Abstract
As an important part of the Internet of Things, the Internet of Vehicles (IoV) has achieved efficient interconnection and collaboration between vehicles and road infrastructure, and between vehicles through advanced information and communication technologies. However, the high-speed movement of vehicles has generated a large number of cross-domain behaviors, which has greatly increased the number of authentications. Existing authentication protocols face challenges such as high cost, high computational overhead, and easy eavesdropping, interception, or tampering. To this end, this paper proposes an ECC-based IoV secure and efficient handover authentication protocol. The protocol adopts a “non-full key escrow” mechanism. The private key of the vehicle is jointly generated by the Trusted Authority (TA) and the vehicle. The TA only holds part of the private key. Even if the TA is malicious, the security of the vehicle’s private key can be ensured. At the same time, the proposed protocol uses the time tree technology in trusted computing to share part of the vehicle’s private data, which not only ensures the security of authentication, but also improves the efficiency of authentication, and solves the high-latency problem caused by the use of blockchain in previous protocols. When the vehicle moves across domains, there is no need to re-register and authenticate, which reduces the authentication overhead. Compared with existing protocols, this protocol is lightweight in both computational and communication overheads, effectively solving the problem of excessive cost.
1. Introduction
As the concept of smart cities is accelerating, the Internet of Things (IoT) technology has evolved from a single-scenario application to a core driving force for promoting urban digital transformation. It is widely used in smart healthcare, intelligent transportation systems (ITSs) and other fields [1]. As an important component of intelligent transportation systems (ITSs), the Internet of Vehicles (IoV) leverages advanced information and communication technologies to enable efficient interconnection and collaboration between vehicles and road infrastructure, and between vehicles themselves, bringing revolutionary changes to ITSs through its rapid development [2]. Due to the openness of the IoV communication architecture, the system faces security threats such as identity impersonation attacks and privacy data leakage [3]. For example, the information interaction between entities faces multi-dimensional security threats such as eavesdropping, interception and tampering by the enemy. Therefore, the identity authentication mechanism has become the core mechanism to ensure the security of the IoV system. It verifies the legitimate identity of the vehicle/infrastructure through cryptographic technology, prevents spoofing attacks by malicious edge nodes [4], and ensures secure and reliable real-time communication between entities in the system.
Figure 1 depicts the process of a vehicle communicating with infrastructure while driving in an IoV scenario. However, with the high-speed movement and frequent cross-domain behavior of vehicles, the number of authentication requests has increased dramatically. This not only places higher demands on the carrying capacity of the communication network, but also poses severe challenges to the performance and efficiency of the authentication protocol. How to achieve fast and secure cross-domain authentication in an IoV environment has become one of the key issues that need to be urgently addressed in the IoV field. In recent years, the academic community has made breakthrough progress in multiple dimensions in the field of vehicle network identity authentication protocols, but still faces many security and efficiency challenges. First, research on authentication protocols based on cryptographic technology, such as protocols based on public key infrastructure (PKI), can provide high security, but they rely on certificates to verify public keys. Errors in certificate authorities can undermine the entire PKI trust chain, which brings challenges to certificate management and increases the complexity and cost of large networks. In addition, in identity-based protocols, although some limitations of PKI-based authentication schemes that require the generation and storage of a large number of certificates have been solved, the user’s private key is usually generated by a trusted third party. When the third party is attacked or abused, it will bring privacy and security risks and face the challenge of public key revocation. There are also some certificateless protocols that use complex bilinear pairing or blockchain, which leads to communication delays, excessive resource consumption, and low system efficiency, and they are vulnerable to man-in-the-middle attacks or user key attacks. It can be seen that designing a vehicle authentication protocol that protects vehicle privacy and security while reducing the system’s computational overhead and communication overhead is still a work with extremely high research value.
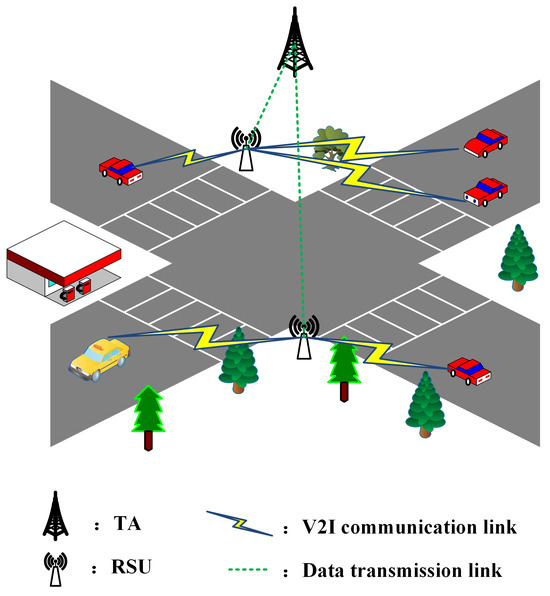
Figure 1.
An Internet of Vehicles scenario.
To address these challenges, this paper proposes a secure and efficient handover authentication protocol. The main contents are as follows:
- A secure and efficient handover authentication protocol for the Internet of Vehicles is proposed, which can achieve mutual authentication and key negotiation between vehicles and Roadside Units (RSUs), and provide secure and reliable real-time communication. The proposed protocol is lightweight, with few message exchanges between entities, which effectively reduces communication and computational overhead and the risk of privacy leakage.
- The proposed protocol uses the time tree technology in trusted computing [5] to share some private data of vehicles, ensuring the security of vehicle authentication while improving the efficiency of authentication. When a vehicle moves across domains, it does not need to re-register and authenticate, reducing the cost of the vehicle in the authentication process.
