U-TFF: A U-Net-Based Anomaly Detection Framework for Robotic Manipulator Energy Consumption Auditing Using Fast Fourier Transform
Abstract
1. Introduction
- Energy consumption serves as the sole data source that is acquired through a side monitoring channel for anomaly detection. This design mitigates the risk of targeted malicious attacks on measurement sensors and enhances the reliability of the proposed method. Notably, it also offers great potential for extension to other systems and applications.
- A novel neural network block for Time–Frequency Fusion is introduced to develop a reconstruction network for anomaly detection. This new block leverages the Fast Fourier Transform to capture essential features in the frequency domain. This complementary knowledge facilitates the feature learning process by enriching feature representations, leading to improved detection performance, especially for anomalies with strong presentation in the frequency domain.
- For this study, we compiled a tailored dataset documenting the energy consumption during the operational phases of a robotic manipulator. This dataset comprises over 6000 instances of energy consumption during normal operations, which were utilized to train the proposed model. Furthermore, more than 6000 instances of energy consumption incorporating simulated anomalies were collected for model verification purposes. The dataset has been made publicly available as an open-source resource to facilitating its utilization and evaluation by fellow researchers.
2. Related Work
2.1. Side-Channel Mechanisms in Anomaly Detection
2.2. Semi-Supervised Learning Anomaly Detection Approaches
2.3. Fast Fourier Transform in Deep Learning
3. Methodology
- Offline model training: In this phase, the robotic manipulator functions normally when executing designated tasks. The corresponding energy consumption data is utilized by the reconstruction network to learn the distribution of normal data patterns. As part of the model training process, a loss function is defined to measure the disparity between the reconstructed output and the original energy consumption data. This loss function quantifying the reconstruction error is then utilized in backpropagation to refine and enhance the performance of the network iteratively.
- Online anomaly detection: A sufficiently trained model should demonstrate the ability to accurately reconstruct input samples following normal patterns with minimal reconstruction errors. However, notable changes may occur in the energy consumption profiles of the robotic manipulator when subjected to attacks or other anomalous conditions. Consequently, the network may fail to accurately reconstruct these anomalous inputs using the normal patterns learned in the offline phase, leading to higher errors. Thus, a static threshold is determined to distinguish anomalies from normal data. Specifically, an input sample is flagged as an anomaly if its reconstruction error value is higher than the predefined threshold.
3.1. Data Processing
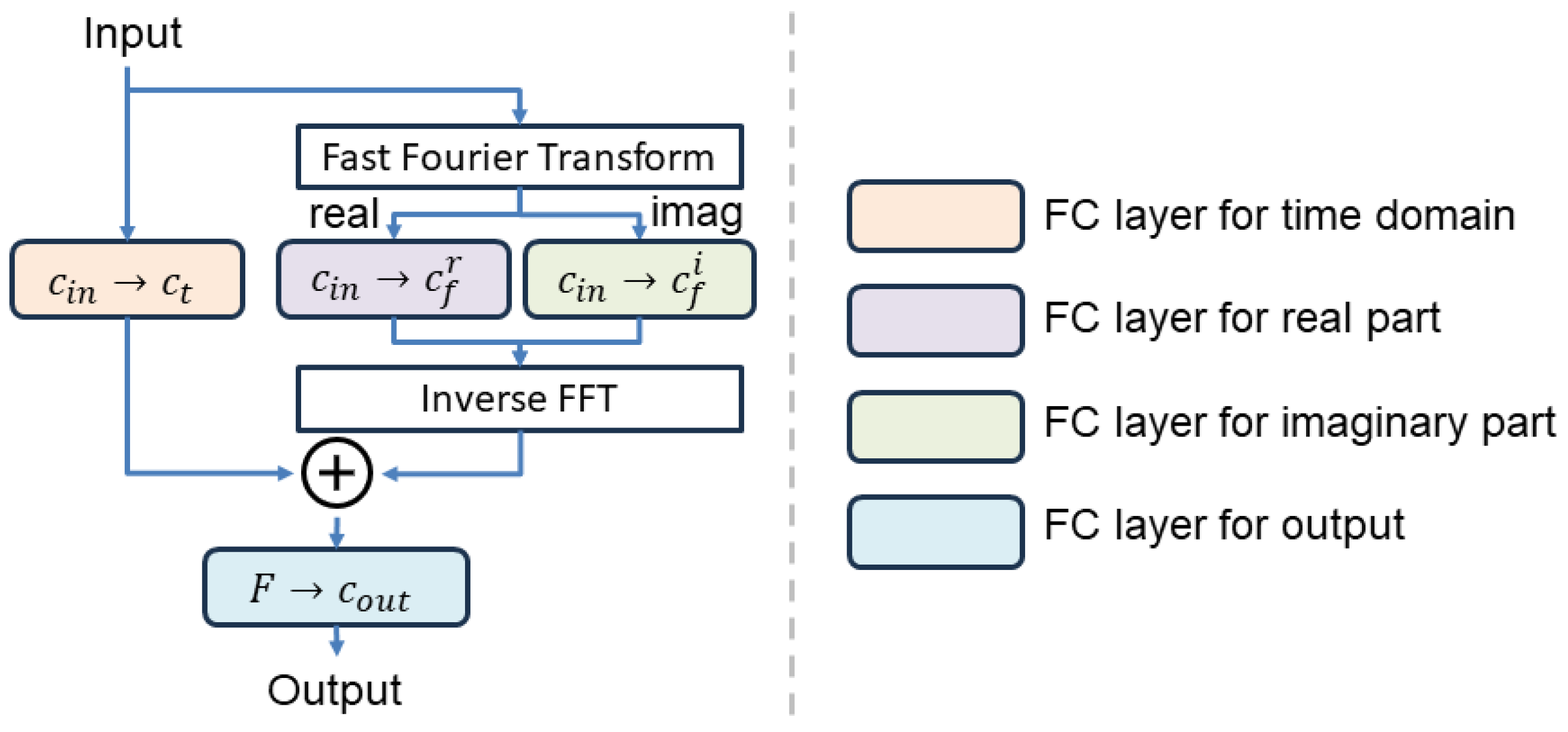
3.2. Time–Frequency Fusion Block
3.3. U-TFF
4. Experiment
4.1. Robotic Manipulator
4.2. Executed Tasks
4.3. Simulated Attack
5. Results and Discussion
5.1. Benchmark Model
