In order to determine the effect of removing branches on the lines of the whole network, the power distribution of the whole network needs to be recalculated, which is complicated and time-consuming. If it is possible to identify the set of lines that are more affected by LE and analyze only the extent of the impact on the branches within the set, it will be possible to shorten the analysis time, take emergency control measures as soon as possible, and effectively avoid cascade tripping caused by mechanically removing overloaded lines. This section proposes a method to quickly search for branches more affected by LE to determine the range of wide-area information that needs to be collected.
2.1. The Definition and Graph Theory Characteristics of the CLS
Rapid judgment of the impact of branch removal on the whole network is of great significance in suppressing the development and spread of grid accidents. Before searching the CLS of the removed branch, it is necessary to find out its characteristics.
Under unfavorable operating conditions, a wide range of LE in the power system is likely to happen after removing the faulty branch, which may lead to cascading tripping accidents. The possible operating states of cascading trips caused by LE are as follows:
The overall load of the system is large, and some branches in the system are in a heavy load state. Once the faulty line is removed, LE will likely cause branch overload.
One line in the system is out of power for maintenance, and the other line is removed by the main protection due to a short-circuit fault, resulting in LE, and the remaining branch is prone to overload.
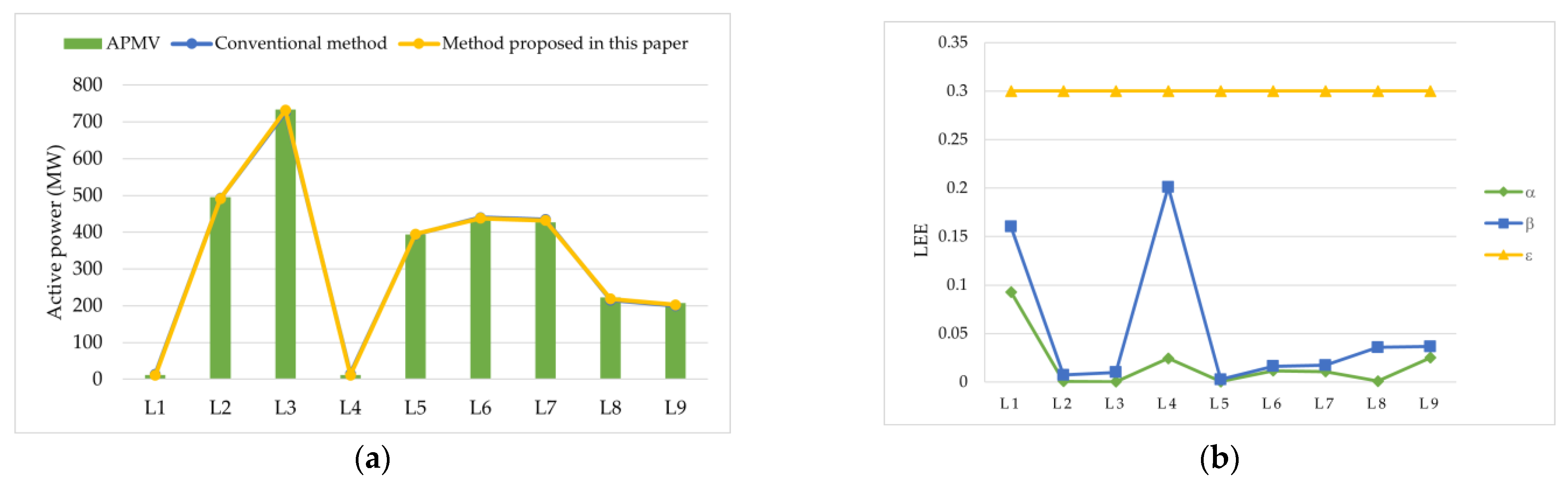
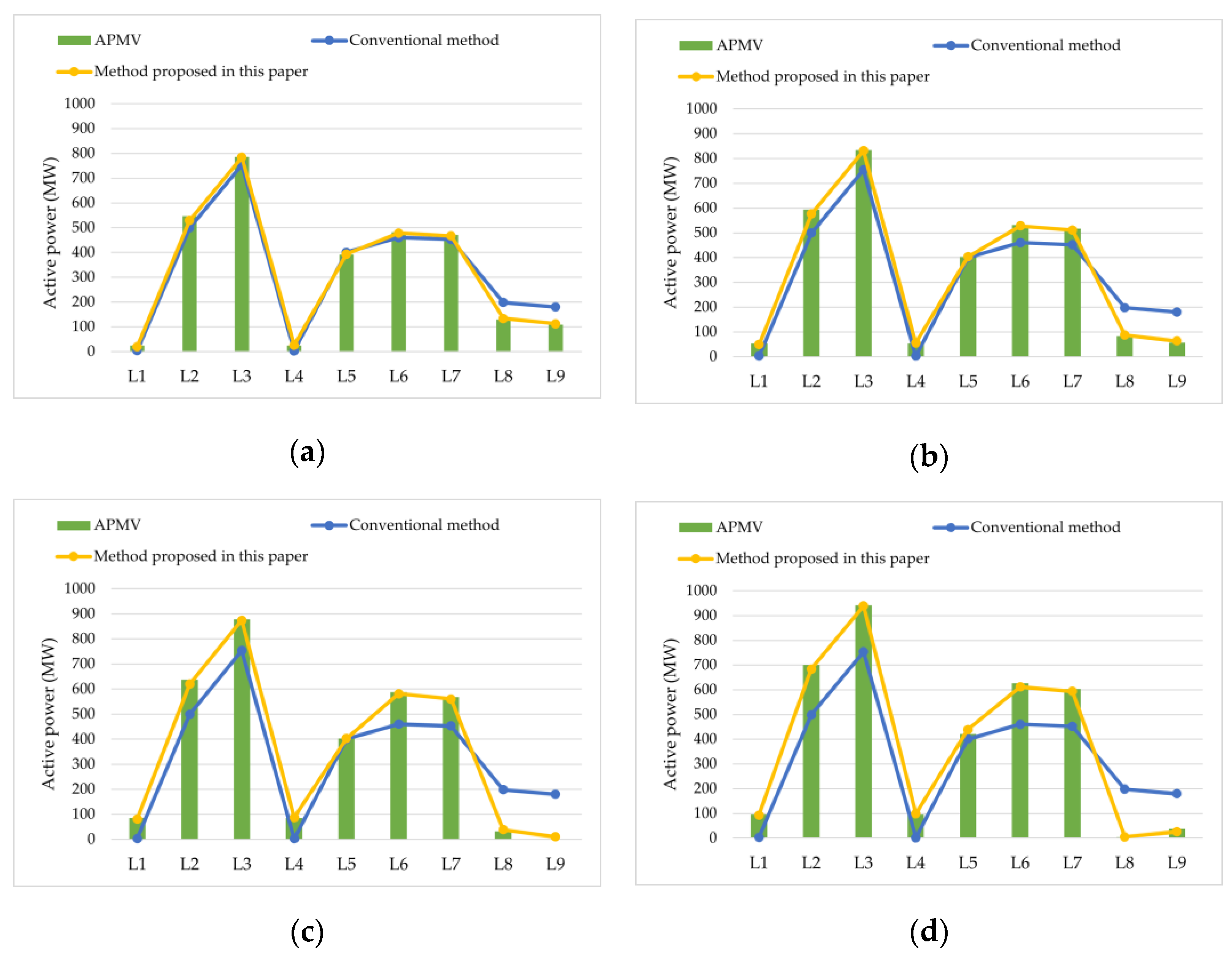
The set of dangerous lines greatly affected by the LE is called the CLS. The definition of the CLS is given according to the load encroachment-related proportional factor (LERPF): the set of all branches satisfying Equation (1) after the faulty line is removed is called the CLS of the removed branch.
where
d is the LERPF of the remaining branches to the faulty branch after it is removed; its value is related to the power grid’s topological structure and branch parameters. The definition of its concept and the derivation of its mathematical expression will be discussed in
Section 3 of this paper. The value of
d can reflect the active power change value of the remaining branches in the network caused by the LE after the faulty branch is removed. The larger the value of
d, the larger the branch is affected by the LE, and vice versa, the smaller the value of
d, the smaller the branch is affected by the LE.
d0 is a fixed value; the larger the value of
d0, the fewer the number of branches included in the CLS of the removed branch and the higher the search speed of the CLS can be improved, but there is a possibility that some of the branches affected by the LE are missed; the smaller the value of
d0, the more branches affected by the LE can be included, but it will increase the collection range of the wide-area information and reduce the speed. Therefore, the value of
d0 should not be too small or too large; many scholars have studied this area and finally concluded that, according to the actual operational requirements, the value of
d0 in the range of 0.2–0.3 is the best [
23].
