Abstract
To address the quantum attacks on number theory-based ciphertext policy attribute-based encryption (CP-ABE), and to avoid private key leakage problems by relying on a trustworthy central authority, we propose a lattice-inspired CP-ABE scheme for data access and sharing based on blockchain in this paper. Firstly, a CP-ABE-based algorithm using learning with errors (LWE) assumption is constructed, which is selective security under linear independence restriction in the random oracle model. Secondly, the blockchain nodes can act as a distributed key management server to offer control over master keys used to generate private keys for different data users that reflect their attributes through launching transactions on the blockchain system. Finally, we develop smart contracts for proving the correctness of proxy re-encryption (PRE) and provide auditability for the whole data-sharing process. Compared with the traditional CP-ABE algorithm, the post-quantum CP-ABE algorithm can significantly improve the computation speed according to the result of the functional and experimental analysis. Moreover, the proposed blockchain-based CP-ABE scheme provides not only multi-cryptography collaboration to enhance the security of data access and sharing but also reduces average transaction response time and throughput.
1. Introduction
With the increasing popularity of blockchain technology, blockchain has been widely used in data access and sharing in weak-trusted or no-trusted networks. However, privacy data protection on the blockchain has become a challenge due to the characteristics of “non-tampering” and “open and transparent”. In recent years, many scholars have put forward some new solutions for privacy protection and data sharing on the blockchain [1,2,3,4,5,6], among which attribute-based encryption algorithm has been widely used in various schemes on the blockchain, such as in data traceability [1], cloud storage [7], medical data sharing [8,9], power systems [10] and Internet of Things [11] due to its advantages of “one-to-many” encryption, fine-grained access control and so on.
The attribute-based encryption (ABE) originated from the fuzzy identity-based encryption [12] proposed by Sahai and Waters in 2005 and then developed into ABE. In key policy attribute-based encryption [13] (KP-ABE), the ciphertext is associated with the attribute and the key with the access policy. However, in ciphertext policy attribute-based encryption (CP-ABE), the key is associated with the attribute and the ciphertext with the access policy. The CP-ABE allows the data owner to freely formulate the access control policy and is more suitable for the distributed storage environment and uncertain deciphering [14]. In recent years, the main research on the ABE mainly focused on computation efficiency [15,16], access policy and attribute hiding [17], and identity management [18,19]. In 2007, Bethencourt et al. [20] proposed a system for the CP-ABE algorithm which allows policies to be expressed as any monotonic tree access structure and is resistant to collusion attacks in which an attacker might obtain multiple private keys. In addition, the “one-to-many” encryption and fine-grained access control could be achieved this way. However, it is proved secure under the generic group heuristic. In 2011, Waters [21] proved the security of the CP-ABE under the standard model and put forward a CP-ABE adopting the linear secret sharing scheme, which improved the efficiency significantly. In 2012, Okamoto [22] et al. proposed the first unbounded inner product ABE scheme, which lifted the restrictions on the predicate terms and size attributes of the previous ABE scheme. In 2013, Gorbunov [23] proposed an ABE scheme based on the polynomial logic circuit. This scheme was designed to resist collusion attacks effectively, and its public parameter and ciphertext size increased linearly with the circuit depth. This scheme made it possible to transform from Boolean formula-based to circuit-based, which had better security by nature. In 2014, Waters [24] proposed an Online-Offline ABE scheme to address the computational bottleneck of encryption and key generation. This scheme was inspired by the ABE scheme put forward by Rouselakis et al. [25], and developed new techniques for ABE that split the computation for encryption into two phases, thus reducing the computation consumption in the online stage.
Recently, the blockchain-enhanced CP-ABE scheme using elliptic curve cryptography (ECC) has become a popular research area due to its potential to provide secure data access and sharing without involving a third party. In 2020, Yuwen Pu [26] presented a privacy-preserving, recoverable, and revocable edge data-sharing scheme based on blockchain technology to achieve attribute revocation in ciphertext-policy attribute-based encryption (CP-ABE), which can protect user’s privacy and resist many attacks. Sheng Gao [27] proposed a new trustworthy, secure ciphertext policy and attribute hiding access control scheme based on blockchain to achieve trustworthy access while guaranteeing the privacy of policy and attribute. Meanwhile, Xuanmei Qin [28] proposed a scheme that manages each attribute across different domains, eliminates the single-point bottleneck of the existing multi-authority blockchain-based CP-ABE schemes, and reduces computation and communication overhead between the user and the multiple attribute authorities. In 2022, Guofeng Zhang [29] proposed a secure and trusted agricultural product traceability system (BCST-APTS) supported by blockchain and CP-ABE encryption technology, thereby ensuring the efficient sharing and supervision of data stored in the Permissioned Blockchain.
However, most of the aforementioned works based their security on cryptographic assumptions related to bilinear maps. It is very natural to seek for solutions to the known attacks on group-based constructions by quantum computers. To address the threat of quantum computing, lattice-based cryptography is a promising approach that provides a new set of assumptions based on finding short vectors in lattices and is believed to be hard for quantum computers. Additionally, new cryptographic protocols have been proposed which rely on the hardness of solving certain lattice problems, including Learning with Errors (LWE). These protocols are expected to provide strong protection against the attacks of quantum computers. At present, lattice-difficulty problems that are provably secure mainly consist of small integer solution problems (SIS) and learning with errors problems (LWE). These two difficult problems are as hard as approximate lattice problems from the worst case to the average case reduction. Recently, several lattice-based encryption schemes have been proposed consecutively, which mainly focus on identity-based encryption [30,31,32] digital signature [33], and zero-knowledge proof [34]. In May 2021, Datta et al. [35] constructed an ABE algorithm based on ciphertext policy according to the LWE-difficulty problem and realized a CP-ABE scheme that could resist quantum attacks.
In addition, for a comprehensive analysis of our security measures, we considered the potential impacts of active and passive side-channel attacks (SCA), fault attacks, and power analysis attacks [36]. We recognize the increasing importance of Post-Quantum Cryptography (PQC) in secure applications, such as smartphones and blockchain systems, as it replaces traditional ECC/RSA algorithms. Therefore, we studied relevant literature [37,38,39]. Furthermore, we acknowledged the significance of NIST lightweight standardization and considered fault attacks as a consideration for side-channel attacks, referring to the research work of Mozaffari-Kermani et al. [40,41,42] in this field.
The contributions of this scheme are as follows:
(a) Form the LWE-CPABE algorithm suitable for blockchain to resist the quantum attacks, improve the CP-ABE scheme proposed by Datta, design the CP-ABE algorithm supporting policy update, and realize the dynamic access control of the data;
(b) Use a threshold proxy re-encryption scheme following a key encapsulation mechanism (KEM) approach to implement distributed key management for the LWE-CPABE algorithm, design the transaction generation algorithm and transaction verification contract, and realize the correctness and integrity verification of the intra-transaction data and the outsourcing storage data;
(c) Carry out the security analysis and simulation experiment, and the results show that this scheme is secure and efficient and is suitable for distributed data sharing and access control.
2. Preliminaries
2.1. Notations
In this paper, we use the following notations and conventions. The security parameter is denoted by λ. A function is considered negligible if it decreases faster than any inverse-polynomial function. Formally, for every constant , there exists an integer such that for all , where is the negligible function.
The abbreviation PPT represents probabilistic polynomial-time algorithms. When sampling from a distribution , we use to denote the random value sampled from the distribution. For a set X, the notation x X indicates that x is sampled uniformly from the elements of set X. Bold lowercase letters, such as , represent vectors, while bold uppercase letters, such as , represent matrices. By default, all vectors in this paper are assumed to be row vectors. In the context of matrices, the -th row is denoted as , and represents the submatrix of composed of all rows indexed by , where is a set of row indexes. For a vector , we use to denote its -norm, and represents the -norm of the vector.
For an integer , we let denote the ring of integers modulo . We use to represent integers in the range .
2.2. B-Bounded
For a family of distributions over the integers and there is a boundary . If we denote that is -bounded for every , it holds that:
Lemma 1.
Let and be positive, and let be a B-bounded distribution family of . We let denote the uniform distribution over . If there is a negligible function such that for all it holds that:
and then the distribution family and are statistically indistinguishable.
2.3. Leftover Hash Lemma
Lemma 2.
(leftover hash lemma) Let , , , and we donte as some polynomial. Then, the following two distributions are statistically indistinguishable:
2.4. Lattice
Here, we briefly describe the necessary background on lattices. A lattice is defined as the discrete addition subgroup with the dimension being in , assuming the positive integers , , and the matrix , and let represent the lattice . For , we let denote as the coset .
2.4.1. Discrete Gaussians
Let be any positive real number. Generating a Gaussian distribution is defined by the probability distribution function (PDF) . For any discrete set , we define . The discrete Gaussian distribution over the lattice with the parameter is defined by PDF :
Lemma 3.
If the parameter of discrete Gaussian distribution is small, then any vector extracted from this distribution will possibly be short.
Lemma 4.
Let m,n,q denote as the positive integers that satisfy and . We define a matrix with parameter and . Then, there is a negligible function such that:
where is the norm of x.
2.4.2. Truncated Discrete Gaussians
The truncated discrete Gaussian distribution with the parameter over is the same as the discrete Gaussian distribution . Expect that it outputs 0 when the norm is larger than . In addition, according to Lemma 1, and are statistically indistinguishable.
2.4.3. Lattice Trapdoors
Lattices with trapdoors function have certain “trapdoors” that allow efficient solutions to hard lattice problems. A trapdoor lattice consists of the following two algorithms:
- ➀
- : The lattice generation algorithm is a randomized algorithm. It takes as input the dimensions n,m and modulus of the matrix and output a matrix together with a lattice trapdoors function .
