3.2. Architectural Hints
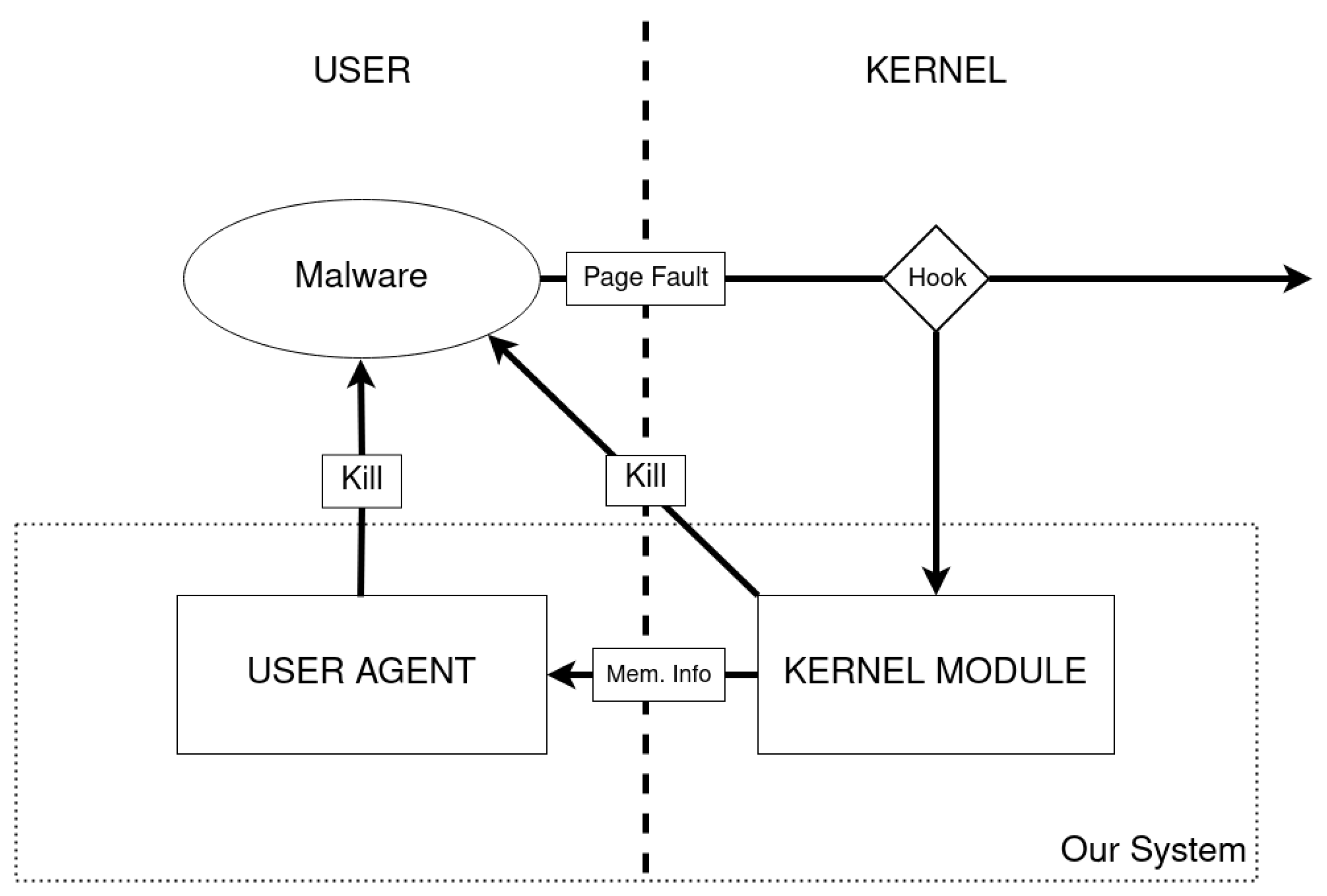
The objectives of our system are two-fold: we want to perform a comprehensive analysis of every executable page that can be exploited by an execution flow of a program, while minimizing at the same time the intrusiveness. To achieve these objectives, our system employs a multi-faceted approach, the scheme of which is summarized in
Figure 2.
The architecture of our solution exploits both a kernel-level layer and a user-level layer. The kernel-level layer, which is fully implemented as a Linux Kernel Module (LKM), performs two critical actions:
- (1)
It intercepts the first access to an executable page (or an updated executable page—this is the case of WX pages), which is carried out via an instruction fetch by the CPU;
- (2)
While handling the interception of the instruction fetch, and after the kernel materialized the target page in RAM, we perform critical checks on the page content which might lead to the forced termination of the application.
