Security Establishment in ADS-B by Format-Preserving Encryption and Blockchain Schemes
Abstract
1. Introduction
- Holistic framework: The solution used a cryptographic module based on a keyed-Hash Message Authentication Code (HMAC) to protect data integrity and authenticity [11];
- Most of the recommended solutions are still in the experimental stage, being tested in controlled settings, and have yet to be implemented [4];
- Deploying FPE algorithms offers certified encryption for the protection of ADS-B messages without any changes in the message’s length;
- While the use of FPE algorithms has been proposed as a security solution to benefit from its advantages [12], it has not yet been implemented and has not been challenged in operational environments such as implementation in SDR and experimentation in flight tests; and
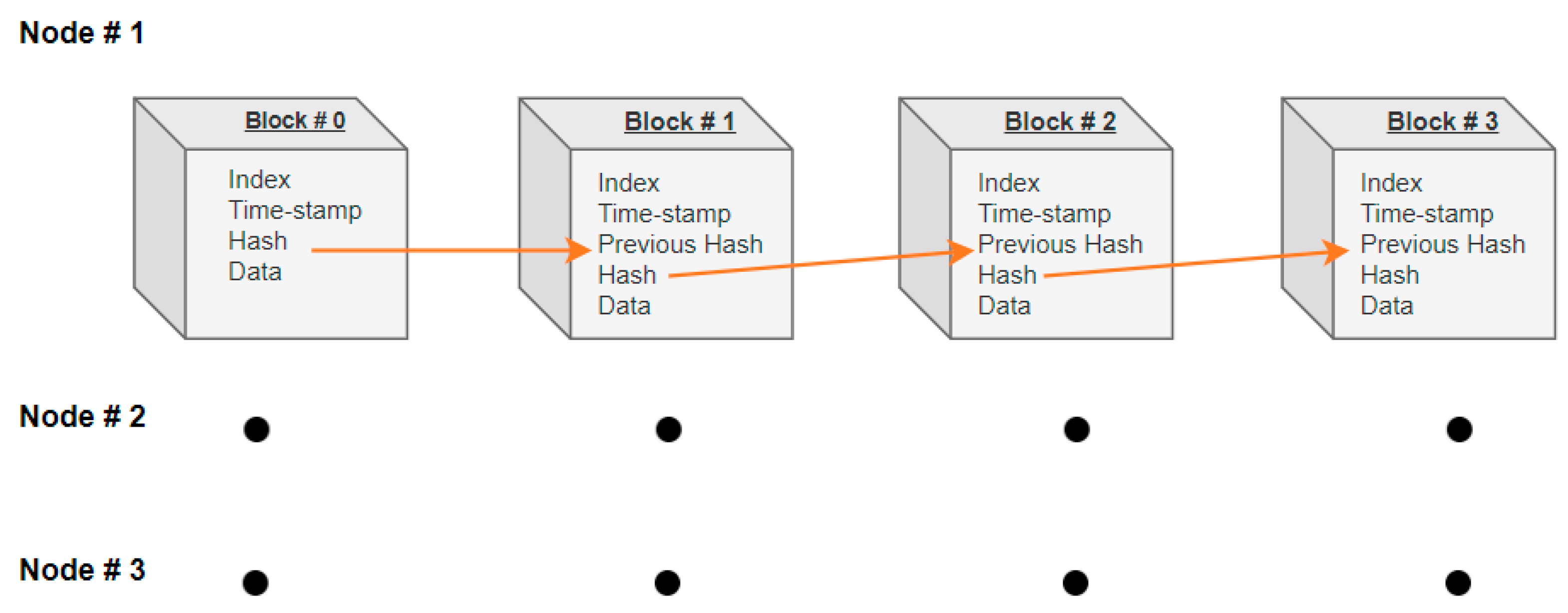
- A permissioned blockchain system helps the operational environment not only to exchange the encryption key among nodes (ADS-B systems), but also to store important information.
2. Literature Review
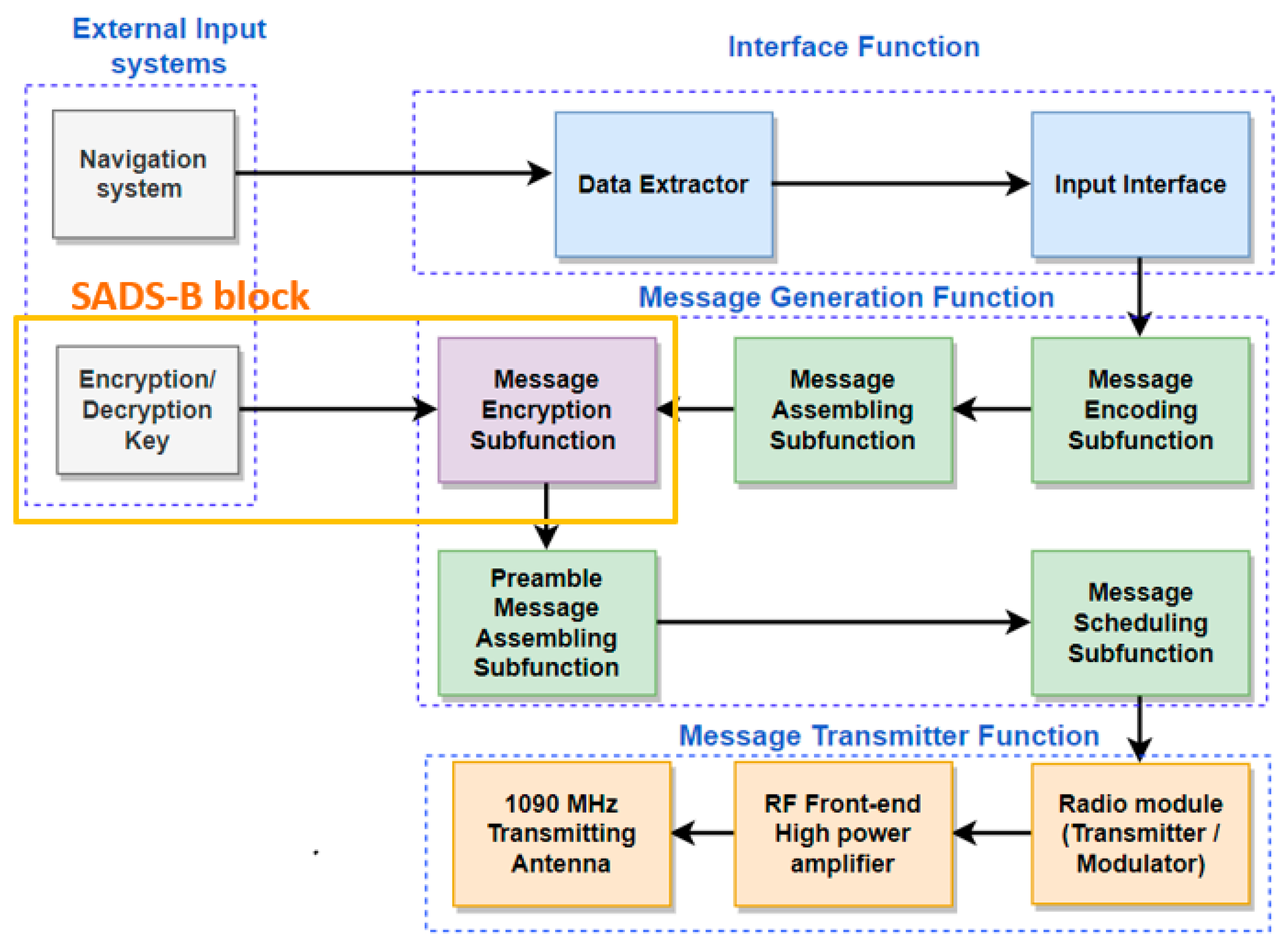
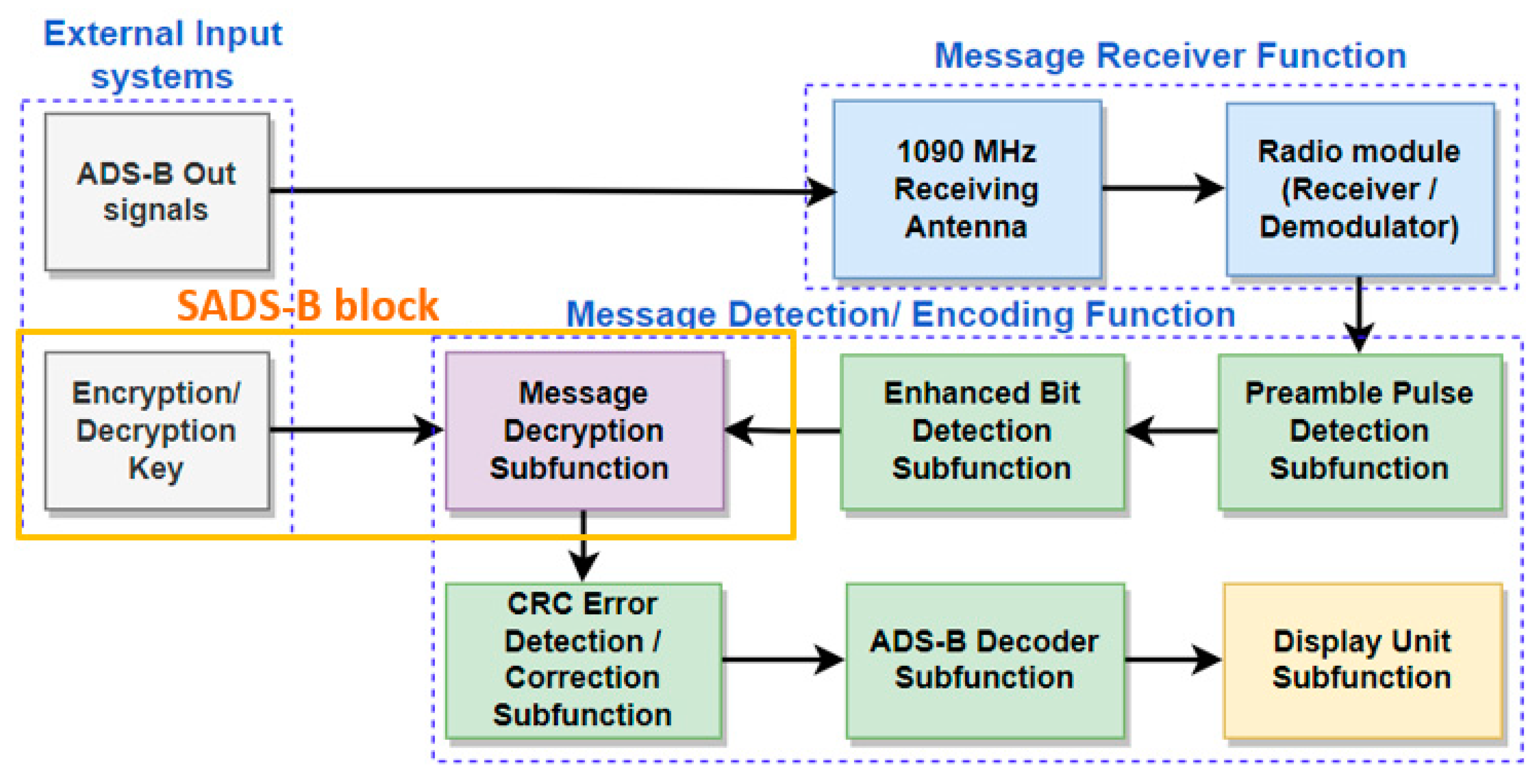
