Designing a Vertical Handover Algorithm for Security-Constrained Applications
Abstract
:1. Introduction
2. Related Works
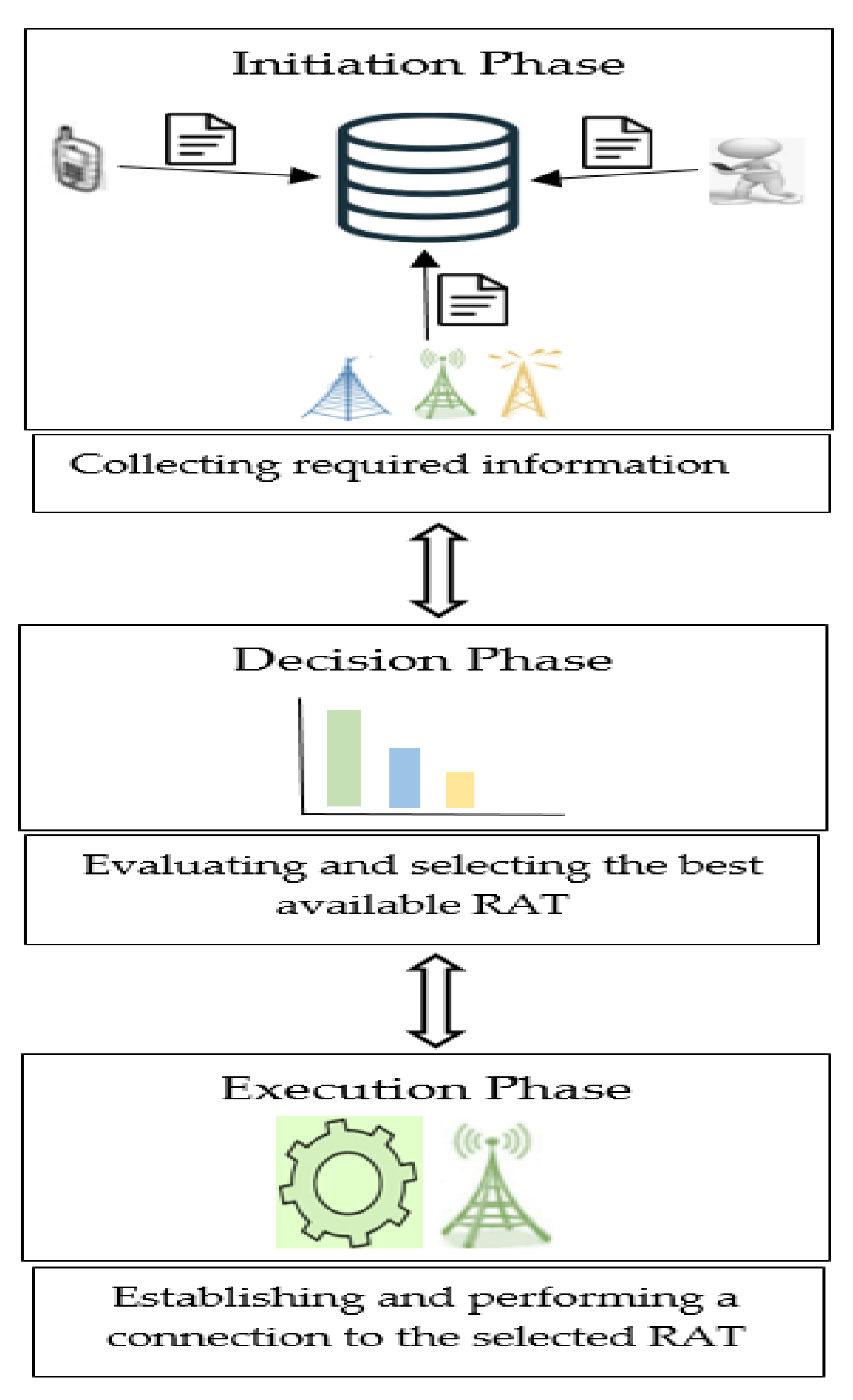
3. Design of the Proposed Algorithm
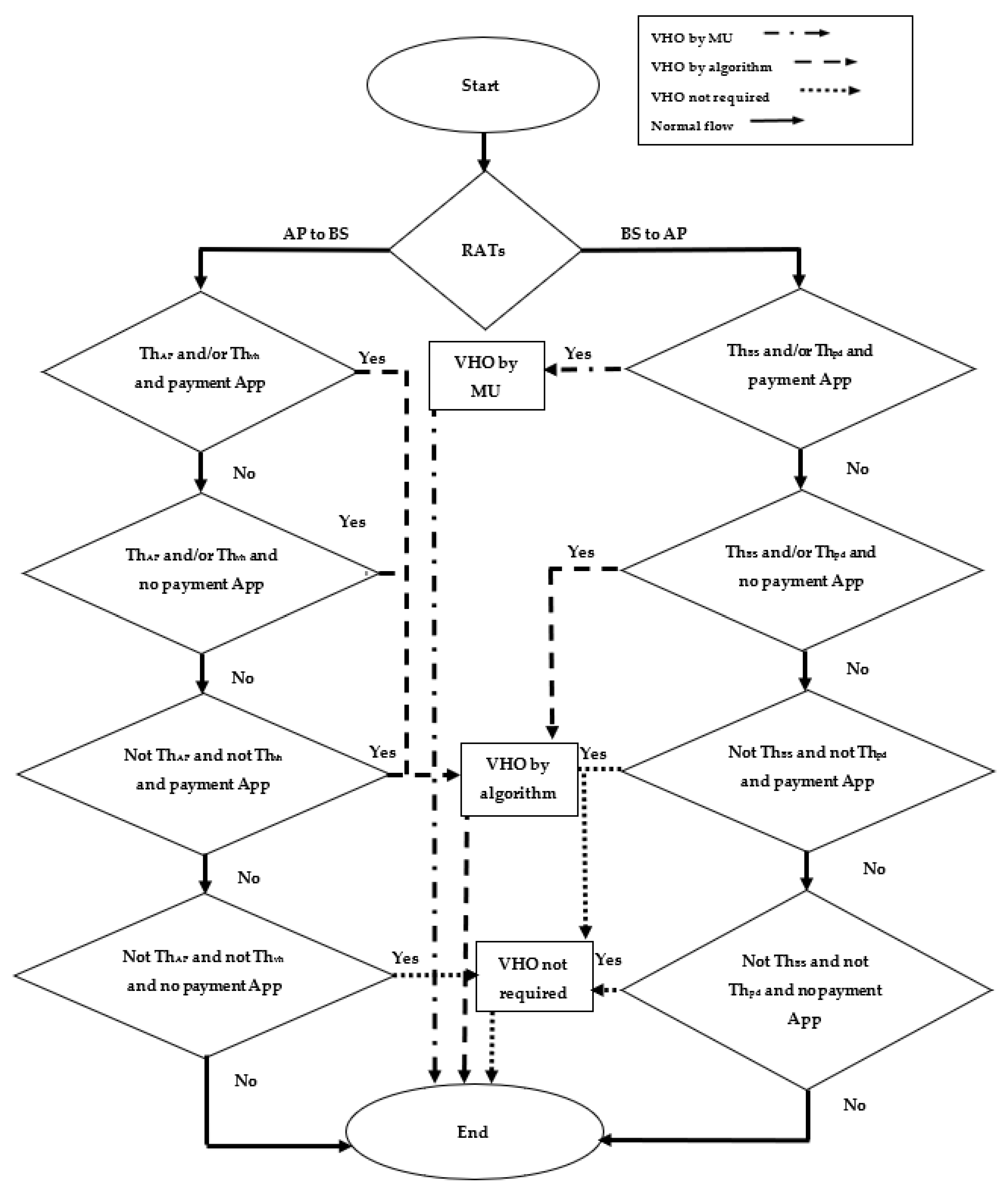
- Distance threshold: ThBS is 1 km for BS and ThAP is 100 m for AP.
- Speed threshold: Thpd is 1–3 m/s for pedestrians and Thvh is 10 m/s for the vehicle.
- BS to AP
- ▪
- If the MU reaches ThBS and/or Thpd and switches to a payment application, then VHO is triggered to an available AP to keep the sensitive session ongoing. It should be therefore considered MU’s responsibility.
- ▪
- If the MU reaches ThBS and/or Thpd and does not switch to a payment application, then VHO is triggered to an available AP to keep the non-sensitive session ongoing. It should be considered by the algorithm dynamically, without MU intervention.
- ▪
- If the MU does not reach ThBS,Thpd and switches to a payment application, then triggering VHO is not required.