- ➁
- : The pre-sampling algorithm takes a matrix , the lattice trapdoors function , a vector , and a parameter as the inputs. And it outputs the vector , which the vector satisfies .
2.5. Learning with Errors (LWE)
For a security parameter , assuming that , and are the function of . We define as the hypothesis of the LWE-hardness problem by parametric , and . For any PPT adversary , there exists a negligible function for any :
where the Oracles and are defined as follows:
is strongly connected with , and it chooses and , and outputs in each query. on each query it chooses and , and outputs .
Definition 1.
If there is a hypothesis that a PPT adversary can break the LWE assumption, then there exists a PPT quantum algorithm that can solve some hard lattice problems in the worst case.
Given the current technical schemes on the hard lattice problems, the LWE assumption is believed to be true for any polynomial and function when all , , , and satisfy the following conditions:
3. LWE-CP-ABE Scheme
3.1. Algorithm Construction
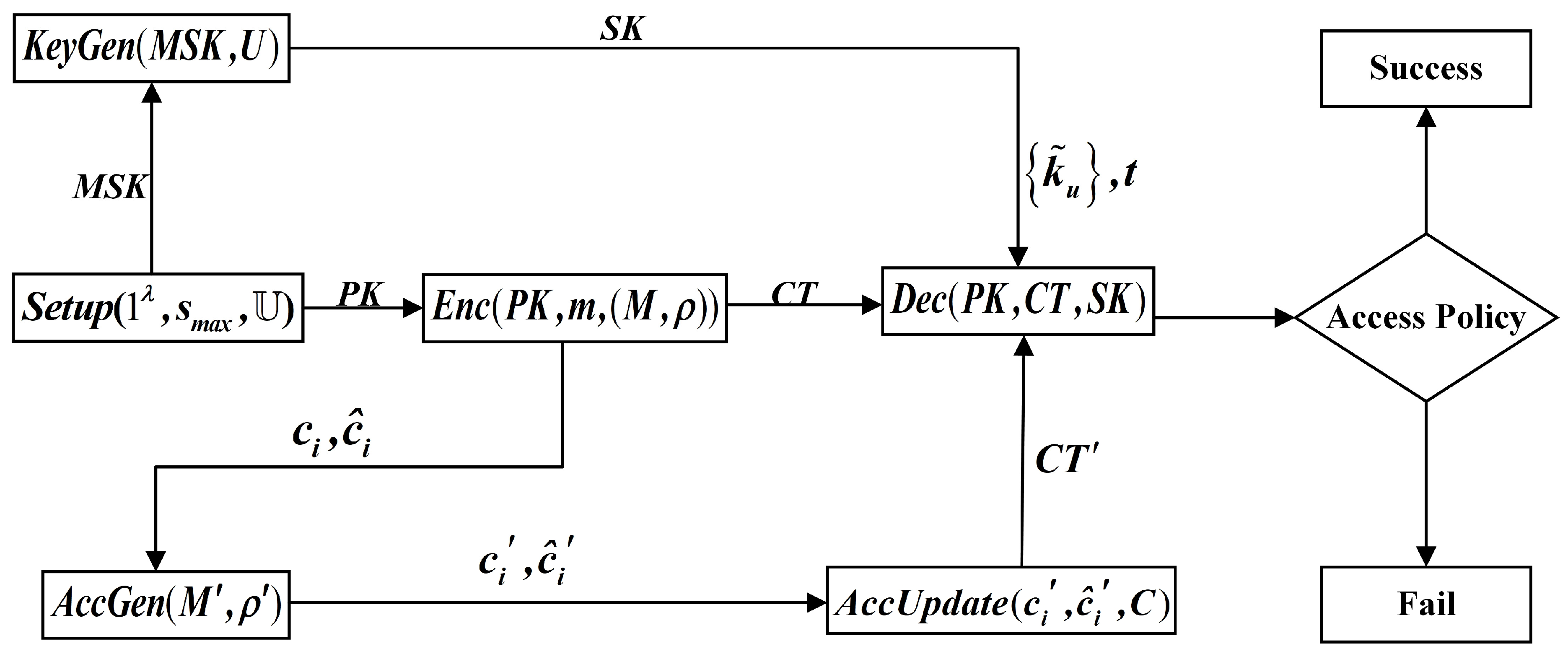
In this section, we present the LWE-CP-ABE scheme for access structures with LSSS using blockchain technology, which is associated with Proxy Re-Encryption (PRE) protocol under a subset of on-chain node client by transforming encrypted data from one public key to another. As shown in Figure 1, our CP-ABE system under LWE assumption LWE – CP − ABE = (Setup, KeyGen, Enc, Dec, AccGen, AccUpdate) mainly consists of six procedures with the following syntax:
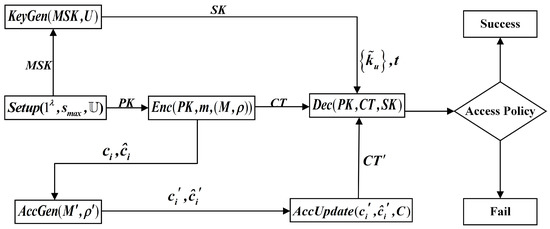
Figure 1.
Flowchart of LWE-CPABE.
(1)
The setup algorithm takes as input the security parameter , the maximum width supported by an LSSS matrix supported by the scheme, and the attribute universe .
For each attribute u in the system, it selects to generate the trapdoors function , and selects the uniformly distributed random matrix and random vector . It outputs the system’s public parameters and the master secret key.
(2)
The key generation algorithm takes as input the user’s attribute set U and MSK. We let a vector and set the vector , The vector is a part of the user attribute SK, and every user has a different , which can prevent conspiracy attacks. For each attribute , a short vector is generated by the trapdoors and satisfies . Finally, it outputs:
(3)
The encryption algorithm takes as input the public parameter PK, a message bit and access policy from LSSS. Let be the mapping function that maps the attribute to the row of the matrix M. that is, is the attribute associated with the row in the matrix . The procedure Randomly samples vectors , and , and then it computes as follows:
and it outputs:
(4)
The decryption algorithm takes as inputs the PK, the ciphertext CT generated with respect to an LSSS, and the user secret key SK related to some subset of attributes U. Let the attribute owned by the user meet the access control policy. We denote as the row vector set corresponding to the attribute and the reconstruction coefficient. For any , let be the row-relevant attribute. The algorithm computes:
and outputs:
(6) .
The ciphertext policy generation algorithm takes as input the new access control policy and outputs the updated policy ciphertext.
(7) .
The ciphertext policy update algorithm takes the policy ciphertext generated by the policy generation algorithm as the input and outputs the new ciphertext .
3.2. Security Model
The proposed CP-ABE scheme is selectively secure under linear independence restriction in the random oracle model if the LWE assumption holds. To prove this assumption, the hybrid security game contains a challenger and an adversary. The challenger simulates the system and answers the adversary’s inquiries. The hybrid game starts as follows.
(1) Setup phase. The reduction algorithm receives a security parameter and an access control policy from the challenger and invokes an adversary. The challenger runs the algorithm to generate the system PK and send it to the adversary.
(2) Secret key queried by an adversary. For each key query, the adversary sends a set of attributes , but these attributes do not satisfy the access control policy . The challenger runs the algorithm and sends the generated user attribute SK to the adversary.
(3) Challenge phase. To generate the challenge ciphertext, the challenger selects a random bit and runs the ENC algorithm to encrypt it using the access control policy. Consequently, the challenger provides that to the adversary.
(4) Repeat step (2).
(5) Guess phase. The hybrid game terminates with an adversary outputting its guess for the bit b encrypted within the challenge ciphertext.
The advantage of the adversary in this game is:
Definition 2.
If there exists a negligible function for any PPT adversary , for all , there is . The LWE-CP-ABE scheme proposed in this paper is selectively secure under linear independence restriction.
