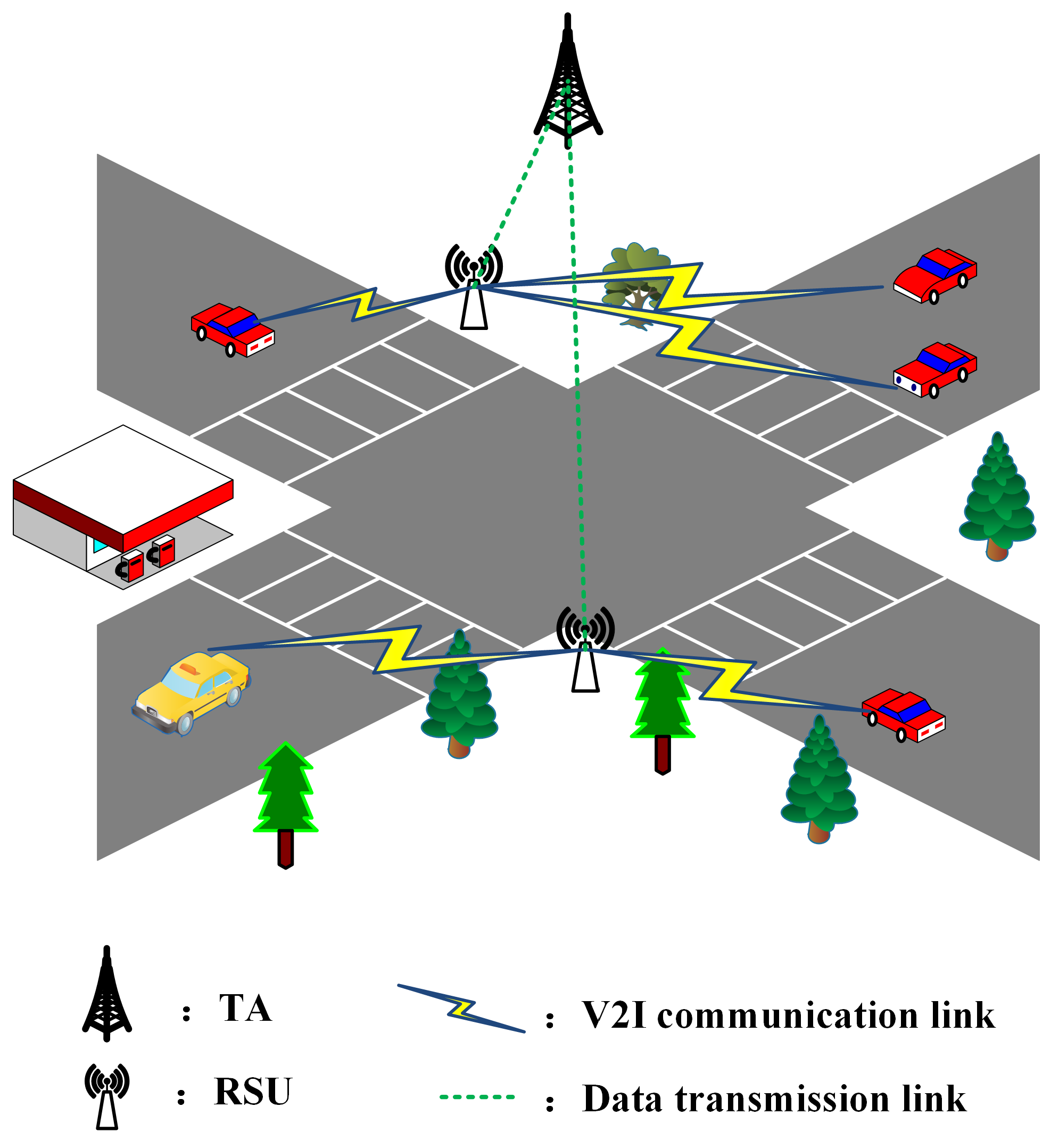
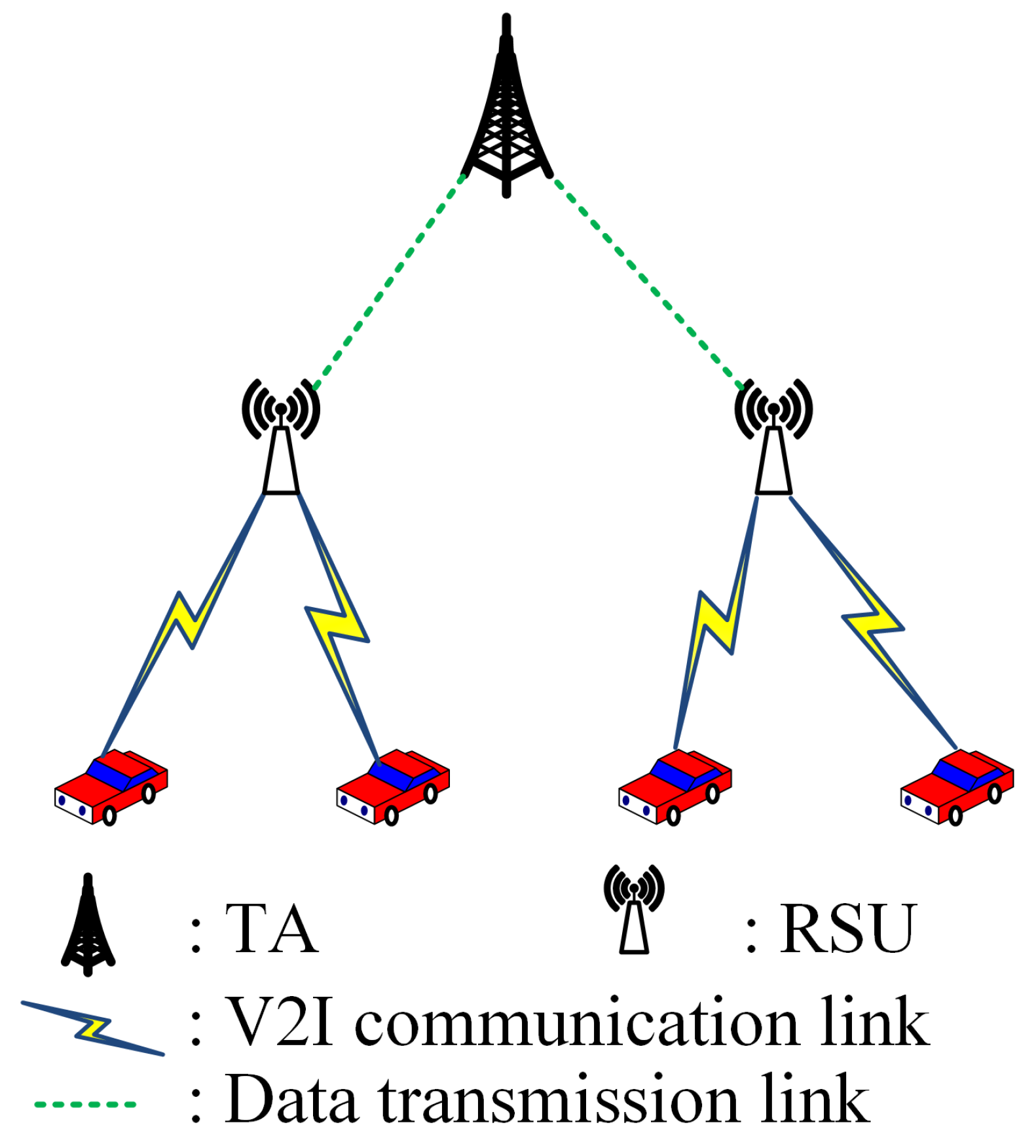
3.2. System Architecture
- TA: Adversaries possess the capability to eavesdrop on, modify, intercept, and replay all messages transmitted over a public communication channel. However, secure transmission mechanisms are designed to prevent adversaries from intercepting such information.
