1. Introduction
As a natural evolution of technologies with an unavoidable link between the digital world and the physical world, the Internet of Things (IoT) is widely adopted in numerous domains [
1,
2] such as smart health, smart cities, smart homes, smart grids, smart transportation, and smart shopping. The lives of individuals are significantly impacted by IoT services. Disabled persons can benefit from independence and participation in their social lives thanks to people-centric solutions such as IoT assistance. For example, IoT systems help with in-home physical therapy rehabilitation [
3]. IoT technologies also help to reduce dangerous circumstances. For instance, IoT has improved the safety and efficiency of hazardous mining jobs, such as the use of autonomous mining tools that keep employees away from dangerous areas [
4]. When combined with warning systems, IoT sensors for temperature, hazardous gas, and smoke can help avoid environmental catastrophes. Several other case studies have also been analyzed in the literature by different researchers [
5]. In fact, an increasing demand for smart devices dedicated to consumer use as well as industrial use is observed, fostering the projection of the IoT market to be worth trillions of dollars per year in the short term. These devices are characterized by advanced capabilities allowing the data treatment with the enhancement of processes and provided services.
Although there are meaningful benefits of IoT, growing threats and security concerns have appeared and developed with the wide spread of this technology [
6]. The heterogeneity of devices, diversity of network protocols and communication technologies contributed to increasing the whole system’s vulnerability. According to [
7], 70% of Internet-connected gadgets are open to cyberthreats.
Among the most popular methods used to attack the IoT environment in recent years, we have cited Distributed Denial of Service (DDoS) [
8].
DDoS assaults on IoT gadgets are on the rise and are responsible for several IoT device malfunctions and data leaks. IoT is growing quickly, thus it is time to update pertinent network security measures.
Software-Defined Networking (SDN), as a powerful paradigm decoupling control plane from data plane, contributed to addressing security issues, especially in the context of IoT environments [
9]. Thus, SDN provides a more flexible, dependable, and secure network.
Consequently, many experts and researchers are supporting the combination of the conceptual models of IoT with the innovative network paradigm SDN, and they encourage building a software-defined Internet of Things (SD-IoT) [
9,
10,
11] platform as a result of SDN’s success in network administration and security maintenance. However, such solutions are built around centralized architectures that present a single point of failure. To overcome the limits of the centralized aspect of SDN, distributed SDN is considered based on multiple controllers. However, the communication between SDN controllers is still challenging and raises security issues. In this context, adopting blockchain on the control plane of SDN architecture can increase the benefit of this paradigm for the management of IoT environment while guaranteeing the security of exchanged information between multiple controllers and domains.
Indeed, due to its distributed structure, blockchain is viewed as a potential option to secure IoT [
12].
Blockchains [
13,
14] are identified as distributed databases that store the data among nodes on a network and guarantee the fidelity and security of data stored on the chain. They are typically used in cases where the data must be trusted without the need for third-party verification. The defining feature of the blockchain is the immutable aspect of the stored data. The latter is stored on the blocks of the chain that are linked together cryptographically, which make it very hard to change without expending considerable resources.
Thus, blockchain technology has been employed to secure several IoT environments [
15] and to mitigate DDoS attacks in IoT environments due to its anonymity, decentralization, and auditability [
12,
16].
On the other hand, the data plane also presents high vulnerability to DDoS attacks [
17]. It is impossible to distinguish between attack traffic and normal traffic during a DDoS attack since they are so similar. They behave quite similarly to typical network packets but in greater quantities and with a greater focus on the target. A malicious assault originating from a small group of nodes is simpler to be detected and stopped. A typical DDoS attack often involves a large number of nodes, and the collective behavior of these nodes dramatically reduces the likelihood of valid requests being completed.
IoT devices and SDN switches presenting the data plane nodes in such architecture generate traffic to SDN controllers and help them to detect malicious traffic using machine and deep learning techniques [
18]. As a result, they can act appropriately. The learning models are frequently made up of a collection of guidelines, processes, or sophisticated “transfer functions” that can be used to find patterns in IoT data related to security incidents as well as identify and forecast behavior [
19].
Hence, a data-driven model for IoT security intelligence could be developed using machine learning and deep learning techniques. Indeed, several machine learning techniques, such as classification and regression analysis, clustering, rule-based techniques, feature-optimization techniques, and deep learning techniques based on artificial neural networks (ANN), such as the multilayer perceptron network, convolutional network, recurrent network, etc., can be used to explore IoT data to improve its security [
20,
21,
22].
Despite the different solutions and techniques proposed to detect and mitigate DDoS attacks in the IoT context, it still presents a challenging harmful behavior for IoT applications. The adoption of SDN to improve the performance of IoT infrastructure also raised some security issues and could increase the vulnerability of IoT networks. Unlike existing research proposals focusing on applying machine learning techniques or blockchain to detect malicious traffic and/or prevent harmful devices, this paper proposes a holistic security approach that considers SD-IoT infrastructure with multiple controllers to overcome the centralization issue of SDN. Blockchain is used in complementarity with an ANN model to maintain a secure record of the analyzed traffic and the malicious one detected to be shared with the other SD-IoT domains, allowing the prevention against future attacks.
The main contributions of this paper are summarized as follows:
The study of DDoS attack in IoT and in SDN as well as the capabilities of the latter to mitigate DDoS effects on IoT.
The review of some detection and mitigation techniques based on new technologies and methods. Specifically, we highlighted the effect of blockchain on this field.
Proposition of a holistic approach to secure IoT environment against DDoS attacks.
The implementation and performance evaluation of the ANN model used to guide the SDN controllers to detect and identify malicious traffic in IoT networks.
The remainder of this paper is organized as follows.
Section 2 presents a background on DDoS attacks in IoT, and this attack in SDN is deeply studied in
Section 3. Then, the SDN capabilities to mitigate DDoS effects on IoT are shown in
Section 4. In
Section 5 and
Section 6, the blockchain effect on SDN security and DDoS attack detection and mitigation techniques are presented, respectively.
Section 7 is dedicated to the description of the proposed solution. In addition,
Section 8 focuses on results and discussion. Finally, conclusions are drawn in
Section 9.
2. DDoS Attack in IoT
IoT networks are vulnerable to a wide range of security threats, including malware, ransomware, phishing attacks, and distributed denial of service (DDoS) attacks. Malware attacks can exploit vulnerabilities in IoT devices and can be used to gain unauthorized access to the device or to other parts of the network. Ransomware attacks involve the encryption of data on IoT devices and can be particularly damaging in IoT networks. Phishing attacks can be used to gain access to IoT devices or to launch other types of attacks, such as DDoS attacks.
DDoS attacks in IoT networks are different from other IoT attacks in several ways. It can involve a large number of compromised devices, making them capable of generating massive amounts of traffic. This can make it more difficult to be detected and mitigated, which can cause widespread disruption to network services. Unlike other types of IoT attacks that may focus on stealing data or gaining control of devices, DDoS attacks in IoT networks can directly impact the availability of network services and devices, causing significant disruption to business operations or even critical infrastructure. DDoS attacks in IoT networks often involve the use of botnets, which are networks of compromised devices that can be controlled remotely by the attacker. Botnets are difficult to detect and can be used for other types of attacks, as well. IoT devices are often designed with limited security controls, making them vulnerable to exploitation by attackers. Thus, DDoS attacks present a significant threat to the IoT because IoT devices are often connected to the Internet and may not have adequate security measures in place. The goal of a DDoS attack is to disrupt the normal functioning of a network resource, such as an IoT device or server, by continuously flooding the system with traffic from fraudulent requests that overwhelm the system and prevent legitimate traffic from passing through. For example, a home webcam or home automation system could get malicious code from an attacker via IoT technology [
23].