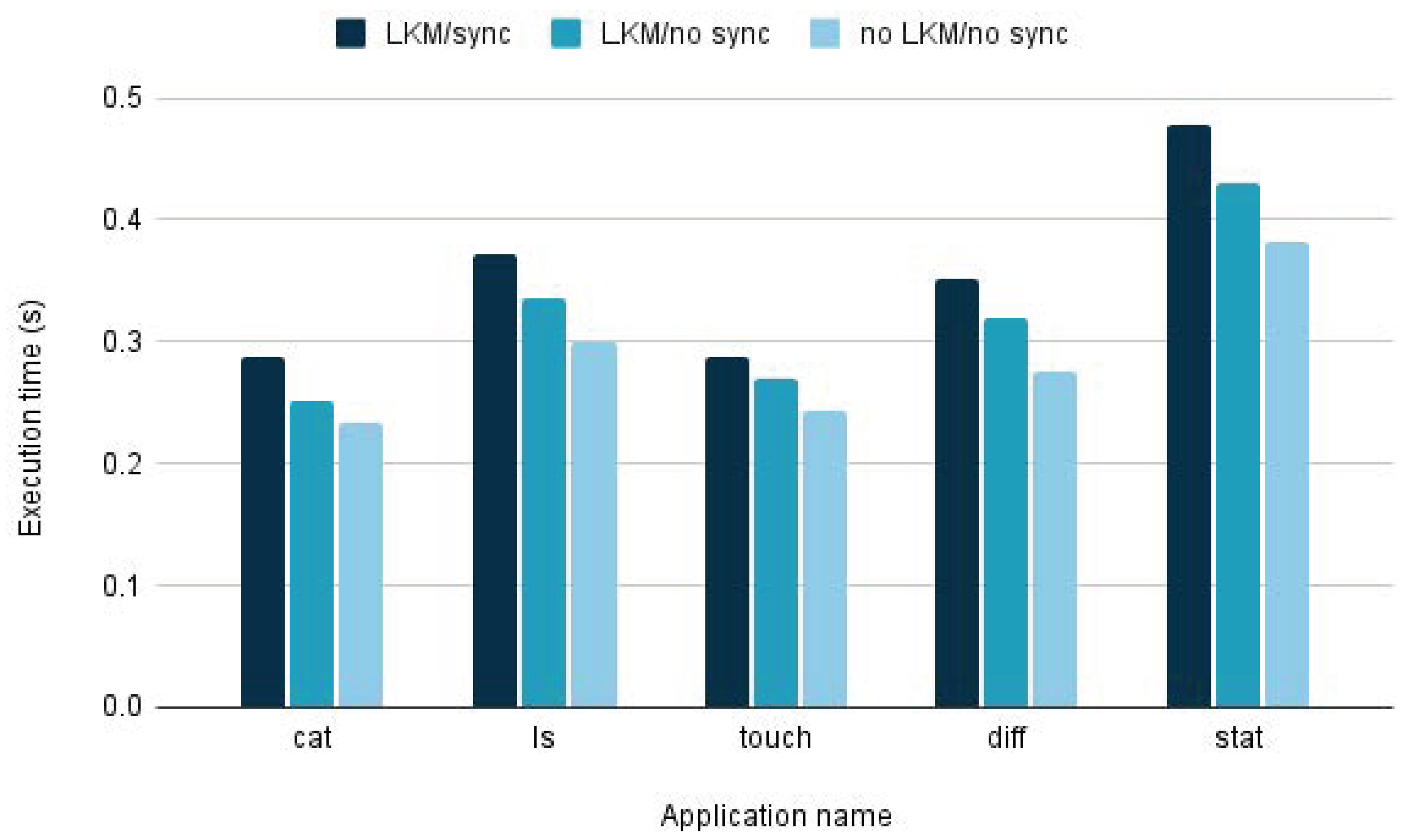
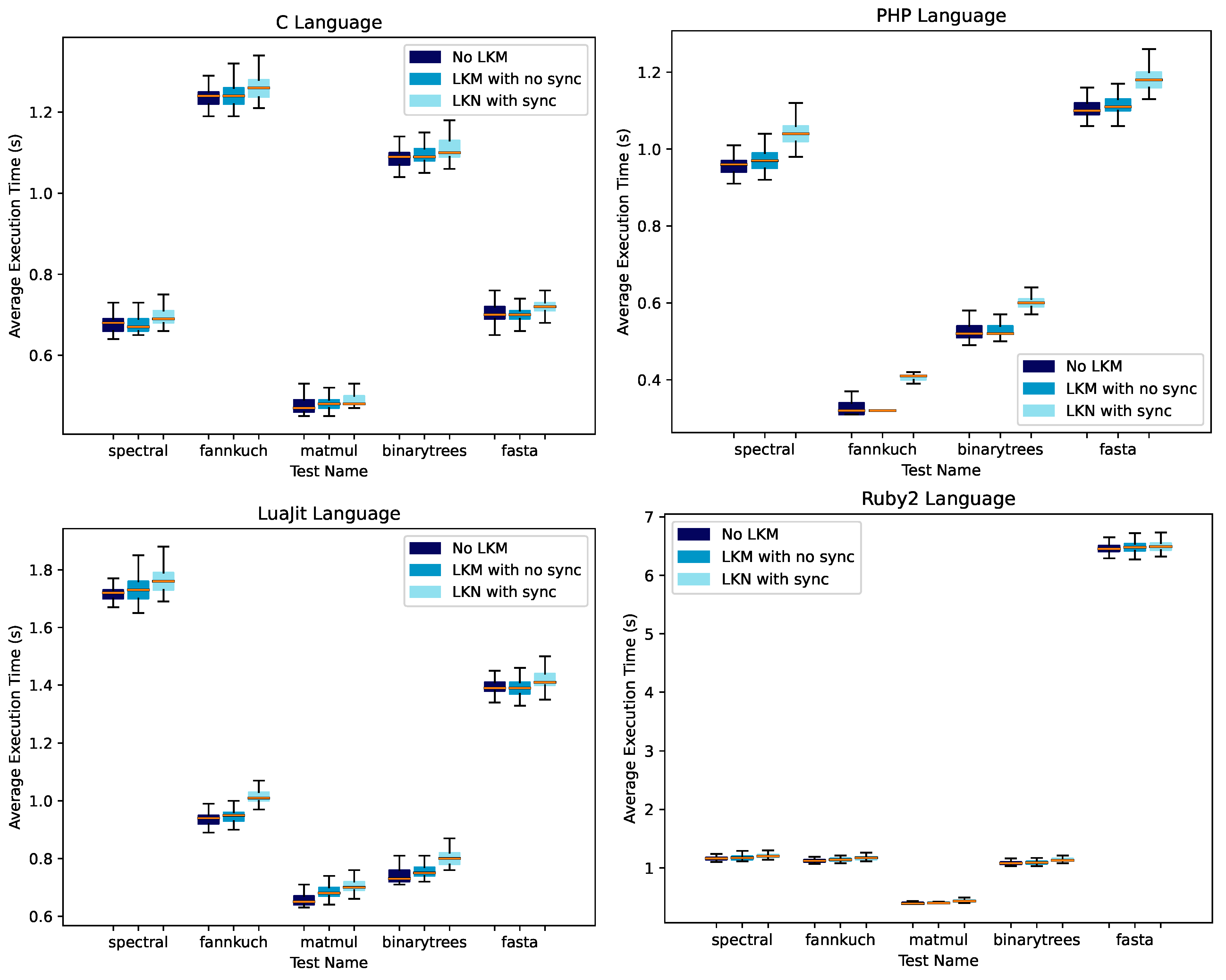
The verification process described in point (2) occurs within the same thread that initiated the access (for instruction fetch) to the executable page. Consequently, it operates synchronously concerning the application’s execution.
To ensure swift handling of this scenario, allowing the thread to quickly resume executing user-level code if the application termination is not prompted, our architecture integrates modules responsible for conducting these critical checks directly at the kernel level. However, in typical situations, it is essential to restrict the number of checks performed synchronously. For instance, a common scenario might involve merely verifying if the page content includes the embedding of shellcode. Limiting the synchronous checks helps maintain efficient and responsive execution of the application by balancing the critical verification tasks without impeding the performance of the user-level code.
To still enable a more ample check of the page content, we exploit the user-level part of the architecture. It involves a program that receives input from the kernel in the form of a tuple: . The denotes the position (linear address) of the first fetched instruction within the page. This program conducts a more comprehensive check of the page content asynchronously concerning the thread that initiated the page access. This approach allows for a broader examination to detect potential malicious signatures within the executable page, carried out off the critical path of the original application’s execution. This checking program can be configured to take action, such as blocking the application (e.g., via the kill() system call), if it identifies any security-critical aspect during the asynchronous check.
Moreover, the
included in the tuple represents a snapshot of the executable page captured at the time of the intercepted instruction fetch. This snapshot capability enables the analysis of the complete history of the content of any WX (Write-Execute) page over time, a feature not facilitated by solutions such as in [
