FPLA: A Flexible Physical Layer Authentication Mechanism for Distributing Quantum Keys Securely via Wireless 5G Channels
Abstract
1. Introduction
- A Dimensional Transformation Residual Network (DTRN) model and a dimensional transformation block (D-block) are proposed to prevent loss of detection accuracy caused by the variation in CSI dimensions;
- A DTRN-based FPLA mechanism is proposed, which dynamically adapts to the antenna diversity in 5G MU-MIMO systems and conforms to QKD network wireless access;
- Authentication performance was evaluated under a time-varying CDL channel model in the 5G FR1 n78 band (3.5 GHz), which aligns with the frequency allocation of China Telecom’s 5G QKD network. The impact of antenna diversity, multiple user access, and various SNR on the authentication performance is evaluated.
2. Related Work
2.1. Quantum Key Distribution (QKD)
2.2. Physical Layer Authentication (PLA)
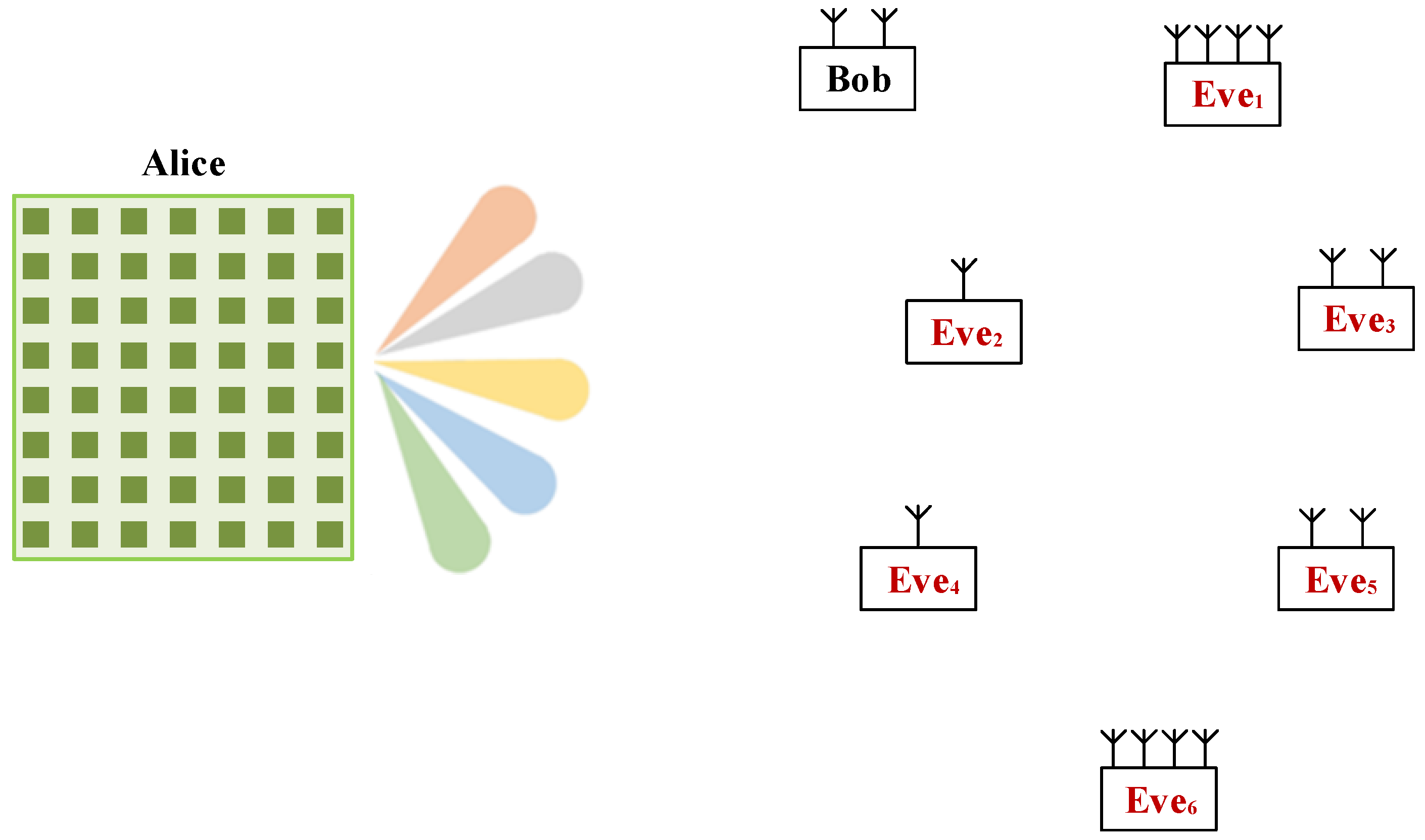
3. System Model
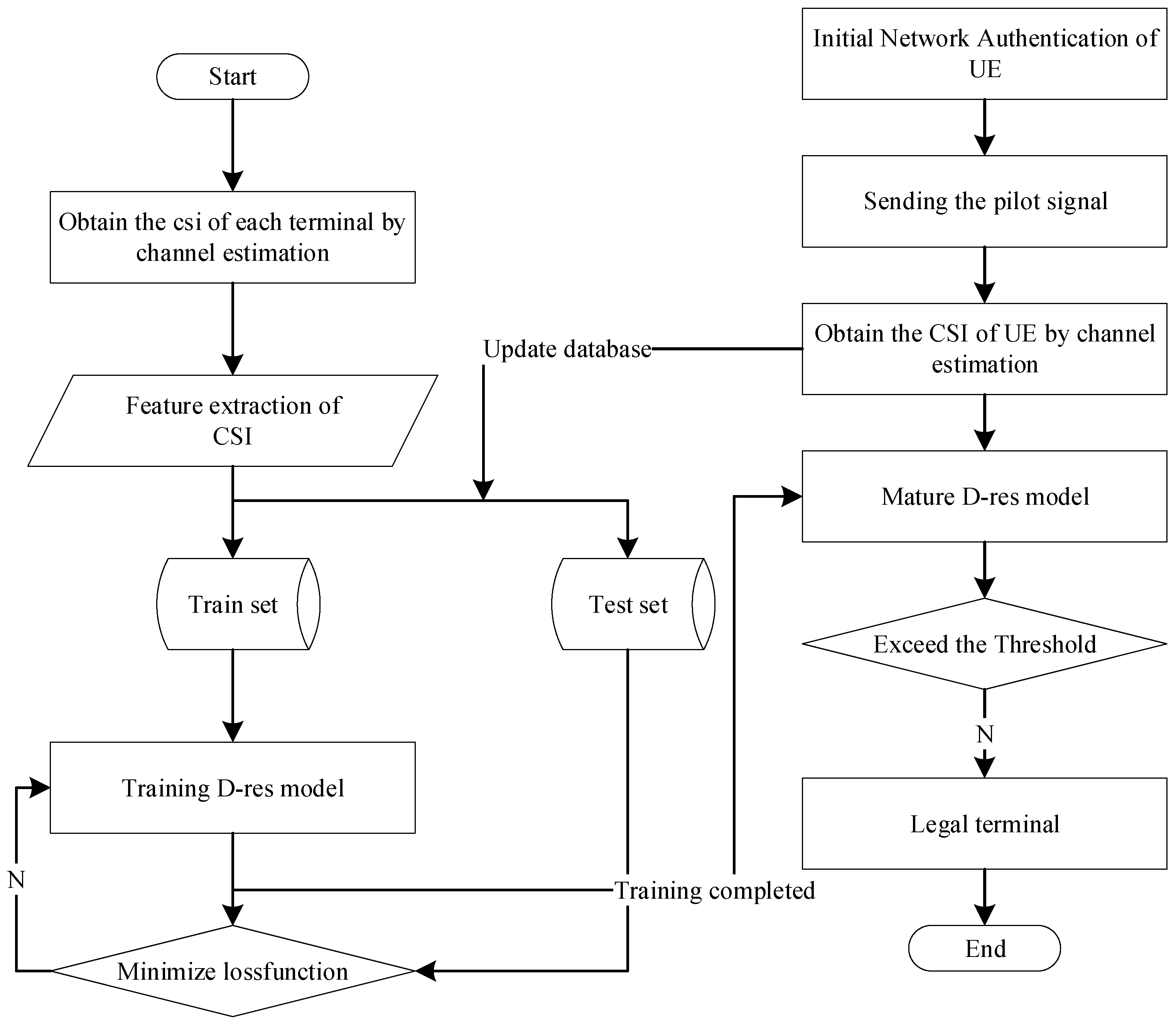
4. Flexible Physical Layer Authentication Mechanism
| Algorithm 1: Train DTRN model |
 |
| Algorithm 2: The operation of FPLA |
 |
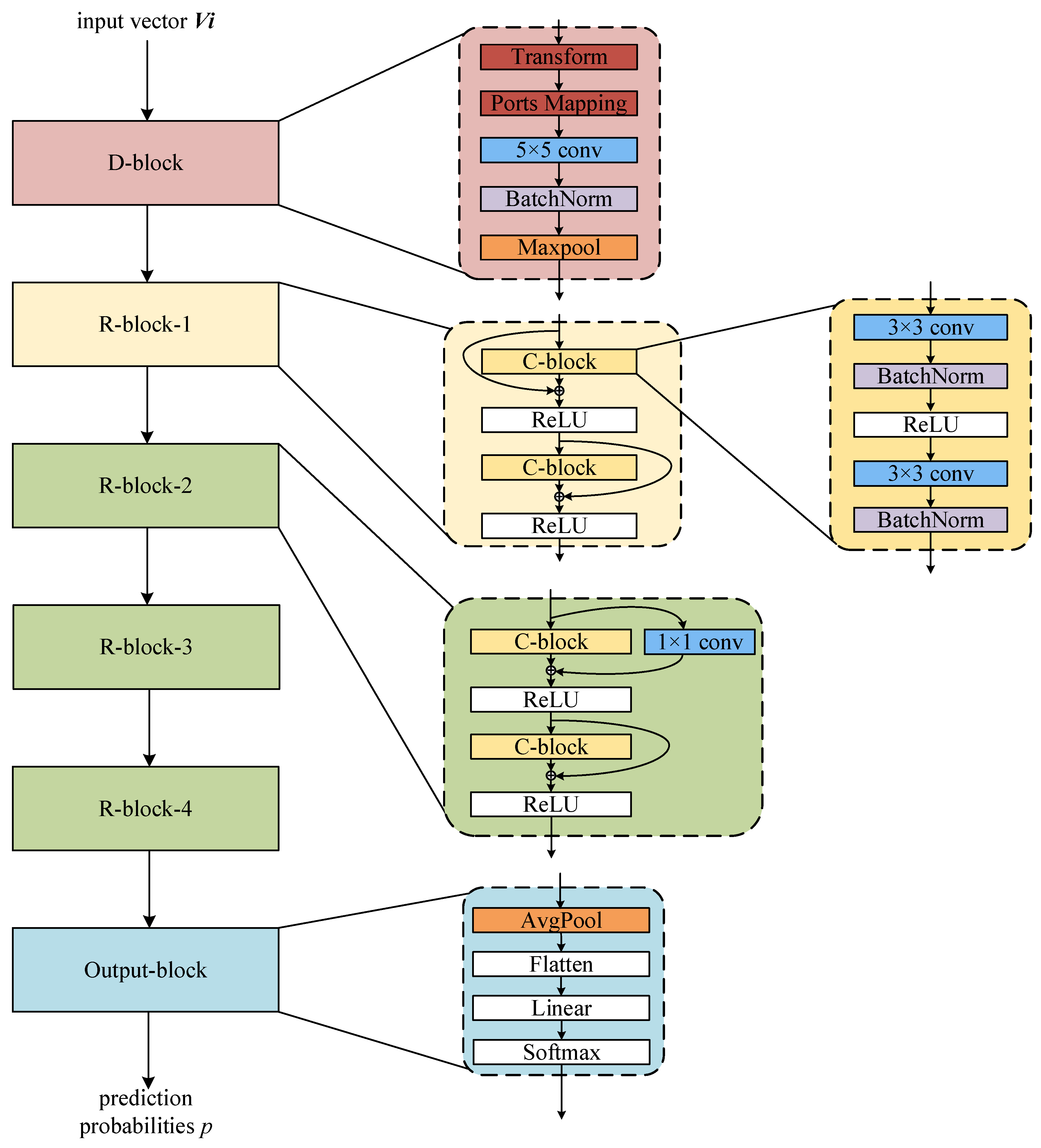
5. Dimensional Transformation Residual Network (DTRN)
6. Evaluation Metrics and Simulation Results
6.1. Evaluation Metrics
- Accuracy ():
- False Alarm Rate ():
- Missed Detection Rate ():
6.2. Simulation Results
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Mehic, M.; Rass, S.; Fazio, P.; Voznak, M. Modern Trends in Quantum Key Distribution Networks. In Quantum Key Distribution Networks A Quality of Service Perspective; Springer: Berlin/Heidelberg, Germany, 2022; pp. 209–223. [Google Scholar] [CrossRef]
- Adnan, M.H.; Ahmad Zukarnain, Z.; Harun, N.Z. Quantum Key Distribution for 5G Networks: A Review, State of Art and Future Directions. Future Internet 2022, 14, 73. [Google Scholar] [CrossRef]