3. Methodology and Solutions
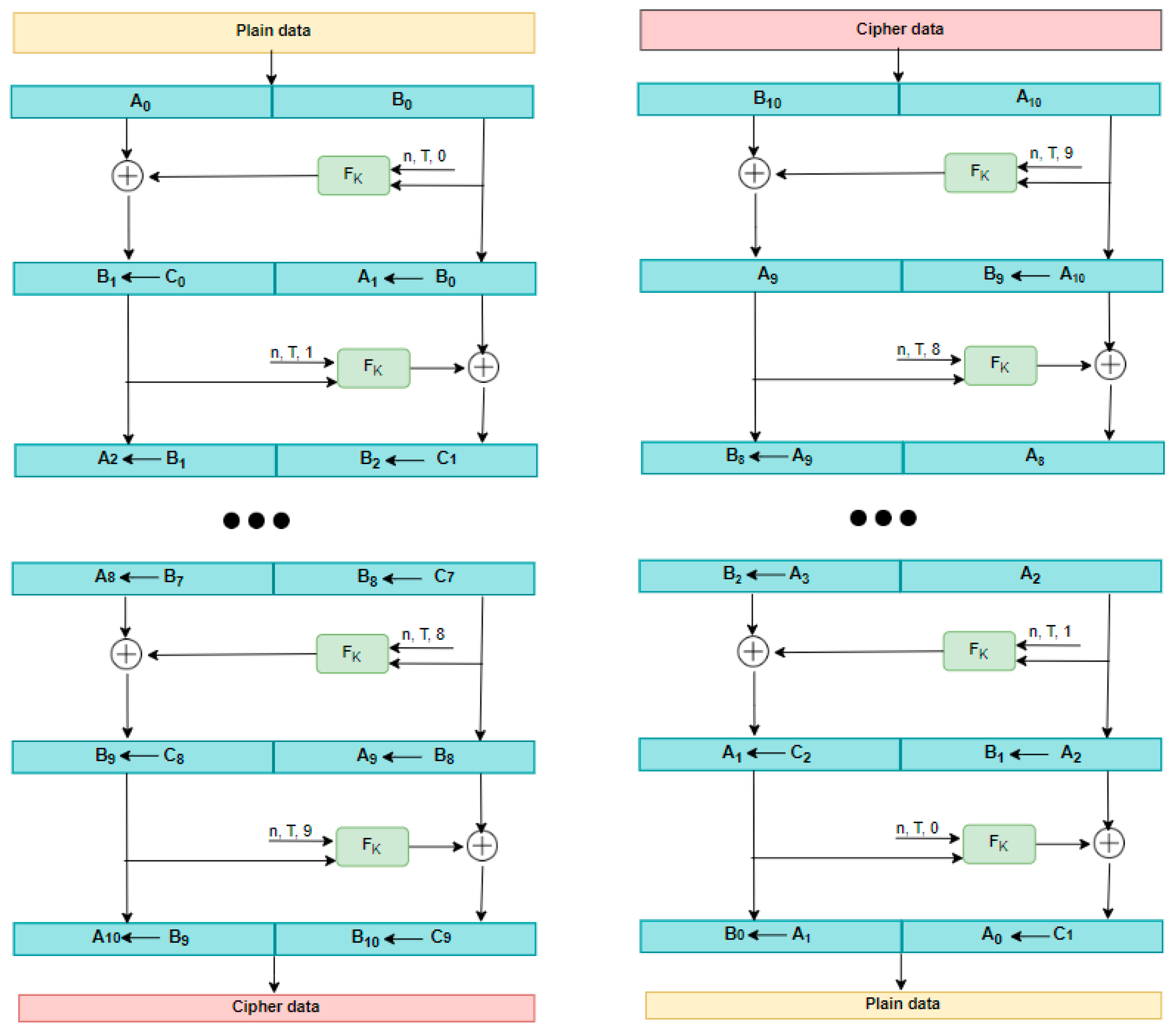
3.1. FFX Algorithm
- I.
- The order of the round indices is changed;
- II.
- The roles of the two components of the data in the round function are switched, so that, in addition to n, T, and i, Ai + 1 (instead of Bi) is used as the input to FK, and Bi + 1 (instead of Ai) is combined with the output to produce Ai (instead of Bi + 1)
- III.
- Modular addition is changed to modular subtraction (the output of FK from Bi +1).
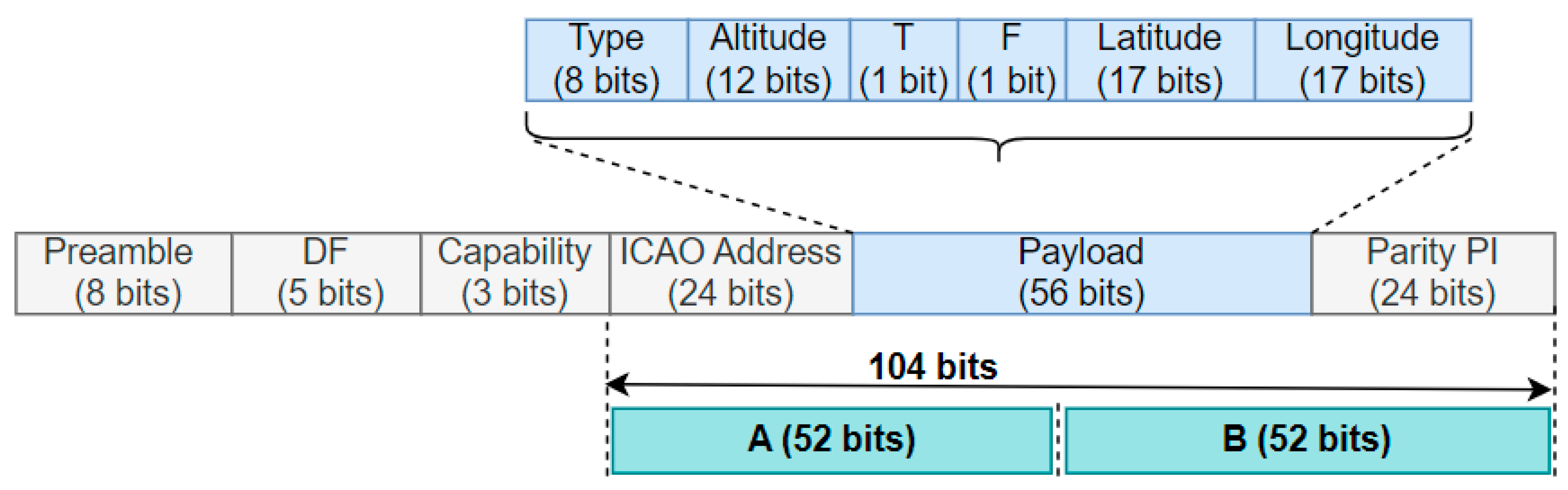
3.2. FFX Scheme Implementation
- I.