21]. This historical analysis provides a more comprehensive view of changes occurring within WX pages, enhancing the detection and understanding of potential security threats.
The combination of an initial synchronous check at the kernel level followed by a subsequent asynchronous check at the user level provides configurability based on the criticality of the hosted services within the system. For services of lower criticality, the synchronous check can be omitted entirely. This prioritizes application performance, allowing the application to continue functioning without delay, even if the asynchronous check later identifies a malicious signature in an executable page that the application has already accessed. This modular approach offers flexibility and adaptability. It allows for straightforward customization and future expansion while enhancing reliability and ease of maintenance. By decoupling the synchronous and asynchronous checks and tailoring their execution based on service criticality, the system can strike a balance between performance optimization and security enforcement, ensuring efficient operation while maintaining a level of security appropriate for the service’s importance.
We also note that performing the kill of the malicious application in JITScanner is a baseline choice, but alternative solutions for the handling of the malware program can be simply adopted. As an example, there are works that have proposed the dynamic setup of facilities at the operating system level in order to manage malware suspicions in specific programs (see, e.g., [
3]). The combination of JITScanner with these solutions can be immediate since, rather than killing the identified malware, JITScanner could simply alert an external system (passing to it baseline information, as for example identifiers of processes and users) in order to let that system start the management of the malware according to its own rules.