4. Blockchain-Based LWE-CP-ABE Data Sharing Scheme
4.1. Overview of Blockchain-Based LWE-CP-ABE
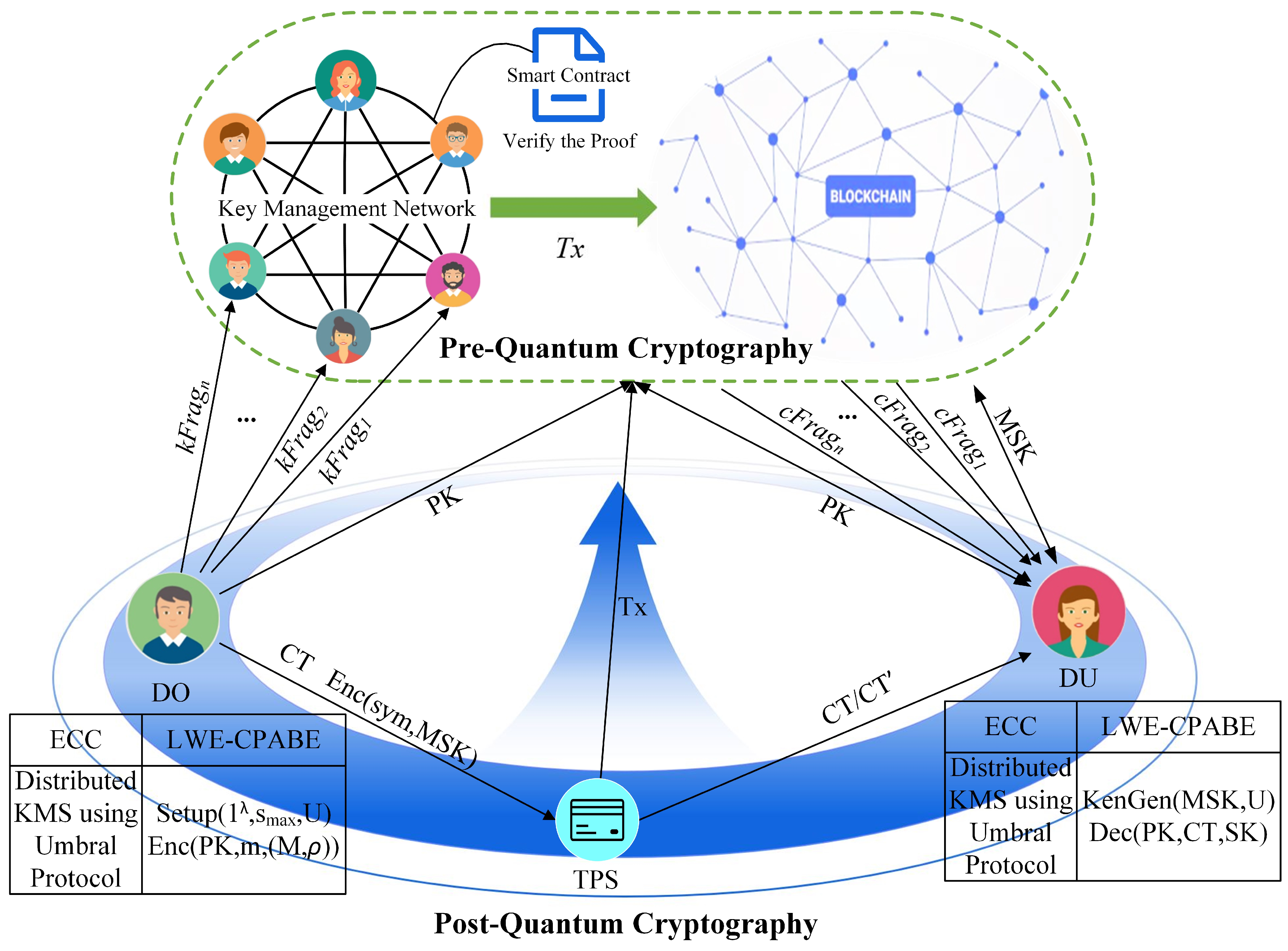
To ensure efficient data sharing and access policy updating on the blockchain, all activities of the ciphertext access control scheme, such as generating the public parameters, secret keys, and oracle functions, are written into the distributed ledger on blockchain. Users can access the authorized data through their user attribute secret key controlled over the blockchain, which matches their attributes, and complete the secure and traceable data sharing. The blockchain-based data-sharing framework of the LWE-CP-ABE is shown in Figure 2. Here, the blockchain system is built with pre-quantum cryptography for master key management and immutable storage of transactions, and CP-ABE is constructed with post-quantum cryptography for access and sharing of ciphertext. The system characters play particular roles described as follows:
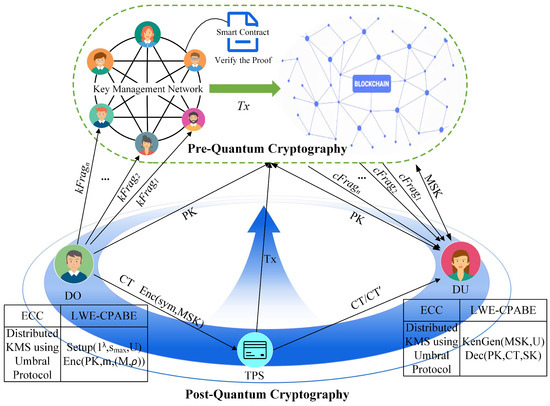
Figure 2.
System architecture.
(1) User (DO, DU). It includes the data owner (DO) and the data user (DU).
When a DO wants to share this information with DU, they can create a policy with the LSSS matrix to grant access to DU. Thus DO generates the global parameters, encrypts the corresponding message, and uploads the transactions to the blockchain.
At the same time, if different DUs want to access the data, they must request the secret keys from the nodes on the blockchain. The DUs use it to decrypt the ciphertext obtained from the third-party storage;
(2) Third-party storage (TPS). It provides API storage services for encrypted data, such as distributed file-sharing network IPFS, and its hash addresses are stored on the blockchain;
(3) Blockchain Network (BN). It comprises a participant node on the blockchain that stands ready to provide decentralized key management services and creates a symmetric key for the master secret key of CP-ABE for the data users. Additionally, the blockchain system provides traceability and auditability of transactions involved in the LWE-CP-ABE access control protocol;
(4) Key Management Network (KMN). A group of blockchain nodes that provides an application of the Proxy Re-Encryption (PRE) scheme ensuring the security of the master secret key distribution in the LWE-CPABE encryption algorithm.
4.2. Data Sharing Scheme in Key Management Network and Blockchain Network
In our LWE-CP-ABE approach based on blockchain for data access and sharing, it is essential that DU can securely acquire the master secret key MSK without needing to involve a central authority or trusted third party. Thus, we introduce the PRE algorithm with ECC applied in the blockchain network, which acts as a decentralized key management service to carry out the master key distribution for data users. To grant the MSK to DU, DO creates a random symmetric key, encrypts the MSK for DUs, and each node is responsible for securely storing and managing the re-encryption keys or the key shares. DU must collect the fragments until he obtains a threshold, t, number of fragments to re-constructed and decrypt the ciphertext at the DU side. The mathematical details of the LWE-CP-ABE protocol running in KMN and BN are described as follows.
In the LWE-CP-ABE scheme, the algorithms select the parameters and the noise distributions , , , . For any , the notation represents the uniform distribution .
(1) System setup. The DO selects the security parameter encoded in unary, the maximum width supported by the LSSS matrix, and the user attribute set associated with the system. The algorithm (Algorithm 1) generates the public key PK and the master secret key MSK.
| Algorithm 1: Setup |
|
Input: the security parameter , the maximum width of an LSSS matrix, and the user attribute set supported by the system; Output: the PK and the MSK,
|
The DO sends the transaction and uploads the PK on the blockchain BN. Specifically, all the public information is recorded in the block through the transaction TxUploadPK = {DO, BN, A, P, Timestamp, PK, SigDO, $Coin}, where A is the LSSS matrix of access control policy, and P represents the operation of a publishing contract, Timestamp is the time stamp of the transaction, SigDO is the signature of DO, and $Coin is the payment for transaction fee.
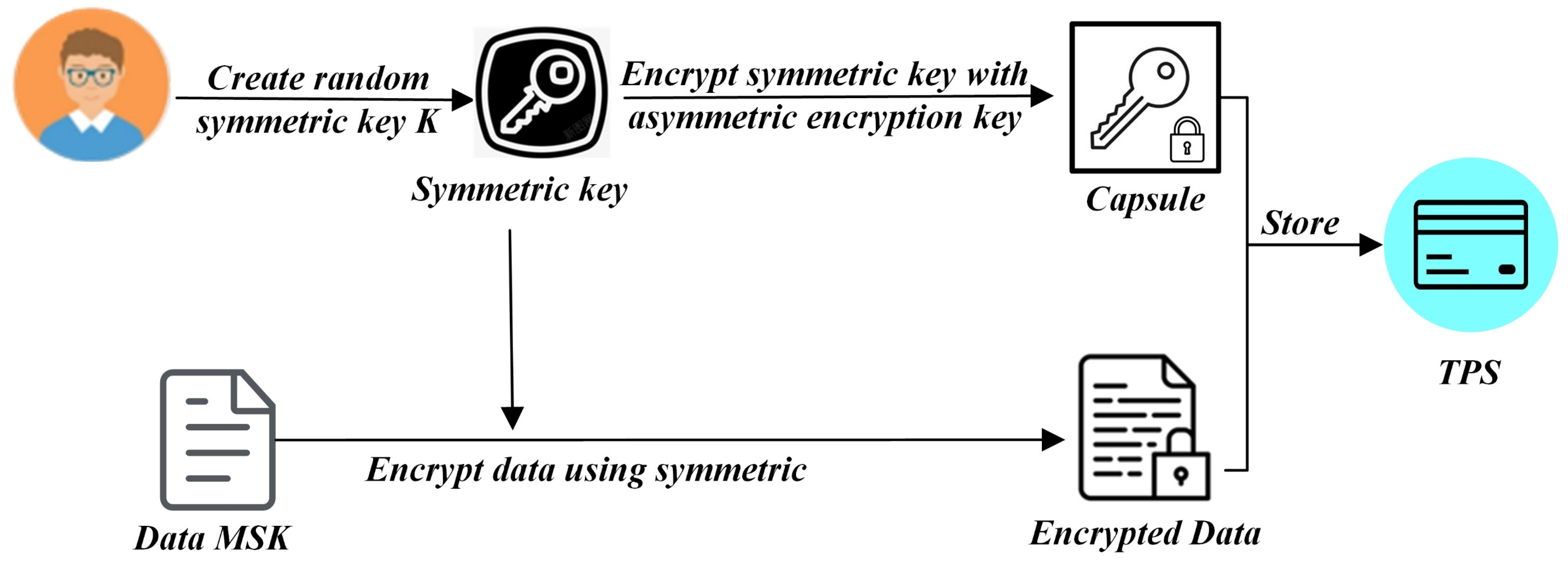
In addition, DO has the MSK they want to share with the DUs. DO can create a PRE protocol running on the nodes of KMN to grant access to DUs. Therefore, the KMN system still uses pre-quantum cryptography with a cyclic group of prime order q. Let be the generator. Then, DO generates a pair of public and secret keys in the blockchain system. That is, sample uniformly at random, computes and outputs the key pair (pk, sk) = (). The re-encryption key generation algorithm takes as input the DO’s secret key a, the DU’s public key, , several fragments N, and a threshold t, DO computes N fragments of the re-encryption key between DO and DU, each of them named kFrag. In this step, an ephemeral symmetric key generated by DO is used to encrypt the MSK, and the symmetric key is encrypted using DO’s asymmetric encryption key. The encrypted MSK and the encrypted symmetric key (the KEM portion, called a capsule) are stored together in TPS. Next, as shown in Figure 3, to gain the MSK, DU requests the capsule-associated key fragments kFrag to give to the KMN for re-encryption operation. Those n designated nodes in KMN perform a partial operation to produce a corresponding ciphertext fragment named cFrag. Meanwhile, a correctness proof for the resulting fragment is constructed using a non-interactive zero-knowledge proof of discrete logarithm equality to verify the correctness. These fragments are returned to DU, which collects cFrags until it obtains an m-of-n threshold. Finally, DU can decrypt the capsule to obtain the symmetric key K to decrypt the encrypted MSK.