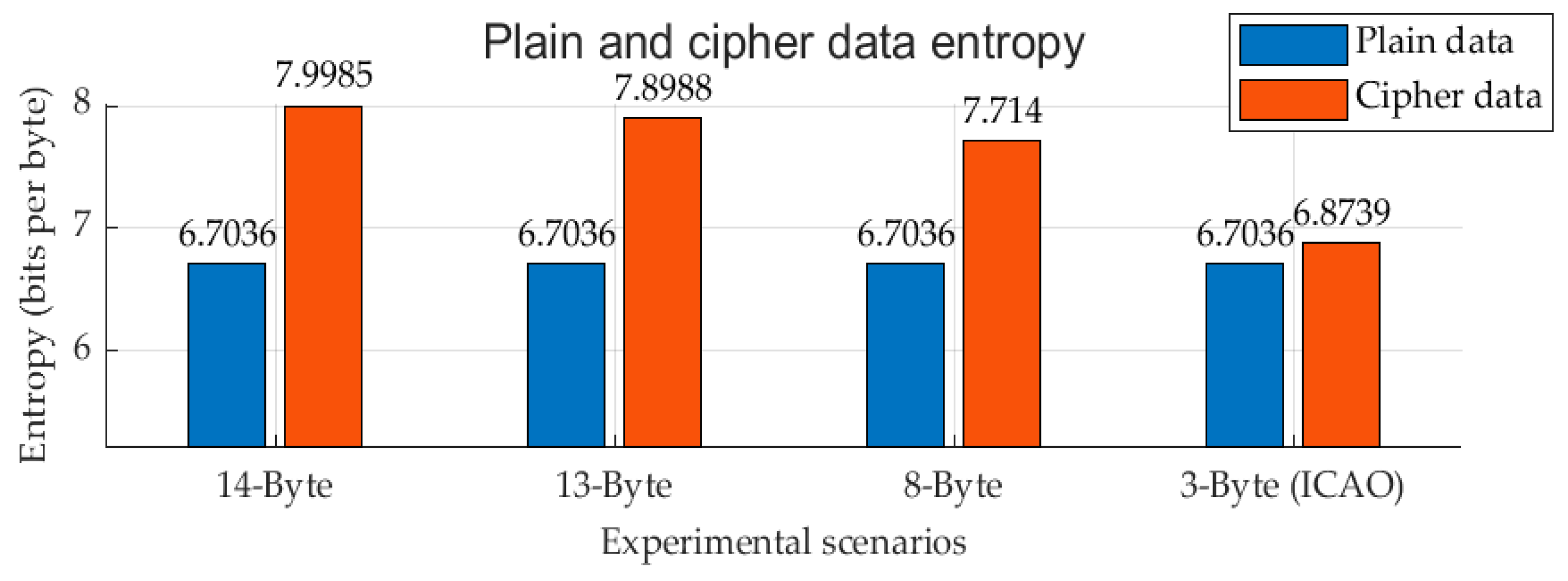
- 14-Byte (whole message encryption)
- II.
- 13-Byte (excluding DF and CA fields)
- III.
- 8-Byte (ICAO and PI fields)
- IV.
- 3-Byte (ICAO field)
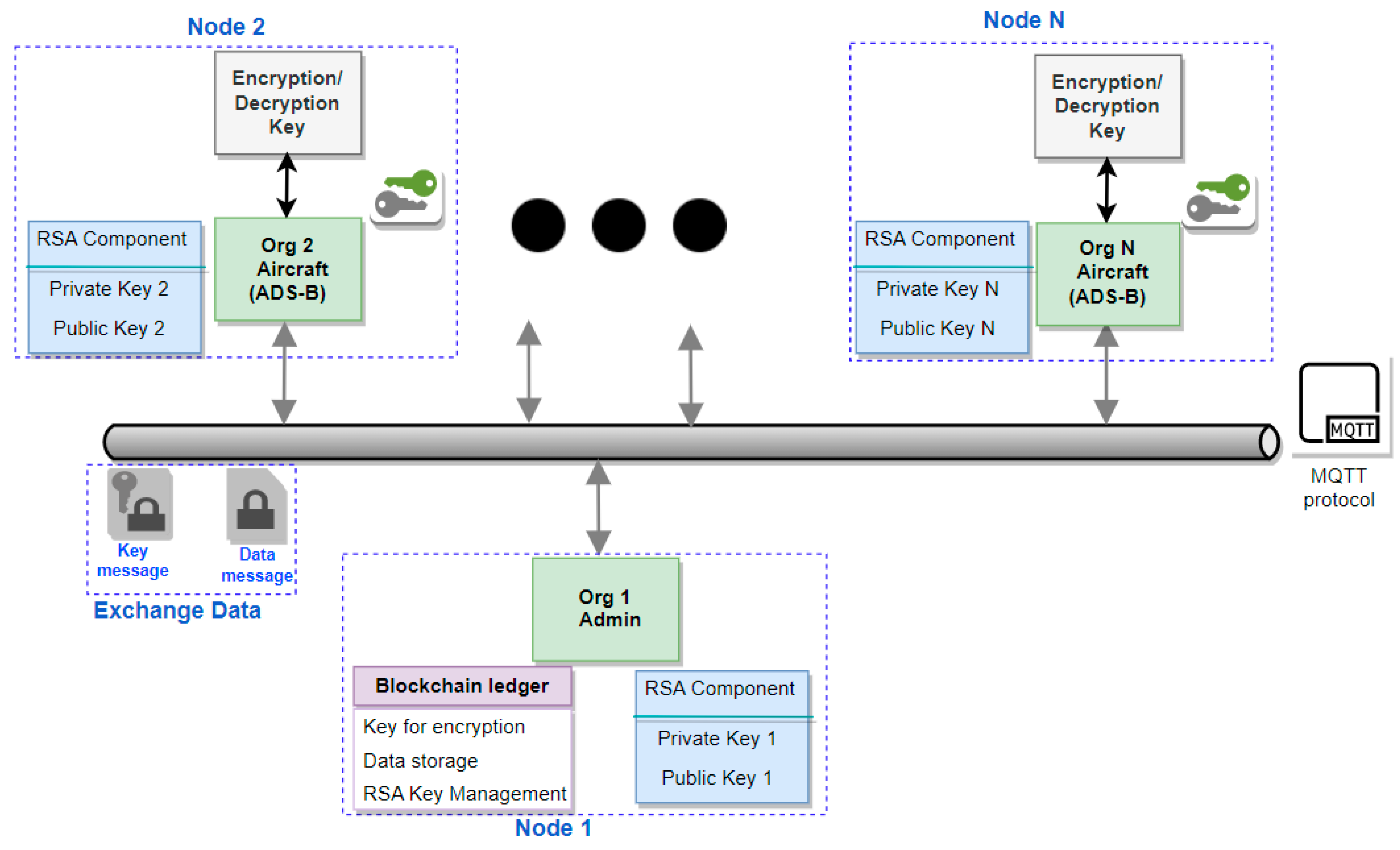
3.3. Blockchain-Based Key Exchange Solution
- Access—trusted members need permission to join;
- Confidentiality—read/write access limitation among members;