- The proposed protocol implements “non-full key escrow”. The private key of the vehicle is generated by the TA and the vehicle separately. The TA only knows part of the vehicle’s private key. Even if the TA is malicious, the security of the vehicle’s private key can be guaranteed.
- Performance analysis shows that compared with existing protocols, the proposed protocol greatly reduces the communication overhead in the authentication process and the computational overhead when switching the authentication process.
The rest of the paper is structured as follows. Section 2 reviews existing authentication protocols. Section 3 introduces the preliminaries, including the system architecture, threat assumptions, and security requirements. Section 4 details the proposed protocol. Section 5 and Section 6 present the security and performance evaluations, respectively. Finally, Section 7 concludes the paper.
2. Related Works
In recent years, scholars have conducted in-depth research on identity authentication protocols to address the problems of rapid vehicle movement and frequent cross-domain communication in the Internet of Vehicles environment, and have proposed a variety of authentication schemes from different perspectives. Due to the limited computing and storage capabilities of devices in the Internet of Vehicles, the designed protocol cannot use overly complex algorithms. In order to address the problem of excessive authentication overhead in the Internet of Vehicles, scholars have proposed many feasible lightweight identity authentication schemes. Next, we will summarize the existing authentication protocol work for protecting the security of the Internet of Vehicles system to achieve vehicle V2I communication from the perspectives of Internet of Vehicles identity authentication schemes based on cryptography, challenge–response, and blockchain. Table 1 compares the advantages and limitations of existing protocols.
2.1. Cryptography-Based Identity Authentication Protocol
Zhang et al. [6] proposed a conditional privacy-preserving authentication scheme (PA-CRT) based on the Chinese Remainder Theorem (CRT) to secure communications in vehicular ad hoc networks (VANETs). By using CRT to assist TAs in the dynamic generation and distribution of group keys, the scheme enhances both the security and efficiency of the system. Subsequently, Xiong et al. [7] developed a CRT-based authentication protocol that supports dynamic group membership. The protocol addresses key issues such as message authentication, anonymity, and conditional privacy, while also ensuring forward and backward security, thereby responding effectively to the limitations of previous approaches. In 2021, Wang et al. [8] introduced a lightweight authentication protocol designed to improve the efficiency of emergency vehicle clearance in the IoV. After completing initial authentication with an RSU, an emergency vehicle can subsequently authenticate with other RSUs more quickly, thereby reducing computational overhead during transit. Subsequently, Wang and Liu [9] proposed a secure and efficient message authentication protocol (SEMA), which combines the advantages of pseudonym-based and group-based schemes to support efficient bidirectional authentication between vehicles and RSUs in VANETs. Despite their advantages, these protocols are still exposed to certain security risks, including desynchronization attacks, attacks by privileged insiders, and the compromise of RSUs. To ensure secure wireless communication between unmanned aerial vehicles (UAVs) and ground stations, He et al. [10] developed a lightweight key agreement protocol capable of maintaining security even in the event of temporary session information leakage, while keeping computational costs low. To address the performance overhead during protocol execution, Li et al. [11] proposed an authentication and key agreement scheme based on ECC. Their approach employs a dynamic credential synchronization framework, using dynamic authentication credentials in place of temporary public keys or static sender credentials to provide both efficiency and anonymity.
2.2. Challenge–Response-Based Authentication Protocol
Challenge–response protects data transmission between the client and server, thereby establishing a secure session key. Cao et al. [12] proposed a capability-based, privacy-preserving switching authentication mechanism for 5G heterogeneous networks (HetNets), building on Duan’s scheme [13] by incorporating user capability information with software-defined networking (SDN) technology. The scheme enables efficient authentication and key agreement between user equipment (UE) and base stations. However, it relies on fixed UE credentials and lacks a mechanism for credential updates, posing potential security risks. To strengthen resistance against physical capture attacks, Zhang et al. [14] designed a lightweight two-stage authentication and key agreement protocol for drones, integrating an embedded physical unclonable function (PUF) to ensure secure communication. Ren et al. [15] also introduced a PUF-based access authentication scheme involving a dual authentication process between drones and ground terminals. Their approach supports mutual authentication, key agreement, and privacy protection, while eliminating the need for key storage and offering robustness against physical attacks. To address the issue of drones being vulnerable to capture during operation, Choi et al. [16] proposed a secure and lightweight authentication and key agreement scheme based on hash functions and XOR operations. The scheme leverages the unique properties of PUFs to defend against various security threats, especially physical capture attacks. Aiming to overcome the limitations of many authentication schemes that do not adequately resist physical emulation and smart card loss attacks, Mo et al. [17] presented a two-factor authentication protocol. This protocol employs PUF technology to prevent physical emulation and sensor node capture, while also improving the efficiency and security of session key management. While the challenge–response handover authentication protocol offers strong robustness, its high computational and storage demands make it impractical for resource-limited IoV environments.
2.3. Blockchain-Based Identity Authentication Protocol
Blockchain offers unique advantages and is widely applied across various fields. It enables cross-domain authentication and key management without relying on a central Trusted Authority, simplifying the authentication process. As a result, numerous blockchain-based identity authentication protocols have been proposed to ensure secure and reliable access.

Table 1.
Advantages and limitations of existing protocols.
Table 1.
