A Robust Sharding-Enabled Blockchain with Efficient Hashgraph Mechanism for MANETs
Abstract
:1. Introduction
- A sharding hashgraph framework with a blacklist is proposed for the MANET-based blockchain. In each shard, the blacklist records the dishonest consensus activities of nodes in a decentralized manner. With the assistance of the blacklist, gossip information is sent to a reliable neighbor, and gossip information from another reliable neighbor is received first. It improves the efficiency of gossip about gossip in hashgraph consensus.
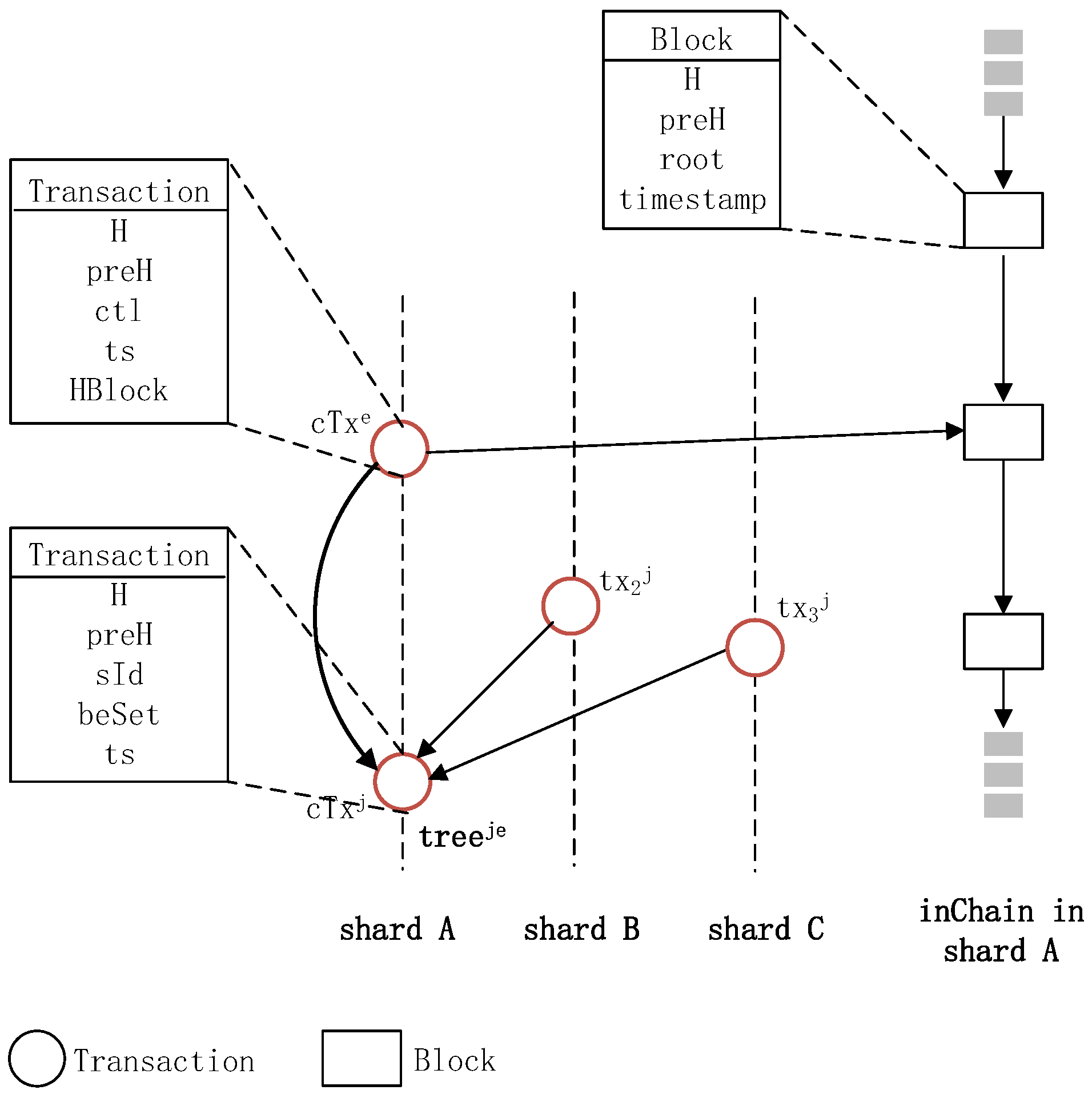
- A tree-assisted inter-sharding consensus is proposed to prevent Sybil attacks. A tree, , whose root is the participation request of a node, is constructed by all involved shards. Based on , the requester with enough reputation values is allowed to join the shard, and its reputation values cannot be reused in other shards. Furthermore, transactions of the requester can be updated to the graph, and the requester propagates gossip information first. Once the requester is allowed to join the shard, its updated transactions can be used directly, and previous virtual voting is counted in hashgraph consensus. Hence, the requester can participate in activities of the shard without waiting.
