An Opcode-Based Vulnerability Detection of Smart Contracts
Abstract
1. Introduction
2. Materials and Methods
2.1. Blockchain
2.2. Smart Contracts
2.3. Mythril Method
- Get the contract’s bytecode;
- Establish the contract account’s initial state;
- Using ‘n’ transactions, investigate the contract’s state space. Although it can be changed, n’s default value;
- When an undesirable situation is discovered, demonstrate or refute the assumptions that led to it. The transactions needed to obtain to a faulty state can be estimated after one is discovered. This can be used to exploit vulnerabilities in addition to aiding in the problem’s underlying cause identification.
3. Types of Vulnerabilities
3.1. Reentrant Vulnerabilities
3.2. Integer Overflow Vulnerabilities
3.3. Short Address Vulnerabilities
3.4. Timestamp Dependency Vulnerabilities
3.5. Transaction Sequence Dependency Vulnerabilities
4. Smart Contract Vulnerability Detection Tools
4.1. Symbolic Execution
4.2. Formal Verification
- Modeling: Turn the smart contract into a formal model by transforming the contract code into a form of a formal specification language (e.g., Solidity);
- Property specification: Specify the security characteristics that must be examined, such as that assets cannot be tampered with or that they are immune to reentrant assaults. Predicate logic or temporal logic are two examples of formal logic that can be used to define these property designations;
- Formal verification: Check the smart contract using formal verification techniques. Typically, this entails verification using instruments like model detectors and automated theorem provers;