5.2. Evaluation Metrics
5.3. Results and Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Liu, T.; Xu, C.; Qiao, Y.; Jiang, C.; Yu, J. Particle Filter SLAM for Vehicle Localization. arXiv 2024, arXiv:2402.07429. [Google Scholar]
- Bui, H.D.; Nguyen, H.; La, H.M.; Li, S. A deep learning-based autonomous robot manipulator for sorting application. In Proceedings of the 2020 Fourth IEEE International Conference on Robotic Computing (IRC), Virtual, 9–11 November 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 298–305. [Google Scholar]
- Zhang, K.; Hutson, C.; Knighton, J.; Herrmann, G.; Scott, T. Radiation tolerance testing methodology of robotic manipulator prior to nuclear waste handling. Front. Robot. AI 2020, 7, 6. [Google Scholar] [CrossRef] [PubMed]
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.K.; Du, X.; Ali, I.; Guizani, M. A survey of machine and deep learning methods for internet of things (IoT) security. IEEE Commun. Surv. Tutor. 2020, 22, 1646–1685. [Google Scholar] [CrossRef]
- Song, G.; Hong, S.H.; Kyzer, T.; Wang, Y. An Energy Consumption Auditing Anomaly Detection System of Robotic Manipulators based on a Generative Adversarial Network. In Proceedings of the Annual Conference of the PHM Society, Salt Lake City, UT, USA, 28 October–2 November 2023; Volume 15. [Google Scholar]
- Jung, W.; Feng, Y.; Khan, S.A.; Xin, C.; Zhao, D.; Zhou, G. DeepAuditor: Distributed Online Intrusion Detection System for IoT devices via Power Side-channel Auditing. In Proceedings of the 2022 21st ACM/IEEE International Conference on Information Processing in Sensor Networks (IPSN), Virtual, 4–6 May 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 415–427. [Google Scholar]
- Zhang, Y.; Zhu, M.; Gui, K.; Yu, J.; Hao, Y.; Sun, H. Development and application of a monte carlo tree search algorithm for simulating da vinci code game strategies. arXiv 2024, arXiv:2403.10720. [Google Scholar]
- Zang, H.; Li, S.; Dong, X.; Ma, D.; Dang, B. Evaluating the social impact of ai in manufacturing: A methodological framework for ethical production. Acad. J. Sociol. Manag. 2024, 2, 21–25. [Google Scholar]
- Zhu, M.; Zhang, Y.; Gong, Y.; Xu, C.; Xiang, Y. Enhancing Credit Card Fraud Detection: A Neural Network and SMOTE Integrated Approach. J. Theory Pract. Eng. Sci. 2024, 4, 23–30. [Google Scholar] [CrossRef]
- Dong, X.; Dang, B.; Zang, H.; Li, S.; Ma, D. The prediction trend of enterprise financial risk based on machine learning arima model. J. Theory Pract. Eng. Sci. 2024, 4, 65–71. [Google Scholar]
- Audibert, J.; Michiardi, P.; Guyard, F.; Marti, S.; Zuluaga, M.A. Usad: Unsupervised anomaly detection on multivariate time series. In Proceedings of the 26th ACM SIGKDD International Conference on Knowledge Discovery & Data Mining, Virtual, 23–27 August 2020; pp. 3395–3404. [Google Scholar]
- Zhang, Y.; Zhu, M.; Gong, Y.; Ding, R. Optimizing science question ranking through model and retrieval-augmented generation. Int. J. Comput. Sci. Inf. Technol. 2023, 1, 124–130. [Google Scholar] [CrossRef]
- Su, J.; Jiang, C.; Jin, X.; Qiao, Y.; Xiao, T.; Ma, H.; Wei, R.; Jing, Z.; Xu, J.; Lin, J. Large Language Models for Forecasting and Anomaly Detection: A Systematic Literature Review. arXiv 2024, arXiv:2402.10350. [Google Scholar]