In fact, the effect of the removed branch on the power flow of the whole network decreases gradually outwards, centered on the removed branch. Thus, in the early stages of incident development, the overloaded branch tends to be electrically close to the resected branch. According to the circuit principle, the graph theory characteristics of the CLS are summarized as follows:
The branches in the CLS can form a loop with the removed branches.
The smaller the loop reactance value is, the greater the influence of LE is. When the loop reactance value is larger, the influence of LE can be ignored.
The fast search method for the CLS proposed in this paper consists of two modules: (1) grid abstraction and dimensionality reduction; (2) path search to determine the CLS. The overall steps for searching for the CLS are shown in
Figure 1.
All the branches within the CLS make up the area highly affected by LE, and if this area can be quickly identified, the analysis can be narrowed down and time saved. Therefore, if backup protection activation exists after a line is removed, the CLS of that removed line is quickly searched to determine the scope of the analysis, and the wide-area information within that scope is used for the identification of the cause of branch overloading.
2.2. The Establishment and Dimension Reduction of the Graph Model
According to the characteristics of the CLS mentioned above, before searching for the CLS of the resected branch, it is necessary to transform the power system into a graph model and then perform a dimensionality reduction process on it so as to realize CLS searching in a smaller area, which greatly reduces the burden of further analyses and calculations and narrows down the target range, thus improving the searching speed.
According to the graph theory, the power system can be abstracted into a graph model, represented by T, and T = (V, E), where
V = {v1, v2, …, vm}, and V represents the set of grid nodes; vi represents the node abstracted from the generator or bus of the power grid;
E = {e1, e2, …, em}, and E represents the edge set of the grid; ei represents the edge abstracted from the transmission line or power transformer. If ei has a direction, then T is a directed graph; otherwise, T is an undirected graph. If ei has weight, then T is a weighted graph; otherwise, it is an unweighted graph. In the weighted graph, the weight of ei is represented by wij. In this paper, the branch reactance is used to represent the branch weight, which is also called branch length.
Suppose
T has
n nodes. If
vi and
vj are directly connected by
ei, then
vi and
vj are called adjacent nodes. If
vi and
vj are connected by a finite number of edges, then all branches from
vi to
vj form a path, denoted by
Pl, and the length of the path is the sum of the weights of all branches on the path, denoted by:
The topological relations of a graph are commonly represented by an adjacency matrix, denoted as
A, and
A is an Nth-order square matrix. The search method for the CLS proposed in this paper is based on undirected graphs. The elements in the adjacency matrix of the undirected graph are denoted by
Aij, as shown in Equation (3).
Reducing the dimension of the graph model is based on the hanging nodes and breakpoints. The definition of hanging nodes and breakpoints is as follows:
According to whether it can form a loop with other lines in the graph, the edges are distinguished. The edges that cannot form a loop with other edges are defined as hanging edges, and the nodes only connected to the hanging edges are defined as hanging nodes.
The number of branches associated with the node is defined as the node‘s branch correlation degree (BCD). The BCD of the node in an undirected graph is equal to the number of non-zero elements in the row/column where the node is located in A.
According to the above definition of hanging nodes and BCD, hanging nodes include:
- (1)
Nodes whose BCD is one.
- (2)
After deleting all nodes in the graph whose BCD is one, the nodes whose BCD becomes one in all remaining nodes.
The BCD of each node in the graph and its neighboring nodes can be quickly obtained by searching A, thus quickly obtaining the hanging nodes.
- 2.
Breakpoints
Suppose T is a connected graph and va is a node in T. If T becomes a non-connected graph after va is removed (removing a node requires removing all the edges associated with it together), then va is called a breakpoint. If T contains breakpoints, then T is called a divisible graph. The breakpoints of the graph can be searched using the Tarjan algorithm based on the depth-first algorithm.