Advantages and limitations of existing protocols.
| Protocol | Advantages | Limitations |
|---|---|---|
| Zhang et al. [6] | Low computation and communication overheads. | Vulnerable to impersonation attacks. |
| Xiong et al. [7] | Guaranteeing forward and backward secrecy. | Vulnerable to desynchronization attacks and privileged insider attacks. |
| Wang et al. [8] | Low computation and communication overheads. | Vulnerable to desynchronization attacks and RSU capture attacks. |
| Wang and Liu [9] | Low computation and communication overheads. | Vulnerable to privileged insider attacks and RSU capture attacks. |
| He et al. [10] | Low computation and communication overheads. | Not handover authentication. |
| Li et al. [11] | Low computation and communication overheads. | Not handover authentication. |
| Cao et al. [12] | Low computation and communication overheads. | Presence of key escrow problem. |
| Zhang et al. [14] | Resist physical capture attacks. | Complexity and high deployment overhead. |
| Ren et al. [15] | Not requiring key storage. | Complexity and high computation overhead. |
| Choi et al. [16] | Resist physical capture attacks. | Not handover authentication. |
| Mo et al. [17] | Resist physical emulation attacks and sensor node capture attacks. | Complexity and high computation overhead. |
| Yazdinejad et al. [18] | Cross-domain authentication. | Complexity and high computation overhead. |
| Zhang et al. [19] | Hide users’ sensitive information on the blockchain. | Complexity and high deployment overhead. |
| Shen et al. [20] | Hide users’ sensitive information on the blockchain. | Not handover authentication. |
| Son et al. [21] | Low computation and communication overheads. | Vulnerable to RSU capture attacks. |
| Yu et al. [22] | Low computation and communication overheads. | Vulnerable to vehicle capture attacks. |
| Gu et al. [23] | Low deployment overheads. | Complexity and high deployment overhead. |
| Kanjanapruthipong et al. [24] | Resist SPoF attacks. | Complexity and high deployment overhead. |
| Wang et al. [25] | Resist vehicle impersonation attacks and tracking attacks. | Complexity and high deployment overhead. |
Yazdinejad et al. [18] proposed an authentication scheme combining blockchain and SDN to tackle repeated authentication issues during frequent handovers in 5G heterogeneous cells, enabling fast and privacy-aware switching within 1 millisecond. However, this scheme causes high communication overhead between the SDN controller and blockchain center and focuses only on data privacy, overlooking identity and location privacy. To address identity privacy concerns from [17], Zhang et al. [19] developed RUSH, a robust universal seamless handover authentication protocol for 5G heterogeneous networks. RUSH offers features like perfect forward secrecy and strong traceability to enhance handover security and reliability. It protects user anonymity by storing a chameleon hash of the user’s identity on the blockchain instead of the actual identity. Shen et al. [20] introduced BASA, a blockchain-assisted authentication mechanism for cross-domain industrial IoT, which uses identity-based signatures and anonymous identity management to protect device privacy. The parties also negotiate session keys to secure future communications. Son et al. [21] proposed a lightweight blockchain-based handover authentication protocol for VANETs to improve network efficiency during handovers. However, vehicles and RSUs in this scheme still undergo time-consuming authentication processes and it does not effectively protect against RSU capture attacks. In a similar vein, Yu et al. [22] developed a handover authentication protocol using blockchain smart contracts that streamlines mutual authentication and key negotiation between 5G vehicles and base stations, lowering authentication costs. Despite these improvements, the protocol lacks guarantees of mutual authentication and untraceability, making it vulnerable to physical vehicle capture attacks. To solve the problem of industrial IoT devices being vulnerable to attacks, Gu et al. [23] proposed an improved protocol based on the string space attack model theory to meet the identity authentication requirements and gave corresponding attack examples. Kanjanapruthipong et al. [24] proposed a decentralized distributed identity authentication processing mechanism based on the blockchain verification paradigm. This scheme can resist various potential attacks and has great potential in identity management. Wang et al. [25] proposed a mechanism that combines Schnorr signature-based authentication and dynamic refresh of temporary identities, which can effectively prevent vehicle impersonation attacks, tracking attacks, etc.
3. Preliminaries
In this section, we present the ECC scheme, system architecture, corresponding threat models and security requirements. To enhance comprehensibility, Table 2 provides a comprehensive overview of symbols employed in our framework.

Table 2.
Notations.
3.1. Elliptic Curve Cryptosystem
The Elliptic Curve Cryptosystem (ECC) is a public key cryptosystem. Let p and q be two large prime numbers. An elliptic curve is defined over the finite field by the equation , where . Let denote an additive cyclic group of order q, and P be a generator of .
Elliptic curve discrete logarithm problem (ECDLP): Given two points, and , the advantages of calculating in probabilistic polynominal time are negligible.
Elliptic curve computing Diffle–Hellman problem (ECCDHP): For a given , , it is extremely difficult to calculate .
Elliptic curve determination Diffie–Hellman problem (ECDDH): For a given four points on , it is difficult to determine .
The latter two problems are considered mathematically insurmountable.
3.2. System Architecture
As shown in Figure 2, our system model contains the following three types, and our protocol assumes that the adversaries cannot extract any information from the trusted computation tree and the timer will not expire.
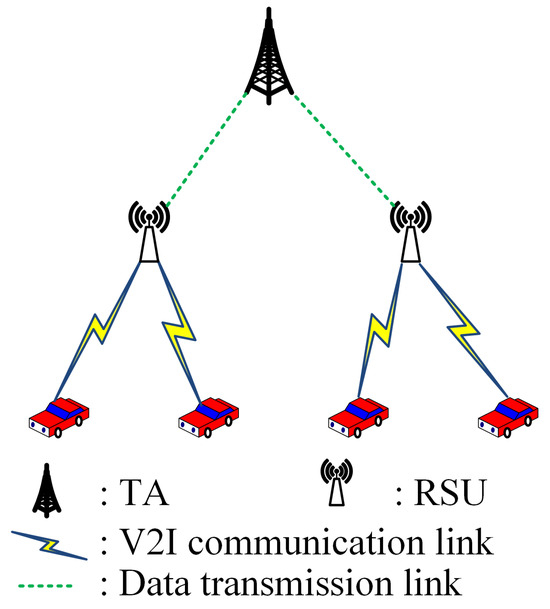
Figure 2.