- Liu, C.; He, S.; Zhou, Q.; Li, S.; Meng, W. Large Language Model Guided Knowledge Distillation for Time Series Anomaly Detection. arXiv 2024, arXiv:2401.15123. [Google Scholar]
- Zhu, M.; Zhang, Y.; Gong, Y.; Xing, K.; Yan, X.; Song, J. Ensemble Methodology: Innovations in Credit Default Prediction Using LightGBM, XGBoost, and LocalEnsemble. arXiv 2024, arXiv:2402.17979. [Google Scholar]
- Ronneberger, O.; Fischer, P.; Brox, T. U-net: Convolutional networks for biomedical image segmentation. In Proceedings of the Medical Image Computing and Computer-Assisted Intervention—MICCAI 2015: 18th International Conference, Part III 18, Munich, Germany, 5–9 October 2015; Springer: Munich, Germany, 2015; pp. 234–241. [Google Scholar]
- Lightbody, D.; Ngo, D.M.; Temko, A.; Murphy, C.C.; Popovici, E. Dragon_Pi: IoT Side-Channel Power Data Intrusion Detection Dataset and Unsupervised Convolutional Autoencoder for Intrusion Detection. Future Internet 2024, 16, 88. [Google Scholar] [CrossRef]
- Raeker-Jordan, N.; Chung, J.; Kong, Z.J.; Williams, C. Ensuring additive manufacturing quality and cyber–physical security via side-channel measurements and transmissions. J. Manuf. Syst. 2024, 73, 275–286. [Google Scholar] [CrossRef]
- Yu, S.Y.; Malawade, A.V.; Chhetri, S.R.; Al Faruque, M.A. Sabotage attack detection for additive manufacturing systems. IEEE Access 2020, 8, 27218–27231. [Google Scholar] [CrossRef]
- Meng, X.; Wang, S.; Liang, Z.; Yao, D.; Zhou, J.; Zhang, Y. Semi-supervised anomaly detection in dynamic communication networks. Inf. Sci. 2021, 571, 527–542. [Google Scholar] [CrossRef]
- Liu, J.; Song, K.; Feng, M.; Yan, Y.; Tu, Z.; Zhu, L. Semi-supervised anomaly detection with dual prototypes autoencoder for industrial surface inspection. Opt. Lasers Eng. 2021, 136, 106324. [Google Scholar] [CrossRef]
- Yang, L.; Chen, J.; Wang, Z.; Wang, W.; Jiang, J.; Dong, X.; Zhang, W. Semi-supervised log-based anomaly detection via probabilistic label estimation. In Proceedings of the 2021 IEEE/ACM 43rd International Conference on Software Engineering (ICSE), Madrid, Spain, 22 May–30 May 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1448–1460. [Google Scholar]
- Jalayer, M.; Orsenigo, C.; Vercellis, C. Fault detection and diagnosis for rotating machinery: A model based on convolutional LSTM, Fast Fourier and continuous wavelet transforms. Comput. Ind. 2021, 125, 103378. [Google Scholar] [CrossRef]
- Li, Z.; Liu, X.; Incecik, A.; Gupta, M.K.; Królczyk, G.M.; Gardoni, P. A novel ensemble deep learning model for cutting tool wear monitoring using audio sensors. J. Manuf. Process. 2022, 79, 233–249. [Google Scholar] [CrossRef]
- Li, M.; Chen, W. FFT-based deep feature learning method for EEG classification. Biomed. Signal Process. Control 2021, 66, 102492. [Google Scholar] [CrossRef]
- Song, G.; Hong, S.H.; Kyzer, T.; Wang, Y. Energy consumption auditing based on a generative adversarial network for anomaly detection of robotic manipulators. Future Gener. Comput. Syst. 2023, 149, 376–389. [Google Scholar] [CrossRef]
- Nantel, E. 4 DoF Robotic Arm. Available online: https://wiki.lynxmotion.com/info/wiki/lynxmotion/view/ses-v2-arms/lss-4dof-arm/#HSpecifications (accessed on 26 May 2024).