- The combination of shard recovery and reconfiguration based on node state is proposed to prevent targeted attacks. Based on node state changes and , a compromised shard can be determined by other shards and then is recovered. When node states are changed frequently in the shard, the shard is reconfigured dynamically and adaptively.
2. Related Works
2.1. Sharding-Enabled Blockchain
2.2. MANET-Based Blockchain
3. Preliminary
4. Behavior-Based Sharding Hashgraph Framework
4.1. System Model
4.2. Network Model
4.3. Security Problem
- Sybil attack. A malicious node intends to create multiple identities to participate in shards, or an identity is used in multiple shards. Intuitively, only when the identity is validated by multiple shards is the node allowed to join a shard. Nevertheless, under unstable communications among shards, high transmission delay makes the node spend a long time waiting for identity authentication.
- Targeted attack. Malicious nodes intend to control a specified shard by compromising honest nodes or joining the shard. When the number of malicious nodes exceeds the fault tolerance of the shard, it is corrupted. Intuitively, the reconfiguration of shards in a small epoch can alleviate the targeted attack. Nevertheless, it results in the frequent interruption of services during shard reconfiguration, reducing the performance of the system.
5. Asynchronous Intra-Sharding and Inter-Sharding Consensus
5.1. Principle of Tree-Assisted Inter-Sharding Consensus
- A cross-shard transaction is generated and updated to the graph of the local shard and sent to involved shards.
- Transactions related to the cross-shard transaction are generated and updated by involved shards in parallel. They refer to the cross-shard transaction and are sent to other involved shards, constructing the tree globally.
- When the cross-shard transaction is used, the number of child nodes of the cross-shard transaction and their validity are checked. Only if the cross-shard transaction is validated by all involved shards is it confirmed. Otherwise, if a given time is expired, the cross-shard transaction is revoked by a newly updated transaction, and the event containing the cross-shard transaction is determined to be a False Event and added into the blacklist.