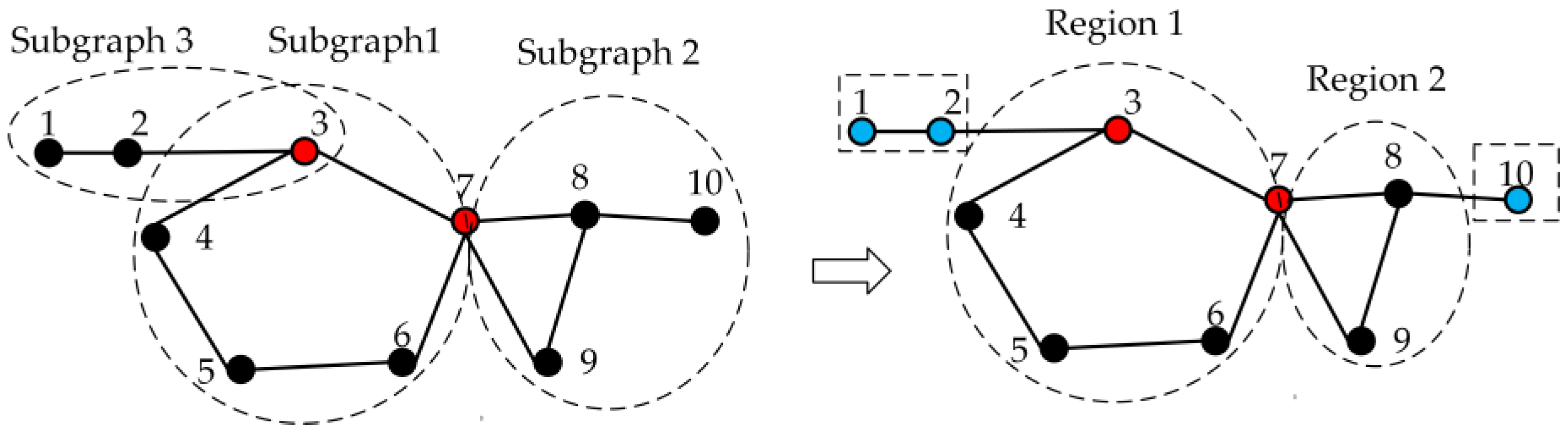
It follows from the graph theory characteristics of the CLS that if there is a breakpoint in a graph, the branch in the CLS and the removal branch should be located in the same subgraph. Therefore, before searching for the CLS, the graph is first divided into multiple subgraphs according to the breakpoints, and then the hanging nodes in each subgraph and the lines connected to them are removed. Finally, multiple LE regions can be obtained, which reduces the dimension of the graph model of the power grid, significantly reducing the target range and the burden of further analysis, thus increasing the search speed.
As shown in
Figure 2, firstly, three subgraphs are obtained according to breakpoints three and seven, then the hanging nodes one, two, and ten in each subgraph are removed, and finally, two LE regions are obtained. After obtaining multiple LE regions, the search of the CLS only needs to be carried out from the LE region where the branch is removed, accelerating the search speed and quickly determining the range of wide-area information that needs to be collected.
2.3. Search Method of CLS Based on Improved Shortest Path Algorithm
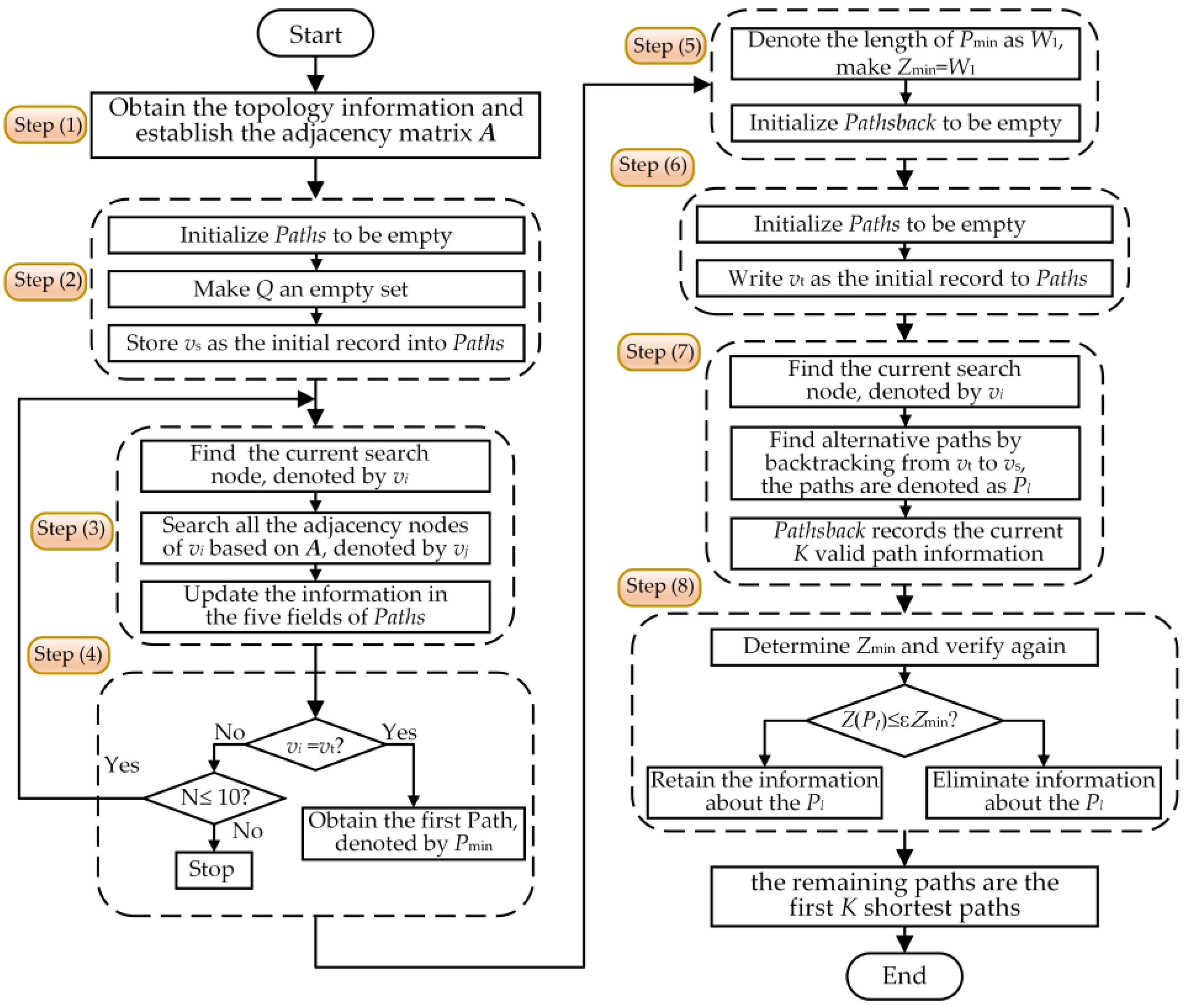
The Dijkstra algorithm is a classical shortest path algorithm for solving the shortest path problem, which can solve the shortest path from one source node to multiple end nodes. In this section, the shortest path algorithm is improved. Differing from the Dijkstra algorithm, which requires repeated traversal, the improved search method ensures the search process’s unidirectionality based on the adjacency matrix, reducing the search process’s complexity. The improved shortest path method is described in detail below.