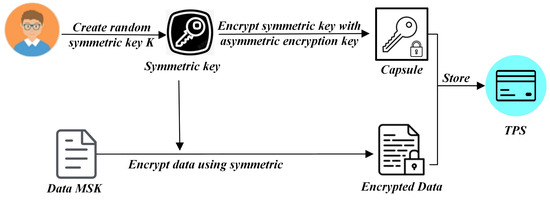
Figure 3.
Proxy Re-Encryption approach for MSK.
Thus, to keep this paper compact, all above mentioned PRE protocol that we introduced uses the UMBERAL scheme [43] and is served as a decentralized key management system to distribute and manage the MSK that is applied to key generation and decryption for DU of LWE-CP-ABE. Meanwhile, the activities of DO/DU, including authorization, request, and policy making, are written into blockchain by a smart contract.
(2) Data encryption. The DO formulates the access control policy . is the LSSS access control policy, in which , represents the mapping (monomorphism) function , and it maps the access control matrix to the attribute set . After that, the DO runs the algorithm, inputs the PK, the plaintext m, and the access control policy , and gets the CT.
The specific algorithm is shown in Algorithm 2.
| Algorithm 2: Data Encryption Algorithm |
| Input: the PK, the plaintext m, and the access control policy ; Output: the CT.
We have;
|
The DO uploads the CT to the TPS, which generates the contract transaction TxCTAddress = {TPS, BN, A, D, Timestamp, CTAddress, SigTPS, $Coin} to upload the hash address of CT on the blockchain. In this transaction, the parameter D denotes the operation type is a data message.
(3) User attribute secret key generation. Each DU firstly requires m of these interactions with m different nodes to obtain a fully re-encrypted capsule. Secondly, DU combines the fragments to decrypt the re-encrypted capsule using his private key. Finally, DU obtains the symmetric key to decrypt encrypted MSK.
DU inputs the attribute information and the MSK and runs the algorithm to output the user attribute SKGID corresponding to the attribute. The specific algorithm is shown in Algorithm 3.
| Algorithm 3: User Attribute Secret Key Generation Algorithm |
|
Input: the MSK and own attribute information ; Output: the user attribute SK,
Compute then Compute ; Output the user attribute SKGID:
SK = ({ku}u∈U, t)
|
(4) Ciphertext decryption. When DU wants to access the data, he retrieves the ciphertext address from the blockchain BN, searches the corresponding CT from the TPS through the ciphertext address CTAddress and downloads it to the local through the transaction TxDownloadCT = {TPS, DU, D, P, Timestamp, CT, SigTPS, $Coin}, where P denotes the trading type as publishing contract. The DU uses the SK to decrypt the CT and obtain the plaintext.
During the process of ciphertext decryption, the SK corresponds to a certain subset of the attribute set . If is not in the row space of the matrix associated with , then the decryption fails. Otherwise, let be a set of row indexes of the matrix and satisfy . Let and be scalar, where is the row of the matrix . The specific algorithm is shown in Algorithm 4.
| Algorithm 4: Decryption Algorithm |
| Input: the CT and the user attribute SKGID; Output: the plaintext m.
|
(5) Ciphertext policy generation. When the attribute set or access control policy needs to be changed, the DU can update the access control policy of the original ciphertext retention. To update the policy, the DO generates a new access control policy , and runs the algorithm to get the updated policy ciphertext :
At the same time, the DO sends transaction TxAccGen = {DO, TPS, A, N, Timestamp, UpdateCT, SigDO, $Coin} to record the updating operation representing N on the blockchain. The DO store the ciphertext of the access policy on TPS, and its hash value is written in the transaction.
(6) Ciphertext policy update. When DO obtains the ciphertext C derived from the original CT, the updated access control policy ciphertext is used to run the algorithm to generate the new ciphertext , which is still uploaded to the original ciphertext address to facilitate the decryption procedures for data users.
To an extent, the users can quickly and efficiently retrieve the required information using the formatted transaction structure in the blockchain encryption protocol based on the LWE-CP-ABE. Meanwhile, the whole log of each node’s process event is recorded into the ledger on blockchain BN, which can offer better auditability and accountability in the dynamic access control system.
5. Analysis of the Scheme
5.1. Analysis of Correctness
Assuming that a data user has the attributes and the LSSS access control policy for which U constitute an authorized set. By construction,
Expanding and , we get
For each , we run algorithm, and then Therefore, for each , it holds that , Hence,
When for , it holds that . Also, is constructed using in Section 3.1, and hence . Thus,
As for the noise part , the following inequalities hold except with negligible probability.
(1) According to Lemma 2, the positive integer coordinates in are from truncated discrete Gaussians distribution , so there is .
(2) the positive integer coordinates in are from the uniform distribution , so there is .
(3) coordinates in are from the uniform distribution , so there is . And coordinates in are statistically close to the truncated discrete Gaussians distribution , so there is . To sum up, for , , so the boundary on is .
(4) if , where comes from a truncated discrete Gaussians distribution , then it holds .
Therefore, given the above conditions, we have that:
Therefore, with almost negligible probability in , the MSB of syT is not affected by the noise mentioned above, which is bounded by q/4, and it does not affect the MSB. That is is the proof of correctness.
5.2. Security Analysis of Algorithm
Definition 3.
If the advantage of any PPT adversary in the above game is negligible, then the LWE-CP-ABE encryption scheme based on the LSSS access control structure is selectively secure under the linear independent restriction.
Definition 4.
If the LWE assumption holds, the proposed LWE-CP-ABE scheme for all access structures is selectively secure.
To prove Definition 3, the hybrid games start with the adversary sending an access policy to the challenger and the challenger sending back the public parameters to the adversary. Then, requests to the challenger a polynomial number of secret keys. For each key query, the attacker sends a series of attributes that do not satisfy the access control policy . In addition, the row of the access control in the matrix is marked by attribute in ; that is, the index of in must be linearly independent. After that, the challenger replies to the corresponding user attribute secret key . Finally, outputs its guess for the bit b encrypted within the challenge ciphertext.
The advantage of the adversary in this game is defined as
Thus, how to generate the public parameters, secret keys, and challenge ciphertext in each hybrid game are described below.
Hyb0: This hybrid game corresponds to the true weak security selective game of the ABE scheme.
| Setup phase | 5. |
| 1. . | 6. |
| 2. . | Challenge phase |
| 3. . | 1. |
| 4. . | 2. |
| 3. | |
| Key query phase | 4. |
| 1. . | 5. |
| 2. . | 6. 7. |
| 3. . 4. |
Hyb1: This game is similar to Hyb0. The changes between Hyb0 and Hyb1 are merely syntactic and indistinguishable. The main difference is described as follows:
1. In the Setup Phase, the generation of an additional matrix is added between Steps 2 and 3;
2. In the Challenge Phase, let the original to . The vectors are generated below using matrices while preparing the challenge ciphertext.
Hyb2: This game is the same as Hyb1, except for the change of the generation of the matrix in the Setup Phase.
The change between Hyb2 and Hyb1 is also only in syntax, so the two mixed games are indistinguishable.
Hyb3: This game is identical to Hyb2, except for the change of the generation of the matrix in the Setup phase:
According to Lemma 1, Hyb3 and Hyb2 are selectively indistinguishable.
Hyb4: This game is the same as Hyb3, except for the change of the matrix in the Setup Phase:
The indistinguishableness between Hyb4 and Hyb3 originates from the enhanced trapdoors lattice sampler function .
Hyb5: This game is analogous to Hyb4, except for the change of vector when answering the key query of the adversary :
The indistinguishableness between Hyb5 and Hyb4 follows from Lemma 1.
Hyb6: This game is the same as Hyb5 except for the generation of vector while answering the key query of the opponent . Let be a vector such that and for all , there is . It is worth noting that due to the game restrictions, the set of the index of row in must be unauthorized to the access control policy , thus ensuring the existence of the vector .
The indistinguishableness between Hyb6 and Hyb5 originates from the enhanced trapdoors function .
Hyb7: This game is the same as Hyb6, except for the change of key module while answering the key query of the adversary :
The change between Hyb7 and Hyb6 is only in syntax, so the hybrid games are indistinguishable.
Hyb8: This game is analogous to Hyb7, except for the generation of vector while answering the key query of the adversary . The changes are described as follows:
The indistinguishableness between Hyb8 and Hyb7 originates from the trapdoors function .