System model.
- TA: Adversaries possess the capability to eavesdrop on, modify, intercept, and replay all messages transmitted over a public communication channel. However, secure transmission mechanisms are designed to prevent adversaries from intercepting such information.
- RSU: Attackers may exploit intercepted sensitive parameters like vehicle control data, cryptographic keys and public information to initiate spoofing attacks or inject malicious messages.
- V: The attacker may exploit session keys or the session state within a specific session to compromise confidential credentials. However, if the current session key has been compromised in a particular session, the attacker remains incapable of deducing both past and future session keys.
3.3. Threat Model
In vehicular network systems, the wireless channel serves as a public medium, rendering Vehicle-to-Infrastructure (V2I) communications susceptible to numerous security threats, including eavesdropping and privacy infringement. Attackers may attempt to eavesdrop on, intercept, analyze, or modify messages transmitted over the channel. The threat model is a formalization of an adversary, under which the adversary’s capabilities and intentions can be programmatically characterized. The attacker’s objective is to gain unauthorized access to the system and subsequently attempt to derive profit from it. By integrating the widely adopted Canetti–Krawczyk adversary model [26] and the Dolev–Yao adversary model [27], we define the attacker’s capabilities as follows:
- Adversaries possess the capability to eavesdrop on, modify, intercept, and replay all messages transmitted over a public communication channel. However, secure transmission mechanisms are designed to prevent adversaries from intercepting such information.
- Attackers may exploit intercepted sensitive parameters like vehicle control data, cryptographic keys and public information to initiate spoofing attacks or inject malicious messages.
- The attacker may exploit session keys or the session state within a specific session to compromise confidential credentials. However, if the current session key has been compromised in a particular session, the attacker remains incapable of deducing both past and future session keys.
- Adversaries cannot extract any information from the trusted computation tree.
3.4. Security Requirements
- Mutual Authentication: During the mutual authentication process, both parties mutually authenticate each other’s legitimacy and verify their authorization to conduct secure encrypted communications.
- Anonymity: During handover authentication procedures, ensuring the confidentiality of vehicle privacy information assumes paramount importance. Vehicle privacy data must not be transmitted in plaintext format, with access restricted exclusively to authorized entities possessing legitimate entitlements to such sensitive information.
- Unlinkability: During the handover authentication process, even if an attacker intercepts certain messages, it remains fundamentally infeasible to ascertain whether these messages originate from the same user terminal.
- Perfect Forward Secrecy: To protect the confidentiality of messages exchanged during prior sessions, the protocol must ensure the provision of perfect forward secrecy. This guarantees that even if an adversary obtains the long-term private keys of the participants, the session keys established in previous communications remain secure against compromise.
- Defend Against Various Common Attacks: To enhance the security of the authentication process, the proposed protocol should be capable of resisting common attacks such as vehicle impersonation attacks, RSU impersonation attacks, replay attacks, man-in-the-middle (MITM) attacks and other known attacks.
- Penalty and Exposure: Malicious vehicles compromising system security must be subject to sanctions by the Trusted Authority (TA) through cryptographic revocation mechanisms.
4. Proposed Protocol
4.1. Initialization Phase
In this phase, the selects a generator P of an additive cyclic group G of order q, along with a cryptographic hash function . The system then computes and generates the master secret key and , and subsequently publishes the system parameters .
4.2. Registration Phase
4.2.1. Vehicle Registration
The vehicle registration process is shown in Table 3. In this phase, the delivers registration services to the vehicle through a secure communication channel, ultimately enabling to acquire the private key and public key .
- selects a secret parameter as a component of its private key, computes , and transmits a registration request message through the secure communication channel to the .
- Upon receiving the registration request from , the randomly selects , computes , generates a component of its partial private key, and transmits the response message through the secure communication channel.
- Upon receiving the response message from the , first sets , and verifies whether equation holds true. If the verification succeeds, proceeds to compute and generate the and . Finally, stores in its memory and publishes . If the verification fails, retransmits the registration request through the secure communication channel.

Table 3.
Vehicle registration stage.
Table 3.
Vehicle registration stage.
| Randomly choose | |
| Compute | |
| send | |
 | |
| Randomly choose u | |
| Compute | |
| send | |
 | |
| Compute | |
| Verify | |
| Compute | |
| store |
4.2.2. Registration
The registration process of RSU is shown in Table 4. In a similar manner, during this phase, the provides the registration services to through the security channel, ultimately enabling to generate its private key and public key .
- randomly selects a secret parameter , computes , and transmits the registration message to the through the security channel.
- Upon receiving the registration information from , the selects a random number , computes , generates a partial private key for , and sends the response message .
- Upon receiving the information, first verifies whether holds true. If satisfied, generates the private key and public key . Subsequently, stores in memory and publishes its public key .

Table 4.
RSU registration stage.
Table 4.
RSU registration stage.
| Randomly choose | |
| Compute | |
| send | |
 | |
| Randomly choose v | |
| Compute | |
| send | |
 | |
| Verify | |
| Compute | |
| store |
4.3. The Initial Authentication Between Vehicles and and the Generation of Cryptographic Keys
The initial authentication between the vehicles and the RSUs and the generation process of the cryptographic keys are shown in Table 5. During this phase, and perform initial authentication to establish a session key , laying the foundation for subsequent re-authentication. After completing initial authentication, a vehicle-specific secret parameter is shared with a legitimate through time tree technology. When the vehicle enters the jurisdiction of another , handover authentication is conducted between the vehicle and the new , thereby reducing authentication overhead and enhancing efficiency.