- Efficiency—higher efficiency in transactions; and
- Trust—the degree of trust.
4. Experimental Results
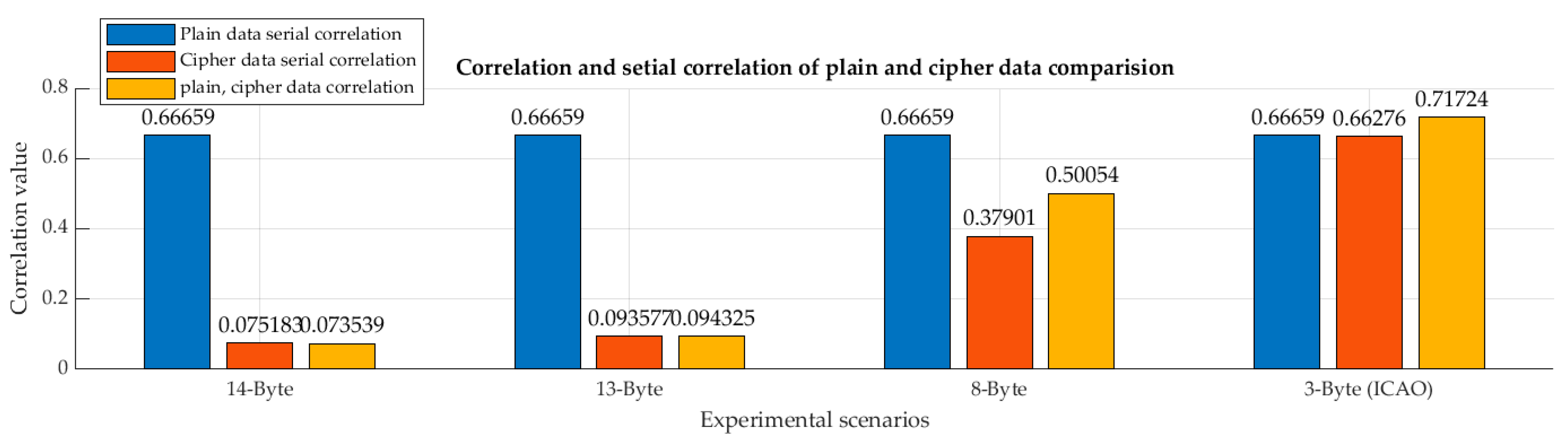
- Entropy and security complexity: In cryptography, entropy is frequently used to measure a bit string’s level of uncertainty. In addition, serial correlation and plain and encrypted data correlation are key indicators for security measurement.