- RSU: Attackers may exploit intercepted sensitive parameters like vehicle control data, cryptographic keys and public information to initiate spoofing attacks or inject malicious messages.
- V: The attacker may exploit session keys or the session state within a specific session to compromise confidential credentials. However, if the current session key has been compromised in a particular session, the attacker remains incapable of deducing both past and future session keys.
3.3. Threat Model
- Adversaries possess the capability to eavesdrop on, modify, intercept, and replay all messages transmitted over a public communication channel. However, secure transmission mechanisms are designed to prevent adversaries from intercepting such information.
- Attackers may exploit intercepted sensitive parameters like vehicle control data, cryptographic keys and public information to initiate spoofing attacks or inject malicious messages.
- The attacker may exploit session keys or the session state within a specific session to compromise confidential credentials. However, if the current session key has been compromised in a particular session, the attacker remains incapable of deducing both past and future session keys.
- Adversaries cannot extract any information from the trusted computation tree.
3.4. Security Requirements
- Mutual Authentication: During the mutual authentication process, both parties mutually authenticate each other’s legitimacy and verify their authorization to conduct secure encrypted communications.
- Anonymity: During handover authentication procedures, ensuring the confidentiality of vehicle privacy information assumes paramount importance. Vehicle privacy data must not be transmitted in plaintext format, with access restricted exclusively to authorized entities possessing legitimate entitlements to such sensitive information.
- Unlinkability: During the handover authentication process, even if an attacker intercepts certain messages, it remains fundamentally infeasible to ascertain whether these messages originate from the same user terminal.
- Perfect Forward Secrecy: To protect the confidentiality of messages exchanged during prior sessions, the protocol must ensure the provision of perfect forward secrecy. This guarantees that even if an adversary obtains the long-term private keys of the participants, the session keys established in previous communications remain secure against compromise.
- Defend Against Various Common Attacks: To enhance the security of the authentication process, the proposed protocol should be capable of resisting common attacks such as vehicle impersonation attacks, RSU impersonation attacks, replay attacks, man-in-the-middle (MITM) attacks and other known attacks.
- Penalty and Exposure: Malicious vehicles compromising system security must be subject to sanctions by the Trusted Authority (TA) through cryptographic revocation mechanisms.
4. Proposed Protocol
4.1. Initialization Phase
4.2. Registration Phase
4.2.1. Vehicle Registration
- selects a secret parameter as a component of its private key, computes , and transmits a registration request message through the secure communication channel to the .
- Upon receiving the registration request from , the randomly selects , computes , generates a component of its partial private key, and transmits the response message through the secure communication channel.
- Upon receiving the response message from the , first sets , and verifies whether equation holds true. If the verification succeeds, proceeds to compute and generate the and . Finally, stores in its memory and publishes . If the verification fails, retransmits the registration request through the secure communication channel.
| Randomly choose | |
| Compute | |
| send | |
 | |
| Randomly choose u | |
| Compute | |
| send | |
 | |
| Compute | |
| Verify | |
| Compute | |
| store |
4.2.2. Registration
- randomly selects a secret parameter , computes , and transmits the registration message to the through the security channel.
- Upon receiving the registration information from , the selects a random number , computes , generates a partial private key for , and sends the response message .
- Upon receiving the information, first verifies whether holds true. If satisfied, generates the private key and public key . Subsequently, stores in memory and publishes its public key .
| Randomly choose | |
| Compute | |
| send | |
 | |
| Randomly choose v | |
| Compute | |
| send | |
 | |
| Verify | |
| Compute | |
| store |
4.3. The Initial Authentication Between Vehicles and and the Generation of Cryptographic Keys
- randomly selects a partial private key , computes , and uses the local ’s along with to derive , pseudonymous identifier and verification parameter . Subsequently, obtains the current timestamp and transmits the message to the .