- ▪
- If the MU does not reach the ThBS,Thpd and does not switch to a payment application, then triggering VHO is not required.
- AP to BS
- ▪
- If the MU reaches ThAP and/or Thvh and switches to a payment application, then VHO is triggered to an available BS to secure and keep the sensitive session ongoing. It should be considered by the algorithm dynamically, without MU intervention.
- ▪
- If the MU reaches ThAP and/or Thvh and does not switch to a payment application, then VHO is triggered to an available BS to keep the non-sensitive session ongoing. It should be considered by the algorithm dynamically, without MU intervention.
- ▪
- If the MU does not reach ThAP, Thvh and does not switch to a payment application, then VHO is triggered to an available BS to secure the ongoing sensitive session. It should be considered by the algorithm dynamically, without MU intervention.
- ▪
- If the MU does not reach the ThAP, Thvh and does not switch to a payment application, then triggering VHO is not required.
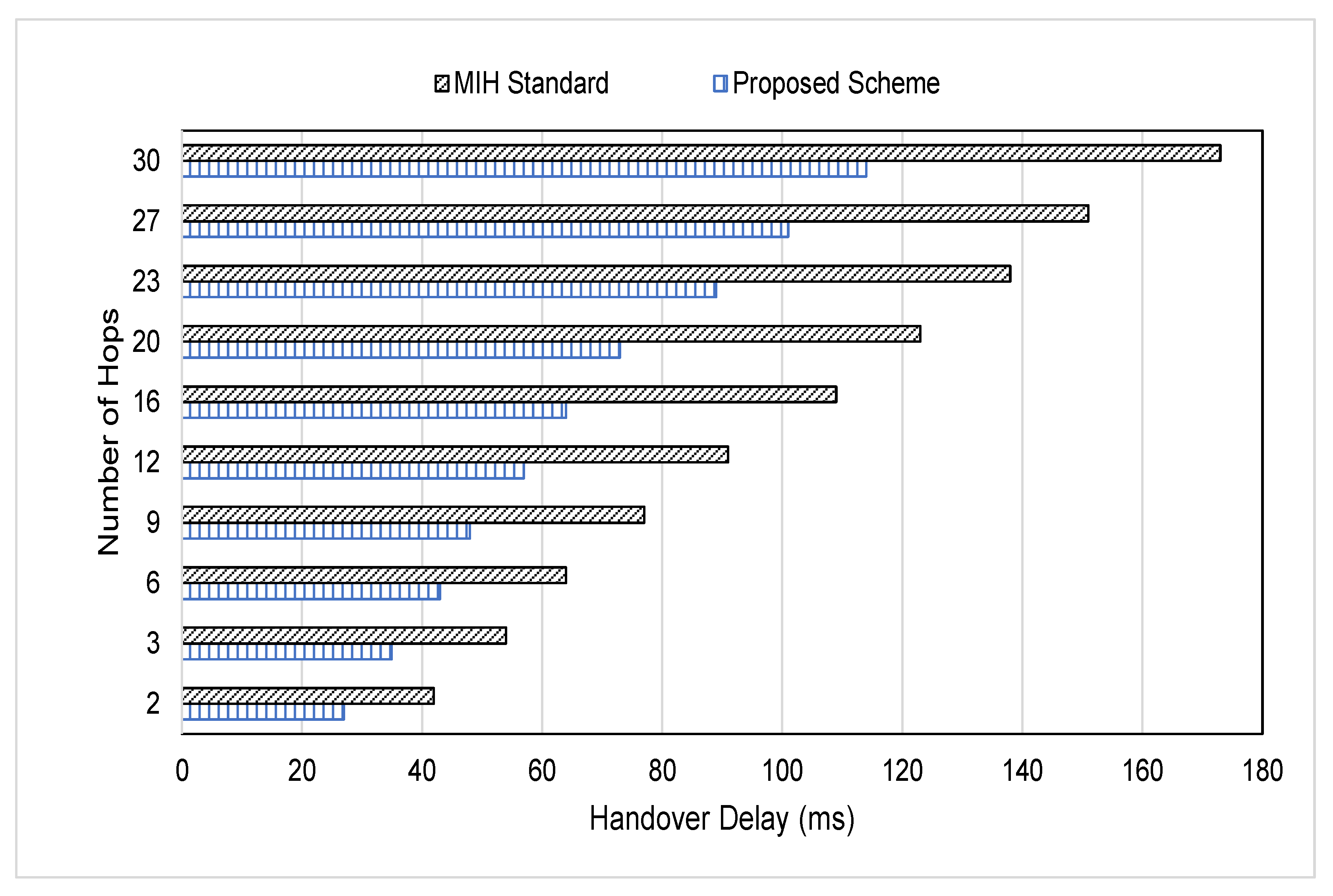
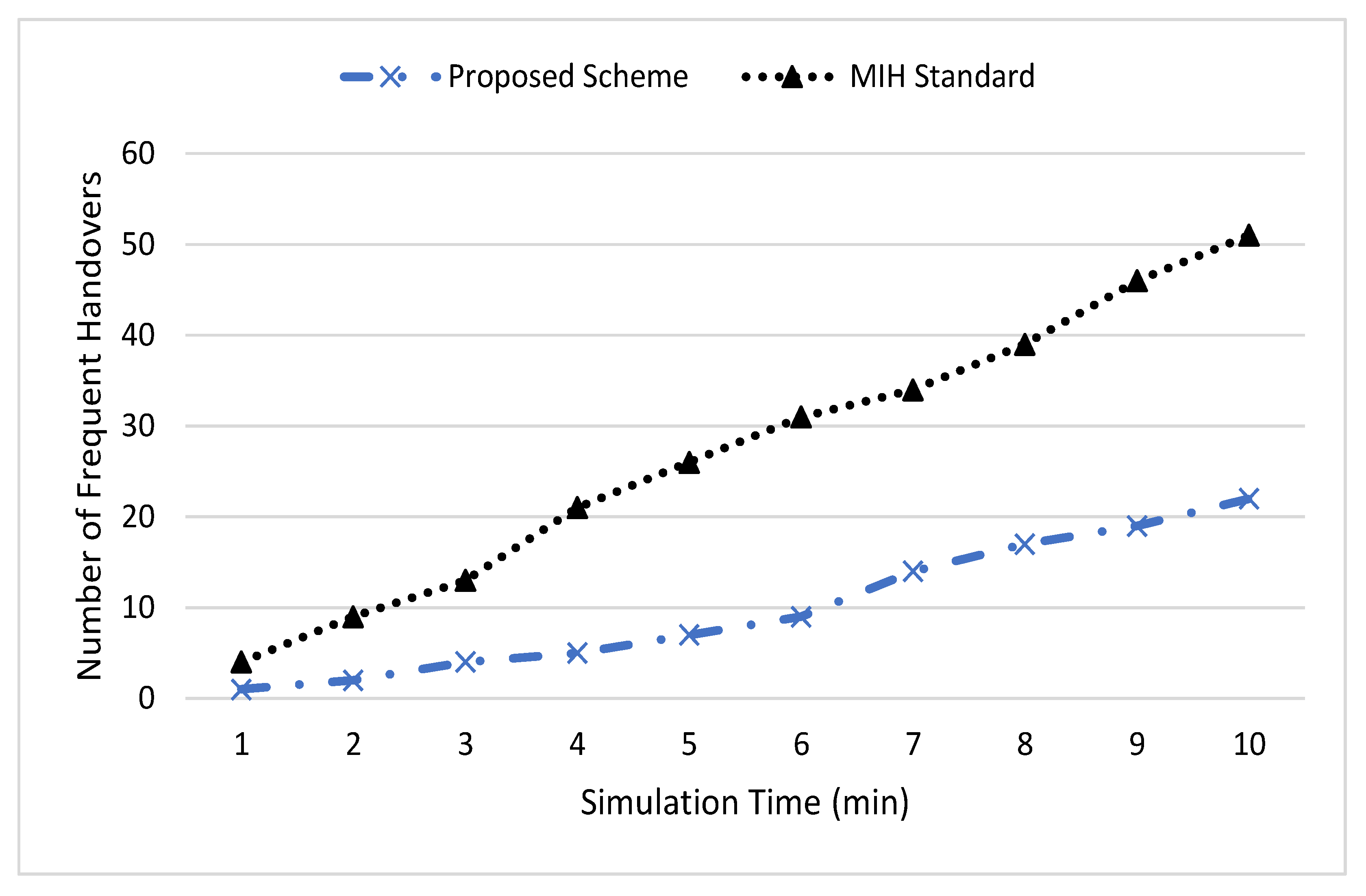
4. Performance Evaluation and Results Discussion
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- International Telecommunication Union (ITU). Committed to Connecting the World, Statistics. Available online: https://www.itu.int/en/ITU-D/Statistics/Pages/stat/default.aspx (accessed on 8 January 2023).
