Improvement of a Conditional Privacy-Preserving and Desynchronization-Resistant Authentication Protocol for IoV
Abstract
1. Introduction
Motivation and Contributions
- Firstly, we point out that Kumar et al.’s protocol cannot resist identity guessing attacks, impersonation attacks and no session key secrecy when the attacker obtains data stored in SC through side-channel attacks, as well as that it is vulnerable to RSU captured attacks and lacks perfect forward secrecy.
- Secondly, we propose a lightweight V2I authentication protocol based on PUF and the Fuzzy Extractor algorithm for the IoV. In particular, we used PUF to resist RSU captured attacks, designed a three-factor secrecy strategy to resist side-channel attacks, and also adopted a conditional privacy-preserving strategy to achieve anonymity and malicious user tracking.
- Our proposed protocol is provably secure under the random oracle model. In comparison to various related protocols, our protocol demonstrates resilience against a range of known attacks and offers lower computational and communication costs.
2. Related Work
3. Preliminaries
3.1. Elliptic Curve Cryptography
- Elliptic Curve Discrete Logarithm Problem (ECDLP): The random points on , where , and . The computation of is hard in polynomial time.
- Computational Diffie–Hellman Problem (CDHP): The random point and on , where and . The computation of is hard in a polynomial time when and are two unknown random numbers.
3.2. Fuzzy Extractor
3.3. Physical Unclonable Function
- Each physical device can provide a unique challenge–response pair, even when the same input challenge bits are used [24];
- Any attempt to alter the behavior of the device will impact the PUF outcomes and render the PUF inoperable [25];
- PUF can be regarded as a one-way function, which greatly guarantees safety features [26].
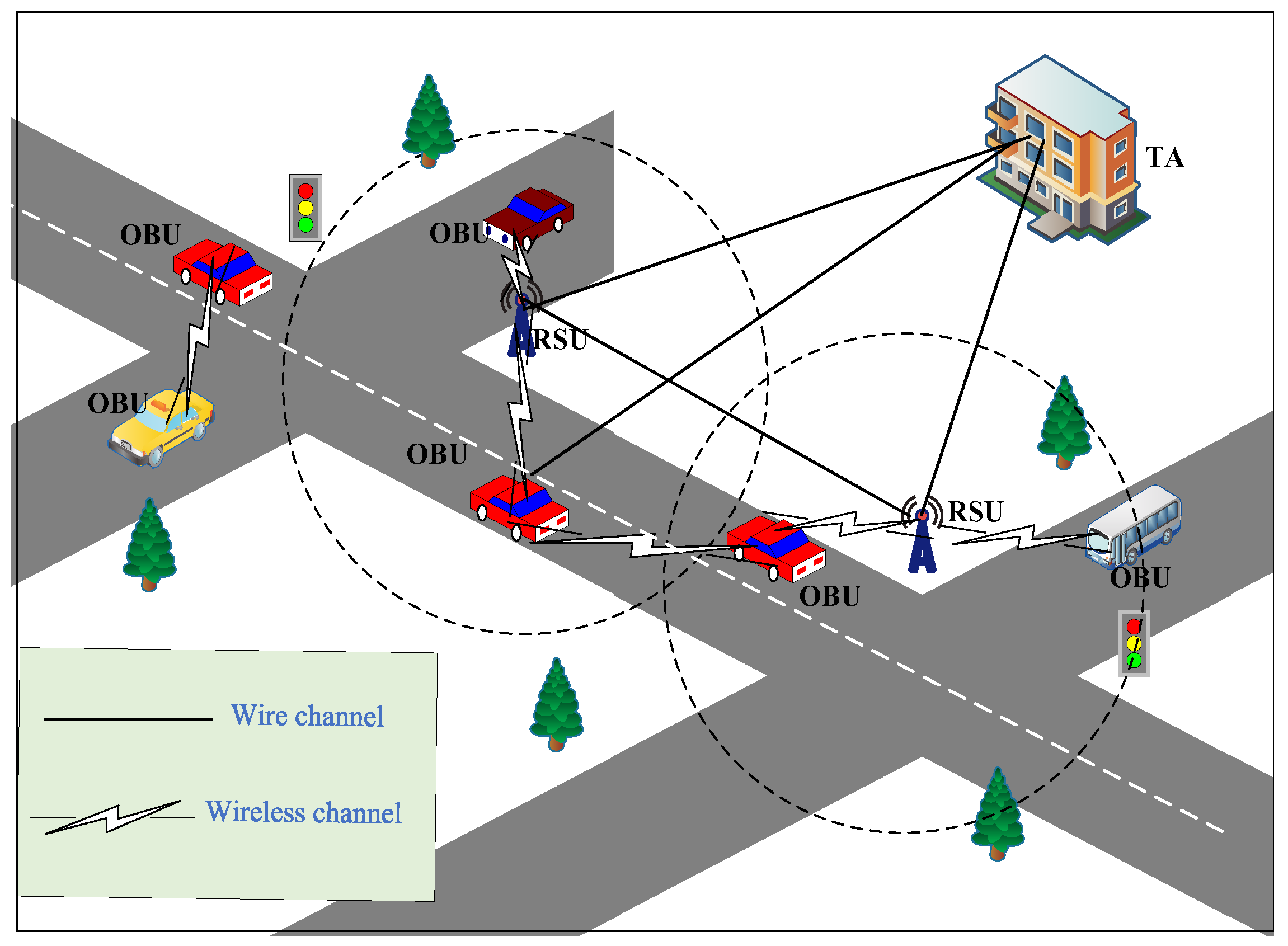
3.4. Network Model
- Trusted Authority (TA): The TA can initialize the system and register the RSU and vehicle. In case of malicious activities, only the Trusted Authority (TA) has the ability to reveal the true identity of the vehicle.