- Upon receiving the message, the first verifies the freshness of through a condition check . If this condition is violated (indicating staleness), the terminates the current session. Otherwise, the retrieves the ’s true identity , sets , computes the ’s , and validates the message’s legitimacy and integrity via the verification equation . If the equation holds, the proceeds with the following steps: The generates a random number , computes and , establishes the session key , updates the pseudonymous identifier to prevent tracking, and encrypts it as . Subsequently, the generates and transmits to the . Finally, the stores in its memory. After updating, the default is set. Here, is a configured threshold representing the maximum number of messages allowed to pass through the before being discarded. If , the must re-register.
- Upon receiving a message from the , first verifies the ’s freshness, then validates the equation . If the equation holds, computes , recovers the pseudonymous identifier , and generates the session key ; otherwise, the resends the authentication request. Finally, replaces parameter with and stores the updated value in its memory.
| Randomly choose | |
| Compute | |
| send | |
 | |
| (via open channel) | |
| Check | |
| Compute | |
| Verify | |
| Randomly choose | |
| Compute | |
| send | |
| save | |
 | |
| (via open channel) | |
| Check | |
| Verify | |
| Compute | |
| save |
4.4. The Handover Authentication Between Vehicles and and the Generation of Cryptographic Keys
- In this step, randomly selects as a component of its private key, computes and , and transmits the message to .
- Upon receiving the message, the first assesses ’s freshness by checking . If this condition is violated, indicating is stale, the terminates the current session. Otherwise, it reconstructs based on from shared information and verifies vehicle validity by checking whether . Then the authenticates the message origin through the equation to ensure it originates from a legitimately authenticated vehicle. Upon successful validation, the proceeds as follows: generates random numbers , computes and , updates the pseudonymous with obfuscation to , generates and session key , and finally updates the information in trusted computing tree and transmits to .
- Upon receiving the message from , performs a freshness check firstly and verifies the equation . If the equation holds true, proceeds to compute , generate the session key , and subsequently update its pseudonymous .
| Randomly choose | |
| Compute | |
| send | |
 | |
| Check | |
| Retrieve | |
| Verify | |
| Check | |
| Randomly choose | |
| Compute | |
| Generate | |
| Update | |
| send | |
 | |
| Check | |
| Verify | |
| Compute | |
| Generate | |
| Update |
4.5. The Revocation of Malicious Vehicles in Vehicular Networks
5. Security Analysis
- Untraceability: In the process of authentication, the protocol proposed in this paper changes the parameters of each authentication randomly and contains dynamic timestamps. The adversary cannot effectively link related vehicles based on some random numbers. Therefore, this protocol is untraceable.
- Anonymity of vehicle identity: When a vehicle attempts to communicate with an RSU or other vehicles, it will use a temporary pseudonym instead of its real identity to transmit on a public channel. Without the master private key of the TA or RSU, the attacker cannot obtain the real identity of the vehicle. Only the TA or RSU can reveal the real information of the vehicle. The vehicle can update autonomously every time it communicates (rather than being generated by a trusted third party like other protocols).
- Perfect forward secrecy: Even if an adversary intercepts messages such as and , deriving the session key (SK) remains infeasible. This is because SK is computed using a secret random value generated by the client. Recovering the SK from the intercepted data would require solving the elliptic curve discrete logarithm problem (ECDLP), which is widely regarded as computationally intractable. As a result, the protocol achieves perfect forward secrecy, ensuring that past session keys remain secure even if long-term private keys are compromised.
- Resistance to DDoS attacks: The system architecture employs multiple registration servers, which improves fault tolerance and enhances overall availability. Due to the protocol’s low transmission and processing overhead, the system remains responsive even when subjected to a high volume of incoming requests. This design allows it to effectively absorb and mitigate the impact of distributed denial-of-service (DDoS) attacks, ensuring continued service for legitimate users.
- Resistance to replay attacks: The protocol prevents adversaries from reusing previously intercepted messages to gain unauthorized access. Each message carries a timestamp T, allowing the server to verify its timeliness. Messages with outdated or invalid timestamps are recognized as replays and are subsequently rejected, thereby mitigating the risk of replay attacks.