- randomly selects a partial private key , computes , and uses the local ’s along with to derive , pseudonymous identifier and verification parameter . Subsequently, obtains the current timestamp and transmits the message to the .
- Upon receiving the message, the first verifies the freshness of through a condition check . If this condition is violated (indicating staleness), the terminates the current session. Otherwise, the retrieves the ’s true identity , sets , computes the ’s , and validates the message’s legitimacy and integrity via the verification equation . If the equation holds, the proceeds with the following steps: The generates a random number , computes and , establishes the session key , updates the pseudonymous identifier to prevent tracking, and encrypts it as . Subsequently, the generates and transmits to the . Finally, the stores in its memory. After updating, the default is set. Here, is a configured threshold representing the maximum number of messages allowed to pass through the before being discarded. If , the must re-register.
- Upon receiving a message from the , first verifies the ’s freshness, then validates the equation . If the equation holds, computes , recovers the pseudonymous identifier , and generates the session key ; otherwise, the resends the authentication request. Finally, replaces parameter with and stores the updated value in its memory.

Table 5.
The initial authentication between vehicles and and the generation of cryptographic keys.
Table 5.
The initial authentication between vehicles and and the generation of cryptographic keys.
| Randomly choose | |
| Compute | |
| send | |
 | |
| (via open channel) | |
| Check | |
| Compute | |
| Verify | |
| Randomly choose | |
| Compute | |
| send | |
| save | |
 | |
| (via open channel) | |
| Check | |
| Verify | |
| Compute | |
| save |
4.4. The Handover Authentication Between Vehicles and and the Generation of Cryptographic Keys
The handover authentication and key generation process between the vehicles and the RSUs is shown in Table 6. In this phase, and undergo initial authentication while is generated through handover authentication, with the entire process conducted over open communication channels.
- In this step, randomly selects as a component of its private key, computes and , and transmits the message to .
- Upon receiving the message, the first assesses ’s freshness by checking . If this condition is violated, indicating is stale, the terminates the current session. Otherwise, it reconstructs based on from shared information and verifies vehicle validity by checking whether . Then the authenticates the message origin through the equation to ensure it originates from a legitimately authenticated vehicle. Upon successful validation, the proceeds as follows: generates random numbers , computes and , updates the pseudonymous with obfuscation to , generates and session key , and finally updates the information in trusted computing tree and transmits to .
- Upon receiving the message from , performs a freshness check firstly and verifies the equation . If the equation holds true, proceeds to compute , generate the session key , and subsequently update its pseudonymous .

Table 6.
The handover authentication between vehicles and and the generation of cryptographic keys.
Table 6.
The handover authentication between vehicles and and the generation of cryptographic keys.
| Randomly choose | |
| Compute | |
| send | |
 | |
| Check | |
| Retrieve | |
| Verify | |
| Check | |
| Randomly choose | |
| Compute | |
| Generate | |
| Update | |
| send | |
 | |
| Check | |
| Verify | |
| Compute | |
| Generate | |
| Update |
4.5. The Revocation of Malicious Vehicles in Vehicular Networks
The malicious vehicle’s true identity is identified through , followed by removal of its credentials from the trusted computing environment and registration in . Subsequently, all shall deny services to vehicles marked as malicious in .
5. Security Analysis
In this section, we show that our protocol satisfies the security requirements mentioned in Section 3.
- Untraceability: In the process of authentication, the protocol proposed in this paper changes the parameters of each authentication randomly and contains dynamic timestamps. The adversary cannot effectively link related vehicles based on some random numbers. Therefore, this protocol is untraceable.
- Anonymity of vehicle identity: When a vehicle attempts to communicate with an RSU or other vehicles, it will use a temporary pseudonym instead of its real identity to transmit on a public channel. Without the master private key of the TA or RSU, the attacker cannot obtain the real identity of the vehicle. Only the TA or RSU can reveal the real information of the vehicle. The vehicle can update autonomously every time it communicates (rather than being generated by a trusted third party like other protocols).
- Perfect forward secrecy: Even if an adversary intercepts messages such as and , deriving the session key (SK) remains infeasible. This is because SK is computed using a secret random value generated by the client. Recovering the SK from the intercepted data would require solving the elliptic curve discrete logarithm problem (ECDLP), which is widely regarded as computationally intractable. As a result, the protocol achieves perfect forward secrecy, ensuring that past session keys remain secure even if long-term private keys are compromised.
- Resistance to DDoS attacks: The system architecture employs multiple registration servers, which improves fault tolerance and enhances overall availability. Due to the protocol’s low transmission and processing overhead, the system remains responsive even when subjected to a high volume of incoming requests. This design allows it to effectively absorb and mitigate the impact of distributed denial-of-service (DDoS) attacks, ensuring continued service for legitimate users.
- Resistance to replay attacks: The protocol prevents adversaries from reusing previously intercepted messages to gain unauthorized access. Each message carries a timestamp T, allowing the server to verify its timeliness. Messages with outdated or invalid timestamps are recognized as replays and are subsequently rejected, thereby mitigating the risk of replay attacks.
- Resistance to man-in-the-middle attacks: As mentioned above, this protocol can prevent ’s identity , random number , and secret parameter C from being recovered by malicious opponents. And this protocol is based on the mutual authentication feature and can resist man-in-the-middle attacks.
- Resistance to imitation attacks: Malicious attackers cannot obtain both the TA’s master private key and the partial private key generated by the vehicle at the same time, so the attacker cannot successfully imitate a legitimate vehicle to generate a signature, and therefore cannot successfully launch a vehicle simulation attack. Malicious attackers will try to launch RSU imitation attacks to obtain vehicle-related privacy information. However, the attacker cannot generate a legitimate sum, so they cannot successfully simulate a legitimate RSU.