- Roadside Units (RSUs): The RSUs are a series of roadside base stations that assist the TA in authentication and share information with the vehicle after negotiating the session key with the vehicle. In addition, the PUF is installed on the RSU.
- Vehicle (OBU): The OBU is deployed in the vehicle. The OBU is responsible for computation and communication with the vehicle and RSUs via wireless channels.
3.5. Attack Model
- The adversary has the capability to intercept messages transmitted over insecure wireless channels. By analyzing the intercepted messages, the adversary can forge valid messages as well as insert or modify the original messages.
- The adversary can steal valid users’ smart cards and sensing devices and gain access to stored values.
- The adversary can launch guessing, known specific session information, impersonation, and session key disclosure attacks based on the obtained values.
4. Review of a V2I Authentication Scheme
4.1. System Initialization
4.2. User Registration
4.3. User Login and Mutual Authentication
5. Security Analysis of a V2I Authentication Scheme
5.1. Side-Channel Attacks
- Identity guessing attacks/no anonymity: If an attacker knows the information in a user’s smart card through side-channel attacks, and the authentication information transmitted via the public channel, where , and , then the adversary can guess and find based on , compute , , and verify whether is correct or not. If yes, the guessed is correct. Therefore, their scheme cannot achieve anonymity.
- No session key secrecy: Once the adversary can know the user’s identity and from the above analysis and can obtain from the public channel, then the adversary can compute , and verifies whether is correct or not. After successful verification, the adversary can calculate the session key .
- Impersonation attacks: According to the above analysis, the adversary can know stored in smart card and can obtain user’s identity and , then they can launch impersonation attacks. The adversary randomly selects , selects two fresh random numbers and , and computes , and the verification parameter , where . Finally, the adversary transmits the service access request to . Obviously, it can pass through the authentication of TA and can establish the session key. So, their scheme is not resistant to impersonation attacks.