- Kundu, N.K.; Dash, S.P.; Mckay, M.R.; Mallik, R.K. Channel estimation and secret key rate analysis of MIMO terahertz quantum key distribution. IEEE Trans. Commun. 2022, 70, 3350–3363. [Google Scholar] [CrossRef]
- Tefera, M.K.; Jin, Z.; Zhang, S. A Review of Fundamental Optimization Approaches and the Role of AI Enabling Technologies in Physical Layer Security. Sensors 2022, 22, 3589. [Google Scholar] [CrossRef] [PubMed]
- Peng, L.; Hu, A.; Zhang, J.; Jiang, Y.; Yu, J.; Yan, Y. Design of a hybrid RF fingerprint extraction and device classification scheme. IEEE Internet Things J. 2018, 6, 349–360. [Google Scholar] [CrossRef]
- Fang, H.; Wang, X.; Hanzo, L. Learning-aided physical layer authentication as an intelligent process. IEEE Trans. Commun. 2018, 67, 2260–2273. [Google Scholar] [CrossRef]
- Dreifuerst, R.M.; Heath, R.W., Jr. Massive MIMO in 5G: How beamforming, codebooks, and feedback enable larger arrays. arXiv 2023, arXiv:2301.13390. [Google Scholar]
- Xiang, H.; Lv, Y.; Chen, J.; Wu, H.; Wu, H.; Dong, Y.; Chen, H. Application of 5G private network based on quantum communication technology in smart grid. In Proceedings of the Third International Symposium on Computer Engineering and Intelligent Communications (ISCEIC 2022), Jaipur, India, 19–20 January 2023; SPIE: Bellingham, WA, USA, 2023; Volume 12462, pp. 59–64. [Google Scholar]
- Liu, R.; Rozenman, G.G.; Kundu, N.K.; Chandra, D.; De, D. Towards the industrialisation of quantum key distribution in communication networks: A short survey. IET Quantum Commun. 2022, 3, 151–163. [Google Scholar] [CrossRef]
- Ghorpade, S.N.; Zennaro, M.; Chaudhari, B.S.; Saeed, R.A.; Alhumyani, H.; Abdel-Khalek, S. A novel enhanced quantum PSO for optimal network configuration in heterogeneous industrial IoT. IEEE Access 2021, 9, 134022–134036. [Google Scholar] [CrossRef]
- Abd El-Latif, A.A.; Abd-El-Atty, B.; Mazurczyk, W.; Fung, C.; Venegas-Andraca, S.E. Secure data encryption based on quantum walks for 5G Internet of Things scenario. IEEE Trans. Netw. Serv. Manag. 2020, 17, 118–131. [Google Scholar] [CrossRef]