Hyb9: This game is similar to Hyb8, except for the matrix generation during the Setup phase. The indistinguishableness between Hyb9 and Hyb8 originates from the enhanced trapdoors function .
Hyb10: This game is the same as Hyb9 except for the generation of the vector in challenging ciphertext during the Challenge phase, i.e.,
According to Lemma 1, Hyb10 and Hyb9 are selectively indistinguishable.
Hyb11: This game is the same as Hyb10, except for the change in challenging ciphertext during the stage of Challenge:
In the Challenge Phase, we have:
According to the hypothesis of the LWE difficulty problem, Hyb10 and Hyb9 are selectively indistinguishable.
For any adversary and any , let be a function. For all , we define the probability of the adversary winning the mixed game as .
According to the definition of Hyb0, for all :. In addition, for all , there is , there is no challenger’s information about selecting the challenge bit in the challenge ciphertext in Hyb11. Therefore, for all , there is: .
In Hyb0 and Hyb1, the vector is uniformly and independently distributed on , and the matrix is uniformly and independently distributed on , so is also uniformly and independently distributed on . It is concluded that for any opponent , there is .
According to the analysis, in Hyb1 and Hyb2, .
satisfies the leftover hash theorem, so there is a negligible function for any opponent in Hyb3 to Hyb10. For all , there is .
Because the hypothesis of the LWE-hardness problem is true, there is a negligible function for any PPT opponent , which satisfies Therefore, the advantage of the opponent in the mixed game is 0.
5.3. Analysis of Security on the Blockchain
This section will introduce the common blockchain attack models and how this scheme can resist these typical attacks.
Conspiracy attacks: In the distributed key management system, the attacker collusion attack would require M nodes to collect the shares of the master key. This means the attacker must pay a high cost for collecting all the pieces together. Furthermore, each user attribute secret key will generate a uniformly and independently distributed random vector when generating in our scheme, and the random vector of any user secret key is different; therefore, the user attribute secret key is hidden by information theory from anyone, so that the conspiracy attack cannot be realized.
Middleman attacks: middleman attack means that the attacker sets up independent exercises at both ends of the correspondence, exchanges the received data, and monitors or tampers the information. In this scheme, all the correspondences among the nodes are conducted in the form of transactions. The transaction is signed by the initiator using the blockchain secret key, and the returned secret data is encrypted by the other party’s public key, so the middleman cannot pass the verification by tampering with the address or forging the signature. Therefore, this scheme can greatly prevent middleman attacks.
Link attacks: link attacks mean the adversary searches for the user’s private data by linking multiple transactions with the same address. In our scheme, the related authorization process of user attributes can be determined by the user, and the user can choose to disclose his identity attributes or hide the identity information to protect privacy. In addition, the relevant data is the ciphertext on the blockchain, and the security is guaranteed by the algorithm security, so the attacker cannot get the relevant information of the user, thus resisting the link attacks.
5.4. Comparative Analysis of Performance
In this section, a comparative study of the proposed approach with other classical CP-ABE schemes is presented in Table 1. It is observed that all the works employ LSSS-based access structures, with [44] utilizing a hierarchical access structure. FAN [7] uses q-PBDHE as its hardness problem without adopting multi-authority mechanisms, which means that the secret key cannot be cracked and the one-way function cannot be inverted within polynomial time. However, there is a negligible probability of cracking it. Sammy [9] utilizes d-DDH hardness problems as security assumptions, providing an ECC scheme instead of a bilinear pairing in terms of computational complexity overhead. Additionally, it employs a multi-authority CP-ABE scheme with a hierarchical LSSS access structure. Datta [35] and Mohammad [45], on the other hand, separately employ LWE and R-LWE CP-ABE to enhance their security through a multi-authority scheme, achieving resistance against quantum attacks, although they are not based on blockchain and introduce a significant increase in computational complexity.

Table 1.
Comparison with related schemes.
Our scheme extends the previous works by utilizing a lattice-based CP-ABE scheme in conjunction with blockchain-based PRE threshold networks to manage the master secret key. It provides automated verification and consensus of transactions through smart contracts, ensuring confidentiality, accountability, and traceability of transactions. Moreover, it is a security type based on the worst-case problem, where the cryptographic algorithm needs to be solved in the worst-case scenario if it is cracked. Lastly, other CP-ABE schemes described in the references require more expensive operations such as multiplication, modulus exponentiation, and bilinear mapping, while our scheme only requires addition operations with lower expense, thereby significantly improving operational efficiency.
5.5. Analysis of Experimental Simulation
To conduct a thorough evaluation of the proposed scheme’s practical effectiveness, a series of experiments were performed in this paper. All experiments were conducted on a computer running the Win10 operating system with the following hardware configuration: Intel Core i7-8750H CPU, 2.20 GHz clock frequency, and 8.0 GB RAM. The paper utilized the PBC [46] library based on pairings and the PALISADE API. A simulation framework was built using the C++ programming language. Additionally, a blockchain virtual network based on Ganache [47] was set up, and the Remix platform provided by Ethereum was used for compiling and deploying smart contract code online. When selecting the performance index, the scheme in this paper does not change the transaction process of the blockchain network but only encrypts the data in the network by LWE-CP-ABE, which will not affect the operation efficiency of the blockchain network. Therefore, this paper only evaluates the performance index of the LWE-CP-ABE scheme.
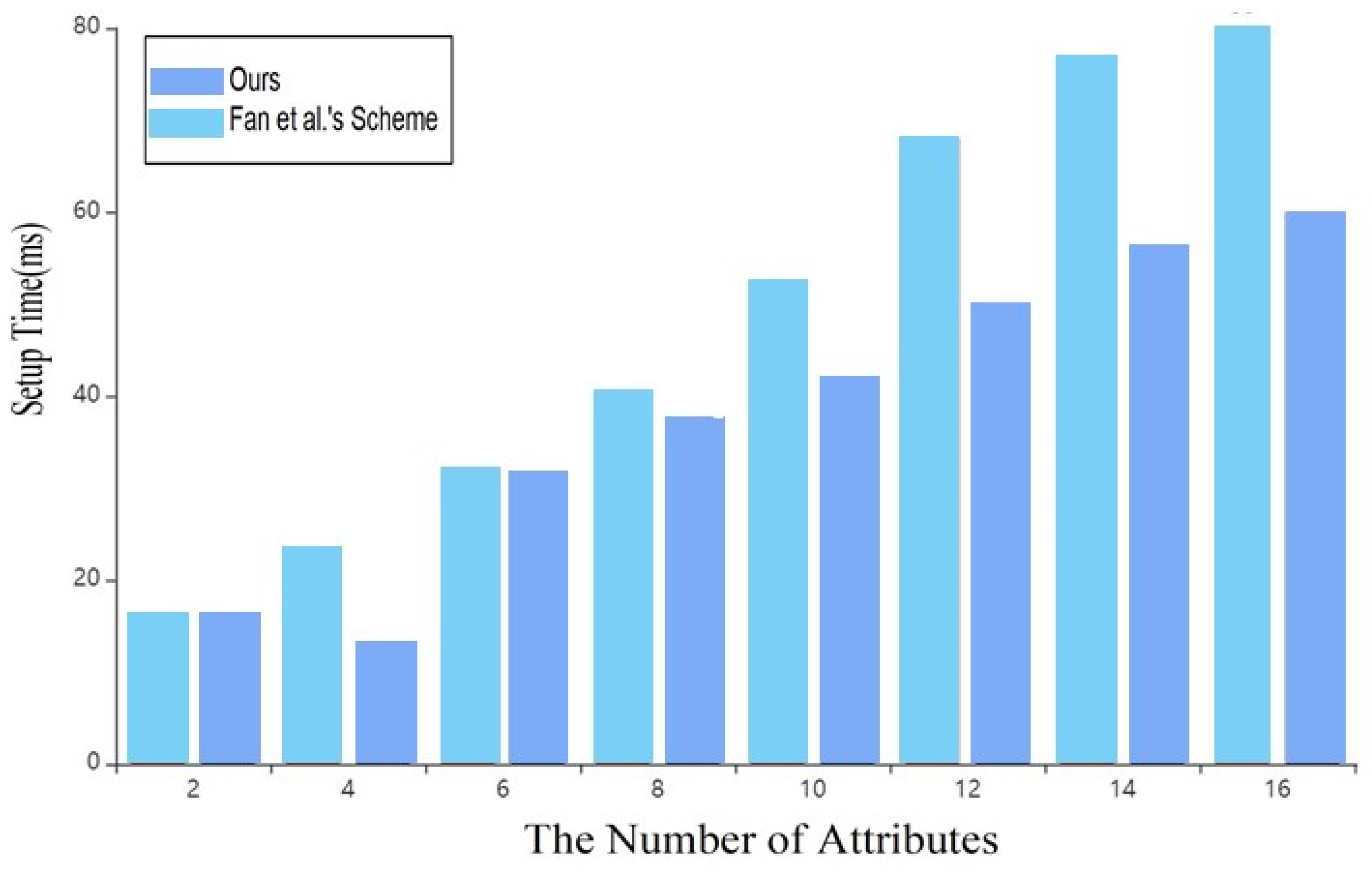
In this experiment, the plaintext data is set to 308B. The scheme in this paper does not need complex operations such as modulus exponentiation and bilinear mapping. Still, only the addition operation, so the time cost in each stage is better than that of the scheme in reference [7].