5.2. Work Process of a Dynamic Shard
| Algorithm 1 is verified in an involved shard. |
| Input: , the graph in the involved shard |
| Output: or False |
| 1: if the signature of the requester is valid && there is a latest cross-shard joined transaction before a latest cross-shard exited transaction of the requester then |
| 2: Get && |
| 3: Retrieve the set of requester’s cross-shard joined transactions, , and set of requester’s cross-shard existed transactions, , from local graph |
| 4: if then |
| 5: for each in do |
| 6: Get an element which from |
| 7: Get an element which from |
| 8: if not exist || || || || is wrong then return False |
| 9: Generate |
| 10: else return False |
| 11: else return False |
| Algorithm 2 is verified in . |
| Input: |
| Output: , or () |
| 1: Get the root of , |
| 2: Get children of in , |
| 3: Retrieve IDs of involved shards from |
| 4: if then |
| 5: Sequence elements in according to and as the previous one of |
| 6: for Each in in ascending order do |
| 7: |
| 8: |
| 9: if then return |
| 10: if a given time is expired then |
| 11: Generate |
| 12: Generate with as the public key of the request according to (3) |
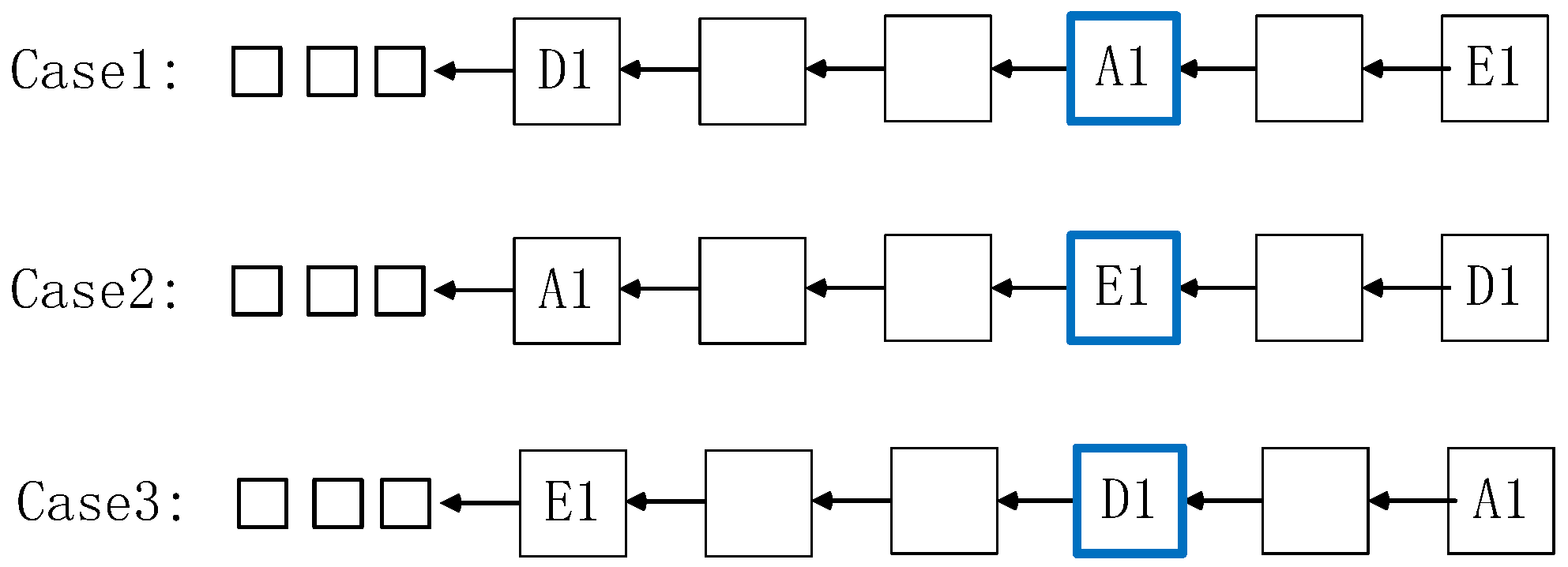
6. Shard Recovery and Reconfiguration
| Algorithm 3 Recovery of Shard A by shard D and E. |
| Input: s, , |
| Output: Recovery of Shard A |
| For a node within shard A |
| 1: The node sends to shard D and E to accuse shard A of being corrupted |
| For shards A, D and E |
| 2: According to s, the lastest trusted block, , is confirmed through the majority principle |
| For both shards D and E |
| 3: if is agreed by shard A then |
| 4: Calculate the reputation value of shard A, , according to (9) |
| 5: if then |
| 6: Verify transactions after in |
| 7: if any false transaction found in then |
| 8: Shard A is reconfigured |
| 9: is the latest block of the chain in shard A |
| 10: else |
| 11: Shard A is reconfigured |