5.2. RSU Captured Attacks
5.3. No Perfect Forward Secrecy
6. Proposed Scheme
6.1. System Initialization
6.2. RSU Registration
6.3. User Registration
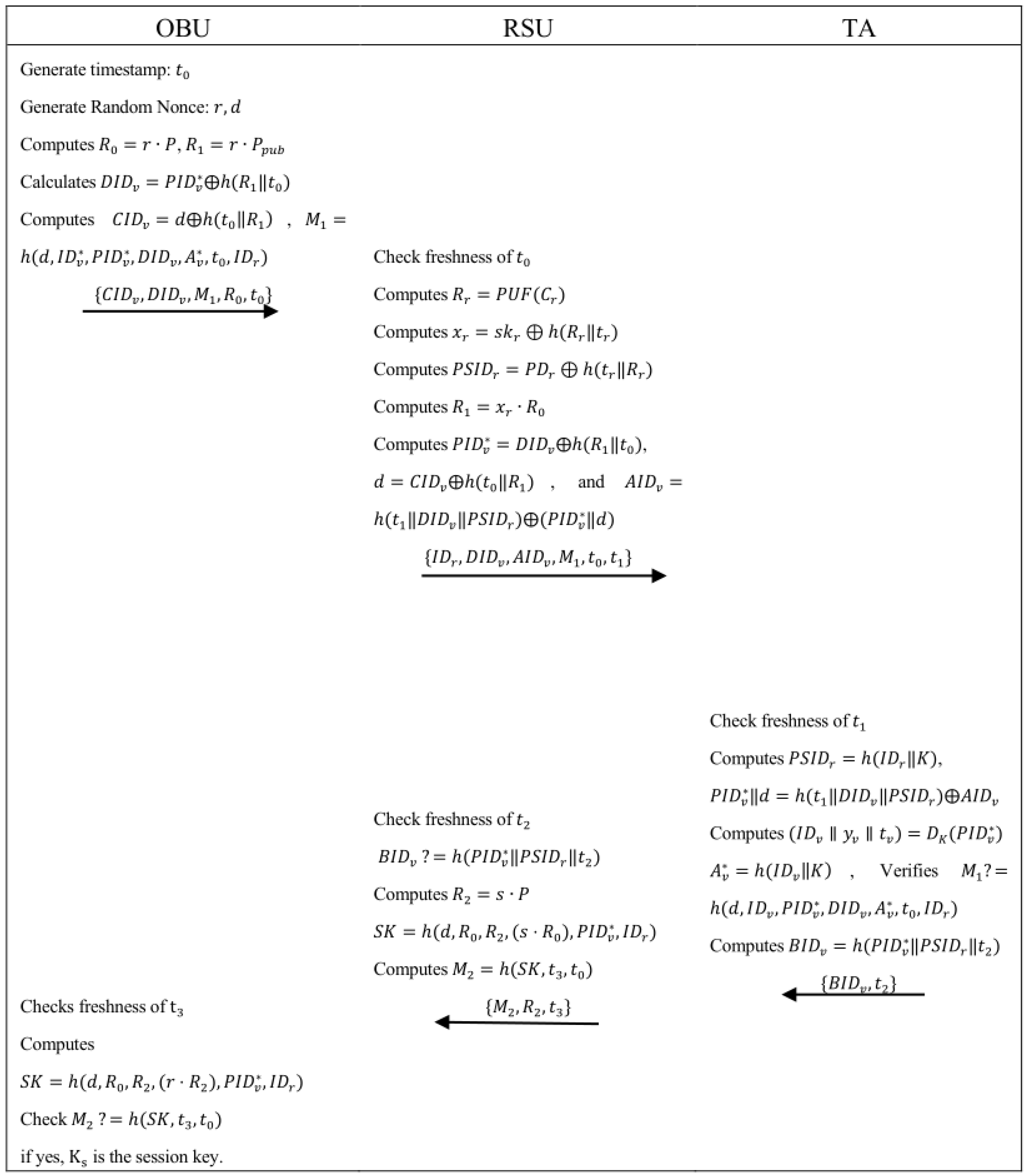
6.4. User Login and Authentication
6.5. Password Renewal and Biometric Change
6.6. Malicious User Tracking
7. Security Analysis
7.1. Formal Security Proof
- Queries: The queries simulate the capabilities of attackers, replicating their potential actions and abilities.