- Al-Mohammed, H.A.; Al-Ali, A.; Yaacoub, E.; Qidwai, U.; Abualsaud, K.; Rzewuski, S.; Flizikowski, A. Machine learning techniques for detecting attackers during quantum key distribution in IoT networks with application to railway scenarios. IEEE Access 2021, 9, 136994–137004. [Google Scholar] [CrossRef]
- Conrad, A.; Isaac, S.; Cochran, R.; Sanchez-Rosales, D.; Wilens, B.; Gutha, A.; Rezaei, T.; Gauthier, D.J.; Kwiat, P. Drone-based quantum key distribution (QKD). In Free-Space Laser Communications XXXIII; SPIE: Bellingham, WA, USA, 2021; Volume 11678, pp. 177–184. [Google Scholar]
- Milovančev, D.; Vokić, N.; Laudenbach, F.; Pacher, C.; Hübel, H.; Schrenk, B. High rate CV-QKD secured mobile WDM fronthaul for dense 5G radio networks. J. Light. Technol. 2021, 39, 3445–3457. [Google Scholar] [CrossRef]
- Cao, Y.; Zhao, Y.; Wang, Q.; Zhang, J.; Ng, S.X.; Hanzo, L. The evolution of quantum key distribution networks: On the road to the qinternet. IEEE Commun. Surv. Tutor. 2022, 24, 839–894. [Google Scholar] [CrossRef]
- Bloom, Y.; Fields, I.; Maslennikov, A.; Rozenman, G.G. Quantum cryptography—A simplified undergraduate experiment and simulation. Physics 2022, 4, 104–123. [Google Scholar] [CrossRef]
- Kaewpuang, R.; Xu, M.; Niyato, D.; Yu, H.; Xiong, Z.; Shen, X.S. Adaptive Resource Allocation in Quantum Key Distribution (QKD) for Federated Learning. In Proceedings of the 2023 International Conference on Computing, Networking and Communications (ICNC), Honolulu, HI, USA, 20–22 February 2023; pp. 71–76. [Google Scholar]
- Solaija, M.S.J.; Salman, H.; Arslan, H. Towards a unified framework for physical layer security in 5G and beyond networks. IEEE Open J. Veh. Technol. 2022, 3, 321–343. [Google Scholar] [CrossRef]
- Muheidat, F.; Dajani, K.; Lo’ai, A.T. Security concerns for 5G/6G mobile network technology and quantum communication. Procedia Comput. Sci. 2022, 203, 32–40. [Google Scholar] [CrossRef]