| 12: is the latest block of the chain in shard A |
7. Performance Evaluation
7.1. Security Analysis
- Sybil attack
- Targeted attack
- Accountability
- Adaptability
- Decentralization
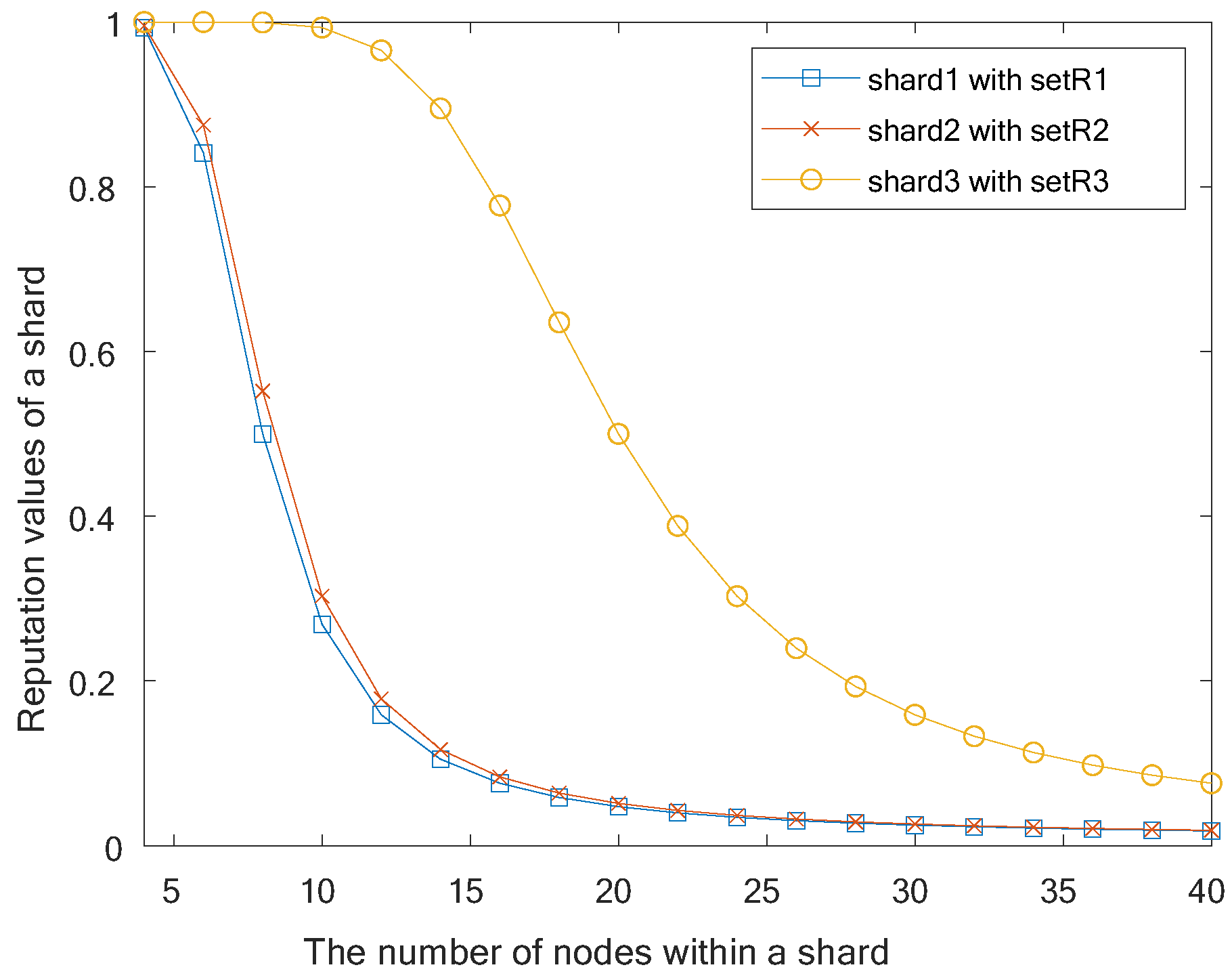
7.2. Experimental Evaluation
7.2.1. Experimental Setting
7.2.2. Experimental Results
- Intra-sharding consensus
- Inter-sharding consensus
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Salman, T.; Zolanvari, M.; Erbad, A.; Jain, R.; Samaka, M. Security services using blockchains: A state of the art survey. IEEE Commun. Surv. Tutor. 2018, 21, 858–880. [Google Scholar]
- Kang, J.; Yu, R.; Huang, X.; Wu, M.; Maharjan, S.; Xie, S.; Zhang, Y. Blockchain for secure and efficient data sharing in vehicular edge computing and networks. IEEE Internet Things J. 2018, 6, 4660–4670. [Google Scholar]
- Sharma, V.; You, I.; Jayakody, D.N.K.; Reina, D.G.; Choo, K.K.R. Neural-blockchain-based ultrareliable caching for edge-enabled UAV networks. IEEE Trans. Ind. Inform. 2019, 15, 5723–5736. [Google Scholar]
- Feng, W.; Yan, Z. MCS-Chain: Decentralized and trustworthy mobile crowdsourcing based on blockchain. Future Gener. Comput. Syst. 2019, 95, 649–666. [Google Scholar]
- Bruzgiene, R.; Narbutaite, L.; Adomkus, T. MANET network in internet of things system. Ad Hoc Netw. 2017, 66, 89–114. [Google Scholar]
- Morales, D.C.; Velloso, P.; Guerre, A.; Nguyen, T.M.T.; Pujolle, G.; Alagha, K.; Dua, G. Blockgraph proof-of-concept. In Proceedings of the SIGCOMM’21 Poster and Demo Sessions, Virtual Event, 23–27 August 2021; pp. 82–84. [Google Scholar]
- Zhou, S.; Zhang, G.; Meng, X. LocTrust: A local and global consensus-combined trust model in MANETs. Peer-to-Peer Netw. Appl. 2022, 15, 355–368. [Google Scholar] [CrossRef]
- Lwin, M.T.; Yim, J.; Ko, Y.B. Blockchain-based lightweight trust management in mobile ad-hoc networks. Sensors 2020, 20, 698. [Google Scholar] [PubMed] [Green Version]