- Analytical feedback: Examine the validation results, if flaws are discovered, inform the developer so that they may be corrected.
4.3. Static Analysis
- Code scan: To find potential flaws, static analysis tools scan smart contract codes. Lexical, syntactic, and semantic analysis of the code is often required for this;
- Detection of defects: After the scan is finished, the static analysis tool searches the code for errors such as integer overflows, array overruns, reentrant attacks, etc.;
- Vulnerability classification: The vulnerabilities are categorized so that programmers may find and address the issue right away.
4.4. Dynamic Analysis
- (a)
- Creating test cases.
- (b)
- Run the test cases.
- (c)
- Examine the test outcomes.
4.5. Model Detection Method
- (a)
- Build the model
- (b)
- Establishing the characteristics
- (c)
- Validate the attributes using model testing tools
5. Detection of Smart Contract Vulnerabilities Based on Opcodes
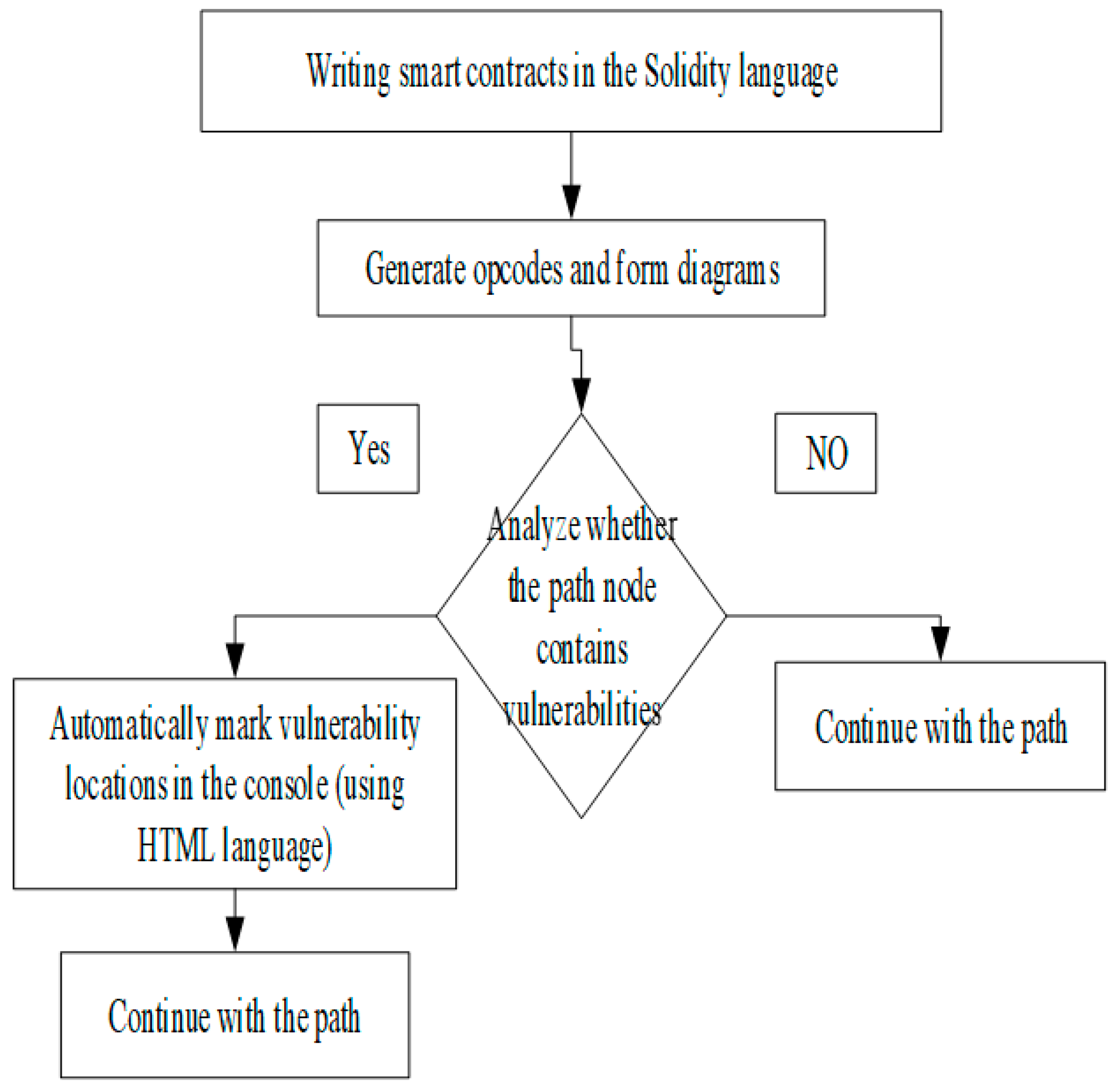
Analyzing the Smart Contract Opcode Flowchart
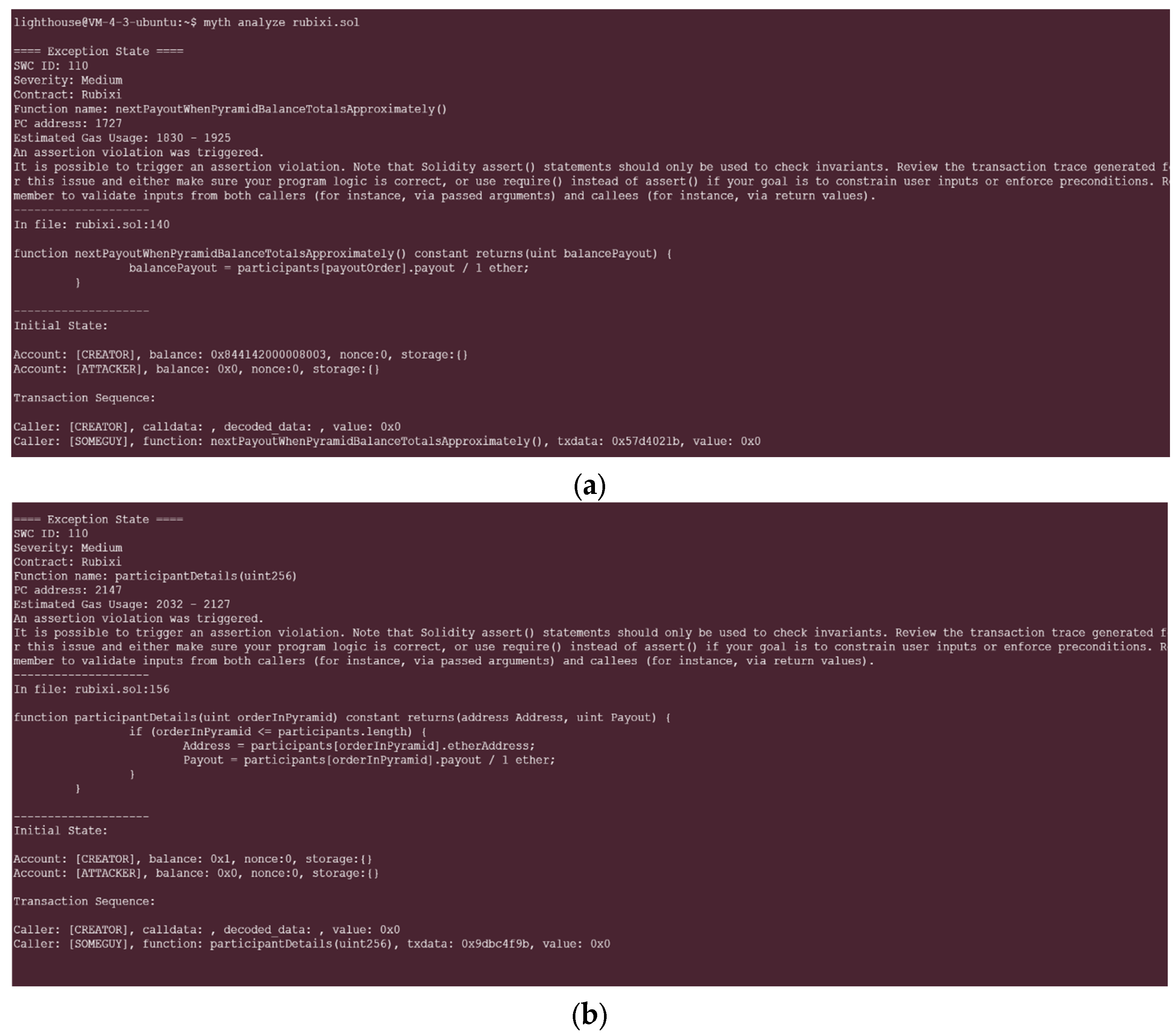
6. Analysis of Experimental Results
6.1. Test Environment
6.2. Detection Performance Comparison
- (a)
- Accuracy: In order to evaluate the pros and cons of detection tools, we first focus on the most common evaluation index, namely accuracy. Accuracy can objectively reflect the most direct detection effect of various detection tools. Usually, the real situation is compared with the matching results of the detection results are used as an important evaluation index, including the following four situations.
- True positive (true positive, TP): For a certain contract, the detection result of the detection tool has loopholes, and the real situation also has loopholes, that is, the detection result is correct;
- False positive (false positive, FP): For a certain contract, the detection result of the detection tool is that there is a loophole, but the real situation is no loophole, that is, there is a misjudgment in the detection result;
- False negative (FN): For a certain contract, the detection result of the detection tool is that there are no loopholes, but the real situation is that there are loopholes, that is, there are missed judgments in the detection results;
- True negative (true negative, TN): For a certain contract, the detection result of the detection tool is no loopholes, and the real situation is also without loopholes, that is, the detection result is correct.
- (b)
- F1-Score: F1-Score is an important measurement index in classification problems. It is the harmonic mean of precision and recall. It is often used as the final evaluation standard for some classification problems. Its calculation method is shown in Formulas (2)–(4):
6.3. Time Performance Comparison
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Szabo, N. Smart contracts: Building blocks for digital markets. EXTROPY J. Transhumanist Thought 1996, 18, 28. [Google Scholar]
- Ethereum. Solidity Documentation [EB/OL]. Available online: https://solidity.readthedocs.io/en/latest/ (accessed on 22 May 2023).