- Sodhro, A.H.; Awad, A.I.; van de Beek, J.; Nikolakopoulos, G. Intelligent authentication of 5G healthcare devices: A survey. Internet Things 2022, 20, 100610. [Google Scholar] [CrossRef]
- Yu, J.; Hu, A.; Li, G.; Peng, L. A robust RF fingerprinting approach using multisampling convolutional neural network. IEEE Internet Things J. 2019, 6, 6786–6799. [Google Scholar] [CrossRef]
- Marabissi, D.; Mucchi, L.; Stomaci, A. IoT nodes authentication and ID spoofing detection based on joint use of physical layer security and machine learning. Future Internet 2022, 14, 61. [Google Scholar] [CrossRef]
- Liu, Y.; Zhang, P.; Liu, J.; Shen, Y.; Jiang, X. Physical layer authentication in MIMO systems: A carrier frequency offset approach. Wirel. Netw. 2022, 28, 1909–1921. [Google Scholar] [CrossRef]
- Wang, S.; Huang, K.; Xu, X.; Zhong, Z.; Zhou, Y. CSI-Based Physical Layer Authentication via Deep Learning. IEEE Wirel. Commun. Lett. 2022, 11, 1748–1752. [Google Scholar] [CrossRef]
- Qiu, X.; Dai, J.; Hayes, M. A learning approach for physical layer authentication using adaptive neural network. IEEE Access 2020, 8, 26139–26149. [Google Scholar] [CrossRef]
- Abdrabou, M.; Gulliver, T.A. Adaptive physical layer authentication using machine learning with antenna diversity. IEEE Trans. Commun. 2022, 70, 6604–6614. [Google Scholar] [CrossRef]
- Caire, G.; Shamai, S. On the achievable throughput of a multiantenna Gaussian broadcast channel. IEEE Trans. Inf. Theory 2003, 49, 1691–1706. [Google Scholar] [CrossRef]
- Peel, C.B.; Hochwald, B.M.; Swindlehurst, A.L. A vector-perturbation technique for near-capacity multiantenna multiuser communication-part I: Channel inversion and regularization. IEEE Trans. Commun. 2005, 53, 195–202. [Google Scholar] [CrossRef]