- : The adversary has the capability to intercept all the messages exchanged over the wireless channel.
- : has the ability to forge the message and sends it to , , or ; if the message is valid, , , or will provide a response .
- : can obtain the agreed session keys between , , and .
- : This query can be executed at most once, generating a random bit , This query can be executed at most once, generating a random bit , which returns the real session key if ; otherwise, a random number is returned.
- : It simulates a side channel attack on the SC and returns the stored values .
- : It simulates a side channel attack on the TPD of RSU and returns the stored information .
- ,, and are in Accept.
- The query has not been executed.
- The queries and has been executed at most once.
- : In this game, we simulate the actual attacks initiated by . Based on the given definition, we obtain the following results:
- : In this game, we simulate eavesdropping attacks where has access to all the messages transmitted publicly. Then, obtains all the messages transmitted between , , and by executing . Then, executes and attempts to guess whether the returned value corresponds to the session key. However, due to the presence of random numbers and ECDLP, the attacker is unable to determine the correlation between the captured messages and the session keys. Thus, we obtain the following:
- : In this game, we simulate collision attacks on the transcripts and hash results. According to the definition of the birthday paradox, the probability of a hash collision is less than , and the collision probability of other transcripts is less than . Thus, we have:
- : This game simulates that executes and to gain the stored information in the SC and in RSU, where , , , where and is the biometric key. In addition, , , and . If wants to gain these parameters, they must guess the biological key or break PUF. Let us assume that the probability of A successfully breaking the PUF is denoted as . Thus, we have:
- : can obtain , through the public channel, which are utilized for session key agreements based on the ECDLP. The simulation in the game assumes that calculates the session keys based on the transcripts. We have:Since the session keys are generated independently and randomly, the advantage of guessing the value is equivalent to guessing the session key itself. We have:Combining the above formulas, we have:
7.2. Informal Security Analysis
- Anonymity and unlinkability: In the user authentication of our scheme, the OBU sends the dynamic identity instead of real identity on the wireless channel. The adversary may listen and intercept information from the common channel to obtain , but it cannot obtain because it is hidden in a pseudonym and only TA can decrypt , and includes a one-way hash function, a random number, and other parameters. Moreover, the RSU only knows the pseudonym and does not know the real identity of the vehicle during the authentication process. Even if the RSU is dishonest, it is not a privacy breach. In addition, the authentication messages in each session are different because they are all made up of random numbers, timestamps, and other parameters. Thus, the protocol provides user anonymity and unlinkability.
- Perfect forward secrecy: In proposed scheme, the session key are composed of random number , ECDLP , , and CDHP or , the pseudonym of vehicle and identity of RSU . Even if the attacker knows these parameters and the current , cannot obtain random numbers and cannot compute previous or future session keys. Thus, the scheme has perfect forward secrecy.
- Known key secrecy: In our scheme, the session key is based on a random number, ECDLP, Diffie–Hellman, and one-way hash function. Even if the attacker gains the session key, they cannot obtain any long-term keys.
- Replay attacks: In our scheme, every message that is sent via the wireless channel contains random numbers and timestamps to ensure the integrity and freshness of the message. For example, in the user authentication phase, the sent message is , where ( is random number), ( is random number), , and (timestamp). So, the proposed scheme has the ability to resist replay attacks.
- Password guessing attacks: If can know the user’s biometric template and all information stored in smart card, it can guess and such that . However, there are candidates of the pair to satisfy this equation when [28]. Therefore, our protocol meets resistance password guessing attacks.
- Three-factory secrecy: If obtains the date from the smart card through side-channel attacks and knows the user’s , and cannot know the correct , cannot launch any attacks without knowing and . For the same reasons, if knows the user’s , or knows the user’s and information stored in the smart card, still cannot launch any attacks. Thus, the proposed protocol can achieve three-factor secrecy.