In the JITScanner architecture, the user-level component can effectively utilize existing code analysis methods accessible in the literature. In our current implementation, we have developed a user-level layer centered around Yara rules, a well-established system renowned for malware classification [
25]. Regarding the kernel-level synchronous check, we have incorporated a baseline check to identify the presence of the meterpreter shellcode within the memory page.
In any case, the check facilities within our solution can be perceived as plug-ins that are highly extensible and can be effortlessly expanded at any given moment. Fundamentally, our solution comprises an engine dedicated to the management of executable pages within an address space. This engine serves as a stable core foundation upon which various checking mechanisms can be built, refined, and enhanced over time.
This modular architecture aligns with our primary research objective, which revolves around providing an effective kernel-level system to combat dynamic loading and obfuscation techniques. These techniques often pose significant challenges to traditional static analysis methodologies. By focusing on the core engine for managing executable pages and offering a flexible framework for diverse checking mechanisms, our solution aims to address these challenges and ensure an evolving and robust defense against dynamic loading and obfuscation techniques commonly utilized by malicious actors.
Our implementation has been tailored for kernel version 5 of Linux, and for x86 processors with PAE (Physical Address Extension) enabled. However, generalizing our LKM to support other architectures should be easy, since we have utilized generic kernel functions wherever possible.
3.3. Executable-Page Access Interception
Within JITScanner’s framework, the primary focus lies in intercepting a genuine access to an executable virtual page, particularly when the CPU actively fetches an instruction from that specific virtual page. Consequently, our solution does not initiate checks on any executable virtual page until the moment when the application actually requires the binary code contained within it.
In line with the typical on-demand paging process, this need arises after an executable page is allocated by the kernel and placed into an RAM frame. Subsequently, the page-table of the application is updated, granting the execution capability and making the page accessible. It is precisely at this point—when the CPU fetches instructions from the executable page—that JITScanner intervenes to conduct the necessary checks and verifications, ensuring the integrity and security of the fetched binary code.
To precisely identify the moment when a memory page is initially accessed for an instruction fetch, our solution employs a series of strategically placed kernel probes within the page fault handling process. Specifically, we utilize the kprobe subsystem provided by the Linux operating system to set up a hook on the return of a core page-fault handling procedure. In greater detail, we have installed a kretprobe on the handle_mm_fault() procedure within the Linux kernel. Upon completion of this procedure’s execution, the target page that triggered the fault has already been materialized in RAM. At this stage, we can conduct the synchronous check on its content since it is now available in memory. Additionally, we take a snapshot of the page, which is managed for subsequent examination by the asynchronous check. This approach allows us to precisely time the execution of checks and efficiently manage the content of accessed pages for both synchronous and asynchronous analysis.
An essential consideration in our hook execution is to perform the page check only if the accessed page for instruction fetch is a legitimate page within the address space. Any attempt to access a non-legitimate page does not result in the actual materialization of the page in RAM through the operating system’s handle_mm_fault() function. Instead, it leads to the delivery of the SIGSEGV signal to the application, indicating a segmentation fault or an invalid memory access attempt.
This distinction is particularly pertinent in our management of WX (Write-Execute) pages. For these pages, an “original” page fault triggered by the operating system—associated with the first access to the virtual executable page, which we intercept using the hook—is insufficient for checking the absence of malicious signatures. As a result, careful consideration is necessary to ensure that our page checks are executed only when the accessed pages are legitimate within the application’s address space, thereby optimizing the effectiveness of our security measures while avoiding unnecessary checks on non-legitimate pages.
For managing WX (Write-Execute) pages, we have developed an innovative kernel-level mechanism that dynamically adjusts the actual page permissions while the program is executing. Despite these dynamic modifications, the page remains “logically” accessible at the application level in both Write (W) and Execute (X) modes.
This kernel-level facility operates entirely transparently to the actual program, ensuring that the application is unaware of these permission modifications. However, it grants us the capability to monitor and track page access—whether for writing data or fetching instructions—throughout the program’s execution.
Essentially, this facility establishes a shadow state machine that aligns with the legitimate permissions granted to the application for the page. By dynamically managing and tracking the permissions without the application’s knowledge, we can maintain security while ensuring necessary access to the pages, offering a nuanced and transparent approach to managing WX pages.