- Germain, K.S.; Kragh, F. Physical-layer authentication using channel state information and machine learning. In Proceedings of the 2020 14th International Conference on Signal Processing and Communication Systems (ICSPCS), Adelaide, SA, Australia, 14–16 December 2020; pp. 1–8. [Google Scholar]
- Fang, H.; Wang, X.; Xu, L. Fuzzy learning for multi-dimensional adaptive physical layer authentication: A compact and robust approach. IEEE Trans. Wirel. Commun. 2020, 19, 5420–5432. [Google Scholar] [CrossRef]
- Schreiber, G.; Tavares, M. 5G new radio physical random access preamble design. In Proceedings of the 2018 IEEE 5G World Forum (5GWF), Silicon Valley, CA, USA, 9–11 July 2018; pp. 215–220. [Google Scholar]
- Dahlman, E.; Parkvall, S.; Skold, J. 5G NR: The Next Generation Wireless Access Technology; Academic Press: Cambridge, MA, USA, 2020. [Google Scholar]
- He, K.; Zhang, X.; Ren, S.; Sun, J. Deep residual learning for image recognition. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, Las Vegas, NV, USA, 27–30 June 2016; pp. 770–778. [Google Scholar]
- Qiu, X.; Sun, X.; Hayes, M. Enhanced security authentication based on convolutional-LSTM networks. Sensors 2021, 21, 5379. [Google Scholar] [CrossRef] [PubMed]
- Chen, S.; Wen, H.; Wu, J.; Chen, J.; Liu, W.; Hu, L.; Chen, Y. Physical-Layer Channel Authentication for 5G via Machine Learning Algorithm. Wirel. Commun. Mob. Comput. 2018, 2018, 6039878. [Google Scholar] [CrossRef]





| … | |||||
|---|---|---|---|---|---|
| Port 1 | |||||
| Port 2 | |||||
| Port 3 | |||||
| Port 4 |
| Block | D-Block | R-Block-1 | R-Block-2 | R-Block-3 | R-Block-4 |
|---|---|---|---|---|---|
| Quantity of convs | 1 | 4 | 4 | 4 | 4 |
| Input channels | 4 | 64 | 64 | 128 | 256 |
| Output channels | 64 | 64 | 128 | 256 | 512 |
| Conv kernel | |||||
| Stride | 2 | 2 | 2 | 2 | 2 |
| Parameter | Value |
|---|---|
| Carrier frequency | 3.5 GHz |
| SCS | 15 kHz |
| Number of resource blocks | 106 |
| Channel bandwidth | 20 MHz |
| Antenna array size for BS | 32 |
| Antenna array size for users | 1, 2, 4 |