- Chandavarkar, B.R.; Ram Mohan Reddy, G. Survey paper: Mobility management in heterogeneous wireless networks. Procedia Eng. 2012, 30, 113–123. [Google Scholar] [CrossRef]
- Goutam, S.; Unnikrishnan, S.; Karandikar, A. Algorithm for vertical handover using multi attribute decision making techniques. In Proceedings of the IEEE International Conference on Communication, Networks and Satellite (Comnetsat), Batam, Indonesia, 17–18 December 2020. [Google Scholar]
- Goutam, S.; Unnikrishnan, S.; Prabavathy, S.S.; Karandikar, A.; Goutam, A. Algorithm for network selection based on SAW and MEW techniques. In Proceedings of the International Conference on Control, Automation, Power and Signal Processing (CAPS), Jabalpur, India, 10–12 December 2021. [Google Scholar]
- Goutam, S.; Unnikrishnan, S. Algorithm for handover decision in IEEE 802.11 WLAN environment based on fuzzy logic. In Proceedings of the IEEE International WIE Conference on Electrical and Computer Engineering (WIECON-ECE), Bangalore, India, 15–16 November 2019. [Google Scholar]
- Goutam, S.; Unnikrishnan, S.; Goutam, A. Model for vertical handover decision in vehicular networks. In Proceedings of the International Conference on Advances in Computing, Communication and Control (ICAC3), Mumbai, India, 1–2 December 2017. [Google Scholar]
- Goutam, S.; Unnikrishnan, S.; Prabavathy, S.S.; Kudu, N. Prediction of vertical handover using multivariate regression model. Int. J. Innov. Technol. Explor. Eng. (IJITEE) 2019, 8, 2626–2633. [Google Scholar] [CrossRef]
- Goutam, S.; Unnikrishnan, S. QoS based vertical handover decision algorithm using fuzzy logic. In Proceedings of the International Conference on Nascent Technologies in Engineering (ICNTE), Navi Mumbai, India, 4–5 January 2019. [Google Scholar]
- Zekri, M.; Jouaber, B.; Zeghlache, D. Context aware vertical handover decision making in heterogeneous wireless networks. In Proceedings of the 35th Conference on Local Computer Networks (LCN), Denver, CO, USA, 10–14 October 2010. [Google Scholar]
- Kassar, M.; Kervella, B.; Pujolle, G. An overview of vertical handover decision strategies in heterogeneous wireless networks. Comput. Commun. 2008, 31, 2607–2620. [Google Scholar] [CrossRef]
- Stevens-Navarro, E.; Wong, V.W.S. Comparison between vertical handoff decision algorithms for heterogeneous wireless networks. In Proceedings of the 63rd Vehicular Technology Conference (VTC), Melbourne, VIC, Australia, 7–10 May 2006. [Google Scholar]
- Chan, P.M.L.; Sheriff, R.E.; Hu, Y.F.; Conforto, P.; Tocci, C. Mobility management incorporating fuzzy logic for heterogeneous a IP environment. IEEE Commun. Mag. 2001, 39, 42–51. [Google Scholar] [CrossRef]
- Chen, W.T.; Liu, J.C.; Huang, H.K. An adaptive scheme for vertical handoff in wireless overlay networks. In Proceedings of the Tenth International Conference on Parallel and Distributed Systems (ICPADS), Newport Beach, CA, USA, 9 July 2004. [Google Scholar]
- McNair, J.; Zhu, F. Vertical handoffs in fourth-generation multinetwork environments. IEEE Wirel. Commun. 2004, 11, 8–15. [Google Scholar] [CrossRef]
- Gyekye-Nkansah, Y.; Agbinya, J. Vertical handoffs decision algorithms using fuzzy logic. In Proceedings of the International Conference on Wireless Broadband and Ultra Wideband Communications, Sydney, Australia, 13–16 March 2006. [Google Scholar]
- Sourav, D.; Amitava, R.; Rabindranath, B. Design and simulation of vertical handover algorithim for vehicular communication. Int. J. Eng. Sci. Technol. 2010, 2, 5509–5525. [Google Scholar]