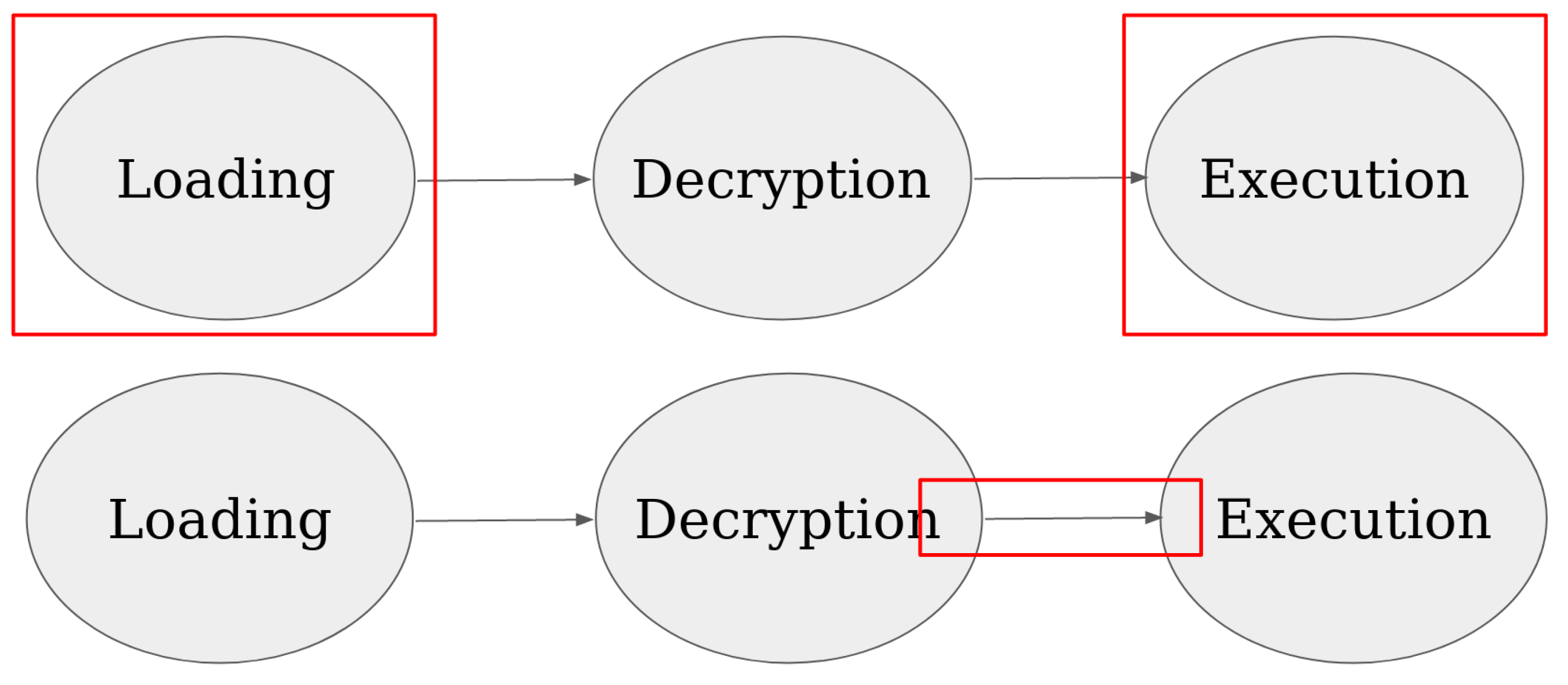
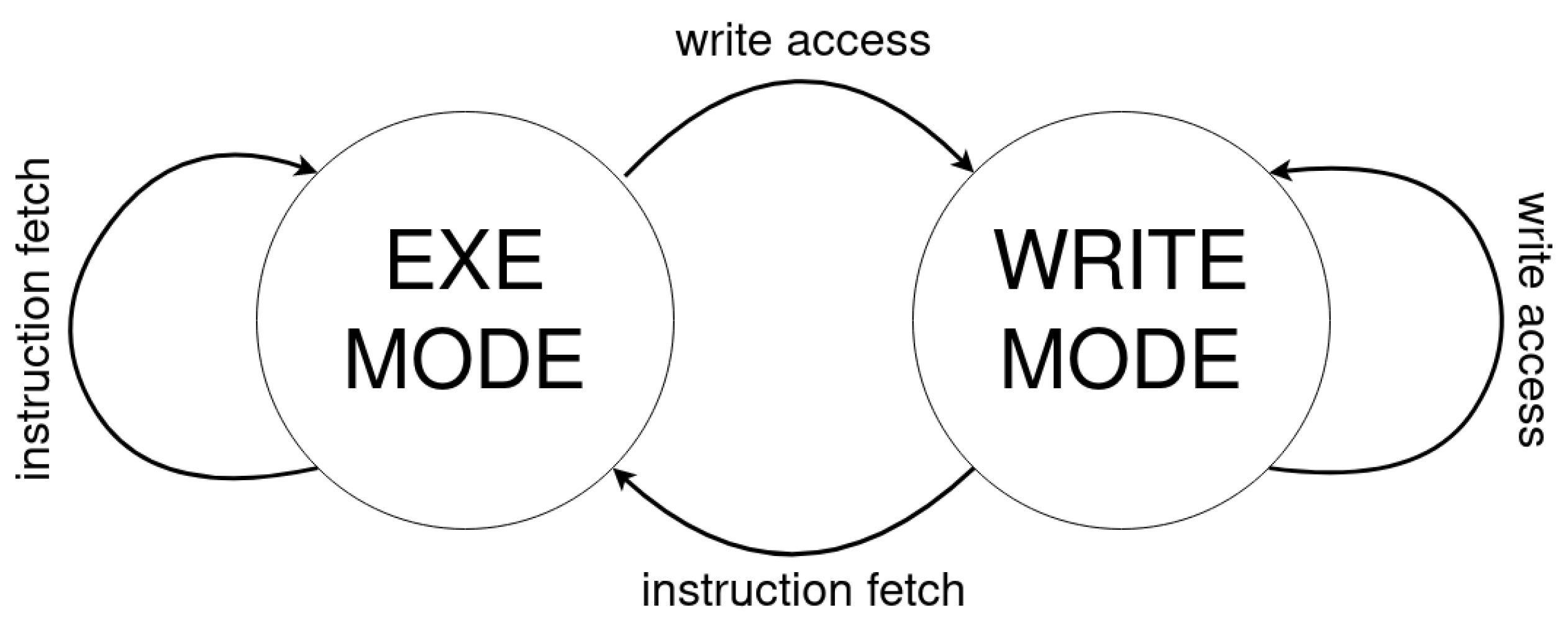
The shadow state machine within our system implements a time-separated alternating mechanism between write and execute permissions for pages. When a page is in “write mode” in the shadow state machine, it allows page-update operations without triggering user execution-mode interruptions such as page faults or interception via our kernel-level support. However, any attempt to execute instructions from that page will result in a fault, redirecting control to our kernel-level hook for interception and handling. Conversely, when a page is in “exec mode” within the shadow state machine, it permits instruction-fetch operations. In this mode, attempts to update the page will trigger a fault, intercepted by our kernel-level support for handling. This alternating logic between write and execute permissions ensures a controlled and secure mechanism for managing page access and operations within the application’s address space. A representation of this logic is shown in
Figure 3.
With our facility that manages page permissions dynamically, we have the capability to trigger the page-verification process whenever the access mode transitions between write and execute permissions. However, based on the goals of our solution, we believe that conducting a signature check on the executable page is essential only during instruction fetches. This is the critical moment where potential exploitation of malicious code could occur, making it the prime instance for initiating the signature check.
By specifically targeting the instruction-fetch operations for page verification, we can efficiently focus our security measures on the most vulnerable points in time, ensuring that checks for malicious signatures are conducted precisely when the executable page is being accessed for instruction execution. This targeted approach enhances the effectiveness of our security measures while optimizing performance by avoiding unnecessary checks during other access modes.
To support shadowing, we set the XD bit on the lowest level of the page table (the PTE), disabling instruction fetches from the page as soon as the WX page is materialized. By doing this, when the user program tries to execute the instructions on the page, a page fault occurs due to the lack of required permissions. We intercept this page fault and do the following:
Clear the XD bit, to allow the user to execute the page from now on;
Clear the W bit, to disable writes on the page;
Suppress the SIGSEGV signal generated by the invalid access to prevent the kernel from terminating the user program or making it run an SIGSEGV handler.
To handle the interception of kernel-level functions responsible for delivering the SIGSEGV signal during CPU fetches, our approach involves suppressing this signal, since the page fault is generated by our shadowing mechanism. In Linux, faults occurring during instruction fetches are managed within the architecture-specific code of the kernel before calling the handle_mm_fault() function. However, these functions cannot be directly hooked using the kprobe mechanism. As an alternative, we have chosen to place a kernel probe on the force_sig_fault() function, which is triggered whenever an invalid memory access occurs. By hooking into this function, we can effectively suppress the delivery of the signal. Moreover, the synchronous checking of page content and the passage of page snapshots to the asynchronous checker are handled through the hook installed on the return of the handle_mm_fault() function. This comprehensive approach enables us to intercept and manage the necessary signals and functions, ensuring the seamless operation of our shadowing mechanism and the subsequent verification processes.
To effectively handle the hook for the force_sig_fault() kernel function, it is crucial to differentiate between standard invalid-access faults and those triggered by our shadow state machine. For this purpose, we utilize two unused bits within the lowest level page table entry (PTE) of the x86 processor. These bits store the original write and execute permissions for a specific page before any modifications by our module.
During the interception of a fault, we check these bits within the PTE. If the fault originates from a genuine invalid access generated by the program and not by our shadow state machine, the bits help us identify this distinction. In such cases, we allow the kernel to handle the fault without any intervention from our module. This mechanism ensures that our system effectively identifies and manages faults triggered by the shadow state machine while allowing standard invalid-access faults to be handled conventionally by the kernel.