Attackers use trial and error techniques and these devices’ built-in login and password lists to attempt to attack vulnerable devices. Due to outdated firmware, IoT devices are more vulnerable to hacking than desktops and smartphones. They are perfect targets for hackers to remotely influence because they are constantly “online”. After becoming infected, these devices are added to botnets and start to take over the server or service that has been attacked [
24].
The main potential damages of DDoS attacks on IoT devices are summarized in
Table 1.
In the literature, the study of DDoS attacks on the IoT environment is generally based on the IoT attack architectural surface areas [
28]. Security issues are analyzed regarding the overall architecture of an IoT system [
29].
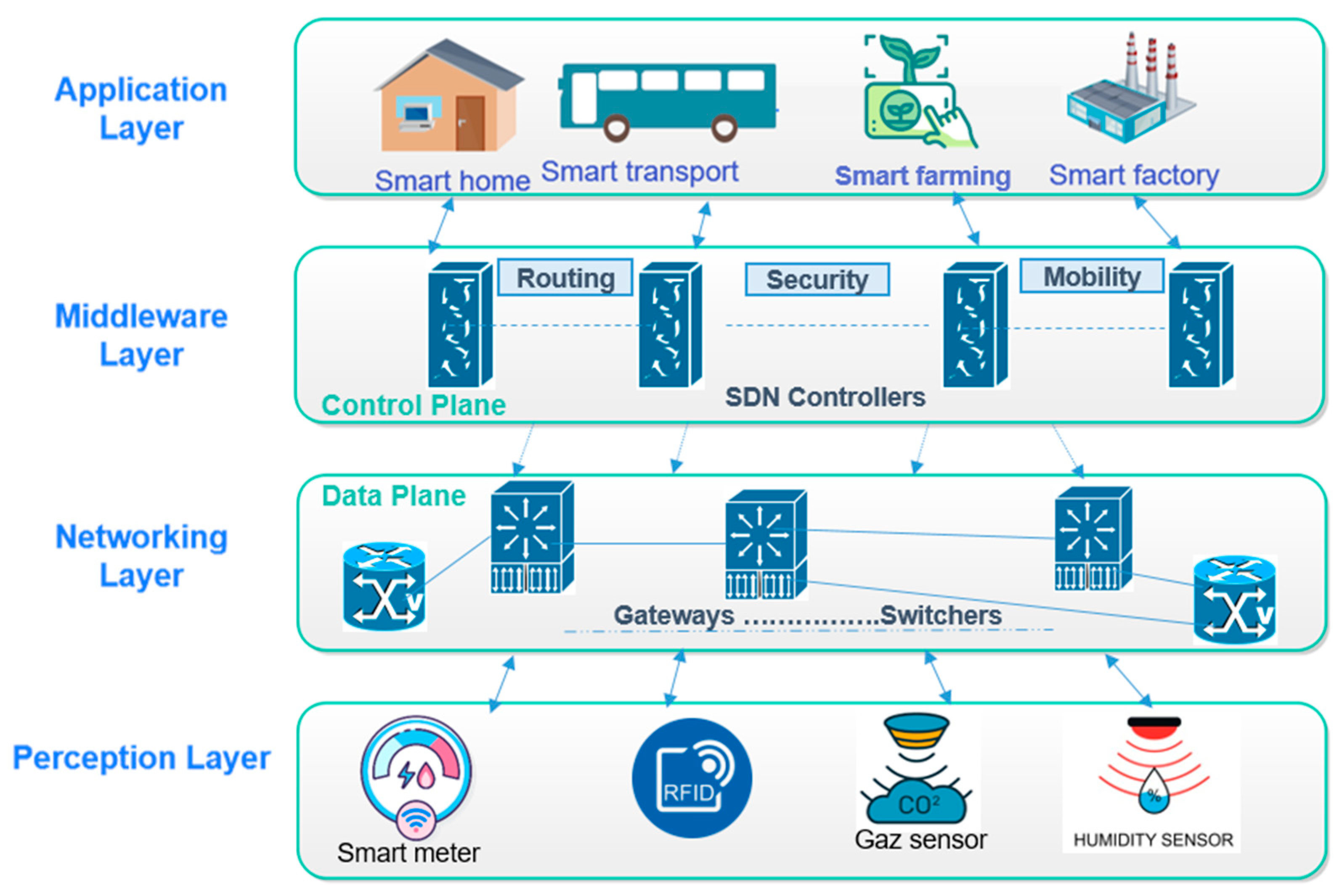
Many experts and research organizations have proposed different IoT architectures. The perception layer, the network layer, and the application layer are regarded to be the three layers of traditional IoT architecture. However, the support or middleware layer—which sits between the network layer and the application layer—is later regarded as a crucial layer in light of the need for data processing and wise decision-making. Hence,
Figure 1 presents the most widely used IoT architecture based on four layers with its adaptation to SDN paradigm: (1) perception layer, (2) networking layer, (3) middleware layer, and (4) application layer.
3. DDoS Attack in SDN
SDN has a number of traits that are connected to its design and structure. It is distinct from traditional network topologies regarding its design features. SDN characteristics are useful for quickly and effectively safeguarding networks with greater flexibility. However, due to various design flaws, SDN itself starts to be exposed to security risks. As a result, there are two ways to characterize SDN design elements. Thus, there are points that make SDN resistant to DDoS assaults while other features might render it vulnerable [
30]. In this section, characteristics of SDN in front of DDoS attacks are highlighted. Then, vulnerability aspects of SDN against DDoS attacks are denoted in addition to security threats target points. Moreover, DDoS attack types and mechanism in SDN are described.
3.1. SDN against DDoS Attacks
DDoS assaults are getting bigger, more frequent, more severe, and more sophisticated on traditional networks. However, SDN has various capabilities that can help mitigate the effects of DDoS assaults to some extent [
30,
31]: (a) network’s overall perspective, (b) control plan and data plan separation, (c) software-based traffic analysis, (d) network Programmability, and (e) updating dynamic network policy. The network is more secure since any dispute may be addressed remotely using a centralized control manager due to the global transparency of the SDN network architecture and the ability to modify traffic-forwarding rules in real time. Additionally, the controller centralizations’, as well as its public nature, raise the possibility of security concerns; DoS and DDoS assaults are two prominent examples. The single point of failure and single point of network failure might both be the SDN controller. With the steady use of SDN technology, it is anticipated that security concerns may worsen [
31].