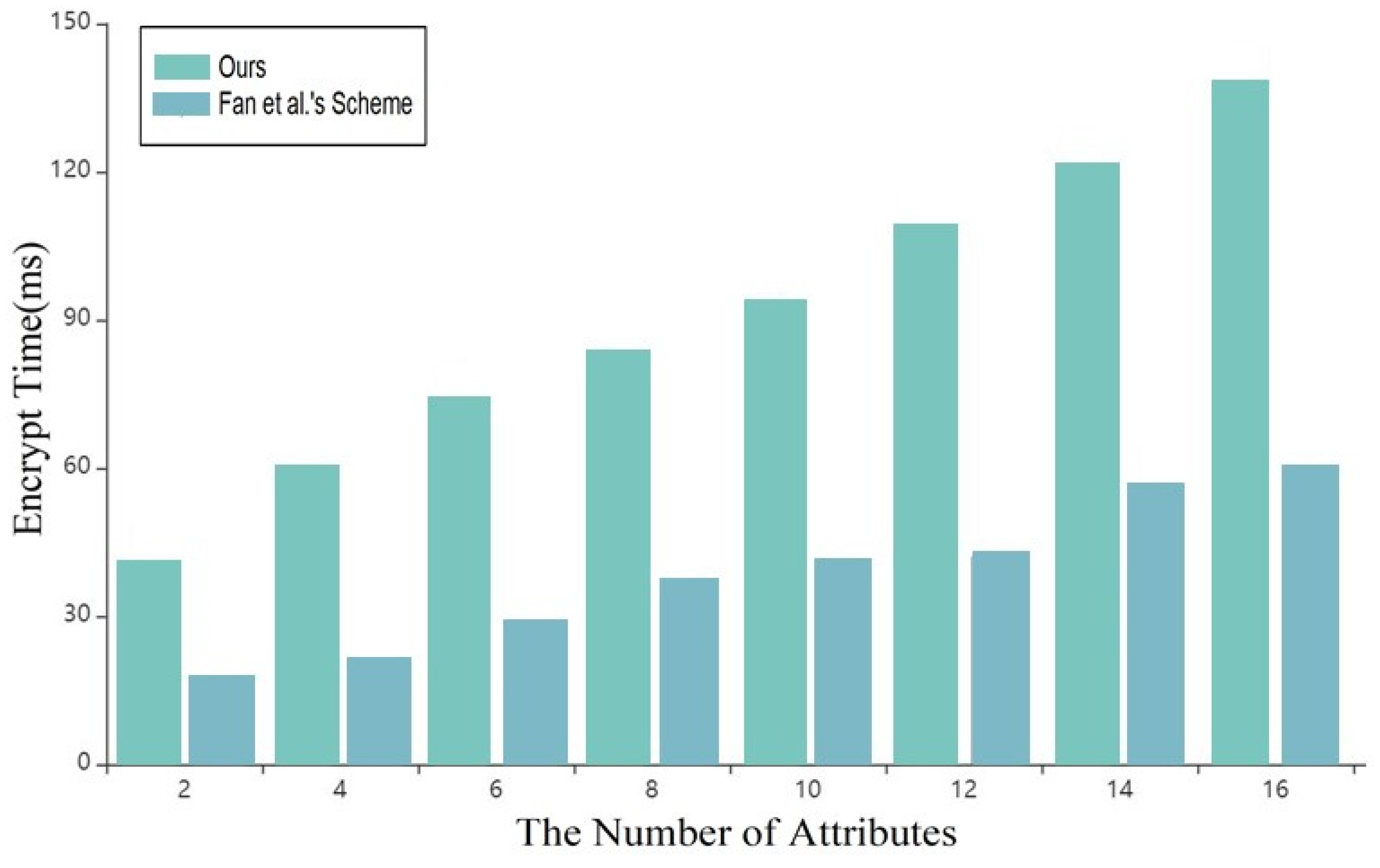
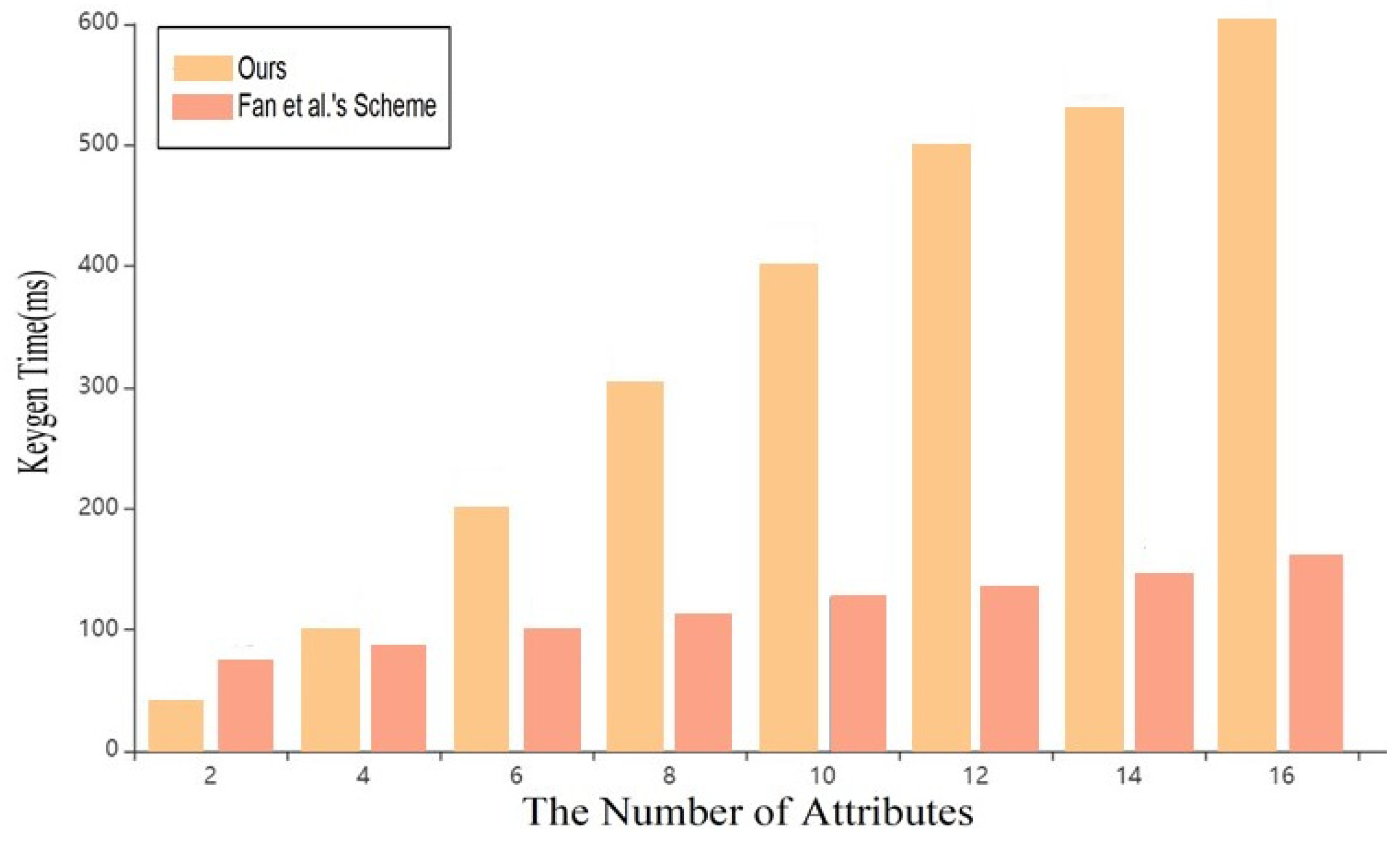
As shown in Figure 4 and Figure 5, with the continuous increase of attributes in the system, the time spent by the data owner in the setup and encryption under the blockchain in this scheme is shorter than that in the scheme of reference [7], which greatly improves the overall efficiency of the system.
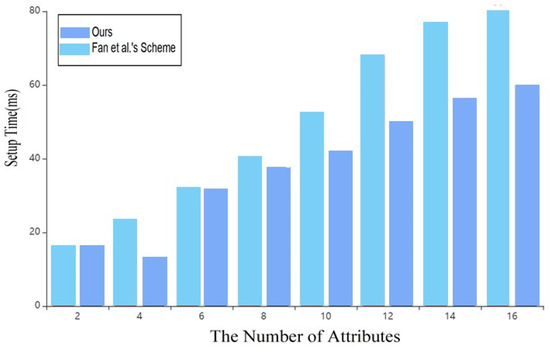
Figure 4.
Time cost of Setup [8].
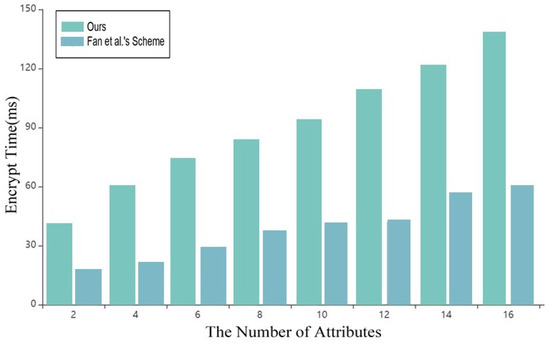
Figure 5.
Time cost of Encryption [8].
As shown in Figure 6, in the key generation stage, with the continuous increase of attributes, this scheme is superior to that in reference [7], and it will be more practical in key generation with multi-user and multi-attribute sets.