- Resistance to man-in-the-middle attacks: As mentioned above, this protocol can prevent ’s identity , random number , and secret parameter C from being recovered by malicious opponents. And this protocol is based on the mutual authentication feature and can resist man-in-the-middle attacks.
- Resistance to imitation attacks: Malicious attackers cannot obtain both the TA’s master private key and the partial private key generated by the vehicle at the same time, so the attacker cannot successfully imitate a legitimate vehicle to generate a signature, and therefore cannot successfully launch a vehicle simulation attack. Malicious attackers will try to launch RSU imitation attacks to obtain vehicle-related privacy information. However, the attacker cannot generate a legitimate sum, so they cannot successfully simulate a legitimate RSU.
- Resistance to single point failure attack: A malicious attacker can launch a single point failure attack on . However, the registered vehicle information is directly written into the trusted computing tree instead of ’s memory, so the adversary cannot obtain the registered vehicle information. The exit of a certain will not change and , so other do not need to regenerate . The multi-registration server structure will not cause the vehicle to fail to register due to a single , because other servers can also register for .
6. Performance Analysis
6.1. Computational Cost
6.2. Communication Cost
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Oladimeji, D.; Gupta, K.; Kose, N.A.; Gundogan, K.; Ge, L.; Liang, F. Smart transportation: An overview of technologies and applications. Sensors 2023, 23, 3880. [Google Scholar] [CrossRef] [PubMed]
- Yuan, M.; Xiao, Y. PMAKA-IoV: A Physical Unclonable Function (PUF)-Based Multi-Factor Authentication and Key Agreement Protocol for Internet of Vehicles. Information 2025, 16, 404. [Google Scholar] [CrossRef]
- Khezri, E.; Hassanzadeh, H.; Yahya, R.O.; Mir, M. Security challenges in internet of vehicles (IoV) for ITS: A survey. Tsinghua Sci. Technol. 2025, 30, 1700–1723. [Google Scholar] [CrossRef]
- Singh, A.; Rani, P.; Ramesh, J.V.N.; Athawale, S.V.; Alkhayyat, A.H.; Aledaily, A.N.; Prola, T.A.; Sharma, R. Blockchain-based lightweight authentication protocol for next-generation trustworthy internet of vehicles communication. IEEE Trans. Consum. Electron. 2024, 70, 4898–4907. [Google Scholar] [CrossRef]
- Tian, J.; Chang, F. Trusted cloud platform management model based on TPM alliance. J. Commun. 2016, 37, 1–10. [Google Scholar]
- Zhang, J.; Cui, J.; Zhong, H.; Chen, Z.; Liu, L. PA-CRT: Chinese remainder theorem based conditional privacy-preserving authentication scheme in vehicular ad-hoc networks. IEEE Trans. Dependable Secur. Comput. 2019, 18, 722–735. [Google Scholar] [CrossRef]
- Xiong, H.; Chen, J.; Mei, Q.; Zhao, Y. Conditional privacy-preserving authentication protocol with dynamic membership updating for VANETs. IEEE Trans. Dependable Secur. Comput. 2020, 19, 2089–2104. [Google Scholar] [CrossRef]
- Wang, C.; Huang, R.; Shen, J.; Liu, J.; Vijayakumar, P.; Kumar, N. A novel lightweight authentication protocol for emergency vehicle avoidance in VANETs. IEEE Internet Things J. 2021, 8, 14248–14257. [Google Scholar] [CrossRef]
- Wang, P.; Liu, Y. SEMA: Secure and efficient message authentication protocol for VANETs. IEEE Syst. J. 2021, 15, 846–855. [Google Scholar] [CrossRef]