- Resistance to single point failure attack: A malicious attacker can launch a single point failure attack on . However, the registered vehicle information is directly written into the trusted computing tree instead of ’s memory, so the adversary cannot obtain the registered vehicle information. The exit of a certain will not change and , so other do not need to regenerate . The multi-registration server structure will not cause the vehicle to fail to register due to a single , because other servers can also register for .
The protocol in this chapter takes security and functional characteristics into consideration. Table 7 gives the security and functional characteristics of the protocol and compares them with existing related protocols [28,29,30]. The proposed protocol can guarantee all security characteristics. Existing related protocols [28,29,30] do not consider or cannot guarantee all security characteristics. The proposed protocol can resist more attacks that may occur in the wireless channel and provide better security than existing protocols.

Table 7.
Security feature comparison.
6. Performance Analysis
In this section, the proposed protocol will be compared with existing handover authentication schemes [28,29,30] in terms of computational cost and communication cost.
6.1. Computational Cost
All protocols were achieved on a four-core 3.2 GHz machine with 8 GB memory, and the results were averaged over 300 randomized simulation runs [31]. The execution time of each basic operation is shown in Table 8 [29].

Table 8.
Execution time of basic operations.
The protocol of Wang et al. [28] requires four one-way hash operations, four bilinear pairing operations, six exponentiation operations, three modular multiplication operations and two modular inverse operations in the initial authentication phase. Therefore, the computational cost of this scheme in the initial authentication phase is about ms. In the handover authentication phase, it requires two one-way hash operations, two bilinear pairing operations, six exponentiation operations and five modular multiplication operations. Therefore, the computational cost of this scheme in the handover authentication phase is about ms.
The protocol of Dwivedi et al. [29] requires twelve one-way hash operations and six elliptic curve scalar multiplications in the initial authentication phase. Therefore, the computational cost of this scheme in the initial authentication phase is about ms. In the handover authentication phase, it requires twenty-one one-way hash operations and twelve elliptic curve scalar multiplications. Therefore, the computational cost of this scheme in the handover authentication phase is about ms.
The protocol of Maria et al. [30] requires four one-way hash operations, two elliptic curve scalar multiplications, two bilinear pairing operations and six exponentiation operations in the initial authentication phase. Therefore, the computational cost of this scheme in the initial authentication phase is about ms. In the handover authentication phase, it requires three one-way hash operations, two elliptic curve scalar multiplications, two bilinear pairing operations and seven exponentiation operations. Therefore, the computational cost of this scheme in the handover authentication phase is about ms.
In the protocol proposed in this paper, in the initial authentication stage, thirteen one-way hash operations and sixteen elliptic curve scalar multiplication operations are required, so the computational cost of the scheme in the initial authentication stage is about ms; in the handover authentication stage, only nine one-way hash operations and four elliptic curve scalar multiplication operations are required, so the computational overhead of the scheme proposed in this paper in the handover authentication stage is approximately ms.
Table 9 and Figure 3 shows that the proposed scheme has extremely superior performance in terms of computational overhead in the handover authentication phase. Compared with the protocols of Wang et al. [28], Dwivedid et al. [29], and Maria et al. [30], the proposed scheme has a lower computational overhead in the handover authentication phase.

Table 9.
Comparison of computational costs of protocols.
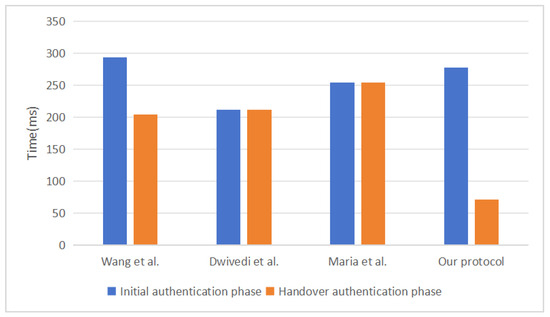
Figure 3.
Comparison of the computational cost [28,29,30].
6.2. Communication Cost
In this section, we analyze the communication overhead of our proposed scheme by combining the schemes of Wang et al. [28], Dwivedi et al. [29], and Maria et al. [30]. For the sake of comparison, this section assumes that are the length of the elliptic curve point, the length of the vehicle or server identity, the output length of the hash function, and the length of the timestamp, respectively. In the implementation, it is assumed that the elliptic curve point is 320 bits, the output length of the hash function is 256 bits, the length of the vehicle or server identity (including the real identity and the disguised identity) is 160 bits, and the length of the timestamp is 32 bits.
In the protocol of Dwivedi et al. [29], in the initial authentication phase, two messages and are transmitted between and , requiring bits and bits, respectively, so the total communication cost of sending these two messages is 2144 bits; in the handover authentication phase, four messages , , and are exchanged among , and , requiring bits, bits, bits and bits, respectively, so the total communication cost of sending these four messages is 3616 bits. In summary, the total communication cost of this scheme is 5760 bits.
In the protocol proposed by Maria et al. [30], the initial authentication phase requires 512 bits in total, comprising , while the handover authentication phase requires 1280 bits (). This results in an overall communication overhead of 1792 bits. However, the protocol does not support multi-domain authentication for vehicles, limiting its applicability in large-scale vehicular networks. Additionally, the messages and are transmitted over public channels without integrity verification at the receiving RSU, leaving the protocol unable to guarantee the confidentiality of public messages or the integrity of the handover process. Building on this, Wang et al. [28] later introduced a protocol that incurs 1056 bits of overhead during initial authentication and 3072 bits during handover authentication, amounting to a total of 4128 bits. Despite the increased communication cost, this scheme does not offer mutual authentication and fails to address the risk of privileged insider attacks.