- Tikhomirov, S.; Voskresenskaya, E.; Ivanitskiy, I.; Takhaviev, R.; Marchenko, E.; Alexandrov, Y. Smartcheck: Static analysis of ethereum smart contracts. In Proceedings of the 1st International Workshop on Emerging Trends in Software Engineering for Blockchain, Gothenburg, Sweden, 27 May–3 June 2018; pp. 9–16. [Google Scholar]
- Feist, J.; Grieco, G.; Groce, A. Slither: A static analysis framework for smart contracts. In Proceedings of the IEEE/ACM 2nd International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB), Montreal, QC, Canada, 27 May 2019; pp. 8–15. [Google Scholar]
- Jiang, B.; Liu, Y.; Chan, W.K. Contractfuzzer: Fuzzing Smart Contracts for Vulnerability Detection. In Proceedings of the 33rd ACM/IEEE International Conference on Automated Software Engineering, Montpellier, France, 3–7 September 2018; pp. 259–269. [Google Scholar]
- Liu, C.; Liu, H.; Cao, Z.; Chen, Z.; Chen, B.; Roscoe, B. Reguard: Finding Reentrancy Bugs in Smart Contracts. In Proceedings of the 40th International Conference on Software Engineering: Companion Proceeedings, Gothenburg, Sweden, 27 May–3 June 2018; pp. 65–68. [Google Scholar]
- Zhou, E.; Hua, S.; Pi, B.; Sun, J.; Nomura, Y.; Yamashita, K.; Kurihara, H. Security Assurance for Smart Contract. In Proceedings of the 9th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 26–28 February 2018; pp. 1–5. [Google Scholar]
- Muller, B. Mythril[EB/OL]. 2019. Available online: https://github.com/ConsenSys/mythril (accessed on 22 May 2023).
- Luu, L.; Chu, D.H.; Olickel, H.; Saxena, P.; Hobor, A. Making Smart Contracts Smarter. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 254–269. [Google Scholar]
- Holzmann, G.J. The model checker SPIN. IEEE Trans. Softw. Eng. 1997, 23, 279–295. [Google Scholar] [CrossRef]
- Ben-Ari, M. Principles of the Spin Model Checker; Springer Science & Business Media: Berlin, Germany, 2008. [Google Scholar]
- Hu, K.; Bai, X.; Gao, L.; Dong, A. Formal Verification Methods for Smart Contracts. Inf. Secur. Res. 2016, 2, 1080–1089. [Google Scholar]
- Wang, W.; Song, J.; Xu, G.; Li, Y.; Wang, H.; Su, C. Contractward: Automated vulnerability detection models for ethereum smart contracts. IEEE Trans. Netw. Sci. Eng. 2020, 8, 1133–1144. [Google Scholar] [CrossRef]