- Identity guessing attacks: In our scheme, , , are transmitted via the wireless channel, and stored into a smart card. Even if the attacker eavesdrops and obtains these messages, cannot verify the guessed identity. Because these messages not only contain identity but also include random numbers, the passwords and biometric keys, such as ( is random number), , , , is the password and is the biometric key. Thus, is unable to verify the accuracy of the guessed identity without having knowledge of , and .
- Forgery attacks and impersonation attacks: Suppose the attacker impersonates user and sends message to RSU, where , , , , , . cannot forge without knowing , and . If the attacker wants to know , they must know the three-factor , password , and biometric key at the same time, which is obviously impossible. Therefore, cannot impersonate the user. Suppose the attacker wants to impersonate RSU and sends to TA, where , , . Since the PUF is unique, even if the attacker obtains Challenger , they cannot obtain and cannot compute the . Thus, the attacker cannot impersonate the RSU without knowing . Supposed the attacker wants to impersonate TA and sends , where , , is the system’s primary key. Since cannot know , cannot impersonate TA. Hence, our scheme effectively mitigates the risks of forgery attacks and impersonation attacks.
- RSU captured attacks: In our scheme, RSU stores , where is the corresponding challenge to generate a response of PUF. Suppose the attacker captures the RSU and obtains the date . Due to the characteristics of PUF, cannot obtain the corresponding and cannot compute private key and shared key . In simpler terms, capturing an RSU will yield no valuable information. Therefore, our protocol effectively withstands RSU capture attacks.
8. Performance Analysis
9. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ali, Q.E.; Ahmad, N.; Malik, A.H.; Ali, G.; Rehman, W.U. Issues, Challenges, and Research Opportunities in Intelligent Transport System for Security and Privacy. Appl. Sci. 2018, 8, 1964. [Google Scholar] [CrossRef]
- Xie, Q.; Ding, Z.; Tang, W.; He, D.; Tan, X. Provable secure and lightweight blockchain-based V2I handover authentication and V2V broadcast protocol for VANETs. IEEE Trans. Veh. Technol. 2023, 72, 15200–15212. [Google Scholar] [CrossRef]
- Zhou, F.; Li, Y.; Ding, Y. Practical V2I Secure Communication Schemes for Heterogeneous VANETs. Appl. Sci. 2019, 9, 3131. [Google Scholar] [CrossRef]
- Gupta, B.B.; Quamara, M. A taxonomy of various attacks on smart card–based applications and countermeasures. Concurr. Comput. Pract. Exp. 2021, 33, 1. [Google Scholar] [CrossRef]
- Kumar, P.; Om, H. A conditional privacy-preserving and desynchronization-resistant authentication protocol for vehicular ad hoc network. J. Supercomput. 2022, 78, 17657–17688. [Google Scholar] [CrossRef]
- Raya, M.; Hubaux, J.P. Securing vehicular ad hoc networks. J. Comput. Secur. 2007, 15, 39–68. [Google Scholar] [CrossRef]
- Joshi, A.; Gaonkar, P.; Bapat, J. A reliable and secure approach for efficient car-to-car communication in intelligent transportation systems. In Proceedings of the 2017 International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), IEEE, Chennai, India, 22–24 March 2017; pp. 1617–1620. [Google Scholar]
- Sun, Y.; Lu, R.; Lin, X.; Shen, X.; Su, J. An efficient pseudonymous authentication scheme with strong privacy preservation for vehicular communications. IEEE Trans. Veh. Technol. 2010, 59, 3589–3603. [Google Scholar] [CrossRef]
- Cui, J.; Wei, L.; Zhang, J.; Xu, Y.; Zhong, H. An efficient message-authentication scheme based on edge computing for vehicular ad hoc networks. IEEE Trans. Intell. Transp. Syst. 2018, 20, 1621–1632. [Google Scholar] [CrossRef]