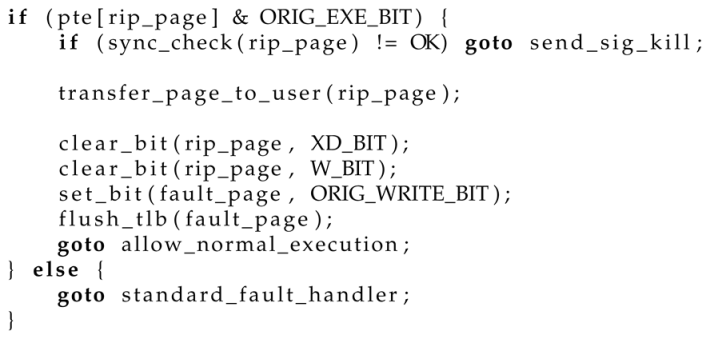
We present in Listings 1 and 2 the main parts related to the hook-based page management process. In Listing 1, we illustrate the management of our state machine in the handle_mm_fault() hook, which is invoked on page materialization and a write access violation. The steps are as follows: first, we do some general checks to ensure that the fault occurred in a valid vm_area with the appropriate flags. We then examine our ORIG_WRITE_BIT bit in the page table, to verify if the page has been modified by our state machine and if writes were initially permitted, if so, we disable execution and allow the write. Otherwise, we let the kernel handle the fault conventionally. In Listing 2, we report the hook for force_sig_fault(), which is called on an execute-address violation. Here, we check if our ORIG_EXE_BIT bit is set in the page table. If it is not set, we let the kernel handle the fault. If it is set, this fault is generated under our state machine and needs to be resolved. To this end, we first run a synchronous check of the page content at kernel level. If a threat is detected, we allow the kernel to complete the fault, resulting in the delivery of the SIGKILL signal to the running process. If no threat is found during the kernel-level check, we transfer the page snapshot to the user agent for asynchronous checking and then fix the page table to allow the execution to continue.
The necessity of a TLB (Translation Lookaside Buffer) flush within the code listings is crucial due to the way TLBs maintain information based on the previous access permissions of a page. When the permissions of a specific page are modified, it becomes imperative to eliminate this page’s address from the TLB across all CPUs involved in executing threads operating within the same address space as the intercepted thread accessing memory.
In our implementation, we have leveraged the __flush_tlb_one_user API provided by the Linux kernel for this purpose. This API allows us to perform a TLB flush for a specific page address. Additionally, we combine this API with the Inter-Processor-Interrupt (IPI) approach to execute the function across all CPUs involved. This approach ensures that the TLBs across all relevant CPUs are updated and purged of the outdated page information, aligning them with the modified access permissions for the page.
| Listing 1. The hook on handle_mm_fault(). |
![Applsci 14 01912 i001]() |
| Listing 2. The hook on force_sig_fault(). |
![Applsci 14 01912 i002]() |
Finally, installing hooks on system calls such as mprotect() is a significant step within our system. This particular system call is capable of altering the access permissions to a page, such as adding executable (X) or writable (W) permissions to a page that previously had different permissions. By placing hooks on system calls such as mprotect(), we ensure the correlation between any change in access permissions and the need to recheck the page content upon the next instruction fetch from that page. This approach guarantees that whenever there is a modification in permissions using mprotect() or similar calls, our system is aware of it. Consequently, it can plan to perform necessary content rechecks when the page is accessed for instruction fetching, aligning with the modified permissions and ensuring security integrity.
3.4. Protection Against DoS
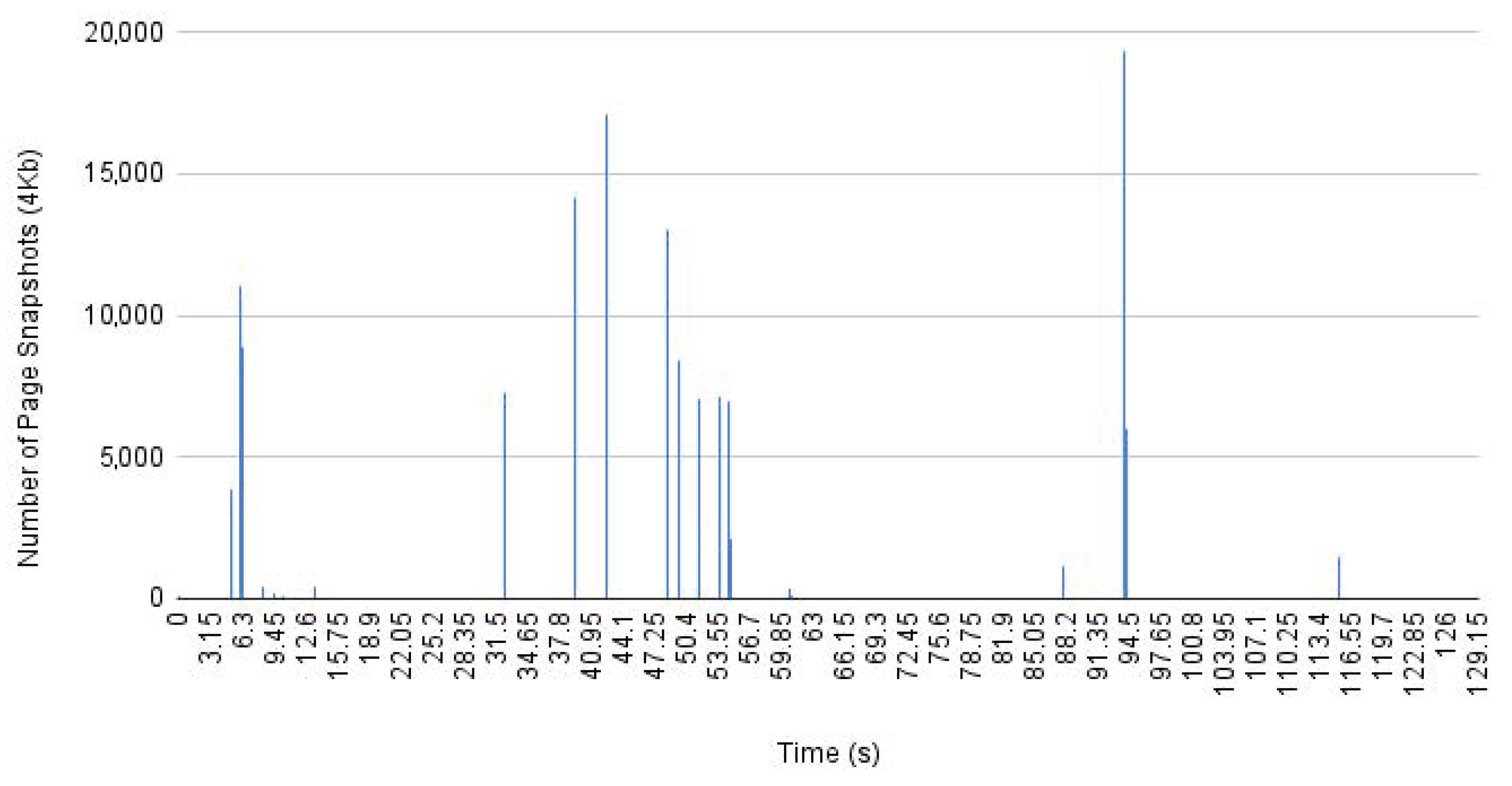
It is integral for our system that the page fault hook and the driver, responsible for transferring page content and metadata to the user-space agent, communicate efficiently. In our architecture, we employ a hash table for this purpose. This hash table organizes intercepted pages, creating copies (page snapshots) and categorizing them based on their associated process ID. These pages are stored within different buckets in the hash table, allowing parallel access for both insertion (storing a copy of an executable page to be checked) and deletion (transferring the page copy to a user-space buffer).