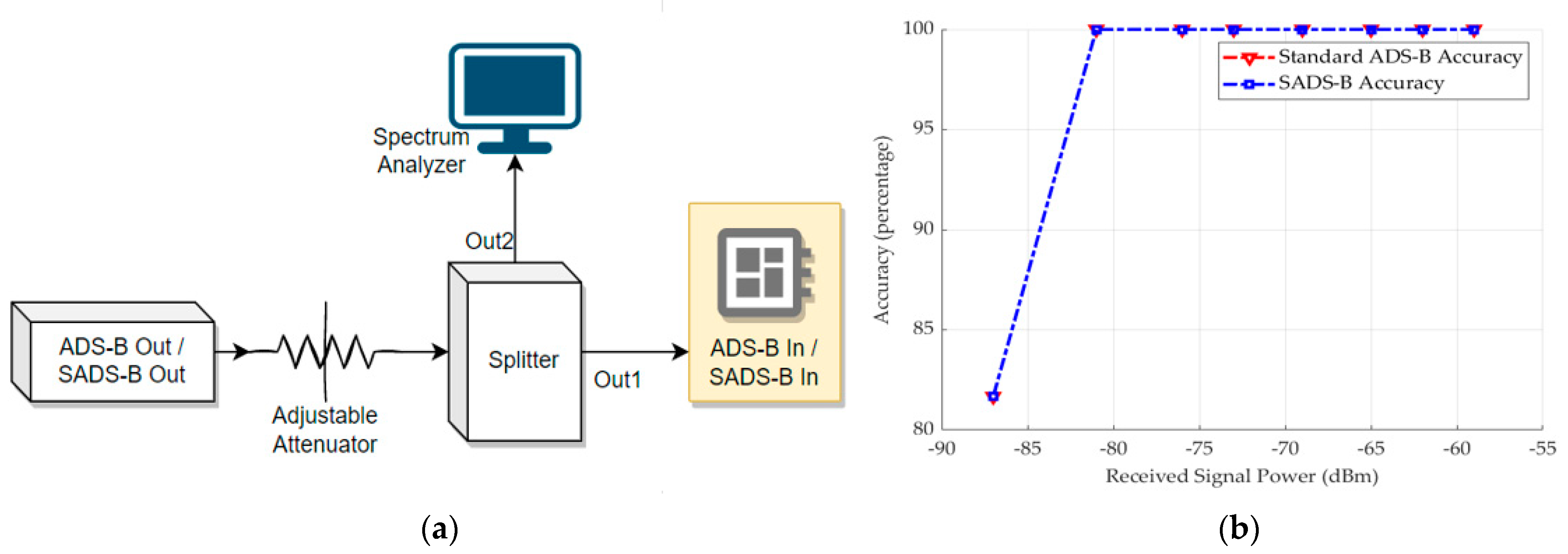
- Sensitivity: The minimum trigger level (MTL) of an ADS-B receiver processing signals within the frequency span of 1089 to 1091 MHz must respect the MTL constraint, which is −84 dBm for ADS-B class “A3” [26].
- Computational time: Encryption increases the time required for message transmission and reception at both ends. Therefore, it is essential to verify the impact of such increased processing time on both ADS-B Out/In.
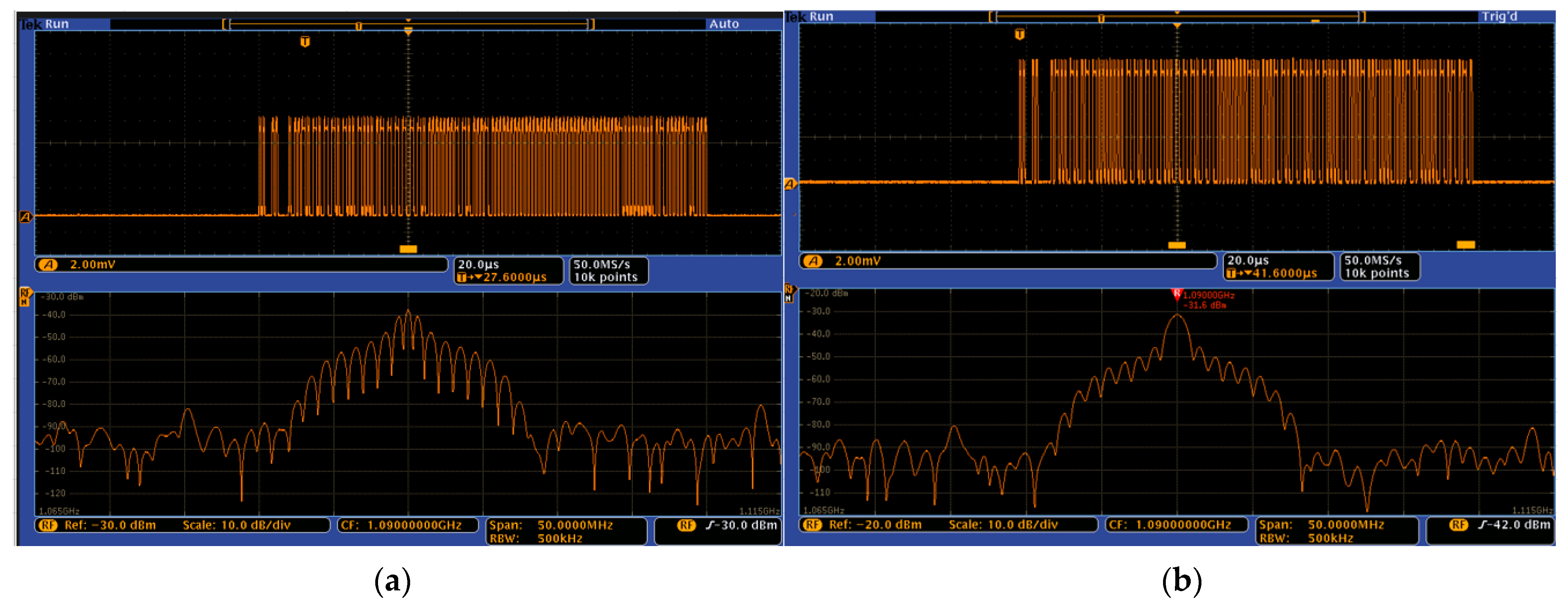
- Waveform comparison: Undoubtedly, applying the FFX algorithm alters the bit sequence in time, so it is wise to observe the spectrum accordingly.
5. Discussion
6. Conclusions
- Investigating the FFX algorithms’ impact on ADS-B messages and how its utilization brings about security advantages to ADS-B sensitive data.
- Designing and implementing FFX algorithms in an SDR system (BladeRF) which is compatible with the standard ADS-B for both the transmitter and receiver.
- Offering a new solution for the key exchange for encryption via the blockchain scheme
- Experimenting with lab and flight tests without any degradation in standard ADS-B performance and key requirements.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Acknowledgments
Conflicts of Interest
References
- The Roadmap for Delivering High Performing Aviation for Europe. European ATM Master Plan Executive: View Edition. SESAR Joint Undertaking (EU Body or Agency) February 2016. Available online: https://www.sesarju.eu/sites/default/files/documents/ATM_MasterPlan_web.pdf (accessed on 24 February 2023).