- Ilbeigi, M.; Morteza, A.; Ehsani, R. An infrastructure-less emergency communication system: A blockchain-based framework. J. Comput. Civ. Eng. 2022, 36, 04021041. [Google Scholar]
- Liu, G.; Dong, H.; Yan, Z.; Zhou, X.; Shimizu, S. B4SDC: A blockchain system for security data collection in MANETs. IEEE Trans. Big Data 2020, 8, 739–752. [Google Scholar]
- Rasool, S.; Iqbal, M.; Dagiuklas, T.; Ul-Qayyum, Z.; Li, S. Reliable data analysis through blockchain based crowdsourcing in mobile ad-hoc cloud. Mob. Netw. Appl. 2020, 25, 153–163. [Google Scholar]
- Jiao, Z.; Zhang, B.; Zhang, L.; Liu, M.; Gong, W.; Li, C. A blockchain-based computing architecture for mobile ad hoc cloud. IEEE Netw. 2020, 34, 140–149. [Google Scholar]
- Luo, J.; Shu, X.; Zhai, Y.; Fu, X.; Ding, B.; Xu, J. A Fast and Robust Solution for Common Knowledge Formation in Decentralized Swarm Robots. J. Intell. Robot. Syst. 2022, 106, 68. [Google Scholar]
- Chatzopoulos, D.; Gujar, S.; Faltings, B.; Hui, P. Localcoin: An ad-hoc payment scheme for areas with high connectivity: Poster. In Proceedings of the 17th ACM International Symposium on Mobile Ad Hoc Networking and Computing, Paderborn, Germany, 5–8 July 2016; pp. 365–366. [Google Scholar]
- Long, T.; Qu, S.; Li, Q.; Kang, H.; Fu, L.; Wang, X.; Zhou, C. Efficient block propagation in wireless blockchain networks and its application in Bitcoin. IEEE Trans. Netw. Sci. Eng. 2021, 8, 3349–3368. [Google Scholar]
- Baird, L.; Harmon, M.; Madsen, P. Hedera: A public hashgraph network & governing council. White Pap. 2019, 1, 9–10. [Google Scholar]
- Castro, M.; Liskov, B. Practical byzantine fault tolerance. In Proceedings of the OsDI, New Orleans, LA, USA, 22–25 February 1999; Volume 99, pp. 173–186. [Google Scholar]
- Ongaro, D.; Ousterhout, J. The raft consensus algorithm. Lect. Notes CS 2015, 190, 2022. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. SSRN. 2008. Available online: https://ssrn.com/abstract=3440802 (accessed on 10 January 2023).