3.2. SDN Vulnerability against DDoS Attacks
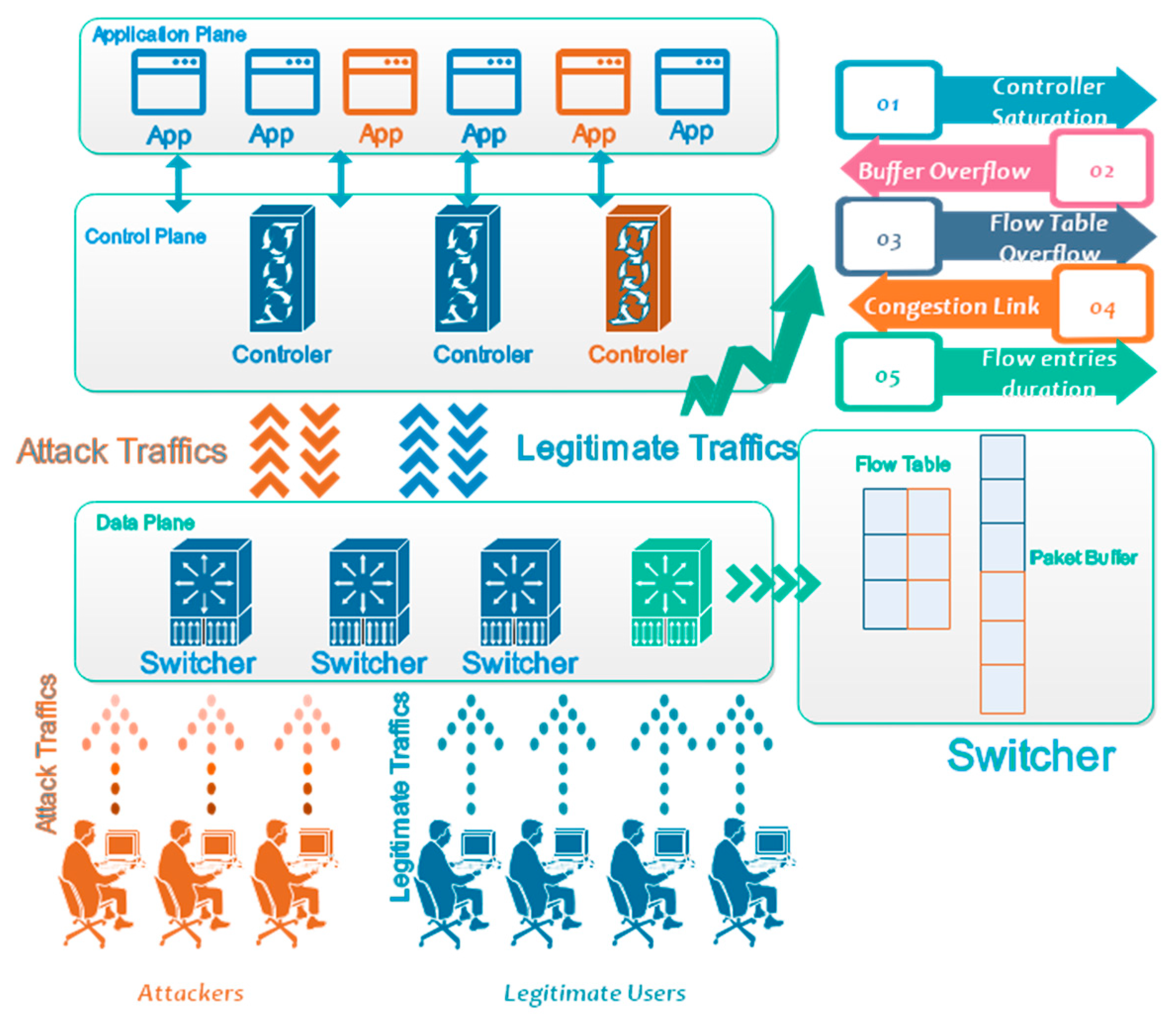
SDN can prevent DDoS assaults by separating the control plane from the data plane. The security concerns with SDN itself, however, have not yet been resolved. SDN inherently may be a victim for DDoS attacks because of its design. SDN is vertically divided into three functional levels. DDoS attacks can target these tiers. These vulnerabilities are: (a) controller saturation, (b) packet buffer overflow/saturation, (c) flow table overflow, (d) control-data plane congestion link/open flow agent overloading, and (e) flow entries duration [
30,
31,
32].
3.3. SDN Security Threats Target Points
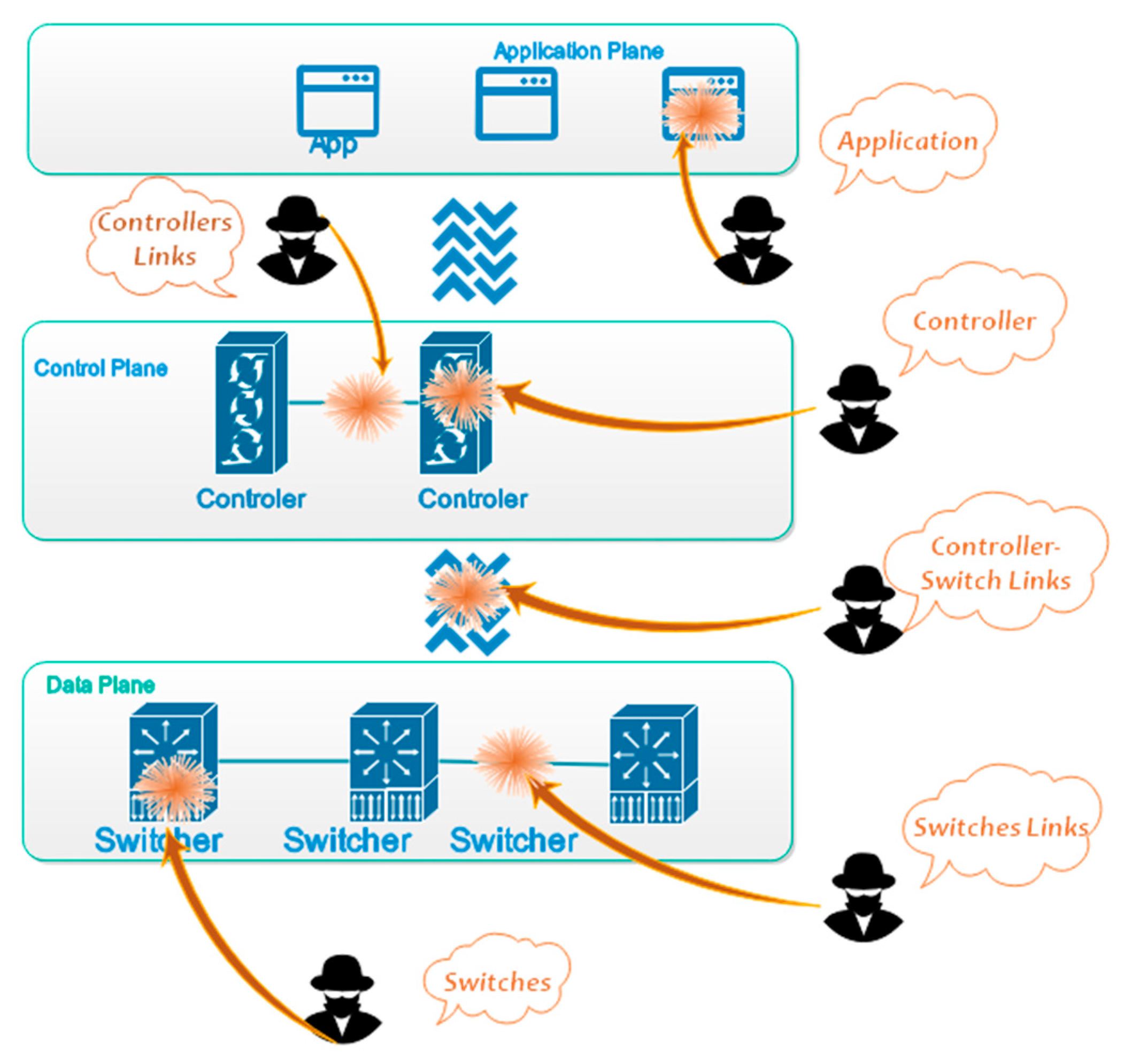
There are three levels in the SDN architecture. Different security dangers can attack any layer. The control plane and controller bandwidth, however, are the most vulnerable DDoS assault targets. The following is a list of potential targets for security concerns in SDN networks as illustrated in
Figure 2: (a) SDN switch, (b) SDN switch links, (c) SDN controller, (d) controller-switch links, (e) controllers links, and (f) applications [
33].