- Liu, Z.; Chong, L.; Peng, T.; Peng, D.-Y.; Liang, H.-B. A realistic distributed conditional privacy-preserving authentication scheme for vehicular ad hoc networks. IEEE Access 2018, 6, 26307–26317. [Google Scholar] [CrossRef]
- Shamir, A. Identity-based cryptosystems and signature schemes. In Advances in Cryptology: Proceedings of CRYPTO 84 4; Springer: Berlin/Heidelberg, Germany, 1985; pp. 47–53. [Google Scholar]
- Zhang, C.; Ho, P.H.; Tapolcai, J. On batch verification with group testing for vehicular communications. Wirel. Netw. 2011, 17, 1851–1865. [Google Scholar] [CrossRef]
- Liu, Y.; He, Z.; Zhao, S.; Wang, L. An efficient anonymous authentication protocol using batch operations for VANETs. Multimed. Tools Appl. 2016, 75, 17689–17709. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Xu, B.; Huang, X. An Efficient Identity-Based Conditional Privacy-Preserving Authentication Scheme for Vehicular Ad Hoc Networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2681–2691. [Google Scholar] [CrossRef]
- Ma, M.; He, D.; Wang, H.; Kumar, N.; Choo, K.K.R. An Efficient and Provably Secure Authenticated Key Agreement Protocol for Fog-Based Vehicular Ad-Hoc Networks. IEEE Internet Things J. 2019, 6, 8065–8075. [Google Scholar] [CrossRef]
- Saleem, M.A.; Li, X.; Ayub, M.F.; Shamshad, S.; Wu, F.; Abbas, H. An Efficient and Physically Secure Privacy-Preserving Key-Agreement Protocol for Vehicular Ad-Hoc Network. IEEE Trans. Intell. Transp. Syst. 2023, 24, 9940–9951. [Google Scholar] [CrossRef]
- Xie, Q.Y.; Ding, Z.; Xie, Q. A Lightweight and Privacy-Preserving Authentication Protocol for Healthcare in IoT Environment. Mathematics 2023, 11, 3857. [Google Scholar] [CrossRef]
- Othman, W.; Fuyou, M.; Xue, K.; Hawbani, A. Physically Secure Lightweight and Privacy-Preserving Message Authentication Protocol for VANET in Smart City. IEEE Trans. Veh. Technol. 2021, 70, 12902–12917. [Google Scholar] [CrossRef]
- Xie, Q.; Ding, Z.; Zheng, P. Provably Secure and Anonymous V2I and V2V Authentication Protocol for VANETs. IEEE Trans. Intell. Transp. Syst. 2023, 24, 7318–7327. [Google Scholar] [CrossRef]
- Xu, T.; Xu, C.; Xu, Z. An efficient three-factor privacy-preserving authentication and key agreement protocol for vehicular ad-hoc network. China Commun. 2021, 18, 315–331. [Google Scholar] [CrossRef]
- Duan, Z.; Mahmood, J.; Yang, Y.; Berwo, M.A.; Yassin, A.A.K.A.; Mumtaz Bhutta, M.N.; Chaudhry, S.A. TFPPASV: A Three-Factor Privacy Preserving Authentication Scheme for VANETs. Secur. Commun. Netw. 2022, 2022, 8259927. [Google Scholar] [CrossRef]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In Advances in Cryptology-EUROCRYPT 2004, Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2–6 May 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 523–540. [Google Scholar]
- Maes, R.; Maes, R. Physically Unclonable Functions: Concept and Constructions; Springer: Berlin/Heidelberg, Germany, 2013. [Google Scholar]
- Aman, M.N.; Chua, K.C.; Sikdar, B. Mutual Authentication in IoT Systems Using Physical Unclonable Functions. IEEE Internet Things J. 2017, 4, 1327–1340. [Google Scholar] [CrossRef]
- Frikken, K.B.; Blanton, M.; Atallah, M.J. Robust authentication using physically unclonable functions. In International Conference on Information Security; Springer: Berlin/Heidelberg, Germany, 2009; pp. 262–277. [Google Scholar]
- Chatterjee, U.; Chakraborty, R.S.; Mukhopadhyay, D. A PUF-based secure communication protocol for IoT. ACM Trans. Embed. Comput. Syst. (TECS) 2017, 16, 1–25. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. Two birds with one stone: Two-factor authentication with security beyond conventional bound. IEEE Trans. Dependable Secur. Comput. 2018, 15, 708–722. [Google Scholar] [CrossRef]