- He, Z.; Zheng, Y.; Chen, S.; Du, Z.; Liu, S.; Zhang, K. Security-Enhanced Lightweight Authentication Key-Agreement Protocol for Unmanned Aerial Vehicle Communication. Appl. Sci. 2025, 15, 4680. [Google Scholar] [CrossRef]
- Li, M.; Hu, S. A Lightweight ECC-Based Authentication and Key Agreement Protocol for IoT with Dynamic Authentication Credentials. Sensors 2024, 24, 7967. [Google Scholar] [CrossRef] [PubMed]
- Cao, J.; Ma, M.; Fu, Y.; Li, H.; Zhang, Y. CPPHA: Capability-based privacy-protection handover authentication mechanism for SDN-based 5G HetNets. IEEE Trans. Dependable Secur. Comput. 2019, 18, 1182–1195. [Google Scholar] [CrossRef]
- Duan, X.; Wang, X. Authentication handover and privacy protection in 5G hetnets using software-defined networking. IEEE Commun. Mag. 2015, 53, 28–35. [Google Scholar] [CrossRef]
- Zhang, L.; Xu, J.; Obaidat, M.S.; Li, X.; Vijayakumar, P. A PUF-based lightweight authentication and key agreement protocol for smart UAV networks. IET Commun. 2022, 16, 1142–1159. [Google Scholar] [CrossRef]
- Ren, X.; Cao, J.; Ma, R.; Luo, Y.; Guan, J.; Zhang, Y.; Li, H. A novel access and handover authentication scheme in UAV-aided satellite-terrestrial integration networks enabling 5G. IEEE Trans. Netw. Serv. Manag. 2023, 20, 3880–3899. [Google Scholar] [CrossRef]
- Choi, J.; Son, S.; Kwon, D.; Park, Y. A PUF-Based Secure Authentication and Key Agreement Scheme for the Internet of Drones. Sensors 2025, 25, 982. [Google Scholar] [CrossRef]
- Mo, J.; Zhang, Z.; Lin, Y. A Practically Secure Two-Factor and Mutual Authentication Protocol for Distributed Wireless Sensor Networks Using PUF. Electronics 2024, 14, 10. [Google Scholar] [CrossRef]
- Yazdinejad, A.; Parizi, R.M.; Dehghantanha, A.; Choo, K.K.R. Blockchain-enabled authentication handover with efficient privacy protection in SDN-based 5G networks. IEEE Trans. Netw. Sci. Eng. 2019, 8, 1120–1132. [Google Scholar] [CrossRef]
- Zhang, Y.; Deng, R.H.; Bertino, E.; Zheng, D. Robust and universal seamless handover authentication in 5G HetNets. IEEE Trans. Dependable Secur. Comput. 2019, 18, 858–874. [Google Scholar] [CrossRef]
- Shen, M.; Liu, H.; Zhu, L.; Xu, K.; Yu, H.; Du, X.; Guizani, M. Blockchain-assisted secure device authentication for cross-domain industrial IoT. IEEE J. Sel. Areas Commun. 2020, 38, 942–954. [Google Scholar] [CrossRef]
- Son, S.; Lee, J.; Park, Y.; Park, Y.; Das, A.K. Design of blockchain-based lightweight V2I handover authentication protocol for VANET. IEEE Trans. Netw. Sci. Eng. 2022, 9, 1346–1358. [Google Scholar] [CrossRef]
- Yu, F.; Ma, M.; Li, X. A blockchain-assisted seamless handover authentication for V2I communication in 5G wireless networks. In Proceedings of the ICC 2021-IEEE International Conference on Communications, Montreal, QC, Canada, 14–23 June 2021; pp. 1–6. [Google Scholar]
- Gu, H.; Shang, J.; Wang, P.; Mi, J.; Bhattacharjya, A. A Secure Protocol Authentication Method Based on the Strand Space Model for Blockchain-Based Industrial Internet of Things. Symmetry 2024, 16, 851. [Google Scholar] [CrossRef]
- Kanjanapruthipong, W.; Boonkrong, S. Blockchain-Based Decentralised Authentication in Closed Environments. Future Internet 2025, 17, 98. [Google Scholar] [CrossRef]