- Li, L.; Huang, D.; Zhang, C. An Efficient DAG Blockchain Architecture for IoT. IEEE Internet Things J. 2022, 10, 1286–1296. [Google Scholar]
- Hong, Z.; Guo, S.; Li, P. Scaling Blockchain via Layered Sharding. IEEE J. Sel. Areas Commun. 2022, 40, 3575–3588. [Google Scholar]
- Huang, H.; Peng, X.; Zhan, J.; Zhang, S.; Lin, Y.; Zheng, Z.; Guo, S. Brokerchain: A cross-shard blockchain protocol for account/balance-based state sharding. In Proceedings of the IEEE INFOCOM 2022-IEEE Conference on Computer Communications, Online, 2–5 May 2022; pp. 1968–1977. [Google Scholar]
- Zhang, X.; Xia, W.; Cui, Q.; Tao, X.; Liu, R.P. Efficient and Trusted Data Sharing in a Sharding-enabled Vehicular Blockchain. IEEE Netw. 2022; early access. [Google Scholar]
- Wang, Y.; Yuan, L.; Jiao, W.; Qiang, Y.; Zhao, J.; Yang, Q.; Li, K. A Fast and Secured Vehicle-to-Vehicle Energy Trading Based on Blockchain Consensus in the Internet of Electric Vehicles. IEEE Trans. Veh. Technol. 2023, 72, 7827–7843. [Google Scholar]
- Benchi, A.; Launay, P.; Guidec, F. Solving consensus in opportunistic networks. In Proceedings of the 16th International Conference on Distributed Computing and Networking, Goa, India, 4–7 January 2015; pp. 1–10. [Google Scholar]
- Luu, L.; Narayanan, V.; Zheng, C.; Baweja, K.; Gilbert, S.; Saxena, P. A secure sharding protocol for open blockchains. In Proceedings of the 2016 ACM SIGSAC conference on computer and communications security, Vienna, Austria, 24–28 October 2016; pp. 17–30. [Google Scholar]
- Wang, J.; Wang, H. Monoxide: Scale out Blockchains with Asynchronous Consensus Zones. In Proceedings of the NSDI, Boston, MA, USA, 26–28 February 2019; Volume 2019, pp. 95–112. [Google Scholar]
- Amiri, M.J.; Agrawal, D.; El Abbadi, A. Sharper: Sharding permissioned blockchains over network clusters. In Proceedings of the 2021 International Conference on Management of Data, Xi’an, China, 20–25 June 2021; pp. 76–88. [Google Scholar]
- Huang, C.; Wang, Z.; Chen, H.; Hu, Q.; Zhang, Q.; Wang, W.; Guan, X. Repchain: A reputation-based secure, fast, and high incentive blockchain system via sharding. IEEE Internet Things J. 2020, 8, 4291–4304. [Google Scholar]
- Wang, L.e.; Bai, Y.; Jiang, Q.; Leung, V.C.; Cai, W.; Li, X. Beh-Raft-Chain: A behavior-based fast blockchain protocol for complex networks. IEEE Trans. Netw. Sci. Eng. 2020, 8, 1154–1166. [Google Scholar]
- Yun, J.; Goh, Y.; Chung, J.M. DQN-based optimization framework for secure sharded blockchain systems. IEEE Internet Things J. 2020, 8, 708–722. [Google Scholar]
- Zhang, M.; Li, J.; Chen, Z.; Chen, H.; Deng, X. An efficient and robust committee structure for sharding blockchain. IEEE Trans. Cloud Comput. 2022; early access. [Google Scholar]