3.4. DDoS Attack Types in SDN
Regarding its main goal of overloading the victim’s network, DDoS attacks could be classified mainly into (i) bandwidth depletion and (ii) network resources depletion. Infecting the data plane, control plane, and interfaces between planes are all targets of various assaults. The SDN’s design is being ruined by these attacks, making it just as difficult to maintain as a network architecture. Following is a list of such attacks based on SDN architecture [
31,
34]: (a) flow table overflow, (b) spoofing of switch, (c) buffer saturation, (d) congestion of southbound API, (e) packet-in flooding, (f) controller saturation, and (g) unauthorized application.
Figure 3 shows the distribution of these attacks among different levels.
3.5. DDoS Attack Mechanism in SDN
After DoS attacks became more prevalent, DDoS attacks started to take shape, with the attacker using a large number of widely separated devices to conduct a distributed attack. DDoS assaults may be broken down into three phases, which are listed below according to [
35,
36]: (1) Phase I: assembling an offensive force, (2) Phase II: propagation, and (3) attack.
The rate of incoming packets to the network rises during a DDoS assault. As a result, faked packets bind the network resources, rendering them unreachable. If this process continues, the server will start dropping packets and eventually become unavailable to newer, legitimately arriving packets.
4. SDN Capabilities to Mitigate DDoS Effects on IoT
The number of DDoS attacks is growing. These assaults, infecting IoT, become more frequent, more severe, and more sophisticated on traditional networks. Although it also threatens SDN networks, this innovative paradigm presents various capabilities that can help mitigate the effects of DDoS assaults to some extent.
4.1. Network’s Overall Perspective
The network’s traffic is seen and controlled by the controller (also known as the Centralized Network Operating System). The information received by querying the end hosts makes it simple to separate the hijacked host from the genuine host when the SDN controller is centrally located.
4.2. Control Plan and Data Plan Separation
Huge experiments are challenging to conduct on conventional networks. Moreover, because control logic is integrated in devices and each device must be updated separately in traditional networks, it is too difficult to evaluate newly installed algorithms. However, SDN dissociates the bottom two planes, making complex systems easier to test. SDN provides excellent dynamic setup flexibility, which creates situations that are conducive to experimentation. Innovative concepts may be quickly implemented and successfully transitioned from the testing stage to the functioning phase.
4.3. Software-Based Traffic Analysis
To monitor and set up the network devices, a variety of application tools are operating on the SDN application plane. There is a wide variety of software and methods for network traffic analysis, which lessens the pressure on switches to parse the information.
4.4. Network Programmability
Applications for programming the controller are placed in a dedicated abstraction level, and these programs further regulate how the network behaves. Thus, it adds flexibility to the IoT network via facilitating the installation of additional intelligence which also makes it more adaptable. Since the network may be programmed, inbound traffic can be analyzed to identify malicious hosts or traffic to keep the network functioning properly.
4.5. Updating Dynamic Network Policy
To mitigate DDoS attacks, the flow rules on OpenFlow switches are dynamically modified. New creative methods to stop the traffic could be rapidly distributed based on the examination of the traffic. In a conventional network, it is challenging to deploy a new regulation to every gadget, but in SDN, updating switches dynamically is simple. The network is more secure since any dispute may be addressed remotely using a centralized control manager due to the global transparency of the SDN network architecture and the ability to modify traffic forwarding rules in real time.
5. Blockchain Effect on SDN Security
The adoption of blockchain to secure SDN is studied in different previous works [
37,
38,
39]. Some research has exploited blockchain in centralized SDN with one controller. Thus, this technology was used on the basis of vertical communication between SDN controllers and data plane nodes. In [
40], blockchain was used to check the integrity of the system by comparing the vSwitch’s traffic flow rules sent to the blockchain. If the rules transmitted by the SDN controller diverge from those in the blockchain, the fraudulent flow rules are identified. Similarly, Boukria et al. [
41] blocked the injection of false flow rule thanks to blockchain. Based on the same technology, authors in [
42] proposed to calculate the SDN nodes’ trust values. Dishonest nodes that provide improper suggestions are filtered out via the blockchain’s consensus mechanism.
On the other hand, in order to secure distributed SDN with multiple controllers, blockchain is also used. BlockTC [
43] was proposed to provide a trustworthy inter-domain collaboration for mobile edge computing based on blockchain. The topology information about domains is collected for all SDN controllers by the blockchain to check the routing accuracy. A two-layer system, a layer of SDN controllers and a layer of blockchain, was proposed by Fernando et al. [
44]. Different SDN controllers exchange control commands that are hashed and registered in the blockchain’s smart contract that will be checked by the targeted controller to confirm the command integrity. In addition, Derhab et al. [
45] proposed BMC-SDN to detect fraudulent flow rule injection. Their proposal considers different master controllers using blockchain to communicate with each other. Then, a reputation mechanism is used by redundant controllers to confirm network flow updates that are recorded in blocks created by the master controller.
Thus, the horizontal communication between multiple controllers allows them to exchange updates about network topology, such as link state, network devices, flow table modifications, lists of network devices, and the relationships among various network domain nodes. Hence, it is critical that controllers maintain a consistent view of the entire network. To do this, the controllers’ east-west interfaces must be used to exchange inter-controller traffic.
6. DDoS Attack Detection and Mitigation Techniques
Cyber, digital, and IoT infrastructures have been seriously threatened by distributed denial-of-service (DDoS) assaults. These attacks have the power to severely disrupt these infrastructures operating while they are restricted to traditional mitigation solutions. Recently, several detection and mitigation techniques were proposed on the basis of new networking paradigms such as SDN, new artificial intelligence methods like machine learning models, as well as blockchain technology.
A collaborative technique to detect and mitigate DDoS flooding attacks on SDN was proposed in [
46]. For this purpose, this solution merges the Snort rules with the sflow-RT application. Several Ryus SDN controllers can exchange DDoS detection and mitigation rules using Redis simple message queue (RSMQ). Singh et al. [
47] considered blockchain technology to defend against DDoS attacks and unauthorized access. The switches in this system are registered and checked with no proof of knowledge. In the blockchain, they are additionally verified using a consensus system based on voting. To recognize aberrant flow traffic, a Boltzmann deep learning engine is also used.