- Singh, A.; Parizi, R.M.; Zhang, Q.; Choo, K.K.R.; Dehghantanha, A. Blockchain smart contracts formalization: Approaches and challenges to address vulnerabilities. Comput. Secur. 2020, 88, 101654. [Google Scholar] [CrossRef]
- Hildenbrandt, E.; Saxena, M.; Rodrigues, N.; Zhu, X.; Daian, P.; Guth, D.; Moore, D.; Park, D.; Zhang, Y.; Stefanescu, A.; et al. Kevm: A Complete Formal Semantics of the Ethereum Virtual Machine. In Proceedings of the IEEE 31st Computer Security Foundations Symposium (CSF), Oxford, UK, 9–12 July 2018; pp. 204–217. [Google Scholar]
- Park, D.; Zhang, Y.; Saxena, M.; Daian, P.; Roşu, G. A formal Verification Tool for Ethereum VM bytecode. In Proceedings of the 2018 26th ACM Joint Meeting on European Software Engineering Conference and Symposium on the Foundations of Software Engineering, Athens, Greece, 23–28 August 2018; pp. 912–915. [Google Scholar]
- Liu, H.; Liu, C.; Zhao, W.; Jiang, Y.; Sun, J. S-gram: Towards Semantic-Aware Security Auditing for Ethereum Smart Contracts. In Proceedings of the 33rd ACM/IEEE International Conference on Automated Software Engineering, Montpellier, France, 3–7 September 2018; pp. 814–819. [Google Scholar]
- Mavridou, A.; Laszka, A. Designing secure ethereum smart contracts: A finite state machine based approach. In Financial Cryptography and Data Security. Proceedings of the 22nd International Conference, FC 2018, Nieuwpoort, Curaçao, 26 February–2 March 2018; Revised Selected Papers 22; Springer: Berlin/Heidelberg, Germany, 2018; pp. 523–540. [Google Scholar]
- Sayeed, S.; Marco-Gisbert, H.; Caira, T. Smart contract: Attacks and protections. IEEE Access 2020, 8, 24416–24427. [Google Scholar] [CrossRef]
- Zhuang, Y.; Liu, Z.; Qian, P.; Liu, Q.; Wang, X.; He, Q. Smart Contract Vulnerability Detection Using Graph Neural Networks. In Proceedings of the Twenty-Ninth International Conference on International Joint Conferences on Artificial Intelligence, Yokohama, Japan, 7–15 January 2021; pp. 3283–3290. [Google Scholar]
- Yong, Y.; Feiyue, W. Current Status and Prospects of Blockchain Technology Development. Acta Autom. Sin. 2016, 42, 481–494. [Google Scholar]
- Yin, M.; Malkhi, D.; Reiter, M.K.; Gueta, G.G.; Abraham, I. HotStuff: BFT consensus in the lens of blockchain. arXiv 2018, arXiv:1803.05069. [Google Scholar]