- Debnath, A.; Kumar, N. Simple additive weighted algorithm for vertical handover in heterogeneous network. In Proceedings of the 2nd PhD Colloquium on Ethically Driven Innovation and Technology for Society (PhD EDITS), Bangalore, India, 8 November 2020. [Google Scholar]
- Yew, H.T.; Chekima, A.; Kiring, A.; Mbulwa, A.I.; Dargham, J.A.; Chung, S.K. RSS based vertical handover schemes in heterogeneous wireless networks: Past, present & future. In Proceedings of the IEEE 2nd International Conference on Artificial Intelligence in Engineering and Technology (IICAIET), Kota Kinabalu, Malaysia, 26–27 September 2020. [Google Scholar]
- Goyal, T.; Kaushal, S. Optimized network selection during handover using analytic hierarchy process in 4G network. In Proceedings of the International Conference on Advances in Computing, Communication, & Automation (ICACCA) (Spring), Dehradun, India, 8–9 April 2016. [Google Scholar]
- Akshay, J.; Elena, L.A.; Ilker, D. Evolutionary 4G/5G network architecture assisted efficient handover signaling. IEEE Access 2018, 3, 256–283. [Google Scholar]
- Huang, Y.; Leu, F.; Liu, J.; Huang, Y.; Chu, W.C. A handover scheme for LTE wireless networks under the assistance of GPS. In Proceedings of the Eighth International Conference on Broadband and Wireless Computing, Communication and Applications, Compiegne, France, 28–30 October 2013. [Google Scholar]
- Kumar, P.; Sandeep, C.; Kumar, S.N. An overview of the factors affecting handovers and effective highlights of handover techniques for next generation wireless networks. Indian J. Public Health Res. Dev. 2018, 9, 722–725. [Google Scholar] [CrossRef]
- Pramod, P.; Sagar, K. A proficient vertical handover decision making algorithm in Internet of vehicles with 5G. In Proceedings of the International Conference on Electronics and Renewable Systems (ICEARS), Tuticorin, India, 16–18 March 2022. [Google Scholar]
- Rubasinghe, D.; Pussella, V.; Marasinghe, M.; Silva, S.; Dampage, U. QoS aware energy efficient vertical handover approach in LTE/WLAN heterogeneous networks. In Proceedings of the IEEE International Conference on Computing, Power and Communication Technologies (GUCON), Greater Noida, India, 2–4 October 2020. [Google Scholar]
- Khattab, O.; Alani, O. A survey on media independent handover (mih) and ip multimedia subsystem (ims) in heterogeneous wireless networks. Int. J. Wirel. Inf. Netw. 2013, 20, 215–228. [Google Scholar] [CrossRef]
- Khattab, O. A new secure algorithm for upcoming sensitive connection between heterogeneous mobile networks. Int. J. Adv. Comput. Sci. Appl. (IJACSA) 2021, 12, 705–709. [Google Scholar] [CrossRef]
- Khattab, O. A comprehensive survey on vertical handover security attacks during execution phase. Int. J. Adv. Trends Comput. Sci. Eng. (IJATCSE) 2019, 8, 1965–1968. [Google Scholar] [CrossRef]
- Khattab, O. Performance analysis of reducing signaling cost for a roaming user in vertical handover algorithm for mobile networks. IOSR J. Comput. Eng. 2017, 19, 94–99. [Google Scholar]
- Khattab, O.; Alani, O. Simulation of performance execution procedure to improve seamless vertical handover in heterogeneous networks. Int. J. Adv. Comput. Sci. Appl. (IJACSA) 2014, 5, 109–113. [Google Scholar] [CrossRef]
- Khattab, O.; Alani, O. I AM 4 VHO: New approach to improve seamless vertical handover in heterogeneous wireless networks. Int. J. Comput. Netw. Commun. (IJCNC) 2013, 5, 53–63. [Google Scholar] [CrossRef]
- Khattab, O.; Alani, O. Mobile IPv4 based procedure for loose coupling architecture to optimize performance in heterogeneous wireless networks. Int. J. Comput. Netw. Wirel. Commun. (IJCNWC) 2013, 3, 56–61. [Google Scholar]