Authors in [
48] introduced a blockchain-based framework for a multilevel DDoS mitigation technique (ML-DDoS) to safeguard IoT devices. The suggested system’s main idea is to employ a device-based verification mechanism powered by blockchain to keep fraudulent devices out of IoT environments. Hyperledger Caliper was used to create the presented framework.
In order to deal with slow-rate DDoS threats, a scalable SDN-based framework that combines an intrusion detection system (IDS) based on deep learning (DL) and an intrusion prevention system (IPS) based on deep reinforcement learning (DRL) was proposed in [
49]. This framework includes scalability aspects like traffic flow sampling and data-plane-based traffic monitoring. Besides, OPTIMIST [
50] presents another solution that is built around a distributed IDS solution designed for IoT networks with optimal placement. A novel offline training strategy was proposed employing WGAN-generated simulated flows in the IDS module, which is based on an LSTM model. On the basis of a factorization machine, a multifeature DDoS intrusion detection system was developed in [
51]. To detect the low rate DDoS attack in this system, flow rule features were first extracted and then used in the factorization machine learning technique. In [
52], an IDS for IoT was proposed based on convolutional neural network (CNN) model and metaheuristic optimization algorithms for feature selection.
Regarding the high importance of DDoS threats, although many researchers addressed this issue, it nevertheless requires genuine attention. The existing work requires a lot of time for attack detection and concentrates mainly on IoT device protection regardless of quality of service (QoS) and/or scalability. The accuracy and precision of some proposed machine learning models could be improved, as well. Thus, in this work, we propose a holistic approach that consider security of the whole IoT network and its scalability, based on the integration of SDN supervision and programmability that considers blockchain to secure distributed multicontroller networks while augmenting the intelligence of these controllers by ANN learning model. A summary of related work is presented in
Table 2.
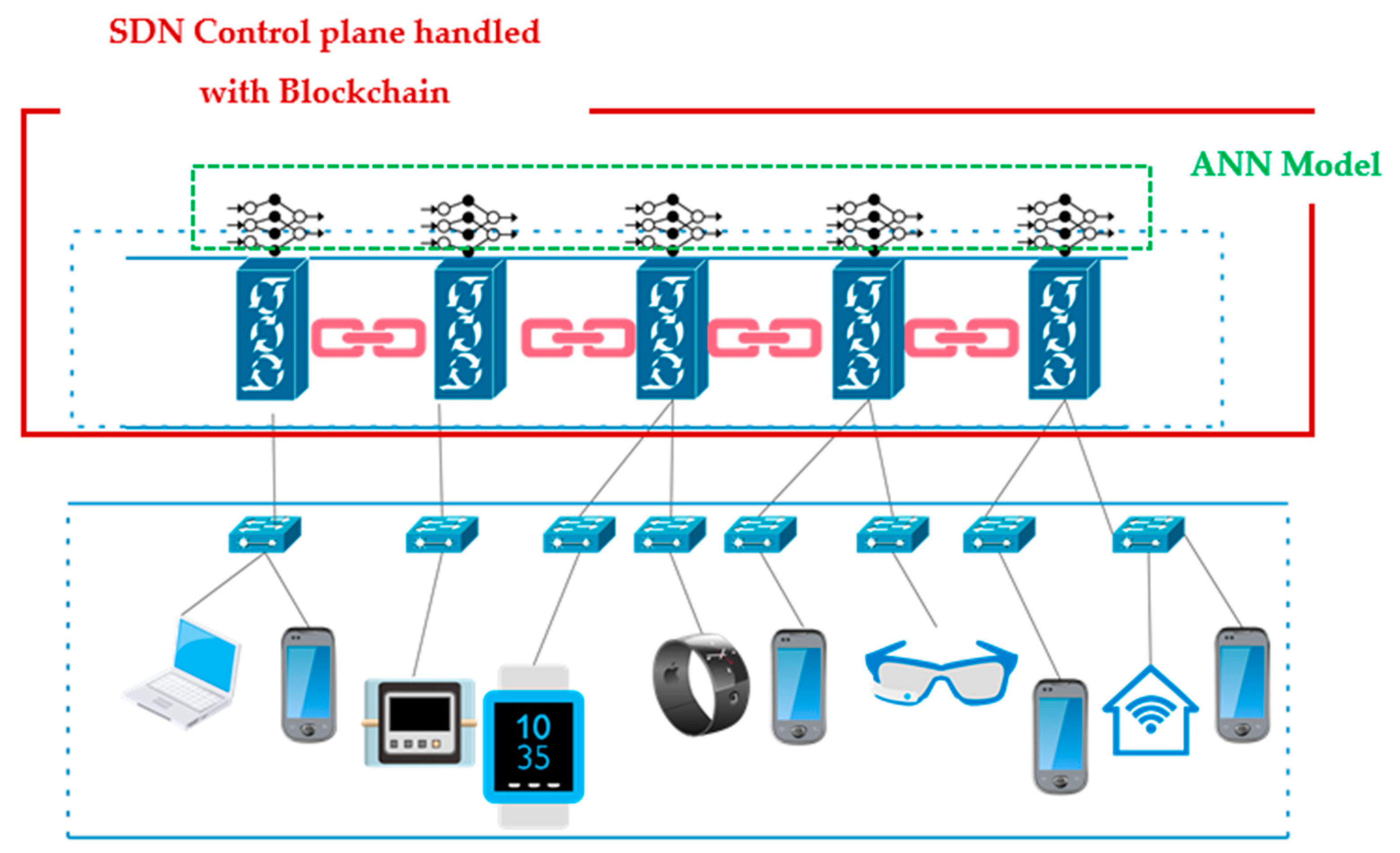
7. Proposed Solution
In this study, a secure system deployed on a distributed SDN network based on multiple controllers handled with blockchain is proposed to protect IoT environment from DDoS attacks. Traffic features are captured, and an artificial neural network (ANN) model is used to detect malicious traffic/nodes and optimize traffic payload. The results of the detection are used to prevent future attacks. A multi-page blockchain is used as a decentralized firewall to block attacks. The blockchain is also used to optimize traffic routing payload. Additionally, the system uses encryption to secure the data exchange. The proposed solution could be divided into three main parts to mitigate DDoS attacks as depicted in
Figure 4:
- (1)
SDN Control plane with security augmented by Blockchain: The SDN control plane is the management layer of the SDN network that oversees and configures the forwarding behavior of the switches. The proposed solution augments the security of the control plane by using blockchain technology, which provides transparency and immutability in communication between different controllers, making it easy to trace the source of any attacks and prevent future attacks from occurring. The blockchain acts as a decentralized firewall to block attacks and optimize traffic routing payload. The distributed nature of the blockchain makes it resistant to any single point of failure, ensuring high availability and resiliency in the network. Having multiple controllers in an SDN-managed IoT network facilitates the ability to scale up or down the network by adding or removing controllers as needed. This makes the management of large IoT networks easier and allows for greater flexibility in network design. Such distributed SDN networks allow fault tolerance: in the event of a failure or malfunction of one controller, other controllers can take over the network management tasks, ensuring that the network remains operational and secure. In addition, the distribution of network management tasks allows load balancing that could reduce the burden on one controller and improve network performance.