In the protocol proposed in this paper, in the initial authentication phase, two messages and are transmitted, requiring bits and bits, respectively, so the total communication cost of sending these two messages is 1824 bits; in the handover authentication phase, two messages and are exchanged, requiring bits and bits, so the total communication cost of sending these messages is 1600 bits. In summary, the total communication overhead of our scheme is 2528 bits. Figure 4 compares the communication overhead of each protocol.
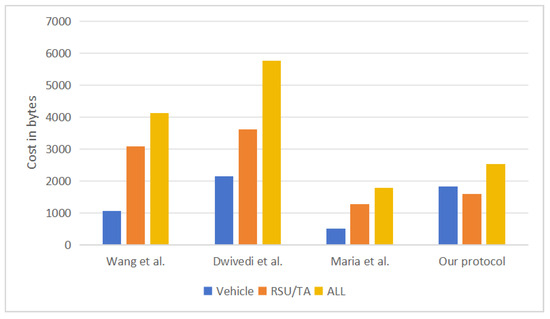
Figure 4.
Comparison of total communication cost [28,29,30].
7. Conclusions
We propose a lightweight handover authentication protocol based on ECC, which aims to solve the security and efficiency problems of cross-domain vehicle authentication in the Internet of Vehicles. The protocol uses cryptography and time tree technology to achieve fast two-way authentication and key negotiation between vehicles and infrastructure, ensuring the security and real-time nature of communication. The core innovation of the protocol lies in the “non-full key escrow” mechanism; that is, the private key of the vehicle is jointly generated by the TA and the vehicle, and the TA only holds part of the private key, thereby effectively preventing malicious TA from fully controlling the vehicle private key and significantly improving security. In addition, the protocol reduces the communication and computing overhead by reducing the number of message exchanges between entities, and uses the time tree technology to share some private data, further improving the authentication efficiency. Vehicles do not need to register and authenticate repeatedly when moving across domains, reducing resource consumption in the authentication process. Experimental results show that compared with existing protocols, this protocol has significant advantages in computing and communication overhead, providing a reliable solution for efficient and secure authentication in the Internet of Vehicles.
In future research, we will focus on the security and efficiency of fast switching authentication in vehicles in practice (including dynamic environmental factors, unforeseen attacks that may occur in actual deployment, etc.), and verify and improve our protocol.
Author Contributions
Conceptualization, J.T. and Y.K.; methodology, Y.K.; software, Y.K.; validation, Y.K.; formal analysis, Y.K.; writing—original draft preparation, Y.K.; writing—review and editing, J.T. and Y.K.; supervision, Y.K.; funding acquisition, J.T. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Natural Science Fund Committee of Hebei Province (F2021201058) and Funds of the Central Government for Local Science and Technology Development (236Z0701G).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data presented in this study are available in B-HAS: Blockchain-assisted efficient handover authentication and secure communication protocol in VANETs [29].
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Oladimeji, D.; Gupta, K.; Kose, N.A.; Gundogan, K.; Ge, L.; Liang, F. Smart transportation: An overview of technologies and applications. Sensors 2023, 23, 3880. [Google Scholar] [CrossRef] [PubMed]
- Yuan, M.; Xiao, Y. PMAKA-IoV: A Physical Unclonable Function (PUF)-Based Multi-Factor Authentication and Key Agreement Protocol for Internet of Vehicles. Information 2025, 16, 404. [Google Scholar] [CrossRef]
- Khezri, E.; Hassanzadeh, H.; Yahya, R.O.; Mir, M. Security challenges in internet of vehicles (IoV) for ITS: A survey. Tsinghua Sci. Technol. 2025, 30, 1700–1723. [Google Scholar] [CrossRef]
- Singh, A.; Rani, P.; Ramesh, J.V.N.; Athawale, S.V.; Alkhayyat, A.H.; Aledaily, A.N.; Prola, T.A.; Sharma, R. Blockchain-based lightweight authentication protocol for next-generation trustworthy internet of vehicles communication. IEEE Trans. Consum. Electron. 2024, 70, 4898–4907. [Google Scholar] [CrossRef]
- Tian, J.; Chang, F. Trusted cloud platform management model based on TPM alliance. J. Commun. 2016, 37, 1–10. [Google Scholar]
- Zhang, J.; Cui, J.; Zhong, H.; Chen, Z.; Liu, L. PA-CRT: Chinese remainder theorem based conditional privacy-preserving authentication scheme in vehicular ad-hoc networks. IEEE Trans. Dependable Secur. Comput. 2019, 18, 722–735. [Google Scholar] [CrossRef]
- Xiong, H.; Chen, J.; Mei, Q.; Zhao, Y. Conditional privacy-preserving authentication protocol with dynamic membership updating for VANETs. IEEE Trans. Dependable Secur. Comput. 2020, 19, 2089–2104. [Google Scholar] [CrossRef]
- Wang, C.; Huang, R.; Shen, J.; Liu, J.; Vijayakumar, P.; Kumar, N. A novel lightweight authentication protocol for emergency vehicle avoidance in VANETs. IEEE Internet Things J. 2021, 8, 14248–14257. [Google Scholar] [CrossRef]
- Wang, P.; Liu, Y. SEMA: Secure and efficient message authentication protocol for VANETs. IEEE Syst. J. 2021, 15, 846–855. [Google Scholar] [CrossRef]