- Zhou, Y.; Long, X.; Chen, L.; Yang, Z. Conditional privacy-preserving authentication and key agreement scheme for roaming services in VANETs. J. Inf. Secur. Appl. 2019, 47, 295–301. [Google Scholar] [CrossRef]
- Wu, T.-Y.; Lee, Z.; Yang, L.; Chen, C.-M. A provably secure authentication and key exchange protocol in vehicular ad hoc networks. Secur. Commun. Netw. 2021, 2021, 9944460. [Google Scholar] [CrossRef]
| Symbols | Meaning |
|---|---|
| , and | Identity of TA, RSU and , respectively |
| The biometric information of | |
| The password of | |
| The biometric key of | |
| The reproduction parameter of | |
| The private key of TA | |
| The private key of RSU | |
| The public key of RSU | |
| The adversary or attacker | |
| The collision resistance one hash function | |
| The symmetric encryption/decryption | |
| The XOR operator | |
| The normal addition operator | |
| The concatenation operator | |
| , | The freshly generated random numbers |
| , | The nonzero positive random number |
| , | The nonzero positive random number |
| The randomized counter | |
| , , , , | Timestamps |
| Properties/Attacks | [5] | [15] | [16] | [21] | [29] | [30] | Ours |
|---|---|---|---|---|---|---|---|
| Unlinkability | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ |
| Mutual authentication | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ |
| Anonymity | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Conditional privacy preservation | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✓ |
| Perfect forward secrecy | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Session key secrecy | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Known session key secrecy | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ |
| Key agreement | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| N-factor secrecy | ✗ | - | ✗ | ✗ | ✗ | ✗ | ✓ |
| Resist message modification | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Resist impersonation attacks | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Resist replay attacks | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Resist password guessing attacks | ✓ | - | ✓ | ✓ | - | ✓ | ✓ |
| Resist identity guessing attacks | ✗ | - | ✓ | ✓ | ✓ | ✓ | ✓ |
| Resist stolen SC attacks | ✗ | ✗ | - | ✓ | - | - | ✓ |
| RSU captured attacks | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ |
| Notations | Description | Execution Time (ms) |
|---|---|---|
| Scalar multiplication | 2.610 | |
| General hash function | 0.019 | |
| Symmetric encryption/decryption | 0.511 |
| Primitive Operations | Communication Cost (bits) |
|---|---|
| Elliptic Curve Point | 256 |
| Message | 256 |
| identity of individual participant | 256 |
| Hash function | 256 |
| Timestamp | 32 |
| Random number | 256 |
| Symmetric encryption/decryption | AES-128 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xie, Q.; Huang, J. Improvement of a Conditional Privacy-Preserving and Desynchronization-Resistant Authentication Protocol for IoV. Appl. Sci. 2024, 14, 2451. https://doi.org/10.3390/app14062451
Xie Q, Huang J. Improvement of a Conditional Privacy-Preserving and Desynchronization-Resistant Authentication Protocol for IoV. Applied Sciences. 2024; 14(6):2451. https://doi.org/10.3390/app14062451
Chicago/Turabian StyleXie, Qi, and Juanjuan Huang. 2024. "Improvement of a Conditional Privacy-Preserving and Desynchronization-Resistant Authentication Protocol for IoV" Applied Sciences 14, no. 6: 2451. https://doi.org/10.3390/app14062451
APA StyleXie, Q., & Huang, J. (2024). Improvement of a Conditional Privacy-Preserving and Desynchronization-Resistant Authentication Protocol for IoV. Applied Sciences, 14(6), 2451. https://doi.org/10.3390/app14062451