- Buterin, V. Ethereum: A Next Generation Smart Contract and Decentralized Application Platform; Udemy: San Francisco, CA, USA, 2017. [Google Scholar]
- Dhillon, V.; Metcalf, D.; Hooper, M.; Dhillon, V.; Metcalf, D.; Hooper, M. The DAO hacked. In Blockchain Enabled Applications: Understand the Blockchain Ecosystem and How to Make it Work for You; Apress: Berkeley, CA, USA, 2017; pp. 67–78. [Google Scholar]
- Bjørner, N.; de Moura, L.; Nachmanson, L.; Wintersteiger, C.M. Programming Z3. In Proceedings of the Engineering Trustworthy Software Systems: 4th International School, SETSS 2018, Chongqing, China, 7–12 April 2018; pp. 148–201. [Google Scholar]
- Kalra, S.; Goel, S.; Dhawan, M.; Sharma, S. Zeus: Analyzing safety of smart contracts. In Proceedings of the Network and Distributed Systems Security (NDSS) Symposium, San Diego, CA, USA, 18–21 February 2018; pp. 1–12. [Google Scholar]
- Mossberg, M.; Manzano, F.; Hennenfent, E.; Groce, A.; Grieco, G.; Feist, J.; Brunson, T.; Dinaburg, A. Manticore: A user-friendly Symbolic Execution Framework for Binaries and Smart Contracts. In Proceedings of the 34th IEEE/ACM International Conference on Automated Software Engineering (ASE), San Diego, CA, USA, 10–15 November 2019; pp. 1186–1189. [Google Scholar]
- Lattner, C.; Adve, V. LLVM: A Compilation Framework for Lifelong Program Analysis & Transformation. In Proceedings of the International Symposium on Code Generation and Optimization, San Jose, CA, USA, 20–24 March 2004; pp. 75–86. [Google Scholar]
- Chen, J.; Xia, X.; Lo, D.; Grundy, J.; Luo, X.; Chen, T. Defectchecker: Automated smart contract defect detection by analyzing evm bytecode. IEEE Trans. Softw. Eng. 2021, 48, 2189–2207. [Google Scholar] [CrossRef]
- Grishchenko, I.; Maffei, M.; Schneidewind, C. A Semantic Framework for the Security Analysis of Ethereum Smart Contracts. In Proceedings of the Principles of Security and Trust: 7th International Conference, POST 2018, Held as Part of the European Joint Conferences on Theory and Practice of Software, ETAPS 2018, Thessaloniki, Greece, 14–20 April 2018; pp. 243–269. [Google Scholar]