- (2)
Artificial Neural Network (ANN) Model: The ANN model is used to distinguish normal traffic and devices from malicious ones. The model uses machine learning algorithms to detect anomalies in network traffic and identify DDoS attacks. It analyzes the patterns of network traffic and learns to distinguish normal traffic from malicious traffic.
The blockchain serves as a distributed ledger that maintains a secure and tamper-proof record of the traffic type (normal or malicious). By using a blockchain at the control plane level, it is possible to ensure that each switch has a consistent and up-to-date version of rules and that any change or update made to the rules are recorded and verified across the network. Once the ANN model identifies an attack, the blockchain is updated with the information on the attack, and the information is shared securely with the other controllers. Hence, any traffic that matches the characteristics of the attack will be denied to reach network resources, and illegitimate traffic of DDoS attacks could be detected and blocked by firewalls of the data plane. Consequently, the ANN model helps in optimizing traffic payload, which reduces network congestion and improves the overall performance of the network.
- (3)
Data Plane with Firewall and Encryption: The data plane is responsible for forwarding the network traffic between different devices in the network. The proposed solution integrates firewalls into the data plane to prevent malicious traffic from entering the network. Firewalls monitor and control the incoming and outgoing network traffic based on the security policies defined by the network administrator. In addition to firewalls, the system uses encryption to secure the data exchange between IoT devices. The use of encryption ensures that the data exchanged between IoT devices is protected from eavesdropping, tampering, and unauthorized access.
In this paper, the implementation of the ANN-based detection system is described, and its results are analyzed in the following subsections.
7.1. ANN-Based Detection System
Once the network traffic is captured, an artificial neural network is processing to detect and identify malicious traffic. ANNs are a type of machine learning algorithm that can recognize patterns and identify anomalies in network traffic. The detection system is implemented on the SDN controllers to identify malicious traffic in real time.
This system is built around five main steps as shown in
Figure 5: (a) data preprocessing, (b) feature selection, (c) splitting the dataset, (d) training the model, and (e) test.
7.1.1. Dataset Description
The “Novel SDN Dataset for Intrusion Detection in IoT Networks” [
53] is used in this work. This dataset is designed to support research in intrusion detection for IoT networks using SDN. It contains network traffic captured from a software-defined network (SDN) in an Internet of Things (IoT) environment during various cyberattacks launched by four attacker hosts against a server and other simulated IoT devices exchanging a large amount of data. The attacks include DoS, DDoS, port scanning, OS fingerprinting, and fuzzing, and were performed with different configurations 10 to 12 times each, depending on the attack type. The testbed used in the experiment was set up using Mininet to simulate an IoT network. It was similar to the Bot-IoT setup and managed by the ONOS controller. The size of the normal traffic is about 2.67 M representing 8.84% of the whole traffic, while DDoS traffic size is around 182 K; the rest of the traffic is related to the other attacks.
This dataset provides a rich set of features that can be used to develop and evaluate intrusion detection systems for IoT networks such as packet counts, byte counts, source and destination IP addresses, port numbers, category, and more. These features are used to develop machine learning models or other analytical techniques that can automatically identify and flag anomalous network activity.
7.1.2. Data Preprocessing
Data preprocessing is a crucial step in any machine learning or data analysis project. It involves cleaning, transforming, and reformatting raw data to make it suitable for analysis. The following are some of the common data preprocessing steps:
Handling Missing Values: Missing data is a common problem in datasets, and it can create bias and affect the accuracy of the model. Therefore, it is important to handle missing values before training the model. The most common techniques for handling missing values include deletion, imputation, and prediction. Deletion techniques include listwise deletion, pairwise deletion, and mean substitution. Imputation techniques include mean imputation, median imputation, and regression imputation. Prediction techniques include k-nearest neighbors (KNN), expectation-maximization (EM), and regression imputation. The choice of technique depends on the nature and distribution of the missing data in the dataset. In the frame of this work, the missed data are removed since they have small proportionally number regarding the hole dataset traffic.
Feature Scaling: Feature scaling is a technique used to normalize the data and bring all the features to a common scale. This is important because the features may have different units, ranges, or distributions, and this can affect the performance of the model. The most common techniques for feature scaling include min-max scaling, standard scaling, and robust scaling. Min-max scaling scales the data to a range between 0 and 1. Standard scaling scales the data to have a mean of 0 and a standard deviation of 1. Robust scaling scales the data based on the median and interquartile range, which is more robust to outliers. This implementation considers the standard scaling.
One-Hot Encoding: One-hot encoding is a technique used to transform categorical data into numerical data. This is important because most machine learning algorithms only work with numerical data. One-hot encoding creates a binary vector for each category, where the vector is all zeros except for the index corresponding to the category, which is set to 1. For example, if a dataset has a categorical feature for color with three categories (red, green, blue), one-hot encoding will create three binary features (red = 001, green = 010, blue = 100) to represent the color feature. The categorical data in the dataset was eliminated while selecting the best feature; therefore, this encoding was not used.
7.1.3. Feature Selection
Feature selection is a technique used to select the most relevant features for the model and reduce the dimensionality of the dataset. This is important because having too many irrelevant or redundant features can lead to overfitting, slower training time, and reduced model performance. Feature selection techniques include filter methods, wrapper methods, and embedded methods. Filter methods use statistical or machine learning measures to rank the features and select the top features. Wrapper methods use a subset of features to train and evaluate the model and select the best subset. Embedded methods use regularization techniques to penalize irrelevant features and select the most relevant features during training. By using a random forest algorithm, a correlation matrix, and hyperparameter selection, the best and most important features are selected. It is worth noting that source, destination IP, and machine addresses were removed because the attackers can spoof them. Also, the category field was removed since this work is processing the IoT architecture by default and it is not needed.
7.1.4. Splitting the Dataset
The step of splitting the dataset involves dividing the available dataset into two separate sets—the training set and the testing set. The training set is used to train the machine learning model, while the testing set is used to evaluate the performance of the model. Typically, the training set is larger than the testing set, with a common split being 70/30 or 80/20. The purpose of this step is to ensure that the machine learning model is not overfitting to the training data and that it is able to generalize well to unseen data. By evaluating the model’s performance on the testing set, we can get an estimate of how well the model will perform on new, unseen data. It is important to ensure that the splitting of the dataset is done randomly, to avoid any bias or skewness in the data. This can be done using various techniques, such as stratified sampling or random shuffling.
7.1.5. Training
AutoKeras is a machine learning library that can be used for automated machine learning (AutoML). It automatically searches for the best neural network architecture and hyperparameters based on the given training data. This helps in building an efficient and accurate ANN model without the need for manual tuning of hyperparameters. The ANN model is trained using the selected architecture and hyperparameters as illustrated in
Table 3.
7.1.6. Validation and Test
After training the model, it is important to check its performance on the validation dataset. This is done to avoid overfitting and to ensure that the model is generalized enough to work well on unseen data. Early stopping is used to prevent overfitting, which means that training is stopped if the model stops improving on the validation dataset. This helps in obtaining the best performing model.