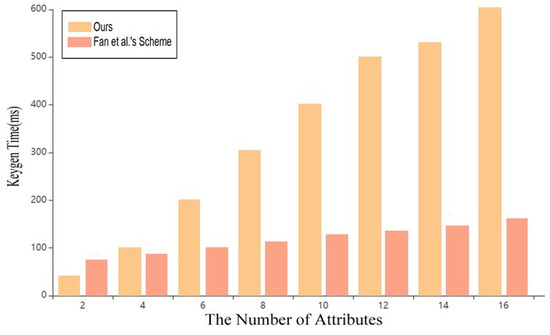
Figure 6.
Time cost of key generation [8].
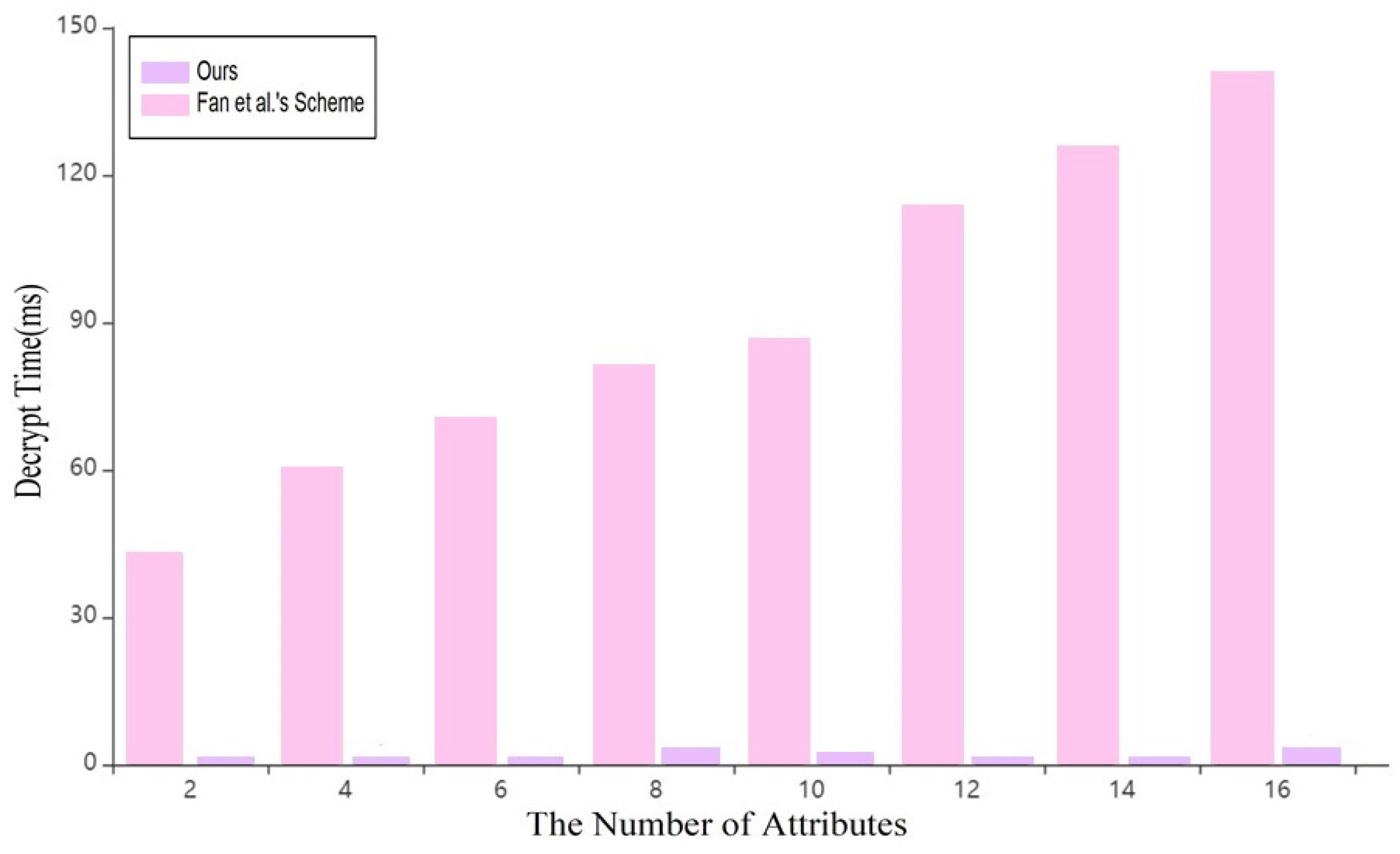
As shown in Figure 7, in the decryption stage, the scheme in this paper takes about 0~2 ms, which is far lower than the scheme in reference [7]. Therefore, it is more suitable for blockchain data sharing.
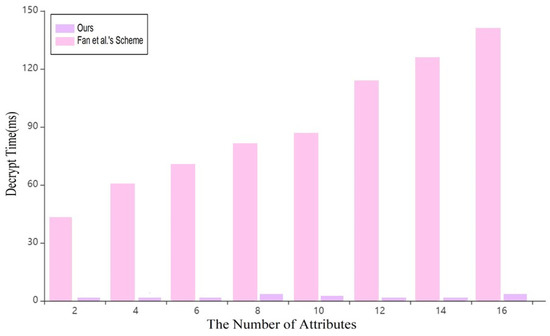
Figure 7.
Time cost of Decryption [8].
In addition, considering the pre-quantum blockchain system, the transaction cost for executing the smart contract related to signature verification on KMS is around 1,091,035 gas, with an execution cost of 965,801 gas. The transaction cost for executing the smart contract related to the correctness of the re-encrypted results is 3,597,371 gas, with an execution cost of 3,300,467 gas. That means that we can create a multi-lateral market to provide incentive mechanisms to enhance the security of access control based on the blockchain system.
6. Conclusions
Privacy protection technology on the blockchain has always been a significant factor in data access and sharing. With the rapid development of quantum computation, the traditional public key cryptosystem based on number theory cannot resist quantum attacks. Therefore, this paper effectively integrates blockchain technology with the lattice attribute-based encryption algorithm and proposes a data-sharing scheme based on LWE-CP-ABE using blockchain technology. This paper improves the CPABE scheme put forward by Datta, designs the ABE algorithm against quantum attacks with the renewable strategy, and fulfills the dynamic protection of data. The lattice-based fine-grained access control of CP-ABE is constructed through the decentralized KMS and formatted transaction structure over a pre-quantum cryptographic blockchain system, which not only ensures the characteristics of the post-quantum CP-ABE algorithm against quantum attacks but also provides the traceable on-chain transactions of the participant’s activities. The simulation experiment shows that the performances (as can be seen in Figure 4, Figure 5, Figure 6 and Figure 7) is superior to the traditional CP-ABE scheme. Meanwhile, decentralized KMS powered by blockchain technology enables the distribution of the key management process between Data Owners and Data Users by applying a threshold proxy re-encryption scheme to eliminate any risk of centralization and collusion.
As a future research direction, we plan to extend our protocol to achieve IND-CCA security in the post-quantum setting. Specifically, we aim to develop a decentralized multi-authority CP-ABE scheme based on blockchain resistant to chosen-ciphertext attacks and can support any non-monotone access structure. Furthermore, we aim to explore comprehensive countermeasures against combined attacks, such as Differential Power Analysis (DPA) and Differential Fault Analysis (DFA). We will investigate and implement countermeasures based on techniques such as Time Insertion (TI) and error detection schemes to enhance the security of our system. These efforts will contribute to strengthening the resilience of our protocol against various differential analysis attacks, ensuring the reliability and security of the system.