The improved shortest path algorithm can search the shortest path from the source node to the end and discover all the first K shortest paths that satisfy Equation (4). The K shortest paths include all branches that satisfy Equation (1), and all branches on these paths constitute the CLS. According to the definition of the CLS and its graph theory characteristics, searching the CLS is equivalent to searching the multiple connected paths between the two ends of the removed branch; that is, searching the first
K shortest paths that can form the loop with the removed branch. The principle of selecting the value of
K in this paper is as shown in Equation (4).
where
Zi is the length of the
ith shortest path between two ends;
Zmin is the minimum length of all the shortest paths between two ends; ε is the threshold value of the path length ratio. The selection principle of the value of ε is as follows: since the larger the value of
d0 is, the smaller the value of ε is, it is approximately considered that ε is inversely proportional to
d0. In order to improve the adaptability of the method proposed in this paper to various types of power grids,
d0 takes the defined median value of 0.25, so take ε = 1/
d0 − 1 = 3; subtracting 1 is an adjustment to the less than equal sign in Equation (4) [
20]. This value is taken to ensure that even in the extreme case, that is, the
K + 1th shortest path has no intersection with the
Kth shortest path, and the APCV due to LE on all branches of the
Kth shortest path is less than 1/4 of the active power of the removed branch (because a small part of the power encroaches on the branch outside the CLS). Therefore, the first to the last shortest path contains all branches with
d >
d0.