- Bhargavan, K.; Delignat-Lavaud, A.; Fournet, C.; Gollamudi, A.; Gonthier, G.; Kobeissi, N.; Kulatova, N.; Rastogi, A.; Sibut-Pinote, T.; Swamy, N. Formal Verification of Smart Contracts: Short Paper. In Proceedings of the ACM Workshop on Programming Languages and Analysis for Security, Vienna, Austria, 24 October 2016; pp. 91–96. [Google Scholar]
- Swamy, N.; Hriţcu, C.; Keller, C.; Rastogi, A.; Delignat-Lavaud, A.; Forest, S.; Bhargavan, K.; Fournet, C.; Strub, P.-Y.; Kohlweiss, M.; et al. Dependent Types and Multi-Monadic Effects in F. In Proceedings of the 43rd annual ACM SIGPLAN-SIGACT Symposium on Principles of Programming Languages, St. Petersburg, FL, USA, 20–22 January 2016; pp. 256–270. [Google Scholar]
- Tann, W.J.W.; Han, X.J.; Gupta, S.S.; Ong, Y.S. Towards safer smart contracts: A sequence learning approach to detecting security threats. arXiv 2018, arXiv:1811.06632. [Google Scholar]
- Nikolić, I.; Kolluri, A.; Sergey, I.; Saxena, P.; Hobor, A. Finding the Greedy, Prodigal, and Suicidal Contracts at Scale. In Proceedings of the 34th Annual Computer Security Applications Conference, San Juan, PR, USA, 3–7 December 2018; pp. 653–663. [Google Scholar]
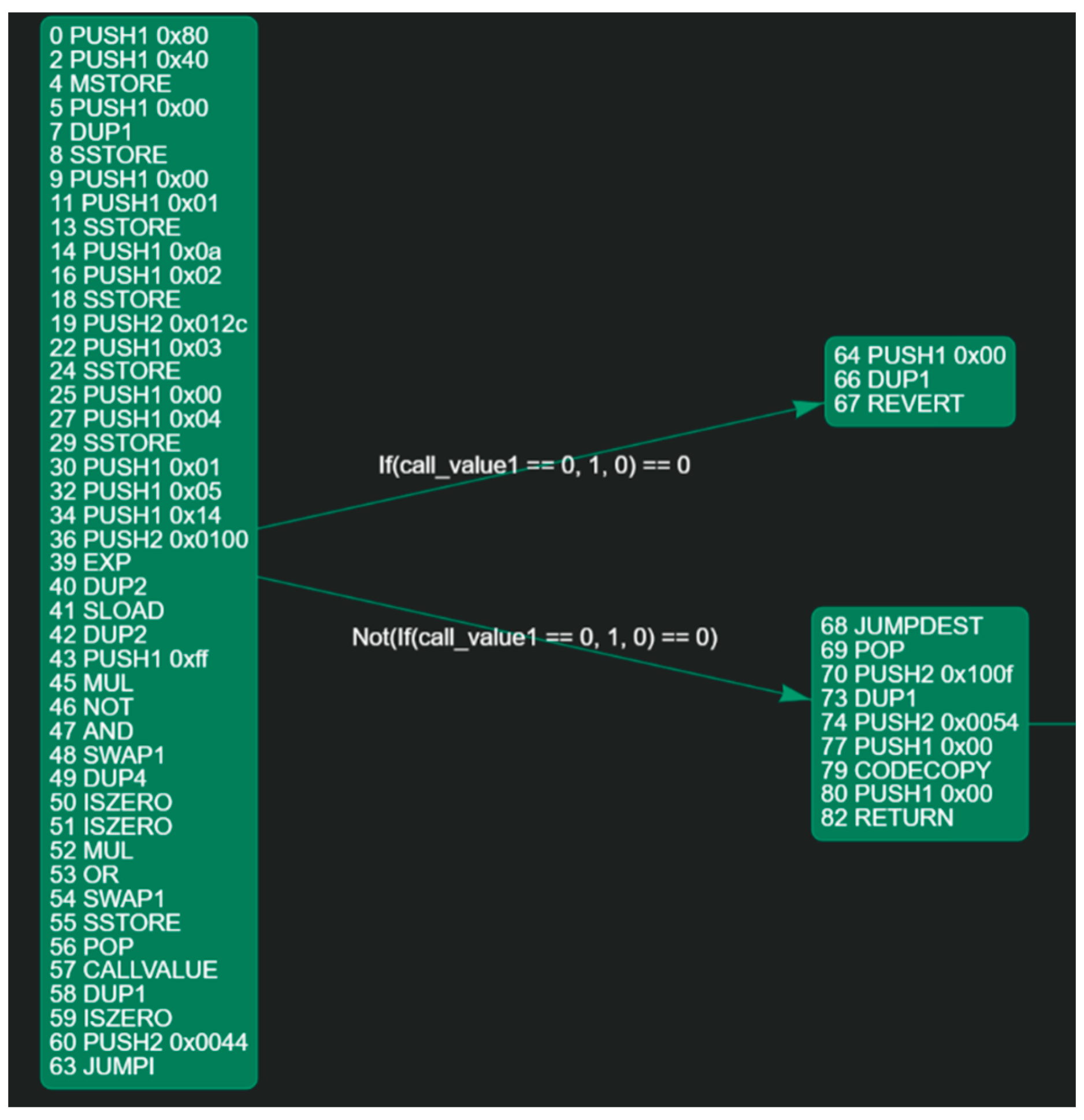
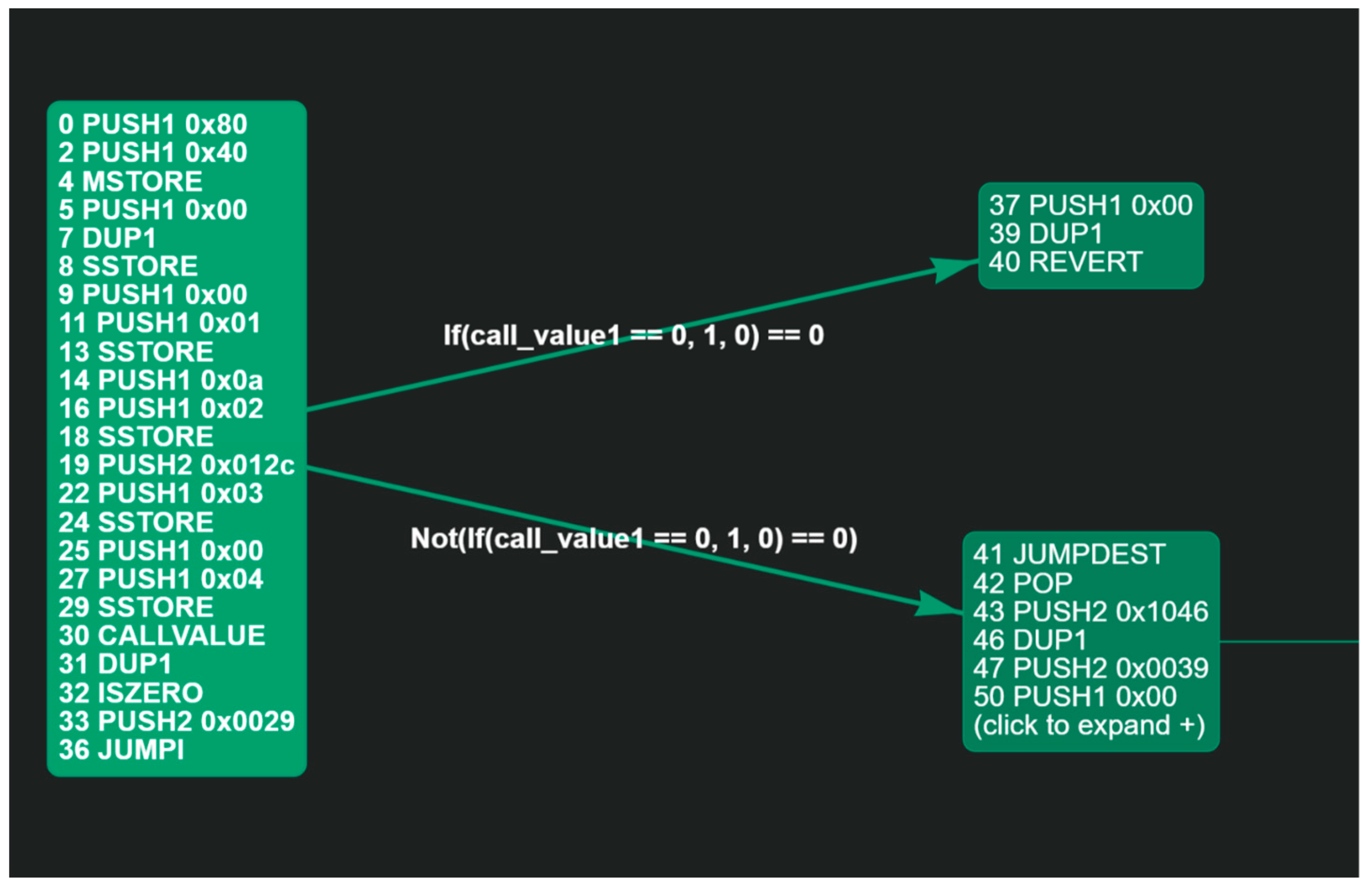


| Method Name | Description | Tools |
|---|---|---|
| Static analysis | Static analysis is the process of examining smart contract source code in order to identify possible risks and vulnerabilities. When the smart contract is not in use, this technique can be used to detect security. Code auditing can be carried out directly or automatically using tools like Smart Check [3] and Slither [4]. | Smart Check [3], Slither [4]. |
| Dynamic analysis | Dynamic analysis is the process of simulating contract’s implementation in an Ethernet virtual machine to find flaws and anomalies. When a smart contract has been deployed, this method is appropriate for security detection and can be carried out automatically using tools or manually. | ContractFuzzer [5] and Reguard [6] |
| Symbolic execution [7] | Symbolic execution is the systematic testing of smart contract code using symbolic variables rather than concrete variables to identify various program execution paths and thereby finding possible flaws and anomalies. This method is appropriate for thorough security testing of smart contracts, but it also necessitates more computational time and resources. | Mythril [8] and Oyente [9] |