- He, Z.; Zheng, Y.; Chen, S.; Du, Z.; Liu, S.; Zhang, K. Security-Enhanced Lightweight Authentication Key-Agreement Protocol for Unmanned Aerial Vehicle Communication. Appl. Sci. 2025, 15, 4680. [Google Scholar] [CrossRef]
- Li, M.; Hu, S. A Lightweight ECC-Based Authentication and Key Agreement Protocol for IoT with Dynamic Authentication Credentials. Sensors 2024, 24, 7967. [Google Scholar] [CrossRef] [PubMed]
- Cao, J.; Ma, M.; Fu, Y.; Li, H.; Zhang, Y. CPPHA: Capability-based privacy-protection handover authentication mechanism for SDN-based 5G HetNets. IEEE Trans. Dependable Secur. Comput. 2019, 18, 1182–1195. [Google Scholar] [CrossRef]
- Duan, X.; Wang, X. Authentication handover and privacy protection in 5G hetnets using software-defined networking. IEEE Commun. Mag. 2015, 53, 28–35. [Google Scholar] [CrossRef]
- Zhang, L.; Xu, J.; Obaidat, M.S.; Li, X.; Vijayakumar, P. A PUF-based lightweight authentication and key agreement protocol for smart UAV networks. IET Commun. 2022, 16, 1142–1159. [Google Scholar] [CrossRef]
- Ren, X.; Cao, J.; Ma, R.; Luo, Y.; Guan, J.; Zhang, Y.; Li, H. A novel access and handover authentication scheme in UAV-aided satellite-terrestrial integration networks enabling 5G. IEEE Trans. Netw. Serv. Manag. 2023, 20, 3880–3899. [Google Scholar] [CrossRef]
- Choi, J.; Son, S.; Kwon, D.; Park, Y. A PUF-Based Secure Authentication and Key Agreement Scheme for the Internet of Drones. Sensors 2025, 25, 982. [Google Scholar] [CrossRef]
- Mo, J.; Zhang, Z.; Lin, Y. A Practically Secure Two-Factor and Mutual Authentication Protocol for Distributed Wireless Sensor Networks Using PUF. Electronics 2024, 14, 10. [Google Scholar] [CrossRef]
- Yazdinejad, A.; Parizi, R.M.; Dehghantanha, A.; Choo, K.K.R. Blockchain-enabled authentication handover with efficient privacy protection in SDN-based 5G networks. IEEE Trans. Netw. Sci. Eng. 2019, 8, 1120–1132. [Google Scholar] [CrossRef]
- Zhang, Y.; Deng, R.H.; Bertino, E.; Zheng, D. Robust and universal seamless handover authentication in 5G HetNets. IEEE Trans. Dependable Secur. Comput. 2019, 18, 858–874. [Google Scholar] [CrossRef]
- Shen, M.; Liu, H.; Zhu, L.; Xu, K.; Yu, H.; Du, X.; Guizani, M. Blockchain-assisted secure device authentication for cross-domain industrial IoT. IEEE J. Sel. Areas Commun. 2020, 38, 942–954. [Google Scholar] [CrossRef]
- Son, S.; Lee, J.; Park, Y.; Park, Y.; Das, A.K. Design of blockchain-based lightweight V2I handover authentication protocol for VANET. IEEE Trans. Netw. Sci. Eng. 2022, 9, 1346–1358. [Google Scholar] [CrossRef]
- Yu, F.; Ma, M.; Li, X. A blockchain-assisted seamless handover authentication for V2I communication in 5G wireless networks. In Proceedings of the ICC 2021-IEEE International Conference on Communications, Montreal, QC, Canada, 14–23 June 2021; pp. 1–6. [Google Scholar]
- Gu, H.; Shang, J.; Wang, P.; Mi, J.; Bhattacharjya, A. A Secure Protocol Authentication Method Based on the Strand Space Model for Blockchain-Based Industrial Internet of Things. Symmetry 2024, 16, 851. [Google Scholar] [CrossRef]
- Kanjanapruthipong, W.; Boonkrong, S. Blockchain-Based Decentralised Authentication in Closed Environments. Future Internet 2025, 17, 98. [Google Scholar] [CrossRef]
- Wang, S.; Wu, Y.; Wen, K.; Zhou, X.; Hu, B.; Xie, Q. An Improved Blockchain-Based Lightweight Vehicle-to-Infrastructure Handover Authentication Protocol for Vehicular Ad Hoc Networks. Mathematics 2025, 13, 1118. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Universally composable notions of key exchange and secure channels. In Proceedings of the Advances in Cryptology—EUROCRYPT 2002: International Conference on the Theory and Applications of Cryptographic Techniques, Amsterdam, The Netherlands, 28 April–2 May 2002; Proceedings 21. Springer: Berlin/Heidelberg, Germany, 2002; pp. 337–351. [Google Scholar]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Wang, C.; Shen, J.; Lai, J.F.; Liu, J. B-TSCA: Blockchain assisted trustworthiness scalable computation for V2I authentication in VANETs. IEEE Trans. Emerg. Top. Comput. 2020, 9, 1386–1396. [Google Scholar] [CrossRef]
- Dwivedi, S.K.; Amin, R.; Vollala, S.; Khan, M.K. B-HAS: Blockchain-assisted efficient handover authentication and secure communication protocol in VANETs. IEEE Trans. Netw. Sci. Eng. 2023, 10, 3491–3504. [Google Scholar] [CrossRef]
- Maria, A.; Pandi, V.; Lazarus, J.D.; Karuppiah, M.; Christo, M.S. BBAAS: Blockchain-based anonymous authentication scheme for providing secure communication in VANETs. Secur. Commun. Netw. 2021, 2021, 6679882. [Google Scholar] [CrossRef]
- Lee, C.C.; Chen, C.T.; Wu, P.H.; Chen, T.Y. Three-factor control protocol based on elliptic curve cryptosystem for universal serial bus mass storage devices. IET Comput. Digit. Tech. 2013, 7, 48–55. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).