However, a critical aspect of this solution is the potential for a flow of page-fault interceptions, potentially caused by a malicious program intending to disrupt our page-management system. This influx of page faults can result in uncontrolled effects due to the intensive memory usage required to store copies of executable pages in the kernel-level hash table before transferring them to the user-space agent.
This scenario of numerous intercepted page faults can lead to an excessive volume of memory usage within the kernel, potentially impacting system stability and performance. It is crucial to develop mechanisms or safeguards within the system to handle such scenarios efficiently, ensuring that the system remains resilient against potential attacks while maintaining its stability and operational integrity.
To fortify the system against Denial of Service (DoS) attacks stemming from memory depletion due to excessive kernel-level allocations, we have integrated an additional hash table. This secondary hash table maintains support for parallel access across different buckets. Each entry within this hash table is responsible for tracking the user ID associated with pending executable-page copies awaiting delivery to the user-level agent, along with a counter representing these pages.
As a preventive measure, we have implemented a threshold mechanism within the system. When the counter surpasses a specified threshold value for a particular user’s pending page copies, it signifies an abnormal influx of page faults. In response, actions are taken to prevent potential DoS scenarios. The system can be configured to either terminate or block the process generating additional page faults on behalf of the same user.
This configuration flexibility is achieved by exposing a parameter within our software architecture, accessible through the /sys file system. This level of configurability enables dynamic adjustments based on the system’s operational needs and the criticality of the protected environment. By providing this flexibility, administrators can fine-tune the system’s response, choosing between process termination or blocking based on the current circumstances and security requirements.
Our system implementes a Time-to-Live (TTL) mechanism as a form of rate-limiting control to prevent excessive page copies from being generated for the same user ID. Once an event (kill/block) occurs due to surpassing the threshold, the corresponding entry in the hash table associated with that user enters a TTL period.
During this TTL period, the counter within the hash table entry is decremented each time a copy of an executable page related to the same user ID is successfully delivered to the user-space agent. However, if processes from the same user generate additional page faults requesting page copies during this TTL period, they are still subjected to termination or blocking. Essentially, no new page copies are allowed for processes of that same user throughout the entire TTL duration.
Furthermore, to contrast DoS caused by excessive memory usage of this second hash table, we added a second TTL. If the entry of the hash table associated with a given user ID keeps a counter that remains set to zero for the whole TTL, then this entry is removed from the hash table—it will be reinserted in the future upon a page fault interception for a program run from the same user ID. This avoids keeping useless entries in this hash table, and thus, contrasting attacks that can be based on the exploitation of programs with the setuid flag active. In fact, these would allow an attacker to operate via multiple user ID values, enlarging at some point in time the number of entries of the hash table.