| CDL channel delay spread | 10 |
| Range of Azimuth offsets | (−60, 60) degree |
| Range of distance between BS and users | (50, 600) m |
| Up-Link SNR | 3, 6, 9, 12, 15 dB |
| Number of malicious users | 1, 2, 3, 4, 5, 6, 7 |
| Mechanism | Approach | Authentication Accuracy and SNR | Samples per UE in Training Dataset | Types of Wireless Networks | Simultaneous Authentication of Multiple Devices with Different Numbers of Antennas |
|---|---|---|---|---|---|
| FPLA mechanism | DTRN | 96.8%, SNR = 3 dB | 300 | 5G FR1 (3.5GHz) | Supported |
| Mechanism [34] | Convolutional-LSTM | 97.6%, SNR = 4 dB | 4000 | IEEE802.11a/g | Supported |
| Mechanism [26] | SVM | 91.0%, SNR = 8 dB | 500 | 5G FR1 (5 GHz) | Not supported |
| Mechanism [35] | AdaBoost | 91.3%, SNR is not specified | 500 | 5G FR1 (3.5GHz) | Not supported |
| Mechanism [29] | GAN | 97.5%, SNR = 6 dB | 400 | Not specified | Not supported |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, Y.; Han, J.; Liu, G.; Zhou, Y.; Liu, T. FPLA: A Flexible Physical Layer Authentication Mechanism for Distributing Quantum Keys Securely via Wireless 5G Channels. Appl. Sci. 2023, 13, 7699. https://doi.org/10.3390/app13137699
Li Y, Han J, Liu G, Zhou Y, Liu T. FPLA: A Flexible Physical Layer Authentication Mechanism for Distributing Quantum Keys Securely via Wireless 5G Channels. Applied Sciences. 2023; 13(13):7699. https://doi.org/10.3390/app13137699
Chicago/Turabian StyleLi, Yuxuan, Jingyuan Han, Gang Liu, Yi Zhou, and Tao Liu. 2023. "FPLA: A Flexible Physical Layer Authentication Mechanism for Distributing Quantum Keys Securely via Wireless 5G Channels" Applied Sciences 13, no. 13: 7699. https://doi.org/10.3390/app13137699
APA StyleLi, Y., Han, J., Liu, G., Zhou, Y., & Liu, T. (2023). FPLA: A Flexible Physical Layer Authentication Mechanism for Distributing Quantum Keys Securely via Wireless 5G Channels. Applied Sciences, 13(13), 7699. https://doi.org/10.3390/app13137699