- Costin, A.; Francillon, A. Ghost in the Air(Traffic): On insecurity of ADS-B protocol and practical attacks on ADS-B devices. Black Hat USA 2012, 1, 1–12. [Google Scholar]
- Schäfer, M.; Lenders, V.; Martinovic, I. Experimental Analysis of Attacks on Next Generation Air Traffic Communication. In Applied Cryptography and Network Security; Jacobson, M., Locasto, M., Mohassel, P., Safavi-Naini, R., Eds.; Springer: Berlin/Heidelberg, Germany, 2013; Volume 7954, pp. 253–271. [Google Scholar] [CrossRef]
- Wu, Z.; Shang, T.; Guo, A. Security Issues in Automatic Dependent Surveillance—Broadcast (ADS-B): A Survey. IEEE Access 2020, 8, 122147–122167. [Google Scholar] [CrossRef]
- Lu, X.; Wu, Z. ATMChain: Blockchain-Based Security Framework for Cyber-Physics System in Air Traffic Management. Secur. Commun. Netw. 2022, 2022, 8542876. [Google Scholar] [CrossRef]
- Arora, A.; Yadav, S.K. BATMAN: Blockchain-Based Aircraft Transmission Mobile Ad Hoc Network. In Proceedings of 2nd International Conference on Communication, Computing and Networking; Krishna, C.R., Dutta, M., Kumar, R., Eds.; Springer: Singapore, 2019; Volume 46, pp. 233–240. [Google Scholar] [CrossRef]
- Reisman, R. Blockchain Serverless Public/Private Key Infrastructure for ADS-B Security, Authentication, and Privacy. In Proceedings of the AIAA Scitech 2019 Forum, San Diego, CA, USA, 7 January 2019. [Google Scholar] [CrossRef]
- Hasin, F.; Taher, K.A. Cyber Threat Mitigation of Impending ADS-B Based Air Traffic Management System Using Blockchain Technology. In Proceedings of International Conference on Trends in Computational and Cognitive Engineering; Kaiser, M.S., Bandyopadhyay, A., Mahmud, M., Ray, K., Eds.; Springer: Singapore, 2021; Volume 1309, pp. 545–556. [Google Scholar] [CrossRef]
- Slimane, H.O.; Benouadah, S.; Shamaileh, K.A.; Devabhaktuni, V.; Kaabouch, N. ADS-B Message Injection Attack on UAVs: Assessment of SVM-based Detection Techniques. In Proceedings of the 2022 IEEE International Conference on Electro Information Technology (eIT), Mankato, MN, USA, 19–21 May 2022; pp. 405–410. [Google Scholar] [CrossRef]
- Karam, R.; Salomon, M.; Couturier, R. Supervised ADS-B Anomaly Detection Using a False Data Generator. In Proceedings of the 2022 2nd International Conference on Computer, Control and Robotics (ICCCR), Shanghai, China, 18–20 March 2022; pp. 218–223. [Google Scholar] [CrossRef]
- Kacem, T.; Wijesekera, D.; Costa, P. ADS-Bsec A Holistic Framework to Secure ADS-B. IEEE Trans. Intell. Veh. 2018, 3, 511–521. [Google Scholar] [CrossRef]
- Finke, C.; Butts, J.; Mills, R.; Grimaila, M. Enhancing the security of aircraft surveillance in the next generation air traffic control system. Int. J. Crit. Infrastruct. Prot. 2013, 6, 3–11. [Google Scholar] [CrossRef]
- Zhou, J.-X.; Yan, J.-H. Secure and Efficient Identity-based Batch Verification Signature Scheme for ADS-B System. KSII Trans. Internet Inf. Syst. 2019, 13, 6243–6259. [Google Scholar] [CrossRef]
- Wesson, K.D. Can Cryptography Secure Next Generation Air Traffic Surveillance? IEEE Secur. Priv. Mag. 2014, 8. Available online: https://www.google.com.tw/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&ved=2ahUKEwjy7pT3iLf9AhXxilYBHY8nBwEQFnoECA8QAQ&url=https%3A%2F%2Fradionavlab.ae.utexas.edu%2Fimages%2Fstories%2Ffiles%2Fpapers%2Fadsb_for_submission.pdf&usg=AOvVaw1cfibP1JxBPYKXBCbk1fiB (accessed on 24 January 2023).
- Strohmeier, M.; Lenders, V.; Martinovic, I. On the Security of the Automatic Dependent Surveillance-Broadcast Protocol. IEEE Commun. Surv. Tutor. 2015, 17, 1066–1087. [Google Scholar] [CrossRef]
- Ziliang, F.; Weijun, P.; Yang, W. A Data Authentication Solution of ADS-B System based on X.509 Certificate. In Proceedings of the 27th International Congress of the Aeronautical Sciences, ICAS, Nice, France, 19–24 September 2010; p. 6. [Google Scholar]
- Baek, J.; Hableel, E.; Byon, Y.-J.; Wong, D.S.; Jang, K.; Yeo, H. How to Protect ADS-B: Confidentiality Framework and Efficient Realization Based on Staged Identity-Based Encryption. IEEE Trans. Intell. Transp. Syst. 2017, 18, 690–700. [Google Scholar] [CrossRef]
- Samuelson, K.; Valovage, E.; Hall, D. Enhanced ADS-B Research. In Proceedings of the 2006 IEEE/AIAA 25th Digital Avionics Systems Conference, Portland, OR, USA, 15–19 October 2006. [Google Scholar]
- Jochum, J. Encrypted Mode Select ADS-B for Tactical Military Situational Awareness. Master’s Thesis, Massachusetts Institute Of Technology, Boston, MA, USA, 2001. [Google Scholar]
- Nguyen, A.-Q.; Amrhar, A.; Zambrano, J.; Brown, G.; Landry, R.J.; Yeste, O. Application of PSK Modulation for Secure ADS-B Avionics. In Proceedings of the 2018 Aviation Technology, Integration, and Operations Conference, Atlanta, GA, USA, 25–29 June 2018. [Google Scholar] [CrossRef]
- Olive, X.; Strohmeier, M.; Lübbe, J. Crowdsourced Air Traffic Data from the OpenSky Network 2020. Zenodo, 15 November 2022. Available online: https://zenodo.org/record/3737101 (accessed on 24 February 2023).