| Model testing | Model testing is the process of creating mathematical models of smart contracts and using model verification to identify possible flaws and anomalies. This technique is appropriate for thorough formal verification of smart contracts, but it necessitates a high level of computer science and mathematical knowledge. | SPIN [10,11] |
| Formal verification [12] | As a method for demonstrating that a system meets certain properties, formal verification is based on logical and mathematical reasoning. It is one of the most precise ways to evaluate the system’s precision and early warning saving behavior. | Not fixed |
| Name | Version |
|---|---|
| Processor | 12th Gen Intel(R) Core(TM) i9-12900H 2.50 GHz |
| Memory | RAM 16G |
| Virtual Machine | CentOS 7 |
| Python | 3.9.0 |
| Solc | 0.6.10 |
| Z3-solver | 4.8.9 |
| Pysha3 | 1.0.2 |
| Detection Tool | Total Number of Vulnerabilities | TP | FP | FN | Accuracy | |
|---|---|---|---|---|---|---|
| Mythril | 236 | 203 | 20 | 23 | 86.02% | 90.42% |
| Text scheme | 236 | 222 | 16 | 4 | 94.07% | 95.69% |
| Oyente | 236 | 198 | 26 | 12 | 83.90% | 91.24% |
| Slither | 236 | 200 | 23 | 18 | 84.75% | 90.70% |
| Smart Check | 236 | 196 | 28 | 14 | 83.05% | 90.34% |
| Experimental Method | Unit Time |
|---|---|
| Mythril analysis before improvement | 59.9 s |
| Text scheme | 28.16 s |
| Slither | 30.9 s |
| Smart Check | 32.3 s |
| Oyente | 35.61 s |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sui, J.; Chu, L.; Bao, H. An Opcode-Based Vulnerability Detection of Smart Contracts. Appl. Sci. 2023, 13, 7721. https://doi.org/10.3390/app13137721
Sui J, Chu L, Bao H. An Opcode-Based Vulnerability Detection of Smart Contracts. Applied Sciences. 2023; 13(13):7721. https://doi.org/10.3390/app13137721
Chicago/Turabian StyleSui, Jia, Lili Chu, and Han Bao. 2023. "An Opcode-Based Vulnerability Detection of Smart Contracts" Applied Sciences 13, no. 13: 7721. https://doi.org/10.3390/app13137721
APA StyleSui, J., Chu, L., & Bao, H. (2023). An Opcode-Based Vulnerability Detection of Smart Contracts. Applied Sciences, 13(13), 7721. https://doi.org/10.3390/app13137721