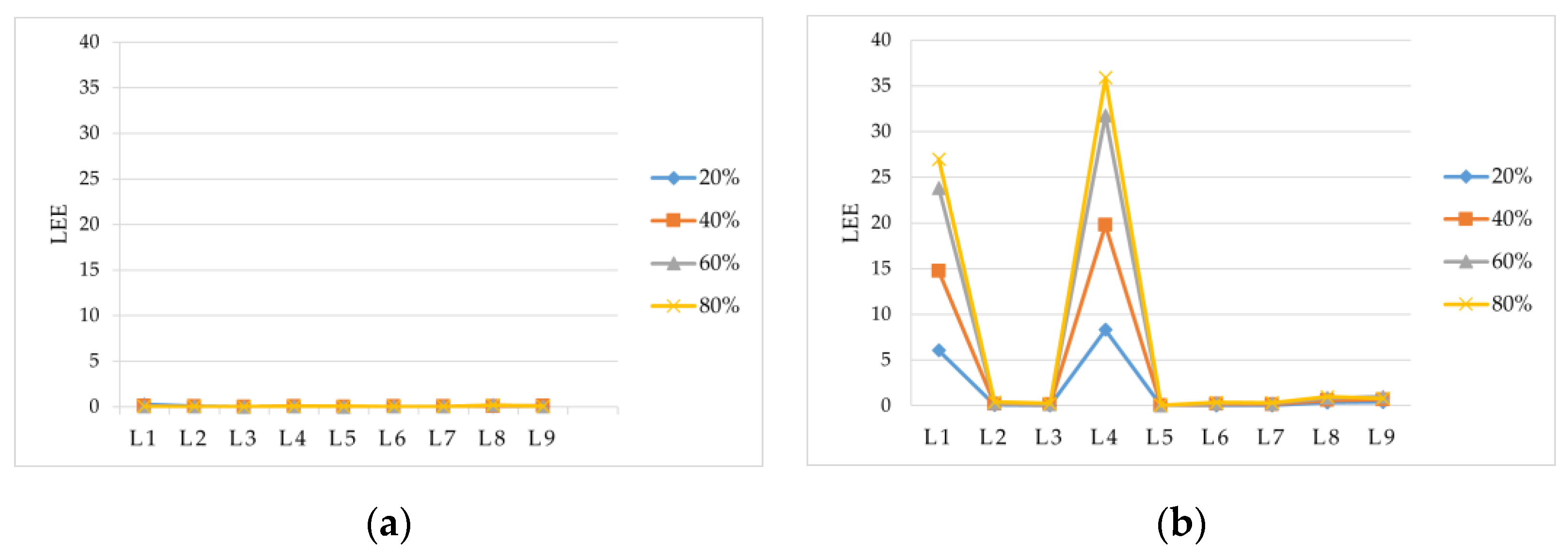
The BCD of all nodes in the path is two except for the source and final nodes, whose BCD is one. The nodes in the path with a BCD of two are defined as inner nodes, and their number is denoted by N. A large number of simulations have found that when N exceeds a certain value, it can be considered that this path is invalid due to the corresponding electrical distance being too long. For medium-sized systems, when N > 10, the branch is less affected by LE and can be ignored. The simulation case in this paper can verify. Therefore, the constraint condition of N ≤ 10 is added to the shortest path search. The value of N can be adjusted according to the different sizes of the system; the larger the system size, the larger N, and vice versa, the smaller. Since the search for the shortest path is limited by ε and N simultaneously, the search speed is not affected by the system size.
Denote the lth shortest path from the source node to the end node by Pl, where the source node is denoted by vs, the end node is denoted by vt, and the path length is denoted by Z(Pl). A data table, denoted by Paths, is constructed to store the information of the first K shortest paths during the search process. Paths contains five fields, which are:
- (1)
The current search node number, denoted by Num.
- (2)
The set of nodes that have been searched, denoted by Q.
- (3)
The edge length between two nodes, denoted by wij.
- (4)
The number of inner nodes, denoted by N.
- (5)
The length of the path, denoted by W.
During the search process, the current search node is determined based on the previous search node, and the current search node is not in the set of nodes that have been searched to ensure the search process‘s unidirectionality, improving the search speed. The improved algorithm consists of the following two parts:
Based on the improved shortest path method for searching for the CLS, the number of the first K shortest paths is limited by the minimum value of the length of all shortest paths. Therefore, when the shortest paths are determined, the number of the first K paths that can satisfy the restriction is very small. Due to the large number of circuits in the transmission grid, many loops include a small number of branches and nodes. When the number of nodes exceeds a certain value, it can be assumed that this loop is invalid due to the excessive length of the corresponding electrical distance. Therefore the method in this paper is not affected by the number of nodes in the grid.
In this section, we fully use the information of the adjacent nodes of the first K-1 paths obtained to discover the Kth shortest path and finally obtain the CLS based on the first K shortest paths that have been searched to satisfy the conditions. The steps of the improved algorithm are shown in
Figure 3. Therefore, when the WAMS monitors the power grid topology changes in real-time, the CLS of the removed branch can be quickly found based on the improved shortest path algorithm, and the acquisition range of wide-area information used to identify LE can be further determined.