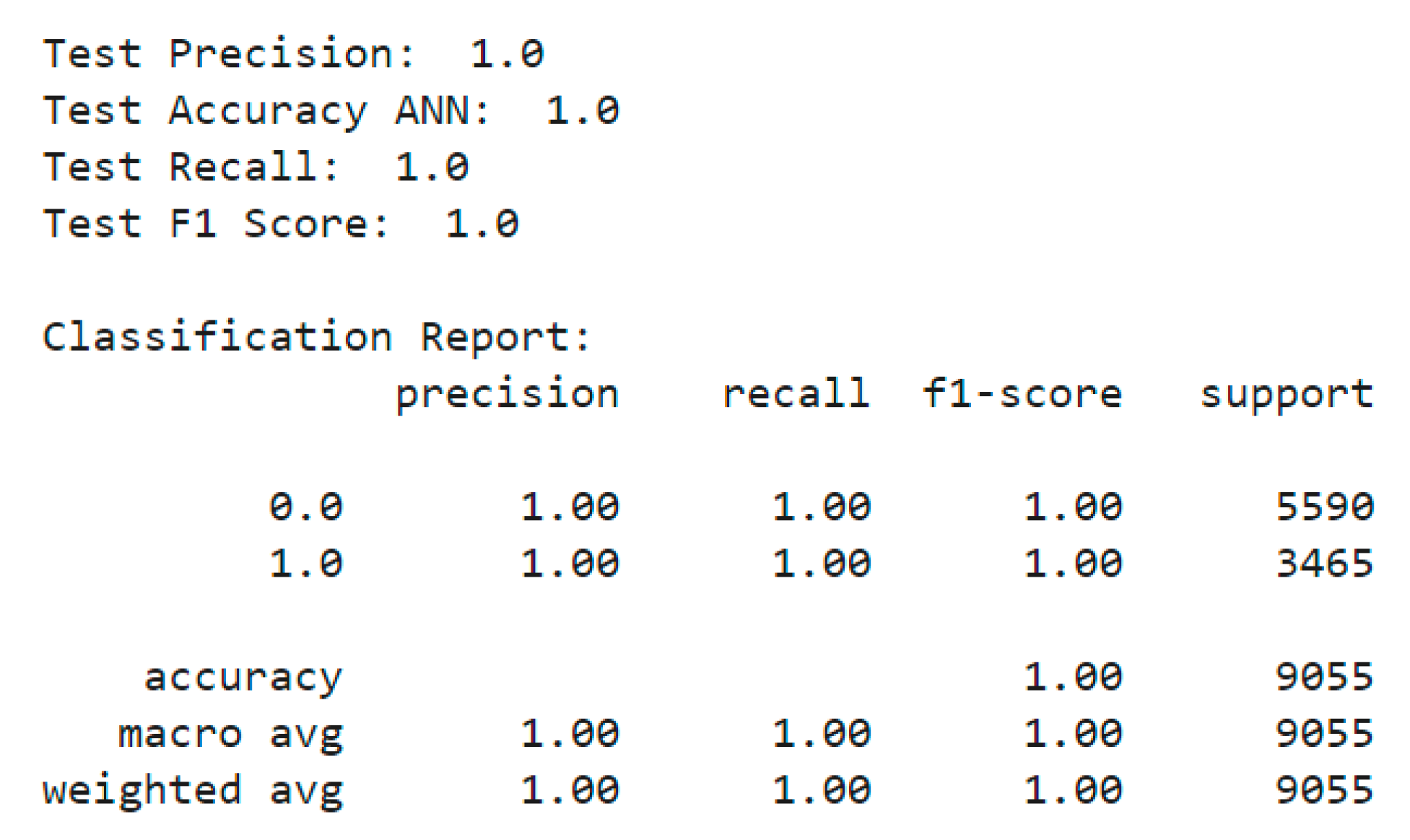
The final step is to test the performance of the ANN model on the testing dataset. The accuracy, precision, recall, F1 score, and other performance metrics are calculated to evaluate the performance of the model. Accuracy measures the percentage of correct predictions, precision measures the number of true positives among all positive predictions, recall measures the number of true positives among all actual positives, and F1 score is the harmonic mean of precision and recall. These metrics help in determining how well the model performs and if it is suitable for the task at hand.
7.2. Implementation Environment
In order to implement the ANN-based detection system, the Keras package on TensorFlow is used. The SkLearn package is also used for preprocessing and performance evaluation metrics for this model. The SDN-IoT dataset [
53] is used to generate IoT traffic in SDN architecture. The performance of the model is evaluated using accuracy and loss performance graphs generated using the Matplotlib package. The objective of this implementation is to determine the best ANN model with high accuracy for detecting DDoS attacks on the SDN-IoT dataset.
To evaluate the detection performance, the cross-validation methods are used. Confusion matrix was used to show the performance of the model by comparing the predicted and actual classes of a set of data. The receiver operating characteristic (ROC) curve shows the trade-off between the true positive rate (TPR) and false positive rate (FPR) of a binary classifier as the decision threshold is varied. Other measures were also used, such as precision, recall, and F1-score.
7.3. Results Analysis
The classification report shows that the model has a precision, recall, and F1-score of 1.0 for both classes, indicating that the model is able to accurately predict both normal and DDoS traffic. The overall accuracy of the model is also very high, at 1.0, indicating that the model can correctly classify all the test data. The precision of a classification model is defined as the number of true positive predictions divided by the total number of positive predictions, and it measures the model’s ability to correctly identify positive cases. In this case, a precision of 1.0 indicates that the model did not make any false positive predictions and correctly identified all positive cases. The recall of a classification model is defined as the number of true positive predictions divided by the total number of positive cases, and it measures the model’s ability to correctly identify positive cases from the total number of actual positive cases. A recall of 1.0 indicates that the model correctly identified all actual positive cases. The F1-score is the harmonic mean of precision and recall, and it provides a single metric for evaluating the overall performance of the model. In this case, the F1-score of 1.0 indicates that the model can correctly identify both normal and DDoS traffic with high precision and recall. The macro-avg and weighted-avg values in the classification report provide overall measures of precision, recall, and F1-score across both classes, considering the number of samples in each class. In this case, both measures have a value of 1.0, indicating that the model performs well across both classes. The classification report is depicted in
Figure 6,while the confusion matrix of ANN detection is illustrated in
Figure 7.