Author Contributions
Conceptualization, T.C.; methodology, Z.R.; software, Y.Y.; formal analysis, J.Z. (Jie Zhu); project administration, J.Z. (Jinyi Zhao). All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Natural Science Foundation of China, grant number No. 61961042 and No.71964037; Yunnan Key Laboratory of Blockchain Application Technology grant number No. 202105AG070005 and No. YNB202108; Yunnan International Joint Research and Development Center for Cross-border Trade and Financial Blockchain, grant number No. 202203AP140010; Kunming International (Foreign-oriented) Science and Technology Research and Development Center for Blockchain Technology in South Asia and Southeast Asia, grant number No. GHJD-2022006; Research on Key Technologies of Cross-Border Trade Blockchain for RCEP, grant number No. 202202AD080011; Scientific Research Foundation of Yunnan Education Department, grant numbers No. 2023Y0657 and No. 2023Y0675.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data used to support the findings of this study are available from the corresponding author upon request.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Huang, S.; Chen, W.; Fan, B. Data security sharing method based on CP-ABE and blockchain. Comput. Syst. Appl. 2019, 28, 79–86. [Google Scholar]
- Wang, X.; Jiang, X.; Li, Y. Model for data access control and sharing based on blockchain. J. Softw. 2019, 30, 1661–1669. [Google Scholar]
- Yang, T.Y.; Cai, J.L.; Zhang, Y.W. Privacy preserving scheme in block chain with provably secure based on SM9 algorithm. J. Softw. 2019, 30, 1692–1704. [Google Scholar]
- Zyskind, G.; Nathan, O. Decentralizing privacy: Using blockchain to protect personal data. In Proceedings of the 2015 IEEE Security and Privacy Workshops, San Jose, CA, USA, 21–22 May 2005. [Google Scholar]
- Zhang, Q.H. Research on Identification and Access Control in Blockchain; Beijing Jiaotong University: Beijing, China, 2018. [Google Scholar]
- Xu, Y.; Xiao, S.; Wang, H. Redactable Blockchain-based Secure and Accountable Data Management. IEEE Trans. Netw. Serv. Manag. 2023, 1, 1. [Google Scholar] [CrossRef]
- Tian, Y.L.; Yang, K.D.; Wang, Z. Algorithm of blockchain data provenance based on ABE. J. Commun. 2019, 40, 101–111. [Google Scholar]
- Fan, Y.; Lin, X.; Liang, W. Trace Chain: A blockchain-based scheme to protect data confidentiality and traceability. Softw. Pract. Exp. 2019, 52, 115–129. [Google Scholar] [CrossRef]
- Wang, H.; Song, Y. Secure cloud based EHR system using attribute-based cryptosystem and blockchain. J. Med. Syst. 2018, 42, 152. [Google Scholar] [CrossRef]
- Sammy, F.; Maria, C.V.S. An Efficient Blockchain Based Data Access with Modified Hierarchical Attribute Access Structure with CP-ABE Using ECC Scheme for Patient Health Record. Secur. Commun. Netw. 2022, 2022, 1–11. [Google Scholar] [CrossRef]
- Xu, Y.; Liu, Z.; Zhang, C. Blockchain-based Trustworthy Energy Dispatching Approach for High Renewable Energy Penetrated Power System. IEEE Internet Things J. 2022, 9, 10036–10047. [Google Scholar] [CrossRef]
- Zhang, Y.; He, D.B.; Kim, K.R.C. BaDS: Blockchain-based architecture for data sharing with ABS and CP-ABE in IoT. Wirel. Commun. Mob. Comput. 2018, 2018, 1–9. [Google Scholar] [CrossRef]
- Sahai, A.; Waters, B. Fuzzy identity-based encryption. In Proceedings of the 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005. [Google Scholar]
- Goyal, V.; Pandey, O.; Sahai, A. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October–3 November 2006. [Google Scholar]
- Wang, Y.; Fan, K. Effective CP-ABE with Hidden Access Policy. J. Comput. Res. Dev. 2019, 56, 2151–2159. [Google Scholar]
- Zhou, Z.; Huang, D.; Wang, Z. Efficient privacy-preserving ciphertext-policy attribute based-encryption and broadcast encryption. IEEE Trans. Comput. 2015, 64, 126–138. [Google Scholar] [CrossRef]
- Yan, G.C.; Ling, L.S. Attribute-based access control for multi-authority systems with constant size ciphertext in clouds. China Commun. 2016, 13, 146–162. [Google Scholar]
- Phuong, T.V.X.; Yang, G.; Susilo, W. Hidden ciphertext policy attribute-based encryption under standard assumptions. IEEE Trans. Inf. Forensics Secur. 2016, 11, 35–45. [Google Scholar] [CrossRef]
- Sushmita, R.; Milos, S.; Amiya, N. Decentralized access control with anonymous authentication of data stored in clouds. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 384–394. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute-based encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 20–23 May 2007. [Google Scholar]
- Waters, B. Ciphertext-policy attribute-based encryption: An expressive, efficient and provable secure realization. In Proceedings of the 14th International Conference on Practice and Theory in Public Key Cryptography Conference on Public Key Cryp-tography, Taormina, Italy, 6–9 March 2011. [Google Scholar]
- Okamoto, T.; Takashima, K. Fully Secure Unbounded Inner-Product and Attribute-Based Encryption. In Proceedings of the 18th International Conference on the Theory and Application of Cryptology and Information Security, Beijing, China, 2–6 December 2012. [Google Scholar]
- Gorbunovo, S.; Vaikuntanathan, V.; Wee, H. Attribute-based encryption for circuits. In Proceedings of the Symposium on Theory of Computing-STOC, Palo Alto, CA, USA, 2–4 June 2013. [Google Scholar]
- Hohenberger, S.; Waters, B. Online/Offline attribute-based encryption. In Proceedings of the 17th International Conference on Practice and Theory in Public-Key Cryptography, Buenos Aires, Argentina, 26–28 March 2014. [Google Scholar]
- Rouselakis, Y.; Waters, B. Practial constructions and new proof methods for large universe attribute-based encryption. In Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, Berlin Germany, 4–8 November 2013. [Google Scholar]
- Pu, Y.W.; Hu, C.Q.; Deng, S.J. R2PEDS: A Recoverable and Revocable Privacy-Preserving Edge Data Sharing Scheme. IEEE Internet Things J. 2020, 7, 8077–8089. [Google Scholar] [CrossRef]
- Gao, S.; Piao, G.R.; Zhu, J.M. TrustAccess: A Trustworthy Secure Ciphertext-Policy and Attribute Hiding Access Control Scheme based on Blockchain. IEEE Trans. Veh. Technol. 2020, 69, 5784–5798. [Google Scholar] [CrossRef]
- Qin, X.M.; Huang, Y.F.; Yang, Z. A Blockchain-based access control scheme with multiple attribute authorities for secure cloud data sharing. J. Syst. Archit. 2020, 112, 101854–101866. [Google Scholar] [CrossRef]
- Zhang, G.F.; Chen, X.; Feng, B. BCST-APTS: Blockchain and CP-ABE Empowered Data Supervision, Sharing, and Privacy Protection Scheme for Secure and Trusted Agricultural Product Traceability System. Secur. Commun. Netw. 2022, 2022, 1–11. [Google Scholar] [CrossRef]
- Ajtai, M. Generating hard instances of lattice problems. In Proceedings of the Twenty-Eighth Annual ACM Symposium on Theory of Computing, Philadelphia PA, USA, 22–24 May 1996. [Google Scholar]
- Regev, O. On lattices, learning with errors, random linear-codes, and cryptography. J. ACM 2009, 56, 84–93. [Google Scholar] [CrossRef]
- Qian, X.Y.; Wu, W.Y. Identity-based Encryption Scheme Based on R-SIS/R-LWE. Comput. Sci. 2019, 30, 1692–1704. [Google Scholar]
- Zhou, Y.H.; Dong, S.S.; Yang, Y.G. A Lattice-based Identity-based Proxy Partially Blind Signature Scheme in the Standard Model. Netinfo Secur. 2021, 21, 37–43. [Google Scholar]
- Zhang, Y.H.; Hu, Y.P.; Liu, X.M. Zero-knowledge Proofs for Attribute-Based Group Signatures with Verifier-local Revocation Over Lattices. J. Electron. Inf. Technol. 2020, 42, 315–321. [Google Scholar]
- Datta, P.; Komargodski, I.; Waters, B. Decentralized Multi-Authority ABE for DNFs form LWE. In Advances in Cryptology–EUROCRYPT 2021: 40th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Zagreb, Croatia, 17–21 October 2021; Spring: Cham, Switzerland, 2021. [Google Scholar]
- Sarker, A.; Kermani, M.M.; Azarderakhsh, R. Fault detection architectures for inverted binary ring-LWE construction benchmarked on FPGA. IEEE Trans. Circuits Syst. II Express Briefs 2020, 68, 1403–1407. [Google Scholar] [CrossRef]
- Anastasova, M.; Azarderakhsh, R.; Kermani, M.M. Time-Efficient Finite Field Microarchitecture Design for Curve448 and Ed448 on Cortex-M4. In Proceedings of the International Conference on Information Security and Cryptology, Seoul, Republic of Korea, 30 November–2 December 2022. [Google Scholar]
- Anastasova, M.; Azarderakhsh, R.; Kermani, M.M. Fast strategies for the implementation of SIKE round 3 on ARM Cortex-M4. IEEE Trans. Circuits Syst. I Regul. Pap. 2021, 68, 4129–4141. [Google Scholar] [CrossRef]
- Sanal, P.; Karagoz, E.; Seo, H. Kyber on ARM64: Compact implementations of Kyber on 64-bit ARM Cortex-A processors. In Proceedings of the Security and Privacy in Communication Networks: 17th EAI International Conference, Canterbury, Great Britain, 6–9 September 2021. [Google Scholar]
- Niasar, B.M.; Azarderakhsh, R.; Kermani, M.M. Cryptographic accelerators for digital signature based on Ed25519. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2021, 29, 1297–1305. [Google Scholar] [CrossRef]
- Kermani, M.M.; Azarderakhsh, R.; Aghaie, A. Reliable and error detection architectures of Pomaranch for false-alarm-sensitive cryptographic applications. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2015, 23, 2804–2812. [Google Scholar] [CrossRef]
- Kermani, M.M.; Masoleh, A.R. Reliable hardware architectures for the third-round SHA-3 finalist Grostl benchmarked on FPGA platform. In Proceedings of the 2011 IEEE International Symposium on Defect and Fault Tolerance in VLSI and Nanotechnology Systems, Vancouver, BC, Canada, 3–5 October 2011. [Google Scholar]
- David. UMBRAL: A Threshold Proxy Re-Encryption Scheme. Available online: https://github.com/nucypher/umbral-doc/blob/master/umbral-doc.pdf (accessed on 6 May 2018).
- Aghaie, A.; Kermani, M.M.; Azarderakhsh, R. Fault diagnosis schemes for secure lightweight cryptographic block cipher RECTANGLE benchmarked on FPGA. In Proceedings of the 2016 IEEE International Conference on Electronics, Circuits and Systems (ICECS), Monte Carlo, Monaco, 11–14 December 2016. [Google Scholar]
- Mohammad, S.R.; Anirban, B.; Shinsaku, K. Decentralized Ciphertext-Policy Attribute-Based Encryption: A Post-Quantum Construction. J. Internet Serv. Inf. Secur. 2017, 7, 3. [Google Scholar]
- Ben, L. PBC Library. Available online: https://crypto.stanford.edu/pbc/ (accessed on 14 June 2013).
- TruffleSuite. Ganache. Available online: https://github.com/trufflesuite/ganache/ (accessed on 26 April 2023).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).