- Rudys, S.; Aleksandravicius, J.; Aleksiejunas, R.; Konovaltsev, A.; Zhu, C.; Greda, L. Physical layer protection for ADS-B against spoofing and jamming. Int. J. Crit. Infrastruct. Prot. 2022, 38, 100555. [Google Scholar] [CrossRef]
- Bellare, M.; Rogaway, P.; Spies, T. The FFX Mode of Operation for Format-Preserving Encryption. Natl. Inst. Stand. Technol. Submiss. 2010, 20, 1–18. [Google Scholar]
- Yang, H.; Yao, M.; Xu, Z.; Liu, B. LHCSAS: A Lightweight and Highly-Compatible Solution for ADS-B Security. In Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–7. [Google Scholar] [CrossRef]
- Agbeyibor, R.C. Secure ADS-B: Towards Airborne Communications Security in the Federal Aviation Administration’s Next Generation Air Transportation System. Ph.D. Thesis, Air Force Institute Of Technology, Wright-Patterson AFB, OH, USA, 2014. Available online: https://apps.dtic.mil/sti/pdfs/ADA600893.pdf (accessed on 24 February 2023).
- RTCA (DO-260B); Minimum Operational Performance Standards for 1090 MHz Extended Squitter Automatic Dependent Surveillance—Broadcast (ADS-B) and Traffic Information Services—Broadcast (TIS-B). RTCA, Inc.: Washington, DC, USA, 2009.
- Raj, K. Foundations of Blockchain. January 2019. Available online: https://app.knovel.com/hotlink/toc/id:kpFB000032/foundations-blockchain/foundations-blockchain (accessed on 24 February 2023).
- Guggenberger, T.; Sedlmeir, J.; Fridgen, G.; Luckow, A. An In-Depth Investigation of Performance Characteristics of Hyperledger Fabric. arXiv 2021, arXiv:2102.07731. [Google Scholar] [CrossRef]
- Nakaike, T.; Zhang, Q.; Ueda, Y.; Inagaki, T.; Ohara, M. Hyperledger Fabric Performance Characterization and Optimization Using GoLevelDB Benchmark. In Proceedings of the 2020 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Toronto, ON, Canada, 4–7 May 2020; pp. 1–9. [Google Scholar] [CrossRef]
- Markani, J.H.; Amrhar, A.; Gagné, J.-M.; Landry, R.J. NextGen ADS-B Software-Defined Reception with Enhanced Techniques. Appl. Sci. 2022, 13, 493. [Google Scholar] [CrossRef]
| Type of Attack | Attack Methods | Attack Severity Level | Impacted Requirement |
|---|---|---|---|
| Passive attacks | Eavesdropping | Low | Confidentiality |
| Jamming | Medium | Availability | |
| Active attacks | Message Injection | High | Authentication |
| Message Deletion | High | Integrity | |
| Message Modification | High | Integrity |
| Software | MATLAB Simulink | C++ | ||
|---|---|---|---|---|
| System type | ADS-B | SADS-B | ADS-B | SADS-B |
| Time (millisecond) | 1.107 | 3.104 | 0.049 | 0.084 |
| Category | Achievability | Security Level | Sensitivity Degradation | Compatibility |
|---|---|---|---|---|
| Public key | Hard | High | Yes | Requires key management, agreement modification |
| Message Authentication Code | Easy | Low | Yes | Requires key management, agreement modification |
| SADS-B with PSK | Medium | Low | Yes | Requires key management, additional software |
| FPE of size 14-, 13-byte | Easy | High | No | Requires key management, additional software |
| FPE ICAO only | Easy | Low | No | Requires key management, additional software |
| Category | Data Integrity | Location Integrity | Confidentiality | Authentication | Remarks |
|---|---|---|---|---|---|
| Public key | Y | Y | Y | Y | Adding extra load |
| Message Authentication Code | N | N | N | Y | Adding extra load |
| SADS-B with PSK | N | N | N | Y | |
| Holistic framework | Y | Y | Y | Y | Adding extra load |
| SVM | P (detect injection) | N | N | N | P = partially addressed |
| Physical layer protection | P (detect injection) | Y | N | N | P = partially addressed |
| supervised deep learning | P (detect injection) | Y | N | N | P = partially addressed |
| FPE & Blockchain (this paper) | Y | Y | Y | Y |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Habibi Markani, J.; Amrhar, A.; Gagné, J.-M.; Landry, R.J. Security Establishment in ADS-B by Format-Preserving Encryption and Blockchain Schemes. Appl. Sci. 2023, 13, 3105. https://doi.org/10.3390/app13053105
Habibi Markani J, Amrhar A, Gagné J-M, Landry RJ. Security Establishment in ADS-B by Format-Preserving Encryption and Blockchain Schemes. Applied Sciences. 2023; 13(5):3105. https://doi.org/10.3390/app13053105
Chicago/Turabian StyleHabibi Markani, Jamal, Abdessamad Amrhar, Jean-Marc Gagné, and René Jr Landry. 2023. "Security Establishment in ADS-B by Format-Preserving Encryption and Blockchain Schemes" Applied Sciences 13, no. 5: 3105. https://doi.org/10.3390/app13053105
APA StyleHabibi Markani, J., Amrhar, A., Gagné, J.-M., & Landry, R. J. (2023). Security Establishment in ADS-B by Format-Preserving Encryption and Blockchain Schemes. Applied Sciences, 13(5), 3105. https://doi.org/10.3390/app13053105