- Wang, S.; Wu, Y.; Wen, K.; Zhou, X.; Hu, B.; Xie, Q. An Improved Blockchain-Based Lightweight Vehicle-to-Infrastructure Handover Authentication Protocol for Vehicular Ad Hoc Networks. Mathematics 2025, 13, 1118. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Universally composable notions of key exchange and secure channels. In Proceedings of the Advances in Cryptology—EUROCRYPT 2002: International Conference on the Theory and Applications of Cryptographic Techniques, Amsterdam, The Netherlands, 28 April–2 May 2002; Proceedings 21. Springer: Berlin/Heidelberg, Germany, 2002; pp. 337–351. [Google Scholar]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Wang, C.; Shen, J.; Lai, J.F.; Liu, J. B-TSCA: Blockchain assisted trustworthiness scalable computation for V2I authentication in VANETs. IEEE Trans. Emerg. Top. Comput. 2020, 9, 1386–1396. [Google Scholar] [CrossRef]
- Dwivedi, S.K.; Amin, R.; Vollala, S.; Khan, M.K. B-HAS: Blockchain-assisted efficient handover authentication and secure communication protocol in VANETs. IEEE Trans. Netw. Sci. Eng. 2023, 10, 3491–3504. [Google Scholar] [CrossRef]
- Maria, A.; Pandi, V.; Lazarus, J.D.; Karuppiah, M.; Christo, M.S. BBAAS: Blockchain-based anonymous authentication scheme for providing secure communication in VANETs. Secur. Commun. Netw. 2021, 2021, 6679882. [Google Scholar] [CrossRef]
- Lee, C.C.; Chen, C.T.; Wu, P.H.; Chen, T.Y. Three-factor control protocol based on elliptic curve cryptosystem for universal serial bus mass storage devices. IET Comput. Digit. Tech. 2013, 7, 48–55. [Google Scholar] [CrossRef]
| Notation | Description |
|---|---|
| The identity of | |
| The identity of | |
| Temporary pseudonym of | |
| Master secret key and public key of | |
| Secret key and public key of | |
| Secret key and public key of | |
| A cyclic additive group of an order q | |
| P | A generator of |
| Prime numbers of | |
| Timestamp | |
| A one-way hash algorithm: | |
| l | The output length of |
| Concatenation operation | |
| Bitwise XOR operation |
| Security Attributes | [28] | [29] | [30] | Our Protocol |
|---|---|---|---|---|
| ✓ | ✓ | ✓ | ✓ | |
| ✓ | ✓ | ✓ | ✓ | |
| ✓ | ✓ | ✗ | ✓ | |
| ✓ | ✓ | ✓ | ✓ | |
| ✓ | ✓ | ✓ | ✓ | |
| ✓ | ✗ | ✓ | ✓ | |
| ✓ | ✓ | ✓ | ✓ | |
| ✗ | ✗ | ✗ | ✓ |
| Symbol | Operation | Execution Time (ms) |
|---|---|---|
| One-way hash function | 0.32 | |
| Elliptic curve scalar multiplication | 17.10 | |
| Exponentiation operation | 19.20 | |
| Bilinear pairing operation | 42.11 | |
| Modular multiplication operation | 0.88 | |
| Modular inverse operation | 2.64 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kong, Y.; Tian, J. An ECC-Based Anonymous and Fast Handover Authentication Protocol for Internet of Vehicles. Appl. Sci. 2025, 15, 5894. https://doi.org/10.3390/app15115894
Kong Y, Tian J. An ECC-Based Anonymous and Fast Handover Authentication Protocol for Internet of Vehicles. Applied Sciences. 2025; 15(11):5894. https://doi.org/10.3390/app15115894
Chicago/Turabian StyleKong, Yiming, and Junfeng Tian. 2025. "An ECC-Based Anonymous and Fast Handover Authentication Protocol for Internet of Vehicles" Applied Sciences 15, no. 11: 5894. https://doi.org/10.3390/app15115894
APA StyleKong, Y., & Tian, J. (2025). An ECC-Based Anonymous and Fast Handover Authentication Protocol for Internet of Vehicles. Applied Sciences, 15(11), 5894. https://doi.org/10.3390/app15115894