- Khattab, O.; Alani, O. Algorithm for seamless vertical handover in heterogeneous mobile networks. In Proceedings of the IEEE Technically Co-Sponsored Science and Information Conference, London, UK, 27–29 August 2014. [Google Scholar]
- Khattab, O.; Alani, O. The design and calculation of algorithm for optimizing vertical handover performance. In Proceedings of the 9th IEEE/IET International Symposium on Communication Systems, Networks and Digital Signal Processing (CSNDSP), Manchester, UK, 23–25 July 2014. [Google Scholar]
- Khattab, O.; Alani, O. An overview of interworking architectures in heterogeneous wireless networks: Objectives, features and challenges. In Proceedings of the 10th International Network Conference (INC), Plymouth, UK, 8–10 July 2014. [Google Scholar]
- Khattab, O.; Alani, O. Survey on media independent handover (MIH) approaches in heterogeneous wireless networks. In Proceedings of the IEEE 19th European Wireless (EW), Guildford, UK, 16–18 April 2013. [Google Scholar]
- Hajar, M.S.; Khaled Chahine, M.; Hamdan, R.; Qdah, M.S. Performance analysis of vertical handover using predictable LGD event based on IEEE 802.21. In Proceedings of the IEEE International Conference on Communications Workshops (ICC Workshops), Montreal, QC, Canada, 14–23 June 2021. [Google Scholar]
- Rong, C.; Min, X.; Lun, T.; Qian-bin, C. Performance parameter analysis and algorithm research of vertical handoff in heterogeneous networks. J. Chongqing Univ. Posts Telecommun. (Nat. Sci. Ed.) 2010, 22, 63–70. [Google Scholar]
- Jianhua, T.; Xiangnong, W.; Lu, W. An improved vertical handoff algorithm based on multiple attribute decision making. J. Shanghai Norm. Univ. (Nat. Sci. Ed.) 2016, 45, 458–463. [Google Scholar]
- Shiwei, G. An improved KNN based decision algorithm for vertical handover in heterogeneous wireless networks. In Proceedings of the 40th Chinese Control Conference (CCC), Shanghai, China, 26–28 July 2021. [Google Scholar]
- Yan, X.; Sekercioglu, A.; Narayanan, S. A survey of vertical handover decision algorithms in fourth generation heterogeneous wireless networks. Comput. Netw. 2010, 54, 1848–1863. [Google Scholar] [CrossRef]
- Fan, Y.; Li, J.; Bhatti, U.A.; Shao, C.; Gong, C.; Cheng, J.; Chen, Y. A multi-watermarking algorithm for medical images using inception v3 and dct. Comput. Mater. Contin. 2023, 74, 1279–1302. [Google Scholar]
- Li, T.; Li, J.; Liu, J.; Huang, M.; Chen, Y.W.; Bhatti, U.A. Robust watermarking algorithm for medical images based on log-polar transform. J. Wirel. Com Netw. 2022, 2022, 24. [Google Scholar] [CrossRef]
- Goutam, S.; Unnikrishnan, S.; Karandikar, A.; Goutam, A. Principal component analysis of VHO parameters. In Proceedings of the IEEE 11th International Conference on Communication Systems and Network Technologies (CSNT), Indore, India, 23–24 April 2022. [Google Scholar]
- Goutam, S.; Unnikrishnan, S.; Karandikar, A. Algorithm for vertical handover using network fitness function. In Proceedings of the International Conference on Control, Automation, Power and Signal Processing (CAPS), Jabalpur, India, 10–12 December 2021. [Google Scholar]
- Kunarak, S.; Duangchan, T. Vertical handover decision based on hybrid artificial neural networks in HetNets of 5G. In Proceedings of the IEEE Region 10 Symposium (TENSYMP), Jeju, Republic of Korea, 23–25 August 2021. [Google Scholar]
- Satapathy, P.; Mahapatro, J. Energy-efficient vertical handover in heterogeneous networks. In Proceedings of the IEEE International IOT, Electronics and Mechatronics Conference (IEMTRONICS), Toronto, ON, Canada, 21–24 April 2021. [Google Scholar]