- Hong, S.H.; Kyzer, T.; Cornelius, J.; Zahiri, F.; Wang, Y. Intelligent anomaly detection of robot manipulator based on energy consumption auditing. In Proceedings of the 2022 IEEE Aerospace Conference (AERO), Big Sky, MT, USA, 5–12 March 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–11. [Google Scholar]
- Xu, J.; Wu, H.; Wang, J.; Long, M. Anomaly transformer: Time series anomaly detection with association discrepancy. arXiv 2021, arXiv:2110.02642. [Google Scholar]
- Geiger, A.; Liu, D.; Alnegheimish, S.; Cuesta-Infante, A.; Veeramachaneni, K. Tadgan: Time series anomaly detection using generative adversarial networks. In Proceedings of the 2020 IEEE International Conference on Big Data (Big Data), Virtual, 10–13 December 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 33–43. [Google Scholar]
- Xiang, Y.; Huo, S.; Wu, Y.; Gong, Y.; Zhu, M. Integrating AI for Enhanced Exploration of Video Recommendation Algorithm via Improved Collaborative Filtering. J. Theory Pract. Eng. Sci. 2024, 4, 83–90. [Google Scholar]
- Guo, J.; Zhang, S.; Qian, Y.; Wang, Y. An adaptively weighted loss-enabled lightweight teacher–student model for real-time railroad inspection on edge devices. Neural Comput. Appl. 2023, 35, 24455–24472. [Google Scholar] [CrossRef]
- Liu, T.; Xu, C.; Qiao, Y.; Jiang, C.; Chen, W. News Recommendation with Attention Mechanism. arXiv 2024, arXiv:2402.07422. [Google Scholar]





| Confusion Matrix | Predicted Label | ||
|---|---|---|---|
| Positive | Negative | ||
| Ground Truth | Positive | 647 | 131 |
| Negative | 204 | 4018 | |
| Detection Manner | Recall | Precision | Accuracy |
|---|---|---|---|
| Instant-level | 0.8316 | 0.7603 | 0.933 |
| Event-level | 0.9375 | 0.9375 | 0.9394 |
| Model | Recall | Precision | Accuracy |
|---|---|---|---|
| DAE | 0.226 | 0.7346 | 0.8554 |
| GAN with one D | 0.787 | 0.8302 | 0.9368 |
| GAN with five D | 0.813 | 0.8044 | 0.935 |
| Anomaly Transformer | 0.342 | 0.9249 | 0.8881 |
| TadGAN | 0.3373 | 0.6142 | 0.8522 |
| Proposed | 0.8316 | 0.7603 | 0.933 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Song, G.; Hong, S.H.; Kyzer, T.; Wang, Y. U-TFF: A U-Net-Based Anomaly Detection Framework for Robotic Manipulator Energy Consumption Auditing Using Fast Fourier Transform. Appl. Sci. 2024, 14, 6202. https://doi.org/10.3390/app14146202
Song G, Hong SH, Kyzer T, Wang Y. U-TFF: A U-Net-Based Anomaly Detection Framework for Robotic Manipulator Energy Consumption Auditing Using Fast Fourier Transform. Applied Sciences. 2024; 14(14):6202. https://doi.org/10.3390/app14146202
Chicago/Turabian StyleSong, Ge, Seong Hyeon Hong, Tristan Kyzer, and Yi Wang. 2024. "U-TFF: A U-Net-Based Anomaly Detection Framework for Robotic Manipulator Energy Consumption Auditing Using Fast Fourier Transform" Applied Sciences 14, no. 14: 6202. https://doi.org/10.3390/app14146202
APA StyleSong, G., Hong, S. H., Kyzer, T., & Wang, Y. (2024). U-TFF: A U-Net-Based Anomaly Detection Framework for Robotic Manipulator Energy Consumption Auditing Using Fast Fourier Transform. Applied Sciences, 14(14), 6202. https://doi.org/10.3390/app14146202