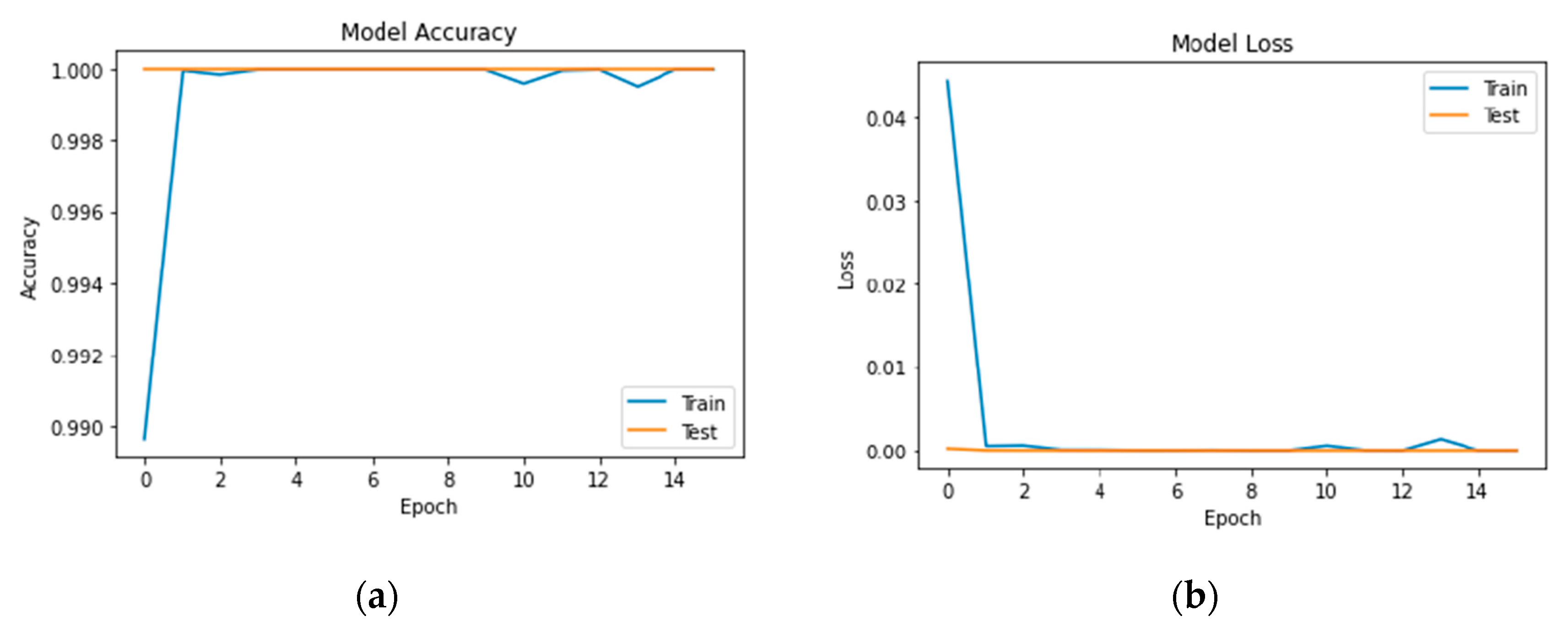
Furthermore,
Figure 8 presents the mdel accuracy and loss. The model accuracy presents the proportion of correct predictions among all predictions. The model loss presents the measure of how well the model fits the training data. The goal is to minimize the loss, which is done using an optimization algorithm during the training process. The obtained results show that both values are optimal.
8. Discussion
The IoT presents a set of security challenges due to its wide application areas and the large number of devices involved. Researchers have proposed a range of solutions to be integrated into the IoT network to enhance its management and to mitigate potential threats. Those studied in this paper are mainly: SDN, machine learning, and blockchain. While these approaches show promise, it is important to also consider their potential drawbacks to ensure that they can be integrated effectively and provide robust security for IoT networks. Among these drawbacks, we cite the device compatibility. Regarding the design of some IoT devices conceived for conventional networks, it causes an inconvenience while integrating SDN paradigm. To overcome such issues, the adoption of specific protocols allowing such adaptation between SDN and IoT devices presents a solution. While SDN management can provide greater security and control over the network, it can also introduce new security risks. For example, if the SDN controllers or switches are compromised, the entire network may be at risk. Additionally, the use of centralized controllers can create a single point of failure, making the network more vulnerable to attacks. It is important to implement strong security measures and protocols to mitigate these risks. Another potential limitation of using SDN management for IoT networks is its scalability. While SDN management can provide greater control and flexibility over the network, it may not be as easily scalable as other network management approaches. This can limit the ability of the network to grow and evolve over time and may require additional resources or restructuring to accommodate future expansion. In summary, while SDN management can provide many benefits for IoT networks in terms of security, control, and flexibility, there are also potential drawbacks and limitations to consider. It is important to carefully evaluate the specific needs and requirements of the network, and to implement strong security measures and protocols to mitigate potential risks.
Consequently, while the proposed solution for securing IoT systems using SDN with a multicontroller and blockchain technology is promising, there are practical challenges that must be considered when implementing such a system.
Among these challenges, we cite the potential cost and resource requirements of deploying multiple controllers for network management. The deployment of multiple controllers can require significant resources, including hardware, software, and network infrastructure. Additionally, it may be necessary to employ skilled personnel to manage and supervise the controller’s operation. It is important to carefully evaluate the cost–benefit trade-offs of using multiple controllers in the context of the specific IoT deployment. Thus, the number of controllers to be deployed should be effective and efficient to optimize the required resources and costs.
Another challenge that must be considered is the impact of blockchain technology on network performance and scalability. The use of blockchain technology introduces additional overhead and latency to the network, which can impact the performance of the system and the user experience. This can be particularly challenging in IoT environments, where real-time data processing and low latency are often critical requirements. In addition, the use of blockchain technology can impact the scalability of the system. Specifically, while the number of transactions and nodes is increased in public blockchain, a scalability issue is raised. For this purpose, the proposed system considers a private blockchain to manage the secure communications between the multiple controllers. The number of transactions is also moderated since the ANN model is handling the data to be exchanged in a secure way via blockchain.
To address these challenges, it is important to carefully evaluate the specific requirements and constraints of the IoT system and to consider the compromise between security, cost, and performance. This could involve conducting a thorough risk assessment to identify potential security threats and vulnerabilities, and adopting new system architecture that balances security requirements with the available resources and performance constraints. It could also involve leveraging techniques and methods related to the adaptation of blockchain and SDN controllers to optimize the system’s performance and to ensure that it meets the specific requirements of the IoT deployment. The mathematical optimization techniques, such as heuristic methods, could be used in the frame of recommender systems [
54] to improve the proposed solution.
9. Conclusions
With the increasing adoption of IoT devices in our daily activities and in widespread services, it becomes increasingly critical to secure and manage the vast amounts of data they generate. SDN has emerged as a promising solution to manage the network traffic generated by IoT devices, while blockchain technology offers a secure and decentralized platform for data sharing and trust management. Consequently, security is crucial for ensuring the integrity of data generated by IoT devices, while DDoS attacks pose a significant threat to the availability of IoT services. In this context, this paper studied DDoS threat in IoT and SDN, as well as the vulnerability of these environments against DDoS attack. Furthermore, different DDoS attack mitigations techniques based on cutting-edge technologies such as, blockchain, and machine learning were reviewed. In fact, this paper aims to investigate innovative techniques and methods that could help IoT services and applications to be delivered in a secure way. For this purpose, the benefit of the integration of SDN paradigms as well as blockchain technology and machine learning models in such environments were deeply analyzed. A holistic secure IoT system that considers multicontroller SDNs with augmented security by blockchain and ANN models was introduced to contribute in detecting and mitigating DDoS attacks. The data plane also could be protected via firewalls and encryption systems. Afterward, the implementation of the ANN-based detection system was detailed, and it proved its high performance. In the future, we plan to develop the implemented solution to deploy the whole system in mini-net emulators with multiple ONOS controllers that perform east-west communications using hyperledger fabric.