- Zeshan, A.; Baykas, T. Location aware vertical handover in a VLC/WLAN hybrid network. IEEE Access 2021, 9, 129810–129819. [Google Scholar] [CrossRef]
- Khattab, O. Enhance vertical handover security during execution phase in mobile networks. Comput. Mater. Contin. 2022, 72, 3863–3875. [Google Scholar] [CrossRef]
- Khan, M.; Han, K. A Vertical Handover Management Scheme based on Decision Modelling in Heterogeneous Wireless Networks. IETE Tech. Rev. 2015, 32, 402–412. [Google Scholar] [CrossRef]
- Tan, X.; Chen, G.; Sun, H. Vertical handover algorithm based on multi-attribute and neural network in heterogeneous integrated network. J. Wirel. Commun. Netw. 2020, 2020, 202. [Google Scholar] [CrossRef]
- Khan, M.; Din, S.; Gohar, M.; Ahmad, A.; Cuomo, S.; Piccialli, F.; Jeon, G. Enabling multimedia aware vertical handover Management in Internet of Things based heterogeneous wireless networks. Multimed. Tools Appl. 2017, 76, 25919–25941. [Google Scholar] [CrossRef]
- Khan, M.; Han, K. A Review of Handover Techniques in Wireless Ad hoc Networks Based on IEEE 802.21 Media Independent Handover Standard. IETE Tech. Rev. 2014, 31, 353–361. [Google Scholar] [CrossRef]



| Reference | Failed Handovers | VHO Delay | Frequent VHOs | VHO Throughput | VHO Packet Loss |
|---|---|---|---|---|---|
| [8] | n/a | √ | n/a | √ | √ |
| [17] | n/a | n/a | n/a | √ | n/a |
| [36] | n/a | n/a | n/a | n/a | √ |
| [39] | n/a | √ | n/a | √ | √ |
| [43] | n/a | √ | √ | √ | n/a |
| [44] | n/a | n/a | √ | √ | n/a |
| [47] | √ | √ | n/a | √ | √ |
| [48] | n/a | n/a | n/a | √ | n/a |
| [49] | n/a | √ | n/a | √ | n/a |
| Proposed algorithm | √ | √ | √ | √ | √ |
| Scenario | ThBS | ThAP | Thpd | Thvh | Payment App. | VHO | MU’s Responsibility (1) Algorithm’s Responsibility (2) |
|---|---|---|---|---|---|---|---|
| BS-AP | √ | n/a | √ | n/a | √ | √ | 1 |
| √ | n/a | × | n/a | √ | √ | 1 | |
| × | n/a | √ | n/a | √ | √ | 1 | |
| √ | n/a | √ | n/a | × | √ | 2 | |
| √ | n/a | × | n/a | × | √ | 2 | |
| × | n/a | √ | n/a | × | √ | 2 | |
| × | n/a | × | n/a | √ | × | 2 | |
| × | n/a | × | n/a | × | × | 2 | |
| AP-BS | n/a | √ | n/a | √ | √ | √ | 2 |
| n/a | √ | n/a | × | √ | √ | 2 | |
| n/a | × | n/a | √ | √ | √ | 2 | |
| n/a | √ | n/a | √ | × | √ | 2 | |
| n/a | √ | n/a | × | × | √ | 2 | |
| n/a | × | n/a | √ | × | √ | 2 | |
| n/a | × | n/a | × | √ | √ | 2 | |
| n/a | × | n/a | × | × | × | 2 |
| Simulation Parameter | Value |
|---|---|
| Number of MUs | 15, 25, 50 |
| MU movement model | Random waypoint mobility model (10 m/s) |
| Propagation channel model | Two-ray ground |
| UMTS network communication range | 1 km |
| Wi-Fi network coverage | 100 m |
| RSS threshold | −62 dBm |
| Traffic type | CBR |
| Packet size | 512 Bytes |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khattab, O.; Khan, M.; Alothman, B. Designing a Vertical Handover Algorithm for Security-Constrained Applications. Appl. Sci. 2023, 13, 2166. https://doi.org/10.3390/app13042166
Khattab O, Khan M, Alothman B. Designing a Vertical Handover Algorithm for Security-Constrained Applications. Applied Sciences. 2023; 13(4):2166. https://doi.org/10.3390/app13042166
Chicago/Turabian StyleKhattab, Omar, Murad Khan, and Basil Alothman. 2023. "Designing a Vertical Handover Algorithm for Security-Constrained Applications" Applied Sciences 13, no. 4: 2166. https://doi.org/10.3390/app13042166
APA StyleKhattab, O., Khan, M., & Alothman, B. (2023). Designing a Vertical Handover Algorithm for Security-Constrained Applications. Applied Sciences, 13(4), 2166. https://doi.org/10.3390/app13042166