- Gao, N.; Huo, R.; Wang, S.; Huang, T.; Liu, Y. Sharding-Hashgraph: A High-Performance Blockchain-Based Framework for Industrial Internet of Things with Hashgraph Mechanism. IEEE Internet Things J. 2021, 9, 17070–17079. [Google Scholar]
- Asheralieva, A.; Niyato, D. Reputation-based coalition formation for secure self-organized and scalable sharding in iot blockchains with mobile-edge computing. IEEE Internet Things J. 2020, 7, 11830–11850. [Google Scholar]
- Zhang, X.; Xia, W.; Wang, X.; Liu, J.; Cui, Q.; Tao, X.; Liu, R.P. The block propagation in blockchain-based vehicular networks. IEEE Internet Things J. 2021, 9, 8001–8011. [Google Scholar]
- Morales, D.C.; Velloso, P.B.; Laubé, A.; Nguyen, T.M.T.; Pujolle, G. A performance evaluation of C4M consensus algorithm. Ann. Telecommun. 2023, 78, 169–182. [Google Scholar]
- Fu, X.; Wang, H.; Shi, P.; Zhang, X. Teegraph: A Blockchain consensus algorithm based on TEE and DAG for data sharing in IoT. J. Syst. Archit. 2022, 122, 102344. [Google Scholar]
- OPNET Network Simulator. Available online: http://opnetprojects.com/opnet-network-simulator/ (accessed on 10 January 2023).









| Recent events | , | , | , |
| Past events | , | , | , |
| Consensus Scheme | Consistency | Leader-Based | Fault Tolerance | Neighbors Selection for Events Propagationn |
|---|---|---|---|---|
| PBFT | Strong | Leader | less than of all nodes | Random |
| traditional hashgraph | Eventual | Leaderless | less than of all nodes | Random |
| Zhang et al. [23] | Eventual | Leader | less than of all nodes | Random |
| Wang et al. [24] | Eventual | Leader | less than | Random |
| our scheme | Eventual | Leaderless | less than of all nodes | Selective |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lai, R.; Zhao, G.; He, Y.; Hou, Z. A Robust Sharding-Enabled Blockchain with Efficient Hashgraph Mechanism for MANETs. Appl. Sci. 2023, 13, 8726. https://doi.org/10.3390/app13158726
Lai R, Zhao G, He Y, Hou Z. A Robust Sharding-Enabled Blockchain with Efficient Hashgraph Mechanism for MANETs. Applied Sciences. 2023; 13(15):8726. https://doi.org/10.3390/app13158726
Chicago/Turabian StyleLai, Ruilin, Gansen Zhao, Yale He, and Zhihao Hou. 2023. "A Robust Sharding-Enabled Blockchain with Efficient Hashgraph Mechanism for MANETs" Applied Sciences 13, no. 15: 8726. https://doi.org/10.3390/app13158726
APA StyleLai, R., Zhao, G., He, Y., & Hou, Z. (2023). A Robust Sharding-Enabled Blockchain with Efficient Hashgraph Mechanism for MANETs. Applied Sciences, 13(15), 8726. https://doi.org/10.3390/app13158726





